#cloud-managed networking
Explore tagged Tumblr posts
Text
High‑Speed and Secure Access Network Solutions – Esconet Technologies
Esconet Technologies offers comprehensive Access Network solutions tailored for enterprise environments. Their network infrastructure suite features high-speed copper and optical fiber connectivity (1 Gbps–100 Gbps), a multilayered design following core/distribution/access best practices, IPv6 readiness, Wi‑Fi 6/6E wireless, cloud-managed systems, advanced security (firewalls, IPS, VPNs), and deployable satellite broadband for remote locations. Partnered with top OEMs (Cisco, Arista, Juniper, Dell, HPE), Esconet ensures scalable, secure, future-ready digital transformation networks. For more details, Visit: Esconet's Access Network solution Page .
#access network solutions#enterprise networking#fiber optic connectivity#high-speed internet infrastructure#Wi-Fi 6 deployment#Wi-Fi 6E network#IPv6 network architecture#cloud-managed networking#enterprise wireless solutions#secure network infrastructure#network security solutions#VPN and firewall services#satellite broadband connectivity#digital transformation infrastructure#Esconet Technologies#copper and fiber network design#scalable network solutions#IT infrastructure services#enterprise IT solutions#smart campus networking
0 notes
Text
Abathur

At Abathur, we believe technology should empower, not complicate.
Our mission is to provide seamless, scalable, and secure solutions for businesses of all sizes. With a team of experts specializing in various tech domains, we ensure our clients stay ahead in an ever-evolving digital landscape.
Why Choose Us? Expert-Led Innovation – Our team is built on experience and expertise. Security First Approach – Cybersecurity is embedded in all our solutions. Scalable & Future-Proof – We design solutions that grow with you. Client-Centric Focus – Your success is our priority.
#Software Development#Web Development#Mobile App Development#API Integration#Artificial Intelligence#Machine Learning#Predictive Analytics#AI Automation#NLP#Data Analytics#Business Intelligence#Big Data#Cybersecurity#Risk Management#Penetration Testing#Cloud Security#Network Security#Compliance#Networking#IT Support#Cloud Management#AWS#Azure#DevOps#Server Management#Digital Marketing#SEO#Social Media Marketing#Paid Ads#Content Marketing
4 notes
·
View notes
Text
Senior Specialist - AI Strategy & Innovation
Job title: Senior Specialist – AI Strategy & Innovation Company: IO Global Job description: to shape the future direction of IOG strategies and products. As a Senior AI Specialist focusing on Big… Development Design, develop, and implement custom AI and machine learning models (including LLMs, deep learning, and NLP… Expected salary: Location: United Kingdom Job date: Fri, 04 Jul 2025 22:34:00…
#Android#Blockchain#cloud-computing#CRM#data-engineering#digital-twin#Ecommerce#ethical AI#ethical-hacking#Frontend#game-dev#hybrid-work#iot#Java#low-code#Networking#NLP Specialist#no-code#product-management#prompt-engineering#proptech#quantum computing#regtech#remote-jobs#sharepoint#solutions-architecture#technical-writing#visa-sponsorship#vr-ar
0 notes
Text
How Cloud-Based Network Monitoring Boosts Performance
In today’s always-connected world, your network is the backbone of everything—whether it’s running a business app, streaming data, or just keeping systems online. But when things slow down or go offline, the impact is immediate and costly. That’s where cloud-based network monitoring comes in—and it’s changing the game for businesses of all sizes.

Key Benefits of Cloud-Based Network Monitoring
Here’s how it helps boost your performance:
Real-time visibility from anywhere, anytime
Faster issue detection and resolution—before users notice
Scalability and flexibility that grow with your business
Fewer outages and surprises with proactive alerts
Peace of mind for IT teams with 24/7 control
Why It Matters for Your Team and Customers
The human side of this is huge. No one wants to be the last to know when there’s an outage. With cloud-based tools, IT teams can get alerts instantly, fix issues faster, and breathe easier knowing they have full control—even on the go. That peace of mind matters, especially when every second of downtime can affect customer experience.
Final Thoughts
It’s not just about fixing problems—it’s about preventing them, and giving your team the tools to work smarter, not harder. In the end, better network visibility leads to better performance, fewer disruptions, and happier users.
If performance, uptime, and flexibility are important to your business, cloud-based network monitoring is a smart move—and one that pays off every single day.
0 notes
Text
Top Network Firewall Solutions for Modern Enterprises in 2025

Today, information doesn't reside in your office anymore—it resides everywhere. From cloud-based systems and remote devices to in-office PCs and customer-facing apps, data is in constant motion. And so are cyber attacks. That's why counting on traditional perimeter security simply won't be enough today. It's time to think smarter, not harder,and that's where creative Network Firewall Solutions shine.
Enterprise Network Security needs have grown larger for 2025. Businesses are not seeking a virtual "doorman." They desire end-to-end solutions that can manage firewall policy administration, superior traffic filtering, hybrid environments, and remote work, while still remaining scalable and manageable.
1. Sangfor Athena NGFW: Next-Gen Security for a Cloud-First World
If you’re looking for a firewall that works with you—not against you—Sangfor Athena NGFW is built for today’s agile enterprise. As one of Sangfor’s leading cyber security products, it’s designed to protect businesses that are embracing cloud technologies, managing remote teams, and juggling compliance requirements across industries.
Key benefits include:
AI-powered threat detection with real-time insights
Advanced traffic filtering to spot suspicious activity
Smart policy control for hybrid and mobile workforces
Seamless integration with Cloud Firewall Services
Centralized dashboard for easier firewall policy management
Whether you’re scaling your business or safeguarding sensitive customer data, this solution balances security with simplicity, so your team stays protected without being overwhelmed.
2. Palo Alto Networks PA-Series: Great for Detailed Control
Palo Alto’s PA-Series remains a trusted name, especially for companies that need detailed traffic and user-level oversight. Their App-ID, User-ID, and Content-ID systems allow IT teams to create very specific access policies.
What it offers:
Efficient processing via Single Pass Architecture
DNS security and threat prevention with sandboxing
Smart segmentation for Zero Trust implementations
Public cloud integration (AWS, Azure)
That said, it may require a more hands-on approach, so it's best suited for organizations with experienced IT security staff.
3. Fortinet FortiGate: Speed & Performance for Multi-Site Enterprises
FortiGate remains a strong contender for businesses with multiple locations. With built-in SD-WAN and reliable performance, it’s a practical choice for growing companies.
Why it works:
Strong support for VPN and Zero Trust setups
FortiGuard threat intel included
Tools for intuitive firewall policy management
Built for distributed teams and branch offices
It’s especially appealing to businesses looking for a balance between performance and reliability across locations.
4. Cisco Firepower NGFW: Designed for Adaptability
Cisco’s Firepower brings together legacy routing strengths with modern defense tools. The result is a modular network firewall solution that works well for companies navigating hybrid or cloud-first environments.
Core capabilities:
Intrusion detection powered by machine learning
Visibility across devices and endpoints
Integration with Cisco SecureX for smart analytics
Centralized management for policies and access
While it’s a robust platform, its complexity might be overkill for small teams without dedicated security pros.
5. Sophos XGS Firewall: Clean UI, Strong Security
For businesses that want security without the technical clutter, Sophos XGS Firewalls offer a streamlined experience. They’re a great choice for SMBs and educational institutions that need to hit the ground running.
Key benefits:
Fast deep-packet inspection with dual engines
Synchronized security between endpoints and firewalls
Built-in response automation
Simple policy creation for non-specialists
It’s an accessible network firewall solution for organizations that want modern protection without a steep learning curve.
What to Look for in a Firewall in 2025
Choosing the right Network Firewall Solutions is about more than specs. It’s about how well it fits into your overall strategy and day-to-day operations.
Here are a few things worth prioritizing:
Firewall Policy Management: Is it simple to write, modify, and push rules to numerous sites without the risk of human error?
Traffic Filtering & Inspection: Can it scan what is occurring inside encrypted traffic? Does it flag suspicious behavior ahead of damage being caused?
Cloud Compatibility: Let’s be real—most of your tools and files aren’t sitting on a local server anymore. They’re out there, across cloud platforms, apps, and services. If your firewall can’t keep up or keeps breaking things in the cloud, it’s going to slow you down. Make sure it fits in—not fights—with the rest of your tech.
Scalability: You’re probably not standing still. Teams grow, services change, and suddenly you’ve got more people and places to protect. A firewall that can’t stretch with you? That’s going to be a problem. Look for something that expands as naturally as your business does, without needing a full rebuild every time.
Secure Remote Access: People don’t just work from the office anymore. They work from cafés, at home, airports—everywhere. You want your firewall to help with that, not get in the way. VPNs, Zero Trust, cloud security—all that stuff should be baked in and work without drama.
Compliance-Focused Features: If you deal with healthcare, payments, or anything sensitive, you know compliance isn’t just a checklist—it’s constant. A good firewall helps you stay ready. It should log what matters, keep data encrypted, and not turn audits into panic mode.
Final Thoughts
Firewalls used to just say “yes” or “no” to incoming traffic. Now, the best network firewall solutions have to do a lot more, without slowing you down.
If your business is growing, going remote, or handling sensitive info, you’ll want something that doesn’t just sit here—it should actively help. Look for a firewall that’s smart, scalable, cloud-aware, and honestly… one that doesn’t make your IT team want to scream.
Choose wisely. And don’t just go with what’s “best.” Go with what’s best for your business.
#firewall policy management#perimeter security#traffic filtering#Enterprise Network Security#Cloud Firewall Services
0 notes
Text

Azure Administration Training – Get AZ-104 Certified - Evision Technoserve
Boost your IT career with Evision Technoserve’s Azure Administration Training and become AZ-104 certified! This industry-focused program offers hands-on labs, real-time projects, and expert-led mentorship to help you master Microsoft Azure essentials—Virtual Machines, Identity, Storage, Networking, and more. Designed for certification success, the course also includes 100% placement assistance to launch your career in cloud computing. Don’t miss out on top internship and job opportunities.
#azure administrator training with placement india#job-ready azure administration course evision#azure certification course with real labs#microsoft azure admin training freshers#az-104 exam guarantee evision technoserve#azure hands-on course for beginners india#cloud computing certification for job seekers#azure virtual machine training with projects#identity management azure course placement#storage & networking azure admin training#exclusive az-104 preparation evision india#azure administration internship program 2025#beginner to expert azure course with jobs#azure certification training with mentorship#placement assured azure admin certification#microsoft azure practical training india#evisiontechnoserve
0 notes
Text
CBDC technology partner India
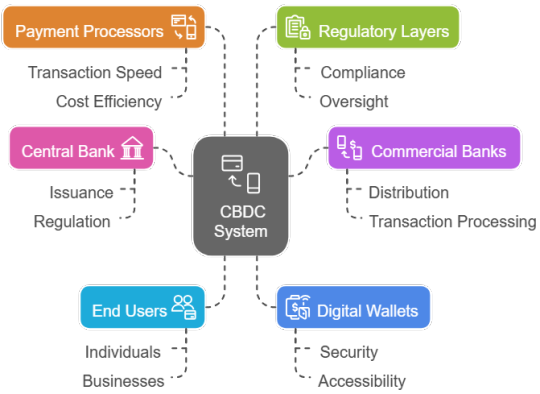
As CBDCs become a global reality, Prodevans equips banks with everything needed to enter the digital currency ecosystem. We provide full-spectrum CBDC implementation — including compliant architecture, token management, real-time reconciliation, secure wallet enablement, and 24/7 L1/L2 support. Trusted for our role in India’s national rollout, we help institutions go beyond pilots to scalable, production-ready platforms ensuring seamless end- user readiness. Our services ensure central bank compliance while delivering performance, observability, and rapid response to evolving regulatory needs. Whether you’re in the pilot phase or preparing for production rollout, Prodevans supports your CBDC journey at every step.
OUR ADDRESS
403, 4TH FLOOR, SAKET CALLIPOLIS, Rainbow Drive, Sarjapur Road, Varthurhobli East Taluk, Doddakannelli, Bengaluru Karnataka 560035
OUR CONTACTS
+91 97044 56015
#CBDC (Central Bank Digital Currency)#Cloud Computing & Cloud Services#Application Modernization#360° Monitoring (Server#Application#Database & Virtualization Monitoring)#Identity & Access Management (IAM)#Automation (incl. ML‑driven#Ansible#network/cloud automation)#DevOps Tools & Support#Infrastructure Management (IaaS/PaaS/SaaS#orchestration#orchestration tools)
0 notes
Text
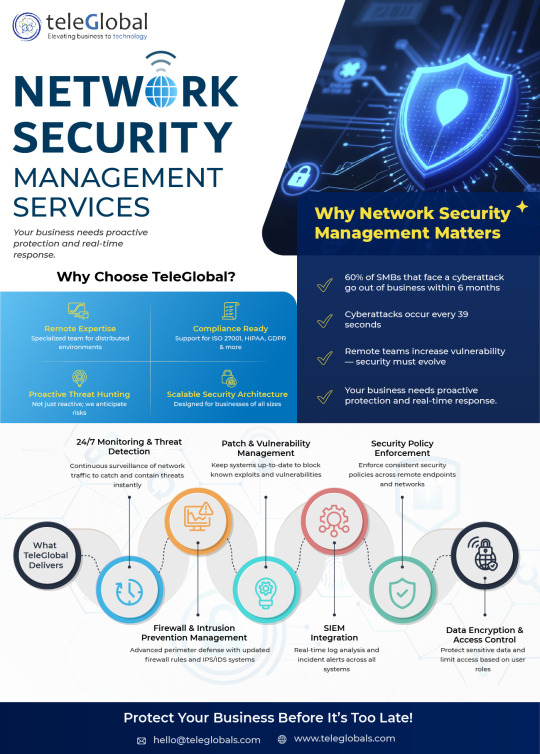
Network Management Services in Pune | Teleglobal
Empower Your Network for Efficient Performance From network setup and monitoring to firewalls and load balancer setup, we offer a secure, optimized, and high-performing network infrastructure. Our Network Management Services provides end-to-end solutions that boost network security, performance, and reliability, ensuring nothing interrupts connectivity of your business.
Optimize Your Network Today https://teleglobals.com/contact-us
#Network Management Services#Network Management#IT Infrastructure#Remote Monitoring#IT Support#Managed Services#Tech solutions#Digital Transformation#Cloud Computing#Cyber Security#Business Continuity
0 notes
Text

The best network management services help manage an organization's network using secure firewalls and malware detection controllers. They also collect data from connected network devices such as switches, routers, access points, and client devices. These services facilitate smooth interaction between devices. Net Access India Limited provides this service at an affordable price. Please reach out to us for more information and a free demo.
#network management services#IT infrastructure management services#IT infrastructure management services in india#net access india limited#gate management software#field force management software#crop management software#IT infra solutions#network management software#managed cybersecurity services#managed datacenter services#end-user support services#endpoint security services#lease management software#board meeting software#phishing simulation services in india#vapt testing services in india#cloud managed services providers in india#mdm solutions#network transformation services
0 notes
Text
Euroland IT Store – Expert IT Services & Support Across the UK
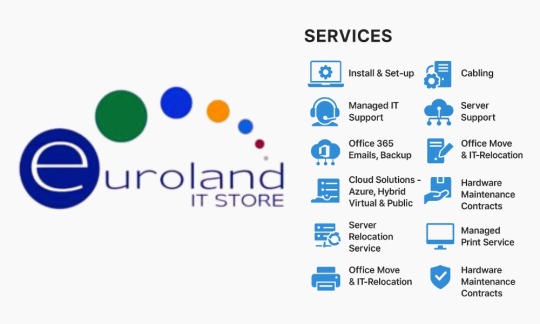
Discover Euroland IT Store's professional IT services, from system installations and network cabling to managed support, cloud solutions, and hardware maintenance. Trusted by businesses nationwide for reliable and efficient IT solutions. Our team ensures minimal downtime and seamless performance, helping your business stay ahead.
0 notes
Text
Cyber Security Services Company | Data Security Solutions

In today’s fast-paced digital world, businesses increasingly rely on technology to store, process, and transmit sensitive data. As companies across industries harness the power of the internet, the need for robust cybersecurity services has never been more crucial. Data breaches and cyberattacks are growing threats from small startups to large corporations that can have devastating consequences. That’s where a cybersecurity company specializing in data protection services and cybersecurity management comes into play.
This blog explores the importance of cybersecurity management, the types of services offered by a cybersecurity services company, and how data protection services and endpoint security services can help businesses protect their sensitive information.
Understanding the Growing Importance of Cybersecurity
The digital transformation that businesses have undergone in recent years has revolutionized operations, providing significant benefits like improved efficiency, better customer engagement, and more streamlined processes. However, this transformation has also opened new doors for cybercriminals who exploit vulnerabilities in systems and networks to steal data, launch attacks, and disrupt operations.
With data breaches and cyberattacks on the rise, organizations must safeguard sensitive information from unauthorized access, manipulation, and theft. Whether it’s customer data, intellectual property, or financial records, securing these assets is paramount to maintaining trust, compliance with regulations, and protecting brand reputation.
Cybersecurity solutions providers play a key role in defending organizations from these threats. Cybersecurity isn’t just a technical need—it’s a business priority that can help prevent costly disruptions, legal ramifications, and loss of customer confidence. This is where the role of a cybersecurity consulting firm becomes indispensable.
What Is a Cybersecurity Services Company?
A cybersecurity services company specializes in identifying, mitigating, and preventing cyber threats. They provide tailored solutions to ensure businesses’ information and infrastructure are well-protected from a wide range of security risks. These companies are essential partners in safeguarding businesses from cyberattacks and ensuring the security of sensitive data and systems.
Key Services Provided by a Cybersecurity Services Company

Cybersecurity companies offer a range of services designed to safeguard businesses from evolving threats. These services include:
Threat Detection & Prevention Services: Cybersecurity companies deploy advanced monitoring tools and techniques to detect vulnerabilities, anomalous activities, and potential threats before they cause harm. This includes setting up firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS).
Risk Management: Cybersecurity firms assess vulnerabilities and design strategies to safeguard businesses from both internal and external threats. A cyber risk management company helps ensure that businesses are prepared for any potential cyber risks.
Cybersecurity Audits & Assessments: Regular security audits and penetration testing are vital for identifying weaknesses in a company’s infrastructure. These audits ensure no part of the system remains unprotected.
Compliance Support: For businesses in regulated industries, cybersecurity compliance services help ensure adherence to standards like GDPR, HIPAA, and PCI DSS. Companies in these industries can also benefit from IT security services companies that provide guidance and support for meeting compliance requirements.
Incident Response & Disaster Recovery: Even with robust security measures, breaches can still occur. Incident response services help businesses respond quickly and effectively to limit damage. Additionally, cybersecurity audit services and vulnerability assessment companies help identify and prevent potential attacks before they materialize.
Employee Training & Awareness: Cybersecurity management companies often provide training programs to raise awareness about phishing, password hygiene, and safe online behavior, reducing human error and improving security.
Types of Data Security Solutions Offered by Cybersecurity Companies

At the core of every cybersecurity service is data protection. Cybersecurity solutions providers offer several key solutions to help businesses secure their information:
Encryption: Encryption ensures that even if data is accessed by cybercriminals, it remains unreadable without the decryption key. Cloud security companies offer encryption solutions to protect data stored in the cloud, safeguarding sensitive information during transit and while at rest.
Access Control & Authentication: Multi-factor authentication (MFA) and role-based access control (RBAC) are implemented to ensure only authorized personnel can access sensitive systems.
Data Loss Prevention (DLP): Data protection services monitor data transfers and emails to prevent unauthorized sharing or leakage of confidential information.
Firewalls & Network Security: Firewalls act as the first line of defense by filtering traffic and blocking harmful activities. Network security services providers ensure that your network is properly configured with firewalls, VPNs, and network segmentation to protect data from external attacks.
Backup & Disaster Recovery: A comprehensive backup and recovery plan ensures that lost or compromised data can be restored with minimal disruption to business operations. Cloud security companies play a key role in providing reliable cloud-based backup and recovery services.
Endpoint Security: With more employees working remotely, endpoint security services are becoming essential. Cybersecurity firms implement solutions to protect mobile devices, laptops, and tablets from threats.
Why Partner with a Cybersecurity Services Company?
Businesses of all sizes can benefit from the specialized expertise of a cybersecurity consulting firm. Here are some reasons why partnering with one is essential:
Expertise and Experience
Cybersecurity is a complex field requiring in-depth knowledge of emerging threats and security solutions. A cybersecurity services company brings years of experience and expertise to the table, ensuring best practices and cutting-edge tools are used to protect your data.
Cost Efficiency
Building an in-house cybersecurity team can be costly. By outsourcing to a cybersecurity solutions provider, businesses gain access to expert resources and advanced technologies without the need to invest in full-time staff.
Proactive Protection
Rather than waiting for a breach to occur, a cybersecurity management company helps you adopt a proactive approach by identifying and neutralizing potential threats before they can impact your business.
Regulatory Compliance
Staying compliant with regulations like GDPR, HIPAA, and CCPA can be challenging. A cybersecurity services company ensures your business complies with relevant data protection laws, avoiding legal complications and fines. These companies provide cybersecurity compliance services to meet the highest standards of data protection.
Business Continuity
Cybersecurity services also encompass disaster recovery planning, ensuring that your business can continue to operate smoothly after a cyber attack or natural disaster. Security operations center services ensure continuous monitoring, offering peace of mind that any security breaches are quickly detected and neutralized.
Conclusion: Protect Your Business with a Cybersecurity Services Company
As cyber threats continue to evolve, businesses must take proactive steps to protect their sensitive data and maintain customer trust. Partnering with a reputable cybersecurity consulting firm ensures that you have the right tools, expertise, and strategies in place to prevent cyberattacks, secure your data, and maintain regulatory compliance.
Whether it’s through penetration testing, endpoint security services, or incident response services, a cybersecurity services company plays a crucial role in keeping your data safe and your business running smoothly.
Investing in cybersecurity solutions today can help prevent significant financial and reputational damage in the future. Don't wait until it's too late—reach out to a trusted cybersecurity services company today to protect your data and your business's future.
#Cyber Security Services Company | Data Security Solutions#Cybersecurity Management Company#Managed Cyber Security Services#Cyber Security Company#Cyber Security Services#Endpoint Security Services#Cybersecurity Solutions Provider#Cyber Security Consulting Firm#Network Security Services#Cybersecurity Audit Services#IT Security Services Company#Cloud Security Company#Data Protection Services#Cybersecurity Compliance Services#Security Operations Center Services#Threat Detection Services#Penetration Testing Company#Incident Response Services#Vulnerability Assessment Company#Cyber Risk Management Company#Information Security Services
0 notes
Text

At Preemptive Technofield, we specialize in helping organizations navigate their digital journey with tailored IT infrastructure solutions. Enhance your business efficiency, agility, and measurable outcomes with our expert consulting.
#network design#it infrastructure#Enterprise System Integration#Cloud Migration#Managed Services#Cybersecurity Solutions#Data Center Solutions#Unified Communications & Collaboration#AMC & IT Support Services
1 note
·
View note
Text
Empower Your Business with Dedicated IT Resources from Quarec Resources Pvt. Ltd.

At Quarec Resources Pvt. Ltd., we provide top-tier Dedicated IT Resources to propel your business forward. Our skilled IT professionals seamlessly integrate with your team, offering expertise in software development, system administration, network management, and more. By choosing our dedicated resources, you gain flexibility, cost-efficiency, and the ability to swiftly adapt to evolving technological demands. Partner with Quarec to ensure your IT operations are robust, scalable, and aligned with your strategic goals.
#Dedicated IT Resources#IT Staff Augmentation#Dedicated IT#Software Development Team#System Administration Services#Network Management Solutions#IT Outsourcing#Remote IT Support#IT Consulting#Cloud Computing Services#Cybersecurity Solutions#Data Analytics Services#IT Project Management#Technical Support Services#IT Infrastructure Management
0 notes
Text
Technical Application Specialist
Job title: Technical Application Specialist Company: Jefferson Frank Job description: Technical Application Specialist Location – London (3 days per week minimum) Contract length – 6 months… Job Description Technical Application Specialist, acting as our Subject Matter Expert, leading the design, support, and continuous improvement… Expected salary: Location: London Job date: Thu, 17 Jul 2025…
#agritech#artificial intelligence#Automotive#Bioinformatics#Cloud Security Specialist#cloud-computing#Crypto#Cybersecurity#data-privacy#DevOps#dotnet#edtech#erp#ethical-hacking#fintech#GIS#hybrid-work#insurtech#it-support#Java#low-code#Machine learning#metaverse#Networking#product-management#Salesforce#site-reliability#technical-writing#visa-sponsorship
0 notes
Text
Bdtechsupport: Comprehensive IT Solutions for Your Business Needs
In today’s fast-paced digital world, businesses require robust IT solutions to stay ahead of the competition. Bdtechsupport is a company that provides innovative, reliable, and professional IT support services to ensure that your business operations run smoothly. With a dedicated team and a variety of services, Bdtechsupport caters to businesses of all sizes and industries. Whether you need managed IT services, technical support, or network solutions, Bdtechsupport has you covered.
For more information, you can visit their website at Bdtechsupport.
What is Bdtechsupport?
Bdtechsupport is an IT support and solutions company that specializes in offering high-quality services to businesses seeking technology-related assistance. From small startups to large enterprises, Bdtechsupport tailors its services to meet the specific needs of your business, providing expert guidance and reliable solutions.
Key Services Offered by Bdtechsupport
Bdtechsupport covers a wide range of IT services, including:
Managed IT Services: These services ensure that your IT systems are constantly monitored, maintained, and optimized. Bdtechsupport proactively addresses any potential issues to minimize downtime and enhance productivity.
Technical Support: With a team of highly skilled technicians, Bdtechsupport offers round-the-clock technical support for any IT-related challenges your business may face.
Network Solutions: Bdtechsupport provides network installation, management, and troubleshooting services to ensure that your communication systems are efficient and secure.
Cloud Services: Bdtechsupport helps businesses transition to cloud computing, enabling better data storage, access, and collaboration.
Cybersecurity Solutions: Protecting your business from cyber threats is crucial. Bdtechsupport offers robust cybersecurity measures to safeguard your sensitive data and prevent security breaches.
Why Choose Bdtechsupport?
Expert Team
Bdtechsupport’s team of experienced IT professionals offers tailored services that address the unique challenges businesses face in the digital landscape. Their expertise helps ensure that your systems operate seamlessly, reducing risks and improving productivity.
Customized Solutions
Bdtechsupport understands that no two businesses are the same. They provide customized solutions that align with your specific business goals and IT requirements. This personalized approach ensures that your IT needs are met efficiently and effectively.
Reliability and Trust
With years of experience and a proven track record, Bdtechsupport has built a reputation for reliability and trust. They take pride in offering consistent, top-quality service, allowing your business to thrive without worrying about IT issues.
Cost-Effective Solutions
Bdtechsupport’s services are designed to be both effective and affordable. By outsourcing your IT needs to Bdtechsupport, you can reduce operational costs while still receiving exceptional service.
Frequently Asked Questions (FAQ)
What industries does Bdtechsupport serve?
Bdtechsupport provides IT solutions to a wide range of industries, including healthcare, education, finance, retail, and more. Their expertise allows them to adapt to the specific IT needs of each sector.
How can I contact Bdtechsupport for support?
You can reach Bdtechsupport through their website at Bdtechsupport Contact or by calling their customer service hotline. They also offer email support for non-urgent inquiries.
Do I need to sign a contract to receive IT support from Bdtechsupport?
Bdtechsupport offers both contract-based and non-contract options. You can choose the service model that best fits your business needs. Whether you need ongoing support or one-time assistance, Bdtechsupport can accommodate you.
How does Bdtechsupport ensure data security?
Bdtechsupport takes data security seriously. They use industry-leading security protocols, encryption, and firewalls to protect your data from cyber threats. Their cybersecurity solutions are designed to keep your sensitive information safe from unauthorized access.
Can Bdtechsupport assist with cloud migration?
Yes, Bdtechsupport has extensive experience with cloud services and can assist businesses with migrating to the cloud. They will ensure a smooth transition with minimal disruption to your operations.
Conclusion: Why Bdtechsupport Is Your Ideal IT Partner
In a world that’s increasingly dependent on technology, having a reliable IT support provider is crucial for the success and growth of any business. Bdtechsupport offers a comprehensive suite of IT services that cater to the unique needs of your business. Their expert team, customized solutions, and commitment to delivering top-quality service make them an ideal partner for any organization looking to enhance its IT infrastructure. With Bdtechsupport, you can focus on what matters most – growing your business – while they take care of all your IT needs.
For more information about the services provided by Bdtechsupport, visit Bdtechsupport today!
#IT Support#Managed IT Services#Network Solutions#Cybersecurity#Cloud Services#Technical Support#Business IT Support#IT Consulting#Business Solutions#Bdtechsupport#Data Security#Cloud Migration#Tech Support
0 notes
Text
Wireless SIP Phones by DC Networks – Smarter Office Communication with ATCOM

DC Networks offers advanced Wireless SIP Phones built for today’s dynamic workplaces. The ATCOM A48WAC is perfect for junior managers with dual-band Wi-Fi and gigabit connectivity, while the ATCOM A68WAC delivers POE support and robust features for senior managers. Fully compatible with any SIP open standard IP PBX—cloud-based or on-premises. Upgrade to ATCOM phones with DC Networks for seamless, scalable communication.
#DC Networks#Wireless SIP Phone#ATCOM SIP Phone#SIP Phone for Office#A48WAC#A68WAC#SIP IP Phone#Dual Band WiFi Phone#Gigabit IP Phone#Business Communication#SIP Phone for Managers#Office VoIP Solutions#Cloud PBX Phone#IP Phone with WiFi#POE SIP Phone
0 notes