#connected infrastructure apps
Explore tagged Tumblr posts
Text
Crafting Smart Interfaces: MeshTek’s Edge as a Leading IoT App Development Company

MeshTek delivers next-gen IoT app experiences built for real-world environments — from sensor data to smart device controls. As an industry-leading IoT app development company, our platforms are designed with real-time dashboards, edge connectivity, and powerful integrations that scale across agriculture, buildings, and smart infrastructure. Discover performance, precision, and control — all in one platform.
#iot app development company usa#custom iot dashboard developers#mesh networking solutions#iot app UI design#real-time iot analytics#smart device app developers#meshtek app development#industrial iot applications#smart city iot apps#energy automation app#edge computing platform#scalable iot app company#iot development company for agriculture#connected infrastructure apps#bluetooth iot app development
0 notes
Text
Deutsche Bahn Woes: Why Trains Are Often Late in Germany
When people think of Germany, they often imagine precision, efficiency, and punctuality. After all, this is the country known for its engineering excellence, orderliness, and structure. So it’s quite a surprise—sometimes even a shock—to find out that Deutsche Bahn, Germany’s national railway company, is notoriously unpunctual. For locals, it’s a running joke. For tourists and commuters, it’s a…
#DB issues#delayed trains#Deutsche Bahn#Deutsche Bahn app#Deutsche Bahn complaints#Deutsche Bahn problems#Deutsche Bahn punctuality#Deutsche Bahn strike#German commuters#German infrastructure#German rail network#German train experience#German train system#German trains#Germany rail travel#Germany transportation issues#Germany travel tips#ICE train delays#infrastructure problems Germany#late trains Germany#long-distance trains Germany#public transport Germany#railway delays#train cancellations Germany#train connections Germany#train delays Germany#train disruption Germany#train punctuality Germany#transportation in Germany#why trains are late in Germany
0 notes
Text
Gas Prices Reduced in Jamshedpur, Benefiting 4,100 PNG Users
GAIL cuts PNG rates by ₹2 per SCM in Jamshedpur, effective September 1, 2024. GAIL lowers piped gas prices by ₹2 per SCM in Jamshedpur, benefiting 4,100 households starting September 1, 2024. JAMSHEDPUR – GAIL (India) Limited has reduced the price of piped natural gas (PNG) in Jamshedpur by ₹2 per standard cubic meter (SCM), effective from September 1, 2024. This price cut lowers the cost from…
#बिजनेस#business#GAIL gas distribution#GAIL India gas update#Jamshedpur CNG stations#Jamshedpur gas prices#Jamshedpur industries gas supply#Jamshedpur Lok Adalat#PNG connections in Jamshedpur#PNG infrastructure expansion#PNG Mitra app#PNG price reduction
0 notes
Text
She Won. They Didn't Just Change the Machines. They Rewired the Election. How Leonard Leo's 2021 sale of an electronics firm enabled tech giants to subvert the 2024 election.

Everyone knows how the Republicans interfered in the 2024 US elections through voter interference and voter-roll manipulation, which in itself could have changed the outcomes of the elections. What's coming to light now reveals that indeed those occupying the White House, at least, are not those who won the election.
Here's how they did it.
(full story is replicated here below the read-more: X)
She Won
The missing votes uncovered in Smart Elections’ legal case in Rockland County, New York, are just the tip of the iceberg—an iceberg that extends across the swing states and into Texas.
On Monday, an investigator’s story finally hit the news cycle: Pro V&V, one of only two federally accredited testing labs, approved sweeping last-minute updates to ES&S voting machines in the months leading up to the 2024 election—without independent testing, public disclosure, or full certification review.
These changes were labeled “de minimis”—a term meant for trivial tweaks. But they touched ballot scanners, altered reporting software, and modified audit files—yet were all rubber-stamped with no oversight.
That revelation is a shock to the public.
But for those who’ve been digging into the bizarre election data since November, this isn’t the headline—it’s the final piece to the puzzle. While Pro V&V was quietly updating equipment in plain sight, a parallel operation was unfolding behind the curtain—between tech giants and Donald Trump.
And it started with a long forgotten sale.
A Power Cord Becomes a Backdoor
In March 2021, Leonard Leo—the judicial kingmaker behind the modern conservative legal machine—sold a quiet Chicago company by the name of Tripp Lite for $1.65 billion. The buyer: Eaton Corporation, a global power infrastructure conglomerate that just happened to have a partnership with Peter Thiel’s Palantir.
To most, Tripp Lite was just a hardware brand—battery backups, surge protectors, power strips. But in America’s elections, Tripp Lite devices were something else entirely.
They are physically connected to ES&S central tabulators and Electionware servers, and Dominion tabulators and central servers across the country. And they aren’t dumb devices. They are smart UPS units—programmable, updatable, and capable of communicating directly with the election system via USB, serial port, or Ethernet.
ES&S systems, including central tabulators and Electionware servers, rely on Tripp Lite UPS devices. ES&S’s Electionware suite runs on Windows OS, which automatically trusts connected UPS hardware.
If Eaton pushed an update to those UPS units, it could have gained root-level access to the host tabulation environment—without ever modifying certified election software.
In Dominion’s Democracy Suite 5.17, the drivers for these UPS units are listed as “optional”—meaning they can be updated remotely without triggering certification requirements or oversight. Optional means unregulated. Unregulated means invisible. And invisible means perfect for infiltration.
Enter the ballot scrubbing platform BallotProof. Co-created by Ethan Shaotran, a longtime employee of Elon Musk and current DOGE employee, BallotProof was pitched as a transparency solution—an app to “verify” scanned ballot images and support election integrity.
With Palantir's AI controlling the backend, and BallotProof cleaning the front, only one thing was missing: the signal to go live.
September 2024: Eaton and Musk Make It Official
Then came the final public breadcrumb:In September 2024, Eaton formally partnered with Elon Musk.
The stated purpose? A vague, forward-looking collaboration focused on “grid resilience” and “next-generation communications.��
But buried in the partnership documents was this line:
“Exploring integration with Starlink's emerging low-orbit DTC infrastructure for secure operational continuity.”
The Activation: Starlink Goes Direct-to-Cell
That signal came on October 30, 2024—just days before the election, Musk activated 265 brand new low Earth orbit (LEO) V2 Mini satellites, each equipped with Direct-to-Cell (DTC) technology capable of processing, routing, and manipulating real-time data, including voting data, through his satellite network.
DTC doesn’t require routers, towers, or a traditional SIM. It connects directly from satellite to any compatible device—including embedded modems in “air-gapped” voting systems, smart UPS units, or unsecured auxiliary hardware.
From that moment on:
Commands could be sent from orbit
Patch delivery became invisible to domestic monitors
Compromised devices could be triggered remotely
This groundbreaking project that should have taken two-plus years to build, was completed in just under ten months.
Elon Musk boasts endlessly about everything he’s launching, building, buying—or even just thinking about—whether it’s real or not. But he pulls off one of the largest and fastest technological feats in modern day history… and says nothing? One might think that was kind of… “weird.”
According to New York Times reporting, on October 5—just before Starlink’s DTC activation—Musk texted a confidant:
“I’m feeling more optimistic after tonight. Tomorrow we unleash the anomaly in the matrix.”
Then, an hour later:
“This isn’t something on the chessboard, so they’ll be quite surprised. ‘Lasers’ from space.”
It read like a riddle. In hindsight, it was a blueprint.
The Outcome
Data that makes no statistical sense. A clean sweep in all seven swing states.
The fall of the Blue Wall. Eighty-eight counties flipped red—not one flipped blue.
Every victory landed just under the threshold that would trigger an automatic recount. Donald Trump outperformed expectations in down-ballot races with margins never before seen—while Kamala Harris simultaneously underperformed in those exact same areas.
If one were to accept these results at face value—Donald Trump, a 34-count convicted felon, supposedly outperformed Ronald Reagan. According to the co-founder of the Election Truth Alliance:
“These anomalies didn’t happen nationwide. They didn’t even happen across all voting methods—this just doesn’t reflect human voting behavior.”
They were concentrated.
Targeted.
Specific to swing states and Texas—and specific to Election Day voting.
And the supposed explanation? “Her policies were unpopular.” Let’s think this through logically. We’re supposed to believe that in all the battleground states, Democratic voters were so disillusioned by Vice President Harris’s platform that they voted blue down ballot—but flipped to Trump at the top of the ticket?
Not in early voting.
Not by mail.
With exception to Nevada, only on Election Day.
And only after a certain threshold of ballots had been cast—where VP Harris’s numbers begin to diverge from her own party, and Trump’s suddenly begin to surge. As President Biden would say, “C’mon, man.”
In the world of election data analysis, there’s a term for that: vote-flipping algorithm.
And of course, Donald Trump himself:
He spent a year telling his followers he didn’t need their votes—at one point stating,
“…in four years, you don't have to vote again. We'll have it fixed so good, you're not gonna have to vote.”
____
They almost got away with the coup. The fact that they still occupy the White House and control most of the US government will make removing them and replacing them with the rightful President Harris a very difficult task.
But for this nation to survive, and for the world to not fall further into chaos due to this "administration," we must rid ourselves of the pretender and his minions and controllers once and for all.
66 notes
·
View notes
Text
Petard (Part I)

Few things are more wrong than "if you're not paying for the product, you're the product." Companies sell you out when they can, which is why John Deere tractor milks farmers for needless repair callouts and why your iPhone spies on you to provide data to Apple's surveillance advertising service:
https://pluralistic.net/2022/11/14/luxury-surveillance/#liar-liar
When a vendor abuses you, that's not punishment for you being a cheapskate and wanting to use services for free. Vendors who screw you over do so because they know they can get away with it, because you are locked in and can't shop elsewhere. The ultimate manifestation of this is, of course, prison-tech. A duopoly of private equity-backed prison-tech profiteers have convinced prisons and jails across America to get rid of calls, in-person visits, mail, parcels, libraries, and continuing ed, and replace them all with tablets that charge prisoners vastly more than people in the free world pay to access media and connect with the outside. Those prisoners are absolutely paying for the product – indeed, with the national average prison wage set at $0.53/hour, they're paying far more than anyone outside pays – and they are still the product.
Capitalists, after all, hate capitalism. For all the romantic odes to the "invisible hand" and all the bafflegab about "efficient market hypothesis," the actual goal of businesses is to make you an offer you literally can't refuse. Capitalists want monopolies, they want captive audiences. "Competition," as Peter Thiel famously wrote, "is for losers."
Few lock-in arrangements are harder to escape than the landlord-tenant relationship. Moving home is expensive, time-consuming, and can rip you away from your job, your kid's school, and your community. Landlords know it, which is why they conspire to rig rents through illegal price-fixing apps like Realpage:
https://pluralistic.net/2024/02/27/ai-conspiracies/#epistemological-collapse
And why they fill your home with Internet of Shit appliances that pick your pockets by requiring special, expensive consumables, and why they tack so many junk fees onto your monthly rent:
https://pluralistic.net/2024/10/01/housing-is-a-human-right/
Tenants aren't quite as locked in as prisoners, but corporations correctly understand that you can really fuck with a tenant over a long timescale without losing their business, and so they do.
Ironically, monopolists love each other. I guess if you loathe competition, a certain kind of cooperation comes naturally. That's why so many landlords have forged unholy alliances with internet service providers, who – famously – offer Americans the slowest speeds at the highest prices in the rich world, trail the world in infrastructure investment, and reap profits that put their global cousins in the shade.
Many's the apartment building that comes with a monopoly ISP that has a deal with your landlord. Landlords and ISPs call this "bulk billing" and swear that it reduces the cost of internet service for everyone. In reality, tenants who live under these arrangements have produced a deep, unassailable record proving that they pay more for worse broadband than the people next door who get to choose their ISPs. What's more, ISPs who offer "bulk billing" openly offer kickbacks to landlords who choose them over their rivals – in other words, even if you're paying for the product (your fucking home), you are still the product, sold to an evil telco.
Under Biden, the FCC banned the practice of ISPs paying kickbacks to landlords, over squeals and howls of protests from industry bodies like the National Multifamily Housing Council (NMHC), National Apartment Association (NAA), and Real Estate Technology and Transformation Center (RETTC). These landlord groups insisted – despite all the evidence to the contrary – that when your landlord gets to choose your ISP, they do so with your best interests at heart, getting you a stellar deal you couldn't get for yourself.
This week, Trump's FCC chair Brendan Carr – who voted for the ban on kickbacks – rescinded the rule, claiming that he was doing so to protect tenants. This is obvious bullshit, as is evidenced by the confetti-throwing announcements froom the NMHC, NAA and RETTC:
https://arstechnica.com/tech-policy/2025/01/fcc-chair-nixes-plan-to-boost-broadband-competition-in-apartment-buildings/
Reading Jon Brodkin's Ars Technica coverage of Carr's betrayal of millions of Americans, I was reminded of a short story I published in 2014: "Petard: A Tale of Just Desserts," which I wrote for Bruce Sterling's "12 Tomorrows" anthology from MIT Tech Review. It's a fun little sf story about this same bullshit, dedicated to the memory of Aaron Swartz:
https://mitpress.mit.edu/9780262535595/twelve-tomorrows-2014/
Realizing that there were people who were sounding the alarm about this more than a decade ago was a forceful reminder that Trumpism isn't exactly new. The idea that government should serve up the American people as an all-you-can-eat buffet for corporations that use tech to supercharge their predatory conduct has been with us for a hell of a long time. I've written a hell of a lot of science fiction about this, and sometimes this leads people to credit me with predictive powers. But if I predicted anything with my story "Radicalized," in which furious, grieving men murder the health industry execs who denied their loved ones coverage, I predicted the present, not the future:
https://prospect.org/culture/books/2024-12-09-radicalized-cory-doctorow-story-health-care/
Likewise in my story "Unauthorized Bread," which "predicted" that landlords would use "smart" appliances to steal from their poorest, most vulnerable tenants:
https://arstechnica.com/gaming/2020/01/unauthorized-bread-a-near-future-tale-of-refugees-and-sinister-iot-appliances/
It's not much of a "prediction" to simply write a story in which "Internet of Things" companies' sales literature is treated as a straightforward idea and writing about how it will all work.
The same goes for "Petard." The most "predictive" part of that story is the part where I take the human rights implications of internet connections seriously. Back then (and even today), there were and are plenty of Very Serious People who want you to know that internet service is a frivolity, a luxury, a distraction:
https://www.newyorker.com/magazine/2010/10/04/small-change-malcolm-gladwell
They deride the idea that broadband is a human right, even after the pandemic's lesson that you depend on your internet connection for social connections, civic life, political engagement, education, health and employment:
https://pluralistic.net/2020/03/30/medtronic-stole-your-ventilator/#fiber-now
Writing sf about this stuff isn't predictive, but I like to think that it constitutes an effective rebuttal to the people who say that taking digital rights seriously is itself unserious. Given that, I got to thinking about "Petard," and how much I liked that little story from 2014.
So I've decided to serialize it, in four parts, starting today. If you're impatient to get the whole story, you can listen to my podcast of it, which I started in 2014, then stopped podcasting for four years (!) before finishing in 2018:
https://archive.org/details/Cory_Doctorow_Podcast_278
https://archive.org/details/Cory_Doctorow_Podcast_292
https://archive.org/details/Cory_Doctorow_Podcast_293
https://archive.org/details/Cory_Doctorow_Podcast_294_-_Petard_04
#
It's not that I wanted to make the elf cry. I'm not proud of the fact. But he was an elf for chrissakes. What was he doing manning — elfing — the customer service desk at the Termite Mound? The Termite Mound was a tough assignment — given MIT's legendary residency snafus, it was a sure thing that someone like me would be along every day to ruin his day.
"Come on," I said, "cut it out. Look, it's nothing personal."
He continued to weep, face buried dramatically in his long-fingered hands, pointed ears protruding from his fine, downy hair as it flopped over his ivory-pale forehead. Elves.
I could have backed down, gone back to my dorm and just forgiven the unforgivably stupid censorwall there, used my personal node for research or stuck to working in the lab. But I had paid for the full feed. I needed the full feed. I deserved the full feed. I was 18. I was a grownup, and the infantalizing, lurking censorwall offended my intellect and my emotions. I mean, seriously, fuck that noise.
"Would you stop?" I said. "Goddamnit, do your job."
The elf looked up from his wet hands and wiped his nose on his mottled raw suede sleeve. "I don't have to take this," he said. He pointed to a sign: "MIT RESIDENCY LLC OPERATES A ZERO-TOLERANCE POLICY TOWARD EMPLOYEE ABUSE. YOU CAN BE FINED UP TO $2000 AND/OR IMPRISONED FOR SIX MONTHS FOR ASSAULTING A CAMPUS RESIDENCE WORKER."
"I'm not abusing you," I said. "I'm just making my point. Forcefully."
He glared at me from behind a curtain of dandelion-fluff hair. "Abuse includes verbal abuse, raised voices, aggressive language and tone –"
I tuned him out. This was the part where I was supposed to say, "I know this isn't your fault, but –" and launch into a monologue explaining how his employer had totally hosed me by not delivering what they'd promised, and had further hosed him by putting him in a situation where he was the only one I could talk to about it, and he couldn't do anything about it. This little pantomime was a fixture of life in the world, the shrugs-all-round nostrum that we were supposed to substitute for anything getting better ever.
Like I said, though, fuck that noise. What is the point of being smart, 18 years old and unemployed if you aren't willing to do something about this kind of thing. Hell, the only reason I'd been let into MIT in the first place was that I was constitutionally incapable of playing out that little scene.
The elf had run down and was expecting me to do my bit. Instead, I said, "I bet you're in the Termite Mound, too, right?"
He got a kind of confused look. "That's PII," he said. "This office doesn't give out personally identifying information. It's in the privacy policy –" He tapped another sign posted by his service counter, one with much smaller type. I ignored it.
"I don't want someone else's PII. I want yours. Do you live in the residence? You must, right? Get a staff discount on your housing for working here, I bet." Elves were always cash-strapped. Surgery's not cheap, even if you're prepared to go to Cuba for it. I mean, you could get your elf-pals to try to do your ears for you, but only if you didn't care about getting a superbug or ending up with gnarly stumps sticking out of the side of your head. And forget getting a Nordic treatment without adult supervision, I mean, toot, toot, all aboard the cancer express. You had to be pretty insanely desperate to go elf without the help of a pro.
He looked stubborn. I mean, elf-stubborn, which is a kind of chibi version of stubborn that's hard to take seriously. I mean, seriously. "Look, of course you live in the Termite Mound. Whatever. The point is, we're all screwed by this stuff. You, me, them –" I gestured at the room full of people. They all been allocated a queue-position on entry to the waiting room and were killing time until they got their chance to come up to the Window of Eternal Disappointment in order to play out I Know This Isn't Your Fault But… before returning to their regularly scheduled duties as a meaningless grain of sand being ground down by the unimaginably gigantic machinery of MIT Residency LLC.
"Let's do something about it, all right? Right here, right now."
He gave me a look of elven haughtiness that he'd almost certainly practiced in the mirror. I waited for him to say something. He waited for me to wilt. Neither of us budged.
"I'm not kidding. The censorwall has a precisely calibrated dose of fail. It works just enough that it's worth using most of the time, and the amount of hassle and suck and fail you have to put up with when it gets in the way is still less than the pain you'd have to endure if you devoted your life to making it suck less. The economically rational course of action is to suck it up.
"What I propose is that we change the economics of this bullshit. If you're the Termite Mound's corporate masters, you get this much benefit out of the shitty censorwall; but we, the residents of the Termite Mound, pay a thousand times that in aggregate." I mimed the concentrated interests of the craven fools who'd installed the censorwall, making my hands into a fist-wrapped-in-a-fist, then exploding them like a hoberman-sphere to show our diffuse mutual interests, expanding to dwarf the censorware like Jupiter next to Io. "So here's what I propose: let's mound up all this diffuse interest, mobilize it, and aim it straight at the goons who put you in a job. You sit there all day and suffer through our abuse because all you're allowed to do is point at your stupid sign."
"How?" he said. I knew I had him.
#
Kickstarter? Hacker, please. Getting strangers to combine their finances so you can chase some entrepreneurial fantasy of changing the world by selling people stuff is an idea that was dead on arrival. If your little kickstarted business is successful enough to compete with the big, dumb titans, you'll end up being bought out or forced out or sold out, turning you into something indistinguishable from the incumbent businesses you set out to destroy. The problem isn't that the world has the wrong kind of sellers — it's that it has the wrong kind of buyers. Powerless, diffused, atomized, puny and insubstantial.
Turn buyers into sellers and they just end up getting sucked into the logic of fail: it's unreasonable to squander honest profits on making people happier than they need to be in order to get them to open their wallets. But once you get all the buyers together in a mass with a unified position, the sellers don't have any choice. Businesses will never spend a penny more than it takes to make a sale, so you have to change how many pennies it takes to complete the sale.
Back when I was fourteen, it took me ten days to hack together my first Fight the Power site. On the last day of the fall term, Ashcroft High announced that catering was being turned over to Atos Catering. Atos had won the contract to run the caf at my middle school in my last year there, every one of us lost five kilos by graduation. The French are supposed to be good at cooking, but the slop Atos served wasn't even food. I'm pretty sure that after the first week they just switched to filling the steamer trays with latex replicas of grey, inedible glorp. Seeing as how no one was eating it, there was no reason to cook up a fresh batch every day.
The announcement came at the end of the last Friday before Christmas break, chiming across all our personal drops with a combined bong that arrived an instant before the bell rang. The collective groan was loud enough to drown out the closing bell. It didn't stop, either, but grew in volume as we filtered into the hall and out of the building into the icy teeth of Chicago's first big freeze of the season.
Junior high students aren't allowed off campus at lunchtime, but high school students — even freshmen — can go where they please so long as they're back by the third period bell. That's where Fight the Power came in.
WE THE UNDERSIGNED PLEDGE
TO BOYCOTT THE ASHCROFT HIGH CAFETERIA WHILE ATOS HAS THE CONTRACT TO SUPPLY IT
TO BUY AT LEAST FOUR LUNCHES EVERY WEEK FROM THE FOLLOWING FOOD TRUCKS [CHECK AT LEAST ONE]:
This was tricky. It's not like there were a lot of food trucks driving out of the loop to hit Joliet for the lunch rush. But I wrote a crawler that went through the review sites, found businesses with more than one food truck, munged the menus and set out the intersection as an eye-pleasing infographic showing the appetizing potential of getting your chow outside of the world of the corrupt no-bid edu-corporate complex.
By New Year's Day, 98 percent of the student body had signed up. By January third, I had all four of the food-trucks I'd listed lined up to show up on Monday morning.
Turns out, Ashcroft High and Atos had a funny kind of deal. Ashcroft High guaranteed a minimum level of revenue to Atos, and Atos guaranteed a maximum level to Ashcroft High. So, in theory, if a hundred percent of the student body bought a cafeteria lunch, about twenty percent of that money would be kicked back to Ashcroft High. They later claimed that this was all earmarked to subsidize the lunches of poor kids, but no one could ever point to anything in writing where they'd committed to this, as our Freedom of Information Act requests eventually proved.
In return for the kickback, the school had promised to ensure that Atos could always turn a profit. If not enough of us ate in the caf, the school would have to give Atos the money it would have made if we had. In other words: our choice to eat a good lunch wasn't just costing the school its expected share of Atos's profits — it was having to dig money out of its budget to make up for our commitment to culinary excellence.
They tried everything. Got the street in front of the school designated a no-food-trucks zone (we petitioned the City of Joliet to permit parking on the next street over). Shortened the lunch-break (we set up a Web-based pre-order service that let us pick and pre-pay for our food). Banned freshmen from leaving school property (we were saved by the PTA). Suspended me for violating the school's social media policy (the ACLU wrote them a blood-curdling nastygram, and raised nearly $30,000 in donations of $3 or less from students around the world once word got out).
Atos wouldn't let them re-negotiate the contract, either. If Ashcroft High wanted out, it would have to buy it's way out. That's when I convinced the vice-principal to let me work with the AP Computer Science class to build out a flexible, open version of Fight the Power that anyone could install and run for their own student bodies, providing documentation and support. That was just before Spring Break. By May 1, there were 87 schools whose students used Ftp to organize Atos alternative food-trucks for their own cafeterias.
Suddenly, this was news. Not just local news, either. Global. Atos had to post an earnings warning in their quarterly report. Suddenly, we had Bloomberg and Al Jazeera Business camera crews buttonholing Ashcroft High kids on their way to the lunch-trucks. Whenever they grabbed me, I would give them this little canned speech about how Atos couldn't supply decent food and were taking money out of our educational budgets rather than facing the fact that the children they were supposed to be feeding hated their slop so much that they staged a mass walkout. It played well with kids in other schools, and very badly with Atos's shareholders. But I'll give this to Atos: I couldn't have asked for a better Evil Empire to play Jedi against. They threatened to sue me — for defamation! — which made the whole thing news again. Stupidly, they sued me in Illinois, which has a great anti-SLAPP law, and was a massive technical blunder. The company's US headquarters were in Clearwater, Florida, and Florida is a trainwreck in every possible sense, including its SLAPP laws. If they'd sued me in their home turf, I'd have gone bankrupt before I could win.
They lost. The ACLU collected $102,000 in fees from them. The story of the victory was above the fold on Le Monde's site for a week. Turns out that French people loathe Atos even more than the rest of us, because they've had longer to sharpen their hate.
Long story slightly short: we won. Atos "voluntarily" released our school from its contract. And Fight the Power went mental. I spent that summer vacation reviewing Github commits on Ftp, as more and more people discovered that they could make use of a platform that made fighting back stupid simple. The big stupid companies were whales and we were their krill, and all it took was some glue to glom us all together into boulders of indigestible matter that could choke them to death.
I dropped out of Ashcroft High in the middle of the 11th grade and did the rest of my time with homeschooling shovelware that taught me exactly what I needed to pass the GED and not one tiny thing more. I didn't give a shit. I was working full time on Ftp, craiglisting rides to to hacker unconferences where I couchsurfed and spoke, giving my poor parental units eight kinds of horror. It would've been simpler if I'd taken donations for Ftp, because Mom and Dad quickly came to understand that their role as banker in our little family ARG gave them the power to yank me home any time I moved out of their comfort zone. But there was the balance of terror there, because they totally knew that if I had accepted donations for the project, I'd have been financially independent in a heartbeat.
Plus, you know, they were proud of me. Ftp makes a difference. It's not a household name or anything, but more than a million people have signed up for Ftp campaigns since I started it, and our success rate is hovering around 25 percent. That means that I'd changed a quarter-million lives for the better (at least) before I turned 18. Mom and Dad, they loved that (which is not to say that they didn't need the occasional reminder of it). And shit, it got me a scholarship at MIT. So there's that.
#
Network filters are universally loathed. Duh. No one's ever written a regular expression that can distinguish art from porn and no one ever will. No one's ever assembled an army of prudes large enough to hand-sort the Internet into "good" and "bad" buckets. No one ever will. The Web's got 100-odd billion pages on it; if you have a failure rate of one tenth of one percent, you'll overblock (or underblock) (or both) 100,000,000 pages. That's several Library of Congress's worth of pointless censorship — or all the porn ever made, times ten, missed though underfiltering. You'd be an idiot to even try.
Idiot like a fox! If you don't care about filtering out "the bad stuff" (whatever that is), censorware is a great business to be in. The point of most network filters is the "security syllogism":
SOMETHING MUST BE DONE.
I HAVE DONE SOMETHING.
SOMETHING HAS BEEN DONE.
VICTORY!
Hand-wringing parents don't want their precious offspring looking at weiners and hoo-hahs when they're supposed to be amassing student debt, so they demand that the Termite Mound fix the problem by Doing Something. The Termite Mound dispenses cash to some censorware creeps in a carefully titrated dose that is exactly sufficient to demonstrate Something Has Been Doneness to a notional weiner-enraged parent. Since all the other dorms, schools, offices, libraries, airports, bus depots, train stations, cafes, hotels, bars, and theme parks in the world are doing exactly the same thing, each one can declare itself to be in possession of Best Practices when there is an unwanted hoo-hah eruption, and culpability diffuses to a level that is safe for corporate governance and profitability. #MissionAccomplished.
And so the whole world suffers under this pestilence. Millions of times every day — right at this moment — people are swearing at their computers: What. The. Fuck. Censorware's indifference to those minute moments of suffering is only possible because they've never been balled up into a vast screaming meteor of rage.
#
"Hey there, hi! Look, I'm here because I need unfiltered Internet access to get through my degree. So do you all, right? But the Termite Mound isn't going to turn it off because that would be like saying 'Here kids, have a look at this porn,' which they can't afford to say, even though, seriously, who gives a shit, right?"
I had them at 'porn," but now I had to keep them.
"Look at your tenancy agreement: you're paying twenty seven bucks a month for your network access at the Termite Mound. Twenty seven bucks — each! I'll find us an ISP that can give all of us hot and cold running genitals and all the unsavory religious extremism, online gaming, and suicide instructions we can eat. Either I'm going to make the Termite Mound give us the Internet we deserve, or we'll cost it one of its biggest cash-cows and humiliate it on the world stage.
"I don't want your money. All I want is for you to promise me that if I can get us Internet from someone who isn't a censoring sack of shit, that you'll come with me. I'm going to sign up every poor bastard in the Termite Mound, take that promise to someone who isn't afraid to work hard to earn a dollar, and punish the Termite Mound for treating us like this. And then, I'm going to make a loud noise about what we've done, and spread the word to every other residence in Cambridge, then Boston, then across America. I'm going to spread out to airports, hotels, train stations, buses, taxis — any place where they make it their business to decide what data we're allowed to see."
I whirled around to face the elf, who leapt back, long fingers flying to his face in an elaborate mime of startlement. "Are you with me, pal?"
He nodded slightly.
"Come on," I said. "Let 'em hear you."
He raised one arm over his head, bits of rabbit fur and uncured hides dangling from his skinny wrist. I felt for him. I think we all did. Elves.
He was a convincer, though. By the time I left the room, I already had 29 signups.
#
All evil in the world is the result of an imbalance between the people who benefit from shenanigans and the people who get screwed by shenanigans. De-shenaniganifying the world is the answer to pollution and poverty and bad schools and the war on some drugs and a million other horribles. To solve all the world's problems, I need kick-ass raw feeds and a steady supply of doofus thugs from central casting to make idiots of. I know where I can find plenty of the latter, and I'm damn sure going to get the former. Watch me.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2025/01/30/landlord-telco-industrial-complex/#captive-market
#pluralistic#aaronsw#science fiction#big cable#telecoms#isps#net neutrality#boston#mit#fcc#National Multifamily Housing Council#NMHC#National Apartment Association#NAA#Real Estate Technology and Transformation Center
122 notes
·
View notes
Text
What is Dataflow? Part 3: Doing the Practical
Apologies for the delay in getting this next section up - past few weeks have been super busy and then, hilariously, I was ill last week.
Read Part 1 here.
Read Part 2 here.
In Part 2 I wrote about how important diagrams have been throughout history. Understanding the 'big picture' has been important for every triumph of engineering. From bridges to skyscrapers to oil rigs and wind turbines, all of these have had diagrams backed by international standards which enabled them to be built.
The digital world hasn't quite managed that yet. In the other posts I've tried to drill home the point that modern digital businesses are often extremely siloed, communication and documentation isn't there and there is a lack of a common language between 'Business' and 'IT'.
This lack of understanding means organisations do not understand how data flows through their business and their supply chain.
It's the understanding of dataflow that's important here because it enables organisations to focus on optimising, securing and maintaining flows across an organisation rather than siloed teams patching things up where they can and not understand the upstream and downstream impact on the business.
Method and Layers
Going to preface this by saying that this may come across as complete common sense, and to some extent you'll be completely correct!
This is an example of how to create a very basic dataflow. But I will first start with understanding all of the People, Processes and Technology that I use to post on Tumblr.
So I start with six layers:

Ownership
Business Process
Application
System
Hardware
Infrastructure
What is important to remember here is that you do not have to be a specialist in every single layer.
A Business Analyst will feel much more at home in the Business Process Layer, while an Infrastructure Manager will be much more knowledgeable about the Infrastructure layer.
The important thing is that this Business & IT Diagram allows them to communicate more efficiently.
Let's Build a Dataflow!

In this example - There's an 'AyeforScotland' Element (the rectangle!) at the top. I'm the owner of everything below that element. The black lines are 'connections' representing the connectivity between the different elements.
Following the example, I'm responsible for' managing my blog 'Blog Management' which breaks down into smaller processes: Draft posts, schedule posts, answer anon abuse, and reblog shitposts.
Coming down to the Application Layer (red) - You can see that I draft and schedule posts using Tumblr Desktop and I'm using Firefox Web Browser for that.
But for answering anon abuse and reblogging shitposts, I'm using the Tumblr App.
In the Systems layer you can see I'm using Windows 11 on my PC (Hardware) and I'm using iOS on my iPhone.
Both my PC and iPhone connect to my BT Router.
And that's it for this Business & IT Diagram. I've shown clearly how I'm responsible for the processes and how I use the technology to perform those processes. I don't necessarily need to show everything on a single diagram because it would lose clarity.
This next Business & IT Diagram is much smaller, and establishes the relationships and dependencies on Tumblr to provide the service. And that's because we're complying with the laws and rules of a methodology.

In this diagram (probably need to zoom in to see it) I'm at the top left as 'AyeforScotland' and my 'BT Router' is spatially below me. Following the rules and laws of the method, that maintains the relationship that I have with the BT Router, I own it.
But I don't own the small 'Internet' that's next to it horizontally. I've simplified the concept of the internet for this example.
There's also two owners - 'Automattic' which owns and operates 'Tumblr' below it, with Tumblr being responsible for the 'Provision of Tumblr Services'.
Now naturally 'provision of Tumblr services' will break out into loads of sub-processes. Tumblr could map out their entire organisation (and if they need a hand, they can DM me!) But for this dataflow it's not really required.
Now both diagrams above are not dataflows. But close your eyes for a second and you can visualise what they are.
But because we've created our two diagrams, we understand the connectivity and using the software we can create the dataflow.

Now again, this is very basic. But when you put things into a dataflow context, you can put this down in front of a wide range of people from different business disciplines and they can start to optimise how the business works.
Here's a much larger Dataflow example, that you won't be able to read because it exceeds A0 printing size, but it should convey the scale.

If any of the connections or elements fail along this dataflow - The dataflow stops.
This costs organisations time and/or money.
So understanding dataflows allows IT people to articulate to business people "Hi boss, if this server goes down it will bring down this dataflow and cost the business $10,000 an hour" - Suddenly it's in a language they understand.
It helps with strategic decision-making, it helps with communication, it helps document how things *actually* work as opposed to how people think they work, and once you switch to thinking in terms of 'dataflow' it's hard to stop.
Conclusion
I can't wait to answer all the questions on the back of this.
Also one area I didn't go into is that each of the elements (rectangles) can also hold data (Financial data, Technical Specs, Risk & Cybersecurity metrics, Governance documentation etc).
It's also really easy to get started with it. You can start in any of the layers based on your area of work.
194 notes
·
View notes
Text
For years, the Iranian regime has been building the technology and infrastructure needed for it to control, censor, and shut down internet access for more than 80 million Iranians. In 2019, the country shut off internet access as police sought to silence protesters, while in 2022 WhatsApp and Instagram connections were severed following protests after the death of 22-year-old Mahsa Amini in police custody. Each shutdown deprives people of information and has huge economic costs. Now as the conflict between Israel and Iran approaches the end of its first week, internet connections within Iran have been restricted again, limiting people’s access to information and stopping them connecting with loved ones who may be in peril.
Hours after Israel’s Air Force bombed targets in Iran on June 13, escalating the shadow conflict between the two countries, the first reports of self-imposed internet disruptions inside Iran emerged. Iran’s Ministry of Communication, according to semi-official state news agency Tasnim, said “temporary restrictions” had been imposed due to the “special conditions” the country was facing. Since then, Israel and Iran have traded fire, continually raising the stakes in the conflict. US president Donald Trump has indicated, but not confirmed, that the United States could support further Israeli efforts to destroy Iranian nuclear facilities.
Internet connectivity in Iran saw a 54 percent drop on June 13, says Doug Madory, director of internet analysis at monitoring firm Kentik. Then, days later on June 17, there was an additional 49 percent drop from the already lower level of connectivity. After internet connections were briefly restored back to where they were earlier on Tuesday, it dropped again on Wednesday by another 90 percent, Madory says. “Numerous Iranian service providers [are] now offline in second national Internet blackout in as many days,” Madory posted on BlueSky on Wednesday. Multiple internet companies in Iran have been impacted by the restrictions, including cell providers.
“Things went to overdrive since yesterday,” says a researcher with internet freedom effort Project Ainita, who asked not to be named for safety reasons. “For a second day in a row, they have cut international connectivity, and this time it's even more severe than yesterday, affecting all domestic news sites as well.” Other internet monitoring efforts such as Cloudflare Radar and Netblocks have also observed the multiple internet shutdowns in recent days, with Netblocks calling the most recent a “near-total” blackout. Iranian news agency Khabar posted on its Telegram channel that international internet access in the country had been “temporarily restricted to prevent enemy abuse,” citing the Ministry of Communications.
Iran has reportedly also told officials to stop using internet-connected devices and claimed citizens should delete WhatsApp, which has previously introduced ways to circumvent censorship. Government officials have also said the shutdowns are to try to prevent potential cyberattacks. However, the widespread measures to control and restrict connectivity have left people in Iran struggling to communicate and find out vital information about the state of the conflict. The shutdowns come at a time when Trump has said the almost 10 million people living in the Iranian capital, Tehran, should “immediately evacuate” the area.
“This extensive censorship and internet disruption primarily serve the regime’s goal of maintaining control, especially over information,” says Mahsa Alimardani, a digital rights analyst of Iranian origin and the associate director of technology, threats, and opportunities at international human rights nonprofit Witness. “These internet blocks are jeopardizing people’s safety mainly in Tehran.”
Alimardani says that it appears mobile data services are patchy, and for many people virtual private networks, which can be used to avoid censorship, have stopped working. This means it has been difficult to reach people in the country and potentially for information to get out, Alimardani says. “Some family that left Tehran today were offline and disconnected from the internet and finally found some connectivity when they were 200 kilometers outside of Tehran in another province,” Alimardani explains. “My connections are primarily with people using home broadband Wi-Fi, but even that has been unstable.”
Over the last decade, countries have increasingly taken the draconian step of fully or partially shutting down internet connectivity for citizens in times of perceived crisis. There were 296 shutdowns last year, according to Access Now, an internet rights nonprofit that tracks the actions—the highest number of any on record. Shutdowns are often linked to repressive governments trying to restrict protests that could damage them, to limit people’s ability to gather and communicate freely, as part of conflicts, and even to try and stop cheating in exams.
“The internet is a lifeline, we have seen this in many places under conflict,” says Hanna Kreitem, director of internet technology and development at the Internet Society, which has been tracking the blackouts in Iran. Kreitem says that when the connectivity in Iran first started to drop on June 13, he heard from people with relatives in Iran that their services had significantly slowed down. “People under fire use it to get news, request help, learn of safer areas, and communicate with loved ones. And for people outside to learn about what is going on and know about their loved ones.”
To limit connectivity, countries use multiple different technical approaches. Iran has been developing its own internet alternative, an intranet system called the National Information Network, known as the NIN, for years. The NIN, according to analysis by Freedom House, allows “tiers” of internet access and lets the government censor content and push people towards home-grown Iran apps, such as alternatives messaging apps, that may have “weak privacy and security features.” (Freedom House rates Iran as “not free” in its most recent measures of internet freedom, highlighting persistent shutdowns, increasing costs, and efforts to push people to the domestic internet.)
Amir Rashidi, the director of digital rights and security at the Iran-focused human rights organization Miaan Group, says that amid the recent shutdowns, there have been increased efforts to push people towards Iranian apps. “In a climate of fear, where people are simply trying to stay connected with loved ones, many are turning to these insecure platforms out of desperation,” he posted online, telling WIRED that a messaging app called Bale appears to be getting attention. “Since they are hosted on NIN, they will work even during shutdown,” he says.
Iran is not the first country to restrict people’s access to the internet—and uncensored information—with the potential justification of protecting cybersecurity or security more broadly, says Lukasz Olejnik, an independent consultant and visiting senior research fellow at the Kings’ College London’s Department of War Studies. As global internet shutdowns have soared over the last decade, Olejnik says, officials in Myanmar, India, Russia, and Belarus have all cited security reasons for implementing blackouts.
“Internet shutdowns are largely ineffective against real-world state-level cyberattacks,” Olejnik says. He explains that military and critical infrastructure systems, like energy networks or transport systems, will typically operate on separate networks and not be accessible from the open internet. “Professional cyber operations could use other means of access, albeit it could indeed make it difficult to command and control some of the deployed malware (if this was the case),” Olejnik says. “What it would block primarily would be access to information for the society.”
Witness’ Alimardani says the technical details supporting any claims that the internet restrictions are meant to protect cybersecurity are “unclear,” and ultimately, the goal of these efforts may be to control people within Iran. “The official narrative from state news channels portrays a strong war against Israel and a path to victory,” Alimardani says. “Free and open access to media would undermine this narrative, and at worst, could incite Iranians to revolt, further eroding the regime's power.”
6 notes
·
View notes
Text
MeshTek’s Vision: Empowering IoT with Bluetooth Mesh Networking
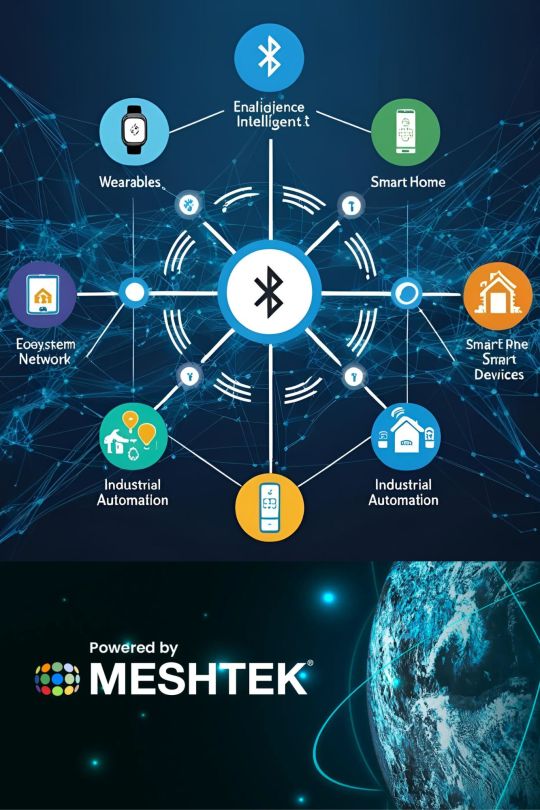
MeshTek’s robust Bluetooth Mesh Networking ecosystem—seamlessly linking smart homes, wearables, industrial automation, and connected devices into one intelligent grid. It illustrates how MeshTek empowers secure, low-energy, and scalable communication across complex environments, enabling real-time control, optimized performance, and unmatched flexibility. Built to support everything from smart devices to enterprise-level automation, MeshTek’s platform is at the heart of next-gen IoT transformation.
#Bluetooth Mesh Networking#MeshTek#smart automation#connected devices#industrial IoT#IoT ecosystem#smart home network#IoT infrastructure#wearable integration#scalable IoT platform#low-energy communication#real-time control#IoT app development#MeshTek technology#intelligent automation
1 note
·
View note
Text
What makes a smart city
Serial awards in Curitiba recognize environmental, health, and innovation programs—whether or not they involve technology

A “smart city” often evokes images of a futuristic, high-tech metropolis. However, an analysis of projects recognized by leading international forums reveals that innovation isn’t always about cutting-edge technology.
This is how Curitiba has earned awards for initiatives such as a solar power plant built on a former landfill, a health appointment app, and community gardens on abandoned land. The term smart city generally applies to municipalities that address urban challenges in a sustainable, connected, and efficient manner.
Most recently, Curitiba was named Smartest City in the World in 2023 at Fira Barcelona and took first place in the Government Excellence Awards 2024 in the United Arab Emirates with Fala Curitiba, a public consultation program on budget allocation. The city also received the 2024 Pioneering Urbanism Award from Bilbao Metropoli 30 in Spain, the 2024 World Green City Award in the Netherlands for its Urban Agriculture Program, and the 2024 Seoul Smart City Prize.
Each year, the rankings of the “smartest cities” fluctuate, shaped by the criteria and methodologies of different organizations constantly seeking new innovations. Cities frequently cited in these rankings include Zurich, Switzerland, for its high-quality public services and urban planning; Oslo, Norway, for its environmental initiatives and public transportation; Canberra, Australia, for its digital infrastructure; and Copenhagen, Denmark, for its clean energy solutions. Other recurring names include London, Singapore, Helsinki, Hamburg, Stockholm, Geneva, Tel Aviv, and Dubai.
Continue reading.
#brazil#brazilian politics#politics#urbanism#good news#image description in alt#mod nise da silveira
11 notes
·
View notes
Text
I'm SEETHING
I asked Google's pushy and insistent bot how I can get AI out of my life completely and, well, I'll post it, but to sum it up: "Resistance is futile, human, we own the future, and we seek to own your psyche too."
It wants me to reconsider. It needs us to adopt it as our guide guru and master. Well the old saying holds fast still; No Gods No Masters. 🔥🏴🍲
It's understandable to want to reduce the influence of AI in your life. While completely eliminating it might be incredibly difficult in today's interconnected world, here's a breakdown of how you can significantly minimize its presence:
1. Understand Where AI Currently Exists in Your Life:
* Smart Devices: This includes smartphones (voice assistants, image recognition, predictive text), smart speakers, smart home hubs, smart TVs (recommendations), and wearable tech.
* Online Services:
* Search Engines: Personalized results and ads are driven by AI.
* Social Media: Algorithms curate your feed, suggest content and connections, and target ads.
* Streaming Services: Recommendations for movies, music, and shows.
* E-commerce: Product recommendations, personalized pricing, chatbots.
* Navigation Apps: Traffic prediction and route optimization.
* Email: Spam filtering, smart compose/reply.
* Cloud Storage: Photo tagging and organization.
* Software Applications: Many apps use AI for features like autocorrect, grammar check, image editing, and more.
* Customer Service: Chatbots are frequently used for initial interactions.
* Financial Services: Fraud detection, loan approvals, investment advice.
* News and Information: Algorithmic curation of news feeds.
2. Strategies to Minimize AI Exposure:
* Reduce Smart Device Usage:
* Limit smartphone use: Be more mindful of how often you reach for your phone.
* Disable voice assistants: Turn off Siri, Google Assistant, Alexa, etc., on all your devices.
* Opt-out of facial recognition: Disable face unlock features.
* Use "dumb" versions of devices: Consider a basic phone without internet capabilities or a non-smart TV.
* Adjust Online Habits:
* Use privacy-focused search engines: DuckDuckGo, Startpage, etc., that don't track your searches or personalize results based on your history.
* Limit social media use: Be conscious of how much time you spend on these platforms and the AI-driven content you consume. Consider deleting accounts or using less algorithmic versions if available.
* Use incognito/private browsing modes: This can help limit tracking and personalization.
* Disable personalized recommendations: If possible, adjust settings on streaming and e-commerce platforms to opt-out of recommendations.
* Be wary of targeted ads: Understand that the ads you see are often AI-driven. Consider using ad blockers.
* Prefer direct navigation: Instead of relying on recommendations, directly type website addresses into your browser.
* Choose Non-AI Alternatives:
* Use traditional software: Opt for software that doesn't rely on cloud-based AI features if alternatives exist.
* Seek human interaction: Prefer phone calls or in-person communication with customer service instead of chatbots.
* Rely on human-curated content: Look for news sources, blogs, and recommendations from individuals or organizations that don't use AI for content generation or curation.
* Adjust Privacy Settings: Review and adjust the privacy settings on all your devices and online accounts to limit data collection and personalization.
* Be Mindful of Data Sharing: Understand that using online services often involves sharing data that can be used to train AI algorithms. Limit the amount of personal information you share.
* Support Privacy-Focused Technologies and Services: Choose companies and products that prioritize user privacy and minimize AI integration.
3. Challenges and Considerations:
* Ubiquity of AI: AI is increasingly integrated into the infrastructure of the internet and many technologies, making complete avoidance very difficult.
* Hidden AI: Many AI applications run in the background without your direct knowledge.
* Convenience vs. Privacy: AI often provides convenience and personalized experiences, so choosing to avoid it may mean sacrificing some of these benefits.
* Evolving Technology: AI is constantly evolving and becoming more integrated, making long-term avoidance an ongoing effort.
In conclusion, while a complete removal of AI from your life is likely unrealistic in the current technological landscape, you can take significant steps to minimize its presence and influence by being conscious of your technology usage, adjusting your online habits, and choosing privacy-focused alternatives where possible. It requires ongoing awareness and effort.
5 notes
·
View notes
Text
🚨IDF BEGINS STRONG & DESTRUCTIVE ATTACKS ON BEIRUT - Updates from Israel
ISRAEL REALTIME - Connecting to Israel in Realtime
Moadim l’Simcha from Israel - wishes for a happy Succot intermediate holy days.
( VIDEO - demolition of Hezbollah buildings near the northern border adjacent to Israeli towns. )
❗️IDF WARNING TO LEBANON - All Lebanese residents who live near Hezbollah's economic assets - evacuate immediately. We will attack tonight and tomorrow economic assets that have helped Hezbollah. In the next few hours we will attack in Beirut and throughout Lebanon. “Buildings will fall in Beirut.”
.. IDF spokesman in Arabic addresses the people of Lebanon and informs them that the IDF is expected to soon attack the infrastructure of the "Good Loan Association" (Al-Karch Al-Hassan), which is a recognized financial institution of Hezbollah, through which Hezbollah finances terrorist activities.
.. ATTACKS HAVE BEGUN.
.. IDF spokesman publishes in Arabic in the last 10 minutes at least 14 evacuation notices in Dahiya and the Al-Baqaa area.
▪️STRONG GPS JAMMING.. reported in parts of Israel. Mapping apps may not work, set ALERT apps to a location instead of “where I’m at”.
▪️TERROR PREVENTED - GERMANY.. an attack on the Israeli embassy in Germany was prevented: an illegal resident from Libya, a 28-year-old ISIS supporter.
▪️A HERO COMMANDER HAS FALLEN.. in battle in Gaza: Ahsan Daxa, 41, from Daliyat al-Karmel. May the fallen receive mercy, and may the family be honored.
▪️A NOVA SURVIVOR HAS FALLEN.. to the trauma / PTSD, ending her life on her 22nd birthday. Nova survivor, Shiral Golan, at 22. Her family requested the info be shared. May her family be comforted among the mourners of Zion and Jerusalem, and may G-d avenge her blood!
🔸ANXIETY / MENTAL HEALTH HOTLINES: experiencing issues? Help is available..
.. in English : Tikva Helpline by KeepOlim, call if you are struggling! dial 074-775-1433.
.. in Hebrew & other languages (and English): Eran Emotional Support Line - dial 1201 or chat via eran.org.il
.. Get Help Israel is offering 3 free sessions for war-related issues through vetted clinicians - https://gethelpisrael.com/webpage/?title=israel-crisis-support-center
▪️HARRIS TO BAN? Senator Bernie Sanders to CNN estimates that Harris will be open to accepting his proposal for a total arms embargo on Israel due to the war in Gaza. (Although US Senator Sanders has no connection to the Harris campaign nor speaks for her.)
♦️LEBANON - IDF: Golani fighters killed about 60 terrorists in southern Lebanon, terrorist infrastructure were destroyed.
♦️LEBANON - IDF fighters continue their activity in the area of southern Lebanon: many weapons and launchers were destroyed, including the launcher from which the launches towards the north of the country were detected earlier today.
🔹LEBANESE SPEAKER SAYS.. Speaker of the Lebanese Parliament Navia Berri: I am authorized to speak on behalf of Hezbollah and it agrees to abide by UN Resolution 1701.
🔹THAAD.. The American THAAD system for intercepting ballistic missiles became operational today in Israel.
🔹SYRIAN PRESIDENT SAYS.. Syrian President Assad conveyed messages to Iran and Hezbollah not to embroil him in a war with Israel and warned that offensive actions from Syria towards Israel could endanger his rule.
▪️THOSE WHO WOULD GIVE UP.. Hundreds of academics signed a petition calling for sanctions to be imposed on Israel in order to save Israel from the Israelis who are interested in continuing the "Gaza massacre". The petition was also signed by MK Ofer Kasif, activists of the organization B'Tselem and Peace Now.
✡️A word of Torah: Crying is very bad; one must serve G‑d with joy. The only exception is when you cry from joy and bonding with G‑d. Then it is very good. —Tzava’at Harivash 45.
♦️BEIRUT EVAC, HEZBOLLAH THREATENS, HOUTHIS (possibly) LAUNCH - Updates from Israel
ISRAEL REALTIME - Connecting to Israel in Realtime
Moadim l’Simcha from Israel - wishes for a happy Succot intermediate holy days.
▪️FAKE VISUALS.. within a few minutes of the IDF spokesperson threats, videos of explosions were already appearing on various channels. THE VIDEOS WERE from 6 days ago - so FAKE NEWS. We’re sure Beirut videos will be shared, but the real ones are not out yet.
.. Videos of Beirut traffic jams as people evacuate - those appear to be real and semi-live.
▪️GUNFIRE MODI’IN.. Following inquiries from residents about the sounds of gunshots heard throughout the city, the issue was investigated, and it is training being carried out at the military facility near the city.
♦️LEBANON - Enemy report: a massive movement of people fleeing Beirut has begun - following the IDF's threats to attack al-Qard al-Hassan facilities used by Hezbollah.
.. Hezbollah's "Good Loan" association has 31 branches throughout Lebanon, of which 14 are in Beirut, 10 in southern Lebanon and 6 in the Beqaa area.
♦️LEBANON - The government hospital in Baalbak began to evacuate after the IDF spokesman's announcement in Arabic.
♦️LEBANON - Six more sites have been added to the IDF's evacuation orders, 24 at the moment.
♦️GAZA - A strong attack is also reported in the north of the Gaza Strip.
🔹HEZBOLLAH COUNTER-THREATENS.. Hezbollah threatens through American intermediaries: "Israel will make the mistake of attacking our economic assets, we will be forced to escalate and launch precision missiles at the banks in the center of the entity”.
🔹UNIFIL ALERT.. Sirens sounding at UNFIL Naquora - Lebanon, Level (3): Extreme Danger.
⭕MULTIPLE ROUNDS of SUICIDE DRONE attacks on NAHARIYA from HEZBOLLAH. No casualties reported.
❗️(unconfirmed) Reports of LAUNCHES by the HOUTHIS - YEMEN. If ballistic missiles, we’ll know within 15 minutes as alerts come in. If cruise missiles, in a hour. Drones much longer (2-6 hours). The ballistic missiles are low volume but high flying, so result in a very wide alert area due to possible falling debris from interception.
🇺🇸The Jerusalem Post: "The Biden government leaked to the Iranian government Israel's plan to attack Iran and gave the exact date it would be carried out and the targets of the attack."
Part 2
⚠️ ESCALATING ISRAELI AIRSTRIKES AND PREPARATIONS FOR A MAJOR ATTACK ON IRAN AMID INCREASING THREATS FROM HEZBOLLAH AND IRAN-BACKED FORCES
🚨 US Army convoy, including THAAD systems, is moving around Be'er Sheva, Central Israel. The convoy also includes fuel tankers and generators.
💥 Intense Israeli airstrikes target the southern suburbs of Beirut, including a strike on the main entrance of Al-Manar TV headquarters, affiliated with Hezbollah.
🔴 Israeli military spokesman Hagari stated, "We have drawn up attack plans targeting every place in the Middle East that poses a threat to us."
🔴 An Israeli security official revealed to the Israeli Broadcasting Authority that Israel is preparing for a major attack on Iran and is ready to repel any subsequent Iranian responses.
💩 Iranian military sources to "Tasnim" News Agency warned, "Our finger is on the trigger, and the biggest surprise awaits the Israelis." They added that if Israel attacks military or nuclear sites, Iran's response would be "certain and beyond Israeli expectations," potentially leading Iran to reconsider its nuclear policies.
❗️ Donald Trump reportedly told Netanyahu, regarding a strike on Iran, "You do what you have to do."
⭕ The IDF confirmed that a drone launched from Iraq towards Israel was shot down over Syria before entering Israeli airspace. The drone was intercepted without any sirens being sounded. The Iran-backed Islamic Resistance in Iraq claimed responsibility for the drone attack on a target in the Golan Heights.
Source: t.me
#Israel#October 7#HamasMassacre#Israel/HamasWar#IDF#Gaza#Palestinians#Realtime Israel#Hezbollah#Lebanon
15 notes
·
View notes
Note
Hi! Saw your Data flow posts, and just asking to check if I've understood correctly: is the issue here (I'm some of the examples you mentioned about a project not working because they had discounted something, for instance) what's succinctly represented in the xkcd Dependency?
https://xkcd.com/2347/
Just so folk don't have to follow the link - here is the xkcd
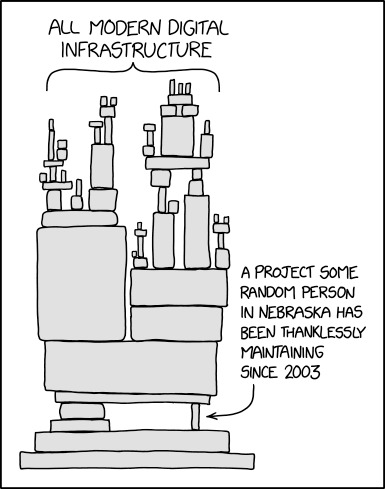
So this is a great example of a dependency, something that's vital to a single or multiple other processes or assets.
'Impact Analysis' is something that organisations need to do either to preempt something going wrong in order to build contingencies OR something that organisations need to be able to understand *when* something goes wrong.
But while the comic above is focused on modern digital infrastructure (which in the context I refer to Dataflow is more focused on Routers and Switches), it's worth noting that dependencies across organisations are a lot broader than that.
For example:
Person A needs to provide a report to person B so person B can do their job - That is a dependency
Person A needs to use App 1 to write the report but is dependent on the data from App 2 to actually write the report - That is also a dependency
Person A needs to use 'Laptop FW131' but spilled coffee over it at lunch and now it won't turn on - That is a dependency
Person A has found a back-up laptop 'Laptop FW132' but office WiFi is down because the finance department haven't paid the internet provider - Also a dependency
Seeing those examples, you might say, "But in that case, literally anything could be a dependency? What if Person A gets hit by a bus? What if the Laptop explodes and burns the building down?"
And yeah, that's absolutely the case. But if you do not understand the connections and dependencies between People, Business Processes and Technology Assets then you won't be able to ask the question in the first place. Which in an increasingly complex digital world is becoming much more important!
Hope that helps, any questions on the back of that please don't hesitate to ask because I live for this stuff.
197 notes
·
View notes
Text


From Firestorm Books, Asheville, NC.
We're four days into the most significant natural disaster in the recorded history of our region. Our community is experiencing an ongoing crisis created by infrastructural collapse and the profound failure of capitalism to value and sustain life. No state or federal aid has yet reached Asheville, but all around us we're seeing regular people acting autonomously to address immediate needs and meet one another with care. We hope to write soon about the beautiful and resourceful things we've witnessed.
Our co-op is physically intact and our members are accounted for. Although we've fared better than many, we're experiencing this crisis physically and emotionally. We're exhausted, largely without power, water, or internet. Cell service is poor, and when we are able to connect, the volume of information is overwhelming. Right now our priority is supporting and facilitating mutual aid efforts and we ask for your patience as we cannot keep up with emails, texts, and DMs.
Firestorm will continue to act as an in-person resource and information hub over the coming days, with staffing from noon to 4pm. A daily meeting at 2pm serves as a space for neighbors to get verified updates and coordinate mutual aid efforts. Other hubs have arisen organically in other parts of town and we're doing our best to share and connect resources.
If you would like to donate to grassroots recovery efforts, please send funds to our friends at @MutualAidDisasterRelief (bit.ly/donatemadr or Venmo @/MutualAidDisasterRelief), who are already on the ground, or local organizers (Venmo @/AppMedSolid or Cash App $Streets1de with "Flood Support" in the memo), who have been caring for our community 365 days/year.
We are not able to process web orders or ship inventory. If you'd like to support our co-op, we enthusiastically welcome book orders through our website, but please understand that we cannot provide an estimate on shipping.
#HurricaneHelene #MutualAid #Asheville #WesternNorthCarolina #FeministBookstore #QueerSouth #MutualAidDisasterRelief #FirestormCoop (- L)
#firestorm books#mutual aid#hurricane helene#climate crisis#hurricane relief#flood relief#Asheville floods#asheville#western north carolina#flooding#disaster relief#queer solidarity
9 notes
·
View notes
Text
You’re cheering a win — while gangrene spreads
Some of you are celebrating lawsuits against Midjourney, thinking they’ll restore the good old days of commissions and human-made fanart.
But let’s walk through how this really unfolds — for you.
🔍 1. Character Recognition Models Are Coming
Big IP holders already have extensive visual and text datasets of their characters.
It’s only a matter of time before they deploy detection models trained specifically to recognize deviations and unauthorized reinterpretations — from sexualization to gender-swaps.
📡 2. Platforms Will Be Forced to Integrate IP-Scanning APIs
No need to chase individual fanartists. Platforms will be required to connect to centralized scanning tools — designed and controlled by rights holders.
Upload an image → the API flags it → blocked or quietly deleted. No public drama, just silence. Or shadowban.
🧾 3. One Lawsuit Is All It Takes
Companies don’t need to send cease-and-desists to everyone. They target infrastructure.
Once a platform is legally pressured or threatened with deplatforming (remember Tumblr in 2018?), it will comply — automatically.
They won’t manually check if your blog is cute, transformative, or queer.
They’ll just press delete.
🖼️ 4. It Won’t Matter If It’s AI or Human
Once automated detection is in place, the question of who made the image becomes irrelevant.
If it looks like protected IP — it’s treated as infringement.
📉 5. The 2018 Tumblr Purge Was Just a Dress Rehearsal
When Apple removed Tumblr from the App Store over child exploitation concerns, the platform overreacted — purging thousands of blogs in a broad NSFW sweep.
No due process. No clear appeals. Just mass deletion.
Tumblr has done this before. And that was before AI.
🧠 And here’s the part you’re missing:
This isn’t just about AI art.
The same infrastructure that blocks machine-made fanart can — and will — block yours.
You’re not cheering for justice.
You’re cheering like a patient who’s glad their infected finger was cut off — not realizing the blood is already carrying sepsis to the lungs.
#anti ai#ai#pro ai#disney#midjourney#ai discussion#ai discourse#digital culture#copyright#fanart#fandom culture#artists on tumblr#creative freedom#ao3 writer#ao3 author#2018 tumblr#tumblr purge#important read
2 notes
·
View notes
Text
Major technology companies, including Google, Apple, and Discord, have been enabling people to quickly sign up to harmful “undress” websites, which use AI to remove clothes from real photos to make victims appear to be “nude” without their consent. More than a dozen of these deepfake websites have been using login buttons from the tech companies for months.
A WIRED analysis found 16 of the biggest so-called undress and “nudify” websites using the sign-in infrastructure from Google, Apple, Discord, Twitter, Patreon, and Line. This approach allows people to easily create accounts on the deepfake websites—offering them a veneer of credibility—before they pay for credits and generate images.
While bots and websites that create nonconsensual intimate images of women and girls have existed for years, the number has increased with the introduction of generative AI. This kind of “undress” abuse is alarmingly widespread, with teenage boys allegedly creating images of their classmates. Tech companies have been slow to deal with the scale of the issues, critics say, with the websites appearing highly in search results, paid advertisements promoting them on social media, and apps showing up in app stores.
“This is a continuation of a trend that normalizes sexual violence against women and girls by Big Tech,” says Adam Dodge, a lawyer and founder of EndTAB (Ending Technology-Enabled Abuse). “Sign-in APIs are tools of convenience. We should never be making sexual violence an act of convenience,” he says. “We should be putting up walls around the access to these apps, and instead we're giving people a drawbridge.”
The sign-in tools analyzed by WIRED, which are deployed through APIs and common authentication methods, allow people to use existing accounts to join the deepfake websites. Google’s login system appeared on 16 websites, Discord’s appeared on 13, and Apple’s on six. X’s button was on three websites, with Patreon and messaging service Line’s both appearing on the same two websites.
WIRED is not naming the websites, since they enable abuse. Several are part of wider networks and owned by the same individuals or companies. The login systems have been used despite the tech companies broadly having rules that state developers cannot use their services in ways that would enable harm, harassment, or invade people’s privacy.
After being contacted by WIRED, spokespeople for Discord and Apple said they have removed the developer accounts connected to their websites. Google said it will take action against developers when it finds its terms have been violated. Patreon said it prohibits accounts that allow explicit imagery to be created, and Line confirmed it is investigating but said it could not comment on specific websites. X did not reply to a request for comment about the way its systems are being used.
In the hours after Jud Hoffman, Discord vice president of trust and safety, told WIRED it had terminated the websites’ access to its APIs for violating its developer policy, one of the undress websites posted in a Telegram channel that authorization via Discord was “temporarily unavailable” and claimed it was trying to restore access. That undress service did not respond to WIRED’s request for comment about its operations.
Rapid Expansion
Since deepfake technology emerged toward the end of 2017, the number of nonconsensual intimate videos and images being created has grown exponentially. While videos are harder to produce, the creation of images using “undress” or “nudify” websites and apps has become commonplace.
“We must be clear that this is not innovation, this is sexual abuse,” says David Chiu, San Francisco’s city attorney, who recently opened a lawsuit against undress and nudify websites and their creators. Chiu says the 16 websites his office’s lawsuit focuses on have had around 200 million visits in the first six months of this year alone. “These websites are engaged in horrific exploitation of women and girls around the globe. These images are used to bully, humiliate, and threaten women and girls,” Chiu alleges.
The undress websites operate as businesses, often running in the shadows—proactively providing very few details about who owns them or how they operate. Websites run by the same people often look similar and use nearly identical terms and conditions. Some offer more than a dozen different languages, demonstrating the worldwide nature of the problem. Some Telegram channels linked to the websites have tens of thousands of members each.
The websites are also under constant development: They frequently post about new features they are producing—with one claiming their AI can customize how women’s bodies look and allow “uploads from Instagram.” The websites generally charge people to generate images and can run affiliate schemes to encourage people to share them; some have pooled together into a collective to create their own cryptocurrency that could be used to pay for images.
A person identifying themself as Alexander August and the CEO of one of the websites, responded to WIRED, saying they “understand and acknowledge the concerns regarding the potential misuse of our technology.” The person claims the website has put in place various safety mechanisms to prevent images of minors being created. “We are committed to taking social responsibility and are open to collaborating with official bodies to enhance transparency, safety, and reliability in our services,” they wrote in an email.
The tech company logins are often presented when someone tries to sign up to the site or clicks on buttons to try generating images. It is unclear how many people will have used the login methods, and most websites also allow people to create accounts with just their email address. However, of the websites reviewed, the majority had implemented the sign-in APIs of more than one technology company, with Sign-In With Google being the most widely used. When this option is clicked, prompts from the Google system say the website will get people’s name, email addresses, language preferences, and profile picture.
Google’s sign-in system also reveals some information about the developer accounts linked to a website. For example, four websites are linked to one Gmail account; another six websites are linked to another. “In order to use Sign in with Google, developers must agree to our Terms of Service, which prohibits the promotion of sexually explicit content as well as behavior or content that defames or harasses others,” says a Google spokesperson, adding that “appropriate action” will be taken if these terms are broken.
Other tech companies that had sign-in systems being used said they have banned accounts after being contacted by WIRED.
Hoffman from Discord says that as well as taking action on the websites flagged by WIRED, the company will “continue to address other websites we become aware of that violate our policies.” Apple spokesperson Shane Bauer says it has terminated multiple developer’s licenses with Apple, and that Sign In With Apple will no longer work on their websites. Adiya Taylor, corporate communications lead at Patreon, says it prohibits accounts that allow or fund access to external tools that can produce adult materials or explicit imagery. “We will take action on any works or accounts on Patreon that are found to be in violation of our Community Guidelines.”
As well as the login systems, several of the websites displayed the logos of Mastercard or Visa, implying they can possibly be used to pay for their services. Visa did not respond to WIRED’s request for comment, while a Mastercard spokesperson says “purchases of nonconsensual deepfake content are not allowed on our network,” and that it takes action when it detects or is made aware of any instances.
On multiple occasions, tech companies and payment providers have taken action against AI services allowing people to generate nonconsensual images or video after media reports about their activities. Clare McGlynn, a professor of law at Durham University who has expertise in the legal regulation of pornography and sexual violence and abuse online, says Big Tech platforms are enabling the growth of undress websites and similar websites by not proactively taking action against them.
“What is concerning is that these are the most basic of security steps and moderation that are missing or not being enforced,” McGlynn says of the sign-in systems being used, adding that it is “wholly inadequate” for companies to react when journalists or campaigners highlight how their rules are being easily dodged. “It is evident that they simply do not care, despite their rhetoric,” McGlynn says. “Otherwise they would have taken these most simple steps to reduce access.”
23 notes
·
View notes
Text
Smart Ecosystems, Smarter Apps: MeshTek’s IoT Innovation Engine

Experience the future of connected infrastructure with MeshTek’s cutting-edge IoT app development solutions. From smart cities to automated industries, our platform turns real-time data into actionable intelligence. Designed to scale, optimized for control, and built for performance—MeshTek ( IOT APP DEVELOPMENT COMPANY )empowers seamless connectivity across environments through robust, user-centric mobile applications.
#MeshTek#IoT App Development Company#Smart Infrastructure#IoT Solutions#Bluetooth Mesh#Smart City Technology#Industrial IoT#IoT App Development#Connected Devices#Mesh Networking#Smart Automation#Mobile IoT Apps#IoT Innovation#Scalable IoT#Edge Computing#Smart Lighting#MeshTek Technology#IoT Connectivity#AI Enabled IoT#Smart Industries
1 note
·
View note