#firewalls
Explore tagged Tumblr posts
Text

my first introduction to firewall during my childhood
Tom and Jerry Tales | S1 E16 Digital Fireball
#genuinely i thought firewalls must exist like this inside the computer#computer science#computer network#computer security#computer forensics#firewalls#coding#cs#csblr#tom and jerry#tom and jerry tales#tom#jerry#i am talking
4 notes
·
View notes
Text
*push to panorama and device* *push to panorama and device* *push to panorama and device* *push to panorama and device* *push to panorama and device*
Get committed get committed get committed get committed ggrtcommitted get committed get committed
2 notes
·
View notes
Text
Network Security Essentials for IT Professionals

In our interconnected world, sadly, now even the tiniest business is heavily dependent on its networks. From smooth communications to critical data storage, the network serves as the spine of this present-day business. Hence, in the eyes of the IT professionals, network security is more than just a technical skill; it is a necessity, a daily task almost, to defend the organization from an ever-growing number of cyber threats.
We at TCCI - Tririd Computer Coaching Institute acknowledge the utmost importance of protecting one's digital assets. Regarded as one of the best computer training institutes in Ahmedabad, we help IT professionals gain knowledge and develop skills needed to erect the robust and secure network infrastructures. Let's explore the major principles and practices an IT professional should know.
Why Network Security is Non-Negotiable for IT Professionals
Cyberattacks have grown in their sophistication and are occurring more frequently. Be it data breaches, ransomware, DDoS attacks, or threats from within, these criminal actions disrupt normal operations, damage the company image, and cause enormous financial losses. For the IT professionals, an inadequate network security could lead to:
System Downtime: Disrupting the business operations.
Data Loss or Theft: Breaching sensitive information.
Reputational Damage: Wearing away customer and stakeholder confidence.
Compliance Penalties: Not conforming to regulatory requirements (e.g., GDPR, HIPAA).
Financial Costs: Reimbursement efforts, legal fees, and lost revenue.
Mastering the fundamentals of network security helps to curb such risks and maintain business continuity.
Fundamental Pillars of Network Security for IT Professionals
Building a resilient network defense requires a multi-layered approach. Here are the core essentials:
1. Firewalls: The First Line of Defense
Role: Firewalls maintain the boundaries between your internal network and other outside networks, such as the internet, and filter inbound-outbound traffic depending on the security parameters established.
Types: Get to know the types of firewalls: packet-filtering, stateful inspection, and NGFWs, which delve further into deep packet inspection and application control.
Implementation: Configure firewall rules so that they accept the necessary traffic only and discard any malicious attempts.
2. Virtual Private Network: Ensure Secure Remote Access
Role: Underneath an unsecured network (such as the internet), they form an encrypted tunnel that allows a remote user or branch office to access internal network resources in a secure fashion.
Importance: Protecting data from being compromised when employees access the internet from outside office perimeter makes it an imperative consideration in remote work cybersecurity.
Implementation: Install strong VPNs with the best encryption and authentication protocols.
3. Access Control: Who Gets In and What Can They Do?
Authentication: Verifying the identity of users (e.g., strong password, Multi-Factor Authentication (MFA), biometric). With an MFA system, access is denied even when passwords have been compromised.
Authorization: Authorizing authenticated users what they can do or see within their network according to their roles (Principle of Least Privilege).
Least Privilege: Granting access rights to users on a need-to-know basis to perform their job function.
4. Intrusion Detection/Prevention Systems (IDS/IPS): The Network Watchdogs
IDS: It examines network traffic and alerts suspicious activity or violations of policy to administrators.
IPS: Takes the next step toward prevention of threats by blocking them in real-time.
Importance: It is important because it detects and prevents network attacks that may circumvent the firewall.
5. Encryption: Protection against Data-In-Transit and At-Rest
Data-in-Transit: Being transmitted across a plane-of-I/O, this setting demands the use of SSL/TLS mechanisms to secure deployment of remote browser (HTTPS), SSH for secure remote access, and even VPNs for network-level transmission encryption.
Data-at-Rest: Encrypt all sensitive data that is stored anywhere-from servers, databases, down to individual devices (say, full-disk encryption).
Importance: Helps keep sensitive information confidential even when intercepted or accessed unlawfully.
6. Regular Patching & Updates: Getting Rid of Vulnerabilities
Role: Software vulnerabilities are the main point of entry for the attackers. By regularly patching the OS, the applications, and the network devices, these security holes are closed.
Process: Have a patch management procedure in place: scan for software vulnerabilities on a regular basis and apply security updates promptly.
7. Network Segmentation: Limiting Blast Radius
Role: Segment the large network into smaller isolated segments (for example, separate VLANs for various departments, for critical servers, and for IoT devices).
Benefit: When one segment faces compromise, the breach is limited within that segment, preventing lateral movement by attackers through the entire network.
8. Security Information and Event Management (SIEM): Centralized Intelligence
Purpose: The SIEM collects and aggregates log data from several security devices such as firewalls, servers, endpoints, anywhere in the network. Once data is gathered, it identifies security incidents or threats, alerting the concerned parties using AI and analytics.
Importance: It offers a centralized view of security events so that threats can be detected and responded to more quickly.
9. Employee Awareness & Training: The Human Firewall
Role: The most advanced security technologies won't stop attacks, if social engineering can trick an employee into unwittingly carrying out attacker's instructions. An employee can be tricked through phishing, for example.
Implementation: Conduct regular cybersecurity awareness training, phishing simulations, and adopt stringent security policies.
The Emerging Threat Landscape
Constant change is demanded from the IT expert. New threats--the ransomware variants more sophisticated than before, supply chain attacks, IoT vulnerabilities, and AI-powered attacks-give the impetus for continuous learning and being vigilant. Cloud security, mobile security, and container security have now also become other critical fronts of overall network defense.
Explore Our Network Security & Cybersecurity Courses at TCCI
Contact TCCI for IT Professional Training
Call us @ +91 98256 18292
Visit us @ http://tccicomputercoaching.com/
#Network Security#IT Security#Cybersecurity#IT Professionals#Data Protection#Firewalls#VPN#Access Control#Computer Classes#Ahmedabad#TCCI
0 notes
Text
#Fortinet#Cybersecurity#GartnerMagicQuadrant#NetworkSecurity#AI#Firewalls#Leadership#electronicsnews#technologynews
0 notes
Text
#PollTime
How do you secure your data best?
A) Encryption 🔏
B) Tokenization 🪙
C) VPN 🛡️
D) Firewalls 🔥
Comments your answer below👇
💻 Explore insights on the latest in #technology on our Blog Page 👉 https://simplelogic-it.com/blogs/
🚀 Ready for your next career move? Check out our #careers page for exciting opportunities 👉 https://simplelogic-it.com/careers/
#itcompany#dropcomment#manageditservices#itmanagedservices#data#dataservices#encryption#tokenuzation#vpn#firewalls#poll#polls#itserviceprovider#managedservices#testyourknowledge#makeitsimple#simplelogicit#simplelogic#makingitsimple#itservices#itconsulting
0 notes
Text

At The JMOR Connection, Inc., we are driven by a single mission: to provide exceptional, reliable technology solutions that keep your business and home systems running smoothly and efficiently. With over 31 years of experience, we understand the unique needs of both small businesses and discerning home users, offering cutting-edge technology and personalized services to solve complex IT challenges.
We believe that quality and integrity are at the heart of everything we do. We aren't just here to fix your IT problems--we are here to build long-term relationships by delivering innovative solutions that ensure the security, scalability, and reliability of your systems. Proactive and preventative measures are our focus to prevent downtime and cybersecurity threats, and we strive to make technology work seamlessly for you, whether at home or at the office.
Our team goes beyond offering technical expertise. We provide value by personalizing services to meet your specific goals, whether you're a business or a home user. We offer a variety of services that span from network security, cloud solutions, to IT support and more. We prioritize security and privacy, applying the latest practices in data protection and regulatory compliance to ensure the safety of your information.
While we may not be the cheapest, we don't compromise on quality. Our clients know that with us, they are receiving the best value and best service in the industry. By investing in us, you are investing in the future success of your technology needs.
We ask one simple question: Are you willing to sacrifice quality for price? At The JMOR Connection, Inc., we believe that quality technology solutions today will lead to a more efficient, secure, and successful tomorrow. We're here to help you grow with scalable, future-proof IT solutions--whether for your business or your home.
#wifi#technology#support#sled#server#phonesystem#networksercurity#networks#iphones#ipcameras#firewalls#Deployment#computers#antivirus
0 notes
Text
Did anyone ever got blocked by Sucuri Firewall, and then got scared believing it was a malware sign?
So. Anyway, today I tried to sign in to a site to get some help.
But then I got blocked from doing this by fucking Sucuri. A firewall/defense program I never heard of before.
And as you can imagine, I got scared, and though it was malware. But I checked online, and seen that some others had similar issues with what I had, with this program just.......blocking some people for random reasons. Including the users of that site. And so I calmed the fuck down.
Did anyone ever had some similar issues?
#false alarm#digital security#firewalls#I almost through this was malware#but that would be quite unlikely with what I saw
0 notes
Text
We Are Hiring
Are you a network professional with a passion for cybersecurity and Fortinet solutions? Join our growing team and take your career to the next level!
🔹 Role: Network Engineer 🔹 Skills: Fortinet SD-WAN, FortiGate Firewall 🔹 Certifications: NSE1, NSE2, NSE3 (NSES), NSE4 🔹 Experience: 8+ Years 🔹 Locations: Bangalore | Mysuru | Pune
We're looking for skilled engineers who can secure networks and build efficient infrastructures using Fortinet technologies. If you’re ready for your next challenge, we want to hear from you!
📧 Apply Now / DM us for more details!
Contact: +91 86906-43242 Visit: https://apthrtech.com/

#WeAreHiring#NetworkEngineer#FortinetJobs#CybersecurityCareers#FortiGate#FortinetSDWAN#NSE4Certified#ITJobsIndia#TechJobsBangalore#JobsInMysuru#JobsInPune#HiringNow#ITJobs2025#NetworkSecurity#Firewalls#SDWAN#JoinOurTeam
0 notes
Text
Inctel Technology: Elevating Network Security Hardware Solutions
In the ever-evolving Digital 3C industry, Inctel Technology stands out as a leading network security hardware supplier. With a commitment to innovation and quality, Inctel Technology provides top-notch solutions that empower businesses to safeguard their digital environments.
As cyber threats become more sophisticated, Inctel Technology's range of products is designed to meet the diverse needs of its clients. From advanced firewalls to robust intrusion detection systems, their offerings ensure that organizations can operate with confidence in their network security.
What sets Inctel Technology apart is not only their high-quality hardware but also their dedication to customer service. The team at Inctel works closely with clients to understand their unique challenges and deliver tailored solutions that enhance security and efficiency.
Inctel Technology is truly a beacon of reliability in the digital landscape, helping businesses thrive while protecting their valuable data.
#cyber threats#firewalls#hardware solutions#Digital 3C#data protection#intrusion detection systems#tailored solutions#innovation
1 note
·
View note
Text
Understanding Cybersecurity: Protecting Your Digital World
In today’s digitally connected world, have you ever stopped to wonder how secure your personal and professional data is? Have you heard terms like firewalls, phishing, or ransomware and thought, What do these mean for me or my business? If you’re unsure, you’re not alone. Cyber security is a critical yet often misunderstood aspect of our lives.
What is Cybersecurity? Cybersecurity refers to the practice of protecting systems, networks, and programs from digital attacks. These attacks are often designed to access, change, or destroy sensitive information, extort money, or disrupt normal business operations.
Why Does Cybersecurity Matter? In a world where digital transformation is accelerating, cybersecurity has become essential for individuals and organizations. Consider these statistics:
Every 39 seconds, a cyberattack occurs.
43% of cyberattacks target small businesses, which are often the least prepared.
Cybercrime is projected to cost the world $10.5 trillion annually by 2025.
The consequences of poor cybersecurity range from financial losses to irreparable damage to your reputation.
Common Cybersecurity Threats You Should Know About
Firewalls: Your Digital Gatekeepers A firewall is like the security guard of your digital network. It monitors and controls incoming and outgoing traffic, blocking unauthorized access while allowing legitimate communication. Think of it as the first line of defense against intruders.
Phishing: Don’t Take the Bait Phishing attacks occur when cybercriminals trick you into providing sensitive information, such as passwords or credit card details, by pretending to be a trustworthy source—often through emails, texts, or fake websites.
Ransomware: Your Data Held Hostage Ransomware is a type of malware that locks you out of your files or systems until you pay a ransom. Even if you pay, there’s no guarantee your data will be restored.
Zero-Day Exploits: Attacks on the Unknown These occur when attackers exploit a software vulnerability that hasn’t yet been identified or patched by developers.
Insider Threats: Danger Within Sometimes, the threat isn’t external. Employees or contractors with malicious intent or poor security practices can cause significant damage.
How Can You Protect Yourself and Your Business?
Educate Your Team Human error is a leading cause of security breaches. Conduct regular training to help your team recognize threats like phishing emails and social engineering tactics.
Implement Multi-Factor Authentication (MFA) Adding an extra layer of security, such as requiring a code sent to your phone along with your password, can thwart many attacks.
Keep Software Updated Regularly update your operating systems, applications, and security software to patch vulnerabilities.
Backup Data Regularly Ensure your data is backed up to an encrypted cloud service or offline storage. This minimizes the impact of ransomware or other attacks.
Adopt Advanced Cybersecurity Tools Use intrusion detection systems, endpoint protection, and encryption to secure sensitive data.
Partner with Cybersecurity Experts If managing cybersecurity feels overwhelming, consider partnering with experts who can provide ongoing monitoring and support.
The Future of Cybersecurity As technology evolves, so do cyber threats. Emerging technologies like artificial intelligence (AI) and quantum computing will bring both new opportunities and new challenges in the fight against cybercrime. Staying informed and proactive is key to keeping your systems and data safe.Final Thoughts Cybersecurity isn’t just an IT issue. It’s a business and personal priority. By understanding common threats and adopting robust security measures, you can protect yourself, your team, and your customers from the growing tide of cybercrime.
0 notes
Text
Effektives Risikomanagement in IT-Datenzentren: Strategien und Ansätze
In der heutigen digitalen Welt sind IT-Datenzentren das Rückgrat vieler Unternehmen. Sie speichern und verwalten kritische Informationen, die für den Geschäftsbetrieb unerlässlich sind. Aufgrund der steigenden Abhängigkeit von digitalen Infrastrukturen ist effektives Risikomanagement in diesen Einrichtungen unerlässlich. Ein gut durchdachtes Risikomanagement kann helfen, potenzielle Bedrohungen…
#Bedrohungsanalyse#Best Practice#Best Practices#Compliance#Cyberangriffe#Cyberbedrohungen#Cybersecurity#Firewalls#Führung#IT-Infrastruktur#IT-Sicherheit#Phishing#Risikoanalyse#Risikomanagement#Sicherheitsmaßnahmen#Sicherheitsvorfälle#Software-Updates
0 notes
Link
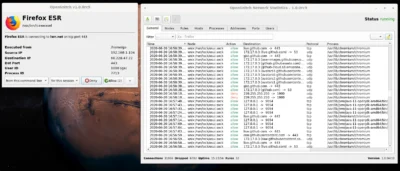
This is not a simple firewall to get started with as it can be a bit of an uphill battle to get all the outgoing connections vetted (if you want to filter those), but I’d imagine once set up, it is a pretty powerful tool to have.
Key features:
Interactive outbound connections filtering.
Block ads, trackers or malware domains system-wide.
Ability to configure system firewall from the GUI (nftables).
Configure input policy, allow inbound services, etc.
Manage multiple nodes from a centralized GUI.
SIEM integration
It is regularly updated, with 74 contributors contributing to over 30 releases. The project has also received over 10,000 starts.
See https://github.com/evilsocket/opensnitch
0 notes
Text
#TechKnowledge Do you know what is Firewall?
Swipe to uncover what it is!
👉 Follow us for more simple, useful tech tips!
💻 Explore insights on the latest in #technology on our Blog Page 👉 https://simplelogic-it.com/blogs/
🚀 Ready for your next career move? Check out our #careers page for exciting opportunities 👉 https://simplelogic-it.com/careers/
#techterms#technologyterms#techcommunity#techinsight#techtalk#knowledgeIispower#didyouknow#firewall#security#digitalsecurity#firewalls#hardware#software#cloud#cloudservices#internalnetwork#makeitsimple#simplelogicit#simplelogic#makingitsimple#itservices#itconsulting
0 notes
Text
Understanding the Difference Between 4G and 5G Networks
As our reliance on mobile connectivity grows, so does the need for faster, more efficient networks. Understanding the difference between 4G and 5G networks is crucial as 5G technology becomes more widely available, promising to revolutionise how we interact with the digital world. From browsing the web to powering autonomous vehicles and smart cities, 5G is set to offer significant advancements…
#4G#5G#5G applications#5G benefits#5G rollout#5G security#AI#AR#automation#autonomous vehicles#bandwidth#cell towers#cloud#Connected Devices#connectivity#cyber threats#data transfer#digital#download speed#emerging tech#encryption#firewalls#Healthcare#infrastructure#innovation#IoT#IT leaders#latency#low latency#Mobile
0 notes
Text
Servicios DNS, DHCP, FTP, web, correo y bases de datos en sistemas operativos

En el entorno actual, donde las redes y los servicios en línea son el corazón de cualquier organización, comprender y dominar la instalación y configuración de servicios críticos como DNS, DHCP, FTP, web, correo y bases de datos es fundamental. Estos servicios no solo facilitan la comunicación y la gestión de información, sino que son esenciales para garantizar el correcto funcionamiento de la infraestructura tecnológica de una empresa. Durante esta clase, no solo aprenderemos los aspectos técnicos de cada servicio, sino que también exploraremos la importancia de la gestión responsable, la ética en el manejo de datos y el valor de la perseverancia para resolver problemas técnicos que puedan surgir. Read the full article
#administraciónderedes#basesdedatos#configuracióndeservidores#configuraciónDHCP#configuraciónDNS#correoelectrónico#encriptacióndatos#éticaenredes#éticaredes#firewalls#gestióndatos#gestióndeseguridad.#gestióndeservidores#instalaciónFTP#permisosusuarios#proteccióndedatos#RedHat#redescorporativas#responsabilidadtécnica#seguridadinformática#seguridadredes#serviciosDNS#serviciosFTP#servidoresweb#Sistemasoperativos#sistemasoperativoscomerciales#WindowsServer
0 notes