#document security
Explore tagged Tumblr posts
Text
Thank you, everyone! Surprise: It’s happening! Our book is coming out. Letterlocking: The Hidden History of the Letter by Jana Dambrogio, Daniel Starza Smith, with the Unlocking History Research Group. Publication date: March 4, 2025. Publisher: The MIT Press. 320 pp, 8x9 inches, 261 color illustration. Hardcover ISBN: 9780262049276, $40.00. Pre-order @mitpress @penguinrandomhouse @amazon @barnesandnoble @bookshop_org @Indiebound @indigo @booksamillion.
Description The rich history of a centuries-old document security technology—folding and securing a letter into its own envelope for delivery—and a comprehensive guide to learning how to make your own locked letters. Before the invention of the gummed envelope in the 1830s, how did people secure their private letters? The answer is letterlocking—the ingenious process of folding, slitting, and securing a letter with a strip of paper and sealing wax so that it becomes its own envelope. The practice, used by historical figures ranging from Elizabeth I and her spymaster to Japanese samurai lords, and nearly entirely forgotten, was an everyday activity for centuries, across cultures, borders, and social classes. In Letterlocking, Jana Dambrogio and Daniel Starza Smith, experts who have pioneered the field over the last ten years, tell the fascinating story of letterlocking within epistolary history, drawing on real historical examples from all over the world. Letterlocking will be accompanied by a website, freely accessible scholarly articles, and instructional videos and diagrams, as well as foldable, tear-out sheets with instructions on how to fold and lock a letter.
Thank you, @barnesandnoble for offering a pre-order discount to your members April 19, on our book “Letterlocking: The Hidden History of the Letter” #BNPreorder
#mitpress #letterlocking #amsr #origami #documentsecurity #letters #correspondence #fold #diy #security #seal #secret #love #write #encryption #spies #invisible #teaching #instructions #book #publication #launch #video #share
https://www.barnesandnoble.com/w/letterlocking-jana-dambrogio/1145200759?ean=9780262049276
Alt text: A sparkling star made of magenta and yellow. In the center the date: March 4, 2025. Blue background with white lettering that says, "Letterlocking, The Hidden History of the Letter by Jana Dambrogio, Daniel Starza Smith, with the Unlocking History Research Group. Pre-order now @mitpress @penguinrandomhouse @amazon @barnesandnoble @bookshop_org @Indiebound @indigo @booksamillion
Thanks to Eirene Pianeta for sharing the gif design template in Canva.
Citation information: Authors: Jana Dambrogio and the Unlocking History Research Group. Title: "Surprise: It's Happening! Letterlocking: The Hidden History of the Letter. Pub date: March 4, 2025, USA (2024))." Letterlocking Instructional Videos. Unlocking History number 6261/Letterlocking Unique Video number: 0304. Date filmed: April 19, 2024. Duration: 1:52. Date posted: April 19, 2024. Video URL: [Insert URL]. Date accessed: [Date].
Copyright 2024. Jana Dambrogio and Massachusetts Institute of Technology (MIT). All rights reserved. The following copyrighted material is made available under the Creative Commons Attribution-NonCommercial 4.0 International (CC BY-NC 4.0) License https://creativecommons.org/licenses/by-nc/4.0/. Contact the MIT Technology Licensing Office for any other licensing inquiries.
To find out more about letterlocking, visit http://letterlocking.org and follow us on social media @letterlocking.
#MITPress#preservethefolds#letterlocking#document security#encryption#publication#ASMR#letters#letter writing#paper folding#origami#DIY
3 notes
·
View notes
Text
Mobile Notaries & Privacy: What You Need to Know

A mobile notary plays a critical role in handling sensitive documents, making confidentiality and security a top priority. Whether notarizing legal agreements, loan documents, or providing an apostille service, maintaining privacy is essential. Clients rely on notaries to protect their personal and financial information, making it crucial to follow strict security measures.
Read More: https://www.raismobilenotary.com/mobile-notaries-privacy-what-you-need-to-know
0 notes
Text
Document management software: automate workflows and minimize repetitive tasks
Document management software (DMS) is an important tool for organizations seeking to enhance their efficiency in storing, sharing, tracking, and managing documents electronically. With features like version control, workflow automation, and robust security, a DMS can transform how businesses operate.
Investing in document management software like PDQDocs is sure to revolutionize your business operations. This software will automate workflows and minimize repetitive tasks while enhancing productivity, improving compliance, and securing your files. Whether you're a solo practitioner or part of a small law firm, PDQDocs is the perfect solution for simplifying your document management needs.

Key Features and Benefits
Centralized Storage - DMS provides a secure and centralized repository for all documents that simplify the process of finding and accessing important files.
Version Control – It keeps track of different document versions effortlessly, allowing users to revert to previous versions when necessary.
Workflow Automation – It automates document-related processes such as routing for approvals or reviews. It saves time and reduces manual effort.
Enhanced Collaboration – It facilitates teamwork by enabling multiple users to access and work on documents simultaneously, improving overall productivity.
Improved Security - DMS offers advanced security features, including access controls and encryption so that sensitive documents are well-protected.
Search and Retrieval – It quickly locates documents using keywords, metadata, or other search criteria, making information retrieval efficient.
Compliance - It helps your organization meet regulatory requirements with audit trails and version histories that maintain accountability.
Why Choose PDQDocs?
PDQDocs is an innovative document management solution tailored for small businesses and legal professionals.
Streamlining Document Creation
It enables users to create unlimited document templates, allowing for customizations that meet specific needs. This flexibility ensures efficient and accurate documentation. All your documents will be managed in one place, your ultimate document management software.
Advanced Automation Features
The software automates the document generation process, significantly enhancing productivity. This means users can focus on strategic tasks rather than repetitive documentation.
Centralized Document Management
Managing multiple clients and projects are always overwhelming. It simplifies this with a centralized system for easy document storage, editing, and retrieval, including direct emailing from the platform. It has a centralized document storage system and users can easily store, edit, retrieve, and share documents.
User-Friendly Interface
Designed with simplicity in mind, it features an intuitive interface that minimizes the need for extensive training, allowing businesses to maximize benefits from day one. Whether drafting contracts, legal agreements, or essential documents, this Document automation software streamlines the process and reduces repetitive tasks with ease.
Ideal for Law Firms and Small Businesses
While beneficial for all small businesses, it is particularly suited for law firms. It meets the unique needs of solo practitioners and small firms by automating legal document creation, enhancing productivity, and reducing administrative burdens.
#document management software#document storage#digital document management#centralized document management#document retrieval#electronic document management#document security#compliance management#records management#document workflow automation#ultimate document management software#innovative desktop software for document generation#document generation software for small business#user friendly document generation software
0 notes
Text
How Can You Check Your Digital Document’s Authenticity?

The new normal, rise of remote and hybrid work models, and widespread penetration of the Internet have ushered in the digital era of documents. As more and more businesses and organizations are moving away from paper-based documents or digitizing their existing records, it’s necessary to check if the digital document you have is authentic.
Admittedly, a digital document is eco-friendly, costs less, and doesn’t require copious amounts of real estate to store unlike their paper contemporary, but they are vulnerable to targeted attacks. This means digital documents can be hacked, forged, and altered easily by someone who has the know-how and isn’t afraid to take risks.
In this scenario, it becomes difficult for you to decide if the document you have is original or a tampered version? Worse, what if the presented document digital is fake? Fortunately, there are several methods you can employ to check the authenticity of digital certificates, aka verifiable credentials.
What is a Digital Certificate?
Before we get into the methods you can use, it’s important to understand the meaning of a digital certificate. A digital certificate is similar to a regular digital document. The key difference is this document is hosted on the blockchain. It also follows the guidelines laid down in the Verifiable Credentials Data Model 1.0 by the World Wide Web Consortium (W3C).
Based on its association with blockchain and the data model rules, the document is tamper-proof, can be verified by machines, and uses privacy-enhancing technologies, like decentralized identifiers (DIDs). This is all well and good, but how can a digital certificate prove authenticity?
4 Ways You Can Check the Authenticity of Your Digital Documents
Here are the four ways you can check the authenticity of your digital documents:
1. Verify the Document’s Digital Signature
Digital documents are signed to authorize the information presented and help build trust in the document. Think of them as regular signatures, but more secure and binding. They use popular digital signature protocols like the DSA (digital signature algorithm).
That being said, this type of signature isn’t exempt from fraud. So, how can you verify the document’s digital signature? Look for two key elements in a digital signature to verify its authenticity, including:
Pairing of private and public keys: Since the digital signature certificate is hosted on a blockchain network, it uses public and private keys for signature. Basically, the issuer uses their private key to securely sign a verifiable credential, whereas the public key is shared with the holder or public (in case a lot of people need to access the secured document). Unless the public key matches the private key, no one can decrypt the encrypted message.
Hash code: When the issuer cryptographically signs a document using their private key, a hash code (containing letters and numbers) is generated based on the document’s content. Ultimately, this code is encrypted using the signer’s private key for the development of a digital signature.
These two elements are your guide to verifying the authenticity of your document. The first step is to match the public key with the private key. If a public and private key don’t match, that’s a definite red flag.
The other option is to compare the hash code. A receiver generates a new hash code for the received document when they decode it. This generated hash code should match the hash code generated during signature. If the code isn’t exactly the same, it could be indicative of a tampered and fake document.
2. Check the document’s metadata
A document’s data can often be found in its metadata (the data about data). The metadata will offer details regarding the document’s content, origin, history, and more. The data is your map to explore the hidden paths of the document and learn all about it. You just need to know where to look and be patient while going through the data.
To illustrate, if you want to check the document’s authenticity, you might want to check how it was created and dive deep into the licenses and rights of the document. So, to discover all this information about the document, you’d want to check its administrative metadata. You might also be interested in checking the location of where the document was created. If yes, look for the document’s geospatial metadata.
But if you are more curious about the document’s creator, keywords, its title, and more, you’d get your answers by exploring the descriptive metadata. Similarly, structural metadata will cover details on the document’s structure, like pages, sequence order, chapters, and more.
Simply put, all the data about the document is already there, you just need to exercise patience and go through it with a fine-toothed comb so you don’t leave any interesting crumbs behind.
3. Authenticate the document’s hash value
A document’s hash value is akin to its digital fingerprint. Just like no two fingerprints are the same, no two hash values are the same (though there might be some exceptions). This is mostly because a hash value, a fixed character string of letters and numbers, is generated solely based on the document’s contents.
When secured on the blockchain, the hash code is submitted on the network, too. This makes the hash value immortal. Here’s the kicker: Whenever someone makes a change to the document (think a change as miniscule as a grammar Nazi removing or adding a comma), its hash value changes inexplicably.
This property makes the hash value a game-changer in the world of document security. For instance, when you send a document to a receiver, you just need to provide the original hash value to the receiver. The recipient will then recalculate the document’s hash to ensure it matches the issuer’s. If it doesn’t it’s a clear indicator of a tampered document.
Most blockchain-based document security platforms use the SHA-256 (secure hash algorithm-256) to secure and tamper-proof documents.
4. Examine the document’s digital trail
A digital trail is akin to a document’s history. Think of this exercise as checking a Google Doc’s history. So, basically examining when the document was created and by who. Further, when and how it was edited and who contributed to the edits. This adds another layer of security to the document.
However, this feature isn’t available for all digital documents. This is mostly provided by blockchain security solutions, like ProofEasy, that want to build a digital fortress around all documents and ensure you know exactly what’s happening with your document.
Keeping track of the digital trail will help you stay on track and check if the document has been altered or tampered. It’s important to note that an original document stored on the blockchain can never be altered because whenever you edit it (even if you’re the issuer), a new hash value is created for the document.
So, you’ll always be in the know when a document is altered or tampered with. An absence of a digital trail will also help you identify fake documents and keep your business secure against fraudsters.
Generate Authentic Documents on ProofEasy
ProofEasy is a blockchain and QR code solution that helps secure existing documents and securely issue new documents. The best part, though? You’ll always be in charge of your documents. All you have to do is go to the unified dashboard to keep track of all your documents and manage them.
The cherry on top is the budget-friendly pricing of the solution. But you don’t have to commit to anything until you’re 100% ready. So, why don’t you take ProofEasy for a spin? Simply sign up on the platform to start your free trial. No credit card details are required.
0 notes
Text
Watching this again, it becomes incredibly clear in s3 that Nate is teaching Parker how to run her own crew. He fully anticipates that she will be his legacy, and more than anyone else---more than Sophie or Hardison, more than Eliot (though I would argue that Eliot never even slightly wanted it)---he is teaching her how to take over, think like he thinks and plan like he plans. He fumbles some of the emotional stuff, never actually tells her explicitly...but by the time you reach s3 he's clearly all-in. He's decided. Parker is going to be Nate 2.0, with different more exciting bugs than the 1.0 version.
#there's a handful of scenes in subsequent episodes where it's the two of them standing in the control room#and poring over schematics and documents#discussing between them how to move chess pieces around the board. it's subtle but it stands out.#(aftshadowing? I guess? not sure what foreshadowing is when the shadows didn't exist at the time.)#anyway I'm just fascinated by nate and parker. two people who are different in every way except#their weird. it vibrates at the same frequency.#they like art but mostly for non-artistic reasons. they think a lot about insurance plans and security systems.#they don't....really understand people except the 3-4 humans that are sometimes okay.#they both go weak the moment you introduce a child to the mix - but it also throws their alien strangeness in sharp relief.#anyway.#leverage
680 notes
·
View notes
Text
so I know a lot of star wars fics use flimsi or datapads to indicate when someone has a lot of work to do (piles of datapads, endless flimsiwork etc) and while all that is well and good, even today a lot of stuff is actually digital, and i imagine it would be even moreso in the future.
however with everything digital you would still need more screen space to be able to keep track of it, which is one of the reasons a lot of people have two monitors these days.
all that is to say: behold! fox's desk:

#star wars#star wars meta#tcw#tcw meta#commander fox#shitposting#this is definitely not a crucial plot point i am working with or anything#anyway my thoughts on that side of star wars worldbuilding#i can see maybe secure datapads being used for very important specific/confidential documents#but like why give someone a wholeass tablet when you can just send an email#'THIS DATAPAD COULD HAVE BEEN A SPEMAIL (space email)' - Fox probably
780 notes
·
View notes
Note
Kitty as someone in a government position whose division is currently in the middle of a multi-year project where we are migrating essential software from old and busted to new cloud version of same software I cannot express how seen your post made me feel. Especially as the youngest supervisor in the group I keep asking questions and just get “idk man that’s what we do” and I’m like “…shouldn’t you know why though? If you does someone know why this is done?” (The answer is no, no one knows why this is done)
yeah i left out the detail that i'm not corporate because of my concern that post would escape containment and context. but know that the details i changed were actually even more horrifying in their original form. like. realizing that this was what they'd been doing this whole time absolutely floored me with the implications.
the thing IS that this was just the upgrade from the old version of this company's software to the cloud software. we have another team helping us migrate from a different company onto theirs for actual financial software, which is taking longer.
BUT the migration team actually asks for our processes so they can map them better, and when we train they'll be doing it onsite from the ground up start to finish. with the upgrade team they started with the assumption that this would not be necessary because we already use their software. this was incorrect.
basically i think if any organization is using sufficiently dated software it's safe to assume that they have deviated significantly from best practices and even if you're 'just' doing an upgrade your training should start from zero instead of assuming any familiarity whatsoever. if they ask for feedback on the upgrade i will probably tell them this in as diplomatic terms as i can manage.
#original#boring work stuff#don't get me wrong part of it is that coworker doesn't want anyone to know how to do their job for job security#but i suspect another big part is that they don't want anyone to realize that they have never known what they're doing#we have a union. you have seniority. your job is so fucking safe. please can we get some documentation.#this is the best possible time to cop to ignorance to save face and relearn without baggage. they won't do it. but they should.
209 notes
·
View notes
Text
AND, THERE IT IS ;
Boxes are loaded onto Air Force One before President Donald Trump's departure at Joint Base Andrews, Maryland, on Friday, February 28, 2025. Luis M. Alvarez/AP
44 notes
·
View notes
Text
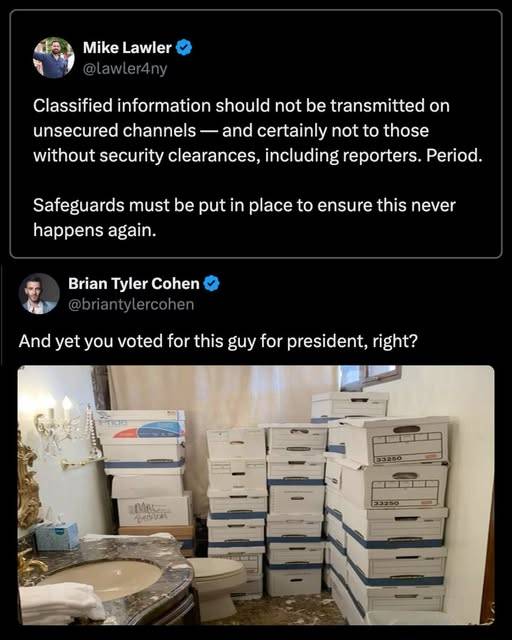
#security clearances#trump regime#christofascists#signal leak#atlantic magazine leak#atlantic magazine#us politics#boxes of documents just in the crapper at maralago
33 notes
·
View notes
Text
Vova, what did you do to deform the glasses?! 😅


#great now i cant stop thinking about him falling asleep with them#and thats why theyre deformed#Maks and Andriy finding him asleep on the table#documents as pillows and so exhausted he just fell asleep#they exchange on look and andriy helps maks to lift vova up#and while maks carries him to that little room and “bed” andriy puts vovas phone on plane mode#(of course he knows the passcode its the day of the first kiss with olena)#Maks carefully taking off the glasses and sighs when he sees theyre deformed#but hey at least vova wore them#or maybe vova cuddled to hard during movie date with olena#snuggled up cuddling as much as possible while watching a movie#when olena hears his deep breaths and sees he fell asleep#his face pressed into her half neck half upper body#and olena carefully removing the glasses and pulling the blanket over him#wrapping her arms around him to keep him close and give him a feeling of security
20 notes
·
View notes
Text
Privacy and confidentiality are critical when dealing with legal documents. A mobile notary helps maintain the integrity of your personal information by offering services directly at your preferred location. This approach reduces the exposure of sensitive documents in public settings, ensuring that your legal matters are handled discreetly and securely.
0 notes
Text
Why Your Business Needs Centralized Document Management Software: Discover PDQ Docs
In the digital age, businesses face an ever-growing need to manage an increasing volume of documents and data. From contracts and invoices to internal memos and client files, organizing and storing these documents efficiently is crucial for maintaining smooth operations. This is where centralized document management software, such as PDQ Docs, can make a significant difference. By offering a centralized system for storing and managing documents, PDQ Docs can help businesses reduce inefficiencies, enhance collaboration, and improve security.
Key Benefits of PDQ Docs as Centralized Document Management Software
PDQ Docs provides several features that make it an ideal choice for businesses seeking to improve their document management processes. One of the primary advantages of using centralized document management software like PDQ Docs is its advanced search functionality. Employees can find any document within seconds, even if it’s buried deep within a large archive. With powerful filtering and keyword search options, PDQ Docs ensures that no time is wasted on manual searches, allowing teams to stay focused on their core tasks.
Another benefit of PDQ Docs is its secure storage system. The software employs encryption protocols to protect sensitive information, ensuring that only authorized users can access specific documents. With the rise in cybersecurity threats, securing company data has never been more critical. PDQ Docs gives businesses peace of mind, knowing that their files are safe from unauthorized access or loss.
Furthermore, PDQ Docs promotes seamless collaboration. In a modern workplace, team members often need to work together on documents regardless of their location. PDQ Docs allows multiple users to access and edit documents simultaneously, fostering real-time collaboration among teams. This feature is particularly useful for businesses with remote or hybrid workforces, as it allows employees to stay connected and productive even when they aren’t in the same office.
How PDQ Docs Improves Efficiency Across Teams
Implementing centralized document management software like PDQ Docs has a direct impact on the efficiency of a business. By centralizing all files into one platform, the need for redundant document versions is eliminated. With PDQ Docs’ version control features, users can track changes, view previous versions, and ensure that everyone is working on the most up-to-date version of a document.
In addition to improving efficiency, PDQ Docs also simplifies compliance management. For businesses in regulated industries, such as healthcare or finance, keeping accurate records is vital. PDQ Docs helps ensure that documents are stored and tracked in accordance with industry standards, reducing the risk of compliance violations.
Conclusion: Why PDQ Docs is Essential for Your Business
In conclusion, centralized document management software like PDQ Docs is an essential tool for modern businesses looking to stay competitive and organized. By centralizing all your documents in one secure, easy-to-use platform, PDQ Docs improves access, collaboration, security, and compliance. Whether you’re a small business or a large enterprise, investing in PDQ Docs can significantly improve the efficiency of your document management processes, ultimately saving you time and money while boosting productivity.
#centralized document management software#document collaboration#file version control#document security#electronic document management#workflow automation#document indexing#digital document organization#document archiving#secure file management#document access control
0 notes
Text
Why Document Verification Matters? ProofEasy To Share Insights & Solutions For It At GITEX

Today, our world is driven by digital transformation, shaping every aspect of our lives. But in this digital era, the need for reliable document verification has never been more critical.
Whether in education or healthcare, the authenticity of documents can mean the difference between success and failure. Document verification is just another element to ensure document security.
That's why, at the GITEX Global 2023 event, ProofEasy is set to take center stage, offering valuable insights and innovative solutions for tackling the challenges of document verification.
The Significance of Document Verification
Document verification plays a pivotal role in ensuring the integrity of various sectors. Here we focus on two prime industries of our society - education and healthcare, where verification of documents is far more superior than one could imagine.
Education
Credential Verification
Document verification ensures the authenticity of educational credentials such as degrees, diplomas, and transcripts.
It prevents admission of students based on fraudulent documents, maintaining the integrity of educational institutions.
Preventing Academic Fraud
Counterfeit degrees and diplomas have become a growing concern, making document verification essential.
It helps in curbing academic fraud and maintaining the reputation of educational institutions.
Enabling Fair Opportunities
Document verification ensures that students and job seekers receive the opportunities they deserve based on their actual qualifications.
It levels the playing field by eliminating the advantage of those who use fake documents.
Data Security
Educational institutions handle vast amounts of sensitive student data.
Document verification helps protect this data from unauthorized access and potential breaches.
Healthcare
Patient Record Accuracy
In healthcare, document verification ensures the accuracy of patient records and medical history.
It reduces the risk of misdiagnosis and incorrect treatment plans.
Patient Identification
Correctly identifying patients is crucial to avoid medication errors and ensure the right treatment is administered.
Document verification aids in accurate patient identification.
Data Privacy and Security
Healthcare providers deal with sensitive patient data, making data security paramount.
Document verification controls access to patient records, enhancing data privacy.
Compliance and Regulations
Healthcare is subject to strict regulations and compliance requirements.
Document verification helps organizations adhere to these regulations, reducing legal risks.
Preventing Medical Identity Theft
Document verification is essential to prevent medical identity theft, where someone uses another person's information for fraudulent medical care.
It safeguards patients from financial and medical consequences.
These points highlight the critical role that document verification plays in both education and healthcare, ensuring trust, accuracy, and security in these vital sectors.
ProofEasy's Document Verification Solutions
ProofEasy understands the critical role that document verification plays in these sectors and is committed to providing innovative solutions to address these challenges.
At GITEX Global 2023, ProofEasy will showcase its advanced document verification offerings. Their solutions leverage patented blockchain verification with unique QR code integration.
With ProofEasy, you can trust that documents are genuine and have not been tampered with.
Expert Insights and Tailored Solutions at GITEX Global 2023
GITEX Global 2023 promises to be a groundbreaking event, and ProofEasy is set to be at the forefront of discussions on document security and verification. Their team of experts will share invaluable insights into the evolving landscape of document verification, including emerging threats and trends.
Moreover, ProofEasy will showcase tailored solutions designed to address the unique challenges faced by educational institutions and healthcare providers.
So, what are you waiting for? Be sure to stop by Stand H3-A06, Hall 3 where ProofEasy will be stationed from October 15th to 18th, 2023 in Dubai Harbour.
#Document Security#exhibition#Verify Documents#Blockchain Verification#Expand North Star#Education#Healthcare
0 notes
Text
We've been married for six years.
I have finally gotten my legal name change completed.
#most of that was 'I'm bad at paperwork'#and 'life is tiring when will i have space to do this'#but there was also a healthy dose of 'this site says to do it this way and that you need documentation a b and c--#--but the clerk says i need document X but i need this document approved before I'm able to get document X and also i lost form C'#anyway I was told to do my social security card first but I couldn't use that to change the name on my license#and most other forms require your license as proof#except for HR at work which couldn’t use my license and needed my social
23 notes
·
View notes
Text
Contingency Plans
Tobirama pulls a Batman and has, in a secure location, detailed plans on what to do if various members of the village go rogue. This includes weaknesses, strategies, last resort measures - the works.
In his own folder, under the "weaknesses" section is just a photo of Izuna winking ;P
#tobiizu#fanfic idea#he did actually have something there#Izuna broke in got past his security and stole the relevant document#that doesn't mean Izuna's contribution is any less accurate#just less complicated
50 notes
·
View notes
Text
I keep hearing dawko talk about a fallfest (in the 70s era) game to explain the mysteries sotm made about it but I don't think there's nearly enough mysteries to make a full blown 70s fallfest game about it. Fiona dying at fallfest can be solved and explained with one newspaper on the ground
I obviously know that fallfest has been being teased for YEARS and they pushed it a lot in sotm but I think at this point it's pushing a future modern day fallfest setting. like I said the Fiona thing can be explained with one newspaper and fallfest is obviously big with how they've been teasing it but that's why I think it'll be in the future
like I think it's not crazy to assume they'll make the big climax finale location (because there isn't a modern day FNAF location set up right now with the pizzaplex out of commission, there's an empty space) a fallfest amusement park taking place in the 2030s, and it's the game where the mimic is the main villain and that's where it's story comes at its crux with Gregory and Vanessa going against it
since it would be on the same carnival grounds it was on decades ago there could be hidden secrets found around the huge map like the Fiona newspaper, MCM animatronics as continuity and Easter eggs since fallfest was pushed in sotm and connected to MCM, and og fazbear fallfest lore in environmental storytelling
this is the only kind of location that could be quote unquote "bigger" or "grander" than the pizzaplex and it'd by all means be awesome and super cool to see and also explain how fazbear ent is still up and running and doing fine even without the pizzaplex. the mimics story climax being at fallfest would connect that modern day game back to sotm just in that being a thing alone
and the secondary villain could easily be vanny!Cassie in this scenario with the main actual campaign being protaganist Gregory (+Vanessa and Freddy by proxy) trying to save Cassie from the mimic and prove his innocence to her after the elevator. then in that game they'd save Cassie and kill the mimic within that campaign at fallfest in a poetic way

just u can't forget this. the tagline of sotm was to understand the past to see the future. we're going back to the future now, sotm was in the past for the sake of understanding it (the mimic, Edwin etc). fallfest is something that doesn't need to be gone back to to understand. it can be history we LEARN in the future as the player
#bc im being so real any fallfest mystery shit ppl can talk about can easily be revealed and solved in environmental storytelling#in a game about something else#i obviously know fallfest is being pushed and teased#but i dont think we're going back to the past. i think all past lore we get from now on in games will be found documents#shit you find around that TELLS you history instead of showing it to you bc youre living it#pandas.txt#sotm spoilers#pre security breach 2#theory#thoughts#fallfest
10 notes
·
View notes