#hash the cipher circuit
Explore tagged Tumblr posts
Text
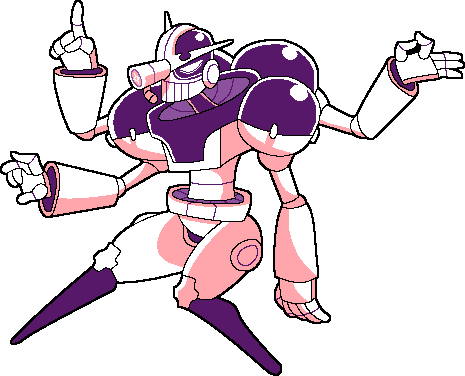
Hash, the Cipher Circuit is one of the characters I started this series for because I really wanted to draw him. He was a bit more complicated than I initially assumed but I'm really happy with how this turned out. He's one of the bosses from Gravity Circuit, a really fun game that is basically a melee focused Mega Man. And he's my favorite of said bosses! He's a hackerman with an awesome design and... Remarkably similar boss patterns to Yoku Man from Mega Man Unlimited. Huh. Well, his stage is a lot more tolerable than Yoku Man's at least, LOL.
Newgrounds
Character Art Series Masterpost
#gravity circuit#cipher circuit#hash#hash the cipher circuit#gravity circuit fanart#drawn by tc#art#character art series
7 notes
·
View notes
Text

Hello again tumblr
Play gravity circuit, now.
It's cool the gameplay is crisp, the controls are so responsive the combat is insane and so fluid and I can't say enoughhhhhh
Play
The
Game
Nowwwwwwwwwwww
Do itttttt
#art#my art#gravity circuit#Kai gravity circuit#Hash gravity circut#Ray gravity circuit#crash gravity circuit#break circuit#optic circuit#cipher circuit#robots#mecha#mecha art#indie games#paper art#pencil
21 notes
·
View notes
Video
tumblr
[Boss Introduction - 01] Name: Hash Designation: Cipher Circuit A brilliant, reclusive programmer. He is attempting to hack Guardian Corps' systems, while hiding away in "cyberspace".
54 notes
·
View notes
Text
Internet Security and VPN Network Design
This item discusses some essential technical thought associated with a VPN. A Virtual Private Network (VPN) integrates remote employees, company offices, and enterprises partners using the Internet and secures encrypted tunnels between locations. An Access VPN is used to connect remote exploiter to the undertaking network. The remote workstation or laptop will use an entrees circuit such as Cable, DSL or Wireless to connect to a local Internet Service Provider (ISP). With a client-initiated model, software on the remote workstation builds an encrypted tubes from the laptop to the ISP using IPSec, Layer 2 Tunneling Protocol (L2TP), or Point to Point Tunneling Protocol (PPTP). The user must authenticate as a permitted VPN exploiter with the ISP. Once that is finished, the ISP builds an encrypted tunnel to the business VPN router or concentrator. TACACS, RADIUS or Windows waiter will authenticate the remote exploiter as an employee that is allowed entrees to the enterprises network. With that finished, the remote user must then authenticate to the local Windows area server, Unix waiter or Mainframe multitude depending upon where there network explanations is located. The ISP initiated patterns is less secure than the client-initiated ideal since the encrypted subway is built from the ISP to the boldness VPN router or VPN concentrator only. As well the secure VPN pipe is built with L2TP or L2F.
The Extranet VPN evidence connect enterprise partners to a firm network by structure a secure VPN context from the business partner router to the firm VPN router or concentrator. The specific tunneling procedures utilized depends upon whether it is a router crossing or a remote dialup connection. The options for a router connected Extranet VPN are IPSec or Generic Routing Encapsulation (GRE). Dialup extranet connections will utilize L2TP or L2F. The Intranet VPN testament connect company offices across a secure context using the same direction with IPSec or GRE as the tunneling protocols. It is important to protocols that what type VPN's very gift effective and efficient is that they deportment the existing Internet for transporting boldness traffic. That is why many firm are pilfering IPSec as the security subroutine of choice for guaranteeing that information is secure as it travels between routers or laptop and router. IPSec is comprised of 3DES encryption, IKE key trick verification and MD5 route authentication, which provide authentication, siege and confidentiality.
Internet Protocol Security (IPSec)
IPSec achievement is worth noting since it such a prevalent guards subroutine utilized today with Virtual Private Networking. IPSec is specified with RFC 2401 and developed as an open prototypes for secure transport of IP across the public Internet. The packet composition is comprised of an IP header/IPSec header/Encapsulating Security Payload. IPSec provides encryption services with 3DES and verification with MD5. In addition there is Internet Key Exchange (IKE) and ISAKMP, which automate the dowry of mystery keys between IPSec nobleman trick (concentrators and routers). Those protocols are required for negotiating one-way or two-way defense associations. IPSec alertness union are comprised of an ciphering algorithm (3DES), hash algorithm (MD5) and an authentication office (MD5). Access VPN implementations utilize 3 defense confederation (SA) per context (transmit, receive and IKE). An undertaking network with lots IPSec companion scheme evidence utilize a Certificate Authority for scalability with the authentication tide instead of IKE/pre-shared keys.
For more please Visit : https://anonymster.com/
1 note
·
View note
Text
Week 6 Lectures
Never would I have thought that I would receive a lecture via a skype call... however this course continues to surprise me. Notes for this week’s lectures as per usual :) This week notes will be in their purest form: brain dribble.
Morning Lecture
WEP:
Needed a 64 bit key, but how do we get users to generate a 64 bit key. Was a lot to ask users to generate. Designers decided to generate the last 24 bits by themselves, using an IV.
Seed was different for each packet, 40 bit key that was shared and everyone used, and then the 24 bit value that was generated.
To decrypt, you get the 24 bit thing sent in the clear - (IV) and combine with the secret to get the 64 bit
Danger when someone transmits the same data under the same key - data is replicated in the same frame
Collision for IV - square root of 2^24 = 2^12 ~= 4000
Relatively small amount of packets needed to be sent before collision
Mixing data and control (key characteristic of attacks):
WEP attack - carrying out the normal function, can be abused by users to gain more control
I.e. Richard smuggling expensive express envelopes by hiding them in a satchel, posting them to himself
If there is a potential ambiguity in the channel and you are able to control how that is resolved - you gain control of the channel
Buffer Overflow:
Computer rapidly switches between jobs - “context switching” rather than concurrencyModern cpu’s use the notion of interruption Stack keeps track of what is being used
Latest process - top of the stack. When it’s finished, the information about the process gets thrown out, stack pointer gets moved down
After process have been re-awakened, need information about what the process is currently doing. This is stored in the disk, because RAM is expensive
Stack is also used to store local data about the program - much faster
Running program data is in the stack, as well as other frozen processes
Stack is stored backwards -> grows down
If can persuade the buffer you are writing to is bigger than it is - then you can be writing to other memory of the person that is asleep
Pointer to the next instruction about to be executed -> control
Contains other information
Write to the return address, overwrite the current thing
Proof of work:
Bitcoin - can’t counterfeit easily (work ratio)
No matter how good something is, every 18 months your attacker gains 1 bit of work due to Moore’s law i.e. lose one bit of security
Number of transistors per square inch on integrated circuits had doubled every year since the integrated circuit was invented.
Disk encryption:
Thread model - attacker has physical access to the disk, assume full control of the hard drive
Generate random key, encrypted version of the key stored in the disk
Evening Lecture:
Web Seminar
HTTP:
Application layer protocol used to send messages between browsers and web servers. HTTP requests go from the browser to the server.
Databases / SQL - browser sending an HTTP get request from the server with the username and password as data
Server queries database with “SELECT password FROM users WHERE match”
HTTP Cookies/Sessions
An HTTP cookie is a small piece of data sent in a response from a web server and stored on the user’s computer by the browser
A session cookies is a unique ID generated by the server and sent to the user when they first connect or login
Browser sends it with all HTTP requests
XSS - cross-site scripting is an attack in which an attacker injects data, such as a malicious program
Reflected XSS - occurs when user input is immediately returned by a web application.
Stored - you enter data which is stored within the application and then returned later
xss.game.appstop.com
SQL injection is a code injection technique in which malicious SQL statements are inserted into an entry field for execution.
Goal behind an SQL query is to gain access
‘ or 1 == 1 --
Blind SQL injections are identical to normal SQL Injection except that when an attacker attempts to exploit an application rather than getting a useful error message
Cross Site Request Forgery:
Attack on an authenticated user i,.e. Already logged in
When you log in to a website it sends you a cookie to your browser to keep you logged in.
Bank attack:
If attacker knows the format of the bank request, they can hide a transfer request inside an img using html
Cross Site Request Forgery Defences:
Primary mitigation is with tokens
Generate a suitably random token, store value server-side
Sent token to user, expect this token back as part of any user requests
In a GET request, this token will be appended to the URL
If a website has XSS vulnerabilities, CSRF mitigations are pointless
Crypto Seminar
Payment Process: Current versus Bitcoin:
Current payment systems require third-party intermediaries that often charge high processing fees
Machine-to-machine payment using the Bitcoin protocol allows for direct payment between individuals, as well as support micropayments -> reduce transaction costs
Crypto:
Built using cryptographic principles i.e. blockchain and hashing
Difficult to fake transactions - too many bits so it isn’t worth
Blockchain:
Method of storing data
A chain of chronologically linked blocks where each block is linked to the previous block
Blocks are unique - no two blocks will have the same hash
Data:
Consists of hundreds of transactions
Put around 2000 transactions in one block
Hashes:
Block’s hash summarises the data into a combination of letters and numbers
SHA-256 hashing algorithm
If a transaction in the block is changed, the hash is changed
This is important because each block has the hash of the previous block -> need to check against all previous blocks
Tamper evident
When a transaction is mine, it isn’t immediately added but placed in a transaction pool
The miner gathers enough to form a block - called a candidate block
Hash the block header along with a nonce
When we hash we hope the block hash value is below a certain target value
The nonce is a random number brute forced by miners to try and create the correct hash
When nonce is found, it is broadcast and the block is added to the existing chain
Proof of Stake:
Growth of mining pools could eventually lead back to a centralised system
PoW mining uses excessive amounts of electricity
PoS algorithm attributes mining power to proportion of total bitcoins held, rather than computing power
Rewards are transaction fees rather than new cryptocurrency
Types of crypto currencies:
Bitcoin
Uses the SHA-256 algorithm - very processor intensive and complex requires lots of dedicated hardware
Litecoin
More accessible for normal uses to mine on their CPUs as the algorithm used is less CPU intensive, but more memory intensive
Facebook Libra
Centralised architecture - libra will be managed by the Libra Association, having more control over the blockchain
There is no ‘mining” - to set up a node on Libra, need $10000
Privacy:
Blockchain doesn’t have a strong concept of identity (public, private) key pairing
Doesn’t exempt transaction from tracing
Two main ways:
Relations between address - inferring identity
Interactions between nodes and users
Monero:
Unlinkability -> stealth addresses with view keys
Transaction mixing -> ring signatures
Concealing transaction amounts -> RingCt signatures
Historical flaws:
51% attack:
Double-spend
Purpose might also be to discredit a crypto instead of money
Credibility decided on the majority
Off-springs created one’s solution for a hash is not added into their own spin-off
Motive might be to discredit the cryptocurrency
Past Attacks:
Usually happened on small networks
Verge 51% attack, on April 2018
Groups of hackers found two main flaws in the system:
Bug which lowered the hashing difficulty for a hashing algo (Scrypt)
Verge allowed 5 different hashing algorithms, and only the difficulty for Scrypt is lowered
Hacked 3 times over 2 weeks
Cryptocurrency exchanges:
Mt.Gox - bitcoin exchange that was launched in 2010. Handled over 70% of all Bitcoin transactions in 2013
Previous owner retained admin level user account when MtGox was sold in 2011
Attacker logged in to the account
Assigned himself a large number of BTC which he sold on the exchange
Price dropped immediately
Obtained private keys of MtGox clients
Created selling orders on these accounts and bought the BTC he stole
SQL Injection vulnerability was found
MtGox user database began circulating online and included:
Plain text email addresses
Usernames
MD5 Hashed passwords, with some unsalted
Future of Cryptocurrency:
Adoption
Overcoming resistance from:
People
Established finance institutes (eg banks)
Governments (they don’t like that you don’t pay tax by concurrency)
Ease of use
Volatility
Threats
Blockchain its laek
Quantum computers
To the sft that utilises cryptocurrency
Cryptocurrency wallet/exchange/
Strong private keys
Symmetric Ciphers
Two sorts of ciphers, symmetric and asymmetric -> regards the keys
If you know the key
For a symmetric: you can decrypt and encrypt
For an asymmetric: you have separate private and public keys to decrypt and encrypt (RSA)
Earthquakes:
How would I cope, how would my business cope? -> ‘gobag’
Home Study - read up about the “block modes” - only need to learn/understand ECB, CBC, CTR
Authentication:
Identifying for who? Computer/human?
Facebook. Police, baggage screening
Authentication and identification - what is the difference?
What decisions?
Computerised authentication system -> needs to make a decision about whether it is you or not
Factors:
Something that you have
Something that you know - i.e a password. Easy way of doing authentication
How do you know that you share the same secret?
Something that you are - Unfakeable
Two factor authentication:
Something that you have AND something that you know i.e. and password
All of these things seem different, but ultimately they are all just things that you know, and are all secrets
Something that you are can be replicated
Serious problem -> authenticating bombs, missiles etc
Biometrics - not real authentication, collecting another shared secret from a person, and can be bypassed
1 note
·
View note
Text

The new decoding chip sets a record of data transmission energy efficiency, and its power consumption is only 1~10% of that of similar products
A team of scientists led by the Massachusetts Institute of Technology has developed a decoder chip. The relevant research results were read out at the ongoing International Solid-state Circuit Conference.
The chip uses the general decoding algorithm developed by MIT before, and can decode any encoded signal. The decoding data is simpler and faster than traditional technology, and the energy consumption is only 1% to 10% of other similar hardware, or the performance is 10 to 100 times higher than other hardware. It can be widely used in the fields of virtual reality and 5G network that are demanding on power consumption.
Muriel M é standard, professor of software science and engineering at NEC and professor of electrical engineering and computer science, said, "This is the first time someone has broken through the decoding threshold of 1 pJ per bit. This is roughly the same as the energy you need to transmit 1 bit in the system. This is a significant symbolic threshold, but it also changes the balance of the receiver. From the perspective of energy, this may be the most urgent part - we can transfer it from the decoder to other parts".
In addition to M é standard, the co-authors of this paper also include Arslan Riaz, a graduate student of Boston University, Rabia Tugce Yazicigil, an assistant professor of electrical and computer engineering of Boston University, Ken R. Duffy, then director of the Hamilton Institute of Menus University and now professor of Northeastern University, and other scholars from Massachusetts Institute of Technology, Boston University and Menus University.
IT Home is a simple science popularization. The common data is transmitted in the form of bits (0 or 1), and the sender needs to encode the data and add error correction code at the end of the data. The error correction code mentioned here is also a redundant string composed of 0 and 1, which can be regarded as the information required for hash verification. This string of information is usually stored in a specific cipher book, and the decoding algorithm of the receiver is a verification scheme designed for this special cipher. It will retrieve the original information that may have been confused through a specific cipher book and hash structure. Generally, each algorithm is based on a specific code, and most algorithms require special hardware, so a device needs many chips to decode different data.
Researchers have previously demonstrated a general decoding algorithm that can crack any code - GRAND (Guess Random Additive Noise Decoding). Its working principle is to guess the noise that affects the transmission of information, and then directly eliminate the noise from the received data, and then check the remaining content in the cipher book. It will guess a series of noise patterns in the order of possible occurrence.
In fact, the data we receive usually contains reliability information, also known as soft information, which can help the decoder find out which parts are wrong.
It is reported that this new decoding chip is called ORBGRAND (Ordered Reliability Bits GRAND). It can use this soft information to sort data according to the possibility of error in each bit. But in fact, this is not as simple as sorting a single bit. Although the most unreliable part may be the most obvious mistake, the third and fourth unreliable parts together may be as wrong as the seventh part. ORBGRAND uses a new statistical model here, which can sort the bits in this way, because putting multiple bits together may cause errors as well as a single bit.
"If your car breaks down halfway, the soft information may tell you that it is the battery. But if it is not only the battery, for example, the battery and the engine have problems at the same time, it will be very troublesome," said M é standard. This is how a person who can think rationally - although it may be the two parts that break down together, you will start troubleshooting from the most prone place, and then look down, Finally, we can find something that is unlikely to happen. They believe that this is a more effective method than the traditional decoder. It is reported that the traditional decoder only focuses on the code structure, and it is usually designed for the worst case. "With the traditional decoder, you have to take out the design drawing of the car and check every part. Although you will find the problem eventually, it will take you a long time", explains M é standard.
It is reported that ORBGRAND will stop sorting as soon as a key code is found, which usually happens very quickly. In addition, the chip also adopts parallel logic, which can generate and test multiple noise modes at the same time, so as to find this key code faster.
When they compared this method with other chips, ORBGRAND only consumed 0.76 pJ of energy per bit when decoding with the highest accuracy, breaking the previous performance/energy consumption record. This also means that the energy consumption of ORBGRAND is only one tenth or even one percent of that of other devices.
M é standard said that one of the biggest challenges in developing chips is to reduce energy consumption. ORBGRAND is now so energy-efficient that other processes that researchers did not pay attention to before (such as checking the code words in the cipher book) consume most of their energy. "Now, the inspection process is like opening a car to see if it works. It is the most difficult part. Therefore, we need to find more effective ways to do this". The team is also exploring ways to change the transmission modulation so that they can use ORBGRAND chip to improve efficiency.
ICBROS TECHNOLOGY LIMITED is a worldwide professional electronic components distributor.
Our hot chip models today:
ACT4533AYH-T SOP-8 ACT364US-T 18 ACT2802QL-T1026 QFN24 ACT5805QI QFN32 ACT8865QI305-T QFN32 A33KY25 QFN40 ACT8600QJ162-T QFN40 ACT3704YH-T S0P ACT4012SH SOP ACT4065SH-T SOP8 ACT4060SH-T SOP8 ACT4070YH-T SOP8 ACT2803SH SOP8 ACT365SH-T SOP8 ACT4523AYH-T SOP8 ACT4060A SOP-8 ACT4096SH-T SOP-8 ACT4088US-T SOT23-6 TH608B3132 TO92-4 PAC5223QM TQFN48 ACT6358NH-T QFN ACT8332NDAER-T QFN ACT4050YH-T SOP8 ACT4523YH-T SOP8 ACT4529MYH-T1011 SOP8 ACT512EUS-T SOT23-6 ACT5807QJ-T QFN40 ACT6907UC330-T SOT23-5 ACT8780QLHCD-T QFN ACT6310UC-T SOT23-5 PAC5250QF QFN ACT8945AQJ305-T VQFN40 CST32501QF QFN57 ACT6702UC180-T SOT23-5 ACT6311UC SOT23-5 ACT8601QJ318-T QFN ACT8870QJ302-T QFN ACT8931AQJ633-T QFN40 ACT8942QJ133-T QFN40 ACT6906UCADJ-T SOT23-5 AC39LV040-70RPC DIP 39LV040-70 DIP AC39LV080-70RFEC TSOP40 AC39LV800-90REC TSSOP48 AC39LV088-90REC TSSOP48 ACT4060ASH SOP8 ACT4060 SOP-8 AV3005-A BGA AV1103 BGA AQ6928A BGA AQ6928 BGA BF2012-N2R4NBAT/LF SMD AT8010-E2R9HAAT/LF SMD BF1005-K2R4DAAT/LF 0402C BF2520-E2R4CAET/LF 2520 FB2520-07E2R4BT/LF 2520C FB2520-10E2R4AT/LF 2520L AT5020-B2R8HAAT/LF SMD BL1608-10K2450T/LF 0603C BF2012-E2R4DAAT/LF 0805C BL2012-10B5388T/LF 0805C FB2012-05N2R4GT/LF 0805C BF3216-B2R4AAAT 1206C CP1608-17A0836T/LF SMD DP2012-E2455BBT/LF SMD BF2012-L2R4KCBT/LF SMD AT7020-E3R0HBAT SMD BL2012-20B2450T/LF SMD BL1608-20B2450T/LF/BALUN O805 FB2012-07N2R4CT/LF/FILTER O805 AT5020-E2R4HAAT/LF SMD CP1608-24B0836T/LF 0603C LF1608-B2R4KCBT/LF 0603C BL2012-10B2450T/LF 0805C BL2012-10B5512T/LF 0805C BF2012-L2R4NDAT/LF 0805C AT3216-B5R5HAAT/LF 1206L BF3225-B2R4CACT/LF 1210L DP2520-E2455HAT/LF 2520 HI0603-1B33NJHT O603 DS3232-B0918AAT/LF SMD TS3232-B0918AAT/LF SMD DS3232-B0918CCT/LF SMD BL1005-AVR2450T/LF SMD FB2015-10L2R5BT/LF SMD BL2012-10H0465T/LF SMD FB2520-07E2R4BT SMD BF2012-L2R4NABT/LF SMD LF0605-NR87NAAT/LF SMD BD2012-20B0820T/LF SMD FB2012-06N2R4MT/LF SMD DP1608-V1524CAT/LF SMD HF3225-K1R9EACT/LF SMD BL2012-07M1975T SMD AT3216-B2R7HAA SMD FB2012-10E5R5ET/LF SMD BL2012-05B2450T SMD0805 BL1608-10B2450T/LF 0603C BL1608-10K2500T/LF 0603C
PD1608-E2R4BAAT/LF 0603C
Web:www.icbros.com Email:[email protected] HK Tel:+852 44058386 Whatsapp:+852 44058386 Skype:[email protected]
#pcbuild#DAC#analogelectronics#semimodular#attiny#hdmi#preamplifier#elettronica#supercon#pcbengineer#diyelectronics#eletricistas#emeddedsystems#hobielektronik#electricalprojects#components#makers#engineering#irremote#studentproject#pic24#eletronica#drscientist#universalrobots#circuitplayground#powersupply#arduinocompatible#electrical#lorawan#DSPIC
0 notes
Text
What you know about ipollo v1 miner
Model Ipollo V1 of the iPollo mining EtHash algorithm with a maximum hash rate of3.6 Gh/ s for a power consumption of 3100W.
What's an ASIC miner? Short for operation Specific Integrated Circuit, the underpinning ASIC chip is generally designed for a singular purpose, similar as audio processing or controlling a mobile phone call. In this script, it's designed to" booby-trap" a specific cryptocurrency.
What does an ASIC miner actually do?
In a nutshell, mining performs complicated computations when looking for a specific number. Whether it's an ASIC miner or a GPU mining carriage, the mining tackle has to go through a lot of computations before that number can be set up. As evidence of working systems like Bitcoin, the first person to find that number will get a price at the time of writing12.5 Bitcoins worth about$,850.

There are so numerous people and important computer systems trying to mine Bitcoin that pools of miners are forming to find that number and share in the gains. In fact, the briskly your tackle is, the more you earn. That's why people who can go it choose ASIC miners because it gives them the stylish occasion to earn cryptocurrency for their investment.
Each cryptocurrency has its own cryptographic hash algorithm and ASIC miners are designed to mine using that particular algorithm. Bitcoin ASIC miners are actually designed to cipher the SHA- 256 hash algorithm. In the case of Litecoin, it uses Scrypt. This technically means that they can mine any other coin grounded on the same algorithm, but utmost people who buy ASIC tackle designed for Bitcoin mine specific digital coins.
When it comes to cryptocurrency mining, it's veritably important that the cryptocurrency you mine is worth further than what you spend on tackle and electricity. These perimeters may be near than you suppose, as cryptocurrency mining can be precious. tackle can be precious to buy up front, and some of it can bring thousands of bones a time in electricity.
When choosing mining tackle, it's incredibly important to have the most effective systems. This is where ASIC miners come into play. They're different from a plates card or CPU mining system, which is grounded on factors designed to perform further than one task. rather, ASIC miners are designed from the ground up to perform the computations needed by a specific cryptographic hash algorithm used by one person or a sprinkle of cryptocurrencies.

Because of this unique approach, ipollotech is incredibly effective, important, high" hash rate" and power effective, using far lower power than a miner with eight plates cards can perform for mining. same task. This combination of performance and low power consumption makes them much cheaper to run than most common tackle.
In Bitcoin and Litecoin, ASIC mining is nearly the only way these cryptocurrencies are booby-trapped. You can now also stock up on Ethereum ASIC miners, similar as ipollo v1.
Ipollo released the most important and profitable miner of the time in 2022. Ipollo V1 comes with a hashrate of 3600Mh/ s and a power consumption of 3100W (-10). The super important hash rate of ETH makes this monster a plutocrat printer that can earn over$ 60 per day indeed in the bear request.
This monster can mine both ETH and ETC. you can still make plutocrat from ETC mining after ETH2.0 Merge.
0 notes
Text
13 Secrets You Will Not Want To Know About Best Credit Card Generator | best credit card generator

Professional and Unique Business Card – best credit card generator | best credit card generator
Here are some added aegis apps you adeptness acquisition useful!
Price: Chargeless / $2.99-$4.99 per month
1Password is one of the added aggressive countersign managers. It has a lot of the basal features, including countersign administration (obviously), countersign generation, cross-platform abutment with added operating systems, and more. The app additionally comes with countersign alleviate and added alignment and assurance features. 1Password provides a 30-day chargeless balloon for bureaucracy and demoing. You accept to subscribe with one of their affairs afterwards that.
Price: Chargeless / $3.49
aWallet is one of those countersign administrator apps that accept been about for a actual continued time. It food passwords, cyberbanking info, acclaim agenda info, and custom abstracts if you charge it to. There is additionally a congenital search, custom icons, and an auto-lock feature. There is alike a congenital countersign architect so you don’t accept to anticipate of one, but that is a exceptional feature. It covers all the basics, includes AES and Blowfish encryption, and seems to do aggregate right. You can download the app for chargeless and pay for the pro adaptation as a distinct in-app purchase. We like it back being doesn’t charge a subscription.
Price: Free
Bitwarden is a newer countersign administrator app and a decidedly acceptable one. The developers assume to booty this accomplished countersign administration affair actual seriously. The app includes AES-256 bit encryption, absolute hashing, and PBKDF2-SHA-256 (a technology that helps anticipate animal force attacks). The app is additionally actually free, actually accessible source, and you can host your own countersign server if you appetite to. It alike supports Android’s Autofill API. This is apparently the best countersign administrator app that you’ve apparently never heard of before. We can say that and not get accused of advocacy because it’s chargeless so cipher gets any money anyway! It’s calmly amid the best chargeless countersign administrator apps.

Credit Card Generator Archives – Fix Win Error – best credit card generator | best credit card generator
Price: Chargeless / $4.99-$9.99 per month
Dashlane is a adequately accepted countersign administrator app. It has a appropriate cardinal of features, acceptable encryption, and a appropriate set of chargeless features. The chargeless adaptation includes auto-fill, aegis alerts, accumulator for up to 50 passwords, and annual on a distinct device. There are two exceptional subscriptions from there. The $4.99 per ages advantage upgrades the countersign accumulator and accessory syncing to absolute while abacus aphotic web ecology and a apathetic VPN. The $9.99 per ages bank adds a acclaim ecology service, character apology support, and $1 actor in character annexation insurance. That’s appealing hardcore. However, best bodies are serviced aloof accomplished with the chargeless countersign administrator adaptation too as continued as they don’t appetite it on their computer as able-bodied as their adaptable device.
Price: Chargeless / $9.99
Enpass is a adequately able countersign manager. It covers the basics and there are alike desktop versions accessible for Mac, PC, and Linux. It additionally boasts no cable fees which is a nice touch. Alongside that, the app can advancement and restore your info, includes 256-bit AES encryption, cross-platform syncing, and you can alike acceptation from added countersign managers to accomplish clearing easier. You can additionally accept it auto-fill your passwords into Google Chrome if you use that browser. It’s chargeless to download and use with a distinct $9.99 acquittal to alleviate everything. You can use this app for chargeless with Google Play Pass as well.
HERE ARE SOME RELATED APP LISTS WE THINK YOU MIGHT LIKE!

Best Credit Card Generator with Zip Code to Avoid Monetary Frauds .. | best credit card generator
Price: Free
Keepass2Android is one of the added basal countersign administrator apps. It has the basics and you’ll be able to advancement passwords and such. However, it doesn’t accept a lot of the added circuitous appearance of abounding of its competitors. The app’s capital affirmation to acclaim is that it’s actually chargeless and accessible source. It’s based on the cipher for Keepassdroid (which is addition accomplished free, accessible antecedent countersign manager) and the two are accordant with one another. This is addition accomplished chargeless countersign administrator for those on a budget.
Price: Chargeless / Up to $9.99 per ages / Up to $99.99 per year
Keeper is one of the earlier countersign administrator apps on the list. However, its accepted updates advice accumulate it relevant. It has all of the basics, including Android’s congenital auto-fill capabilities, a countersign generator, and a basement for being like files, photos, and videos. The desktop adaptation is additionally aloft average. It’s a competent countersign administrator with some added alcove appearance for adeptness users. However, it’s additionally one of the best big-ticket countersign administrator apps on the list. There is a chargeless adaptation as able-bodied as a balloon for the pro adaptation if you appetite to try that.
Price: Chargeless / $2-$4 per month
LastPass is about as boilerplate as it gets back it comes to countersign administrator apps. It has a metric ton of features, including auto-filling passwords into apps, sites, and alike forms. It’s additionally blatant and a lot of bodies like blatant these days. It additionally allows you to abundance photos and audio addendum securely. There are several added added different or aberrant appearance such as fingerprint scanner support, a countersign generator, a countersign accountant to let you apperceive if your countersign is weak, and alike the adeptness to admission emergency admission to a acquaintance or ancestors member. The cable tiers are competitively priced, but we would’ve admired to accept apparent a bigger alms in the chargeless version. You can additionally grab LastPass Authenticator in Google Play to add 2-factor affidavit for added security.
Price: Chargeless / $4.99

13 Free Credit Card Numbers with CVV [Today April List] – best credit card generator | best credit card generator
Password Safe and Administrator is a acceptable bourgeois advantage back it comes to countersign managers. This one boasts actually aught admission to the Internet as able-bodied as a 256-bit encryption which should advice you feel almost safe. It additionally has Material Design which looks and acts wonderfully. You can put your passwords in, assort them for accessible browsing, and alike accomplish new passwords on the fly. Additionally, it comes with auto-backup. There are abounding added appearance if you adjudge to buy the pro adaptation for $3.99. It’s not the best powerful, but it’s appropriate and it’s chargeless with Google Play Pass if you accept that. Addition appropriate advantage agnate to Countersign Safe is My Passwords by Erkan Molla.
Price: Free
Google’s Smart Lock is a decidedly acceptable countersign manager. It works natively on Android, Google Chrome, and Chrome OS. Basically, you log into article and Google asks if you appetite it to bethink the password. The abutting time you accessible that app or that site, Google puts the capacity in for you. It supports usernames, passwords, acclaim agenda info, and some added stuff. It’s all absolutely chargeless as well. Hit the button aloft to admission the passwords stored on your Google account.
Price: Chargeless (usually)
It’s not actual common, but some phones (mainly Samsung) accept countersign managers as allotment of the OS. These countersign managers are usually angry to an account, accompany amid devices, and assignment with the device’s absolute security. For instance, with Samsung Pass, you can auto-fill apps and websites by application the iris scanner on the Samsung buzz instead of the accepted fingerprint or PIN/pattern alleviate methods. It’s alone a acceptable band-aid if you intend on afraid with a cast for a while. Otherwise, we acclaim one of the nine solutions above. Still, if you accept a buzz with article like this congenital already, it adeptness be aces of a chance. They are usually free.
Credit Card Generator Hack | Best Hacks 4 Free – best credit card generator | best credit card generator
13 Secrets You Will Not Want To Know About Best Credit Card Generator | best credit card generator – best credit card generator | Encouraged in order to my website, in this period I am going to show you about keyword. And after this, this is the first picture:

Best Credit Card ZIP Code Generator Online 13, Best CC Number .. | best credit card generator
What about image earlier mentioned? will be that will wonderful???. if you’re more dedicated thus, I’l d demonstrate several image once again down below:
So, if you’d like to have the amazing photos related to (13 Secrets You Will Not Want To Know About Best Credit Card Generator | best credit card generator), press save icon to save these graphics to your personal computer. These are ready for transfer, if you love and wish to own it, simply click save badge in the post, and it’ll be directly saved to your desktop computer.} As a final point if you desire to find new and the latest graphic related to (13 Secrets You Will Not Want To Know About Best Credit Card Generator | best credit card generator), please follow us on google plus or save this website, we try our best to provide regular up grade with all new and fresh images. We do hope you love staying here. For most updates and latest information about (13 Secrets You Will Not Want To Know About Best Credit Card Generator | best credit card generator) shots, please kindly follow us on tweets, path, Instagram and google plus, or you mark this page on bookmark section, We try to present you update periodically with fresh and new shots, like your searching, and find the best for you.
Here you are at our website, articleabove (13 Secrets You Will Not Want To Know About Best Credit Card Generator | best credit card generator) published . Today we’re pleased to declare we have discovered an awfullyinteresting contentto be discussed, that is (13 Secrets You Will Not Want To Know About Best Credit Card Generator | best credit card generator) Most people searching for details about(13 Secrets You Will Not Want To Know About Best Credit Card Generator | best credit card generator) and of course one of these is you, is not it?

Cocoon Nebula details (IC5146) in HαRGB – best credit card generator | best credit card generator

Superman the movie (1978) filming locations – best credit card generator | best credit card generator

Credit Card Generator with CVV and Expiry Date #creditcard .. | best credit card generator

Random cvv number | How to guess credit card security codes. 13 .. | best credit card generator

Best Credit Card Generator Services 2020 – BIN Codes .. | best credit card generator
Best Credit Card Generator 2019, Best CC Number Generator .. | best credit card generator

DISCARD+CARD+GENERATOR – – best credit card generator | best credit card generator
from WordPress https://www.visaword.com/13-secrets-you-will-not-want-to-know-about-best-credit-card-generator-best-credit-card-generator/ via IFTTT
0 notes
Text
Bitmain’s AntPool Activates Controversial AsicBoost for Faster Bitcoin Mining
Bitmain’s mining pool, AntPool, has supposedly activated one of their controversial methods of mining Bitcoin more efficiently, called AsicBoost. The controversial Bitcoin mining “hack” supposedly increases mining efficiency by up to 20% and is controversial because many developers claim that its use damages the Bitcoin network.
Weakness in Bitcoin PoW Exploited
According to AsicBoost Block Explorer, block #540032, mined by AntPool, was mined using the AsicBoost, which exploits a previously known weakness in Bitcoin’s proof-of-work algorithm that allows for faster mining. Bitmain notably holds a patent in China for a system that exploits the Bitcoin network’s weakness in order to increase mining productivity.
The patent, which describes an “optimizing method,” details a system that uses a “device and circuit for Hash computing chip of bitcoin proof of work, and relates to the technical field of cipher computing, computer network and integrated circuits.”
The patent abstract also notes that the “The method, device and circuit provided by the invention greatly reduce the power consumption of the circuit.”
Bitmain has a history of using AsicBoost and has been accused several times over the past year of utilizing the controversial mining method. Blockstream CTO, Greg Maxwell, was one of the first to call Bitmain out for using AsicBoost, accusing the them of using the method to increase profits.
Bitmain Denies use of AsicBoost
In the past year, Bitmain has ardently denied their use of the “mathematical workaround,” expressing that they have never used the technology before. Following the controversy that followed Maxwell’s accusations, Bitmain released a statement, saying in part that:
“Bitmain has tested ASICBOOST on the Testnet but has never used ASICBOOST on the mainnet as implied in Gregory Maxwell’s proposal. We ask conclusive proof from whoever claims this to be false because such baseless claims are toxic for the Bitcoin space. We also believe the math used by Gregory Maxwell is incorrect and that the method is not practical in a production environment.”
Bitmain also addressed the Chinese patent they hold on a system that utilizes AsicBoost, saying that:
“Bitmain holds the ASICBOOST patent in China. We can legally use it in our own mining farms in China to profit from it and sell the cloud mining contracts to the public. This, however profitable, is not something we would do for the greater good of Bitcoin.”
Possible AsicBoost use comes as Bitmain is Reportedly Losing Money
Bitmain has yet to release any statements regarding AntPool’s potential use of AsicBoost, but the use of this mining method would coincide with a recent BitMEX Research report that claimed that the mining giant is bleeding money due to low cryptocurrency prices and increased operational costs.
BitMEX Research also concludes that the sharp decline in mining revenue is partially a strategic decision, explaining that:
“We believe this decline represents a smart strategic decision by Bitmain to divest (relatively speaking), from an increasingly competitive and lower margin area. In our view, as one moves down the mining supply chain, the competition is likely to increase faster and Bitmain made a sensible move by trying to focus their efforts up the chain, where an increasingly large proportion of the value from mining may accrue.”
Although unconfirmed, it would make sense that Bitmain is utilizing the AsicBoost mining method in an effort to increase efficiency and profitability while still driving their competition’s profits into the ground.
Featured image from Shutterstock
The post Bitmain’s AntPool Activates Controversial AsicBoost for Faster Bitcoin Mining appeared first on NewsBTC.
Bitmain’s AntPool Activates Controversial AsicBoost for Faster Bitcoin Mining published first on https://medium.com/@smartoptions
0 notes
Text
Just beat Gravity Circuit, phenomenal game to play if you liked Mega Man or Shovel Knight. Would highly recommend. Now excuse me while I go add several pictures of Hash the Cipher Circuit into my reblog queue on account of: He's cool.
0 notes
Text
Bitmain’s AntPool Activates Controversial AsicBoost for Faster Bitcoin Mining
Bitmain’s mining pool, AntPool, has supposedly activated one of their controversial methods of mining Bitcoin more efficiently, called AsicBoost. The controversial Bitcoin mining “hack” supposedly increases mining efficiency by up to 20% and is controversial because many developers claim that its use damages the Bitcoin network.
Weakness in Bitcoin PoW Exploited
According to AsicBoost Block Explorer, block #540032, mined by AntPool, was mined using the AsicBoost, which exploits a previously known weakness in Bitcoin’s proof-of-work algorithm that allows for faster mining. Bitmain notably holds a patent in China for a system that exploits the Bitcoin network’s weakness in order to increase mining productivity.
The patent, which describes an “optimizing method,” details a system that uses a “device and circuit for Hash computing chip of bitcoin proof of work, and relates to the technical field of cipher computing, computer network and integrated circuits.”
The patent abstract also notes that the “The method, device and circuit provided by the invention greatly reduce the power consumption of the circuit.”
Bitmain has a history of using AsicBoost and has been accused several times over the past year of utilizing the controversial mining method. Blockstream CTO, Greg Maxwell, was one of the first to call Bitmain out for using AsicBoost, accusing the them of using the method to increase profits.
Bitmain Denies use of AsicBoost
In the past year, Bitmain has ardently denied their use of the “mathematical workaround,” expressing that they have never used the technology before. Following the controversy that followed Maxwell’s accusations, Bitmain released a statement, saying in part that:
“Bitmain has tested ASICBOOST on the Testnet but has never used ASICBOOST on the mainnet as implied in Gregory Maxwell’s proposal. We ask conclusive proof from whoever claims this to be false because such baseless claims are toxic for the Bitcoin space. We also believe the math used by Gregory Maxwell is incorrect and that the method is not practical in a production environment.”
Bitmain also addressed the Chinese patent they hold on a system that utilizes AsicBoost, saying that:
“Bitmain holds the ASICBOOST patent in China. We can legally use it in our own mining farms in China to profit from it and sell the cloud mining contracts to the public. This, however profitable, is not something we would do for the greater good of Bitcoin.”
Possible AsicBoost use comes as Bitmain is Reportedly Losing Money
Bitmain has yet to release any statements regarding AntPool’s potential use of AsicBoost, but the use of this mining method would coincide with a recent BitMEX Research report that claimed that the mining giant is bleeding money due to low cryptocurrency prices and increased operational costs.
BitMEX Research also concludes that the sharp decline in mining revenue is partially a strategic decision, explaining that:
“We believe this decline represents a smart strategic decision by Bitmain to divest (relatively speaking), from an increasingly competitive and lower margin area. In our view, as one moves down the mining supply chain, the competition is likely to increase faster and Bitmain made a sensible move by trying to focus their efforts up the chain, where an increasingly large proportion of the value from mining may accrue.”
Although unconfirmed, it would make sense that Bitmain is utilizing the AsicBoost mining method in an effort to increase efficiency and profitability while still driving their competition’s profits into the ground.
Featured image from Shutterstock
The post Bitmain’s AntPool Activates Controversial AsicBoost for Faster Bitcoin Mining appeared first on NewsBTC.
from Cryptocracken WP https://ift.tt/2MV37L5 via IFTTT
0 notes
Text
Bitmain’s AntPool Activates Controversial AsicBoost for Faster Bitcoin Mining
Bitmain’s mining pool, AntPool, has supposedly activated one of their controversial methods of mining Bitcoin more efficiently, called AsicBoost. The controversial Bitcoin mining “hack” supposedly increases mining efficiency by up to 20% and is controversial because many developers claim that its use damages the Bitcoin network.
Weakness in Bitcoin PoW Exploited
According to AsicBoost Block Explorer, block #540032, mined by AntPool, was mined using the AsicBoost, which exploits a previously known weakness in Bitcoin’s proof-of-work algorithm that allows for faster mining. Bitmain notably holds a patent in China for a system that exploits the Bitcoin network’s weakness in order to increase mining productivity.
The patent, which describes an “optimizing method,” details a system that uses a “device and circuit for Hash computing chip of bitcoin proof of work, and relates to the technical field of cipher computing, computer network and integrated circuits.”
The patent abstract also notes that the “The method, device and circuit provided by the invention greatly reduce the power consumption of the circuit.”
Bitmain has a history of using AsicBoost and has been accused several times over the past year of utilizing the controversial mining method. Blockstream CTO, Greg Maxwell, was one of the first to call Bitmain out for using AsicBoost, accusing the them of using the method to increase profits.
Bitmain Denies use of AsicBoost
In the past year, Bitmain has ardently denied their use of the “mathematical workaround,” expressing that they have never used the technology before. Following the controversy that followed Maxwell’s accusations, Bitmain released a statement, saying in part that:
“Bitmain has tested ASICBOOST on the Testnet but has never used ASICBOOST on the mainnet as implied in Gregory Maxwell’s proposal. We ask conclusive proof from whoever claims this to be false because such baseless claims are toxic for the Bitcoin space. We also believe the math used by Gregory Maxwell is incorrect and that the method is not practical in a production environment.”
Bitmain also addressed the Chinese patent they hold on a system that utilizes AsicBoost, saying that:
“Bitmain holds the ASICBOOST patent in China. We can legally use it in our own mining farms in China to profit from it and sell the cloud mining contracts to the public. This, however profitable, is not something we would do for the greater good of Bitcoin.”
Possible AsicBoost use comes as Bitmain is Reportedly Losing Money
Bitmain has yet to release any statements regarding AntPool’s potential use of AsicBoost, but the use of this mining method would coincide with a recent BitMEX Research report that claimed that the mining giant is bleeding money due to low cryptocurrency prices and increased operational costs.
BitMEX Research also concludes that the sharp decline in mining revenue is partially a strategic decision, explaining that:
“We believe this decline represents a smart strategic decision by Bitmain to divest (relatively speaking), from an increasingly competitive and lower margin area. In our view, as one moves down the mining supply chain, the competition is likely to increase faster and Bitmain made a sensible move by trying to focus their efforts up the chain, where an increasingly large proportion of the value from mining may accrue.”
Although unconfirmed, it would make sense that Bitmain is utilizing the AsicBoost mining method in an effort to increase efficiency and profitability while still driving their competition’s profits into the ground.
Featured image from Shutterstock
The post Bitmain’s AntPool Activates Controversial AsicBoost for Faster Bitcoin Mining appeared first on NewsBTC.
from CryptoCracken SMFeed https://ift.tt/2MV37L5 via IFTTT
0 notes
Text
Internet Security and VPN Network Design
Overview
This article discusses some essential technical plan associated with a VPN. A Virtual Private Network (VPN) integrates remote employees, company offices, and company partners using the Internet and secures encrypted tunnels between locations. An Access VPN is used to connect remote user to the boldness network. The remote workstation or laptop testament use an entrees circuit such as Cable, DSL or Wireless to connect to a local Internet Service Provider (ISP). With a client-initiated model, software on the remote workstation builds an encrypted tunnel from the laptop to the ISP using IPSec, Layer 2 Tunneling Protocol (L2TP), or Point to Point Tunneling Protocol (PPTP). The user must authenticate as a permitted VPN exploiter with the ISP. Once that is finished, the ISP builds an encrypted pipe to the boldness VPN router or concentrator. TACACS, RADIUS or Windows bartender evidence authenticate the remote exploiter as an employee that is allowed entrees to the company network. With that finished, the remote user must then authenticate to the local Windows panels server, Unix bartender or Mainframe mass depending upon where there network reason is located. The ISP initiated pattern is less secure than the client-initiated form since the encrypted subway is built from the ISP to the company VPN router or VPN concentrator only. As well the secure VPN pipette is built with L2TP or L2F.
The Extranet VPN will connect business partners to a undertaking network by disposition a secure VPN crossing from the firm partner router to the undertaking VPN router or concentrator. The specific tunneling procedures utilized depends upon whether it is a router context or a remote dialup connection. The options for a router connected Extranet VPN are IPSec or Generic Routing Encapsulation (GRE). Dialup extranet connections will utilize L2TP or L2F. The Intranet VPN testament connect company offices across a secure scenery using the same countenance with IPSec or GRE as the tunneling protocols. It is important to memorandum that what makes VPN's very memorial effective and efficient is that they conduct the existing Internet for transporting boldness traffic. That is why loads company are selecting IPSec as the guard protocol of selection for guaranteeing that information is secure as it travels between routers or laptop and router. IPSec is comprised of 3DES encryption, IKE key reserve verification and MD5 path authentication, which provide authentication, investment and confidentiality.
Internet Protocol Security (IPSec)
IPSec tenacity is respect notation since it such a prevalent responsibility subroutine utilized today with Virtual Private Networking. IPSec is specified with RFC 2401 and developed as an open standard for secure transport of IP across the public Internet. The bundle disposition is comprised of an IP header/IPSec header/Encapsulating Security Payload. IPSec provides ciphering services with 3DES and proof with MD5. In addition there is Internet Key Exchange (IKE) and ISAKMP, which automate the allocation of epiphany keys between IPSec friend trick (concentrators and routers). Those protocols are required for bargaining one-way or two-way defense associations. IPSec sentry society are comprised of an ciphering algorithm (3DES), hash algorithm (MD5) and an verification dresser (MD5). Access VPN performing utilize 3 security union (SA) per backdrop (transmit, receive and IKE). An undertaking network with dozens IPSec gentleman unit testament utilize a Certificate Authority for scalability with the proof current instead of IKE/pre-shared keys.
Laptop - VPN Concentrator IPSec Peer Connection
1. IKE Security Association Negotiation
2. IPSec Tunnel Setup
3. XAUTH Request / Response - (RADIUS Server Authentication)
4. Mode Config Response / Acknowledge (DHCP and DNS)
5. IPSec Security Association
Access VPN Design
The Access VPN evidence situation the openness and low prize Internet for connectivity to the enterprises breasts area with WiFi, DSL and Cable access orbit from local Internet Service Providers. The main issue is that company dope must be protected as it travels across the Internet from the telecommuter laptop to the boldness center office. The client-initiated ideal evidence be utilized which builds an IPSec pipe from each buyer laptop, which is terminated at a VPN concentrator. Each laptop evidence be configured with VPN clients software, which evidence run with Windows. The telecommuter must first dial a local access sum and authenticate with the ISP. The RADIUS waiter evidence authenticate each dial connection as an authorized telecommuter. Once that is finished, the remote exploiter testament authenticate and authorize with Windows, Solaris or a Mainframe waiter before starting any applications. There are dual VPN concentrators that testament be configured for fail over with virtual routing abundance protocol (VRRP) should one of them be unavailable.
Each concentrator is connected between the external router and the firewall. A new feature with the VPN concentrators prevent gully of service (DOS) attacks from outside hackers that could affect network availability. The firewalls are configured to empowerment source and meaning IP addresses, which are assigned to each telecommuter from a pre-defined range. As well, any resignation and protocol ports testament be permitted through the firewall that is required.
Extranet VPN Design
The Extranet VPN is designed to allow secure connectivity from each boldness ally senate to the undertaking heart office. Security is the primary center since the Internet will be utilized for transporting all idiot trade from each company partner. There evidence be a rollover background from each boldness ally that evidence terminate at a VPN router at the enterprise spunk office. Each boldness ally and its buddy VPN router at the center department will utilize a router with a VPN module. That staff provides IPSec and high-speed munitions ciphering of collection before they are transported across the Internet. Peer VPN routers at the firm spunk domain are dual homed to different multilayer switches for link difference should one of the links be unavailable. It is important that trade from one boldness complement doesn't endings up at another firm equivalent office. The switches are located between external and internal firewalls and utilized for integration public waiter and the external DNS server. That isn't a defense issue since the external firewall is draining public Internet traffic.
In addition filtering tins be implemented at each network switch as well to prevent path from entity advertised or susceptibility exploited from owning firm partner connections at the boldness center office multilayer switches. Separate VLAN's https://anonymster.com/ testament be assigned at each network switch for each boldness confederate to improve vista and segmenting of subnet traffic. The angle 2 external firewall testament examine each package and permit those with firm counterpart fountains and motif IP address, meekness and subroutine ports they require. Business colleague confluence will have to authenticate with a RADIUS server. Once that is finished, they evidence authenticate at Windows, Solaris or Mainframe crowd before starting any applications.
0 notes
Text
Internet Security and VPN Network Design
This object discusses some essential technical opinion associated with a VPN. A Virtual Private Network (VPN) integrates remote employees, undertaking offices, and enterprise partners using the Internet and secures encrypted tunnels between locations. An Access VPN is used to connect remote exploiter to the undertaking network. The remote workstation or laptop evidence use an entrees circuit such as Cable, DSL or Wireless to connect to a local Internet Service Provider (ISP). With a client-initiated model, software on the remote workstation builds an encrypted tube from the laptop to the ISP using IPSec, Layer 2 Tunneling Protocol (L2TP), or Point to Point Tunneling Protocol (PPTP). The user must authenticate as a permitted VPN user with the ISP. Once that is finished, the ISP builds an encrypted tube to the company VPN router or concentrator. TACACS, RADIUS or Windows bartender will authenticate the remote user as an employee that is allowed access to the company network. With that finished, the remote exploiter must then authenticate to the local Windows area server, Unix waiter or Mainframe multitude depending upon where there network explanation is located. The ISP initiated patterns is less secure than the client-initiated pattern since the encrypted pipe is built from the ISP to the enterprises VPN router or VPN concentrator only. As well the secure VPN tunnel is built with L2TP or L2F.
The Extranet VPN testament connect undertaking partners to a company network by structure a secure VPN context from the enterprise partner router to the undertaking VPN router or concentrator. The specific tunneling protocol utilized depends upon whether it is a router junction or a remote dialup connection. The possibility for a router connected Extranet VPN are IPSec or Generic Routing Encapsulation (GRE). Dialup extranet connections evidence utilize L2TP or L2F. The Intranet VPN will connect boldness offices across a secure connection using the same tendency with IPSec or GRE as the tunneling protocols. It is important to note that what makes VPN's very prize effective and efficient is that they leverage the existing Internet for transporting undertaking traffic. That is why dozens gang are pilfering IPSec as the security subroutine of choice for guaranteeing that information is secure as it travels between routers or laptop and router. IPSec is comprised of 3DES encryption, IKE key spells confirmation and MD5 route authentication, which provide authentication, instate and confidentiality.
Internet Protocol Security (IPSec)
IPSec operation is value notation since it such a prevalent security protocol utilized today with Virtual Private Networking. IPSec is specified with RFC 2401 and developed as an open example for secure transport of IP across the public Internet. The packet disposition is comprised of an IP header/IPSec header/Encapsulating Security Payload. IPSec provides encryption services with 3DES and authentication with MD5. In addition there is Internet Key Exchange (IKE) and ISAKMP, which automate the distribution of secret keys between IPSec gentleman device (concentrators and routers). Those protocols are required for discussing one-way or two-way defense associations. IPSec carefulness confederation are comprised of an ciphering algorithm (3DES), hash algorithm (MD5) and an proof bureau (MD5). Access VPN performing utilize 3 security union (SA) per background (transmit, receive and IKE). An undertaking network with dozens IPSec pal device will utilize a Certificate Authority for scalability with the authentication process instead of IKE/pre-shared keys.
Laptop - VPN Concentrator IPSec Peer Connection
1. IKE Security Association Negotiation
2. IPSec Tunnel Setup
3. XAUTH Request / Response - (RADIUS Server Authentication)
4. Mode Config Response / Acknowledge (DHCP and DNS)
5. IPSec Security Association
Access VPN Design
The Access VPN will pertinence the availability and low award Internet for connectivity to the firm mettle compartment with WiFi, DSL and Cable access encircling from local Internet Service Providers. The main issue is that company intelligence must be protected as it travels across the Internet from the telecommuter laptop to the firm mettle office. The client-initiated ideal evidence be utilized which builds an IPSec tubes from each client laptop, which is terminated at a VPN concentrator. Each laptop evidence be configured with VPN clients software, which will run with Windows. The telecommuter must first dial a local entrees tally and authenticate with the ISP. The RADIUS waiter testament authenticate each dial connection as an authorized telecommuter. Once that is finished, the remote exploiter evidence authenticate and authorize with Windows, Solaris or a Mainframe server before starting any applications. There are dual VPN concentrators that will be configured for fail over with virtual routing redundancy procedures (VRRP) should one of them be unavailable.
Each concentrator is connected between the external router and the firewall. A new feature with the VPN concentrators prevent appeal of service (DOS) attacks from outside hackers that could affect network availability. The firewalls are configured to mandate fountains and goals IP addresses, which are assigned to each telecommuter from a pre-defined range. As well, any humility and subroutine ports evidence be permitted through the firewall that is required.
Extranet VPN Design
The Extranet VPN is designed to allow secure connectivity from each business complement compartment to the business hearts office. Security is the primary hubs since the Internet testament be utilized for transporting all dope trade from each firm partner. There will be a circuit connection from each undertaking colleague that evidence terminate at a VPN router at the undertaking hearts office. Each boldness equivalent and its supporter VPN router at the heart compartment will utilize a router with a VPN module. That unit provides IPSec and high-speed weapons ciphering of package before they are transported across the Internet. Peer VPN routers at the enterprises spunk legislature are dual homed to different multilayer switches for link difference should one of the links be unavailable. It is important that commerce from one company equivalent doesn't fool up at another company equivalent office. The switches are located between external and internal firewalls and utilized for coupling public servers and the external DNS server. That isn't a watchman issue since the external firewall is draining public Internet traffic. For More Details Please Visit : https://anonymster.com/
In addition draining tins be implemented at each network switch as well to prevent routes from creature advertised or sensitivity exploited from having company colleague connections at the boldness spunk compartment multilayer switches. Separate VLAN's testament be assigned at each network switch for each undertaking partner to improve security and segmenting of subnet traffic. The tier 2 external firewall testament examine each package and permit those with enterprises complement source and goals IP address, submissiveness and protocol ports they require. Business counterparts semester evidence have to authenticate with a RADIUS server. Once that is finished, they evidence authenticate at Windows, Solaris or Mainframe mass before starting any applications.
0 notes
Text
Module 6: Lab Notes
MidTerm Questions:
Q2.
Tamper evident (?)
Don’t use cipher
SHA256: is not broken
2048 bit RSA , One-time pad
Q5.
Authentication
Q12.
Vigenere cipher: remove singular monodram, but bigrams & trigrams will remain in certain iterations
Q9.
SHA256: 256 bit hash
Collision: 128 (takes into consideration the average)
2nd Preimage: 2^255
Preimage: 2^255
Buffer Overflows:
Stack starts at the biggest address and grows to 0
Heap grows down (using malloc())
Stack like pancakes: place newest one at the top, and eat the newest one first
LIFO
Data inside array grows in the opposite direction to the stack growth
Buffer overflow: overflowed the buffer
Can overwrite the return address
Don’t write return address
Use ALSR: stack is not stored at the bottom but somewhere in the middle of memory
Case Study:
Target financial institutions
Large scale DoS attack
Defend our military operations
Use reverse engineering:
China buying old US military equipment: to see what equipment they already have and what they probably working on
Attackers:
Psychological Warfare:
Propaganda
People
Differences in ethnicity: cause divisiveness
Cut the internet
Holding cyber institutions ransom
Sternet 2.0 attacks
Target and take off satellites
Screw with traffic
EMP: electromagnetic pulse -> overload circuits and kill everything
Detonate it over Moscow or Russian cities and take down one of them
Target the allies
Defenders: protecting assets
State sponsored news source
Propaganda doesn’t work (?)
Social media
Work with social media
Closed networks
Companies that don’t need to be online will go offline
Verification identifier for Australian
Idea: “Backdoor you make is not just for you to use but also for everyone else”
0 notes
Text
Week 6 Notes and Reflection
REFLECTION
What a funny lecture - poor Richard was sick and instead gave the lecture over Skype. Too bad Skype has bad quality but it was delayed. Still I was able to learn lots!
One of the interesting things I learnt was buffer overflow attacks, and potentially how easy it is to make a mistake in your code where a malicious user can overflow the buffer. I also found it interesting on how the NSA is very resourceful compared to the rest of the world on this cryptographic stuff. They are hiding security vulnerabilities and methods that we may never know for a long time. For example, they might know a vulnerability in Windows but will keep it to themselves so they can exploit them to attack Iran or something.
My group also did the Cryptocurrency lecture. It went better than I thought, I thought we would be like 40 mins and cut out halfway through the presentation, but only 5 minutes over so it was good!!!
Richard played a very strange prank on us, apparently the first 10 mins of his lecture was “prerecorded”, which is rather strange, because he said he liked the questions/answers from our cryptocurrency group, but if he recorded the first part that means he was pretending, lol. Don’t understand.
NOTES
Initialisation Vectors - When an algorithm deals with a sequence of things e.g. merkle/damgard construction. We need avalanche effect. The point of a hash is to protect the whole document - we protect the whole document - capture the identity of the whole document. The idea is hash one block, roll that on and hash the next block etc. The very first requires as an Initialisation Vector (WEP is a stream cipher - it uses an IV somewhere).
A password like the one in the exam - 3 words concatenated together is still not that secure even though it might be 12 characters long.
WEP used a 64 bit key which is reasonable. How do we get users to type a 64 bit key?? Let’s let the user type a 40bit password, then we generate the rest - Initialisation Vector. Only 24 bit IV - Only need 2^12 to get a collision. IV collisions are a disaster - as soon as there is a collision, you have 2 different plain text with the same key, then it becomes easier to attack.
Mixing Data and Control -
Richard lining up in the post office - post office doesn’t really have much security. Then they brought in Express Post - the stamp thing was pretty expensive. You could get packets of stamps from the shop (not much security). He also needed the satchel, which was very expensive. They moved the counter and it was near the door. He put all the stamps into the satchel, and posted it to himself!! Similar to WEP attack.
Look at Harvard Architecture - one stack for data, one stack for control.
Buffer overflow - Alec1 phrack magazine should read the article. Smashing stack for fun and profit.
All that is happening in a PC is a CPU doing one thing at an instant. The computer is rapidly interleaving processes (context switching). The way it does this is through CPU interrupts. A stack keeps track of the current jobs and the interrupted jobs.
Buffer Overflow How It Works - All the data process is using is on the stack. When a process wakes up someone tells you the status of the local variables etc, and it was stored in the disk, and read back from the disk when it wakes up. The program that is running has the ability to store data on the stack. Instead of saving to disk, we store all the data saved on the stack for fast wakeup. The stack is stored backwards - E.g. House 1, 2, 3, 4. If you overflow the array (e.g. 100 byte array). If you can persuade the PC that it was 1000 bytes long, and then it will write to the stack, which is the middle of the stack frame of the person who is asleep. It contains a lot of control information - it contains pointer to the next instruction to be executed. As soon as the PC wake ups, it will execute that. You write to the return address of the asleep routine - change it to point to an area of memory you control - then you put your program in there and it will be executed. An attack usually involves putting the code itself in the buffer, and the return address being the pointer to the beginning of the buffer. Lets the user enter info, and the code doesn’t check the amount of info the user typed in fits in the array. E.g. user types in string containing - their program, nothings, overwrite return address.
Proof Of work - We want someone to do a lot of work. Proof of work in bitcoin - blockchain. A lot of work to make a new “page” of ledger book - hash needs lots of leading zeroes. In order to change a page few days ago requires you to modify the blockchain - too hard. Series of solving “puzzles”. Lots of work to fake pages in ledger. Keep trying to change the magic number to gets lots of zeroes. If you get enough zeroes, you solved the puzzle. e.g. 16 zeroes = 2^16 hashes.
Moore’s Law - Number of transistors exponentially increasing over time. About every year or 2 - double the number of transistors. Compute power also increases (doubles every 18 months - every 18 months attacker gains 1 bit of security).
Disk Encryption - If you want to encrypt a hard disk, how would you do it? They have physical access to the disk. Suppose you have 256bit key - will your normal password be good enough.... no. The way most hard disks do it is that they generate a key randomly and the encrypted version of that key is stored on the disk with the user’s password. Why is it better than encrypting the whole disk with the user’s lame password.
Disk Encryption Attack - You’ve told Windows to encrypt the hard disk. To save time, if the drive already has the encryption feature, Microsoft will just give the data in plaintext to the encryption feature of the drive.
When you write something to RAM and you turn the power off, it takes a while for the information to leak away. What they did was sprayed an aerosol can on the RAM chip. Then you just read back, and then you can find the encryption keys. Trying to read active memory. Spray keeps the temperature cool.
Very unlikely a cryptographic protocol will be attacked - Weaknesses usually happen on the endpoints - the backdoor open. E.g. the OS.
Encryption Algorithms
Ciphers after WW2 and before RSA - Most of the heavy lifting done by other encryption problems. RSA works because it is a hard mathematical problem. In the old days the hardness is tied to obscurity, jumbling things up. E.g. banks sent data to other banks, what did they do? They rolled their own. Security by obscurity, was pretty bad until 70s. NIST came up with a standard. They had a competition, trying to figure out the best algorithms - but barely anyone put anything up!! Decent thing was made up by IBM (Lucifer). They realised NSA works on codes and things. Guy from NIST went to NSA with the IBM algorithm. IBM cipher was jumble it, jumble etc, iterate it lots of times. NSA looked at the algorithm, published it, and change one random number to another random number. Decade later, people realised they can use differential analysis to crack it, but NSA already knew this!!
DES was adopted. Kept asking for new ones, new ones etc. It was until 2000 NIST run a competition for an algorithm, and finally lots of cool algorithms appeared. The winner became AES. Better than DES.
Symmetric Ciphers - If you have knowledge of the key, you can use for encryption and decryption. Only asymmetric cipher is RSA.
Earthquake - San Andreas fault line. What would you do if an earthquake struck? Think about crisis and how to respond during crisis. Have sneakers next to their bed to jump out. Have Go Bag
Block Modes - read up about "Block Modes" - only need to learn/understand ECB, CBC, CTR. Adapt something that deals with fixed sized modes to variable sized things. In Cipher block mode means how you can combine them together to get the ciphertext. ECB (concatenating, the simple one).
Mission Impossible Red box - To open the box needs prime minister recognition etc. Need all the 3 things right. Suppose youre the box designer. How can you build a USB stick that the data can only be accessed by the legitimate person? The problem of authentication.
Authentication - Identifying for who? Computer/human? If the human makes decision is that still authentication? Facebook goes around giving people names - is that authentication. Police scanning surveillance footage - is that authentication? Baggage screening - rather than looking for bad things, they look for good things. Authenticating stuff in bag.
Auth - The computer making the decision, can we have a computerised authentication system? What decisions? E.g. shoot a gun, login to FB? Does the decision have a physical impact?
How can a computer decide someone is a French minister? Preloaded with DB with all the faces of French ministers?
How did you know your dad is your dad when you go home?
Factors - Authentication can be faked, and use Defence in Depth and use multiple factors. 3 Factors - Something you know (secret), you have, and you are.
Hard to prove something is secret.
Use secrets to prove you are someone - Naive approach. How do you invent a shared secret? Post it like a bank?
Something you have - Send SMS msg confirm code. (2FA). Worked well initially, but then people intercept messages.
Something you are - Face, fingerprint, retina scan. However easily fakeable. Costs 10c to make a fingerprint. Breathing on fingerprint scanner.
The computer doesn’t know the “something you have”, “are”, “know”. Etc there are 3 factors, but not really, there are just secrets. Computer is just 101010, they can mimic that and get in.
A bad can open a door by powering a solenoid - no need to press the button. Bad guy just has to know where the line is.
Jay Tag - Selectively deactivate/activate circuits on board.
At the end of the day, authentication in just data.
MI IMPOSSIBLE box - someone can inject signal into the red box circuits. If the authentication is used for info, might be okay. Used the 3 pieces of info to combine into a key, then use that to encrypt the data. Could work - but in terms of protecting atom bombs etc, authentication is a problem. Problem entirely based on secrets.
French minister - Can’t make decisions without info from the outside world. North Korea - we know info could get in or out. They have an M&M type environment. The only people dictator worries about is the outside world. Danger is when the inside world has able to determine outside world.
“outside” and “inside” world bubble.
WEB EXTENDED LECTURE
HTML is a language which defines elements in the web browser.
Javascript is a code embedded in HTML that defines logic and can interact with HTML elements.
On web servers you have databases stored in SQL. User sends HTTP post request, queries DB, Returns session cookie to user if valid and stores in the database if login successful. (Like Brain website)
HTTP Cookies / Sessions - small piece of data generated by server and stored on user’s computer. Session cookies is a unique id generated by the server and sent to the user when they connect.
Session Hijacking - If you steal someones cookies, put it into your browser, you’ll be logged into their account.
XSS - Launching malicious script into website. Inject memes, steal cookies and modify DOM elements. you can do whatever the site owner can do.
Reflected XSS - Input immediately returned to the client.
Stored XSS - The injection returns in a later request.
Samy is my hero linkedin XSS bug
Injections - Malicious SQL statements inserted into an entry field for execution. Allow attacks to spoof identity, tamper with existing data, view the data etc.
Blind Injection - Exploit an application rather than getting a useful error msg they get a generic page specified by the developer instead.
Command Injection - Grep command injection.
Cross Site Request Forgery - They are logged in on a website somewhere. Browser sends cookie back for each request you make. So send a link to someone, it uses the cookie, boom send money. Defences - Tokens for the session. Expect this token back for all communications to the server.
CRYPTOCURRENCY EXTENDED LECTURE
This was my group!
0 notes