#Network Management Solutions
Explore tagged Tumblr posts
Text
Empower Your Business with Dedicated IT Resources from Quarec Resources Pvt. Ltd.

At Quarec Resources Pvt. Ltd., we provide top-tier Dedicated IT Resources to propel your business forward. Our skilled IT professionals seamlessly integrate with your team, offering expertise in software development, system administration, network management, and more. By choosing our dedicated resources, you gain flexibility, cost-efficiency, and the ability to swiftly adapt to evolving technological demands. Partner with Quarec to ensure your IT operations are robust, scalable, and aligned with your strategic goals.
#Dedicated IT Resources#IT Staff Augmentation#Dedicated IT#Software Development Team#System Administration Services#Network Management Solutions#IT Outsourcing#Remote IT Support#IT Consulting#Cloud Computing Services#Cybersecurity Solutions#Data Analytics Services#IT Project Management#Technical Support Services#IT Infrastructure Management
0 notes
Text
BMW New Car Sales Executive
Job title: BMW New Car Sales Executive Company: BMW Group Retail Job description: on, one weekend off. IT literate – knowledge of MS Office & CRM systems preferred. Rewards Working Pattern: 5-day schedule… a premium BMW at a reduced cost. Specialist training with BMW UK + BMW Accreditation. Genuine career progression… Expected salary: Location: Warrington, Cheshire Job date: Sun, 29 Jun 2025…
#agritech#artificial intelligence#audio-dsp#Automotive#Azure#Backend#Broadcast#CRM Specialist#Crypto#data-engineering#data-privacy#embedded-systems#game-dev#govtech#healthtech#Java#legaltech#low-code#marine-tech#metaverse#mlops#Networking#no-code#product-management#prompt-engineering#proptech#remote-jobs#SEO#solutions-architecture
2 notes
·
View notes
Text

Smart Home Solutions at Palm Beach Audio Visions
At Palm Beach Audio Visions (PBAV), we are passionate about delivering exceptional audio visual, home automation, lighting, and technology integration solutions for residential and commercial projects. From the initial concept to the final system deployment, we are dedicated to ensuring that projects are completed on time and within budget while exceeding industry standards for quality. Our team of experienced professionals brings a wealth of expertise in the high-end market and a strong focus on building lasting relationships with our clients. Feel free to visit us!
#Lutron Homeworks Dealer Whole House Smart Lighting Consultant#Design#Installation#Manager Solutions#Smart Home Network Setup Wifi Installation#Smart Home Security Camera Installation#Lutron Smart Window Electric Shades#Outdoor Entertainment System Design Installation Solution with Pool Patio Surround Sound Speakers#Outdoor Patio TV speaker Solution with Surround Sound#Universal Remote Control Smart Touch Screen Solution Programming Installation in Frenchman's Creek Palm Beach Gardens#Samsung QLED#Sony OLED#LG OLED Smart TV Dealer Installation Service#Home Theater System Consultant#Design and Installation Services#Sonos Dealer and Speaker Installation#Surround Sound Setup with In-ceiling Invisible Speakers#Whole House Multi Room Home Audio Installation Services#Smart Home Technology Consultant#Whole Home Automation Expert Installation Company#Control4 Smart Home Dealer - Installer
3 notes
·
View notes
Text
Cybersecurity Made Easy: Sigzen Technologie’s Approach to Effective Vulnerability Management
In today’s digital age, cybersecurity is paramount to safeguarding sensitive data and maintaining business continuity. As cyber threats continue to evolve, organizations must adopt comprehensive strategies to mitigate risks effectively. Sigzen Technologies offers cutting-edge solutions in Vulnerability Management, making cybersecurity easy and effective for businesses of all sizes. Vulnerability…

View On WordPress
#Cybersecurity Solutions#Data Privacy#Information Security#Network Vulnerabilities#Security Solutions#Vulnerability Management
3 notes
·
View notes
Text
Maximize Rack Space with Vertical Cable Management at RitchField Network Solutions
Efficient cable management is the backbone of any high-performing IT infrastructure. At RitchField Network Solutions, we offer robust vertical cable management solutions designed to streamline your server rooms and data centers while enhancing airflow, organization, and accessibility.

Vertical cable management is essential for maintaining a clean and efficient network setup. Unlike horizontal cable managers that route cables across racks, vertical cable management systems guide and secure cables along the side of server cabinets or racks. This method prevents tangled wires, reduces stress on connections, and allows technicians to identify and access cables quickly during maintenance or upgrades.
At RitchField Network Solutions, we provide a range of vertical cable management options tailored to your specific requirements. Whether you manage a small server room or a large-scale data center, our products ensure that cables are neatly organized and safely routed. Our vertical cable managers are compatible with all standard 19-inch racks and offer features such as finger duct panels, brush strips, and tool-less mounting for fast installation.
One of the primary benefits of vertical cable management is improved airflow. When cables are neatly routed and secured vertically, they no longer obstruct fans or vents, allowing your cooling systems to operate more effectively. This not only protects sensitive equipment from overheating but also contributes to energy savings and extended hardware lifespan.
RitchField Network Solutions also understands the importance of scalability. As your network grows, so do your cable management needs. Our vertical cable managers are designed with flexibility in mind, making it easy to add or reconfigure cabling without disrupting your current setup.
In summary, vertical cable management from RitchField Network Solutions helps maintain the integrity, efficiency, and aesthetics of your IT infrastructure. Investing in quality cable management today leads to fewer outages, faster service times, and a more professional environment tomorrow.
Explore our full range of cable management solutions and speak with our experts to find the right fit for your organization. RitchField Network Solutions—where network performance meets precision.
0 notes
Text
Seamless Intelligence in Your Palm: The Future of IoT Control

The next evolution in IoT app development, where AI integration, Bluetooth mesh networking, and edge computing combine to enable seamless control of smart systems. From real-time data to over-the-air updates, the mobile interface brings intelligent automation to your fingertips — built for scale, security, and sustainability.
#IoT App Development#Bluetooth Mesh Networking#Edge Computing#AI-Driven Automation#Smart City Solutions#IoT Mobile Control#Real-Time IoT Monitoring#Secure IoT Communication#OTA Firmware Updates#Low Power IoT Devices#Scalable IoT Platforms#Intelligent Device Management#IoT
0 notes
Text

Power your infrastructure with Microsoft Windows Server 2022 Standard – built for performance, scalability, and top-tier security.
Whether you're managing virtual machines, handling network roles, or running enterprise-level applications, Windows Server 2022 is your reliable solution.
✅ Genuine Microsoft License ✅ Instant Digital Delivery ✅ Lifetime Activation ✅ Enterprise-Grade Security ✅ Best Price Online
👉 Get it now from TechLicence – your trusted Microsoft partner: www.techlicence.com
#Power your infrastructure with Microsoft Windows Server 2022 Standard – built for performance#scalability#and top-tier security.#Whether you're managing virtual machines#handling network roles#or running enterprise-level applications#Windows Server 2022 is your reliable solution.#✅ Genuine Microsoft License#✅ Instant Digital Delivery#✅ Lifetime Activation#✅ Enterprise-Grade Security#✅ Best Price Online#👉 Get it now from TechLicence – your trusted Microsoft partner: www.techlicence.com#windowssoftware#PCUpgrade#Microsoft#DigitalLicense#productkey#windowsserver2022#windowsserverstandard#standard2022#serverstandard2022#microsoftwindowsserver#serversolutions#security#serverkey
0 notes
Text
FTTX and FTTH – Understanding the fundamentals in Telecommunication
The telecommunications industry has evolved swiftly over the past few decades. From dial-up connections to fiber optic technology, the transformation has been nothing short of remarkable. Two key terms that frequently come up in this context are FTTH (Fiber to the Home) and FTTX (Fiber to the X), with X being a variable. This article will shed light on these two concepts, their operational mechanism, practical use cases in varied geographic locations, and the leading players in the FTTH and FTTX network planning and design.
0 notes
Text
Click Techs Leading the Way in IT Consulting Services for Businesses
Click Techs offers expert IT Consulting Services tailored to your business needs. From strategic planning to infrastructure optimization, our team ensures your technology aligns with your goals
#IT Consulting Services#Managed IT Services#network infrastructure#technology solutions#security & compliance
0 notes
Text
Bots Now Dominate the Web: Why This Growing Problem Demands Urgent Action

The digital world, once a bustling marketplace of human interaction, has undergone a silent, pervasive transformation. Data from 2024 and early 2025 reveals a startling reality: bots now dominate web traffic, accounting for over 50% of all internet activity. While some of these automated programs are "good" – diligently indexing content for search engines or enabling helpful chatbots – a significant and escalating proportion are "bad bots," mimicking human behavior for malicious purposes. This widespread bot dominance web traffic presents a serious and ever-growing problem for businesses, cybersecurity, and the overall integrity of the web. The sheer volume and sophistication of these malicious bots internet traffic are redefining the landscape of online security.
The rise of bot traffic on the internet is significantly fueled by rapid advancements in Artificial Intelligence (AI) and Large Language Models (LLMs). These technologies simplify the creation and scaling of sophisticated, evasive bots, allowing even less skilled malicious actors to launch high-volume attacks. As of early 2025, malicious bots account for a staggering 37% of all internet traffic, a substantial increase from previous years, signaling a deepening bot problem online.
The Unseen Majority: How Bots Came to Dominate the Web
For the first time in a decade, automated traffic has surpassed human activity. This shift is primarily attributed to the proliferation of AI and LLMs, which have democratized bot development, making it more accessible to a wider range of actors. These advancements enable bots to mimic human interaction with startling accuracy, often bypassing traditional security measures.
The sophistication of these bad bots internet traffic is constantly evolving. They employ techniques like IP rotation, mimicking legitimate browser fingerprints, and distributing attacks across vast networks of compromised devices (botnets). The goal is simple: evade detection by blending in with legitimate web traffic automation. This makes it increasingly difficult for organizations to differentiate between genuine human users and malicious automated scripts, amplifying the bot problem online.
The Multifaceted Problem: Impacts of Bot Dominance

The pervasive presence of malicious bots internet traffic creates a myriad of complex and costly issues across various aspects of the digital economy. Understanding the full scope of the impact of bots on business is crucial for developing effective defense strategies.
Financial Drain & Fraud
The direct financial implications of bot fraud are staggering. Malicious bots are instrumental in various fraudulent activities that directly hit a business's bottom line:
Credential Stuffing and Account Takeovers (ATOs): Bots automate login attempts using stolen username/password combinations from data breaches. Successful ATOs lead to financial theft, misuse of loyalty points, and damage to customer trust.
Carding and Gift Card Fraud: Bots test stolen credit card numbers against e-commerce sites or attempt to drain balances from stolen digital gift cards, leading to chargebacks and direct financial losses.
Ad Fraud and Click Fraud: Bots simulate clicks and impressions on online advertisements, depleting advertisers' budgets without generating genuine leads or conversions. This distorts analytics and wastes significant marketing spend.
Scalping and Inventory Hoarding: In industries with high-demand, limited-stock items (like concert tickets, sneakers, or popular gaming consoles), bots rapidly purchase inventory, only for it to be resold at inflated prices on secondary markets. This infuriates legitimate customers and damages brand reputation.
Cybersecurity Risks & Data Integrity
Cybersecurity bot attacks represent a fundamental threat to an organization's digital infrastructure and sensitive data. Bots are often the first line of attack in broader cyber campaigns:
Vulnerability Scanning and Exploitation: Bots automatically scan websites and APIs for known vulnerabilities (e.g., SQL injection, cross-site scripting), identifying weak points that can then be exploited for unauthorized access or data exfiltration.
Distributed Denial-of-Service (DDoS) Attacks: Botnets, vast networks of compromised devices controlled by attackers, flood target websites, servers, or networks with overwhelming volumes of traffic, rendering them inaccessible to legitimate users.
API Abuse: With the rise of API-driven applications, bots increasingly target APIs to scrape data, create fake accounts, exploit business logic, or launch sophisticated fraud schemes that bypass traditional web application firewalls.
Data Scraping: Competitors or malicious actors use bots to steal valuable data, including pricing information, product catalogs, customer reviews, and proprietary content, leading to competitive disadvantage and intellectual property theft.
Operational & Performance Disruptions
The sheer volume of web traffic automation from bots places immense strain on IT infrastructure:
Server Strain and Increased Costs: High bot traffic consumes valuable server resources, bandwidth, and computing power, leading to increased hosting expenses and the need for costly infrastructure upgrades.
Degraded Website Performance: Overwhelmed servers result in slower loading times, timeouts, and poor responsiveness for legitimate users, severely impacting user experience and conversion rates.
Skewed Analytics: Bot traffic contaminates website and application analytics, inflating metrics like page views, unique visitors, and clicks while distorting bounce rates and conversion rates. This leads to flawed business decisions based on inaccurate data.
Brand Reputation & Trust
Beyond the technical and financial impacts, bot dominance web traffic erodes trust and damages brand reputation:
Spam and Misinformation: Spam bots flood comment sections, forums, and social media platforms with unsolicited advertising, malicious links, or propaganda, harming a website's credibility and user experience.
Customer Frustration: When legitimate customers are unable to access services due to DDoS attacks, or when they can't purchase items due to bot-driven scalping, their frustration can quickly turn into negative reviews and a damaged brand image.
SEO Penalties: Google and other search engines penalize websites with low-quality or duplicate content, which can result from content scraping by bots, negatively impacting search engine rankings and organic traffic.
Industries Under Siege: Where Bot Threats are Most Acute

While the bot problem online affects nearly every sector, certain industries consistently face a higher proportion and more sophisticated online bot threats:
Financial Services: A primary target due to the sensitive nature of data and high-value transactions. They face relentless account takeover bots, credential stuffing, and fraud attempts.
Retail: Highly susceptible to bot fraud related to inventory scalping, gift card fraud, price scraping, and loyalty program abuse.
Travel: Experiences a significant percentage of bad bots internet traffic, used for competitive price scraping, account takeovers, and fraudulent bookings.
Gaming: Often sees the highest proportion of sophisticated bot traffic, including bots used for cheating, account compromise, and inventory manipulation within in-game economies.
Media and Entertainment: Targeted for content scraping, ad fraud, and credential stuffing on streaming platforms.
Fighting Back: Strategies for Bot Management and Mitigation

Combating bot dominance requires a proactive, multi-layered, and continuously evolving defense strategy. Relying on outdated methods is no longer sufficient against today's sophisticated malicious bots internet attacks.
Advanced Bot Management Solutions: The cornerstone of modern bot defense. These specialized platforms utilize a combination of behavioral analysis (distinguishing human-like patterns from automated ones), machine learning (adapting to new bot tactics), device fingerprinting, and real-time threat intelligence. They go beyond simple IP blocking or CAPTCHAs to detect and mitigate even the most evasive bots.
Robust API Security: Given that 44% of advanced bot traffic targeted APIs in 2024, securing these digital gateways is paramount. Implementing strong authentication mechanisms (like OAuth, API keys), strict access controls, and rate limiting on API endpoints can significantly reduce the attack surface for API security bots. Regular API penetration testing is also crucial.
Multi-Factor Authentication (MFA): Implementing MFA adds a critical layer of security beyond just passwords. Even if bots manage to acquire stolen credentials through credential stuffing, MFA can prevent unauthorized access by requiring a second verification step (e.g., a code from a mobile app), drastically reducing account takeover bots success rates.
Continuous Monitoring and Analytics: Businesses must actively monitor their web traffic automation for unusual patterns. This includes spikes in requests from a single IP, abnormally high failed login attempts, unusual user-agent strings, or suspicious conversion rates. Real-time dashboards and automated alerts are essential for early detection of online bot threats.
Regular Security Audits and Patching: Proactive vulnerability management is key. Regularly auditing web applications, APIs, and underlying infrastructure for security flaws, and promptly patching identified vulnerabilities, closes potential entry points for bots.
User-Agent and Proxy Analysis: Many simpler bots still rely on outdated browser user-agent strings or operate through known dubious proxy services. Implementing rules to block traffic from such indicators can filter out a significant portion of commodity bot attacks. Detecting traffic from residential proxies, which more advanced bots now use, requires more sophisticated analysis.
Rate Limiting and Throttling: While not a complete solution, judiciously applying rate limits on specific endpoints (e.g., login pages, search functions, API calls) can prevent brute-force attacks and resource exhaustion caused by excessive bot requests.
Conclusion: Securing the Human-Centric Web
The landscape of the internet has fundamentally shifted. Bots now dominate the web, and this poses a significant, evolving bot problem online for businesses, their customers, and the integrity of digital interactions. From sophisticated bot fraud schemes to debilitating cybersecurity bot attacks, the impact is wide-ranging and costly.
Ignoring this reality is no longer an option. As AI continues to empower bots to become even more evasive and intelligent, businesses must embrace comprehensive and adaptive bot management solutions. Investing in robust API security, implementing strong authentication, and continuously monitoring for unusual patterns are not merely best practices; they are essential for survival in the current digital climate.
The future of the web depends on our ability to effectively differentiate between humans and machines, safeguarding digital assets and ensuring a secure, reliable, and authentic online experience for everyone. By adopting proactive strategies, organizations can protect their revenue, reputation, and customer trust from the pervasive and growing threat of malicious web traffic automation. The time for urgent action is now.
#Cyber Security Services Company | Data Security Solutions#Top-rated Cyber Security Services Company Offering Advanced Protection#Threat Detection#Risk Assessment#Data Security Solutions For Businesses Worldwide.#Cybersecurity services company#Data security solutions#Managed cybersecurity services#Enterprise cyber protection#Data breach prevention services#Cyber threat protection#IT security solutions provider#Endpoint security services#Network security services#Cybersecurity consulting company
0 notes
Text
Metabolomics Bioinformatician
Job title: Metabolomics Bioinformatician Company: Syngenta Job description: Syngenta scientists. Supporting data generation when required. Networking within Syngenta and the external bioinformatics… chemistry on data processing requirements. processing of metabolomics data using specialist software (vendor or open source… Expected salary: Location: Bracknell, Berkshire Job date: Tue, 01 Jul 2025…
#Automotive#Bioinformatics Specialist#cloud-native#CRM#Crypto#CTO#deep-learning#DevOps#Ecommerce#edtech#erp#ethical AI#game-dev#HPC#Java#mlops#mobile-development#Networking#NFT#project-management#Python#qa-testing#quantum computing#remote-jobs#Salesforce#solutions-architecture#technical-writing#telecoms#ux-design
1 note
·
View note
Text
How to Choose the Right Endpoint Protection Platform for Your Business
The global Endpoint Protection Platforms (EPP) market is poised for significant expansion in the coming years, fueled by the relentless surge in cyber threats and the transformation of work environments. As organizations continue to adopt flexible work models, particularly remote and hybrid setups, securing endpoint devices—laptops, desktops, mobile devices, and servers—has become a top priority…
#AI in Cybersecurity#antivirus software#business#Business Intelligence#cybersecurity#cybersecurity threats#data protection#endpoint management#endpoint protection#Endpoint Protection Platforms#Endpoint Security#EPP#integrated security#IT security solutions#machine learning in cybersecurity#Malware Protection#mobile endpoint security#Network Security#Security#Threat Detection
0 notes
Text

Finally got to the part of MMBN5 I got stuck on as a kid! I'm cracking this accursed letter this time!
Update: That was super easy and I'm not sure how I got stuck on it as a kid.
Update 2: ... I'm stuck. Again.
Update 3:

the fucking WINDOW IN LAN'S HOUSE!?!?!?!?!?? WHY. WHY. WHY. WHY. WHY. WHY. WHY WOULD YOU PUT A DOG HOUSE IN THE FRONT YARD AND THEN NOT HAVE ANYTHING INTERACTABLE BEHIND THE HOUSE BECAUSE YOU HAVE TO GO TO THE FUCKING WINDOW THAT'S INSIDE THE HOUSE TO SEE SOMETHING OUTSIDE THE HOUSE!?!?!?!?!?
#original#megaman battle network#solved it#i remember what i THOUGHT it said as a kid very clearly: “go back to ACDC”#but that's. not even close. i have no idea how i managed to get it so wrong#i remember getting my parents to help#it wasn't hard to figure out that each black square corresponded to a character in the message#but idk i guess it was really hard to figure out which characters they corresponded to#this time it was easy because i had a monospace font to just type them side by side#but i guess it was a lot harder trying to do it with pen and paper#and i think i remember trying to rearrange the letters into something else#because the letters i got were nonsense#okay the letters for “go back to” are in fact in the real solution. and so are the letters “acd”#which. means i got close? but how did i mess it up if i got so many of the correct letters?#must've been missing some crucial letters in the first paragraph#ANYWAY! for the sake of my poor childhood self! i solve this TODAY!#update: i have failed to solve it#i went to the place it told me to go! kinda! what the fuck does “out back” mean! it's out front!#and now i'm here and i've interacted with all 2 things here and i have no idea what to do#i don't want to look this up. i want to solve this. but god DAMN THIS IS FRUSTRATING!!!!!#IT SAYS “DOGHOUSE OUTBACK”! WHAT ELSE COULD THAT POSSIBLY MEAN!?!#update: god fucking damn it
1 note
·
View note
Text
Sigzen Technologies's Shield: Safeguarding Your Systems Through Advanced Server Patching
Sigzen Technologies’s Shield represents a paradigm shift in the landscape of cybersecurity defenses. Its multifaceted approach encompasses not just basic patching but a holistic, proactive strategy to fortify systems against evolving threats. This section aims to delve deeper into the core innovations that set Sigzen Technologies’s Shield apart in the domain of advanced server patching. Enhanced…
View On WordPress
#Advanced Server Patching#Data Security#Information Security#IT Infrastructure#IT Management#IT Security#Network Protection#Patch Management#Server Management#Server Security#Technology Solutions#Vulnerability Patching
2 notes
·
View notes
Text
High‑Speed and Secure Access Network Solutions – Esconet Technologies
Esconet Technologies offers comprehensive Access Network solutions tailored for enterprise environments. Their network infrastructure suite features high-speed copper and optical fiber connectivity (1 Gbps–100 Gbps), a multilayered design following core/distribution/access best practices, IPv6 readiness, Wi‑Fi 6/6E wireless, cloud-managed systems, advanced security (firewalls, IPS, VPNs), and deployable satellite broadband for remote locations. Partnered with top OEMs (Cisco, Arista, Juniper, Dell, HPE), Esconet ensures scalable, secure, future-ready digital transformation networks. For more details, Visit: Esconet's Access Network solution Page .
#access network solutions#enterprise networking#fiber optic connectivity#high-speed internet infrastructure#Wi-Fi 6 deployment#Wi-Fi 6E network#IPv6 network architecture#cloud-managed networking#enterprise wireless solutions#secure network infrastructure#network security solutions#VPN and firewall services#satellite broadband connectivity#digital transformation infrastructure#Esconet Technologies#copper and fiber network design#scalable network solutions#IT infrastructure services#enterprise IT solutions#smart campus networking
0 notes
Text
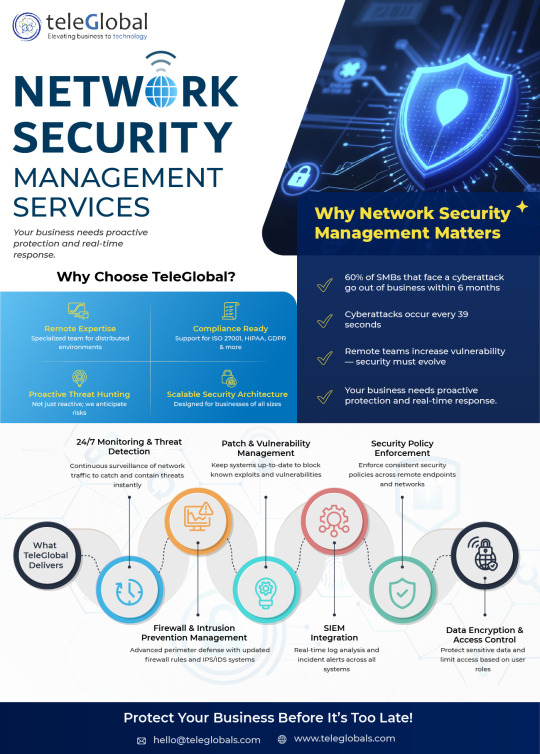
Network Management Services in Pune | Teleglobal
Empower Your Network for Efficient Performance From network setup and monitoring to firewalls and load balancer setup, we offer a secure, optimized, and high-performing network infrastructure. Our Network Management Services provides end-to-end solutions that boost network security, performance, and reliability, ensuring nothing interrupts connectivity of your business.
Optimize Your Network Today https://teleglobals.com/contact-us
#Network Management Services#Network Management#IT Infrastructure#Remote Monitoring#IT Support#Managed Services#Tech solutions#Digital Transformation#Cloud Computing#Cyber Security#Business Continuity
0 notes