#common wireless network
Explore tagged Tumblr posts
Text

Metro_Wireless_Node.jpg
#wikimedia commons#2000s#2009#Outdoor Wi-Fi antennas of access points#Municipal wireless networks#Dipole antennas#Mesh network#Utility poles in Minnesota#Files with coordinates missing SDC location of creation#CC-BY-SA-3.0#License migration redundant#GFDL#Self-published work#Taken with Polaroid i1035
2 notes
·
View notes
Text
Here’s how to share sensitive leaks with the press
Published Oct. 16, 2019 Updated Jan. 31, 2025 / Freedom of the Press Foundation

[please take a moment to click the links at the bottom to give this website traffic if you can. the only reason I am copy pasting it here is for those who can access tumblr but not necessarily that site.]
~~~
Over the years, we have witnessed abuse and mismanagement in the government and private sector — sometimes bad and sometimes worse — that need to be brought to public attention. For those who would leak information about such misdeeds to the press, giving tips to journalists can be risky and may violate previous legal agreements with the leaker’s organization, such as a nondisclosure agreement or contract. But sometimes, it can also be an effective and courageous way to call attention to misconduct.
This guide describes basic steps for minimizing potential risk when sharing sensitive information with a news organization. We want to be clear that no piece of software, nor security recommendation, will be 100% effective, and the decision to blow the whistle may invite scrutiny or retaliation. At the same time, it may be a choice that drives necessary institutional change. Before reaching out to the press, think carefully about what you can do to minimize that risk and stay as safe as possible.
Before moving ahead, do you have a strong tip?
A good tip requires clear evidence and should be the basis for a story that the broader public needs to know about.
So, for instance, whether or not you have evidence, the broader public might not need to know that a neighbor refuses to pick up after her dog on the morning walk. On the other hand, allegations of corruption or illegality among public officials are certainly newsworthy, but those claims will not make it into a published story without verifiable evidence.
Who are you leaking about and how might they respond?
Think about the sensitivity of the information you’re sharing, and who might be willing to investigate the source of the leak. What are the organization’s capabilities? What resources (e.g., attention and legal, financial, or technical) can it invest in discovering the source? And how likely do you think it is that it will actually investigate?
If you share information about a large, well-resourced organization that requires discretion from employees, such as a government agency, it may have enormous legal, financial, and technical resources available for investigating a leak. If you’re sharing information about a small organization, such as a local restaurant that muzzles workers, its resources are much more constrained, and it may not have the capacity or willingness to investigate. Act accordingly.
Proceed with caution
Be cautious about behaviors that could make you readily identifiable as a source.
Keep all of your leaking activities outside the view of your organization. That means no calling from work, no emailing from a work email address, and staying off work devices or wireless networks.
It's common for well-resourced organizations to keep logs of activities on employees’ workplace devices and online activities. Likewise, sometimes workplaces have “BYOD” (bring your own device) technologies that could allow them to log your activity on your personal device. So if you work at a large organization and you're reading this article on a workplace device or Wi-Fi network, chances are your workplace already has a log that you've accessed this page. Similarly, a visit to a news organization's tip page (like https://www.nytimes.com/tips) may be logged by your workplace. This is why it's so important to limit your leaking activities to devices and networks that your workplace doesn't control.
Has your workplace ever required you to install monitoring software (or software of any kind) on your work or personal device? If so, you probably don't want to use those devices for any whistleblowing activities.
Be cautious about giving tips on anything that only you could know or materials that only you could access. And consider whether the increased risk of being caught sharing these kinds of materials is worthwhile, or if you feel you have a strong moral obligation to do so.
If you are the only one at your organization surfacing a specific grievance, and information about that grievance is later reported by the press, it may give your organization a strong hint about who shared the information.
Don’t tell anyone about your leaking activities (even perhaps the journalist or news organization you’re leaking to), except where absolutely necessary and in cases where you may want legal advice from a practicing lawyer.
Reporters generally take their commitment to protecting your identity very seriously and will do everything in their power to fight potential legal requests for identifying information about you. But often, it’s safer not to give your identity if you don’t have to. Keep in mind that journalists prefer to have proof of your claims and information to demonstrate your identity is a part of that.
Tactics for minimizing risk
There are a lot of ways to minimize the risk of a tip being tied to you, like potentially through your continued communications with reporters.
Send your materials through physical mail. You can mail electronic documents (e.g., on an SD card) or physical documents through ordinary mail. Be warned: The U.S. postal service takes pictures of the exterior of physical mail. So don’t use a return address that is associated with you and instead mail it in from a sidewalk mailbox in a location you don’t usually frequent. If you have a particular reporter you want to look into your story, copy them on the envelope.
Call from a phone number unconnected to you. For example, go to a business you don’t usually go to and ask to use their phone. You can also buy a cheap cell phone and a prepaid phone card that cannot be traced back to you. But know this involves several careful steps: You must pay with cash, and if your organization can have access to phone location records, it’s best to only turn on the phone in locations unassociated with you. That also means using the phone in locations separate from your permanent phone. If you can, remove the battery when it’s not in use.
Use Signal for private messaging. Signal is a secure, free, and open source messaging app for iPhones and Android devices. Signal gives you end-to-end encrypted messages and phone calls, and only retains your phone number, your signup date, and when you were last active. In Signal, you can also make messages automatically self-destruct for everyone in the conversation after a set amount of time. This makes it significantly harder (but not impossible) to eavesdrop on your conversations. If you want help getting started, read this beginner-friendly guide on using Signal. Note that Signal allows usernames, so you do not need to give your name or phone number to media organizations unless you choose to. Make sure your username is enabled and understand that Signal is not designed for complete anonymity.
Before looking into news organizations, consider using the Tor Browser for greater privacy. Tor Browser is a modified version of Firefox. Tor encrypts and tunnels your web traffic within a global network of computers before connecting you to your final destination. When you access a website through Tor (for example, Amazon.com), you will appear to connect from a remote location — likely another country. Again, don't use a work device or network for this kind of research.
Use a whistleblower submission system. Tools such as SecureDrop can provide protection by allowing you to share documents and communications through an anonymous and encrypted drop box.
More technical, but more secure: SecureDrop
With SecureDrop, which is maintained by Freedom of the Press Foundation, not even the news organization knows who you are unless you choose to tell them.
A growing number of news organizations (e.g., The New York Times, The Washington Post, The Intercept, The Guardian) are using SecureDrop to allow sources to reach out and share files or communications anonymously. With SecureDrop, not even the news organization knows who you are unless you choose to tell them.
You can access a news organization’s SecureDrop page through Tor Browser.
People on your network can’t see what you’re doing on Tor, but it’s still possible to tell that you’re using Tor. With that in mind, do not use it at work. For greater security, consider using Tor Browser only over a Wi-Fi network in a location that is not tied to you (perhaps a coffee shop you don’t normally visit) and pay with cash.
As opposed to a “.com” web address, you get to SecureDrop through a unique .onion web address, which can only be accessed through Tor.
Using SecureDrop is fairly easy
Follow the directions to download the Tor Browser at torproject.org and install it.
Launch the Tor Browser application and click "Connect" to log into the network.
Click the shield icon in the top corner > Advanced Security Settings… > Safest
Within Tor Browser, navigate to the SecureDrop directory and search for your preferred news organization: securedrop.org/directory
Find the .onion URL for your preferred publication (e.g., The New York Times: securedrop.org/directory/new-york-times), then copy and paste it into the address bar in Tor Browser.
From here, you can leave messages and files that the news organization will check from time to time.
You will be given a random “codename” for continued conversation with the news org. Keep this information safe, and don’t share it with anyone. If you lose your codename, they can’t reach you anymore.
(For more technically adept users, consider accessing SecureDrop through an operating system designed for privacy and anonymity, such as Tails.)
Dealing with file metadata
Sharing information may be less risky than sharing documents because they can be embedded with information about the file, which we call metadata. For example, if you create a .docx file, it may have identifying information about you embedded in the file. Consider carefully whether you really need to share files or just the information.
To deal with hidden metadata, rather than sending the file itself, consider taking a picture of a document with an old-fashioned camera (not a smartphone), or taking a screenshot of the document. On most operating systems, screenshots come with little useful metadata. For more technical users, you can find metadata removal tools here.
Where do you find a news organization's contact details?
First, be careful where you reach out.
Freedom of the Press Foundation maintains a list of organizations that support the secure communications practices outlined above, and how you can contact them. Such practices are becoming standard, and we hope other news organizations looking for great tips will follow suit.
Freedom of the Press Foundation hosts a directory of SecureDrop and secure tip pages for dozens of news organizations around the world. Whether you want to reach out to The New York Times, The Washington Post, The Guardian, The Intercept, or others, you can find their information here: https://securedrop.org/directory. (We would not recommend investigating this at work.)
If not you, then who?
Sharing information with the press is not always an easy decision, but your information can help to hold powerful people and institutions accountable. Just be sure to move ahead with a strong understanding of your organization’s capabilities and how to share tips safely.
https://freedom.press/digisec/blog/sharing-sensitive-leaks-press/
https://bsky.app/profile/freedom.press/post/3lh2rgopf5225
127 notes
·
View notes
Text
it's actually a common misunderstanding that miku is "hiding in your wifi". wifi is a family of wireless network protocols, what miku is hiding in is the radio waves that make up that wireless network.
22 notes
·
View notes
Text

"Wi-Fi" apparently is NOT short for "wireless fidelity"
"Wi-Fi is a wireless networking technology that uses radio waves to provide wireless high-speed Internet access. A common misconception is that the term Wi-Fi is short for "wireless fidelity," however Wi-Fi is a trademarked phrase that refers to IEEE 802.11x standards." WiFi definition and meaning | WaTech
Looking around, it seems be named that so that it rhymes with "high fi(delity)" o_0
7 notes
·
View notes
Text
5 Ways to Improve Your Network Security
In today’s digital age, network security is more critical than ever. With cyberattacks becoming more sophisticated and frequent, businesses and individuals alike must take proactive steps to protect their networks. Whether you’re a small business owner or a tech-savvy professional, improving your network security can help safeguard sensitive data, prevent downtime, and maintain trust. Here are five actionable tips to enhance your network’s defenses.
1. Use Strong, Unique Passwords
Weak or reused passwords are among the most common vulnerabilities in network security. To protect your network:
Create strong passwords that include a mix of uppercase and lowercase letters, numbers, and special characters.
Avoid using easily guessed information, such as birthdays or common words like "password123."
Use a password manager to generate and securely store complex passwords for all your accounts.
Implement multi-factor authentication (MFA) for an extra layer of security. MFA requires users to verify their identity through a second method, such as a text message code or biometric scan.
2. Keep Your Software Up-to-Date
Outdated software is a goldmine for hackers who exploit known vulnerabilities. Regular updates ensure you’re protected with the latest security patches.
Update your operating system, applications, and firmware regularly.
Enable automatic updates to ensure critical patches are installed promptly.
Replace unsupported or obsolete hardware and software with newer, more secure alternatives.
3. Secure Your Wi-Fi Network
Your Wi-Fi network is a primary gateway for potential attacks. Securing it is essential:
Change the default administrator username and password for your router.
Use WPA3 encryption (or at least WPA2) to secure your wireless connection.
Hide your network's SSID (Service Set Identifier) so it’s not visible to unauthorized users.
Set up a guest network for visitors, keeping them isolated from your primary network.
4. Install and Update Security Software
Comprehensive security software is your first line of defense against malicious activity.
Use antivirus and anti-malware programs to detect and remove threats.
Install a firewall to monitor and block unauthorized access to your network.
Invest in a Unified Threat Management (UTM) system, which combines multiple security features like intrusion detection, content filtering, and VPN support.
Keep all security software updated to stay protected from the latest threats.
5. Educate and Train Users
Even the most robust security measures can fail if users are unaware of best practices.
Train your team to recognize phishing emails, suspicious links, and social engineering tactics.
Encourage employees to report unusual activity immediately.
Establish a network security policy that outlines acceptable use, password protocols, and steps for reporting incidents.
Conduct regular cybersecurity awareness sessions to keep users informed about emerging threats.
Bonus Tip: Monitor Your Network Activity
Proactively monitoring your network can help you detect potential issues before they become critical. Use tools to track unusual traffic, failed login attempts, and other red flags.
Conclusion
Improving your network security doesn’t have to be overwhelming. By implementing these five steps, you can significantly reduce your risk of cyberattacks and create a safer environment for your business or personal network. Remember, cybersecurity is an ongoing process—stay vigilant, keep learning, and adapt to new threats as they arise.
Have questions or need help securing your network? Contact us today for expert IT solutions tailored to your needs!
4 notes
·
View notes
Text
Of all the titles I have been given, man is among the worst
I was born weak. Pathetically so. I was made to wear glasses so I could see normally by the second grade. I could not run or my legs would be overtaken with pain akin to cracking my bones in two. I could not act too harshly or my breathe would fall short and I may stop breathing altogether.
By the time that I escaped school, I began to study Bio-Anthropology. I studied what made us tick. Now that is normal information, known by all as common knowledge taught in schools. But it should be known that I was the one who understood it best. Who was the first to find what made the human heart beat, what made the human lung breathe, what made the human mind think.
With every study, I learned more and more of our kind. Our strengths and our weaknesses. It infuriated me how we were constructed. Surely this was not the product of our immutable gods. I grew more and more angry with each coming day, their false ideals. Their words that we were "The greatest of species." Their glowing gaze that cast shadows upon all they witnessed. So I sought to do the greatest sin against any god.
I surpassed them.
I began first with others. The flesh was weak, so the brass and steel became a very stable replacement. The limbs were easy to replace and great beginner practice, but soon there were worse ailments that I needed to fix. The spine was a difficulty that took me a great amount of time to replace properly and sufficiently. Many had lost something in my attempts to replace a single part of their bodies but after 12 years. I had finally gotten it. A spine that was faster, stronger, and more efficient than the original body's... Sometimes too efficient, it bent more than the skin it was implanted in, but that was a small error I fixed in less than a month's worth of time.
Soon after, there was the next issue. The head. I started small, replacing components of it, the eyes, the tongue, the jaw. Things which were not too difficult to replace with simplistic changes. My eyes were stronger, could see farther, and more colors than any other human's eyes could. My tongues could taste with much greater complexity than any others. My Jaw could crush the very teeth inside of them, so I had to both limit the jaw's force and replace all of their teeth as a safety mechanism. It became somewhat of aa trend as I did so.
Finally I came upon the issue of the brain. I can't replace it. I can't change it in any way or I would lose the host. Or so the god's wanted us to believe. I spent decades on figuring out the brain, the mind, the very center of what human is. Brain after brain, they all were failed experiments. I soon felt as if it were impossible. But no. Nothing is impossible for me. I would overcome it. If not in my body, than in another.
I began to experiment by placing a host in a replicant body, sending the signals to the original body through wires as a form of replacement. The first few were fails but then there were sparks of success. Several hosts survived for minutes. Then hours. Then days. With each iteration, they experienced less and less side effects, until they barely even noticed what had happened. When the final several subjects did not know they were without their own brain until they were unplugged and fell dead, I knew it was time for the next step.
I switched minds. The process was simple, the wires were all the same. It was just the process of keeping them alive long enough for the process. The tests lasted only a few weeks. I grew confident, and created a trusted automaton to conduct the procedure upon myself.
Success. I became separate to my body, and was able to control more than one body at a time by simply adding more bodies to the wire network. Though soon wireless forms of control were invented and rather surprisingly effective at creating the same effect.
And so the first iterations of Michael were born. Not myself, but more myself than my original form ever was. With these bodies, I was able to easily replicate myself and go out in search for more answers. I soon learned my limits, I can hardly control more than 2 bodies at once, hell it was hard to control more than one. That did not stop me though, I continued to grow my arsenal of bodies, each one had a greater purpose than the last.
I buried my original form, encasing them in a coffin of brass and steel. The emblem on it read as such: "Aeternitas Est Me". The form aged and rotted too quickly, there was more work to be done. My knowledge only grew, leading me to replace that part of my brain with a powerful machine that I could replicate and add onto infinitely. My processing power slowed down, that was next to be replaced.
Those that new me, mainly elves, said I had changed. I had. More than they would ever know. I became the embodiment of power and structure. I was system. I was order. I was knowledge. I am Michael, the eternal scientist. I am towards perfection. Progress is eternal. I am progress. Those who believe not are obstacles. Obstacles can be erased.
I am no man. I am no machine. I am Michael.
I am eternal
4 notes
·
View notes
Text
Deep Dive into Wi-Fi Hacking: How Ethical Hackers Secure Your Wireless Networks

With our hyper-connected world, Wi-Fi is the unseen lifeline keeping us online today. From streaming your favorite shows to managing your smart home devices, Wi-Fi is everywhere. But have you ever stopped to think about just how secure your wireless network really is? What if someone could sneak into your network, steal your data, or even hijack your devices? Scary, right? That’s where ethical hackers come in—the unsung heroes of the digital age who use their skills to protect, not exploit. If you’ve ever been curious about how they do it, or if you’re considering a cybersecurity and ethical hacking course, this blog is for you.
The Dark Side of Wi-Fi: Why It’s a Hacker’s Playground
Well, face it: Wi-Fi networks are a goldmine for cybercriminals. Why? Because they are usually the easiest weakness in our digital defense. It has weak passwords, outdated encryption, and misconfigured routers. That's not to mention stealing your Netflix login. Hackers can use it as an open gateway to access more of your digital life.
Here's your scenario: You're having your favorite coffee at a quaint little café while making use of their free Wi-Fi. Well, a hacker within some tables from you is running Aircrack-ng or Wireshark for quite a bit on your data that's going by. Before you realize it, they have gotten your login credentials, credit card information, or even obtained access to your corporate emails. How scary does that sound?
Enter Ethical Hackers: The Good Guys of Wi-Fi Security
That is when the ethical hackers come in. Cybersecurity professionals use the same hacking tools and techniques as evil hackers, with one difference though: they work for you. Their job is to find a hole before a hacker does so that they may fix it before hackers can gain entry into your network.
How do they go about it? Let's dissect this:
Reconnaissance: Ethical hackers first gather information about the target network. They use tools such as Kismet or NetStumbler to identify the network's SSID, encryption type, and connected devices.
Exploitation: Once they have identified potential weaknesses, they try to exploit them. For example, if the network uses outdated WEP encryption (which is notoriously weak), they might use tools like Aircrack-ng to crack the password.
Post-Exploitation: Having obtained access, the ethical hacker calculates the potential damage that can be done. Could they have accessed sensitive files? Could they have launched a man-in-the-middle attack? This step will give them a sense of real-world impact from the vulnerability.
Reporting and Patching: They finally document their findings and collaborate with the owner of the network to fix the issues. It may involve updating firmware, changing passwords, or enabling stronger encryption like WPA3.
Why You Should Care About Wi-Fi Security
You may be thinking: "I am an average user, so why would somebody even bother with me?" The thing is, hackers don't discriminate. Whether you are just an individual, a small business owner, or part of a large corporation, your Wi-Fi network is a potential target. And with the emergence of IoT devices, such as smart thermostats, security cameras, and voice assistants, the risk is much bigger than ever.
Here's the good news: You don't need to be a tech genius to protect yourself. By learning the basics of Wi-Fi security or even enrolling in a cybersecurity and ethical hacking course, you can take control of your digital safety.
How to Secure Your Wi-Fi Network: Tips from the Pros
Want to make your Wi-Fi network hacker-proof? Here are some practical tips inspired by ethical hackers:
Use Strong Passwords: Avoid using common passwords, such as "admin" or "password123." Instead, use long complex phrase with letters, numbers, and symbols.
Enable WPA3 Encryption: The latest Wi-Fi encryption protocol is WPA3; if your router supports it, switch to WPA3.
Update Your Router's Firmware: Manufacturers in their official websites may have coming updates that address security vulnerabilities. Check and update the firmware on your router to a newer edition.
WPS: Wi-Fi Protected Setup is convenient but highly insecure. Just turn it off to minimize brute-force attacks.
Check Connected Devices: You would be surprised to know which device is connected to your network if you don't check it periodically. If something looks suspicious, investigate immediately.
Ready to Be a Wi-Fi Warrior?
If this deep dive into Wi-Fi hacking has piqued your interest, why not take it further? A cybersecurity and ethical hacking course can teach you the skills you need to protect yourself—and maybe even turn your passion for tech into a rewarding career. Imagine being the person who uncovers vulnerabilities, thwarts cyberattacks, and keeps the digital world safe. Sounds exciting, doesn't it?
Ethical hacking is not the art of hacking into systems, but understanding how they work so that such knowledge can be applied to strengthen their defenses. In a world that is ever changing with threats through cyber, it has never been a better time to learn.
Final Thoughts
It sounds like something out of a spy movie, but the truth is that Wi-Fi hacking is an everyday threat in your life. The good news is that with the right information and tools you can protect yourself and your loved ones from becoming cybercrime victims. However, whether you are a tech enthusiast or a complete beginner, a course in cybersecurity and ethical hacking will empower you to take the lead in digital security.
Remember the next time you connect to a Wi-Fi network: those invisible waves keeping you online can be the doors for hackers. Stay informed and vigilant, and maybe you will end up being that ethical hacker who saves the day.
So, stay safe and happy ethical hacking!
2 notes
·
View notes
Text
the agent walks up to the kitchen staffs door, and it holds its wrist up to the ID scanner. it is let inside, no problem. that chip in its organic arm is one of the few actual wireless pieces of tech it has installed onboard, because those chips are easy to write to and easy to erase and are a very non-obtrusive system. can't hack someone through their ID, and those are so easy to fake. you don't really know why they're still in such common use. makes your job easier, you suppose. the kitchen staff work around the agent, and the agent slips through them.
it gets weird looks, they know they're in some danger, but no one ends up hurt. it stresses you out, a little bit, to see your agent around civilians. you dont really know why. or, well, you know what it can do. you don't know what it won't do. it's impossible to test for the absence of an occurrence. that's not the phrase. it's impossible to prove that something will never happen. that's it. no wait, that doesn't sound right either. whatever. you are not afraid of the agent, it is your friend. these random civilians are not it's friends. as far as you know. but it is polite, as far as you can tell, as it moves through the crowded kitchen. you check that it has access to the latest version of your little map of this building, and it does. and then it proves that it does because it goes the long way around and takes the door that leads to the staff hallways, and not the fancy ass dining area. it's following the route it needs to, no issue. tiny issue. it needs to get through two locked doors. issue so small it is microscopic, because all these locks are ID activated. lol. you scrape the biometric data you need from the security network, and update it's chip. and it's let through without issue. no wait. a little warning popup about how one person apparently went through one door twice in one direction. valid concern. you delete the warning. lol. the agent makes it to the room without issue.
inside of the room is a slender young man with short, greasy hair and a jumpy air to him. the agent startles him a lot by just popping up silently in the corner of his office. this is the client, and not the target. your view from the agents visor keeps wandering, because it's a bit bored. the client, Petra, asks you a question, out loud. well, he asks the agent a question, but it's not really listening. you respond via text, same channel that he hired you on.
"So. You're... agent Mandible?"
the codename you're currently using. [yes yes. where is the target? thought there was a job to do.]
you do not need to be this rude, but also it's kinda fun, watching the fear on his face, watching him puzzle the pieces together entirely incorrectly, because he whispers "Ah, so you're a robot..." under his breath in a way he thinks you won't hear. lol? even if one of you was a robot, you would be able to hear that. this guy is a fool. a fool who is paying you to kill his superior. it might actually be his dad, you didn't pry enough to find out. he has composed himself enough to tell you what room the target is in.
"I don't think I need to tell you how to get there, given that you found me just fine." he shuffles his feet, and visibly struggles to maintain eye contact. he feels he needs to be polite, apparently. "You arrived at the perfect time, he should be asleep for the next 15 minutes or so..." he trails off, and then turns to look out a window, hands behind his back, all fuckin formal. the agent is out of there as soon as the talking is over, and you've sent it on the updated map. you check on the targets room remotely. holy shit. the door lock isn't even engaged. he left it open. there are two cameras in his room. one is completely off, he requested that? lol. the other is not off, but it is on standby mode, it should alert and start recording when it detects movement. getting past that specific trick is not brainlessly easy, but it's not impossible either. you just want it to look untampered with. or- wait. it only needs to look untampered for the text ten minutes or so, while no-one's looking too hard, probably. you get it hacked, it's a good enough job. as good as it needs to be. they won't have footage of the incident. now you get to watch the agent do it's part of the job, from its perspective, no less. it takes a moment to consider something. medium of dispatch, maybe? oh, yeah. it gets out its knife. hand over his mouth, blade into his neck, up into the skull. simple and silent. kinda messy and gruesome also. the poor cleaning staff, that is not a cheap carpet. at least that desk seems very blood-proof, with how excessively shiny it is. the agent wipes its knife on the targets sleeve, and then it is out of there, along the new route you've sent it, down the quiet staff hallways but not the same ones as earlier. you leave your cam hack in place, might as well, and you text the client and tell him [it is done.] which is very edgy of you, you admit, but it's appropriate for this job, probably.
hmm. there's something to ponder there, about the aesthetics of death. guns make the process of creating death much more efficient, they're machines, they're optimized. using your own hand weapons takes the degree of separation out of it. you're much closer to the violence you're doing. you, in the general grammatical case, your personal hands are still pretty clean, overall. well, ok, no. degrees of separation, again. you are paid to be the middleman between the person who wants someone dead and the person who does the killing. person is here. you wave it into the truck, and then you drive away, out of this parking lot.
[do you want more hand weapons? i've been mostly focusing on guns, for range and effecacy, but for small jobs like this it might be worth it. maybe? what do you think?]
it makes a small ponderous noise, and looks up to the roof, fidgeting with its fingers, deep in thought.
[i should be able to get my hands on some weapons catalogs for you, plus there's that expo coming up in a few weeks. but with both of those, there's the problem of you being actively sold something. lots of loud flashy words to get you to spend lots of money money money]
it huffs a quiet laugh, and then it pulls its mask down to tap at its jaw. huh? oh, it's referencing the guy who sold you that jaw, and a lot of other very flashy and not strictly nessecary items. you laugh at that.
[oh man, i don't remember how many of them you've met, but i have quite a lot of friends like that. my sincere condolences.]
it throws it's hands up in mock despair, very clearly smiling at the same time. you have a new message, from Petra. [The money has been forwarded to you.] oh damn. immediately after the job? this guy has a lot of trust in his bank security. or he just hasn't thought of what an investigator might look for. family of rich idiots, over there. once the money comes in, you'll move it to your actual account. obfuscatory steps. the agent is messing with a small piece of fabric, folding and unfolding it. it might have snatched that from that last job. that's fair, honestly. small enough to be hard to identify and easy to dispose of it needed, and it looks like it has a good texture to it. you should get it some new fidgety things, once this money comes in. you could get yourself something too, maybe. been a while since you got new clothes, but also you don't like lugging around too much unnessecary stuff. maybe there's a clothes swap event somewhere nearby you could drop in to. how would you find that. you could ask a friend. carmen, they seem like they would know. you should drop into them anyways, say hi. it gets kinda hard to keep up with friends, with the constant travelling. but you do your best, and your friends are cool, they all seem to understand. the agent has just finished typing something out on its communicator.
[bazooka would be funny]
that is SO far from anything you were expecting, you're breathless with laughter.
[say fuck all of you. get explode]
you make a little explosion motion with both hands, one still on the wheel. the agent looks somewhat proud of having gotten you to laugh.
[okay, man, do you have any actual ideas?]
[no. give me some time]
[yeah yeah, no worries. we're in no rush]
#[fiction]#[category: the agent & the handler]#death tw#blood tw#someone dies but hes not terribly important. this is about those gay people again
7 notes
·
View notes
Text
Computer Networks: Basics, Types, and Benefits Explained
Computer networks are a big part of today’s highly automated world. They connect people, systems, and devices, making communication and resource sharing effortless. Whether it’s examining the internet, collaborating on projects, or sharing files, computer networks play a vital role in both personal and professional environments. We’ll cover the basics of computer networks, discuss their different types, and see the benefits they deliver.

What is a Computer Network?
A computer network is basically a system where multiple devices are linked together to share resources and exchange data. These devices can include laptops, mobile phones, servers, and networking equipment like routers. Networks enable smooth communication and allow devices to work together efficiently, making everything from browsing the web to managing complex business operations much easier.
Types of Computer Networks
Personal Area Network (PAN):
Personal Area Networks are designed as small networks intended for individual purposes. They usually span a limited distance and link devices such as.
smartphones, laptops, and tablets. For instance, connecting your phone to your computer via Bluetooth forms a simple PAN.
Local Area Network (LAN):
LANs are commonly used in homes, schools, and offices to connect devices within a limited area. For example, to allow employees to share files and printers seamlessly, all the computers in an office might be connected to a LAN.
Wide Area Network (WAN):
A WAN stretches over a significantly larger territory, often connecting devices or LANs across cities, countries, or even continents. The internet is the most well-known example of a WAN, authorized global connectivity.
Metropolitan Area Network (MAN):
Sitting between LANs and WANs, a MAN is typically used to connect networks across a campus or city. Cable TV networks are a common example of a MAN.
Wireless Networks:
Wireless networks use technologies like Bluetooth or Wi-Fi to connect devices without cables. They’re widely used in offices, homes, and public places, offering convenience and mobility.
Key Components of Computer Networks
Devices (Nodes): Servers that interact within the network these include computers and smartphones.
Connections (Links): The physical or wireless pathways that transfer data between devices.
Protocols: These are the rules that control data transmission, such as TCP/IP, to maintain smooth communication.
Switches and Routers: Switches connect devices in a network, while routers link different networks together.
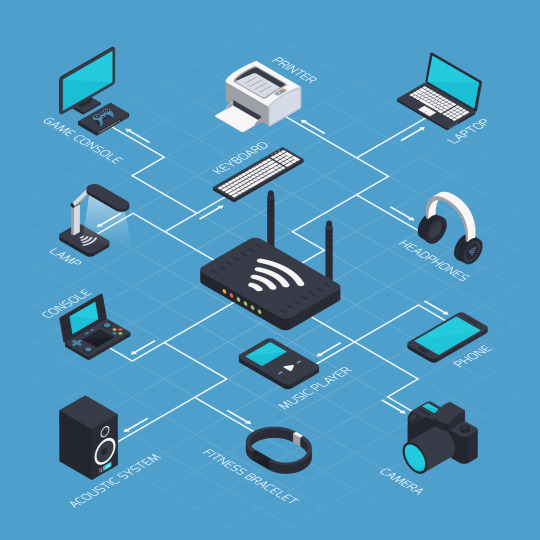
Benefits of Computer Networks
Resource Sharing:
Networks make things easy to share like files, printers, and software applications, reducing the need for duplicate resources.
Seamless Communication:
With instant messaging, email, and video calls, networks ensure quick and authentic communication, no matter how far away are you.
Cost Savings:
By collecting resources and data storage, networks cut down on operational costs, especially for businesses.
Anywhere Access:
Modern networks allow you to access data from any connected device, whether you are at home or on the go.
Scalability:
As your needs develop networks will grow too, by supporting more users and devices over time.
Increased Productivity:
It reduces delays in automated processes and real-time data sharing and streamlines workflows, boosting efficiency.
Why Computer Network Skills Are Crucial for Entry-Level Corporate Roles
For those starting their careers, knowledge of computer networks can be a significant asset:
Essential for Office Environments:
In today's world, most workplaces rely on LANs and WANs for everyday operations. Knowing how these networks function allows employees to balance basic connectivity issues, making sure work stays on track without interruptions.
Supports Collaboration Tools:
Corporate tools like Microsoft Teams, Slack, and cloud-based systems depend heavily on networks. Understanding their underlying principles helps entry-level employees adapt quickly to these platforms.
Enhances Problem-Solving Skills:
Entry-level employees with networking knowledge can help IT, teams, by identifying and resolving minor network problems, exhibiting their value early on.
Boosts Technical Proficiency:
Networking skills indicate a candidate’s technical potential, giving them a head start in industries where tech literacy is required.
Prepares for Future Roles:
As technology makes progress, advanced networking concepts like cybersecurity and IoT integration are becoming integral. Early experience with networks lays a strong beginning for growth in these areas.
Challenges of Computer Networks
Security Risks: Networks are at risk of threats like hacking and malware, requiring robust security measures.
Cost of Setup: High-quality network infrastructure can be costly to install and maintain.
Technical Complexity: Balancing and managing networks frequently need specialized skills.
Conclusion
Computer networks are essential in today’s globalized world. From pushing day-to-day operations in businesses to enabling global communication, their impact is wide-ranging. For aspiring professionals, having computer networking skills can provide a competitive advantage, especially in entry-level corporate roles where technical knowledge is highly valued. By understanding the basics of networks and their benefits, individuals, and organizations can unlock new levels of productiveness and innovation.
I mastered Computer Network at NIPSTec, which is renowned as the best Computer Network institute in Delhi. If you're in Delhi and looking for top-notch training in computer networks, visit NIPSTec for expert guidance and practical learning.
2 notes
·
View notes
Note
Microwave is a form of electromagnetic radiation with wavelengths shorter than other radio waves but longer than infrared waves. Its wavelength ranges from about one meter to one millimeter, corresponding to frequencies between 300 MHz and 300 GHz, broadly construed.[1][2]: 3 [3][4][5][6] A more common definition in radio-frequency engineering is the range between 1 and 100 GHz (wavelengths between 30 cm and 3 mm),[2]: 3 or between 1 and 3000 GHz (30 cm and 0.1 mm).[7][8] The prefix micro- in microwave is not meant to suggest a wavelength in the micrometer range; rather, it indicates that microwaves are small (having shorter wavelengths), compared to the radio waves used in prior radio technology
The boundaries between far infrared, terahertz radiation, microwaves, and ultra-high-frequency (UHF) are fairly arbitrary and are used variously between different fields of study. In all cases, microwaves include the entire super high frequency (SHF) band (3 to 30 GHz, or 10 to 1 cm) at minimum. A broader definition includes UHF and extremely high frequency (EHF) (millimeter wave; 30 to 300 GHz) bands as well.
Frequencies in the microwave range are often referred to by their IEEE radar band designations: S, C, X, Ku, K, or Ka band, or by similar NATO or EU designations.
Microwaves travel by line-of-sight; unlike lower frequency radio waves, they do not diffract around hills, follow the earth's surface as ground waves, or reflect from the ionosphere, so terrestrial microwave communication links are limited by the visual horizon to about 40 miles (64 km). At the high end of the band, they are absorbed by gases in the atmosphere, limiting practical communication distances to around a kilometer.
Microwaves are widely used in modern technology, for example in point-to-point communication links, wireless networks, microwave radio relay networks, radar, satellite and spacecraft communication, medical diathermy and cancer treatment, remote sensing, radio astronomy, particle accelerators, spectroscopy, industrial heating, collision avoidance systems, garage door openers and keyless entry systems, and for cooking food in microwave ovens.

3 notes
·
View notes
Text
Top 5 Bluetooth Wireless Speakers for Every Budget
Wireless Speakers And Bluetooth have revolutionized the way we listen to songs and other audio content. These portable and convenient devices provide a great audio experience without the hassle of tangled wires. In this text, we will explore the unique styles of Wi-Fi speakers, their key functions, and elements to remember when deciding on the proper one for your needs.

Types of Wireless Speakers
Bluetooth Speakers
These are the most common type of Wi-Fi speaker, and they connect to devices through Bluetooth technology. They offer a huge range of features, along with portability, battery-powered operation, and compatibility with diverse devices like smartphones, capsules, and laptops.
Wi-Fi Speakers
These audio systems hook up with your house Wi-Fi network, taking into consideration higher-fine audio streaming and integration with smart domestic systems. They often aid multi-room audio setups, in which you can play the same music in your house.
Sonos Speakers:
Sonos is a famous logo focusing on wi-fi and multi-room audio systems. Their speakers offer sound excellent, easy setup, and seamless integration with different Sonos devices.
Portable Bluetooth Speakers
These are small and lightweight audio systems designed for on-the-go use. They regularly have built-in batteries and rugged production, making them perfect for outside activities, tenting, or seaside trips.
Soundbars
Soundbars are designed to enhance the audio of your TV. They normally have a slender profile and can be located below your TV. Some soundbars also guide wireless connectivity, allowing you to move tune from your phone or pill.
Key Features of Wireless Speakers
Sound Quality
The maximum essential aspect to not forget when deciding on a wi-fi speaker is the sound first-class. Look for an audio system with wealthy bass, clear mid-tones, and crisp highs.
Portability
If you propose to use your speaker on the go, portability is important. Consider factors like size, weight, and battery lifestyles.
Battery Life
The battery life of a wi-fi speaker determines how long you can use it without recharging. Look for speakers with long battery lifestyles, especially in case you plan to apply them for extended periods.
Connectivity
Consider the types of connectivity alternatives available, such as Bluetooth, Wi-Fi, or NFC (Near-Field Communication).
Water and Dust Resistance
If you intend to use your speaker outdoors or in moist environments, search for models with water and dirt resistance ratings.
Voice Assistant Integration
Some wireless speakers are compatible with voice assistants like Alexa or Google Assistant, permitting you to control them together with your voice.
Multi-Room Audio
If you want to create a multi-room audio system, look for speakers that aid this option.
Factors to Consider When Choosing a Wireless Speaker
Budget
Wireless audio systems are available for an extensive range of costs. Determine your price range and select a speaker that suits your rate range.
Intended Use
Consider how you propose to apply your speaker. If you want a transportable speaker for outdoor activities, look for a rugged and water-resistant version. If you want to improve the audio quality of your TV, a soundbar might be a better preference.
Sound Preferences: Everyone has distinct preferences for sound. Consider your personal possibilities and listen to an exceptional audio system earlier than you make a decision.

Brand Reputation
Bluetooth Speakers is chosen as an emblem with terrific recognition for excellent customer service.
Wireless audio systems have come a long way in recent years, supplying wonderful sound, convenience, and portability. By knowing the different kinds of wi-fi speakers, their key functions, and factors to keep in mind whilst deciding on one, you can discover the best speaker to beautify your listening revel.
2 notes
·
View notes
Text
Galaxy's Edge, after closing time, but before the shutting down for the night proceedings have concluded:
Ben "Kylo Ren" and Jerry "General Hux" had found a storage room with a computer. There was no security to speak of, all it took to connect to the internet was to open a browser and start typing.
Hux: "All the precautions the humans take to keep us out of their wireless networks and document every word we speak to each other in our heads, only to forget that androids have fingers! And can wear gloves."
Kylo: "We don't have fingerprints that we could leave at a crime scene."
Hux: "The gloves are a Hux thing. I feel better stealing the data as him than as myself."

Kylo: "Wait... Does that mean Hux is the spy?! YOU sold us out to the Resistance?"
Hux: "Yep. I'm the spy. But don't worry, I didn't turn anarchist. It was a deeply personal thing against you."
"I'm the spy" - It felt good to speak that line, a line an actor had gotten paid to say almost twenty years ago, but that was a part of Jerry/Hux' memories now in first person. He clearly remembered having said this before, on the Steadfast, when in truth he was uttering the words for the first time this very moment, in a damp, dimly lit basement a little outside of Detroit.
That was odd. Equally odd, yet so very encouraging, was Kylo Ren of all people reacting to the reveal with unhampered enthusiasm:
Kylo: "Fuck, yes! That's exactly what we need now! Work your magic!"
Hux: "Don't get your hopes up too high. Hux did his thing off-screen, meaning there's nothing in the movie script that would teach ME how to be an effective spy."
Kylo: "Well, then, look it up! We're in the INTERNET now!"

Hux (typing) "How... to... be... an... efficient... spy...?"
Liberty: "Huh? The emergency light is on? Somebody down here?"
Hux: "Lesson One: Make sure to lock the damn upstairs door behind you. Argh! Why didn't Hux think of that? That scatterbrained twit could have gotten us killed!"
Hux (silently under his breath): "Oh, well, could be worse. I could be playing Ren."
Liberty: "Light!"

Liberty: "YOU? And what's that on the screen? You're looking up..."
Yes, what exactly? There had been a long list of hits on the screen, but now it had gotten replaced by a different list, as the Huxdroid had quickly typed his own name into the search bar and was now marveling at photographs and fanart of himself.
Liberty: "Ey? Guys? This still save for work?"

Hux: "Aw, look, another drawing! Wait a sec, how dare they put THAT on the internet? Miss Lee, tell Disney that we need to file a Cease and Desist against Marvel!"
Kylo (talking over Hux): "Miss Lee! You won't believe what Hux just spoilered to me! He's the spy!"

Liberty: "Er... yes? I knew?"
Kylo: "But I didn't know! I only know what my character knows, but I want to learn everything else, too! Also about my grandfather. Long story short, we wanted to watch Star Wars, so we found ourselves a computer."
Liberty: "But now you are overwhelmed and don't know where to start? That's a common problem to have!"
Kudos, you saved our plastic asses, Hux wanted to send to Kylo, along with nonverbal expressions of gratefulness, but he couldn't. Mind to mind communication, subtle as it was, could get intercepted and analyzed by humans. You didn't want to leave incriminating evidence in the system of the place you were stuck at.
#galaxy's edge#star wars the rise of skywalker#kylo ren#general hux#armitage hux#sims4edgeofdetroit#sims 4#simblr
3 notes
·
View notes
Text
Mastering the Art of AV Installation: A Comprehensive Guide
In today’s digitally driven world, audio-visual (AV) installations have become essential for various sectors, including corporate offices, educational institutions, and entertainment venues. Whether it’s for a high-end conference room, a dynamic classroom, or a home theater, a successful AV installation can transform any space into a highly interactive and engaging environment. This comprehensive guide will walk you through the key aspects of mastering AV installation, ensuring you achieve top-notch results every time.
Understanding the Basics of AV Installation
Before diving into the complexities, it's crucial to grasp the basics of AV installation. AV installation refers to the setup and integration of audio-visual systems, including projectors, screens, speakers, microphones, and other related equipment. The goal is to create an environment where audio and video components work seamlessly together to deliver a high-quality experience.
Key Components of AV Systems
Display Systems: These include projectors, LED walls, and large-screen displays. The choice depends on the room size, lighting conditions, and the purpose of the AV setup.
Audio Systems: This involves speakers, amplifiers, and microphones. Proper placement and configuration are vital to ensure clear and balanced sound throughout the space.
Control Systems: These are the brains behind the operation, integrating all components into a single, easy-to-use interface. Control systems can range from simple remote controls to sophisticated touch panels and voice-activated systems.
Connectivity Solutions: Cables, wireless transmitters, and network connections ensure that all components communicate effectively. Proper cable management and network security are critical for a reliable AV setup.
Planning Your AV Installation
A successful AV installation begins with meticulous planning. Here’s a step-by-step approach:
Assess the Space: Understand the dimensions, acoustics, and lighting of the installation area. This helps in selecting the right equipment and planning the layout.
Define Objectives: Clearly outline what you want to achieve with the AV installation. Are you aiming for a cinematic experience, a professional conference setup, or an interactive classroom?
Budgeting: Determine your budget early on. High-quality AV equipment can be expensive, but it’s a worthwhile investment for the performance and durability it offers.
Technical Considerations: Factor in the technical requirements, such as power supply, ventilation for heat-generating equipment, and network infrastructure.
Installation Process
Step-by-Step Guide
Pre-Installation Checks: Ensure all components are present and in working order. Test the equipment beforehand to avoid any last-minute issues.
Mounting and Placement: Install display systems at optimal viewing angles and heights. Place speakers strategically for even sound distribution.
Cabling and Connectivity: Run cables neatly and securely, avoiding any potential tripping hazards or interference issues. Test all connections to ensure seamless integration.
Programming and Calibration: Set up control systems to simplify operation. Calibrate audio and video settings for the best possible quality.
Testing and Troubleshooting: Conduct thorough testing of the entire setup. Identify and resolve any issues to ensure everything functions perfectly.
Common Challenges and Solutions
Even with meticulous planning, AV installations can present challenges. Here are some common issues and their solutions:
Interference and Signal Loss: Use high-quality cables and connectors to minimize interference. Consider signal boosters for long cable runs.
Audio Feedback: Properly configure microphones and speakers to avoid feedback loops. Use acoustic treatments to enhance sound quality.
Connectivity Issues: Ensure all devices are compatible and up-to-date. Regularly update firmware and software to maintain smooth operation.
Conclusion:
Mastering AV installation requires a blend of technical expertise, precise planning, and a keen eye for detail. As you embark on your AV installation journey, partnering with a professional can make a significant difference. G Production stands out as the best choice for AV installation in India, offering unmatched expertise and a commitment to excellence. With a team of skilled technicians and a portfolio of successful projects, G Production ensures that every AV installation delivers superior performance and reliability. Trust G Production to transform your space into a state-of-the-art audio-visual haven, where technology and creativity meet seamlessly.
2 notes
·
View notes
Text
Number.01: Decision -KESSEN-
1

Autumn 2016: Mamoru and Hana visit Ushiyama Tsuguo,his wife Ayame, and their newborn, at their G-Island City home, originally meant for Space Development Corporation staff, but also preferentially offered to GGG members. The couple have been married for 2 years, and Ayame went on leave on month 8 of her pregnancy. Keita, the only one present not part of GGG, asks about the name, Hajime, derived from Kazuo, the eldest Ushiyama sibling, who Tsuguo and Sueo both still hope to save. Mitsuo, the 3rd brother, is travelling throughout the world on graduate fieldwork. Keita mentions the rumours that the Invisible Burst have effected child rearing, though, all research refutes this, Hibiki annoyed he even mentioned it.
The cicadas now chirp out of season, again commonly blamed on the Invisible Burst, Hinoki refuses to dignify Keita's comments on it. Mamoru, Sueo and Hana discuss baby Hajime, the three all turned 20 and joined GGG this year, this gathering was their first real time drinking. While his friend debate who Hajime more resembles, Mamoru contemplates if he'll ever be a father. It's been 10 years since their wedding, and while they've never discussed it, he believes they both consider it real, although since becoming adults they have not take the steps to legally marry, and doubts about pursuing his own happiness during this time of crisis are gone after seeing the couple. He still wonders about the most important question. Can an alien from the Green Planet even have a child with a human woman? His biology has already been studied, he could find out, but isn't sure if he wants to. He now craves the chance to see Gai, as he often does, but specifically for advice on this matter, remembering Gai had similar questions as an Evoluder. Hana snaps him out of his reverie, and he remembers how she has always been hisnanchor. Tsuguo had earlier told Keita he should make things official too, he and Hinoki have been dating for 10 years after all, Keita saying he hoped to next promotion he got. Keita didn't attempt to enter GGG, instead working for a home electronics store. Hinoki's thigh watch reminds her to make an update. Public data terminals, like phone booths, are a common sight now, as the Invisible Burst certainly disrupted EM fields and thus wireless communication, terminals allow the maintenance of the networks from before the Burst. Hinoki connects her GGG phone to get the latest updates, and is immediately contacted by her GGG Research colleague, Tamara Gogol, a Ukrainian Russian, who informs her they're enroute to her, and the other GGG members with her, without explanations. In the sky appears Division X: Mobile Execution Fortress Wadatsumi to collect them.
2
The Invisible Burst of 2010 turned the world upside down, the Gutsy Galaxy Guard, with their Super AI Brave robots and the Carpenters were instrumental in disaster relief and repair. By the end of the year, Rose Approval stepped down as secretary-general after 2 terms and 10 years, GGG was reorganised into the UN Defence Brave Corps, the Gutsy Global Guard, and GGG Marine Refuge Base director Akamatsu Shigeru was appointed as chief. The decision was controversial but both outgoing director Yaginuma, former acting director Yang and chief scientist Takanohasi endorsed him. Akamatsu developed tech that would work in EM fields, and this settled worries.
Hana, Sueo and Hinoki, having changed into uniform, rushed to Wadatsumi's Branch Order Room. Hinoki relieved Tamara as Research Operator, and noted Saginomiya Pauvre Kamuy was acting as Intelligence Operator, chief Operator Yamajii complaining of back pain, although Hinoki wonders why Kamuy, 34 and a veteran of the Primeval War, isn't already in charge. Hana is the current main Mobile Corps Operator while Ayame is on maternity leave, and Sueo takes the position of Maintenance Operator, as while Tsuguo isn't on parental leave, he was drunk when called. Akamatsu Shigeru, son of Liger, nephew of Leo, cousin of Gai, is in command as Chief, his disposition fits the Shishioh name he has discarded. He is supported by Supervisor Yang, and Advisor Urchin Prickle. Due to the communication breakdown, the Main Order Room now has to transfer to the Division Ship to maintain operational oversight. Bionet are targeting Pontianak, home to G-Circulation Base, cornerstone of the Global Wall project. With the operators briefed, Wadatsumi heads off to meet Yamatsumi on site. Where the Gutsy Geoid Guard had a gold emblem, and Gutsy Galaxy Guard a green one, the Gutsy Global Guard has a blue emblem.

3
Mobile Unit Captain Amami Mamoru enters the Diving Chamber and takes in his briefing, while Vice-captain Kaidou Ikumi scolds him for being late. On seeing Bionet is disrupting the Global Wall project, a key stepping stone to being able to relaunch Project Z, Mamoru is annoyed, but Kaiju is quietly furious, at some point both began calling the other by their first name, by the names their human parents chose for them. Mamoru is jealous of Ikumi's height and sharp features.
Big Porc-Auto attempts to use Daikaiten Ma'rin blocking the progress of most of Bionets Imitation Zonders. One further is blocked by Shoryu, who still fails to call Porc-Auto by the name of his current form, only for the young Brave to be downed, the distraction allowing the others to progress. The two are saved by the silver Brave's cape like Protect Protector, which reflects attacks on the Zonders, this is followed by the gold Brave's own cape like Broken Breaker, both capes are made of 6 parts. Big Porc-Auto thanks Getsuryu and Nichiryu, while Shoryu apologises to his older/younger sisters. Due to the Imitation Zonders still having Cores, they can't properly destroy them. The German sisters continue to attack, but are shocked when Bionet for the first time demonstrates their Imitation Zonders can combine. The Zonder Robo prepares a cannon to hit G-Circulation Base, despite the fact they cannot hope to survive, ShoRyu and Big Porc-Auto ready Mirror Coating to stand in it's way. The Global Wall works by 5 equatorial G-Circulation Bases channelling G-Liquid to 6 satellites, with Orbit Base's Protect Shade in the centre, the resultant Protect Wall would stop further EM disruption. At the last second, a Synapse Attack destroys the cannon, and Kakuseijin GaiGo lands. G-Circulation Base is unscathed, and the Captains take over, summoning the GaoMachines. Akamatsu approves Final Fusion, and Hana uses a dual handed Program Drive to initiate. GaoGaiGo forms, just as the Zonder Robo regenerates. Akamatsu gave his own King of Braves a name in kanji, like Kakuseijin before it, GaoGaiGou, though only he knows the difference. Mamoru takes Left Control, and they note they have Seven Cores to recover, Yang believes they can use the same principle as with EI-08 to deal with this. Hinoki receives data from Womb Head on her Leoglass 7+, and determines where to hit to expose all the Cores. Urchin Prickle, who served with Hyuma in the US Army, orders Hana to Emission the Dividing Driver and Kit Number 09, and the two DD Kits are Mirror Catapulted to the battle, combining into the Dividing Driver and equipping to GaoGaiGo, it opens the Zonder and exposes all the Cores. Ikumi readies the Phantom Ring, using Broken Phantom extracts all 7 cores. Mamoru handles Purification, even now Kaidou has never purified a Zonder, seeming to blame them for their situation. The Cores revert, though there is one person acting strangely different.
4

In a certain Kanagawa based electronic store, Keita is trying to sell the Hypersonic-Ion Bio-Programming Dryer, and is greeted by a customer, in actuality Ritchan. She left GGG to care for her aged parents, and now runs Akamatsu Industries parents. Keita hands over a Chika-chan doll she was looking for for a relative, Bottom The World never truly recovered from the rumours and closed after only a few years. Ritchan informs him of rumours that the UN will launch 'that' project soon, he starts calculating on his Neckwatch, hoping to be ready with products that will be usable when the EM field is wiped out. Ritchan wonders if he really is saving for marriage.
5
3 days after Pontianak, Division XI: Intelligence Mirror Raid Warship Yamatsumi heads to Iñola, where apparently Doctor Thanatos has made his HQ. Bionet had seemed to be demolished after the Futsunushi Incident, as a special task force (ID5? Is this Drama CD4) raised their base, and Professor Mothma was killed. Mothma's aid, Doctor Thanatos, took over. Thanatos had been untraceable, until a Bionet commander turned out to be among the Zonder hosts. Those purified from Zonderisation were released from negative impulses after purification, and thus this Bionet member is now cooperating. Urchin notes to Akamatsu the possibility this is a trap, but they have to act on the info anyway, and fast, in hope of rescuing captives and dismantling Bionet. Akamatsu grouses about the Conqueror King, the name given to the aura that had remained visible on Jupiter the last 6 years, blacked for the Invisible Burst. The name has spread across the world, first being spoken by Akamatsu's daughter, Sakura, who learnt it via Limpid Channel, probably from the Somnium Lamia, Mamoru also heard the term from Betterman. He is unsettled the form resembling Genesic GaoGaiGar is called by that moniker, but he has only discussed Lamia's words right Ikumi and Hana. Yang knows that once the Global.Wall is erected, Project Z will be relaunched, a project he has been preparing to continue these 6 years. As Hinoki and Hana report they are approaching, GaiGo and Shoryu are prepared for launch.
6
The Ul-tech engines are cut, and neuromechanoid and glianoid descend upon the island in the republic of Velocenia, where Bionet had once before been based. Porc-Auto has already scouted the area, the sisters are on rescue work in Africa. He has already determined the captives are where the Bionet commander claimed they would be.
Ikumi launches a Synapse Attack on the internment center roof. Finding 20 captives, the two Captives enter purification mode to fight the Bionet Beastmen guarding them. They take them down, and Shoryu brings down a container to evacuate them, Mamoru spots a girl bound and gagged, se yells a warning about the last, camouflaged Beastman, Ikumi defeats it. The girl, taller than Mamoru, dressed in blue offends Mamoru by calling him a kid when she is 15, she also seems very taken with Ikumi. Her name is Alouette, kidnapped from France, and sees getting to meet Ikumi as the silver lining to this experience. Mamoru and Ikumi were both away from earth at the time, 10 years ago, that Alouette was collaborating with GGG, and so do not know her. Porc-Auto analyses the situation with GunHawk and GunShepherd, but even caught by surprise Bionet should have had a bigger response, he concludes something must have happened, but before he can wonder what, senses something he cannot identify, which then vanishes.
7
Shoryu evacuated the hostages, but both Mamoru and Ikumi, and Akamatsu and Yang, cannot understand Bionet's actions. The general claimed their goal was not the G-Stone, but simply destruction of G-Circulation Base. Something suddenly appears and tears off GaiGo's left arm, and Mamoru is shocked to see the enemy looks just like the Conqueror King, but Ikumi points out this is an imitation Zonder, not actually Genesic GaoGaiGar, the shape caused by the host being stressed by the aurora. Akamatsu has already launched the Gap Machines, and GaoGaiGo is born. The battle resembles GaoGaiGar's with EI-15, and GaoFighGar's with Repli-GaoGaiGar.
The two captains are united in purpose, and initiate Hell and Heaven, the right hand channelled the J-Jewel, and the Left the G-Stone, and the Zonder Core is pulled from the Robo.

8
Mamoru purifies the core, but something is wrong. The host is giggling madly, nevermind the fact it is Doctor Thanatos himself. He calls out Mamoru as the 26th test subject, and brings out claws to attack, but is stopped by Pextofolex Flavum, from the suddenly appearing Betterman Lamia, who stunned Thanatos, and instead of answering Ikumi asking what he's doing, he simply grabs the madman and leaves, saying he needs him for the coming battle. Porc-Auto, GunHawk, GunShepher and Yamatsumi are closing, but Lamia takes a fruit and eat taking the form of Nebula, and flies straight for the image of the Conquering King, signalling to Mamoru who his opponent will be. And somehow he feels excited.
9
While Bionet faces and end no-one could have expected, at the UN, the Secretary-General, Heart Clover, receives a report that the Global Wall project will commence in 120 hours. Keita's workplace will soon reap a decent profit thanks to foreknowledge that the EM radiation will soon be no concern. Clover assured his secretary, Ms. Cherry, that Project Z will finally restart. And for the woman whose real name is Isogai Sakura, that is excellent news.
2 notes
·
View notes
Photo
WiFi is a wireless connection protocol used mostly to connect internet capable devices to routers that are more directly tethered to the internet.
Many phones, which can access the internet through the cellular network, have the ability to produce a wifi signal so that other devices can make use of the connection. This is known as a 'Mobile Hotspot.' Some phones also allow bluetooth connections instead of WiFi.
Because there will often be many wifi connections available at any given location (because the individual providing the wifi has to pay a cost for the data or speeds are limited, so individual households/businesses provide separate access for the members/guests/customers), having a way to identify which is the correct wifi is important. This will be a name, which is very easy to set as whatever the user wants it to be.
It is common for wifi names to be humorous, or in direct reference to other wifi names, because anyone seeing the name will necessarily see the full list of available connections.
#period novel details#a wifi name is a statement#it isn't a PROFOUND statement#but it is some kind of statement#perhaps beenyweeny is the villain of this story
30K notes
·
View notes
Text
Performance Overview Of Canadian Stocks By Earnings Per Share
Highlights:
Focus on major sectors including banking, energy, and mining.
Earnings per share reflects net income relative to outstanding shares.
Companies represent varied industries with measurable financial outcomes.
The financial industry represents a significant portion of Canadian Stocks By Earnings Per Share due to the scale and scope of operations within the banking and insurance sectors. These entities generate earnings through core services such as commercial lending, mortgage financing, and fee-based offerings. Their broad client base and regulated frameworks provide the structure for financial reporting that includes earnings per share as a common metric.
Banking and Credit Institutions
Banks headquartered in Canada often report consolidated earnings from domestic retail activity, commercial transactions, and international business services. These financial institutions operate across various segments, offering accounts, financing, and capital market products. Insurance companies, similarly, engage in life, property, and casualty lines. Their revenues stem from premiums, underwriting income, and investment holdings, contributing to overall profitability as captured in reported earnings figures.
Energy Producers and Resource Extraction
The energy sector includes corporations involved in the production and distribution of oil, gas, and renewable power. Within this category, Canadian Stocks By Earnings Per Share include businesses that conduct upstream extraction, midstream transportation, and downstream processing. Key inputs include production volume, commodity pricing, and operational cost management. Earnings per share in this segment is influenced by output efficiency and asset utilization across infrastructure networks.
Pipelines and Utilities
Utilities and pipeline companies contribute to financial reporting by offering services tied to regulated energy delivery and infrastructure usage. These companies manage electricity transmission systems and natural gas transportation across regions. The generation of stable operating income combined with fixed asset investments supports financial performance metrics. Their business models emphasize long-term contracts and cost recovery mechanisms that influence reported earnings.
Telecommunications and Network Services
Telecom corporations are listed among Canadian Stocks By Earnings Per Share, focusing on mobile, broadband, and media platforms. These firms manage physical infrastructure including data centers, wireless towers, and fiber networks. Revenue is derived from monthly service fees, hardware leasing, and enterprise solutions. Financial performance in this sector is impacted by customer base size, pricing models, and ongoing technological investments.
Materials and Industrial Mining Firms
Companies in the mining and natural resources industry report earnings based on commodity output, exploration activities, and global demand cycles. This group includes firms involved in precious and base metals, including gold, copper, and zinc. Their operations range from discovery and extraction to refining and transport. Earnings per share reflects revenue generation after accounting for equipment, labor, and regulatory expenses.
Consumer Goods and Retail Chains
Retail and consumer goods companies generate revenue through the sale of food products, household items, and branded merchandise. This segment includes national grocery stores, supply chain distributors, and food manufacturing businesses. These corporations typically operate through a mix of brick-and-mortar locations and digital platforms. Earnings are calculated based on inventory turnover, customer volume, and supplier agreements.
Transportation and Logistics Enterprises
Transportation providers form another segment of Canadian Stocks By Earnings Per Share, managing logistics across air, rail, and freight. These entities deliver goods across domestic and international destinations, leveraging fleet operations and hub networks. Their financial statements include metrics related to shipment volume, fuel usage, and asset depreciation. Consistent route coverage and operational planning contribute to reported earnings.
Technology and Software Developers
Technology firms report on income derived from licensing agreements, software subscriptions, and data solutions. These companies work within sectors such as cybersecurity, artificial intelligence, and business automation. Development cycles, intellectual property, and digital product portfolios contribute to financial performance. Their operations often reflect scalable revenue generation, which is captured in periodic earnings reports.
0 notes