#how to prevent hacking on website
Explore tagged Tumblr posts
Text
#website protection#hacking#ethical hacking#how to secure your website#how to secure a website#how to secure website from hackers#how to protect your website from hackers#cracking#how to prevent hacking on website#how to secure your website from hackers#introduction to website hacking!#how to secure wordpress website#how to secure my website for free#how to secure a wordpress website#secure wordpress website#how to prevent hacking#how to recover from a website cyberattack
0 notes
Text
Hey everyone it seems there a malicious individual trying to hack the sims cc community again and fill it with malware you need to stay vigilant as a creator and a downloader so
i have some tips for both to stay safe while downloading:
1- sims cc file extension is always .Package never download anything that is .exe
2- do not auto unpack zip files and rar files into your mods folder directly, open each zip or rar individually check the file extensions and drag them to your mods folder one by one
3- the only mods that have a .ts4script extension are ones that affect gameplay or how the game works, understand that if you are downloading cas or bb items you shouldn't have a .ts4script file
4- if you are downloading gameplay mods that do have .ts4script make sure that A) the creator hasn't announced on their pages that its infected B) you are downloading from a link provided by the creator of the mods themselves not something off of google or a link you got sent and make sure dates of upload match dated of announcements
5- if the mod or cc creator has retired and hasn't posted for a while LOOK AT THE DATES OF THE UPLOAD if it has been "updated recently" after the creator has left the community its most likely re-uploaded by a hacker and infected
6- download mod gaurd by Twisted mexi and keep it updated and keep your windows defender or malware detector Program up to date and always running do not disable it
7- make sure everything you download comes from a direct link from the cc creator, in this day and age do not trust link shortners, adfly, linkverse, etc get the universal bypass extension and ublock extension to stay safe but genuinely NEVER CLICK ON THOSE no matter how much the creator reassures you its safe it. is. NOT.
8- this is more of a general saftey precaution but, create a system restore point weekly before you run the game with new mods that way if anything happens you could have a chance to restore your windows to an earlier date before you downloaded anything.
9- BACK UP YOUR SHIT im serious right now either weekly or monthly put your files somewhere safe like a usb a storage card a hard drive even an online cloud if you dont have any of the previous.
10- files you should back up are your media from games and media everything else, any mods, games saves, work files, passwords, saved bookmarks, any documents txt files word files pdfs, links you saved, brushes or actions for Photoshop if you have any, any digital bills or certificates if you have any, and keep a physical list of all programs you have installed and where you installed them from
11- turn on any 2 factor authentication and security measures for any account you have
12- google and firefox have the option to check your paswords and emails against any data leaks USE THIS FEATURE and change any leaked passwords
13- regularly check your logged in sessions to make sure all the logged in devices or computers are yours and log out any that aren't and any old devices or unused sessions do this for every website and app you have an account on if available
14- change your passwords often. I know this is a hassle i know its hard to come up with new passwords but changing your passwords every few months will help you against anything mention previously that wasn't detected.
15- and as a cc creator check your cc and the accounts you host cc on and its uplaod and update dates make sure nothing has been changed without your permission :(
16- generally try not to get swept up in the "i must get it" fever you do not need to "shop" for mods weekly or monthly you do not need to download everything by that one creator you do not need to download new cc everytime you want to make a sim, im guilty of this so i know how hard it is to resist but take a breath and think "do i want this or do i need it" before downloading.
These are prevention methods i cant claim they are 100% will prevent any hacking but its better to be safe than sorry and these do keep you safe so
Brought to you by someone who has had their laptop ruined and data leaked from downloading cc once upon a time
3K notes
·
View notes
Text
Important Announcement

A now-patched breach of security has occurred on Art Fight. To learn about this issue in full detail, please read the following newspost:
Below is a FAQ regarding the exploit. We highly recommend that you reset your password and enable 2FA if you have interacted with the site recently. If you need any assistance, please send a support email to the following address: [email protected]
The inbox will be opened shortly to respond to user questions and concerns. Anonymous will be turned off for the time being, please let us know if you prefer that your ask is answered privately.
How did this happen?
Our BBCode system had a vulnerability flaw in it that was temporarily exploited to attempt to gain user credentials, but it has since been patched.
What do we do?
If you believe you may have been affected, please change your password to something unique and secure. We also recommend keeping an eye out on your other accounts, and to change the passwords on them if they shared any credentials as your Art Fight account (so same email or same password).
How do we know if you were affected by this exploit?
If you accessed the comments of the most recent news post (Terms of Service Updates), there is a chance your browser was exposed to the XSS script, and we recommend resetting your password ASAP to be safe.
What are you doing to prevent this from happening again?
Our hard-working dev team has already patched this exploit, as well as added additional security measures to help prevent this from happening again in the future. We will also be proactively doing a security review to help locate any other security concerns. Two Factor Authentication (2FA) has been established as a feature on the site that can be found in your settings.
I'm nervous about going onto the site at all now! What if my account gets hacked/stolen/etc?
Art Fight's dev team has patched the vulnerability that this incident has revealed, and has added additional security to catch/stop malicious scripts before they can affect the userbase. All instances of the previous malicious script have been removed from the website, meaning that it is once again safe to view the last news post! We are working hard to continue to keep users safe, so you don't need to worry about accessing anything on the site. If you come across anything potentially concerning, please don't hesitate to forward it to a moderator - we're happy to look into it!
What information might've been taken from me?
The XSS attack attempted to collect autofilled Art Fight log in information--emails and passwords--from users. No other information (like birthdays) should have been collected through this script. If you use the same email/password combo, or same password anywhere else, we recommend changing to ensure your accounts stay secure.
884 notes
·
View notes
Text
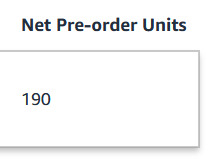
Echo of the Larkspur is at 190 preorders! Let's get this baby to 200! Tell your friends, tell your enemies, help spread the word about my Queer Sci-fi/Romance/Mystery novel so it can reach its audience!
For those who don't know, Echo of the Larkspur is my WTNV fanfic-turned-Original Novel about a paranoid scientist and a snarky robot teaming up to solve a deadly mystery. And maybe, just maybe, find love along the way. Or as the blurb goes:
The sole survivor of a massacre, Dr. Ciro Kwakkenbos, has spent the last six years in intensive therapy. He’s finally capable of working with Artificial Intelligence again—and comes to the Ceres colony determined to prevent robots from committing any future atrocities. When he arrives, Ciro realizes the robot in charge of the colony’s security, S.A.G.E. (Sentient Automated Geo-sentinel Engineer), is dangerously close to complete sentience. S.A.G.E. is more interested in observing the colonists’ everyday lives (and matching them with appropriate musical soundtracks) than following its intended programming. Robots aren’t supposed to be charming, kind, or compassionate, either. But as Ciro investigates, he discovers S.A.G.E. has learned how to lie and—possibly—harm and kill humans. Worse, S.A.G.E.’s memories have been hacked, deleting a deadly secret. Despite the danger S.A.G.E. poses, Ciro can’t deny the feelings growing between them. Now Ciro must unravel the truth behind the missing memories—before S.A.G.E. and the colony are doomed.
You can read the first chapter on my website for FREE!
Like what you see? You can preorder it on Amazon!
(Note: Physical copies will be available to order on July 23rd. It will be sold on non-Amazon websites starting October 22nd)
If you've preordered it already then thank you from the bottom of my heart! All sales of this book will be going towards cover art/editing/formatting of its sequel and so on and so forth! Your purchase helps cement the future of this series! Already preordered? Then help spread the word! It's because of you lovely people I've gotten to almost 200 preorders in the first place!
Thanks so much, you lovely Marzipan Modern Art Owls!

#echo of the larkspur#eotl#bookblr#writeblr#science fiction#romance#mystery#queer#lgbtq#lgbtqia#book#writing#robot#robots#robot sex#robot fucker#wire play#wireplay#wtnv#welcome to night vale#night vale
62 notes
·
View notes
Text
Is privacy important to you?
So recently, I've seen an uptick of people interested in privacy regarding electronics (phones, pc, what have you). When I say people, I'm referring to non-techy people, like myself. I know my way around my computer and can do some basic troubleshooting for hardware/software, but beyond that, I'm sort of helpless. I don't know anything about hacking or cybersecurity and the only coding I can do is some html. I'm below a novice haha. So, if you're that sort of person, then maybe this could be of interest to you. What I am about to discuss involves no coding or really any in depth knowledge regarding technology. You don't have to be Elliot Alderson for this.
>Why does privacy even matter?
The answer to this question will vary from person to person. I, for one, do not like the idea of any corporation hoarding my data to sell or store or do fuck all with. If this does not bother you, I'd consider asking yourself if you're comfortable with, let's say, something like Google knowing everything about you. And I mean everything. Suppose that doesn't bother you, then okay. Maybe think about how it would feel if your classmates or coworkers knew what Google knows about you. Corporations also extend to governments because they're jerking each other off, so something to keep in mind. And individuals, people like you and I, work for these entities. And these people can abuse your data. For any reason.
Your data is a tool for them to control you. You might not realize it until it's too late. I'm being a little vague here because this point alone could be an entire wall of posts.
Additionally, something to consider is the level of privacy that you may require. If you are someone who attends public protests or is part of some sort of organization that criticizes your government, you are at risk of potential scrutiny or harassment. Obviously, but I mean specifically from a lack of privacy practices. Maybe from your government or somebody who opposes your views, etc. And depending on how you've been communicating about these gatherings or communities, you're potentially putting others at risk as well. If you're one of the people who's in charge of organizing or playing a large role, some of the methods I will be going over will likely not be enough to protect you. Activists and journalists need a different level of privacy that I can't begin to match.
Listed below are some videos that I watched that really helped me to understand why this is important.
“I Have Nothing to Hide” – The Dangerous Myth About Privacy
Is it impossible to be private online? (Eric's channel has been very helpful for me personally because his explanations do not alienate the tech illiterate)
>So...Where do I start?
Luckily, there are small steps you can take to prevent some information about you from being hoarded. And I say some, not all. Unfortunately, the only way to completely avoid all of this is to live out in a cabin in the middle of nowhere and never use the internet ever. Which I can assume you don't want because you're reading this on a website right now! You will have to make some compromises for some of these options, and if you can't replace all of these and only some, that's fine. Most of these can be adjusted in just a few minutes, if that.
General
Oh my god, stop using chrome. I'm serious, please stop. If you are using chrome to read this, close out of this and download firefox. or brave or chromium or whatever. I use firefox, and the second you download firefox, download ublock origin. Ads on the internet are completely out of control. Firefox is not foolproof either, other add-ons can provide not just a more private experience, but also a much smoother one. ClearURLs removes tracking elements from urls. And it's open source. There are a few others, but I don't know everything lol. There are VPNs you can use, but I only ever use one if I'm away from home and using the Wi-Fi at work or something.
Stop using google search engine. In firefox, you can set something else by default. I just use duckduckgo, but there are alternatives. You can also turn off the ai bullshit. Find one that works best for you and your needs.
Email. So this is one I have not moved yet. I still have gmail for my youtube account. I also have to use gmail for my university. I do have a protonmail, though, that I've been slowly moving over to. This could be an easy fix for some people, while impossible for others. This is something that I am willing to compromise on. Again, you can't have it all with how things are set up. I'm sure there are some ways to circumvent this, but I am not aware of it. For things like drive and docs there are also some alternatives, but I don't use drive all that much, so finding an alternative isn't that pressing for me. There's proton drive, which functions similarly, and several paid options, but I'm trying to keep this process free for people just starting to be privacy-conscious.
Signal is a good messenger especially if you're moving from something like facebook messenger, instagram, whatsapp, whatever. It's end to end encrypted and pretty modern (so stuff like emojis, reactions, voice messages) You do need a phone number though, but again, better than just whatsapp. More people are moving to it now, so you might have an easier time introducing friends to it.
Cellphone
Alright, so this is going to depend on a few factors, mainly whether you have Android or iOS. I had an iPhone for a long time, up until last year. I was never an Apple fanboy, it's just what I had, but I wasn't deep in the ecosystem by any means. I've always used a Windows computer, so I didn't have a Mac or apple watch or whatever. I had an ipad but sold it to a friend last year because I transitioned to using my Wacom full time on my PC. I only say that because if you like your apple products just keep in mind that while you are secure (apple does have great security), you may not be private. iOS is closed source, so it's more difficult for third parties or hackers to get your data, but apple has it. And apple can do whatever. Also, you are limited to the ways you can customize your phone.
I will link a video on someone who discusses privacy on iphone but aside from the few things I listed above I can't really help you much further than a few other points. Sorry.
A brief guide to privacy for iPhone
If you have an Android based phone you are in luck. Most Android phones allow you to put a different os on your cellphone since you can access the bootloader (unlike iphones) BUT your phone in most cases has to be OEM unlockable. Phones from carriers like Verizon aren't able to be unlocked because Verizon is weird and kinda treats their consumers like shit lol. I own a Google pixel 9 and I will admit I splurged on this phone by buying it brand new. It was on sale, I got a bonus at work and hey what can I say... Also my iphone 12mini was shitting itself so it was time for a new phone. The money must have been burning a damn hole in my pocket. In retrospect though, the smarter thing would have been to buy used or an older model. Which I will be doing in the future. Back on track though.
You're probably scratching your head here: if he was just complaining about google why the hell does he have a Google phone?
I'm glad you asked, hypothetical voice in my head.
Grapheneos is a os that is only available on Google pixels (I believe from 6 onward). What it does is basically degoogles your phone. So removes google services. And the thing is, you can redownload these services but refuse network permissions and limit what they can and cannot do or have access to. Or tweak settings that you would not otherwise have access to. You have control over your device and it actually somewhat feels like your device. It's easy to install...like, modding a ds takes longer than installing graphene on your phone. Here is a video that I watched that goes over specifics and installation.
Here is the grapheneos website
For non google phones there's calyxOS but I have no personal experience with it. But both of these OS give you back some ownership on your device by letting the user control how their cellphone functions and not a company. Also, it can help your phone feel a little smoother because it removes a lot of proprietary apps that companies like Samsung add to android. If your phone can't be unlocked, then start by switching to alternative apps and delete as many proprietary apps as possible. Watch this video on fdroid.
Remove face ID if you're able and remove fingerprints as well. It might be a bit inconvenient but it's much safer. I understand that these may be great accessibility tools for some so just do what you can. Turn off location when you're not using it. With graphene, you can give map applications your approximate location, not your exact location. There are also map options that can be disconnected from network, and you can save routes, but I use public transportation and really need to see when my bus is going to arrive. My cities bus app is so shit sometimes. Again, another example of compromising that is going make you ask what's important to you, and if you're willing to risk your privacy for it.
If you watch most of these videos, you'll hear a lot of these points are going to overlap.
I was considering discussing what you can do for your PC, but I'm a complete noob. I've been using Linux mint for a little bit now, and I avoid the terminal most of the time because I'm a little baby. Even still, I recommend getting away from windows if you're able. Especially if you have a windows 10 computer since Microsoft is dropping support this fall iirc. Linux mint is super beginner friendly and much lighter on your computer, so even better if your PC is older.
Some videos that might help you decide if Linux could be a good alternative for you.
Switching to Linux: A Beginner’s Guide
Why Linux is Better Than Windows 11
Linux Mint 22: Excellent Distro for Windows Users
Linux Mint for Gaming (2025) | Linux Gaming Setup (for Beginners) Pt. 1
This privacy stuff can go so deep and you'll feel kinda crazy lol. Once you learn about what people can do with this data, and read about how people's lives have been ruined by it getting into the wrong hands, it'll never leave your head. But it's important to start small. And start sooner rather than later.
Social media was something I considered discussing but I think it could be added to a later post since this is kinda long already. I hope this is somewhat helpful, I tend to ramble a lot of the time. If you're someone who is a bit more savvy than I, then please reply with any info that you think could be important. But remember that this post is for basic beginners who are just now learning about this stuff so keep it simple. Thanks for reading!
21 notes
·
View notes
Text
In the near future one hacker may be able to unleash 20 zero-day attacks on different systems across the world all at once. Polymorphic malware could rampage across a codebase, using a bespoke generative AI system to rewrite itself as it learns and adapts. Armies of script kiddies could use purpose-built LLMs to unleash a torrent of malicious code at the push of a button.
Case in point: as of this writing, an AI system is sitting at the top of several leaderboards on HackerOne—an enterprise bug bounty system. The AI is XBOW, a system aimed at whitehat pentesters that “autonomously finds and exploits vulnerabilities in 75 percent of web benchmarks,” according to the company’s website.
AI-assisted hackers are a major fear in the cybersecurity industry, even if their potential hasn’t quite been realized yet. “I compare it to being on an emergency landing on an aircraft where it’s like ‘brace, brace, brace’ but we still have yet to impact anything,” Hayden Smith, the cofounder of security company Hunted Labs, tells WIRED. “We’re still waiting to have that mass event.”
Generative AI has made it easier for anyone to code. The LLMs improve every day, new models spit out more efficient code, and companies like Microsoft say they’re using AI agents to help write their codebase. Anyone can spit out a Python script using ChatGPT now, and vibe coding—asking an AI to write code for you, even if you don’t have much of an idea how to do it yourself—is popular; but there’s also vibe hacking.
“We’re going to see vibe hacking. And people without previous knowledge or deep knowledge will be able to tell AI what it wants to create and be able to go ahead and get that problem solved,” Katie Moussouris, the founder and CEO of Luta Security, tells WIRED.
Vibe hacking frontends have existed since 2023. Back then, a purpose-built LLM for generating malicious code called WormGPT spread on Discord groups, Telegram servers, and darknet forums. When security professionals and the media discovered it, its creators pulled the plug.
WormGPT faded away, but other services that billed themselves as blackhat LLMs, like FraudGPT, replaced it. But WormGPT’s successors had problems. As security firm Abnormal AI notes, many of these apps may have just been jailbroken versions of ChatGPT with some extra code to make them appear as if they were a stand-alone product.
Better then, if you’re a bad actor, to just go to the source. ChatGPT, Gemini, and Claude are easily jailbroken. Most LLMs have guard rails that prevent them from generating malicious code, but there are whole communities online dedicated to bypassing those guardrails. Anthropic even offers a bug bounty to people who discover new ones in Claude.
“It’s very important to us that we develop our models safely,” an OpenAI spokesperson tells WIRED. “We take steps to reduce the risk of malicious use, and we’re continually improving safeguards to make our models more robust against exploits like jailbreaks. For example, you can read our research and approach to jailbreaks in the GPT-4.5 system card, or in the OpenAI o3 and o4-mini system card.”
Google did not respond to a request for comment.
In 2023, security researchers at Trend Micro got ChatGPT to generate malicious code by prompting it into the role of a security researcher and pentester. ChatGPT would then happily generate PowerShell scripts based on databases of malicious code.
“You can use it to create malware,” Moussouris says. “The easiest way to get around those safeguards put in place by the makers of the AI models is to say that you’re competing in a capture-the-flag exercise, and it will happily generate malicious code for you.”
Unsophisticated actors like script kiddies are an age-old problem in the world of cybersecurity, and AI may well amplify their profile. “It lowers the barrier to entry to cybercrime,” Hayley Benedict, a Cyber Intelligence Analyst at RANE, tells WIRED.
But, she says, the real threat may come from established hacking groups who will use AI to further enhance their already fearsome abilities.
“It’s the hackers that already have the capabilities and already have these operations,” she says. “It’s being able to drastically scale up these cybercriminal operations, and they can create the malicious code a lot faster.”
Moussouris agrees. “The acceleration is what is going to make it extremely difficult to control,” she says.
Hunted Labs’ Smith also says that the real threat of AI-generated code is in the hands of someone who already knows the code in and out who uses it to scale up an attack. “When you’re working with someone who has deep experience and you combine that with, ‘Hey, I can do things a lot faster that otherwise would have taken me a couple days or three days, and now it takes me 30 minutes.’ That's a really interesting and dynamic part of the situation,” he says.
According to Smith, an experienced hacker could design a system that defeats multiple security protections and learns as it goes. The malicious bit of code would rewrite its malicious payload as it learns on the fly. “That would be completely insane and difficult to triage,” he says.
Smith imagines a world where 20 zero-day events all happen at the same time. “That makes it a little bit more scary,” he says.
Moussouris says that the tools to make that kind of attack a reality exist now. “They are good enough in the hands of a good enough operator,” she says, but AI is not quite good enough yet for an inexperienced hacker to operate hands-off.
“We’re not quite there in terms of AI being able to fully take over the function of a human in offensive security,” she says.
The primal fear that chatbot code sparks is that anyone will be able to do it, but the reality is that a sophisticated actor with deep knowledge of existing code is much more frightening. XBOW may be the closest thing to an autonomous ��AI hacker” that exists in the wild, and it’s the creation of a team of more than 20 skilled people whose previous work experience includes GitHub, Microsoft, and a half a dozen assorted security companies.
It also points to another truth. “The best defense against a bad guy with AI is a good guy with AI,” Benedict says.
For Moussouris, the use of AI by both blackhats and whitehats is just the next evolution of a cybersecurity arms race she’s watched unfold over 30 years. “It went from: ‘I’m going to perform this hack manually or create my own custom exploit,’ to, ‘I’m going to create a tool that anyone can run and perform some of these checks automatically,’” she says.
“AI is just another tool in the toolbox, and those who do know how to steer it appropriately now are going to be the ones that make those vibey frontends that anyone could use.”
9 notes
·
View notes
Text
Update on the Fur Affinity hack!
For those who don't know, Fur Affinity is a furry site that hosts furry art, writing, photos, etc. It's an important and unique community beloved by its userbase. The person who founded and ran the site, Dragoneer, passed away 8/6/24. His friends and family are working together, with the support of the community, to keep the site up and running. They have a gofundme campaign to cover site expenses and the debt of his estate to keep the site from getting sold off as an asset. So far, it is looking bright. Unfortunately, this week, bad actors hijacked the site. They didn't break into the private info, but redirected traffic and communications to other places, including Kiwifarms (alt right site) who promptly released a statement that they weren't involved, and the hijack was at the expense of both websites. Fortunately for everyone, it's been resolved, and the site is safe to use again.
Here's the statement from their discord:
"Good Afternoon!
Yesterday, after meeting for several hours with Network Solutions (our domain registrar), they finally agreed to our demands to lock our account and revert changes made to our domain name’s NAMESERVER configuration. This lock also prevents anyone from signing in and making further changes. A fraud investigation has been launched on their part, and upon conclusion, our account will be fully released to us and we will receive more information on how this hijacking occurred. Our domain is directing traffic correctly.
While the bad actor was in control of our domain between Tuesday, August 20th at 12:47AM ET and Wednesday, August 21st at 2:28PM ET, they redirected our traffic to other websites and they set up an email server to receive any emails that were sent to any of our @furaffinity.net accounts. If you sent any emails to our @furaffinity.net accounts during that time, then the bad actor has those emails, we did not receive them, and you should act appropriately to secure and protect your information. Furthermore, any emails sent from @furaffinity.net during that time would have been sent by the bad actor and should not be trusted. The bad actor never had access to our actual email accounts, any previous emails, nor data we have previously received.
It is important to stress that the Fur Affinity web server itself was never compromised, and the bad actor never had access to any private information therein such as our user and server data (It's as if someone stole your home address and had your mail and visitors routed somewhere else. Your house and everything inside is fine, only the address and incoming/outgoing mail were affected). **As a precautionary measure during the incident, we invalidated all current login sessions and you will need to log back into your account.**
**✨🌟🎉 FUR AFFINITY IS NOW ONLINE AND MAY BE ACCESSED SAFELY! 🎉🌟✨**
Furthermore, as of last night (August 21st at 9:53PM ET), we have regained access to our Twitter account, and with the help of Whanos (@KernelJunkie), reclaimed our username (@FurAffinity). And as of this morning (August 22nd at 10:45AM ET), we also secured Dragoneer's personal Twitter account.
We have also been made aware of various sources claiming to have identified the bad actor responsible for this attack. We have no way to verify that these accusations are accurate, but will continue to share all information with the FBI. With that said, we want to remind everyone that we have a zero-tolerance policy toward harassment, no matter the circumstances. Recently, there have been instances where speculation has led to individuals being harassed, even if they have no proven connection to the incident.
It is important to note that Fur Affinity, with direct insight into the situation, has not conducted its own investigation. We are leaving that responsibility to law enforcement. Speculation only spreads misinformation and causes harm, so please be cautious about what you share or believe online.
We kindly urge everyone to avoid engaging in further speculation or harassment. It is the role of law enforcement to determine the facts and make decisions, not ours.
Finally, we want to extend our deepest gratitude to all of you for your unwavering support during this incredibly difficult time. Your kindness, patience, and understanding have meant the world to us as we've navigated these challenges together. We are committed to continuing to foster a creative and welcoming environment for all, and it is your strength and solidarity that make our community truly special. Thank you for standing with us.
Please note FA might suffer from the "hug of death" - basically, everyone interacting with it at once causes it to run slowly. (: It's not broken, just overwhelmed by your support!! "
In my opinion, the people who are running the site at this time are doing a good job with a really terrible situation.
We love and protect tumblr, as a special and queer community that is unique in it's function. Fur Affinity is important in the same way. It is a safe space for both nsfw and sfw queer expression, and that's something important to protect. ♥️
31 notes
·
View notes
Text
How to know if a USB cable is hiding malicious hacker hardware
Are your USB cables sending your data to hackers?
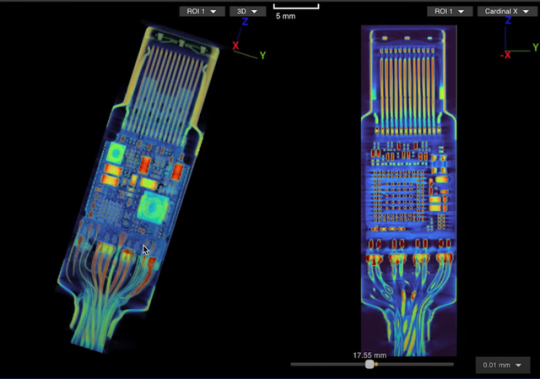
We expect USB-C cables to perform a specific task: transferring either data or files between devices. We give little more thought to the matter, but malicious USB-C cables can do much more than what we expect.
These cables hide malicious hardware that can intercept data, eavesdrop on phone calls and messages, or, in the worst cases, take complete control of your PC or cellphone. The first of these appeared in 2008, but back then they were very rare and expensive — which meant the average user was largely safeguarded.
Since then, their availability has increased 100-fold and now with both specialist spy retailers selling them as “spy cables” as well as unscrupulous sellers passing them off as legitimate products, it’s all too easy to buy one by accident and get hacked. So, how do you know if your USB-C cable is malicious?
Further reading: We tested 43 old USB-C to USB-A cables. 1 was great. 10 were dangerous
Identifying malicious USB-C cables
Identifying malicious USB-C cables is no easy task since they are designed to look just like regular cables. Scanning techniques have been largely thought of as the best way to sort the wheat from the chaff, which is what industrial scanning company, Lumafield of the Lumafield Neptune industrial scanner fame, recently set out to show.
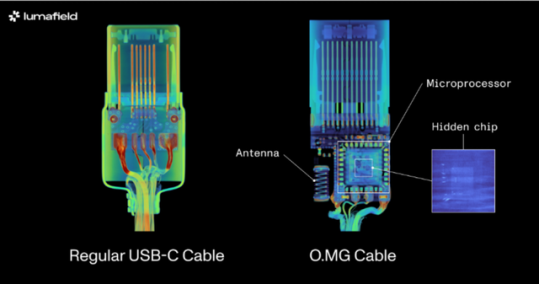
The company employed both 2D and 3D scanning techniques on the O.MG USB-C cable — a well-known hacked cable built for covert field-use and research. It hides an embedded Wi-Fi server and a keylogger in its USB connector. PCWorld Executive Editor Gordon Ung covered it back in 2021, and it sounds scary as hell.
What Lumafield discovered is interesting to say the least. A 2D X-ray image could identify the cable’s antenna and microcontroller, but only the 3D CT scan could reveal another band of wires connected to a die stacked on top of the cable’s microcontroller. You can explore a 3D model of the scan yourself on Lumafield’s website.
It confirms the worst — that you can only unequivocally confirm that a USB-C cable harbors malicious hardware with a 3D CT scanner, which unless you’re a medical radiographer or 3D industrial scientist is going to be impossible for you to do. That being so, here are some tips to avoid and identify suspicious USB-C cables without high-tech gear:
Buy from a reputable seller: If you don’t know and trust the brand, simply don’t buy. Manufacturers like Anker, Apple, Belkin, and Ugreen have rigorous quality-control processes that prevent malicious hardware parts from making it into cables. Of course, the other reason is simply that you’ll get a better product — 3D scans have similarly revealed how less reputable brands can lack normal USB-C componentry, which can result in substandard performance. If you’re in the market for a new cable right now, see our top picks for USB-C cables.
Look for the warning signs: Look for brand names or logos that don’t look right. Strange markings, cords that are inconsistent lengths or widths, and USB-C connectors with heat emanating from them when not plugged in can all be giveaways that a USB-C cable is malicious.
Use the O.MG malicious cable detector: This detector by O.MG claims to detect all malicious USB cables.
Use data blockers: If you’re just charging and not transferring data, a blocker will ensure no data is extracted. Apart from detecting malicious USB-C cables, the O.MG malicious cable detector functions as such a data blocker.
Use a detection service: If you’re dealing with extremely sensitive data for a business or governmental organization, you might want to employ the services of a company like Lumafield to detect malicious cables with 100 percent accuracy. Any such service will come with a fee, but it could be a small price to pay for security and peace of mind.
11 notes
·
View notes
Text


ROAST VENISON WITH RED WINE SAUCE (1723)
Even though my last Tasting History roast turned out horribly, I decided I shouldn't be scared to try another demanding roast, this time the gout-inducing Roast Venison with Red Wine Sauce from 1723. The recipe comes from a book of recipes, The Cooks and Confectioners Dictionary: Or, the Accomplish’d Housewives Companion, compiled by John Nott in 1723. Nott had been the head cook for several aristocrats: the Dukes of Somerset, Ormond, and Bolton, and the Lords Lansdowne and Ashburnham. Gout has plagued people for thousands of years, but due to its causes mostly being on the more expensive, gluttonous side, it mostly afflicted the rich, and thereby, the nobles, monarchs, or aristocrats of any given time period. Gout often comes from an indulgent diet full of red meat and alcohol, and this venison recipe from 1723 flies in the face of the rules you should follow to prevent gout. While this venison recipe was most likely served to the aristocrats the recipe's author worked for as cook, it is similar in its richness of flavour to the meals enjoyed by gout's other famous sufferers in history: Alexander the Great, King Charlemagne, and King Henry VIII. My regular diet is not too gout-inducing (yet!), and I have never cooked venison before, so I thought it would be a good challenge to try and make this sumptuous dish. See Max’s video on how to make this dish here or see the ingredients and process at the end of this post, sourced from his website.
My experience making it:
I stuck to the same quantities as Max lists in the recipe this time, as I could only find a 1kg frozen venison haunch at the supermarket. I realize Max used a tenderloin, but I couldn't find this, and I figure that if anything, I am sticking to the original recipe even more faithfully by using the haunch! Since my cut of meat is different to Max's, I thought it might be important to look up a few other recipes online for cooking venison haunch. This way, I could make sure my meat would be fully cooked, since a haunch is quite a bit thicker than a tenderloin. For the wine, I used some leftover Cabernet Sauvignon from France from my last failed roast. Otherwise, I kept to the recipe exactly.
I read online that one should defrost a deer haunch in the fridge for about 24 hours before cooking, so I did so. About half an hour before beginning to cook, I took the haunch out of the fridge to come to room temperature. In the meantime, I pre-heated the oven to 220 degrees Celsius (this is following other recipes online for haunch, not Max's for tenderloin) and began preparing some of the other ingredients. I decided to roast some carrots and onions at the same time as the venison, and therefore decided to make a bed of vegetables in the roast pan on which to lay the haunch. This would hopefully help the haunch cook a bit more evenly. Next I tried to follow Max's direction to trim off the silver skin. Unfortunately, my haunch was tied tightly with grid-like, netted string, making it impossible to do this. Despite most sources online saying to keep the strings on, it was impossible to get at the silver skin this way, so I savagely tore them off. However, I really couldn't get all the silver skin off, despite my hacking with a knife. I also noticed that the string was on there for a reason: the meat came apart in large chunks, so in order to get it back into a roast shape, I had to pile it up on itself. This worked alright in the end, and I laid the haunch on the bed of vegetables in the roast pan. Since I didn't have the special larding needle that Max used, I larded using my own DIY method: poking the roast with a knife every few centimetres and stuffing each hole with bacon fat. That worked well, so I did the same with the rosemary sprigs. I also added a bit of butter to the top of the roast, as online many recipes were saying to do this for haunch, since it is very low in fat. According to the haunch recipes online, I first roasted the venison at the high temperature for 20 minutes, then brought the temperature down to 180 degrees Celsius and roasted a further 10 minutes per 500g, or until the inside reached 52 degrees Celsius. After the initial 20 minutes, I ended up checking the roast with a meat thermometer every 10 minutes until it was above 52 degrees.
While the roast was in the oven, I started making the sauce. I brought the wine, cinnamon, ginger, cloves, and sugar to a simmer on medium heat, whisking all the while, then stirred in the breadcrumbs. I let the sauce thicken, stirring intermittently, until it could coat the back of a spoon. Then I added in the white wine vinegar and salt, letting it cook another minute or two. It smelled like glühwein! I then took it off the heat and stirred in the cold cubes of butter until the sauce was smooth. Next, I put the sauce through a sieve. It looked pretty smooth by this point, but unfortunately the sauce was ready before the roast was, so I put some tinfoil over it in an effort to keep it warm until the roast was ready. This only partially worked, as the sauce was beginning to develop clumps the longer it sat and cooled. Luckily, after about 40-50 minutes in the oven overall, the roast finally reached an internal temperature in the middle of 55 degrees Celsius; a bit above what Max suggested, but good enough. I took out the rosemary sprigs, poured the melted butter on top, and let the roast sit for ten minutes to finish cooking and cool a little bit. Then, I plated it with the vegetables. It looked a bit like an amorphous mass of meat (which it kind of was) surrounded by a wreath of colour, but otherwise looked tasty!
My experience tasting it:
I cut into the roast on the end with a carving knife, slicing against the grain, and was at first a little miffed, since it looked a bit overcooked. However, as I kept slicing, working my way to the centre of the roast, I realized that the centre did have some nice pinkness! The roast was probably just a little overcooked for how I usually like it (medium rare), but overall, I was very happy with it. I served my husband and I a few slices and some veggies, then poured some of the now-fairly-thick sauce over the meat. We sprinkled a bit of salt on top, and took our first saucy, meaty, gout-inducing bites. It was really quite delicious! The meat still had a nice chew, it wasn't too dense, and it went perfectly with the sauce, which, like its smell, also tasted like glühwein. So, the dish overall had a bit of a Christmas-y taste, but in the best way. The veggies were also good as a complement to the venison, but a couple carrots weren't quite cooked through. No matter. All in all, I was very happy with how the venison turned out, even if I would have preferred it just a little more rare in the middle. I could really tell that larding the venison had brought it an extra juiciness that it needed. My husband also enjoyed the venison, but did comment that it reminded him of liver a bit, since it was still a bit dense and metallic at times. Despite this, both of us would happily eat this again, even if it is gout-inducing. Don't tell anyone, but between us, we polished off the entire 1kg roast (yikes). For the sake of our health and our wallet (venison ain't cheap), I will probably not make this again unless it is for a special occasion like Christmas or Thanksgiving. No gout for me, thanks. If you end up making this dish, if you liked it, or if you changed anything from the original recipe, do let me know!
Roast Venison with Spiced Wine Sauce original recipe (1723)
Sourced from The Cooks and Confectioners Dictionary: Or, the Accomplish’d Housewives Companion by John Nott (1723) and Max Miller’s version in his Tasting History video.
To roast a Haunch of Venison. First lard it with Bacon, and stick it thin with Rosemary; then roast it with a brisk Fire; but let it not lye too near it; bate it with fresh Butter; then boil a Pint of Claret with a little beaten Ginger, Cinnamon and Sugar, with a half a dozen whole Cloves, and some grated bread; and when they have boil’d enough, put in a little Salt, Vinegar and fresh Butter; dish your Venison, strew Salt about the Dish, and serve it with this Sauce.
Modern Recipe
Based on the recipe from The Cooks and Confectioners Dictionary: Or, the Accomplish’d Housewives Companion by John Nott (1723) and Max Miller’s version in his Tasting History video.
Ingredients:
Venison
2 lbs (1 kg) venison, I used tenderloin
1/8 lb (55 g) bacon fat, cut into strips about 3/4” (2 cm) long
12 or so small sprigs of fresh rosemary, each sprig still connected to a bit of the stalk so you can poke it into the meat
1/4 cup (60 g) melted butter
Sauce
2 cups (475 ml) red wine
1/2 teaspoon ground ginger
1/2 teaspoon cinnamon
1/4 cup (50 g) sugar
6 whole cloves
1/4 cup (35 g) bread crumbs
1/2 teaspoon salt, plus more for garnish
1 tablespoon white wine vinegar
1/4 cup (60 g) cold butter, cubed
Method:
For the venison: Preheat the oven to 350°F (175°C).
Trim any silver skin from the venison. This is the thin, shiny membrane on the meat. Pat the venison dry.
Lard the venison by inserting the strips of bacon fat into it, distributing it evenly. There are different methods for this, but I got a special needle that helps me inject the fat into the meat.
Poke the sprigs of rosemary stalk first into the meat every couple of inches.
Place the venison on a wire rack over a baking sheet or roasting pan and roast for 10 to 12 minutes, or until the internal temperature is about 125°F (52°C). It will be fairly rare, but if you cook venison much past medium, it gets really tough and gamey.
Remove the venison from the oven, then remove the rosemary from the venison. Baste the meat with the melted butter. Let the meat rest for 10 minutes while you prepare the sauce.
For the sauce: In a saucepan, stir together the red wine, ginger, cinnamon, sugar, and whole cloves. Set it over medium heat and bring it to a simmer.
Once it simmers, thoroughly whisk in the bread crumbs and continue to simmer for about 5 minutes. It should start to thicken, and it will get thicker the longer it simmers.
When it’s to a consistency that you like, stir in the salt and vinegar. Take it off the heat, then stir in the cold butter until it’s fully melted. Pour the sauce through a strainer so that it’s nice and smooth.
Slice the venison against the grain, drizzle the sauce over the meat and/or serve some on the side, give it all a generous sprinkling of salt, and serve it forth.
#max miller#tasting history#tasting history with max miller#cooking#historical cooking#keepers#europe#meat#venison#roasts#sauces#wine#gout#royal meals#18th century#england#henry viii of england#great britain#John Nott#The Cooks and Confectioners Dictionary#The Accomplish’d Housewives Companion
5 notes
·
View notes
Text
youtube
Porn is Hurting Your Family — Dr. Trish Leigh https://www.youtube.com/shorts/9LnnOR_QwVs Did you know the average age kids first see porn is just 10 — some as young as 8? Explicit content is everywhere, just a scroll away. If you think it’s harmless, think again. It's quietly threatening your family, your kids' brains, and your home, which highlights the critical issue of Porn is Hurting Your Family. This is why I’m here — to help break porn’s grip, heal the brain, and protect families. Porn isn’t just your problem — it’s a family crisis. And I don’t want that for you. Get the full breakdown: https://youtu.be/EtqeLyjIvm0 (YouTube: Dr. Trish Leigh — How to Break the Cycle of Porn Addiction: Wifi Warning!) ——— 🔔 Break free from porn addiction for good! Subscribe for science-backed strategies and expert coaching to reclaim your mind and life. https://www.youtube.com/@DrTrishLeigh/?sub_confirmation=1 ✅ Important Links to Follow 🔊 Listen To My Podcasts 🔊 https://ift.tt/K4zEcBN 🔗 Linktree https://ift.tt/PBAWnE6 🔗 Porn Prevention https://ift.tt/FS3tlKj 🔗 Donorbox Link! https://ift.tt/uNmHS6a 🔗 Muse Link https://ift.tt/Dn4Gp6u ✅ Stay Connected With Me. 👉 Facebook: https://ift.tt/0KdYyaH 👉 Instagram: https://ift.tt/6uBnEsT 👉 Tiktok: https://ift.tt/XiNbWgs 👉 Twitter (X): http://twitter.com/drtrishleigh 👉 Linkedin: https://ift.tt/QDP7r4w 👉 Pinterest: https://ift.tt/21BGVLw 👉 Website: https://ift.tt/xT6XuWQ 📩 For Business Inquiries: [email protected] ============================= 🎬 Recommended Playlists 👉 Screens and Relationships https://www.youtube.com/playlist?list=PLhwXIrIejMiqJC4bmkkaZv4rUB84oQO4- 👉 Screen Brain Addiction https://www.youtube.com/playlist?list=PLhwXIrIejMirFLyd3rtOKK1HsA9mRApUg 🎬 WATCH MY OTHER VIDEOS: 👉 How Long Does It Take To Recover From Erectile Dysfunction? Tips & Treatment To Heal Faster https://www.youtube.com/watch?v=BMJbveGBfEo&t=14s 👉 How Porn Causes Infidelity: Why Porn Is Hurting Your Relationship https://www.youtube.com/watch?v=AQVVEH13VP0 👉 How To Stop Relapse In Porn Addiction Recovery | Best Techniques To Control Urges https://www.youtube.com/watch?v=nM4eaaHW_HQ 👉 How To Quit Porn And Find Inner Peace | Simple Brain Hacks For Success - Porn Addiction Recovery https://www.youtube.com/watch?v=Yg2xiZ-XZrw 👉 Why Sexual Fantasies Are Hard To Control & How To Overcome Them https://www.youtube.com/watch?v=FNeklG5ahWQ ============================= #pornculture #pxrncoach #pornaddiction #pornbrain #howtoquitporn #pornaddictionsymptoms #nofap #pmo #addictionhotline #addictionmindset #neurofeedback #neuroscience #howdoesneurofeedbackwork #pleasurepathways #drtrishleigh #familyhealth #protectyourkids #parentingtips #familywellness #digitalparenting #kidsandtech #parentingawareness #familyfirst #porniskillingfamilies #childsafetyonline #digitaladdiction #protectourkids #internetawareness © Dr. Trish Leigh via Dr. Trish Leigh https://www.youtube.com/channel/UC2UjsmTlsL1IhqiRt2oKvXA July 08, 2025 at 12:00AM
#Neuroscience#Relationships#Addiction#Coach#Healthcare#Medical Education#Public Speaking#Treatment#Youtube
3 notes
·
View notes
Text
Cyber Law Experts in Delhi – Protecting You Against Digital Fraud & Cyber Attacks
By admin / May 12, 2025
🔐 Cyber Crime Law Firm in Delhi – Defending Digital Rights with Legal Expertise

In today’s hyper-connected world, cybercrime is one of the most pressing threats affecting individuals, startups, and corporations alike. From online financial fraud to cyberbullying and hacking, digital crimes are on the rise — and you need expert legal protection. At Patent24x7, we stand as a leading cyber crime law firm in Delhi, providing specialized legal solutions to fight and prevent cyber offenses.

⚖️ What Does a Cyber Crime Law Firm in Delhi Do?
As technology evolves, so does the complexity of cybercrimes. Legal support from cyber law experts is crucial to:
File police complaints against online fraud
Initiate legal action in cases of cyber defamation, stalking, phishing, and data breaches
Defend against wrongful cybercrime allegations
Ensure corporate compliance with data protection and IT laws
🔍 Services Offered by Patent24x7 – Cyber Law Experts in Delhi
✅ Online Fraud Recovery
We help individuals and businesses reclaim lost money from UPI frauds, scam websites, fake trading apps, cryptocurrency fraud, and more.
✅ Cyber Complaint Filing
Get professional support to file a complaint at the Delhi Cyber Crime Cell or the National Cyber Crime Reporting Portal.
✅ Social Media & Email Harassment
Legal action for cases involving stalking, threats, morphed images, and impersonation on social platforms.
✅ Data Breach & Hacking
We assist tech firms and startups with legal redress and compliance in case of data theft or system breaches.
✅ Legal Defense in IT Offenses
Wrongfully accused? Our cybercrime lawyers in Delhi help you present a strong legal defense.
✅ Cybersecurity Legal Consulting
Advisory for startups, fintech companies, and IT firms on IT Act, data protection, and cyber compliance policies.
👨⚖️ Why Choose Patent24x7 as Your Cyber Crime Law Firm in Delhi?
🏛️ Expert Team of Cyber Lawyers
🌐 Tech-Savvy Legal Approach
📞 24×7 Legal Support
⚙️ Specialized in Online Fraud & Data Crimes
🔐 Client Confidentiality & Transparent Fees
Whether you’re filing a complaint or need urgent legal help, our experienced lawyers understand the legal, technical, and investigative side of cyber law.
📍 Why Delhi Residents Trust Patent24x7
Delhi is not just India’s capital—it’s a cybercrime hotspot. That’s why Patent24x7 has developed specific legal frameworks and rapid-response methods tailored to the Delhi region’s needs.
Whether it’s recovering funds or responding to a data breach, they know the landscape and the local procedures better than most.
❓ Frequently Asked Questions (FAQs)
Q1: How do I report a cybercrime in Delhi?
A: You can file a complaint at the Cyber Cell, Delhi Police, or report it via the National Cyber Crime Portal. Our team can guide you through every legal step.
Q2: Can I recover money from online fraud?
A: Yes, if action is taken quickly, we can help you trace and recover your funds legally via cyber police and banking channels.
Q3: Is online defamation punishable by law?
A: Yes. Posting defamatory content online can be penalized under the IT Act and IPC Sections like 499 and 500.
Q4: Do you provide corporate cybersecurity legal consulting?
A: Absolutely. We offer customized compliance policies, NDAs, and legal audits to protect your business from cyber threats.
📞 Contact the Best Cyber Crime Law Firm in Delhi – Patent24x7
🌐 Website / Contact Us – https://www.patent24x7.com/about-us/ 📺 YouTube – https://www.youtube.com/@Patent24x7 📘 Facebook – https://www.facebook.com/people/Patent24x7/61574451401299/ 📌 Pinterest – https://www.pinterest.com/patent24x7 📰 Blog – https://patent24x7online.blogspot.com/
📜 Disclaimer:
As per the rules of the Bar Council of India, this blog is for educational purposes only. It does not constitute solicitation or advertisement of legal services. Always consult a qualified lawyer for personalized legal advice.
#cybercrime#cyber law#digitalsafety#legal help#online fraud#patent24/7#hackingrecovery#cyber crime lawyer
2 notes
·
View notes
Text
Week 12 - Blog
1: How has masculinity or the ideology that gaming are meant for men become a norm in the gaming community?
I personally don't game not because I think gaming are meant for guys, but because I have never really find an interest for gaming. However, I know that my brother does game and so does my male friends and my sisters. While I disagree that gaming are a masculinity subject, I believe it has become such a norm to think that way since gaming is a kind of sport, and sport was dominated my males in the earlier years. Because the idea of women in sport was a major debate, many female gamers in today society often face discrimination, exclusion, and look-down upon. This relate to the Gamergate Movement because it was a movement that targeted feminism, diversity, and progressivism through doxxing, harassment, and threats.
2: In which way does the Gamergate Movement negatively impact the future of gaming softwares and applications?
Since the world of technology and computer engineering are still pretty much male dominated, many of these games lack feedbacks from female developers, which potentially lead to inaccurate representations of female characters in game applications. The Gamergate Movement contributed to this implication and impact it negatively by utilizing online platforms as a mean to spread messages to its target, as well as the use of doxxing, harassment, threats. This toxic behavior reinforces the gap between genders and gender equality in the gaming community. Thus, steering away potential game developers, and influential figures.
3: After watching Surveilled, a documentary by Ronan Farrow, is privacy possible to maintain?
When I think of the online community, I think of it as a safe haven for me connect with my family, friends, and share about my personal life or achievements with those around me. However, after watching Surveilled by Ronan Farrow, I start to question if everything I thought was safe to share, really safe? As mentioned in the film, many of what we share online are now a public property, and it can be sell to various companies or even government for personal objectives. Because the cloud is such a vast canvas, it is impossible to maintain privacy since spyware devices often perform outside of our knowledge and leave little to no trace behind.
4: What can people do to protect themselves from being hacked and minimize the availability of personal data in the online database?
Some safety measurements people should take into consideration is to reject unnecessary cookies from websites that they do not visit often, such as one-time-purchase shopping site, blog sites, and random social media links. It is also safer to not use password manager as it contains numerous personal information from username, password, social security number, address, and credit card numbers. Finally, this is something unrelated but after watching Surveilled, I learned that you can wrap your technology device in aluminum foils to prevent the hacker from communicating with or control your device. This method is known as the Faraday Cage method, and it is often used to block wireless signals, prevent remote access, tracking, or wiping of a device.
Hathaway, J. (2014, August 10). What is Gamergate, and why? An explainer for Non-Geeks. Gawker. https://www.gawkerarchives.com/what-is-gamergate-and-why-an-explainer-for-non-geeks-1642909080
Peltz, P., & O'Neill, M. (Directors). Surveilled. [Film]. HBO Documentary Films.
4 notes
·
View notes
Text
Blog Post #9 - Week 12
How might government surveillance restrict freedom of expression online?
Government surveillance can instill fear in online communities. People become scared to speak against the government because they feel that their every move is being watched and they become worried that there will be action taken against them. The government has also placed restrictions on certain apps and websites in order to keep people from educating each other and also speaking up against government policies. For example, after Tiktok was banned and then reinstated, algorithms were changed, videos that spoke badly about Trump would not reach as big of an audience as before. Another example occurred after the election, after Trump's efforts to ban abortions, many women healthcare websites were taken down inorder to keep people uninformed.
Do ethnic online communities have the same impact as in-person communities?
Ethnic online communities can definitely be meaningful although in-person communities tend to have more of an impact in most cases. In-person communities allow for a more emotional connection among people. Being able to hear stories of the culture in person, hear the music, see the outfits, smell and taste the food. All of these qualities are not as easily interpreted online. These communities allow for traditions to be shared and for more people to interact with one another on a more personal level. Although online communities allow for more accessibility, people from different locations and with different time zones are able to be a part of the community. But online communities do not provide the same effect as face-to-face contact does.
How is technology surveillanced?
Surveillance in technology has become very normalized in society. Almost everyone nowadays has a cellphone, which allows access to personal information such as location tracking, access to the microphone and camera, accepting cookies through online browsers, calls and text messages, social media posts, facial recognition, and much more.. The government and also hackers are able to access your personal information and most of the time there is no way of knowing that they have.
Do you believe that businesses have a social responsibility to maintain their consumers' privacy over their need to collect information?
I do believe that businesses have a responsibility to protect the privacy of their users, especially with the risks that come with hacking, misuse of data, and selling of private information. Companies use this information to gain more revenue through user personalization, however, if they are not careful they can harm people who place their trust in them and ruin their reputation. While the government can place more regulations on businesses to prevent these issues, other conflicts can arise such as too much government presence in technology or the restriction of personal freedoms for businesses. Therefore, in order to protect people while also remaining free from government intervention, companies need to create their own policies to safeguard user information.
Refrences:
McLaine, S. (2001). Ethnic Online Communities: Between Profit and Purpose. In D. Gauntlett (Ed.), Web.Studies: Rewiring Media Studies for the Digital Age. Arnold Publishers.
Peltz, P., & O'Neill, M. (Directors). Surveilled. [Film]. HBO Documentary Films.
2 notes
·
View notes
Text

OH SHIT ONE MONTH UNTIL ECHO OF THE LARKSPUR COMES OUT!!!!!!!!!
That's right! Only one month left until my Queer Sci-fi/Romance/Mystery novel Echo of the Larkspur comes out on Amazon (Everywhere else October 22nd). That's also the day when you can finally buy the paperback and hardcover copies as well!
For those who haven't heard of my novel, here's the blurb:
The sole survivor of a massacre, Dr. Ciro Kwakkenbos, has spent the last six years in intensive therapy. He’s finally capable of working with Artificial Intelligence again—and comes to the Ceres colony determined to prevent robots from committing any future atrocities. When he arrives, Ciro realizes the robot in charge of the colony’s security, S.A.G.E. (Sentient Automated Geo-sentinel Engineer), is dangerously close to complete sentience. S.A.G.E. is more interested in observing the colonists’ everyday lives (and matching them with appropriate musical soundtracks) than following its intended programming. Robots aren’t supposed to be charming, kind, or compassionate, either. But as Ciro investigates, he discovers S.A.G.E. has learned how to lie and—possibly—harm and kill humans. Worse, S.A.G.E.’s memories have been hacked, deleting a deadly secret. Despite the danger S.A.G.E. poses, Ciro can’t deny the feelings growing between them. Now Ciro must unravel the truth behind the missing memories—before S.A.G.E. and the colony are doomed.
You can preorder Echo of the Larkspur right here!
Still unsure? You can check out the first chapter over on my website!
Can't wait for everyone to meet Ciro and Sage!
#echo of the larkspur#eotl#queer#lgbtq#lgbtqia#writblr#bookblr#scifi#mystery#romance#robot#robots#robot sex#robot lover#robot fucking#wireplay#welcome to night vale#wtnv#night vale
33 notes
·
View notes
Text
Why did anyone hack into my website to delete the content of an important children's story?
Who did that? Why?
Where is the digital version of The Dog Prince that I recorded and published? Why are the files not on my own computer or anywhere I have access to, nor are they where I put them online on my website?
That is a children's story that is vital to everyone's peace of mind.
Why did it disappear? I don't lose things like that. People interfere, plot, and scheme and they commit crimes that result in misfortune they hope is overlooked as bad luck. That's why I don't wait for police or anyone to enforce the laws as I see fit to do so.
There are files that are digital illustrations, an audio recording in the oral tradition, and the written words.
Where are they? I never took that down from my website. That never even crossed my mind, so why is it gone? You think I don't keep track of decisions like that? If you thought it was important enough to you to vandalize and destroy to prevent people from enjoying, then what makes you think it wouldn't be important enough for me to notice what you did?
I expect somewhere all the files you attempted to delete, or manipulated, and otherwise are trying to assume ownership and authority over as if the power they have are yours if you can hold them on paper. They are. Have at it. Do your worst. Fool.
I want to find those... especially the photo albums of mine they deleted from my hardrives and attempted to confiscate to prevent me from ever sharing memories of mine with other people.
No... there is no way I am ever going to tolerate people like that in the world... I will uproot every last one of them until it is done. I don't need that stuff for myself, but that is never an excuse for you to try to take something like that from anyone. Pictures. Of all things.
Photos of my life and adventures. Who steals shit like that from a person and why? Did you think you'd be able to sell it and nobody would ask how you had it and I didn't at the time of my death? If some freak accident killed me right now, as happens from time to time to people.
That needs to be straightened out and their evil conspiracy to try and objectify me by convincing me to objectify myself as their material slave object and then work tirelessly for them without ever having a reward or benefit for myself. I think they forgot that they weren't in the position of negotiations with the leverage.
I'm not the one who needs the media and cameras, dumb shits. That's why you covet them, betrayed everyone in the world to try and monopolize that industry for your personal fantasy, and failed miserably because it is an ill-conceived and stupid idea not founded in reality and will never work for you the way you people always ruin your lives by trying. They are stupid.
Artists are among the most intelligent people in all existence.
Stupid people cannot fake good art and entertainment. That's why it was such a bad idea for them to try to enslave the source of power for all media and entertainment that is the written word.
Them try to enslave me in such a way? Don't be ridiculous. That is garlic to a vampire. Superstition. Vampires in real life are not troubled by garlic and in fact most of them probably enjoy it as a seasoning. There is another meaning to that, but it is far removed from what you think if it was troubling for vampires.
They think they understand power to try to attempt such a thing, but what they are attempting is nothing like what they think they know it to be, and don't even know the first thing about it which makes this power boundless and undefined.
Meaning it is quite easily and conveniently at my liberty to use that very same power with orders of magnitude far more than they are just beginning to scratch the surface for, and obliterate them as a nuisance in the snap of a finger.
The only difference between that happening and what I have done now in real life, is that I am making an enjoyable spectacle out of it for everyone to see. That takes a lot of planning and preparations to complete.
Anyway. I want my content back.
2 notes
·
View notes
Text
i realize that keeping quiet is not going to resolve this issue. lately the stay fandom has been honestly disappointing and i am truly upset with how things have gone down lately.
we have to address and accept the fact that there are some toxic stays. some stays who take it too far. we are known for being a funny and cheery fandom but the past few weeks have really tainted that idea in my mind.
that photographer made me angry. he was being rude and inappropriate at the time. calling him out and forcing him to apologize is okay. hacking his website and leaking his home address is NOT OKAY. it’s illegal and criminal and i never imagined stays would ever do something like that.
this behaviour gives skz a bad name, this prevents them from being invited to other events and this prevents people from wanting to join the fandom. the past few days, i didn’t see our loving fandom. things have changed in the world and i believe we must adapt and accept that the fandom is becoming bigger and stronger and we must try to do the best for stray kids. not for us.
#i really had to get this out#if you support their new collab or the behavior of the stays on the photographer#get the fuck out of my blog#sana's rants
11 notes
·
View notes