#encryption as a service
Explore tagged Tumblr posts
Text
UPDATE! REBLOG THIS VERSION!
#reaux speaks#zoom#terms of service#ai#artificial intelligence#privacy#safety#internet#end to end encryption#virtual#remote#black mirror#joan is awful#twitter#instagram#tiktok#meetings#therapy
23K notes
·
View notes
Note
i am so devastated by todays outcome. i am so sick to my stomach. this has me so heartbroken. i don’t know what to say or do. i know this is so stupid, all things considered, but i am genuinely scared they will take tumblr/ao3 away. fanfic/fandom is such a safe space for me. i am at a loss. you and so many others have changed my life on here. please know i love you and your work. i know there are more pressing things, i just had to get this off my chest. i hope they don’t care enough to take it, but i fear they will.
oh man
i dont think its silly you're worried about that. im sure u know there are bigger fish to fry but sometimes its those kind of losses that weigh on you a lot and i dont blame you. and with the whole anti porn thing a lot of conservatives r trying to push i think its a valid concern
i dont want to feed you empty platitudes about what will be okay and what wont. but i do have confidence in the fact that we will get through this and that there is perhaps no time better than now that people will want to come together and make things and find joy and that hope will persevere even over persecution.
i love you too and i love everyone here and i love that there is a place like this for us. it will be okay regardless but. its a good reminder to continuing being kind to each other for things we might take for granted right now like access
#return to sender#i know people are going to see this ask in a certain way but i do understand#its not necessarily even these things but like. a certain worry about censorship that has been prevalent for a long time#i think itll be fine though genuinely#but i do encourage everyone to start using a vpn sooner rather than later and also speaking through encrypted messaging services if you can
24 notes
·
View notes
Text

#best SSL certificate providers for free#SSL (Secure Sockets Layer)#Importance of SSL certificate for your website#SSL certificate#free SSL certificate providers#best SSL provider#Let's Encrypt#SSL for Free#GoDaddy#GoGetSSL#Bluehost#Website Security Certificate#Free SSL certificate#Liveblack#ssl service provider#ssl certificate providers#top SSL certificate providers
2 notes
·
View notes
Text
most of you are too young to know this but 10-15 years ago it was a common refrain that you couldn't really trust signal or that it was a CIA plot.
2 notes
·
View notes
Text
That fighting game with the transgender nun girl unfortunately fucking sucks
#'the US was correct to try to criminalize encryption in the 90s and 00s in order to give the military a monopoly upon it' ok man#also i think multiple playable characters are secret service agents? why#i think the whitehouse is a magical spaceship?#and there's a guy who's Bishounen Dr Doom or something. which annoys me for several other reasons
13 notes
·
View notes
Text

In this article, we’ll explore how skill-based IVR call routing can In this article, we’ll explore how skill-based IVR call routing can improve customer satisfaction and improve platforms cloud industry. Learn More...
#cloud technology#unified communications#hotel pbx#hotel hospitality#hotel phone system#phonesuite voiceware#hotel telephone system#voiceware#voice services#hotel phone#encrypted voip#ip telephony#benefits of voip#IVR#ivr solution#ivr system#ivr services#hotel phone installation#phonesuite pbx
3 notes
·
View notes
Text
oh i forgot to tell yall i got foxy grandpas number + email address lmao
#he told me if i email him im supposed to call him by his code name (he gave that to me as well#and he wants me to use a certain encrypted email service that i forgot lmaoooo#im getting into something
4 notes
·
View notes
Text
lmaoo i could probably pass the cc exam without even taking the course
4 notes
·
View notes
Text
Another approach is to use Git. No, seriously, I know it's like a programmer thing, but it works for all text files and can technically work for xml based files like Word also.
If you're not confident on using a command prompt, check out Github Desktop. Contrary to the name you don't have to put repositories it makes online (and if you do they don't have to be public).
Git is helpful because all those versions of files don't remain visible in one folder, you always just see the most recent version. Past versions exist in the commit history, and you can. Roll back to specific versions, branch off from them, all that good stuff.
REMEMBER: WHEN YOU'RE WORKING ON A PIECE OF WRITING, NEVER DELETE ANYTHING
Ok, so you have a big paper due in July. You make a folder for the project called "Big Paper." You get to work, and save a file titled "PaperTopic.doc" in that folder.
You go back to your draft the next day. DO NOT simply open "PaperTopic.doc" and start editing/adding/revising. You are going to make a folder titled "Paper Versions." You are going to make a copy of "PaperTopic.doc." You are going to move it into the "Paper Versions" Folder.
Then you are going to go back to the original "PaperTopic.doc," and rename it "PaperTopic 5.14.24.doc." And you're going to repeat this EVERY DAY that you work on this project. Soon the "Paper Versions" will look like this:
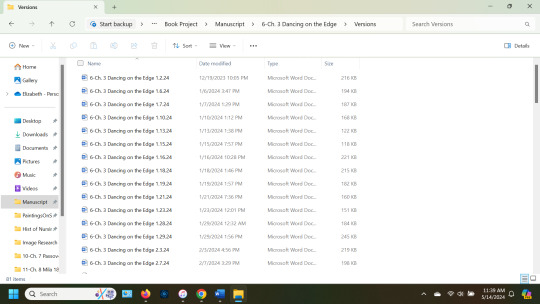
I post about this every 6 months or so, and I will continue to do so; because one day, it WILL save your ass. You're welcome.
Also, back it up to an external hard drive at least once a week.
#writing#writers#creative writing#also please please make backups!!!#they dont have to be in a cloud service#but if you want the peace of mind of cloud stuff without them spying on you consider putting your backups on cloud platforms in password#protected zip files. those are encrypted so Google or whoever wont be able to peek at them#i personally use a free tier Oracle Cloud server as my “house fire” level backup but ik thats not practical for most#remember that backups living on the same device arent really backups at all#since your whole hard drive could fail#and a bad power surge could take out all the drives in your computer#stay safe yall!
2K notes
·
View notes
Text
OpenDrive https://www.opendrive.com/zero-knowledge-encryption stands “a cut above the rest” offering the Zero-Knowledge Encryption option with the Secure Files Folder, which is available to all premium (paid) users.
0 notes
Text
Column-Level Encryption: A Must-Have for Financial Institutions in 2025
In 2025’s fast-paced financial landscape, protecting sensitive data is critical. With increasing cyber threats and regulatory pressures, column-level encryption has emerged as a precise and powerful solution. Unlike full-database encryption, this method encrypts only specific data columns—such as credit card details or PII—offering both security and efficiency.
What is Column-Level Encryption?
Column-level encryption secures sensitive database fields, ensuring that only authorized users can access them—even if other parts of the database are compromised. This method reduces processing load and improves performance.
0 notes
Text
Top 7 Reasons Your Business Needs Email Security Now

In today’s digital-first environment, email is more than just a communication tool—it’s a gateway to your business. While it’s indispensable for daily operations, it’s also one of the most exploited vectors for cyberattacks. From phishing scams to ransomware, threats are increasingly sophisticated and damaging. Without robust email security, your business is vulnerable to data breaches, financial losses, and reputational harm.
If you've been putting off upgrading your email defenses, here are the top 7 reasons why your business needs email security now, before it's too late.
1. Phishing Attacks Are on the Rise
Phishing is no longer a crude scam easily spotted by spelling errors or sketchy links. Modern phishing emails are highly targeted (spear phishing) and often mimic trusted brands, suppliers, or even colleagues. According to Verizon’s Data Breach Investigations Report, over 90% of cyberattacks begin with a phishing email.
These attacks are designed to trick employees into revealing credentials, making payments, or downloading malware. Email security solutions use AI and threat intelligence to detect and block these emails before they reach inboxes, significantly reducing your risk.
Key takeaway: Even tech-savvy employees can fall for well-crafted phishing emails. Email security solutions provide an essential layer of automated defense.
2. Prevent Financial Loss and Business Disruption
Cybercriminals don’t just want data—they want money. Business Email Compromise (BEC) scams, where attackers impersonate executives or vendors to trick employees into transferring funds, cost businesses billions annually.
And it’s not just direct fraud. Malware-laden attachments or malicious links can disrupt operations, lock files through ransomware, and cost thousands (or millions) to resolve. The downtime from a successful attack can cripple small to mid-sized businesses.
A strong email security system not only scans for known threats but also uses behavioral analysis to flag suspicious requests or activities.
Key takeaway: Email-based attacks can cause major financial and operational damage. Proactive security saves money and protects business continuity.
3. Protect Your Brand and Customer Trust
Customers, partners, and suppliers expect your business to keep their data safe. A single compromised email could lead to a data breach that exposes sensitive client information, and once trust is lost, it’s hard to regain.
Imagine a scenario where attackers use your domain to send phishing emails to your customers. This not only harms them but also damages your brand’s credibility. Email security systems with features like DMARC, DKIM, and SPF help prevent spoofing and impersonation by ensuring only verified senders can use your domain.
Key takeaway: Email security protects not just your internal systems, but your external reputation.
4. Ensure Regulatory Compliance
Whether you operate in finance, healthcare, e-commerce, or any industry handling personal data, regulatory compliance is non-negotiable. Regulations such as GDPR, HIPAA, and PCI-DSS require organizations to implement reasonable security measures, including for email communications.
Failing to secure your email systems could result in hefty fines and legal repercussions. Many email security solutions offer compliance features like encryption, data loss prevention (DLP), and audit trails to help you stay aligned with legal requirements.
Key takeaway: Email security helps you meet industry regulations and avoid costly compliance penalties.
5. Support a Remote and Hybrid Workforce
With the rise of remote work, employees are accessing emails from home networks, personal devices, and public Wi-Fi, creating more entry points for attackers. In many cases, the company’s internal firewall offers no protection once the employee is outside the office environment.
Cloud-based email security solutions protect users wherever they are. Whether it’s on a laptop, mobile device, or tablet, emails are scanned in real-time, ensuring threats are blocked before they’re opened.
Key takeaway: Email security needs to follow your workforce, not just your office network.
6. Stop Spam and Boost Productivity
Annoying as it may seem, spam is more than just a nuisance. It clogs inboxes, distracts employees, and can often carry hidden threats. Time wasted sorting through irrelevant or harmful emails adds up, hurting productivity across your organization.
Email security platforms come with robust spam filters that drastically reduce the volume of unwanted messages, allowing your team to focus on what matters. Advanced solutions even adapt over time to recognize evolving spam tactics and adjust filters automatically.
Key takeaway: Cleaner inboxes mean higher efficiency and lower risk.
7. Stay Ahead with Threat Intelligence and AI
Cyber threats are constantly evolving, and yesterday’s defenses won’t stop today’s attacks. Modern email security tools use machine learning, artificial intelligence, and threat intelligence feeds to detect even zero-day exploits and advanced persistent threats (APTs).
These systems learn from global data patterns, flagging suspicious emails even if they haven’t been seen before. The result? Real-time protection that gets smarter over time.
Some platforms also offer dashboards, alerts, and analytics, giving your IT team insights into attack trends and vulnerabilities.
Key takeaway: AI-powered email security is essential for staying ahead of fast-moving cyber threats.
Bonus: Why Built-In Email Filters Aren’t Enough
Many businesses rely solely on built-in filters provided by email services like Microsoft Office 365 or Gmail. While these offer a basic level of protection, they’re not tailored for business-grade security. They often miss advanced threats, lack DLP capabilities, and don’t provide compliance-specific features.
Standalone or integrated third-party email security solutions offer deeper visibility, better threat detection, and comprehensive control. For businesses that can’t afford a breach, upgrading is a smart move.
Key takeaway: Default filters are a start, but not a strategy.
Final Thoughts
Email is at the heart of business communication—and that’s exactly why it’s a prime target for cybercriminals. Ignoring email security is like leaving your front door wide open in a dangerous neighborhood. From financial loss to reputational damage and compliance risks, the consequences of an unsecured email system can be devastating.
Implementing a modern, AI-driven email security solution is one of the smartest and most cost-effective steps you can take to protect your business. Whether you’re a small startup or a growing enterprise, the time to act is now.
#email security#email security solutions#email security service#email encryption#cloud email security#email protection
0 notes
Text
Cybersecurity Considerations in Cloud-Based Estimating Service Platforms
Introduction The rapid adoption of cloud-based tools in industries like construction, manufacturing, and engineering has revolutionized how businesses handle estimating services. Cloud-based estimating service platforms provide immense benefits, such as accessibility, collaboration, and real-time updates, which help companies improve efficiency and reduce costs. However, the increased use of these platforms also raises significant cybersecurity concerns. Protecting sensitive data, ensuring platform reliability, and maintaining secure access are all critical components of ensuring the success of cloud-based estimating services.
This article will explore the cybersecurity considerations that organizations must take into account when utilizing cloud-based estimating services. We will highlight the importance of robust security measures, best practices for mitigating risks, and the role of the cloud service provider in safeguarding data.
Understanding the Cybersecurity Risks in Cloud-Based Estimating Services Cloud-based estimating services store vast amounts of sensitive information, including cost estimates, project budgets, pricing data, and contract details. This data is crucial for project planning, and its loss or theft could result in financial, legal, or reputational damage. The cybersecurity risks in cloud platforms include data breaches, unauthorized access, data manipulation, and service outages that can disrupt operations.
Hackers and cybercriminals may target cloud-based estimating services to access proprietary cost data, sensitive client information, or intellectual property. This makes cloud security a critical concern for businesses that rely on these services. Additionally, the remote nature of cloud access increases the potential for data exposure, especially if users access the platform from unsecured devices or networks.
Choosing a Secure Cloud Service Provider One of the first steps in ensuring cybersecurity for cloud-based estimating services is selecting a reliable cloud service provider (CSP) that prioritizes security. Reputable CSPs offer advanced security features, including end-to-end encryption, multi-factor authentication (MFA), and continuous monitoring of their networks. They should also comply with industry standards and regulations, such as the General Data Protection Regulation (GDPR) or the Health Insurance Portability and Accountability Act (HIPAA), depending on the industry.
Before selecting a CSP, organizations should thoroughly evaluate the provider’s security protocols, certifications, and track record. It’s also important to assess the provider’s ability to scale security measures as your business grows. A strong partnership with a reputable provider ensures that security is embedded into the platform from the ground up.
Data Encryption and Secure Storage Data encryption is one of the most effective measures for securing sensitive information in cloud-based estimating platforms. By encrypting data both during transmission and at rest, companies can ensure that even if hackers intercept the data, they cannot access or misuse it.
In addition to encryption, secure storage practices are crucial for protecting estimating data. Cloud service providers should store data in secure data centers equipped with physical security measures, such as biometric access controls, surveillance, and disaster recovery plans. These physical and digital safeguards help protect against both cyber threats and natural disasters.
User Access Control and Authentication Controlling user access is another essential aspect of cybersecurity in cloud-based estimating services. Businesses must establish strict user access protocols to ensure that only authorized personnel can access sensitive project data and cost estimates. This includes defining user roles, limiting permissions, and requiring strong authentication methods.
Multi-factor authentication (MFA) is a powerful tool for enhancing access security. By requiring users to provide additional verification, such as a code sent to their mobile device, alongside their username and password, MFA ensures that only legitimate users can access the platform.
Organizations should also regularly review and update user access permissions to ensure that former employees or contractors do not retain access to sensitive information after their engagement ends.
Data Backup and Disaster Recovery Plans Data loss is a major risk for businesses relying on cloud-based estimating services. Whether due to a cyber attack, natural disaster, or technical failure, losing critical estimating data can severely disrupt project timelines and budget management. Therefore, having a solid data backup and disaster recovery plan is crucial.
Cloud-based platforms should offer automated data backups to prevent loss of estimates and other project information. It is important for businesses to regularly test their backup systems and ensure that data can be quickly recovered in the event of an incident. The disaster recovery plan should also outline clear steps for restoring access to the platform, rebuilding project estimates, and ensuring continuity of operations.
Monitoring and Incident Response Continuous monitoring of the cloud environment is essential for detecting potential security threats. Cloud service providers should implement real-time threat detection systems to identify unusual activities, such as unauthorized access attempts or unusual data transfers. Monitoring tools can also track user behaviors, alert administrators about security anomalies, and provide insights into potential vulnerabilities.
In addition to monitoring, businesses should have a clear incident response plan in place. This plan outlines the steps to take in the event of a cyberattack, such as isolating affected systems, notifying affected parties, and coordinating with cybersecurity experts. A well-defined response plan helps minimize the impact of a security breach and ensures that the organization can recover quickly.
Employee Training and Security Awareness Even with the best technology in place, human error remains one of the largest cybersecurity risks. Employees who are unaware of security best practices may inadvertently compromise data by clicking on phishing emails, using weak passwords, or accessing the platform from unsecured devices.
To mitigate this risk, organizations should provide regular cybersecurity training to all employees who use cloud-based estimating services. Training should cover topics such as identifying phishing attempts, using strong and unique passwords, and securing devices. A culture of cybersecurity awareness helps reduce the chances of a successful attack and empowers employees to play an active role in protecting company data.
Compliance and Regulatory Requirements Depending on the industry, businesses using cloud-based estimating services must comply with various regulations related to data security and privacy. For instance, the construction industry may need to adhere to data protection laws, while healthcare-related estimating services might be subject to HIPAA regulations.
Cloud service providers should be transparent about their compliance with these regulations, and businesses should ensure that they understand their obligations when using cloud-based platforms. By partnering with a provider that meets the required compliance standards, companies can avoid legal and financial penalties while safeguarding their data.
Conclusion As cloud-based estimating services become increasingly integral to project planning and execution, securing sensitive data and protecting against cybersecurity threats are paramount concerns. Organizations must take proactive measures, such as selecting reputable service providers, implementing data encryption, controlling user access, and creating robust backup and disaster recovery plans. With a focus on cybersecurity, companies can confidently leverage cloud-based estimating services while minimizing the risk of data breaches and service disruptions.
By investing in the right security tools, maintaining ongoing monitoring, and ensuring employee awareness, businesses can strengthen the cybersecurity of their cloud-based estimating platforms and protect the valuable data that drives their projects forward.
#Estimating Service#cybersecurity#cloud-based platforms#data encryption#user access control#multi-factor authentication#cloud security#disaster recovery#data backup#incident response#project estimating#estimating tools#secure storage#data protection#compliance#security measures#cybersecurity best practices#project budgeting#risk management#phishing prevention#employee training#cloud service provider#threat detection#construction estimating#privacy regulations#disaster recovery planning#data breaches#system monitoring#project security#secure access
0 notes
Text
5 Reasons Why a VPN with Advanced Encryption is Essential for Online Security
In today’s digital age, online security and privacy are more important than ever. With an increasing number of cyber threats, data breaches, and surveillance systems, safeguarding your personal information is a necessity. One of the most effective ways to ensure online security is by using a VPN with advanced encryption. A Virtual Private Network (VPN) is an essential tool for protecting your data, securing your privacy, and preventing unauthorized access while browsing the web. But not all VPNs are created equal. To truly enhance your security, you need a VPN with robust encryption protocols. A nordvpn voucher provides users with discounts or special offers on NordVPN's premium subscription plans. By using a voucher, you can enjoy top-tier online privacy and security services at a lower cost, making NordVPN more accessible for everyone.
In this blog post, explore 5 reasons why a VPN with advanced encryption is essential for online security and how it helps protect you in a variety of ways, from safe browsing to anonymous online activity. Also look at some of the best advanced VPNs for online privacy and security to help you choose the right solution for your needs.
1. Protects Your Data from Hackers
The most critical reason to use a high-security VPN with military-grade encryption is to protect your data from hackers. Cybercriminals often target users on unsecured networks, such as public Wi-Fi hotspots, where data is more vulnerable. Without encryption, sensitive information like passwords, credit card numbers, and personal messages can easily be intercepted.
A VPN with advanced encryption protocols for secure data transmission ensures that your internet traffic is encrypted, making it impossible for hackers to access your private information. When you use a secure VPN for privacy and data protection in 2025, all your online activities are shielded from malicious attacks. This is particularly important if you often use public Wi-Fi or connect to networks you don’t trust. With military-grade encryption, even the most advanced hackers will be unable to break through your protection.
Key benefit: Prevents hackers from intercepting and stealing your sensitive data.
2. Keeps Your Online Activities Private
Another significant advantage of using a VPN with advanced encryption protocols is that it shields your online activities from being tracked or monitored by third parties, including internet service providers (ISPs), governments, and advertisers. Without encryption, your internet traffic is visible to anyone with access to the network, and this can lead to unwanted surveillance and data collection.
A VPN with military-grade security for avoiding online surveillance masks your online identity and makes it difficult for third parties to track your activities. By using encryption, your browsing history, search queries, and even your location remain private. This is essential if you value your privacy and don’t want your online movements to be exposed to anyone who might be watching.
Key benefit: Ensures complete privacy by encrypting your online activities.
3. Secures Sensitive Data During Online Transactions
Every time you make an online purchase, conduct a banking transaction, or log into an online account, you are sharing sensitive personal information. Without encryption, this data can be exposed to attackers, leading to identity theft, financial fraud, or other malicious activities. By using the best advanced VPN for online privacy and security, you can be sure that your personal and financial data is always protected.
A VPN with advanced encryption protocols for secure data transmission ensures that any data you send over the internet, including login credentials, payment details, and personal messages, is encrypted and secure. This means that even if hackers attempt to intercept the transmission, they will not be able to decode the data. Whether you’re shopping online or managing your bank account, a high-security VPN offers peace of mind.
Key benefit: Safeguards your sensitive financial and personal information during online transactions.
4. Prevents Online Tracking and Profiling
One of the most pervasive problems online today is the constant tracking of your activities. Websites and advertisers use tracking cookies and other methods to collect data on your browsing habits, interests, and personal preferences. This information is then used to target you with personalized ads or sold to third parties.
By using a secure VPN for privacy and data protection in 2025, you can bypass tracking systems and prevent companies from profiling you based on your online behavior. When you connect to a high-tech VPN for privacy and security on public Wi-Fi networks, your real IP address is hidden, and your internet traffic is encrypted, making it difficult for advertisers and websites to monitor or track your activity.
A VPN with advanced encryption protocols for secure data transmission also ensures that your browsing history is erased, preventing third parties from building a detailed profile of you. This is an essential feature if you want to maintain control over your personal data and avoid invasive online marketing tactics.
Key benefit: Stops websites and advertisers from tracking your online activity.
5. Bypasses Geo-Restrictions and Accesses Restricted Content
Another critical reason why a VPN with advanced encryption is so important is that it allows you to access geo-restricted content and unblock websites that may be restricted in your region. Many services, like streaming platforms (Netflix, Hulu, BBC iPlayer, etc.), apply geo-blocking to restrict content access based on your geographical location.
By using a fast and secure VPN service for accessing geo-restricted content, you can virtually change your location and access content from any part of the world. With next-gen VPN solutions for total anonymity online, you can browse the internet as if you were in a different country, enjoying unrestricted access to websites, services, and media.
Additionally, the fastest VPN service with low latency for gaming and streaming ensures that your streaming and browsing experience remains smooth without any buffering or lag, even when accessing content from other countries.
Key benefit: Unblocks geo-restricted content and ensures smooth streaming and gaming.
FAQs: Best VPN
Q1: What is the best VPN with advanced encryption for online privacy?
A1: Some of the best VPNs with advanced encryption for privacy include NordVPN, ExpressVPN, and CyberGhost. These services use military-grade encryption to protect your data and offer features like secure browsing, geo-unblocking, and anti-tracking.
Q2: How does a VPN with advanced encryption protect my data?
A2: A VPN with advanced encryption encrypts your internet traffic, making it unreadable to anyone trying to intercept it, such as hackers or government surveillance agencies. It ensures that your personal information and browsing activities remain private.
Q3: Can a VPN help me unblock geo-restricted content?
A3: Yes, a VPN can help you bypass geo-restrictions by allowing you to connect to a server in a different location. This makes it appear as if you're browsing from another country, enabling access to content that may be restricted in your region.
Q4: Are there any free VPNs with military-grade encryption?
A4: While there are some free VPNs available, most free services don’t offer military-grade encryption or the same level of security as paid VPNs. To ensure the highest level of protection, it’s recommended to use a premium VPN service.
Conclusion
In an age where cyber threats, data breaches, and online surveillance are commonplace, using a VPN with advanced encryption has become essential for ensuring online security and privacy. Whether you want to protect your personal data from hackers, prevent online tracking, or access geo-restricted content, a VPN can provide the solution.
Here’s a quick recap of why you need a VPN with advanced encryption:
Protects your data from hackers by encrypting internet traffic.
Keeps your online activities private and prevents surveillance.
Secures sensitive data during online transactions, ensuring your information stays safe.
Prevents online tracking and profiling by advertisers and third parties.
Bypasses geo-restrictions and allows access to restricted content and websites.
To experience the full benefits of online privacy and security, consider opting for a high-security VPN with military-grade encryption. Some of the best advanced VPNs for online privacy and security available today include ExpressVPN, NordVPN, and CyberGhost, which offer robust encryption protocols and excellent features for online protection.
A VPN with advanced encryption is a crucial tool for anyone looking to enhance their online security and privacy. Whether you’re browsing the web, making online transactions, or streaming content, a VPN helps keep your data safe and your identity anonymous. Make sure to choose a VPN that offers strong encryption, reliable performance, and excellent security features to protect yourself online.

#vpn#Advanced VPN Encryption#best vpn#vpn service#free vpn#nord vpn#Online Security#Best VPN for Privacy#VPN for Safe Browsing#VPN for Streaming#VPN for Gaming#Secure VPN for 2025#VPN for Public Wi-Fi Security
0 notes
Text
Privacy Enhancing Technologies (PETs): The Future of Secure Data Management-Tejasvi Addagada
Data privacy has become an very important for businesses, governments, and individuals alike. With the increasing volume of personal and sensitive information being collected, the need for robust privacy enhancing technologies (PETs) has never been greater. These technologies help organizations balance data privacy, security, and utility, ensuring compliance with data protection laws while enabling innovative uses of data.
In this article, we will explore what privacy enhancing technologies (PETs) are, their emerging trends, their role in data risk management in financial services, and how they integrate into data management services in Mumbai, India and beyond.
What Are Privacy Enhancing Technologies (PETs)?
Privacy enhancing technologies (PETs) refer to a set of tools, techniques, and approaches designed to protect personal data while allowing organizations to extract value from it. PETs enable businesses to process data securely, ensuring confidentiality, anonymity, and compliance with data protection regulations such as GDPR and CCPA.
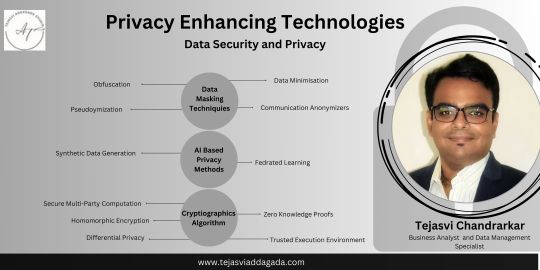
Key Features of PETs:
Data Minimization: Reducing the amount of personal data collected or shared.
Secure Data Processing: Enabling computation on encrypted or anonymized data.
User Anonymity: Protecting individual identities while allowing data analysis.
Data Access Control: Ensuring only authorized parties can use data.
PETs are crucial for organizations that handle large-scale personal information, such as those in financial services, healthcare, and digital marketing.
Emerging Privacy Enhancing Technologies
As technology evolves, several cutting-edge privacy enhancing technologies (PETs) are emerging to address data security and privacy concerns.
Federated Learning : Federated learning enables machine learning models to be trained across multiple decentralized devices or servers without exchanging raw data. This technique is widely used in sectors such as healthcare and finance, where data privacy is paramount.
Homomorphic Encryption: This encryption method allows computations to be performed on encrypted data without decrypting it first, ensuring that sensitive information remains protected during processing.
Differential Privacy: A statistical technique that introduces random noise into datasets, preventing individual data points from being traced while still allowing for useful data analysis.
Secure Multi-Party Computation (SMPC): SMPC enables multiple parties to collaboratively analyze data without revealing their individual inputs, ensuring privacy and security.
Synthetic Data Generation: Using data quality generative AI, synthetic data is created to mimic real-world datasets while eliminating privacy risks, making it ideal for testing and research.
These innovations are helping businesses strengthen their data privacy strategies while enabling new applications of data-driven decision-making.
What is Data Privacy, and Why is it Important?
Data privacy refers to the protection of personal information from unauthorized access, use, or disclosure. It ensures that individuals maintain control over their data while organizations adhere to regulatory standards.
Why Data Privacy Matters?
Legal Compliance: Regulations like GDPR and CCPA mandate strict data privacy measures.
Consumer Trust: Businesses that prioritize data privacy build stronger customer relationships.
Data Security: Prevents unauthorized data breaches and cyber threats.
Competitive Advantage: Organizations that uphold strong privacy policies gain an edge over competitors.
By integrating privacy enhancing technologies (PETs), businesses can reinforce their data privacy efforts while unlocking new opportunities for data-driven innovation.
Evaluating Privacy Enhancing Technologies for Organizations
For businesses looking to implement privacy enhancing technologies (PETs), evaluating the right solutions is essential.
Key Considerations for Implementing PETs:
Compliance Requirements: Does the technology align with regulatory frameworks like GDPR?
Data Sensitivity: What type of data is being processed, and how critical is its protection?
Integration Capability: Can the PET be seamlessly integrated into existing data management systems?
Performance Impact: Does the technology affect processing speed or system efficiency?
Cost and Scalability: Is the solution cost-effective and scalable for future growth?
Organizations in sectors such as banking and healthcare are increasingly investing in PETs as part of their data risk management in financial services strategy to protect sensitive financial and medical records.
How Can PETs Support Data Governance and Enable New, Innovative Uses of Data?
Effective corporate data governance relies on ensuring that data is used responsibly while maintaining security and compliance. Privacy enhancing technologies (PETs) play a vital role in strengthening governance frameworks by:
Enhancing Secure Data Sharing: PETs enable secure data collaboration across institutions without exposing sensitive information.
Enabling Ethical AI and Machine Learning: Data quality generative AI can analyze data while ensuring privacy, improving AI model accuracy.
Promoting Transparency: PETs support transparent and auditable data processing practices.
In industries like healthcare, PETs facilitate privacy-preserving research, allowing organizations to share patient data securely for medical advancements.
Primary Barriers and Enabling Factors in PET Adoption
While PETs offer substantial benefits, their adoption faces certain challenges.
Barriers to Adoption:
High Implementation Costs: Some PETs require significant investment in infrastructure and expertise.
Complex Integration: Integrating PETs with existing data management services in Mumbai, India, and other regions can be complex.
Regulatory Uncertainty: As privacy laws evolve, businesses may struggle to keep up with compliance requirements.
Enabling Factors for Adoption:
Growing Data Privacy Awareness: Organizations recognize the need for robust privacy measures.
Advancements in AI and Cloud Security: AI-driven PETs are making privacy protection more efficient.
Government and Industry Support: Initiatives promoting PET adoption encourage wider implementation
By addressing these barriers, businesses can leverage PETs more effectively for secure data governance.
Factoring PETs into Risk Assessment Frameworks
Organizations must integrate PETs into their data risk management in financial services and other industries to balance risks, harms, and benefits when handling personal data.
Risk-Benefit Assessment for PET Implementation:
Identify Potential Risks: Evaluate data exposure risks and compliance challenges.
Assess Technology Suitability: Determine which PETs align with business objectives.
Implement Continuous Monitoring: Regularly assess the effectiveness of PETs in mitigating risks. Develop Privacy Policies: Create clear guidelines for data handling and protection.
In financial services, PETs support fraud detection, secure transactions, and privacy-preserving credit assessments, ensuring regulatory compliance.
The Benefits of Privacy Enhancing Technologies (PETs)
The implementation of privacy enhancing technologies (PETs) brings numerous benefits to businesses, governments, and consumers.
Key Benefits of PETs:
Stronger Data Security: Prevents unauthorized data breaches and cyber attacks.
Regulatory Compliance: Ensures adherence to privacy laws and industry standards.
Improved Consumer Trust: Encourages customer confidence in data handling practices.
Enhanced Innovation: Enables secure data analytics and AI model training. Efficient Data Governance: Strengthens policies and processes for responsible data management.
Organizations investing in PETs can achieve a competitive advantage by ensuring data security without compromising business growth.
A Review of Tools, Techniques, and Scope of PETs
Various tools and techniques fall under the umbrella of privacy enhancing technologies (PETs), each with its own use case and scope.
Top PET Tools and Techniques:
Zero-Knowledge Proofs (ZKPs): Enables authentication without revealing sensitive information.
Blockchain for Privacy: Secure, decentralized data management and transactions.
AI-Driven Anonymization: Uses data quality generative AI to mask personal data.
Data Masking and Tokenization: Protects sensitive data during storage and processing.
As data privacy concerns grow, the demand for PETs will continue to rise, shaping the future of data management services in Mumbai, India, and beyond.
Conclusion
Privacy enhancing technologies (PETs) are transforming how businesses and organizations manage data privacy and security. By integrating PETs into their data governance and data risk management in financial services, companies can ensure regulatory compliance, enhance security, and unlock innovative data-driven solutions.
As industries continue to adopt privacy enhancing technologies (PETs), the future of data privacy will be defined by a balance between security, compliance, and technological advancement. Businesses that invest in PETs today will be better positioned to navigate the evolving landscape of digital privacy and data management. Also Read:

Understanding the Data Management Framework | Tejasvi Addagada
#tejasvi addagada#data management#data governance#privacy enhancing technologies#PETs#data risk management in financial services#data management services in Mumbai#GDPR and CCPA#Homomorphic Encryption#Mumbai#India#USA#Canada
0 notes
Text

In this blog post, we’ll explore some helpful tips on how to choose the right metrics and KPIs to properly track progress within your call and contact center operations. Learn More...
#call center#cloud voip#cloud technology#KPI#unified communications#ip telephony#hotel phone installation#cloud telephony#VoIP#cloud calling#voice services#hotel phone#voiceware#encrypt phone calls#phonesuite console#encrypted voip#voice traffic#phonesuite voiceware#hotel hospitality#hotel phone system#voip benefits#voip encryption#hospitality
2 notes
·
View notes