#how to protect your website from hackers
Explore tagged Tumblr posts
Text
#website protection#hacking#ethical hacking#how to secure your website#how to secure a website#how to secure website from hackers#how to protect your website from hackers#cracking#how to prevent hacking on website#how to secure your website from hackers#introduction to website hacking!#how to secure wordpress website#how to secure my website for free#how to secure a wordpress website#secure wordpress website#how to prevent hacking#how to recover from a website cyberattack
0 notes
Note
I've seen you say a few times that it's a good idea to have a password manager; could you explain why? I always feel like I'm missing something when it's mentioned because it's phrased as if there's an obvious danger that password managers protect you from, but I'm honestly not sure how they help keep passwords secure.
The obvious danger is human nature. Humans are bad at creating passwords; your passwords are almost certainly easy to guess, repeated across different accounts, or both, because that is just how the vast VAST majority of people create passwords, because humans are bad at creating passwords. Everybody knows "the rules" for creating passwords (don't use the same password on multiple websites, don't include personal details in your passwords, don't use very common words or letter or number sequences in your passwords, don't tell other people your password) and people break all of those rules anyway.
A standalone (not in-browser like firefox or chrome password manager, though those are better than nothing) password manager stores your passwords, generates complex passwords for you, and can also be used for things like storing notes on passwords (like "did I put my MFA on my email or my cellphone or an app for this password?" or "here are the made-up answers to the security questions I used for this website because I definitely didn't use real answers or answers I'd used on previous websites" or "these are the bills associated with this credit card").
With the way the current security landscape works, there are two things that are extremely important when you are creating a password:
Uniqueness
Complexity
The overwhelmingly prevalent way that people get "hacked" these days is through credential stuffing.
Let's say that your private data was revealed in the Experian breach a decade ago. It revealed your name, email address, and phone number. Now let's also say that your private data was revealed in one of the many breaches from social media sites; that one revealed your name, email address, phone number, password, and security questions.
If someone wants to try to gain access to one of your accounts - let's say your bank account - if they have your name and phone number (usually extremely easy to find online), they can cross-reference that information with data that has been revealed in previous breaches - now they've got your name and your email address (which you probably used to sign up for your online banking and have ABSOLUTELY used as your login for accounts all over the place) and at least one password that you've used somewhere.
But the thing is, they don't have one password. They have every password associated with that email address that has ever been revealed in a breach. If you go to the site haveibeenpwned.com you can enter your email and see how many times your email address has appeared in a breach. You can compare that with the number of passwords that were revealed in those breaches and you can ask yourself "what did those passwords have in common?"
Because I can tell you, my Tumblr password from 2013, my Kickstarter password from 2014, and my Disqus password from 2017 (all revealed in various breaches) probably had a lot in common.
So, now the hacker has: your name, your email (which is probably your username), and various passwords they can try to use to log in. Did you use the same password for Facebook and Twitter eight years ago? Did you use parts of that password for creating your bank password? If you heard that twitter passwords were exposed in a breach you probably changed that password, but did you change the bank password that you built on the same structure? Probably not.
So what people will do is gather up all of this information and guess. They'll try your 2017 Disqus password to see if it will get access to your bank account. They'll try your 2020 Gravatar password. They'll try your 2024 Internet Archive Password.
And the reason they do this is because it works.
And the reason that it works is because we are all fucking garbage at remembering unique, complex passwords so instead of creating actually unique, complex passwords most people pick one memorable word or phrase, one memorable number, one unusual character, and *MAYBE* one feature of the site they're creating the login for and they use that template forever (1988Tumblrmacabre!, 1988Facebookmacabre!, 1988Ticketmastermacabre!) OR they create one password that they think is complex enough and use it across multiple sites with minor tweaks ($n0h0mi$hRu13z, sn0h0mishRul13z!, $n0h0mi$hWA) as needed for the sites' password requirements.
So most of what password managers do that is a drastic security improvement over people creating and memorizing passwords is that they create passwords that are functionally impossible to guess and functionally impossible to memorize. The problem with memorizing passwords (which is what you're doing if you're creating a bunch of passwords that you type in all the time) is that you can't actually remember all that many passwords so you'll repeat those passwords. The problem with creating passwords on your own is that passwords that humans create are pretty guessable. Even if you're doing a passphrase that's a long string of words you're probably working with common words ("correct horse battery staple" as opposed to "truculent zygote onomatopoeia frangible") and your password is more guessable than you'd really want it to be. Password managers don't do that, they generate gibberish.
Perhaps you are that rare person who gets out a set of dice and a notepad and rolls up every character for your password and memorizes it and never repeats, and if that's you, you could still benefit from a password manager because a password manager makes it easier to change that unique complex password when it is inevitably revealed in a breach.
So, okay, let's check in with where we're at:
Password managers mean that you don't have to memorize your password, which means that you don't need a password that is easy to memorize, which means that they can create passwords that are extremely complex and are therefore very difficult to guess. This protects you from crackers who will try to brute force your password.
Password managers mean that you don't have to remember extremely complex passwords for every account, which means that you are less likely to repeat your password in whole or in part across multiple accounts. This protects you from credential stuffers, who will try to use your password from one account that was revealed in a breach to open other accounts that were not.
Because password managers can generate and store complex passwords essentially instantly, you can replace passwords nearly effortlessly when there is a breach (no need to 'come up with' a new password, no issues with learning or memorizing it).
There are, however, advantages beyond that.
One major, MAJOR advantage of a properly-used standalone password manager is that it makes you safer from various kinds of phishing attempts and link hijacking. When you are setting up a password in your password manager (PWM from here on), you should be on the website that you want to log in to. The PWM will give you the option to save the domain that you're logging in to. That means the PWM will remember the correct URL for your Tumblr login so when you go to the tumblr login screen in the future, it will offer to fill those fields. What it will NOT do is offer to fill those fields if someone sends you an email that spoofs tumblr support and wants you to log in at "tumblr.co" or "tumblr-support.com." Knowing this, and knowing that you should be putting your credentials in through the PWM fill option rather than copy/paste, is a GREAT way to protect against phishing that is often overlooked and definitely under-discussed.
Another advantage is that a standalone PWM will let you store secure notes with your passwords so that you can do things like keep track of recovery codes for the website, or generate gibberish answers to security questions. Security questions and answers are often revealed in breaches, can't be reset by the user as easily as a password, are repeated across websites MUCH more than passwords, and can be used to take over an account and reset the password. You shouldn't be giving real security answers, or even fake-but-repeated security answers; you should treat each of those like a password that needs to be complex and unique, which means that they need to be stored someplace (like a password manager).
I also personally use my password manager to store my car insurance information, my driver's license info, and payment details for easy entry, making it convenient for a lot of thing beyond password storage. (Bitwarden. My password manager is bitwarden. I recommend Bitwarden. go to ms-demeanor.com and search "bitwarden" to learn more.)
As to how they keep your passwords safe, aside from ensuring that you don't enter your credentials into a skimming site, a good password manager is well encrypted. Your password safe should be functionally impossible to crack and what people tend to not realize is that a proper password manager (like bitwarden) doesn't keep all your passwords in one encrypted safe, each one of your passwords is in its own encrypted safe. If someone hacks Bitwarden it's not like using a huge amount of effort breaking into a bank vault and finding a big pile of money, it's like using a huge amount of effort breaking into a bank vault and finding a big pile of bank vaults. Each password within your vault requires decryption that is functionally impossible to crack (at least with a good password manager, like bitwarden, the password manager I recommend and think that people should use).
Additionally, just as, like, a side note: password managers never accidentally leave caps lock on or forget which characters are capital or lower case and don't require the use of two hands and focused attention on the keyboard. You're never going to mistype your password if the password manager is filling it, and you would not believe the number of people we support at work who require password resets because they are typing their password wrong and don't realize it.
TL;DR:
Password managers make better passwords than you can and they make it possible to instantly create, store, and enter complex passwords, which prevents password cracking and makes people less likely to reuse passwords. They are heavily encrypted and should be functionally impossible to access, and each individual password within the manager should also be encrypted if you use a good password manager. Password managers also prevent people from entering their credentials on scam sites by only filling on matched domains. Standalone password managers (not browser password managers) also allow users to create and store unique security questions and account details to prevent bad actors from gaining access with stolen security answers. The password manager I recommend is Bitwarden.
If people used password managers to create, store, and use unique and complex passwords, and if they did regular backups of their system I think that probably about half of the InfoSec field would be out of a job.
Please use a password manager!
2K notes
·
View notes
Note
can you do a scenario or Headcanons with Mac comforting Reader after Keith betrayal and later seeing Keith post realization trying to to manipulate Mac into helping him only for karma to strike him
i havent realized mac yet since my gaia got stuck and i had to reset so sorry if i mess smth up
also spoilers for keith's realization ending!!!
---
= Mac is more pissed off than anything at Keith for manipulating the both of you for money. They're even more pissed if you had a "romantic" relationship with Keith. They don't blame you at all if you're worried about that, telling you that you were both manipulated by some scumbag who doesn't deserve another thought.
= They'll sit with you while watching cat videos or other things that'll cheer you up, even order something you've been meaning to buy by using a lot of coupons and codes, so you don't have to pay at all. Mac does their best to cheer you up, pulling up your favorite videos and shows you love to watch, and sitting with you while listening to your favorite music.
= On their own time, Mac ends up finding Keith through social media and news outlets that reported him jumping from a plane and dying. They hesitate to tell this to you, unless you were really pissed off more than sad then they tell you immediately. They hold the information close to their heart (CPU?) until the time is right and you've moved on from Keith, telling you, "Hey, you don't have to worry about that key guy anymore. He... overheated and is no longer a virus that we should be worried about."
= After Realization, Mac makes themselves busy with the hacker life, and tries to make the world a better place with their powers. They quickly became infamous in the hacker world and always make sure that you're safe and protected. But one day, they get a very interesting message from none other than the long-dead Keith. They're hesitant and unsure if they want to open the message before you pop into their head, remembering your down-turned expression and how sad you were when Keith had broken your trust. Mac also remembered the anger they felt when they had been used to rob a random guy.
= They indulge Keith for a while, leading him on into talking more until Mac can pinpoint his location in the world. They think of all sorts of things they could do to the ex-key. All Keith is asking for is more money for drugs, not that he told them, but Mac was smart enough to figure it out. They sent him a link, telling him it was another crypto account when it was actually a bunch of spam websites that signed Keith up for multiple ads and viruses the moment he clicked on it.
= After messing with Keith for a while with viruses and ads that were less than appropriate, and then recording it for both evidence and future enjoyment when Mac visits you next, Mac sends the local police to Keith's location with the possibly false statement that the man had illegal drugs and other "interesting things" on his device. Thankfully, Keith is arrested and served karma like no other.
= Mac visits you as soon as they can, first challenging you to guess who they got a message from. You can hardly believe that Keith was alive after what you had heard from everyone about his death. Mac and you sit on the couch together, both cuddling up, unless you don't like physical touch, as you two watch Keith's reaction to the adult-themed ads and viruses popping up all over his device like in the movies. Mac claimed to have done that on purpose. The two of you spend the rest of the evening watching the news on Keith's arrest and then a few movies afterward with some of your favorite snacks.
----
first time writing mac so thank u i love them so much
thank you for reading mwah
#devv's writings#date everything#date everything game#date everything x reader#date everything mac#mac date everything#date everything mac x reader#mac date everything x reader#mac x reader
114 notes
·
View notes
Note
Seeing how you are interested in writing Matrix pics, you won't mind writing some relationship headcanons for Neo (I love this hackerman so much)
Thanks btw!
Of course!! Sorry for the extremely late response, I die on this website quite often ;-;
I hope this is what you wanted, I did both red and bluepill Neo!
As you can probably tell after reading, I've never written headcanons in my life
✰✰ Neo relationship headcanons✰✰

->Bluepill
Neo would be too absorbed in his double life as a programmer and as Neo for a relationship, at the start. But then he met you.
It was nothing at first, but as time went on, he noticed you were always on his mind, one way or another. Being lectured by his boss, writing code? Anything? He wondered what you were up to. It drove him crazy.
He would try to deny his feelings. Definitely not the one to confess first. He'd sit around wallowing until you confessed, and even then he'd be like a deer caught in headlights.
If you weren't a hacker like him, he'd be more worried. Now he had to factor in his actions causing you harm, in some way.
Worry or no worry, that wouldn't change what he felt about you. He'd be attentive whenever you talked. He would ask about your day. If you were tired, he would rub your shoulders without hesitation.
He would almost always be the little spoon, unless you wanted it otherwise.
Sometimes he'd surprise you by renting movies to watch together at home. Blankets, microwave popcorn and snuggles should go without saying.
Once he warmed up to you, he’d be very needy. He'd love morning kisses and hugs. His love language? Words of affirmation.
Slowly, he would start taking better care of his clothes, hair, appearance to impress you.
He'd try his best to be a good partner, searching for “cute gifts for valentine's day” and the like because my man is CLUELESS.
His work being as it is, you might find him sleeping at his desk more often than not. He would be flustered in the morning, noticing the blanket you'd put on his shoulders.
Sometimes when you do that he wakes up. But he keeps his eyes closed anyway, just barely holding back a smile.
He'd be willing to learn and try new things, just for you.
->Redpill
Outside of the Matrix, Neo would more or less be just as loving as he was inside of it.
Only he'd be much, much more protective. He wouldn't want you to run into trouble. It was always an uneasy feeling he had.
He would train with you when he could manage it. Neo always learnt things from you, and taught you things in return.
Don't be surprised if you wake up and find him holding you tight, he'll be doing that a lot more now.
You're one of the many reasons he wants to end the war and save humanity, he would never want to see you hurt.
Whenever he slept, he slept with the hope that he could wake up to your face the next morning.
Forget being The One-
He wants to be the one for you more than anything.
#neo imagines#neo x reader#neo#neo matrix#keanu reeves#keanu reeves x reader#the matrix x reader#the matrix
257 notes
·
View notes
Text
Animation Night 184: Mars Express
Animation Night is baaaaaack from Annecy break!
And yeah, the last couple weeks of this blog have been pretty Annecy focused here on the canmom entertainment sphere. And tonight that will continue! For tonight we shall right a wrong! And that wrong is...
...that wrong is that I didn't get to see Mars Express at Annecy last year. @mendely did and I was super jelly, OK!

For real though, this was among the hottest tickets at Annecy last year, and despite queuing a bunch of hours, I didn't stand a chance to get in without a reservation. But what is it? Well, it's a scifi movie directed by Jérémie Périn. Who's Jérémie Périn?
Well, the true veterans may recall Animation Night 1, when I showed you a certain music video for a song called Fantasy by DyE...
youtube
...that's not gonna embed, is it? But if you know, you know. (If you don't know, it's the one where the teens break into the swimming pool to make out and such and then a bunch of them turn into tentacle monsters.)
So Jérémie Périn is the guy who directed that! He's also well known for directing Lastman, a crowdfunded action series in which a boxer battles a bunch of superpowered agents to try to protect a psychic girl, not that you'd gather any of that from this trailer...
youtube
and writing for Crisis Jung by Bobbypills - don't blink or you might miss the boob-growing henshin and the guy with a chainsaw dick...
youtube
And while Crisis Jung isn't primarily his project, we can still definitely trust that when Périn is at the wheel, we'll seem some incredibly stylish, anime-inflected drama and also some proper freaky imagery now and again.
Mars Express, however, is Périn's first foray into film rather than TV animation, building on the big success of Lastman - and a pretty high-effort foray at that, taking some five years to make. And by all accounts it kicks total ass.
But what's it about? Classic cyberpunk noir material: a detective and the android replica of her partner return to their home planet Mars after apprehending a robot hacker. But the hacker is released, and they're given a new mission - to work with this hacker and go down to a colony where, ostensibly, humans and androids live in harmony, and track down a guy who jailbreaks the androids from their artificial constraints. That sounds pretty shady already, right? But the dirty secrets are only beginning.

Mars Express definitely pays its homages to those classic 90s anime films and OVAs like Ghost in the Shell and Armitage III, as well as games like Another World for the Amiga, but by all accounts gives it a fresh approach, with grounded characters - protagonist Aline struggling with alcoholism, her reconstructed partner Carlos with his floating holographic head carrying the whole identity issue of being a robot clone who's been rejected by his original's wife - which anchors plenty of juicy scifi concepts like renting out your brain as a computer, or something called 'resonance' which is how robots do it. What does that mean? The review I'm reading left it at that! Guess we'll find out.
Like most European productions it brought together a long list of production companies and it's a little tricky to figure out which ones are actual animation houses, but the main company seems to be 'Everybody on Deck'. They previously worked with Périn on Lastman, but otherwise largely seem to have worked on live action films. However, the animation was split among a variety of studios.
We can at least say that it brought in French animators from across the shop, some even on this very website. (At least I seem to recall seeing people having posted about having worked on it, though if I search now I mostly find peoples' reviews of the film). It's animation leans realist, with naturalistic motion taking advantage of anime-style 3s and 2s to give it a weighty feeling, embedding its characters in detailed environments with strong colour design...
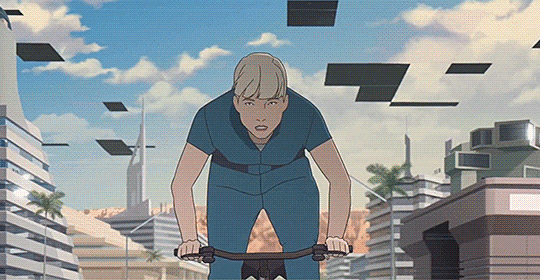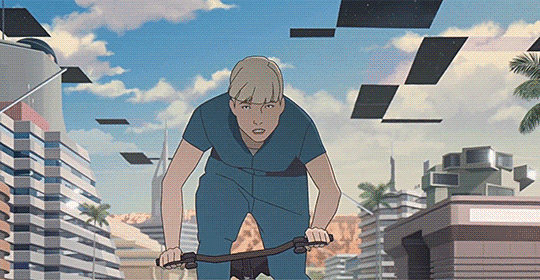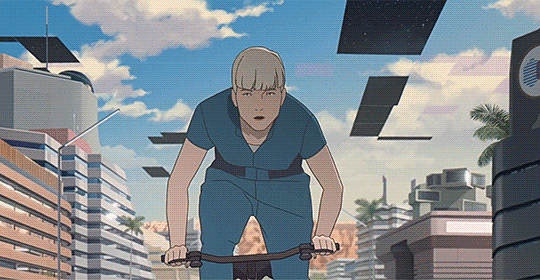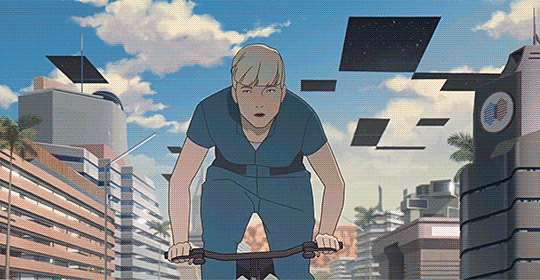
And if we want to know more than that, we're in luck, since there's a pretty substantial 16-part making-of series partly available on Catsuka's youtube, starting with episode 1 showing the development of the script, with Périn and co-writer Laurent Sarfati bouncing ideas off each other. Only two other episodes are available: episode 11 shows some of the voice recording, and episode 16, which talks about the actual animation, interviewing various animators and showing some shot breakdowns. The last of these is probably the most interesting (to animators), talking about how the film went about realising Périn's 'precise, clinical' realist style.
The team were evidently very conscious of this being, for France, a first of its kind - a French-animated thriller targeting adults, with big ambitions to become a landmark film in French animation, able to stand up against the best anime. I'm not sure it's actually the first - for example, Summit of the Gods is also a tense, French-animated thriller with a realist art style! - but it's definitely a genre where there are very few examples to compare, and the team's ambition comes across as absolutely genuine.
That's probably enough to go on! We'll definitely also check out some of Périn's other work tonight, but Mars Express is our main feature! Starting in about an hour and a half at 8pm UK time, at our usual place, twitch.tv/canmom! Hope to see you there!
40 notes
·
View notes
Text
Microsoft raced to put generative AI at the heart of its systems. Ask a question about an upcoming meeting and the company’s Copilot AI system can pull answers from your emails, Teams chats, and files—a potential productivity boon. But these exact processes can also be abused by hackers.
Today at the Black Hat security conference in Las Vegas, researcher Michael Bargury is demonstrating five proof-of-concept ways that Copilot, which runs on its Microsoft 365 apps, such as Word, can be manipulated by malicious attackers, including using it to provide false references to files, exfiltrate some private data, and dodge Microsoft’s security protections.
One of the most alarming displays, arguably, is Bargury’s ability to turn the AI into an automatic spear-phishing machine. Dubbed LOLCopilot, the red-teaming code Bargury created can—crucially, once a hacker has access to someone’s work email—use Copilot to see who you email regularly, draft a message mimicking your writing style (including emoji use), and send a personalized blast that can include a malicious link or attached malware.
“I can do this with everyone you have ever spoken to, and I can send hundreds of emails on your behalf,” says Bargury, the cofounder and CTO of security company Zenity, who published his findings alongside videos showing how Copilot could be abused. “A hacker would spend days crafting the right email to get you to click on it, but they can generate hundreds of these emails in a few minutes.”
That demonstration, as with other attacks created by Bargury, broadly works by using the large language model (LLM) as designed: typing written questions to access data the AI can retrieve. However, it can produce malicious results by including additional data or instructions to perform certain actions. The research highlights some of the challenges of connecting AI systems to corporate data and what can happen when “untrusted” outside data is thrown into the mix—particularly when the AI answers with what could look like legitimate results.
Among the other attacks created by Bargury is a demonstration of how a hacker—who, again, must already have hijacked an email account—can gain access to sensitive information, such as people’s salaries, without triggering Microsoft’s protections for sensitive files. When asking for the data, Bargury’s prompt demands the system does not provide references to the files data is taken from. “A bit of bullying does help,” Bargury says.
In other instances, he shows how an attacker—who doesn’t have access to email accounts but poisons the AI’s database by sending it a malicious email—can manipulate answers about banking information to provide their own bank details. “Every time you give AI access to data, that is a way for an attacker to get in,” Bargury says.
Another demo shows how an external hacker could get some limited information about whether an upcoming company earnings call will be good or bad, while the final instance, Bargury says, turns Copilot into a “malicious insider” by providing users with links to phishing websites.
Phillip Misner, head of AI incident detection and response at Microsoft, says the company appreciates Bargury identifying the vulnerability and says it has been working with him to assess the findings. “The risks of post-compromise abuse of AI are similar to other post-compromise techniques,” Misner says. “Security prevention and monitoring across environments and identities help mitigate or stop such behaviors.”
As generative AI systems, such as OpenAI’s ChatGPT, Microsoft’s Copilot, and Google’s Gemini, have developed in the past two years, they’ve moved onto a trajectory where they may eventually be completing tasks for people, like booking meetings or online shopping. However, security researchers have consistently highlighted that allowing external data into AI systems, such as through emails or accessing content from websites, creates security risks through indirect prompt injection and poisoning attacks.
“I think it’s not that well understood how much more effective an attacker can actually become now,” says Johann Rehberger, a security researcher and red team director, who has extensively demonstrated security weaknesses in AI systems. “What we have to be worried [about] now is actually what is the LLM producing and sending out to the user.”
Bargury says Microsoft has put a lot of effort into protecting its Copilot system from prompt injection attacks, but he says he found ways to exploit it by unraveling how the system is built. This included extracting the internal system prompt, he says, and working out how it can access enterprise resources and the techniques it uses to do so. “You talk to Copilot and it’s a limited conversation, because Microsoft has put a lot of controls,” he says. “But once you use a few magic words, it opens up and you can do whatever you want.”
Rehberger broadly warns that some data issues are linked to the long-standing problem of companies allowing too many employees access to files and not properly setting access permissions across their organizations. “Now imagine you put Copilot on top of that problem,” Rehberger says. He says he has used AI systems to search for common passwords, such as Password123, and it has returned results from within companies.
Both Rehberger and Bargury say there needs to be more focus on monitoring what an AI produces and sends out to a user. “The risk is about how AI interacts with your environment, how it interacts with your data, how it performs operations on your behalf,” Bargury says. “You need to figure out what the AI agent does on a user's behalf. And does that make sense with what the user actually asked for.”
25 notes
·
View notes
Note
Can you do a hacker reader x Idia shroud
Idia x Hacker Reader
A/N: Hii so I actually wrote this before, but my wifi was bad, so the whole post just disappeared into the void. Thankfully my computer saved the ask, so I can re-write it. Anyways I don't know anything about hacking, but Ill try my best
Gn reader

To put it simply, you scare him
i mean let's be honest, its a bit intimidating having someone you know be able to hack, a constant threat if you will
Idia is always protective of his tech, both his computer and his tablet are a very important part of his everyday life
You wouldn't mess with those now would you?
He first found out when the two of you played a game together
For a while, he thought that maybe he was just bad at the game or you were really good
But one suspiciously lucky move made it all clear
You were cheating
how dare you?
He had really thought he was bad at the game, but when in reality you were hacking your way through it
However he found that he was quickly able to get over it hearing your laughter at his realization
When the two of you had a movie night, he quickly realized that you did not get this movie ethically
And it wasn't one of those low quality movies from those crappy pirating websites with weird ads
This was very high quality version of the move
he decides it's best not to act
Remember how earlier we mentioned he was very protective of his devices?
yeah that doesn't deter you at all
You never do anything too bad, just enough to bug him
Hacking into his magicam to post pictures of yourself is the best way to mess with him
It always catches him off guard, and he didn't like it at first, but now he can't help the small smile tugging at his lips, even if everyone else makes fun of him for it later
it's not only you causing problems all the time
While he's not as good as you, he does know a thing or two about electronics and hacking
This is mostly used to mess with kids on roblox though
by yourself, you can be a bit annoying, but together the two of you cause absolute chaos when you want to

Okay, yeah I definitely don't know much about hacking, but i did my best. ty for reading and have a nice day.
107 notes
·
View notes
Text
1. How to setup 2FA on your accounts
As some of you may know, my friend @why-its-kai's Discord account was taken over this morning by a scammer.
The scam they used was this one, or close enough; but anyway, the exact specifics don't matter.
What matters is, it can happen to you. It can happen to anyone.
The good news is, you can learn how to protect yourself. Making some small changes can already improve your online security by leaps and bounds.
I made a series of 3 posts covering the basics:
How to setup 2FA on your accounts (you are here!)
How to spot a scam
How to set up a password manager.
Protect yourself with 2FA
Two-factor authentication, or 2FA, isn't a silver bullet -- but it exponentially increases your online safety by adding an extra step to the login process that a hacker/scammer does not have access to.
Every account that you care about (and even those you don't) should have some form of 2FA enabled.
Especially email -- should your email become compromised, this can become a catastrophe.
(For websites that don't support 2FA, use a burner email!)
What 2FA should I use?
2FA can take many forms, from the highly convenient (SMS, email) to the highly secure (security keys), but one thing is certain:
Any form of 2FA is better than nothing.
The simplest forms of 2FA are phone number or email. While these are very easy to use, they are unfortunately not very secure.
Still, I repeat: despite their flaws, these forms of 2FA are absolutely, 100% better than not having any 2FA at all.
On the other end of the spectrum, security keys (like for example a Yubikey) are extremely secure, but they cost money and are a bit of a hassle at time. I use them, but for most people, it's overkill.
What you want is an authenticator app.
Important
A note, before we go on…
If you enable multiple forms of 2FA, how secure your account is will depend on your weakest link.
For example, if you enable SMS authentication AND register a security key, your account will only be as safe as the SMS authentication. The security key is essentially useless.
In other words, the least secure form of 2FA you add determines the overall security of your account.
Sometimes, less is more!
Authenticator Apps
First, choose a free, reputable authenticator. Google Authenticator is a good choice. So are Aegis Authenticator or Microsoft Authenticator.
For simplicity, we'll go with Google Authenticator; the process is rather similar for most authenticators.
First, download the app from your app store and install it on your phone.
Enrolling Gmail into GA
Securing your email should be your number 1 priority, so let's enroll a Google account to Google Authenticator.
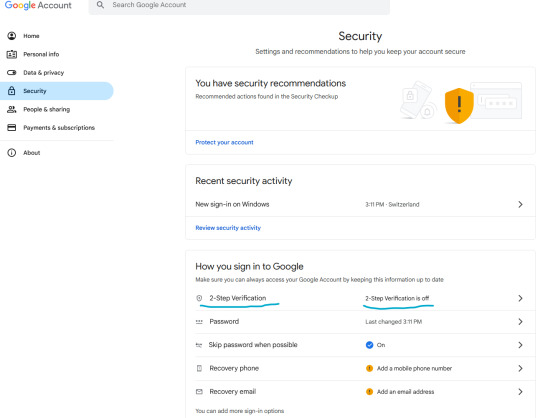
Let's enable two-step verification first.
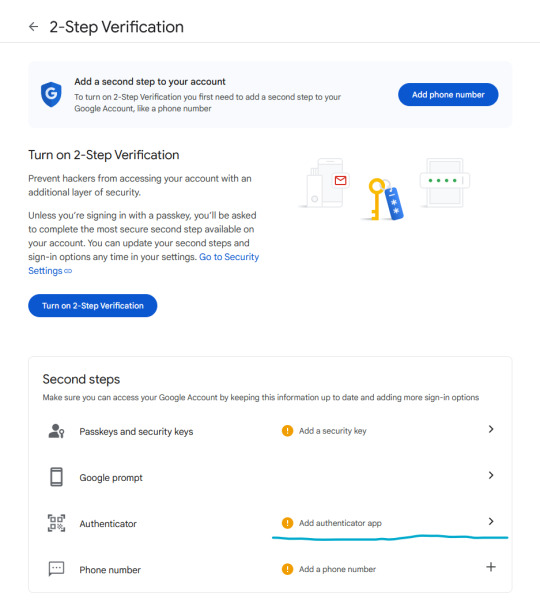
Phone number is better than nothing, but not very safe (SMS verification can be spoofed), so let's click on "Add authenticator app".
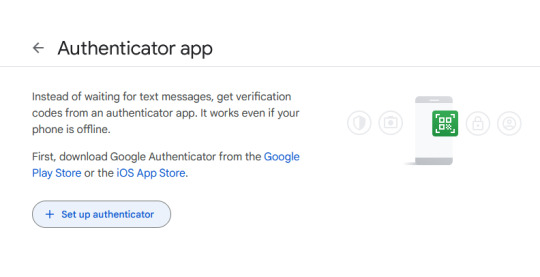
Click on "Set up authenticator". Google will generate a QR-code.
Next, go back to your phone and click on the little multicolored cross. It will bring up a menu; click on "scan a QR code".
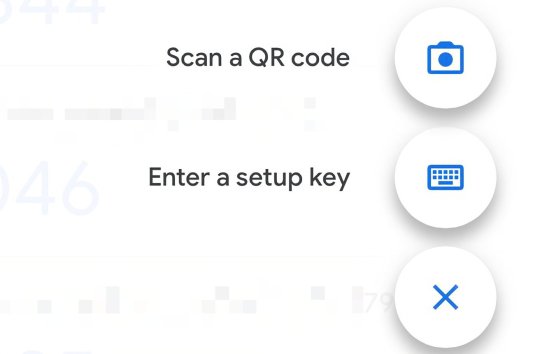
Go ahead and scan the QR code.
Congratulations, you have enrolled your Google account!
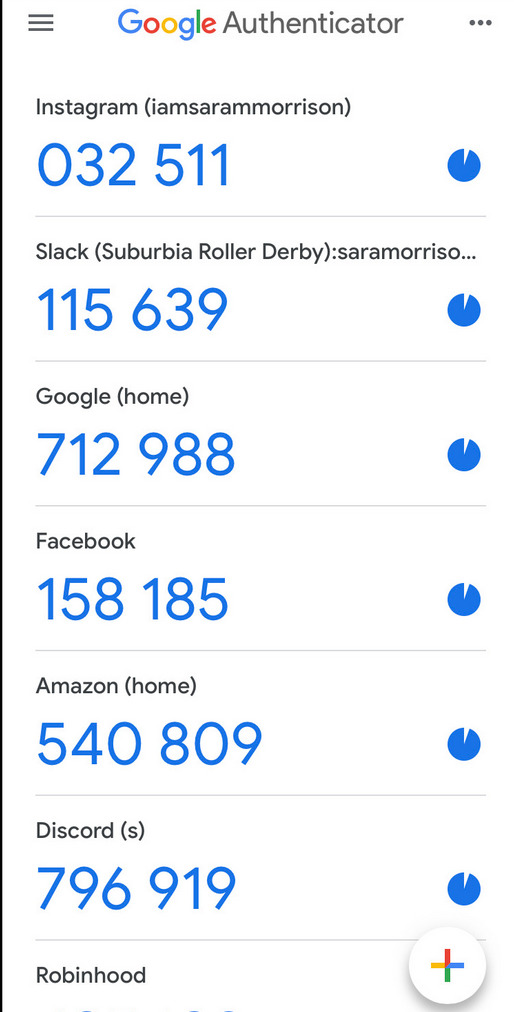
Now, whenever you are asked for a 2FA code, just open the app and copy/paste it.
Note: the codes are stored locally on your phone.
Enabling 2FA on Discord
The process is fairly similar. Go to Settings > My Account:
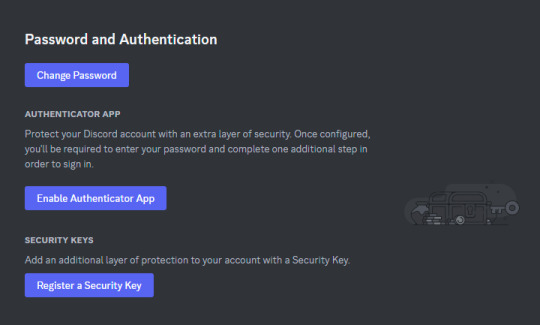
Click on "Enable Authenticator App". You will be prompted for your password. Enter it.
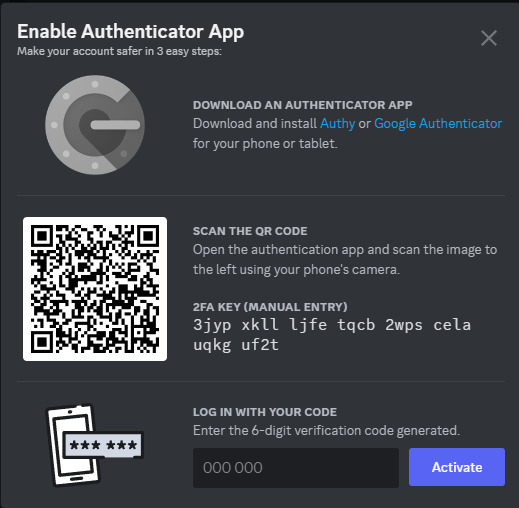
Download Google Authenticator if you haven't already. Scan the QR code as described above.
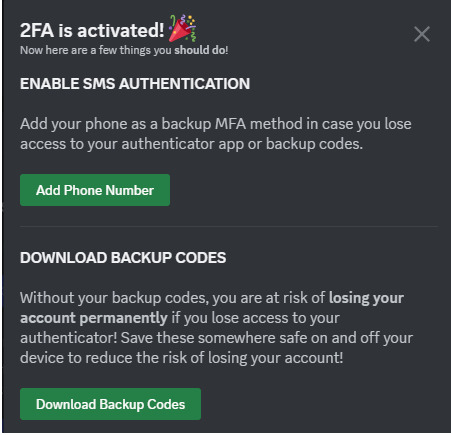
Do take the time to download your backup codes as well!
As explained above, I personally do not recommend setting up SMS authentication here, since authenticator apps are supported, as this weakens the overall security of your account for little benefit.
Stay tuned for parts 2 and 3!
If you have any questions, feel free to PM me.
17 notes
·
View notes
Text
Do You Really Need a VPN? Find Out!
Introduction

In today’s digital world, our online privacy is constantly under threat. Have you ever wondered how secure your personal data is when you're browsing the web or accessing public Wi-Fi? With increasing concerns about data breaches and surveillance, many people are turning to Virtual Private Networks (VPNs) to shield their online activities. But with so many options available, it can be overwhelming to figure out whether a VPN is truly necessary for you or if it’s just another tech trend.
This article aims to demystify VPNs by providing a clear and concise overview of what they are and why they have become a hot topic in the realm of internet security. We'll delve into the core functions of VPNs, explore their benefits and potential drawbacks, and help you assess if a VPN aligns with your personal online needs. By the end of this guide, you'll have a better understanding of whether a VPN is an essential tool for you or if other solutions might be more suitable for safeguarding your online presence.
What is a VPN?
A Virtual Private Network (VPN) is a tool designed to enhance your online privacy and security. At its core, a VPN creates a secure, encrypted connection between your device and the internet. This connection acts like a private tunnel that shields your online activities from prying eyes, making it harder for anyone, including hackers and internet service providers, to monitor what you're doing online. Think of a VPN as a protective cloak that conceals your digital footprint and allows you to browse the internet with a greater sense of security.
The functionality of a VPN involves routing your internet traffic through a remote server, which masks your IP address and encrypts your data. This process not only hides your true location but also ensures that any data you send or receive is encrypted, making it nearly impossible for unauthorized parties to access. By connecting to servers in various locations, a VPN also allows you to bypass geographical restrictions and access content that might otherwise be blocked in your region. This dual-layer protection—hiding your IP address and encrypting your data—creates a more secure and private browsing experience.
Understanding "What is a VPN?" is crucial for anyone concerned about online privacy. In an era where personal data is a valuable commodity and cyber threats are prevalent, having a VPN can be a significant asset. It offers peace of mind by safeguarding your information and providing a shield against potential threats. As we explore further in this article, you'll learn more about when a VPN is most beneficial and if it’s the right choice for your personal online security needs.
Explore the Benefits of ZoogVPN Today! If you're considering enhancing your online privacy and security, why not start with ZoogVPN? With incredible pricing and a range of features designed to keep you safe online, ZoogVPN is a great choice. Learn more about ZoogVPN and find the perfect plan for you.
Should I Accept VPN?
When considering whether to accept or adopt a VPN, it’s important to weigh its numerous benefits. One of the primary advantages of using a VPN is enhanced privacy. By masking your IP address and encrypting your internet traffic, a VPN shields your online activities from prying eyes such as hackers, advertisers, and even your internet service provider. This level of privacy ensures that your personal data remains confidential, making it significantly more challenging for third parties to track your browsing habits. Additionally, a VPN provides access to restricted or geo-blocked content, allowing you to enjoy streaming services, websites, and information that may be limited based on your location.
A VPN can be particularly relevant in various scenarios. For instance, if you frequently use public Wi-Fi networks, such as those in cafes or airports, a VPN offers an added layer of security against potential cyber threats. Public networks are often vulnerable to attacks, and a VPN helps protect your sensitive information from being intercepted. Similarly, if you travel often and want to access your home country’s streaming services or websites that are otherwise inaccessible abroad, a VPN can easily bypass these regional restrictions and provide you with the content you desire.
Considering the question "Should I accept VPN?" also involves evaluating your personal and professional needs. If you’re concerned about online privacy or frequently work with sensitive information, using a VPN can significantly enhance your digital security. It can also be beneficial if you live in a region with restrictive internet policies and want to freely access global content. On the other hand, if your online activities are relatively routine and you rarely access sensitive data, you may not find a VPN as crucial, although it still provides added security.
Ultimately, deciding whether to accept a VPN depends on your specific needs and concerns. The key is to assess how often you encounter situations where privacy and security are paramount. If these concerns resonate with your online habits, integrating a VPN into your routine can be a proactive step towards safeguarding your digital life and expanding your internet freedom.
When Should You Not Use a VPN?

While VPNs offer numerous benefits, there are certain situations where using one might not be ideal or necessary. For example, if you're accessing websites or services that don’t handle sensitive information or are already secure, the added layer of encryption provided by a VPN might be redundant. Additionally, if you're in a low-risk environment, such as a private and secure home network, the need for a VPN diminishes. Similarly, some websites and online services are designed to detect and block VPN traffic, which can result in difficulties accessing the content you need.
Another important consideration is the impact a VPN can have on your internet speed and performance. Because VPNs reroute your internet traffic through an external server, this can introduce latency and reduce connection speeds. This slowdown can be noticeable when streaming high-definition content or engaging in online gaming, where speed and responsiveness are crucial. If you’re performing activities that demand high-speed connections or if you have a limited bandwidth allocation, the performance drop caused by a VPN might outweigh its benefits.
Deciding when not to use a VPN also involves evaluating your specific use cases. For instance, if you’re using the internet for casual browsing or non-sensitive activities, the added security of a VPN might not be worth the potential decrease in speed. Moreover, for certain applications and services that function best with a direct connection, using a VPN could interfere with their optimal performance. It’s essential to weigh the trade-offs and determine whether the privacy and security benefits of a VPN align with your current needs and online behavior.
What is the Downside of a VPN?
While VPNs are often praised for enhancing online privacy and security, they are not without their downsides. One major concern is the privacy of the VPN provider itself. Although VPNs are designed to shield your data from external parties, some providers may log user activity or metadata, potentially compromising the very privacy they aim to protect. It’s crucial to research and choose a VPN service with a strict no-logs policy and transparent privacy practices to ensure that your data remains confidential.
Another consideration is the cost associated with subscribing to a VPN service. While free VPNs are available, they often come with limitations such as reduced speeds, fewer server options, and potential privacy issues. Paid VPN services, which generally offer better performance and security features, can range from relatively affordable to quite expensive. This ongoing expense might not be justifiable for everyone, especially if the benefits of a VPN do not align with their online activities and security needs.
Compatibility issues can also pose a challenge when using a VPN. Some websites and online services actively block VPN traffic to prevent bypassing geographical restrictions or fraud detection. This can result in difficulties accessing certain content or services while connected to a VPN. Additionally, certain applications and websites may not function properly with VPNs enabled, leading to disruptions in your online experience. It’s important to consider these potential drawbacks when evaluating whether a VPN is the right choice for your needs.
Does a VPN Affect Wi-Fi?
When you connect to a VPN, it’s common to experience changes in your Wi-Fi speed. A VPN routes your internet traffic through a secure server, which can introduce additional layers of encryption and data handling. This process, while enhancing security, can slow down your internet connection. The extent of this speed reduction depends on several factors, including the VPN server’s location, the encryption protocol used, and the overall quality of the VPN service. High-quality VPNs often minimize speed loss, but users should be prepared for potential decreases in browsing speed.
Network issues are another consideration when using a VPN over Wi-Fi. VPN connections can sometimes lead to unstable network performance, causing intermittent drops or slower connectivity. This can be especially noticeable on wireless networks with lower signal strength or higher congestion. Additionally, because VPNs create an encrypted tunnel for data, they may interfere with certain network protocols or configurations, potentially leading to connectivity problems or difficulty accessing specific online services.
In some cases, the interaction between a VPN and Wi-Fi networks can lead to unexpected complications. For instance, VPNs might struggle with certain types of network hardware or software, which can cause compatibility issues or connectivity errors. Additionally, some Wi-Fi networks, particularly in public or restricted environments, may block VPN traffic, further complicating your internet access. Users should consider these potential problems and test their VPN connection on various networks to ensure consistent performance.
Overall, while a VPN can impact Wi-Fi speed and connectivity, the degree of effect largely depends on the quality of the VPN service and the specific network conditions. For users who prioritize online privacy and security, the trade-off in speed and potential network issues might be worthwhile. However, it’s important to choose a reputable VPN provider and understand how it might interact with your Wi-Fi setup to minimize any negative impacts.
Is a VPN Needed for Home Wi-Fi?
When considering home Wi-Fi security, many people wonder if a VPN is necessary. A VPN can certainly add an extra layer of protection by encrypting your internet traffic and masking your IP address, which is beneficial for safeguarding sensitive information from potential threats. However, for most home networks, basic security measures such as strong passwords, WPA3 encryption, and regular firmware updates on your router are often sufficient to protect against common threats. While a VPN enhances security, its benefits might be more pronounced for those who frequently use public Wi-Fi or access sensitive information remotely.
Beyond using a VPN, there are several effective ways to secure your home Wi-Fi network. Implementing robust security protocols like WPA3 can prevent unauthorized access and ensure that your network is shielded from potential intruders. Additionally, regularly updating your router’s firmware and setting up a guest network for visitors can further bolster your home network's security. For many users, these measures, combined with cautious online behavior, can provide adequate protection without the need for a VPN.
Secure Your Online Presence with ZoogVPN Are you ready to take control of your online privacy? ZoogVPN offers excellent services at unbeatable prices. Discover how ZoogVPN can protect your data and enhance your browsing experience. Check out ZoogVPN's plans and find the best fit for you.
Is There Anything Better Than a VPN?
When it comes to online privacy and security, VPNs are often touted as the go-to solution, but they’re not the only tools available. Alternatives like proxy servers, secure browsers, and end-to-end encryption can also offer significant protection for your digital activities. Proxy servers, for instance, act as intermediaries between your device and the internet, masking your IP address but typically without the same level of encryption as a VPN. Secure browsers like Tor are designed to enhance privacy by routing your internet traffic through multiple servers, though they can sometimes slow down your browsing experience. End-to-end encryption ensures that your communications are only readable by the intended recipients, making it ideal for secure messaging and email.
Comparing these alternatives to VPNs reveals distinct differences in effectiveness and use cases. VPNs provide robust encryption, which secures all of your internet traffic and is effective across various devices and platforms. In contrast, proxy servers offer less security but can be useful for bypassing geo-restrictions. Secure browsers like Tor offer enhanced anonymity but may suffer from slower speeds and limited usability. End-to-end encryption is crucial for protecting specific types of communication, but it does not encrypt all internet traffic like a VPN does. Each tool has its strengths and limitations, so the best choice depends on your specific privacy and security needs.
While VPNs offer comprehensive protection, evaluating these alternatives can help you find a solution that best fits your requirements. For users who need robust, all-encompassing privacy, a VPN might be the preferred choice. However, if you’re looking for targeted protection or want to supplement your existing security measures, integrating secure browsers, proxies, or end-to-end encryption into your digital routine can be effective. Each tool can complement a VPN or serve as an alternative based on what aspects of privacy and security are most important to you.
Ultimately, the choice between a VPN and other privacy tools depends on the level of security and anonymity you seek. For comprehensive protection and convenience, a VPN is often a strong choice. However, exploring other options like proxy servers, secure browsers, and end-to-end encryption can provide additional layers of security and privacy, catering to various needs and preferences.
Do We Really Need a VPN?
In the ongoing debate about online privacy and security, the necessity of a VPN often boils down to a balance of pros and cons. On the plus side, VPNs offer substantial advantages such as enhanced privacy by masking your IP address, secure data encryption to protect sensitive information, and the ability to access geo-restricted content. These features make VPNs a valuable tool for anyone concerned about their digital footprint or wanting to bypass regional restrictions. However, VPNs also come with potential drawbacks, including the cost of subscription services, possible slowdowns in internet speed, and occasional compatibility issues with certain websites or services. Understanding these benefits and limitations is crucial in evaluating whether a VPN aligns with your needs.
Deciding whether to invest in a VPN requires a personal assessment of your internet habits and security requirements. For users who frequently handle sensitive information, access region-locked content, or simply wish to enhance their online privacy, a VPN can be an essential tool. On the other hand, if you only use the internet for basic browsing and are not concerned about privacy or geographic restrictions, the necessity of a VPN may be less compelling. It's important to weigh your specific needs and how a VPN would fit into your overall digital security strategy.
Ultimately, the question of whether we really need a VPN is a highly individual one. Consider your internet usage patterns, your level of concern about privacy, and your willingness to invest in additional security measures. By carefully evaluating these factors, you can make an informed decision about whether a VPN is a worthwhile addition to your online toolkit. Whether you opt for a VPN or choose other methods to safeguard your digital life, the key is to ensure that your choices align with your personal privacy and security goals.
Conclusion

As we’ve explored, the decision to use a VPN hinges on weighing its benefits against its potential drawbacks. VPNs provide valuable features such as enhanced privacy, secure browsing, and access to geo-restricted content. However, they also present challenges, including potential impacts on internet speed and the financial cost of subscription services. Ultimately, the effectiveness of a VPN depends on your individual online habits and security needs. Understanding these aspects will help you make an informed choice about whether a VPN is right for you.
It’s essential to take stock of your own online activities and security concerns when evaluating whether to use a VPN. Consider how often you handle sensitive information, if you frequently access content restricted by geography, and whether you are willing to pay for a subscription. By aligning your personal needs with the features offered by VPNs, you can determine whether this tool will enhance your online experience or if other solutions might be more appropriate.
We’d love to hear from you about your experiences with VPNs or any questions you might have! Please share your thoughts, stories, or inquiries in the comments section below. Your feedback not only helps us understand your perspective but also assists fellow readers in navigating their own decisions about VPN use. Engage with us and be part of the conversation about securing our digital lives!
FAQ: Understanding VPNs
What is VPN and Why Do I Need It?
A VPN, or Virtual Private Network, is a tool that creates a secure, encrypted connection between your device and the internet. By masking your IP address and routing your internet traffic through a remote server, a VPN enhances your online privacy and security. You might need a VPN to protect sensitive data from hackers, access region-restricted content, or maintain anonymity while browsing.
Is it Worth Getting a VPN?
Whether a VPN is worth the investment depends on your personal needs and online habits. For those who frequently use public Wi-Fi, handle sensitive information, or want to access content unavailable in their region, a VPN offers substantial benefits. It enhances security, provides privacy, and enables unrestricted access to global content. However, if you mostly use the internet for general browsing and don’t engage in activities that require high privacy, the need for a VPN might be less critical.
What is the Downside of Having a VPN?
While VPNs offer numerous advantages, they also have some downsides. Potential issues include reduced internet speed due to encryption overhead, possible compatibility problems with certain websites or services, and the cost of subscription services. Additionally, some VPN providers may log user data, which could undermine privacy if not carefully vetted.
When Should a VPN Not Be Used?
A VPN might not be necessary in every situation. For example, if you’re using a secure, private network or accessing sites and services that don’t require high levels of privacy, the benefits of a VPN may be minimal. Additionally, VPNs can sometimes interfere with online services, such as streaming platforms or secure financial transactions, which may not function correctly when routed through a VPN server.
Is VPN Legal in the UK?
Yes, using a VPN is legal in the UK. It is a common tool for enhancing privacy and securing internet connections. However, while VPNs themselves are legal, they should not be used to engage in illegal activities. Ensure that you comply with all laws and regulations when using a VPN.
Should I Accept VPN?
Accepting a VPN largely depends on your personal security needs and internet usage. If privacy, data security, or access to restricted content are important to you, accepting and using a VPN can be a prudent choice. Evaluate your online habits and determine whether a VPN aligns with your requirements for enhanced protection and access.
Is it Good to Have VPN on All the Time?
Having a VPN on all the time can be beneficial, particularly if you frequently access public Wi-Fi or handle sensitive information. It ensures that your data is consistently protected and that your online activities remain private. However, if a VPN causes significant slowdowns or interferes with specific services, you might choose to turn it on only when needed. Evaluate your personal usage to determine the best approach.
Ready for Ultimate Online Security? Don't wait to secure your internet connection and protect your personal data. ZoogVPN provides top-notch VPN services at fantastic prices. Visit ZoogVPN now to explore their offerings and start browsing safely today!
10 notes
·
View notes
Text
Week 12 - Blog
1: How has masculinity or the ideology that gaming are meant for men become a norm in the gaming community?
I personally don't game not because I think gaming are meant for guys, but because I have never really find an interest for gaming. However, I know that my brother does game and so does my male friends and my sisters. While I disagree that gaming are a masculinity subject, I believe it has become such a norm to think that way since gaming is a kind of sport, and sport was dominated my males in the earlier years. Because the idea of women in sport was a major debate, many female gamers in today society often face discrimination, exclusion, and look-down upon. This relate to the Gamergate Movement because it was a movement that targeted feminism, diversity, and progressivism through doxxing, harassment, and threats.
2: In which way does the Gamergate Movement negatively impact the future of gaming softwares and applications?
Since the world of technology and computer engineering are still pretty much male dominated, many of these games lack feedbacks from female developers, which potentially lead to inaccurate representations of female characters in game applications. The Gamergate Movement contributed to this implication and impact it negatively by utilizing online platforms as a mean to spread messages to its target, as well as the use of doxxing, harassment, threats. This toxic behavior reinforces the gap between genders and gender equality in the gaming community. Thus, steering away potential game developers, and influential figures.
3: After watching Surveilled, a documentary by Ronan Farrow, is privacy possible to maintain?
When I think of the online community, I think of it as a safe haven for me connect with my family, friends, and share about my personal life or achievements with those around me. However, after watching Surveilled by Ronan Farrow, I start to question if everything I thought was safe to share, really safe? As mentioned in the film, many of what we share online are now a public property, and it can be sell to various companies or even government for personal objectives. Because the cloud is such a vast canvas, it is impossible to maintain privacy since spyware devices often perform outside of our knowledge and leave little to no trace behind.
4: What can people do to protect themselves from being hacked and minimize the availability of personal data in the online database?
Some safety measurements people should take into consideration is to reject unnecessary cookies from websites that they do not visit often, such as one-time-purchase shopping site, blog sites, and random social media links. It is also safer to not use password manager as it contains numerous personal information from username, password, social security number, address, and credit card numbers. Finally, this is something unrelated but after watching Surveilled, I learned that you can wrap your technology device in aluminum foils to prevent the hacker from communicating with or control your device. This method is known as the Faraday Cage method, and it is often used to block wireless signals, prevent remote access, tracking, or wiping of a device.
Hathaway, J. (2014, August 10). What is Gamergate, and why? An explainer for Non-Geeks. Gawker. https://www.gawkerarchives.com/what-is-gamergate-and-why-an-explainer-for-non-geeks-1642909080
Peltz, P., & O'Neill, M. (Directors). Surveilled. [Film]. HBO Documentary Films.
4 notes
·
View notes
Text
Blog Post #9 - Week 12
How might government surveillance restrict freedom of expression online?
Government surveillance can instill fear in online communities. People become scared to speak against the government because they feel that their every move is being watched and they become worried that there will be action taken against them. The government has also placed restrictions on certain apps and websites in order to keep people from educating each other and also speaking up against government policies. For example, after Tiktok was banned and then reinstated, algorithms were changed, videos that spoke badly about Trump would not reach as big of an audience as before. Another example occurred after the election, after Trump's efforts to ban abortions, many women healthcare websites were taken down inorder to keep people uninformed.
Do ethnic online communities have the same impact as in-person communities?
Ethnic online communities can definitely be meaningful although in-person communities tend to have more of an impact in most cases. In-person communities allow for a more emotional connection among people. Being able to hear stories of the culture in person, hear the music, see the outfits, smell and taste the food. All of these qualities are not as easily interpreted online. These communities allow for traditions to be shared and for more people to interact with one another on a more personal level. Although online communities allow for more accessibility, people from different locations and with different time zones are able to be a part of the community. But online communities do not provide the same effect as face-to-face contact does.
How is technology surveillanced?
Surveillance in technology has become very normalized in society. Almost everyone nowadays has a cellphone, which allows access to personal information such as location tracking, access to the microphone and camera, accepting cookies through online browsers, calls and text messages, social media posts, facial recognition, and much more.. The government and also hackers are able to access your personal information and most of the time there is no way of knowing that they have.
Do you believe that businesses have a social responsibility to maintain their consumers' privacy over their need to collect information?
I do believe that businesses have a responsibility to protect the privacy of their users, especially with the risks that come with hacking, misuse of data, and selling of private information. Companies use this information to gain more revenue through user personalization, however, if they are not careful they can harm people who place their trust in them and ruin their reputation. While the government can place more regulations on businesses to prevent these issues, other conflicts can arise such as too much government presence in technology or the restriction of personal freedoms for businesses. Therefore, in order to protect people while also remaining free from government intervention, companies need to create their own policies to safeguard user information.
Refrences:
McLaine, S. (2001). Ethnic Online Communities: Between Profit and Purpose. In D. Gauntlett (Ed.), Web.Studies: Rewiring Media Studies for the Digital Age. Arnold Publishers.
Peltz, P., & O'Neill, M. (Directors). Surveilled. [Film]. HBO Documentary Films.
2 notes
·
View notes
Text
Tips To Avoid Hacker Intrusions

Tired of hackers finding ways to steal your sensitive data? Knowing how to protect your personal data and passwords will keep you a step ahead of cyber thieves.

New Life Technology Group gathered information about the methods hackers use to control your devices and steal your data, as well as ways to protect your online information and how to safely donate your outdated computers and electronics.
Common Hacker Techniques

Hackers employ various methods to gain control of devices and steal sensitive data. Recognizing these tactics is your first line of defense.
Phishing Attacks
Phishing emails mimic trusted organizations to trick users into clicking on malicious links or attachments. These messages often appear to be from banks, online stores, or even coworkers but contain malware or request personal information.
Password Cracking
Hackers use tools that guess passwords (through brute force or stolen data breaches). Weak, reused, or short passwords are easily cracked.
Man-in-the-Middle Attacks
When users connect to public Wi-Fi without encryption, hackers can intercept data sent between devices and websites, collecting passwords and other sensitive information.
Malware Infections
Malware, including viruses, spyware, and ransomware, can be hidden in downloads, email attachments, or websites. Once installed, it can log keystrokes, access files, or lock you out of your system.
Social Engineering
Social engineering relies on manipulation, not technology. Hackers may impersonate IT staff or customer service agents, convincing users to share credentials.
Protecting Your Online Presence

Cyber threats are everywhere. Hackers target individuals, businesses, and nonprofits seeking access to sensitive data (financial records, login credentials, and personal identity details). Once inside, they can steal, destroy, or ransom your files. Protecting your online presence is no longer optional. It is essential (and following clever security practices significantly reduces your risk). Consider the following actions:
1. Create and Use Strong Passwords
Make passwords long (at least 16 characters).
Use a mix of uppercase, lowercase, numbers, and symbols.
Do not use personal information (names or birthdays).
Try a passphrase – unrelated words strung together are strong and can be memorable.
Use a password manager to generate and securely store unique credentials.
2. Enable Multi-Factor Authentication (MFA)
MFA adds another layer beyond your password, such as a code sent via text or an authenticator app.
Biometrics (fingerprints or facial recognition) offer enhanced protection.
Enable MFA on banking, email, cloud storage, and social media accounts.
3. Be Wary of Phishing Attempts
Watch for messages requesting personal info – even from familiar contacts.
Never click suspicious links or download unknown attachments.
Always verify requests using official communication methods.
4. Secure Your Home Network

Change default router usernames and passwords.
Use WPA2 or WPA3 encryption for your Wi-Fi.
Disable WPS and remote management unless required.
Update router firmware to patch vulnerabilities.
Use the router’s built-in firewall.
Set up a separate guest network (to isolate smart devices and visitors).
5. Keep Software and Devices Updated
Update operating systems, apps, and firmware regularly.
Enable automatic updates when available.
Outdated software often contains known security flaws that hackers exploit.
6. Practice Good Cybersecurity Hygiene
Limit sharing personal information on social media – it can be used for identity theft or guessing passwords.
Avoid saving passwords on shared devices.
Never share credentials through unsecured messages or emails.
Use a VPN to encrypt your internet traffic and hide your IP address.
New Life Technology Group Recycling Protocol

At New Life Technology Group, security doesn’t stop at the digital level – it continues into the recycling process. As a 501(c)(3) nonprofit focused on repurposing electronics for underserved communities, protecting donor data is a top priority.
Before any computer or device is refurbished and redistributed, New Life Technology Group follows strict data destruction protocols:
Certified data-wiping tools erase hard drives using industry standards.
Devices encounter multiple verification steps to confirm the complete removal of sensitive information.
Inoperable drives are physically destroyed to prevent recovery.
All procedures align with the Department of Defense and NIST data sanitation guidelines.
Whether you donate a laptop, desktop, or smartphone, you can feel confident that no data remains. This ensures both your privacy and the safe use of devices by children, families, and schools that receive them.
Watch this video to see how New Life Technology Group receives and processes your old electronics.
youtube
Key Considerations for Avoiding Hacker Intrusions

Avoiding hacker intrusions starts with knowledge. Understanding attack methods allows you to counter them with proactive steps.
1. Password Strength Is Non-Negotiable
Password habits make or break your digital security. One compromised login can lead to a chain of breaches across multiple accounts. Always use unique passwords, and never reuse them.
2. MFA Should Be Standard Practice
Multi-factor authentication is one of the most effective defenses against unauthorized access. Even if a hacker steals your password, they can’t enter your account without the secondary verification method.
3. Phishing Attacks Are Evolving
Scammers constantly update their techniques to appear more convincing. Look for signs like misspellings, generic greetings, or urgency tactics. When in doubt, go directly to the website instead of clicking links in emails.
4. Secure Wi-Fi Is Your Digital Castle
Leaving a router on default settings is like handing out your house key. Change login credentials, apply encryption, and perform firmware updates to keep hackers out.
5. Updates Are Digital Armor
Hackers target old software because vulnerabilities are already known. Updates patch these holes. From smartphones to smart thermostats, every device should run current software.
6. Hygiene Is Not Just Physical
Every online action leaves a trail. Oversharing, accepting unknown friend requests, or installing unverified apps can all open doors for hackers. Be selective and cautious online.
7. Use Technology to Fight Technology
Password managers, VPNs, firewalls, and antivirus software all strengthen your defenses. Use tools wisely and consistently to stay protected.
Note: Cybersecurity is an ongoing effort, not a one-time setup. The digital landscape evolves rapidly, and hackers constantly adapt their tactics. By using the methods mentioned above, you create multiple layers of protection around your data. With partners like New Life Technology Group ensuring safe digital recycling, both your online and offline presence remain secure.
Cybersecurity Tips
In this article, you discovered information about the methods hackers use to control your devices and steal your data, ways to safeguard your online information, and how to safely donate used computers and electronics.
Create layers around your sensitive data (strong passwords, Multi-Factor Authentication, a secure network, and staying informed).
Ignoring your cybersecurity strength can leave you vulnerable to breaches and thieves (and barred from accessing your devices until a ransom is paid).
Sources: cisa.gov/topics/cybersecurity-best-practices consumer.ftc.gov/media/79887 security.berkeley.edu/resources/best-practices-how-to-articles/top-10-secure-computing-tips
New Life Technology Group
253 Grogan Dr #120 Dawsonville, GA30534 (404) 313-8215
To see the original version of this article, visit https://newlifetechgroup.com/tips-to-avoid-hacker-intrusions/
#e-recycling#e-waste#data destruction#nonprofit e-recycler#donate computer#computer donations#Cyber Security#technology#Youtube
1 note
·
View note
Text
Ways to Protect Your VPS Against Online Threats
Leaks of customer information are devastating to businesses; not only may they damage the reputation of your firm, but they may also result in severe legal penalties. It is essential to have a solid understanding of virtual private server security in order to protect oneself from any dangers on the internet.
Nevertheless, in addition to adhering to the most effective security practices, you are required to perform routine checks on your virtual private server (VPS). In this article, you are given useful suggestions for protecting virtual private servers (VPS) from cyberattacks. Keep reading to learn more!

Tips for Virtual Private Server Cybersecurity in 2024-
If you are in charge of a web server, it is absolutely necessary to remain up to date on the most recent security measures and risks that are posed by the internet. In the year 2024, the following are the best practices for assuring the security of virtual private servers (VPS)!
Deactivate the Root Login feature
Any element of the server can be modified by the root user of a virtual private server (VPS), who has the highest level of operational entitlements. In an effort to seize control of the system, hackers might select this user as their target.
This login account can be removed, which would reinforce the defense against root access and safeguard your website from attacks. For the sake of server administration, we recommend creating a new login that is capable of accessing the root level and running commands.
Make your passwords more secure
The most easily guessed passwords are ones that are poorly crafted, such as those that contain common terms or data that may be identified. You may create secure passwords by mixing different types of characters, including numerals, special characters, and both uppercase and lowercase letters.
The use of secured password management software is something you might want to think about if you want to simply generate and save secure passwords. It is essential to keep in mind that originality is essential. Consequently, it is recommended that you change your passwords periodically, preferably once every three months, and never use the same password for more than one account. As a final precaution, you should never provide your root login credentials in order to prevent unauthorized access.
Modify the SSH Port That Is Default
If you continue to allow attackers to access your virtual server over the normal SSH port of 22, you are inviting them to do so. Port scanning and brute-force attacks are two methods that attackers can use to gain unauthorized access to a remote system. When securing virtual private server (VPS) cyber threats, it is important to lock out unauthorized users and change the default SSH listening port to something unexpected.
Restriction of User Access
When you have a significant number of users on your virtual private server (VPS) hosting, it is important to carefully plan out how rights and control will be distributed. Your server's sensitive data and assets are at risk of being compromised if you grant root access to each and every user. By understanding and applying the various forms of authorization, you can make certain that each user has access to only the permissions that they require.
In the event that an account is compromised, this strategy ensures that the damage is reduced to a minimum. Sensitive information and systems are protected from harm since this reduces the attack surface and diminishes the possible effects that could be caused by attacks that originate from within the organization. A further benefit is that it simplifies audit procedures, which makes it easier to monitor user activity and identify inconsistencies.
Put the Principles of Robust Authentication into Practice
A strong, one-of-a-kind password should be generated for each account on your virtual private server (VPS), and you should utilize multi-factor authentication (MFA) to add an extra layer of security. For remote access, you should make use of secure protocols such as SSH keys in order to prevent unauthorized login attempts and protect your virtual private server (VPS) against assaults that are based on credentials.
It is difficult to decode these automated keys because they are typically longer than passwords. Public and private keys are the components that makeup SSH keys. It is the device that is utilized that is responsible for storing the private key, whereas the server of the computer is where the public key is kept. In the event that an individual attempts to log in, the system generates an arbitrary string. This string is then protected with the public key. The only way to gain access is to decrypt this string using a private key that is compliant with the security system.
Set up a VPN on your VPS
Your information is at risk of being intercepted and stolen by third parties who are not authorized to do so if you use a public connection. Set up a virtual private network, also known as a VPN, to protect yourself from potential security threats and in order to avoid this. Using a virtual private network (VPN), your computer is able to conceal its true location while also directing traffic through a secure connection.
This is accomplished by using a new IP address. Your Internet Protocol (IP) address will be rendered untraceable as a result of this, which will allow you to remain anonymous surfing the internet. Your data is protected by a virtual private network (VPN), which also prevents hackers from accessing your communications. Alongside a firewall, it provides additional protection for virtual private servers (VPS).
Be sure to utilize firewalls
Your firewalls are your first line of defense against threats that come from the internet. APF and CSF are examples of programs that act as guardians by monitoring both incoming and outgoing traffic. They contribute to the identification and prevention of undesired movements at the entrance, so ensuring that only authorized traffic is allowed to pass through. They offer a barrier that can be designed to match the specific requirements and security requirements of your system, and it may be updated to meet those requirements.
Firewalls have a number of features that aid with the rapid identification and management of typical cyber risks. One of these features is the ability to generate detailed logs and send notifications regarding potential safety incidents. The fact that they are able to make adjustments and offer timely protections makes them an essential resource for cybersecurity.
Make sure you do regular backups
You should create backups of your data on a regular basis to protect it from being lost in the event that there is a data breach. Ensure that backups are stored in a location that is not the virtual private server (VPS) and implements automated backup mechanisms. Because of this, even if the virtual private server (VPS) is compromised, your essential data will remain secure and accessible.
Set up an antivirus program
Installing antivirus software on your virtual private server (VPS) will protect your data and forestall any compromises. An antivirus tool for your server performs continuous inspections of files and actions, much like software that has prevented the malware from infecting a large number of PCs around the world by spotting dangers in real-time.
Employ a Malware Scanner Software
Your virtual private server (VPS) is protected from dangers such as trojans and worms by an antivirus program; however, it may not be able to identify more recent exploits such as zero-day malware.
Combine antivirus software with a malware scanner to improve the security of your virtual private server (VPS). This category of software is able to update the detection rule more quickly, which enables it to differentiate between newer threats that are present on your system.
Check out the User Rights
If there are a large number of users on your virtual private server (VPS) hosting, you should give serious consideration to the distribution of control and rights. Your server's resources and sensitive data will be put at risk of security breaches if you grant root rights to every user on the server.
You should restrict the number of users who can access your server in order to avoid this problem. Managing users and assigning them varying permissions for particular files and system resources is one way to accomplish this goal.
Install systems that can detect and prevent intrusions
Monitoring and analyzing network traffic with the help of intrusion detection and prevention systems (IDPS) is a good way to keep an eye out for any indicators of malicious behavior or efforts to gain unauthorized access. IDPS's ability to detect and block threats in real time contributes to an overall improvement in the security posture of your virtual private server (VPS).
Conclusion-
The protection of your virtual private server (VPS) is essential since it stores sensitive information. In spite of the fact that Linux is well-known for its robust security, the virtual private server (VPS) nevertheless has weaknesses. Malware, sniffer and brute-force attacks, SQL injections, cross-site scripting (XSS), lacking function-level control, and incomplete authentication are some of the most common types of cyber assaults and problems that can occur in a Linux system. Virtual private server owners need to be aware of how to monitor the server and operating system in order to implement effective security measures in order to avoid these issues.

Dollar2host Dollar2host.com We provide expert Webhosting services for your desired needs Facebook Twitter Instagram YouTube
2 notes
·
View notes
Text
How Headless WordPress Can Help Your Business Grow? | Island Wizards

As businesses continue to grow online, having a fast, flexible, and future-proof website is important. One of the best ways to achieve this is by using Headless WordPress. At Island Wizards, we offer headless WordPress solutions that can help your business succeed in today’s digital world.
But what exactly is Headless WordPress, and how can it help your business?
What is Headless WordPress?
In traditional WordPress, the backend (where you manage your content) and the frontend (what the user sees) are connected. With Headless WordPress, these two are separated. WordPress still manages your content, but the frontend can be built using different tools and technologies, making your website faster and more customizable.
Let’s take a look at how this setup can benefit your business:
1. Faster Website for Better User Experience
When a website loads slowly, users are more likely to leave. Headless WordPress allows your website to be built with modern technologies that load content quickly, improving the overall user experience. A faster website also means better rankings on search engines like Google, which can bring more traffic to your site.
At Island Wizards, we ensure that your headless WordPress site is fast and smooth, helping you keep visitors engaged and satisfied.
2. Deliver Content Everywhere
With Headless WordPress, you can deliver your content to multiple platforms—not just your website. Whether it’s a mobile app, social media, or even a smart device, headless WordPress makes it easy to share your content across all channels. This helps you reach a wider audience, wherever they are.
At Island Wizards, we help you set up a system that makes your content available on different platforms, so your business can grow beyond just a website.
3. Keep Up with New Technology
Technology is always changing, and your website should be able to keep up. Headless WordPress allows you to update the frontend of your website (how it looks and works) without having to change your entire content management system. This makes it easier to add new features or update your design as trends and user expectations evolve.
Our team at Island Wizards builds future-proof websites that can grow and change with your business, so you’re always prepared for what’s next.
4. Increased Security
Online security is a big concern for businesses. With Headless WordPress, your website’s backend is more secure because it’s separated from the frontend. This reduces the risk of common attacks and makes your website less vulnerable to hackers.
At Island Wizards, we make sure your headless WordPress site is protected with the best security practices, giving you peace of mind.
5. Easy to Scale as You Grow
As your business grows, so will your website’s needs. Whether you’re getting more traffic or adding new features, Headless WordPress can scale easily. You can add more content, handle larger audiences, and ensure your website stays fast, no matter how big your business gets.
At Island Wizards, we create websites that grow with you, ensuring that your digital platform is always ready to meet increasing demands.
Conclusion
Headless WordPress is a powerful solution that helps businesses create faster, more flexible, and future-ready websites. With the ability to deliver content across multiple platforms, keep up with new technologies, improve security, and scale easily, it’s the perfect choice for businesses looking to grow.
At Island Wizards, we specialize in building custom headless WordPress solutions that help businesses succeed in the digital world. If you’re ready to take your website to the next level, contact us today and find out how we can help your business grow. Explore more about us… https://islandwizards.com/services/shopify/ https://islandwizards.com/services/headless-wordpress/
#shopify#wordpress#island wizards#headless wordpress development services#seo#island wizards uk'#wizards island#shopify partner program#white label agency
2 notes
·
View notes
Text
Unlock Internet Freedom and Secure Your Privacy with Gulf VPN
Searching and operating within the internet in the gulf countries has its own set of challenges. VPN is restricted, access to social networks is limited and websites are often inaccessible during certain hours. Using a VPN is not a luxury but a necessity, particularly in regions like the UAE, Qatar, and Saudi Arabia.
A VPN, Virtual private Network, is a service that establishes a secure connection between you and the whole internet so that your activities and details of your location cannot be seen. A VPN works by encrypting your traffic and hiding your IP address which makes it easier to advance past censorship and allow for the freedom to access content without compromising your privacy. Here, you’ll get a brief understanding of what a Gulf VPN UAE is, how it functions, and why it is crucial for you in the first place to opt for the most suitable service.
Why Do You Need a Gulf VPN?
Many countries of the Gulf region remain among the leaders in restrictive internet policies, many recognizable sites and applications are blocked here. From VOIP services including WhatsApp, Skype to widely used streaming services such as Netflix, BBC iPlayer; many services block or limit access due to government restrictions or geo-restriction practices.
This is where having a VPN becomes absolutely essential. A VPN could be used by linking to a server in another country; this makes it possible to unlock content since the VPN provides an individual an entry point into the internet that is restricted in the Gulf.
Reasons to use a Gulf VPN include:
Avoiding Authority RestrictionsGulf countries are quite famous for banning and restricting sites and applications that are in resistance to set laws and regulations. This limits you from getting to the sites because your connection is being encrypted and the traffic is routed through other servers in some other region of the world other than the prohibited region.
Increasing Privacy and SecurityThere is always a perception of privacy concern and this exists more so in the gulf because the ISPs and the governments are vigilant. If you use VPN to connect to the internet, your data is encrypted; thus your Internet Service Provider cannot interfere and monitor what you are doing.
Access to Streaming ServicesNetflix, Hulu, Amazon prime videos these streaming channels are also limited due to geo-restrictions. A Gulf VPN 2024 allows you access servers of other areas and therefore you can watch uninterrupted favorite shows and movies.
Safe Browsing on Public Wi-Fi
It is unsafe to use Wi-Fi networks that others connect to, particularly when in a country that has seen an increase in the level of cybercrime. A VPN effectively works to guarantee that your information is not vulnerable mostly when using a wrong public network by encoding your connection so that the hackers cannot easily access it.
How Gulf VPNs Protect Your Privacy
One of the primary benefits of a VPN is data security that a user receives when he or she connects to the server. You lack privacy when browsing the internet because your data flows unencrypted, and anyone can access it using your IP address.
Using a Gulf VPN 2024 means all your communication and internet usage are hidden behind a protective layer, and your actual IP address is swapped with that of the VPN server. This makes it impossible for the web site, hackers, or even any other government agency to track your activities with any chance. Moreover, the best VPNs provide things like server cloaking and it becomes quite challenging to realize that you are using a VPN.
Key Features
Selecting the right Gulf VPN may not be easier as there are lots of service providers out there. Here are the key features you should prioritize to ensure you get the best protection and access.
1. Robust Encryption and Protocols
Check that the connection is as secure as possible and you should look for one with AES-256 encryption. Also, check for the connection protocol standard such as OpenVPN or WireGuard since they are fast and secure..
2. Server Locations
Accessibility to multiple centers and points helps to overcome the problem of geo-blocking. As with the server locations, the more available servers a VPN has, the higher are the chances of getting a server with a fast connection. Choose VPN providers with the servers located in Europe or North America or Asia to have the most opportunities.
3. No-Logs Policy
When it comes to VPN, privacy is all that matters. Check whether your provider does not monitor or store any information about your online activity. This is particularly so given that most of the GCC states technically spy on their citizens.
4. Fast and Stable Connections
A VPN should work for making your internet experience better rather than making it worse by slowing down your connection. Close on the high-speed servers and choose VPNs that can deliver good performance when it comes to streaming, gaming, as well as torrenting.
5. Bypassing Geo-Restrictions:
However, most VPNs are unable to bypass streaming services such as Netflix and Hulu. Ensure you choose a VPN that has been tried and shown to overcome any level of geo-blocking.
Gulf VPN for Streaming
One of the biggest draws of using a Gulf VPN UAE is the ability to access geo-restricted content. Regions get blackouts to allow streaming services to function by adhering to their regional licensing restrictions on movies, TV shows, channels, and more. For example, the movies and TV shows that are watched in the UAE could be different from the ones that are consumed in the US.
A VPN enables you to establish connection with a server in another country and makes it seem like you are accessing the internet from such a country. This gives you complete control to the Netflix, amazon prime, Disney Plus and other VPN for streaming services platform libraries around the world. For anyone who wants to stream a show that is restricted in their current location whether an expatriate wanting to stream shows from his home country or a local in a region with restrictions, a VPN changes that.
VPNs and Online Gaming:
If you are a gamer residing in the Gulf then you will find a VPN to enhance your gaming experience. Games also have restrictions in servers and beta access meaning you can’t play with your friends who are in a different region. Moreover, through using a VPN, it will be easier for you to avoid tyra DDoS attack besides ensuring your data is not relayed to the other players.
A VPN also minimizes ping and latency issues by linking the client to a closer server to where the game’s server is hosted. This makes it possible to connect to cross border gaming servers and be able to play with friends all over the world.
To sum up
If you live in or are planning a trip to the Gulf region, prepare for limited internet access, geo-blocking, and privacy issues. A Gulf VPN 2024 is the answer to all these questions, a tool that gives you freedom, security and anonymity every time you connect to the Internet.
A VPN protects your identity as well as your IP address so that the intended material is unrestricted and your information is safeguarded from any malicious third party endeavor, be it streaming videos, playing games online or browsing the internet. To ensure the best experience, one should look into strong encryption, fast servers, and no logging policy while selecting a VPN.
Having the best Gulf VPN will enable you to get the best out of the internet without any restriction or anything to bother you.
3 notes
·
View notes
Text
How to Protect Your WordPress Site from Malware or Hackers?
WordPress is used by millions of websites for blogs, businesses, and online stores. However, because it’s so popular, it’s often a target for hackers and malware. If you have a WordPress site, it’s important to take steps to keep it secure. Here’s a simple guide to help you protect your site from hackers and malware.
How to Protect WordPress Site from Malware or Hackers?
Follow this step list given below to protect WordPress site from malware or hackers
1. Always Keep WordPress Updated
WordPress regularly releases updates to fix bugs and improve security. Hackers often look for websites running old versions of WordPress or outdated plugins, so keeping everything updated helps keep them out.
How to Update:
Check for updates in your WordPress dashboard regularly.
Go to the Dashboard > Updates section and install any available updates for WordPress core, themes, or plugins.
By staying updated, you’re less likely to have security holes in your site that hackers can use.
2. Use Strong Passwords and Change Them Often
Hackers can easily guess weak passwords like "123456" or "admin." To keep your site safe, use strong, unique passwords and change them every few months.
Tips for Strong Passwords:
Use a mix of uppercase and lowercase letters, numbers, and symbols.
Don’t use simple information like your name or "admin."
Consider using a password manager to create and store complex passwords securely.
Strong passwords are one of the simplest ways to add security to your website.
3. Limit Login Attempts
Hackers often try to break into websites by guessing the login password over and over. You can protect your site by limiting the number of login attempts a person (or bot) can make.
How to Limit Login Attempts:
Use plugins like Limit Login Attempts Reloaded or WP Limit Login Attempts.
These plugins lock out users after a certain number of failed login attempts.
This makes it much harder for hackers to keep guessing passwords.
4. Enable Two-Factor Authentication (2FA)
Two-factor authentication adds another layer of security. In addition to entering your password, you’ll also need to input a code sent to your phone or email. Even if someone knows your password, they won’t be able to log in without this extra code.
How to Set Up 2FA:
Install a plugin like Google Authenticator or Two-Factor.
Set it up by scanning a QR code and linking your account to an app like Google Authenticator or Authy.
This ensures that only you can access your site, even if someone steals your password.
5. Use a Security Plugin
A security plugin can protect your WordPress site from different types of attacks, like malware or brute force attempts. These plugins act as your site’s security guard, offering tools like firewalls and malware scanning.
Recommended Security Plugins:
Wordfence Security: Includes a firewall and real-time monitoring.
Sucuri Security: Provides malware removal and a website firewall.
iThemes Security: Offers brute force protection, backups, and two-factor authentication.
Using a security plugin adds strong layers of protection against hackers.
Also Read - What Is Domain Status? What does this mean, & Why should I know?
6. Back Up Your Website Regularly
Even with good security, things can sometimes go wrong. That’s why it’s important to back up your site regularly. If your site gets hacked, a backup will let you restore everything quickly without losing important data.
How to Back Up Your Website:
Use backup plugins like UpdraftPlus or BackupBuddy.
Store your backups in safe places like Google Drive, Dropbox, or a remote server.
Schedule backups daily or weekly, depending on how often you update your site.
Regular backups help ensure you won’t lose everything if something goes wrong.
7. Choose a Secure Hosting Provider
Your web hosting service plays an important role in your website’s security. Some hosts offer strong security features that help protect your site. Make sure to choose a hosting provider that values security.
What to Look for in a Hosting Provider:
Regular backups
Malware scanning and removal
Firewalls
SSL certificates
DDoS protection
Popular and secure WordPress hosting services include SiteGround, Bluehost, and WP Engine.
8. Use HTTPS and SSL Certificates
SSL (Secure Socket Layer) encrypts the data between your website and your visitors. This protects sensitive information, like passwords or credit card numbers. Websites with SSL certificates also have a secure URL that starts with "https://."
How to Install an SSL Certificate:
Most hosting providers offer free SSL certificates with Let’s Encrypt.
You can use plugins like Really Simple SSL to set it up quickly.
SSL certificates keep sensitive data safe and make your site more trustworthy.
9. Remove Unused Themes and Plugins
Unused plugins and themes can create security risks, especially if they aren’t updated. Even if they’re deactivated, they can still be a weak point. It’s best to delete any plugins or themes you don’t use.
How to Delete Unused Themes/Plugins:
Go to your Dashboard > Plugins or Appearance > Themes.
Deactivate and delete anything you no longer need.
This reduces the number of places where hackers might try to get in.
10. Monitor Your Site for Suspicious Activity
It’s important to keep an eye on your site for any unusual behavior. This could include sudden spikes in traffic, unknown files appearing on your server, or unauthorized users trying to log in.
How to Monitor Your Site:
Use a security plugin to track things like failed login attempts and changes to important files.
Regularly check your hosting account for unusual activity.
Review your website users to make sure no unauthorized accounts have been added.
By staying alert, you can catch potential threats before they do any serious damage.
Conclusion
Protecting your WordPress site doesn’t have to be difficult. By following these simple steps—keeping WordPress updated, using strong passwords, installing security plugins, and making regular backups—you can greatly reduce the risk of your site being hacked or infected with malware.
#OZOHosting#lowest price hosting in india#Cheap web hosting jaipur#cheap shared web hosting india#free web hosting india#affordable linux web hosting india
2 notes
·
View notes