#how to secure website from hackers
Explore tagged Tumblr posts
Text
#website protection#hacking#ethical hacking#how to secure your website#how to secure a website#how to secure website from hackers#how to protect your website from hackers#cracking#how to prevent hacking on website#how to secure your website from hackers#introduction to website hacking!#how to secure wordpress website#how to secure my website for free#how to secure a wordpress website#secure wordpress website#how to prevent hacking#how to recover from a website cyberattack
0 notes
Text
#WordPress Website Development#Why WordPress Security is Important?#What is the best wordpress security plugin?#How to protect wordpress site from hackers
1 note
·
View note
Text
Hey everyone it seems there a malicious individual trying to hack the sims cc community again and fill it with malware you need to stay vigilant as a creator and a downloader so
i have some tips for both to stay safe while downloading:
1- sims cc file extension is always .Package never download anything that is .exe
2- do not auto unpack zip files and rar files into your mods folder directly, open each zip or rar individually check the file extensions and drag them to your mods folder one by one
3- the only mods that have a .ts4script extension are ones that affect gameplay or how the game works, understand that if you are downloading cas or bb items you shouldn't have a .ts4script file
4- if you are downloading gameplay mods that do have .ts4script make sure that A) the creator hasn't announced on their pages that its infected B) you are downloading from a link provided by the creator of the mods themselves not something off of google or a link you got sent and make sure dates of upload match dated of announcements
5- if the mod or cc creator has retired and hasn't posted for a while LOOK AT THE DATES OF THE UPLOAD if it has been "updated recently" after the creator has left the community its most likely re-uploaded by a hacker and infected
6- download mod gaurd by Twisted mexi and keep it updated and keep your windows defender or malware detector Program up to date and always running do not disable it
7- make sure everything you download comes from a direct link from the cc creator, in this day and age do not trust link shortners, adfly, linkverse, etc get the universal bypass extension and ublock extension to stay safe but genuinely NEVER CLICK ON THOSE no matter how much the creator reassures you its safe it. is. NOT.
8- this is more of a general saftey precaution but, create a system restore point weekly before you run the game with new mods that way if anything happens you could have a chance to restore your windows to an earlier date before you downloaded anything.
9- BACK UP YOUR SHIT im serious right now either weekly or monthly put your files somewhere safe like a usb a storage card a hard drive even an online cloud if you dont have any of the previous.
10- files you should back up are your media from games and media everything else, any mods, games saves, work files, passwords, saved bookmarks, any documents txt files word files pdfs, links you saved, brushes or actions for Photoshop if you have any, any digital bills or certificates if you have any, and keep a physical list of all programs you have installed and where you installed them from
11- turn on any 2 factor authentication and security measures for any account you have
12- google and firefox have the option to check your paswords and emails against any data leaks USE THIS FEATURE and change any leaked passwords
13- regularly check your logged in sessions to make sure all the logged in devices or computers are yours and log out any that aren't and any old devices or unused sessions do this for every website and app you have an account on if available
14- change your passwords often. I know this is a hassle i know its hard to come up with new passwords but changing your passwords every few months will help you against anything mention previously that wasn't detected.
15- and as a cc creator check your cc and the accounts you host cc on and its uplaod and update dates make sure nothing has been changed without your permission :(
16- generally try not to get swept up in the "i must get it" fever you do not need to "shop" for mods weekly or monthly you do not need to download everything by that one creator you do not need to download new cc everytime you want to make a sim, im guilty of this so i know how hard it is to resist but take a breath and think "do i want this or do i need it" before downloading.
These are prevention methods i cant claim they are 100% will prevent any hacking but its better to be safe than sorry and these do keep you safe so
Brought to you by someone who has had their laptop ruined and data leaked from downloading cc once upon a time
3K notes
·
View notes
Text
Someone accessed my Gmail 2 days ago, compromising my linked accounts like Twitter and YouTube. Here's how it happened, why I fell for it, and what you can learn to avoid making the same mistake:
The scam I fell victim to was a cookie hijack. The hacker used malicious software to steal my browser cookies (stuff like autofill, auto sign in, etc), allowing them to sign in to my Gmail and other accounts, completely bypassing my 2FA and other security protocols.
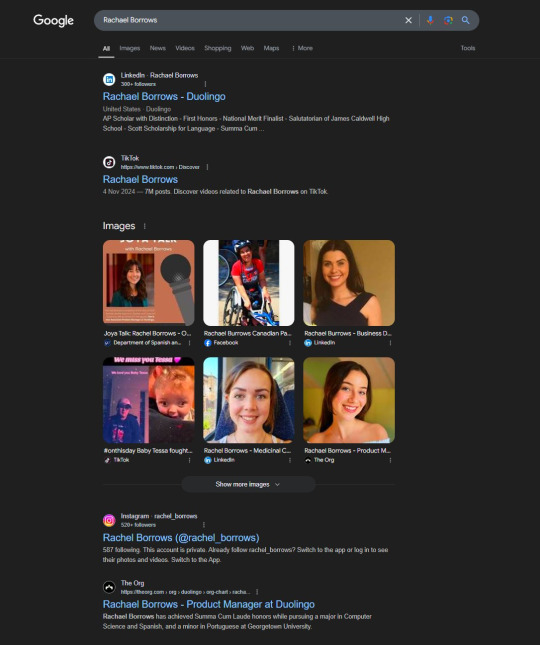
A few days ago, I received a DM from @Rachael_Borrows, who claimed to be a manager at @Duolingo. The account seemed legitimate. It was verified, created in 2019, and had over 1k followers, consistent with other managers I’d seen at the time n I even did a Google search of this person and didnt find anything suspicious.
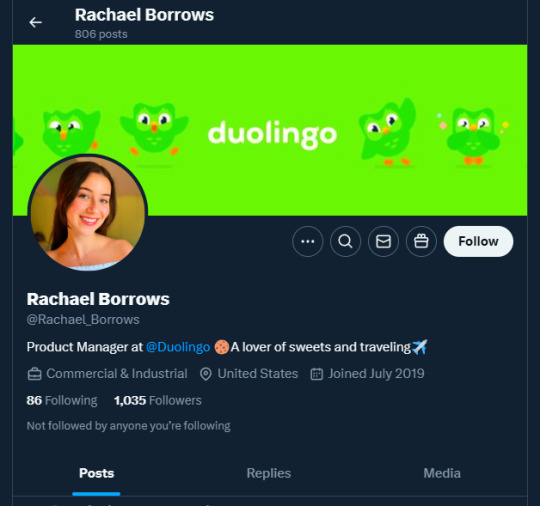
She claimed that @Duolingo wanted me to create a promo video, which got me excited and managed to get my guard down. After discussing I was asked to sign a contract and at app(.)fastsigndocu(.)com. If you see this link, ITS A SCAM! Do NOT download ANY files from this site.
Unfortunately, I downloaded a file from the website, and it downloaded without triggering any firewall or antivirus warnings. Thinking it was just a PDF, I opened it. The moment I did, my console and Google Chrome flashed. That’s when I knew I was in trouble. I immediately did an antivirus scan and these were some of the programs it found that were added to my PC without me knowing:

The thing about cookie hijacking is that it completely bypasses 2FA which should have been my strongest line of defense. I was immediately signed out of all my accounts and within a minute, they changed everything: passwords, 2FA, phone, recovery emails, backup codes, etc.
I tried all methods but hit dead ends trying to recover them. Thankfully, my Discord wasn’t connected, so I alerted everyone I knew there. I also had an alternate account, @JLCmapping, managed by a friend, which I used to immediately inform @/TeamYouTube about the situation
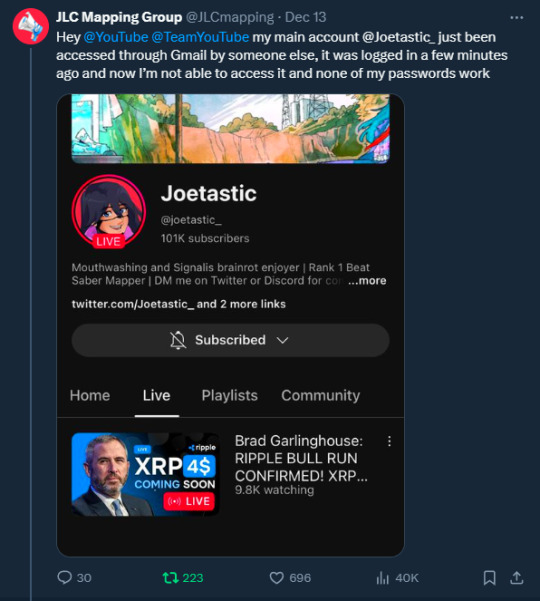
Meanwhile, the hackers turned my YouTube channel into a crypto channel and used my Twitter account to spam hundreds of messages, trying to use my image and reputation to scam more victims
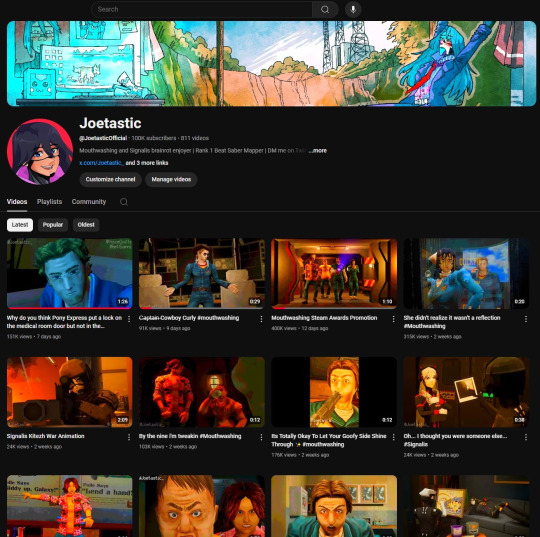
Thankfully, YouTube responded quickly and terminated the channel. Within 48 hours, they locked the hacker out of my Gmail and restored my access. They also helped me recover my channel, which has been renamed to JoetasticOfficial since Joetastic_ was no longer available.
Since then, I’ve taken several steps to secure my accounts and prevent this from happening again. This has been a wake-up call to me, and now I am more cautious around people online. I hope sharing it helps others avoid falling victim to similar attacks. (End)
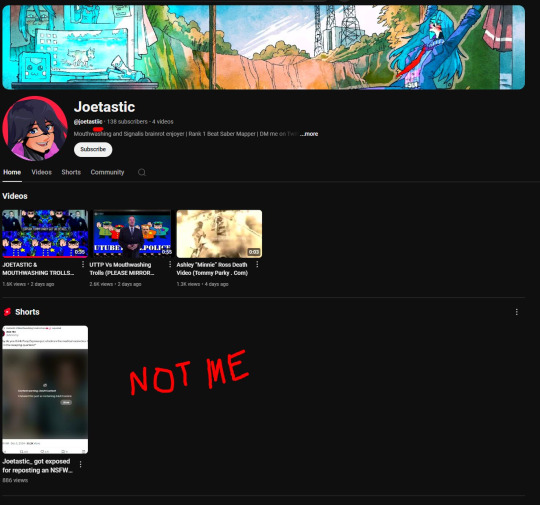
(side note) Around this time, people also started to impersonate me on TikTok and YouTube. With my accounts terminated, anyone searching for "Joetastic" would only find the imposter's profiles. I’m unsure whether they are connected or if it’s just an unfortunate coincidence, but it made the situation even more stressful.
3K notes
·
View notes
Note
I've seen you say a few times that it's a good idea to have a password manager; could you explain why? I always feel like I'm missing something when it's mentioned because it's phrased as if there's an obvious danger that password managers protect you from, but I'm honestly not sure how they help keep passwords secure.
The obvious danger is human nature. Humans are bad at creating passwords; your passwords are almost certainly easy to guess, repeated across different accounts, or both, because that is just how the vast VAST majority of people create passwords, because humans are bad at creating passwords. Everybody knows "the rules" for creating passwords (don't use the same password on multiple websites, don't include personal details in your passwords, don't use very common words or letter or number sequences in your passwords, don't tell other people your password) and people break all of those rules anyway.
A standalone (not in-browser like firefox or chrome password manager, though those are better than nothing) password manager stores your passwords, generates complex passwords for you, and can also be used for things like storing notes on passwords (like "did I put my MFA on my email or my cellphone or an app for this password?" or "here are the made-up answers to the security questions I used for this website because I definitely didn't use real answers or answers I'd used on previous websites" or "these are the bills associated with this credit card").
With the way the current security landscape works, there are two things that are extremely important when you are creating a password:
Uniqueness
Complexity
The overwhelmingly prevalent way that people get "hacked" these days is through credential stuffing.
Let's say that your private data was revealed in the Experian breach a decade ago. It revealed your name, email address, and phone number. Now let's also say that your private data was revealed in one of the many breaches from social media sites; that one revealed your name, email address, phone number, password, and security questions.
If someone wants to try to gain access to one of your accounts - let's say your bank account - if they have your name and phone number (usually extremely easy to find online), they can cross-reference that information with data that has been revealed in previous breaches - now they've got your name and your email address (which you probably used to sign up for your online banking and have ABSOLUTELY used as your login for accounts all over the place) and at least one password that you've used somewhere.
But the thing is, they don't have one password. They have every password associated with that email address that has ever been revealed in a breach. If you go to the site haveibeenpwned.com you can enter your email and see how many times your email address has appeared in a breach. You can compare that with the number of passwords that were revealed in those breaches and you can ask yourself "what did those passwords have in common?"
Because I can tell you, my Tumblr password from 2013, my Kickstarter password from 2014, and my Disqus password from 2017 (all revealed in various breaches) probably had a lot in common.
So, now the hacker has: your name, your email (which is probably your username), and various passwords they can try to use to log in. Did you use the same password for Facebook and Twitter eight years ago? Did you use parts of that password for creating your bank password? If you heard that twitter passwords were exposed in a breach you probably changed that password, but did you change the bank password that you built on the same structure? Probably not.
So what people will do is gather up all of this information and guess. They'll try your 2017 Disqus password to see if it will get access to your bank account. They'll try your 2020 Gravatar password. They'll try your 2024 Internet Archive Password.
And the reason they do this is because it works.
And the reason that it works is because we are all fucking garbage at remembering unique, complex passwords so instead of creating actually unique, complex passwords most people pick one memorable word or phrase, one memorable number, one unusual character, and *MAYBE* one feature of the site they're creating the login for and they use that template forever (1988Tumblrmacabre!, 1988Facebookmacabre!, 1988Ticketmastermacabre!) OR they create one password that they think is complex enough and use it across multiple sites with minor tweaks ($n0h0mi$hRu13z, sn0h0mishRul13z!, $n0h0mi$hWA) as needed for the sites' password requirements.
So most of what password managers do that is a drastic security improvement over people creating and memorizing passwords is that they create passwords that are functionally impossible to guess and functionally impossible to memorize. The problem with memorizing passwords (which is what you're doing if you're creating a bunch of passwords that you type in all the time) is that you can't actually remember all that many passwords so you'll repeat those passwords. The problem with creating passwords on your own is that passwords that humans create are pretty guessable. Even if you're doing a passphrase that's a long string of words you're probably working with common words ("correct horse battery staple" as opposed to "truculent zygote onomatopoeia frangible") and your password is more guessable than you'd really want it to be. Password managers don't do that, they generate gibberish.
Perhaps you are that rare person who gets out a set of dice and a notepad and rolls up every character for your password and memorizes it and never repeats, and if that's you, you could still benefit from a password manager because a password manager makes it easier to change that unique complex password when it is inevitably revealed in a breach.
So, okay, let's check in with where we're at:
Password managers mean that you don't have to memorize your password, which means that you don't need a password that is easy to memorize, which means that they can create passwords that are extremely complex and are therefore very difficult to guess. This protects you from crackers who will try to brute force your password.
Password managers mean that you don't have to remember extremely complex passwords for every account, which means that you are less likely to repeat your password in whole or in part across multiple accounts. This protects you from credential stuffers, who will try to use your password from one account that was revealed in a breach to open other accounts that were not.
Because password managers can generate and store complex passwords essentially instantly, you can replace passwords nearly effortlessly when there is a breach (no need to 'come up with' a new password, no issues with learning or memorizing it).
There are, however, advantages beyond that.
One major, MAJOR advantage of a properly-used standalone password manager is that it makes you safer from various kinds of phishing attempts and link hijacking. When you are setting up a password in your password manager (PWM from here on), you should be on the website that you want to log in to. The PWM will give you the option to save the domain that you're logging in to. That means the PWM will remember the correct URL for your Tumblr login so when you go to the tumblr login screen in the future, it will offer to fill those fields. What it will NOT do is offer to fill those fields if someone sends you an email that spoofs tumblr support and wants you to log in at "tumblr.co" or "tumblr-support.com." Knowing this, and knowing that you should be putting your credentials in through the PWM fill option rather than copy/paste, is a GREAT way to protect against phishing that is often overlooked and definitely under-discussed.
Another advantage is that a standalone PWM will let you store secure notes with your passwords so that you can do things like keep track of recovery codes for the website, or generate gibberish answers to security questions. Security questions and answers are often revealed in breaches, can't be reset by the user as easily as a password, are repeated across websites MUCH more than passwords, and can be used to take over an account and reset the password. You shouldn't be giving real security answers, or even fake-but-repeated security answers; you should treat each of those like a password that needs to be complex and unique, which means that they need to be stored someplace (like a password manager).
I also personally use my password manager to store my car insurance information, my driver's license info, and payment details for easy entry, making it convenient for a lot of thing beyond password storage. (Bitwarden. My password manager is bitwarden. I recommend Bitwarden. go to ms-demeanor.com and search "bitwarden" to learn more.)
As to how they keep your passwords safe, aside from ensuring that you don't enter your credentials into a skimming site, a good password manager is well encrypted. Your password safe should be functionally impossible to crack and what people tend to not realize is that a proper password manager (like bitwarden) doesn't keep all your passwords in one encrypted safe, each one of your passwords is in its own encrypted safe. If someone hacks Bitwarden it's not like using a huge amount of effort breaking into a bank vault and finding a big pile of money, it's like using a huge amount of effort breaking into a bank vault and finding a big pile of bank vaults. Each password within your vault requires decryption that is functionally impossible to crack (at least with a good password manager, like bitwarden, the password manager I recommend and think that people should use).
Additionally, just as, like, a side note: password managers never accidentally leave caps lock on or forget which characters are capital or lower case and don't require the use of two hands and focused attention on the keyboard. You're never going to mistype your password if the password manager is filling it, and you would not believe the number of people we support at work who require password resets because they are typing their password wrong and don't realize it.
TL;DR:
Password managers make better passwords than you can and they make it possible to instantly create, store, and enter complex passwords, which prevents password cracking and makes people less likely to reuse passwords. They are heavily encrypted and should be functionally impossible to access, and each individual password within the manager should also be encrypted if you use a good password manager. Password managers also prevent people from entering their credentials on scam sites by only filling on matched domains. Standalone password managers (not browser password managers) also allow users to create and store unique security questions and account details to prevent bad actors from gaining access with stolen security answers. The password manager I recommend is Bitwarden.
If people used password managers to create, store, and use unique and complex passwords, and if they did regular backups of their system I think that probably about half of the InfoSec field would be out of a job.
Please use a password manager!
2K notes
·
View notes
Text
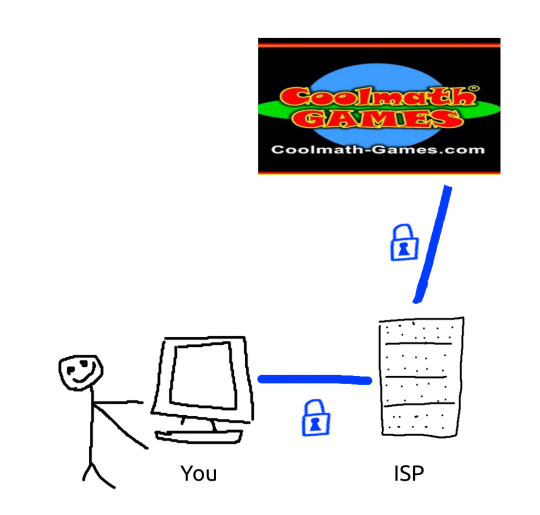
VPNs do not make you more secure
here's how they work!
first of all, most of your internet traffic is already encrypted via TLS (Transport Layer Security). Things that aren't encrypted are usually videogames or less important applications.
a VPN encrypts traffic between your computer and the VPN server you're using.
your Internet Service Provider (ISP) sits in the middle of that transaction.
cue the MS paint diagram
Without a VPN:
With a VPN:
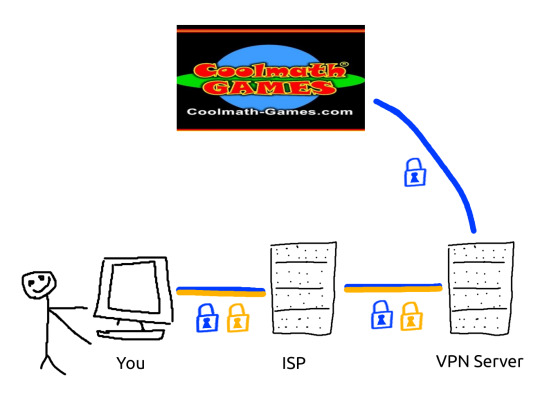
the traffic between your VPN server and the rest of the internet is not encrypted any further.
things that VPNs are good for:
bypassing geo-blocking
bypassing website blocks set up by your ISP
obscuring network traffic from your ISP
things that VPNs are not good for:
browsing the internet without having your activity logged. every company that gives internet service logs the activity, it's half of how they make sure they're not being hacked.
hiding information from the government. VPN providers WILL bend to subpoenas, they WILL turn over logs of your network activity.
cybersecurity. VPNs can't save you once the traffic is between them and the final destination. they don't analyze your traffic to detect and stop hackers, they don't add any encryption where it matters.
VPNs are not a shortcut to security. you cannot pay 15 dollars a month to forgo all responsibility for your own digital privacy. do your research, use a password manager, stay safe.
my friends i hope you find this information useful. you have been sold a lie. remember to show extreme skepticism to youtube sponsorships and journalism websites which sing their praises.
sources: i have a certificate iv in cybersecurity
2K notes
·
View notes
Text
(Epilogue!) Bill Dickey NSFW headcanons (and drabble)
MDNI!!! this is very much 18+ content, shoo! shoo!
Warnings: general gross behaviour, stalking, dick stepping (mild mention), humiliation, misogynistic terms and cuss words LMK if i missed anything!!
-----------------------------------------------------------------
One of those guys to buy a body pillow of his fav or one of a girl that looks like his crush
That thing reeks and we all know it
Only showers if absolutely necessary
soft stalks his person of interests
Uses websites like 4chan to find home camera's of girls near him
Remember that scandal that happened years ago? There were these cameras people has put up in around their houses and you were supposed to enter a passcode to get into your feed Except, most people didn’t do that. So, many hackers were able to easily get into people’s home cameras and watch them without them noticing One even made a site where you could find these cams for free and watch people. This was sent all over 4chan and enjoyed by incel perverts all over the world
Some freaks would go as far as to use the microphone function to talk to people, others would send secret gifts to people’s doorstep’s after watching them, to freak em out
A public security notice was immediately thrown out there by the company when the site was discovered But a lot of people didn’t see the news, never checked their email and left their passcodes unused.
The site is still up, or the cams are at least still able to be hacked into
I know Bill is the type of bastard to find a pretty girl who was too much of a dumb bimbo to change her passcode and watch her. How convenient she has a camera in her bedroom.
Secretly loves having his dick stepped on
and being humiliated by someone far bigger than him (preferably a big-chested bimbo doll)
His glasses fog up as hes fucking his fist while watching some porno
alternatively: he's watching you through a secret camera feed
Whimpers like a bitch in heat when he's getting close
Imagining you fucking bill and him uncharacteristically inviting you over to the Eltingville club
Joining a club meeting a week or so after fucking Bill and everyone knows but no one fucking says anything You’re gaming, probably some rpg with big chested ladies, when you suddenly blurt out how pathetic Bill really is, and how quickly he finished Bill puts on an act, calling you a braid dead femoid who doesn’t know what the fuck she’s talking about But deep down, his stomach is doing back flips because oh my god he’s so embarrassed and oh my god he has the biggest boner of his life right now
It goes without saying that before meeting you he had never touched a girl before, let alone fucked one
PWP below the cut
"Put it in already." You whine at Bill who is currently fumbling his cock against your leaking cunt. "S-Shut the hell up stupid bitch, let me take my god damn t-time."
You roll your eyes, leaning on your hand as you wait for him to push his cock into you. Sure it's barely over 5 inches but by god do you want it deep inside you right this second. And to think this guy had been following you home from the bus stop not even an hour ago. Christ, what was wrong with you? "You sure y'don't want me to help, dumbass?" You groan, not waiting for an answer and grabbing his cock. Surprisingly he actually has a condom on, even though he genuinely forgot they existed for a split second. ("Oh man I forgot about those.." He just wanted a creampie like in a real porn, man!)
"He-Hey! Careful with that you're gonna rip it off you dumb cuu--nnttt.." His swear was cut short as you guided his swollen glans into your heat. "There we go, loser. Now move your hips, you do know how to do that, right? Or do I have to help you with that too?"
"Shut the hell up.." Bill tsk'ed, and slid the rest of his throbbing dick into your hot pussy. "F-Fuhhh.." He bit his lip so hard he was sure he was going to break skin any second.
"That's good huh?" You giggled, pressing your plump ass flush against his hips. His hairy tummy tickled against your butt slightly once your skin met.
"Oh my f-ff..." Bill's eyes rolled back, pressing himself as close to you as possible and promptly cumming hard into the condom you'd managed to find at the last second. His mind went blank as he pumped a thick load into your warm heat.
"You've got to be kidding me.." You snorted, clearly annoyed. That was your last condom for fuck's sake!
#bill dickey#bill dickey x you#bill dickey x reader#bill dickey smut#smut#eltingville smut#welcome to the eltingville club#headcanons#bill dickey headcanons
451 notes
·
View notes
Text

Matt Wuerker. Politico
* * * *
LETTERS FROM AN AMERICAN
March 11, 2025
Heather Cox Richardson
Mar 12, 2025
The stock market continued to fall today. The Dow Jones Industrial Average fell another 478 points, or 1.14%; the S&P 500 fell almost 0.8%; and the Nasdaq Composite fell almost 0.2%. The S&P 500 briefly held its own in trading today, but then Trump announced on his social media platform that he was going to double the tariffs on steel and aluminum from the new 25% rates to a 50% rate on Canada and might increase tariffs to “permanently shut down the automobile manufacturing business in Canada.”
Stocks fell again.
Unable to admit that he might be wrong, President Donald Trump is doubling down on the policies that are crashing the economy. In addition to his tariff threats, he also reiterated that “the only thing that makes sense is for Canada to become our cherished Fifty First State,” an outrageous position that he suddenly began to advance after the 2024 presidential election and which has Canadians so furious they are boycotting U.S. goods and booing the Star-Spangled Banner.
More than 100 top business leaders met with Trump today to urge him to stop destabilizing what had been a booming economy with his on-again-off-again tariffs. Mark Zandi, chief economist of Moody’s Analytics, told Jeff Stein and Isaac Arnsdorf of the Washington Post that in private, “[b]usiness leaders, CEOs and COOs are nervous, bordering on unnerved, by the policies that are being implemented, how they’re being implemented and what the fallout is. There’s overwhelming uncertainty and increasing discomfort with how policy is being implemented.”
The extreme unpredictability means that no one knows where or how to invest. Market strategist Art Hogan told CNN’s Matt Egan, “This market is just blatantly sick and tired of the back and forth on trade policy.” Yesterday, Delta Air Lines cut its forecasts for its first-quarter revenue and profits by half, a sign of weakening corporate and consumer confidence and concerns about the safety of air travel. Today, Southwest Airlines and United Airlines cut their forecasts, and American Airlines forecast a first-quarter loss.
When he talked to reporters, Trump reasserted that he intends to do what he wants regardless of the business leaders’ input. “Markets are going to go up and they’re going to go down, but you know what, we have to rebuild our country. Long-term what I’m doing is making our country strong again.” White House press secretary Karoline Leavitt advised, “If people are looking for certainty, they should look at the record of this president.”
Not everyone will find that suggestion comforting.
Trump backed off on his threat to raise the tariffs on Canadian steel and aluminum to 50%, but went ahead with his threat to place 25% tariffs on all imported steel and aluminum products. Those tariffs took effect at midnight.
In the face of his own troubles, Trump’s sidekick billionaire Elon Musk is also escalating his destructive behavior. Yesterday Musk’s social media platform X underwent three separate outages that spanned more than six hours. Lily Jamali and Liv McMahon of the BBC reported that Oxford professor Ciaran Martin, former head of the United Kingdom’s National Cyber Security Center, said that the outages appear to have been an attack called a “distributed denial of service,” or DDoS, attack. This is an old technique in which hackers flood a server to prevent authentic users from reaching a website.
"I can't think of a company of the size and standing internationally of X that's fallen over to a DDoS attack for a very long time," Martin said. The outage "doesn't reflect well on their cyber security." Without any evidence, Musk blamed hackers in Ukraine for the outages, an accusation Martin called “pretty much garbage.”
Four days ago, another of Musk’s SpaceX rockets exploded after takeoff, and now SpaceX’s Starlink internet service is facing headwinds. In February, Mexican billionaire Carlos Slim canceled his collaborations with Starlink after growing tensions with Musk culminated with Musk alleging on X that Slim is tied to organized crime. The loss of that deal cost Musk about $7 billion in the short term, but more in the long term as Slim will work with European and Chinese companies in 25 Latin American countries rather than Starlink. Slim has said he would invest $22 billion in those projects over the next three years.
Also in February, after U.S. negotiators threatened to cut Ukraine’s access to the 42,000 Starlink terminals that supply information to the front lines, the European Commission began to look for either government or commercial alternatives. The European Commission is made up of a college of commissioners from each of the 27 European Union countries. It acts as the main executive branch of the European Union.
On Sunday, Musk posted: “[M]y Starlink system is the backbone of the Ukrainian army. Their entire front line would collapse if I turned it off.” Poland pays for about half the Starlink terminals in Ukraine, about $50 million a year. Poland’s minister of foreign affairs, Radosław Sikorski, responded that “if SpaceX proves to be an unreliable provider we will be forced to look for other suppliers.” “Be quiet, small man,” Musk replied. “You pay a tiny fraction of the cost. And there is no substitute for Starlink.”
After all the tariff drama with Canada, last week Ontario also cancelled a deal it had with Starlink.
But perhaps the biggest hit Musk has taken lately is over his Tesla car brand. On February 6, Musk’s younger brother Kimbal, who sits on Tesla’s board, sold more than $27 million worth of shares in the company. Tesla chair Robyn Denholm sold about $43 million worth of Tesla stock in February and recently sold another $33 million. Tesla CFO Vaibhav Taneja has sold $8 million worth over the past 90 days. Yesterday, board member James Murdoch sold just over $13 million worth of stock.
Fred Lambert of Electrek, which follows the news about electric vehicles and Tesla, noted that Tesla stock dropped 15% yesterday, “down more than 50% from its all-time high just a few months ago.” “Tesla insiders are unloading,” he concluded.
Tesla sales are dropping across the globe owing to the unpopularity of Musk’s antics, along with the cuts and data breaches from his “Department of Government Efficiency.” Protesters have been gathering at Tesla dealerships to express their dismay. While the protests have been peaceful, as Chris Isidore of CNN reports, there have also been reports of vandalism. Tesla owners are facing ridicule as protesters take out their anger toward Musk on his customers, and at least one competitor is working to lure consumers away from Musk’s brand by offering a discount to Tesla owners.
Trump has jumped to Musk’s defense, posting just after midnight this morning that “Elon Musk is ‘putting it on the line’ in order to help our Nation, and he is doing a FANTASTIC JOB! But the Radical Left Lunatics, as they often do, are trying to illegally and collusively boycott Tesla, one of the World’s great automakers, and Elon’s ‘baby,’ in order to attack and do harm to Elon, and everything he stands for. They tried to do it to me at the 2024 Presidential Ballot Box, but how did that work out? In any event, I’m going to buy a brand new Tesla tomorrow morning as a show of confidence and support for Elon Musk, a truly great American.”
Indeed, today Trump used the office of the presidency to bolster Musk’s business. Teslas were lined up at the White House, where Trump read from a Tesla sales pitch—photographer Andrew Harnik caught an image of his notes. And then the same man who gave a blanket pardon to those convicted of violent crimes related to the January 6, 2021, attack on the U.S. Capitol called those protesting at Tesla dealerships “domestic terrorists” and promised that the government would make sure they “go through hell.”
Trump and Musk appear to have taken the downturn in their fortunes by becoming more aggressive. Martin Pengelly of The Guardian noted that in the middle of Monday’s stock market plunge, Trump posted or reposted more than 100 messages on his social media channel. All of them showed him in a positive light, including reminders of the 2004 first season of the television show The Apprentice, in which Trump starred: a golden moment in Trump’s past when his ratings were high and the audience seemed to believe he was a brilliant and powerful businessman.
Today, egged on by Musk, Trump pushed again to take over other countries. He told reporters: "When you take away that artificial line that looks like it was done with a ruler…and you look at that beautiful formation of Canada and the United States, there is no place anywhere in the world that looks like that…. And then if you add Greenland…that's pretty good."
The Trump administration also announced today it was cutting about half the employees in the Department of Education. The Senate confirmed Linda McMahon, who has little experience with education, to head the department on March 3 by a party-line vote. Shutting down the department "was the president's mandate—his directive to me," McMahon told Fox News Channel host Laura Ingraham. McMahon assured Ingraham that existing grants and programs would not “fall through the cracks.”
But when Ingraham asked her what IDEA stood for—the Individuals with Disabilities Education Act—she wasn’t sure, although she knew it was “the programs for disabled and needs.” Ingraham knew what the acronym meant but assured McMahon that after 30 years on the job, she still didn’t know all the acronyms. McMahon replied: “This is my fifth day on the job and I’m really trying to learn them very quickly.”
Musk lashed out at Arizona senator Mark Kelly on social media yesterday, after Kelly posted pictures of his recent trip to Ukraine and discussed the history of Russia’s invasion, concluding “it’s important we stand with Ukraine.” Musk responded: “You are a traitor.”
Kelly, who was in the Navy for 25 years and flew 39 combat missions in the Gulf War before becoming an astronaut, responded: “Traitor? Elon, if you don’t understand that defending freedom is a basic tenet of what makes America great and keeps us safe, maybe you should leave it to those of us who do.”
LETTERS FROM AN AMERICAN
HEATHER COX RICHARDSON
#Matt Wuerker#Politico#Letters From An American#Heather Cox Richardson#Mark Kelly#veterans#IDEA#disabilities#war in Ukraine#the Economy#the Stock market#economic news#tariffs#wrong way
119 notes
·
View notes
Text
· ୨୧ · · Yandere Hacker hc

W/c : 301
A/N ┊I kinda went crazy bout this, becareful out their folks. This piece of work is used for entertainment purposes and no ones ip is actually being stolen! Also this is not proofread (゜ロ゜;ノ)ノ enjoy dis hc heheueheueu
PAIRING ┊Yan!Hacker x Reader
TW ┊mention of phishing links, cyber hacking, blackmail,

Yandere!Hacker was a recluse individual; he stayed inside his home all day, looking at his screen and watching some random videos, sometimes he'd play video games but he just exploits it to get what he wants. That was when he came across one of your posts and immediately followed you, your personality online was cute to him. Curiosity got the best of him, and he wanted to see what you looked like.
Yan!Hacker set up a phishing link for you in hopes that you'd fall for it, he pretended to be one of your beloved fans and commented on one of your posts, and sent you a link to a website.
“Aww! I love your blog, sm! Your post reminds me of this one cat pic I saw. Https://insert-cat-linkheredon'tclickit. com "
He was baffled on how you just easily fell for it. When you clicked on that link, it exposed your sensitive information to him; Once he takes you for himself, he should really tell you about all the mediocre scams; maybe he'd teach his future kids about it, too.
Yan!Hacker would go so far as to check up on your security footage, he watched as you were bathing and eating. In his eyes, nothing was wrong with what he was doing; he was just checking up on his future partner, he'd secretly just take pictures or video record you doing your normal routines. He kept them in a secret folder for him to just pleasure himself with.
Yan!Hacker uses scummy websites he made to get people so he could get information from them and exploiting peoppe for money in exchange he doesn't share their sensitive info. It was an awful practice, but he did make money off of it. A significantly large amount of money...
Using all the information he had from you, he decided to finally strike. He sent you countless dm's about how he has your information. It was blatant blackmail; if you didn't comply with him, he'd leak your info, and your life would be ruined forever. Any group chats, Dm's, and past deleted photos will be exposed if you didn't love him and him alone.

@kitsuvio
#yandere x y/n#yandere fanfiction#yandere fanfic#yandere headcanons#yandere headcanon#yan x you#yandere#yandere drabble#yandere x reader#yan x reader#yandere hacker#yan#yandere x darling#tw yandere#fic#x reader
105 notes
·
View notes
Text
Tech Tuesday - Introductions
A/N: Entirely written on my phone. Apologies for errors!
A/N2: This chapter is mainly an introduction to the setting and the majority of the characters. It'll be different readers for each character (give or take).

Ok, first day, very important to not make an idiot of yourself. That's been your internal mantra for the entire commute. You've been really hoping it'll help you out today.
You've gotten a ticket to take to IT for your new work laptop but you got lost trying to find your way there. You look around at the signs, trying to figure it out when someone gently coughs to get your attention. Turning you see a tall, lean man with short blondish brown hair and light blue eyes.
"Do you need some help?" His accent and soft tone help soothe your nerves.
"Um..." you hesitate. "I'm, I'm trying to find the IT department?"
His eyes widen as he smiles, "you must be the new hire." You nod and he holds out his hand, "I'm Jonathan, manager of the IT department. I'll show you the way."
He talks as he guides you to the one section of the building you hadn't been to yet.
"Here is our own little corner of the world," Jonathan gestures around the open area. "For a new employee you're going to want to talk to Jake." He points to a young man with spiky hair, glasses and a goatee who's talking on the phone.
"Ain't gonna happen for a while." A large bear of a man with a beard and a bald top, wearing a Lynyrd Skinner shirt steps towards you. "He's helping that little old lady on the third floor that never remembers her password."
"Ah, yes," Jonathan winces. "She is quite the talker." He looks to you and introduces the second man as Syverson. "We both run the department but Sy is better at managing the employees while I'm better at convincing the higher ups to give us a better budget."
"One of th' smoothest talkers I've ever worked with," Sy grins. "As far as your laptop, you wait right here an' I'll go get from Walter. He's our main hardware guy. Then we'll get...hmmm." He looks around as he ponders.
"Johnny is currently mid battle with that hacker he keeps toying with," Jonathan muses. "How is Ransom's mood today?"
Sy snorts, "same as always. Definitely don't wanna scare the lady away." He snaps his fingers, "Rogers!"
A head pops out of a cubicle, "you call?"
"Got a new employee," Sy explains. "Gonna need you to help her get her laptop setup." Sy turns and heads to where you're guessing Walter is with the hardware you'll need.
You turn back to where Steve was situated and almost jump at seeing him so close. He's huge but you didn't hear him at all! The big and tall blonde man's eyes are shining with enthusiasm.
He holds out his hand and you introduce yourself. "It's nice to meet you. Not a lot of new people around here lately. I work with the designs for our internal programs. Me and Bucky," he gestures back to his cubicle, "work together on the UX and accessibility stuff for the external website."
"That's impressive," you nod, practically hypnotized by his eyes. And his muscles, if you're being honest with yourself.
Sy returns and hands Steve the laptop. "Follow me," Steve smiles as he turns. You try your best to fight the urge to ogle his ass. It's your first day and you don't want to already make a fool of yourself! No matter how handsome these guys are.
Steve takes you through the setup. He's incredibly patient and kind. Plus his voice could keep your attention forever. He's going through some of the standard company security stuff when there's a knock. You both turn and you see a burly man with a beanie and a beard so full you almost miss the lip piercing.
"Hey, Curtis. What's up?"
"Bucky's out getting another coffee," Curtis starts. "Need you to tell him I've got the code worked out for the next update and need him to check the legacy compatibility."
"Sure thing," Steve nods and Curtis heads back to whenever he'd been.
"Don't you have an internal communications thing for this?" You're surprised that someone has to intervene in the communication.
Steve chuckles as he pulls out his phone. "Bucky never responds to work stuff while he's out, even just to a cafe. But there's a time crunch on this and I'm the only person he'll actually check his phone for."
"Oh," is all you can say.
Steve finishes his text and gets back to your training. When you're done you thank him for everything and he blushes a little.
"If you want I can help you with the physical setup at your desk?" He almost looks like he's pleading for you to say yes.
"It won't be a problem? I don't want to get you in trouble."
"Not at all," he assures. "Besides, I don't want to be here for the upcoming Bucky and Curtis debate."
You giggle nervously, "ok. And thank you!"

Tagging @alicedopey; @delicatebarness; @ellethespaceunicorn; @icefrozendeadlyqueen; @late-to-the-party-81; @lokislady82 ; @ronearoundblindly
Also tagging @jaqui-has-a-conspiracy-theory to test if this post is working!
Please let me know if you'd like to be tagged.
#tech tuesday#Jonathan Pine#Captain Syverson#Syverson#Walter Marshall#Jake Jensen#Ransom Drysdale#Steve Rogers#Bucky Barnes#Curtis Everett
106 notes
·
View notes
Text
SORRY I FORGOT ABOUT THE MULTIVERSE THING. anyway this is like my fourth time trying to get this damn link to show up on this site so hopefully the fourth time'll be the charm or whatever since the third wasn't-
[A link is attached to a news website, apparently for the digital version of the Castelia Times. Upon clicking on it, the first thing that comes up—unless there is an adblocker involved—is a pop-up informing the website visitor that this is one of their five free articles for this month, and that they should consider subscribing to support journalism.
Once they've dealt with the pop-up as they will, though, the title of the article becomes clear: Anonymous Leaker Reveals Aether Foundation Involvement in 2017 Alolan Ultra Beast Crisis.
It becomes immediately clear after a handful of paragraphs that the reporter is not fond of Aether's recent expansion into other regions from Sinnoh to Unova and therefore is absolutely delighted that an anonymous hacker found and leaked security footage stored on Aether's own servers.
Previous leaks/data dumps provided by this particular hacker have ranged from revealing that a professor at Blueberry Academy was far more concerned with her ancestor's conspiracy theories than the well-being of her own students to leaking emails making it clear that the upper management of Silph Co. was not only aware of Team Rocket's plans to take over their Saffron City building but thought it would ultimately increase profits in the long run to allow the team to do what they wanted.
This, however, is something a little bigger. There are two main videos that have been shared with the wider internet, seemingly taken from security camera footage in the Alolan branch of the Aether Foundation.
According to the reporter, viewer discretion is advised, and they have provided warnings for Pokémon abuse, child abuse, and—for some reason—a woman named Lusamine Aether, who is apparently the current president of the Aether Foundation.
In the first video attached, Lusamine is shown verbally berating a young girl, referred to as Lillie, who looks very similar to her. She refers to the girl as disappointing in comparison to her companion—a girl of similar age referred to by Lusamine as Selene—before claiming that she doesn't have any children who would "reject her love" and that maybe if Lillie had been better, she could have saved Cosmog, something that seems from context to be a Pokémon that Lusamine will be forcing to "use its power."
The second video attached seems to pick up close to where the last one left off, albeit in a different room, and in one where there are numerous Pokémon implied from what Lusamine says about them to have been frozen solid and "preserved" while they were still alive. The girls from earlier are horrified before a boy in black who bears significant resemblance to both Lillie and Lusamine rushes in with another friend in tow.
The exact words "All I ever did was give you two all the love I had, and all you did was betray me! You have no right to ask for my attention now!" are uttered by Lusamine, before she declares in response to the other boy (who is apparently named Hau) that they once were family, perhaps, before her former children (who she describes as wretches) left her.
She then forces the Cosmog inside a container to use its power at the expense of its own wellbeing, opening Ultra Wormholes all over Alola in addition to one right there, before ordering someone working for her to "quiet those children for me" as she doesn't "want to hear from them again," which is a wild thing to say about a group of preteens (and one kid who looks like a young, particularly edgy teenager).
The reporter's article concludes with stating that neither the Aether Foundation's main branch nor their Unova branch have responded to a request for comment, and they're frankly unsure of how to get in touch with the hacker Sedici, but that the Alolan government is taking clear evidence of Lusamine Aether's involvement in the Ulra Beast Crisis very seriously and there are rumors of the International Police getting involved.]
26 notes
·
View notes
Text
FOUND YOU

Yandere Jihoon x fem reader.
WC: 3.8K
Jihoon was never one for relationships. His stoic behavior tends to bore the ladies, but he's had is fair share of flings. However, when some low life hacker tries to access his files; he cant help but look into you more, and some more, and a little more until he becomes obsessed. Jihoon makes it his mission to find you.
WARNINGS: YANDERE, stalking, DUB CON, phone sex, spying, unconsented filming, use of sex toys, fingering, mention of kidnapping, sugar daddy Jihoon, bratty reader.
A/N: i love this fic and I love you woozi.
One semester left… just one. Why on earth would they raise your tuition by $5,000? Are they forgetting both of your parents are dead and you have no job? The financial aid office is no help and you're already about $10,000 in debt. How nice. You look at your computer, contemplating. There's always that option… no it’s not safe. But damn you need money, you need your degree, you need to get out of this fucking city and start over. You look down at your cat Bruno sitting at your feet.
“Should I?”
He just gives you a judgemental look and walks away. This fucking cat…
You have no other choice. You pull out your spare laptop, not risking your pc getting any viruses. A few months ago you drunkenly stumbled upon a website on the dark web that gives you access to IP addresses of major company computers. You very easily figured out how to access their files, you can see everything; their expenses, investments, and payments. It would be so easy to transfer money to an offshore account and cover your traces. Scrolling through the list of companies you try to find one you’ve never heard of. More popular companies tend to have more security.
“Universe factory?”
Hmmm. Doesn't ring a bell. It’s located about fifteen miles from your apartment so you aren't worried about them finding you. Weirdly, you can't find any bank accounts linked to this company. Scouring through some files, this seems to be a music company of sorts? You find samples of songs, lyrics, beats, and oh shit.. Drug shipments? Why is this in the music files? You try to dive deeper only for your connection to completely cut off and your computer blue screens. Fucking hell. The computer won’t turn back on and you won't have a chance to cover your tracks. So much for being computer savvy…
“Fuckkkkk” youre actually fucked. These people are clearly good if they are able to shut off your computer so they may have already found your address by now. You're hoping your vpn and security walls help you. You get up and start to pace. Why on earth did you think this was a good idea? Of course you somehow chose the shadiest fucking company on earth. There's nothing to do now but stress and wait for your likely impending death.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
“The fuck?”
Jihoon’s studio is his safe space. He’s lucky Cheol lets him pursue his passions on the side, this mafia thing tends to take up a lot of his time so being able to unwind in his own space is a treasure. But when he returns to his computer he senses something is wrong. Someone’s gone through his files. Now, Jihoon wouldn't be too worried if all that was on this computer was his music, but recently he’s been using the Universe factory as a coverup to store documents from past business deals. Now this couldnt have been the work of some amaetur, in order to get past all his security takes some real skill, and to be able to do it without a trace? Hm…
Jihoon looks through his files, trying to catalog all the incriminating evidence.
“Tiger’s super wicked diss track?” he speaks in disbelief. When the fuck did Soonyoung get in his studio? And record a fucking distrack?
Jihoon runs a program to see the location of the last user to access his encrypted files. Nothing? Hmm… This is too random to be a coincidence, this person must've found his IP address and started from there. He decides to be bold and search his IP addresses on his self made database, it wouldn't hurt.
“ “FoundYou.com”? What the fuck?”
Well he hit the jackpot. He was able to look at who accessed this website in the past 24 hours and who interacted with the universe factory link. He traced the computer to a rural part of antarctica… ok that's definitely not the real location. He digs a little deeper finding layers and layers of security. He’s starting to think this may not be some silly hacker and could be a rival mafia pulling at strings. After an hour he’s confident he’s found the real address and hacker. About fifteen miles from him lives a Y/N L/N, full time student, studying in computer science, $10,437.76 in debt and an orphan… hm. He looks up your instagram and woah. He wasn’t expecting you to look like that. He sees your friends, finds their instagrams, just to see more pictures of you cover his bases. Your college friends speak highly of you, your highschool friends love you, oh wow even your elementary school friends still hang out with you. He digs a little deeper, just to know who he’s dealing with. You adopted a cat a year ago, a cat who visits the vet very often. Gestational blockages, broken arm, not eating, bladder infection… This cat seems like a handful.
“Bruno? Like Bruno Mars or Bruno from Encanto?” he whispers to himself.
You visited the hospital last year from a broken pinky, your dermatologist keeps increasing the strength of your acne medication, you take very strong pills for your cramps. Car accident when you were 7, therapy for 10 years and dead parents?… Figures.
Your credit card statement says a lot about you. $7 matcha lattes three times a week despite being in debt. $15 chipotle bowls and 12am Mcdonalds. You really like shopping at Adam and eve… freaky. You bought $100 worth of things from amazon yesterday. You sure do buy a lot of cat toys on amazon, this cat is spoiled. Hair dye, batteries, water bottles, 12 pound bag of skittles?
“Woozi, what are you doing?” Soonyoung whispers in his ear.
Jihoon jumps, “When did you even get in here?”
“You get too immersed in your work, but why are you on amazon?”
“None of your business get out! AND WHEN DID YOU RECORD A DISS TRACK IN HERE.”
Hoshi’s eyes widen and he quickly makes his exit leaving Jihoon alone again. He knows he’s being a creep but he doesn't have it in him to care. You’re just so interesting.
~~~~~~~~~~~~~~~~~~~~
“Bruno there's no one at the door stop growling.”
You open the door to show him no one is outside, but low and behold sitting outside your apartment is a large bouquet of hydrangeas… your favorite flower.
“The fuck?”
You further inspect the flowers, seeing a note in the center.
“My precious little hacker, I’ll be seeing you soon. P.S check your bank account - Woozi’s Universe factory.”
You drop the flowers. Oh my god.You figured something like this would happen but now that it's happening you're freaked out. God, you should have minded your business. Now the little money you had is probably gone as some sort of twisted revenge. As you login to your bank app you're sure you've lost your mind and you're seeing things. $20,000 was wired to your savings account.
“What the fuck.”
You know better than to touch this money. It’s too good to be true. But, this would pay off your debt and get you a better apartment… fuck. You check your email to see what time the money was wired only to see an email from your school saying there were changes made to your account. Can this day get any worse? But it somehow gets better, not only is your tuition paid but all your debt is cleared… you must've suffered a head injury and you're making all of this up while in a coma.
“Bruno, I might be killed in the next 7 days… Then you’ll have to fend for yourself.”
~~~~~~~~~~~~~~~~~~~~~~
“Bruno, I might be killed in the next 7 days.. Then you’ll have to fend for yourself.” your sweet voice rings out.
Jihoon had to see your reaction to his gift. He’s glad you didn't notice the green dot on your mac as he watched you through the webcam. He loves the way you talk to Bruno like he’s a human.
It took a lot of digging to figure out your favorite flower, it was one of your security questions for your bank app. He hopes you appreciate his generosity, it’s not everyday that he goes out of his way to spoil someone. He sees you looking absolutely bewildered and he can’t help but smile. But this smile quickly drops when you turn to your computer and your eyes widen, presumably seeing your camera is on.
“YOU FUCKING CREEP!” you scream as you power off your computer, leaving him staring at a blank screen.
He just smiles in response. He’s gonna have so much fun with you.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
The gifts don't end. Everyday at 4pm you arrive home and on your doorstep is something new, perfume, jewelry, bags, clothes, cat toys. This person must be rich. Though today the bell never rings. You even stand in your hallway looking for the delivery but it never comes.
“Well isn't that weird?” you say to yourself as you unlock your door.
“Bruno?” Usually he comes running up to you when you unlock your door.
You see Bruno inspecting a bright red gift box sitting on your kitchen counter. You stop dead in your tracks. How the fuck did they get in your apartment?
“Bruno! Move away from that.” you say and scoop him up.
Oh god. This is getting insane. Leaving the gifts on your doorstep is one thing but coming inside?
You stare at the gift for an hour. You're too afraid to open it. That is until it starts to vibrate. Is this a fucking bomb? You jump and open the box, seeing a brand new phone… Um Ok? The phone is receiving a call from an unknown number and obviously you don't answer it, setting the phone back down only for the same number to call again. You hesitantly answer.
“Hello?”
“Hi, my love.”
“Who is this?”
“Don’t worry about it, yet.”
“Ok, I’m gonna hang up.”
“Y/N, I wouldn't do that f I was you.”
“Stop being a fucking creep and sending shit to my door step.”
He just laughs.
“I left one more gift for you, why don’t you go look.”
You sigh and walk to your door, looking out the peephole first and opening it, picking up the large box.
“Are there killer wasps in here?” you sarcastically say.
“No, there are no wasps,” he laughs.
You open the box and pause, turning your head to your computer to see your camera is on.
“Are you watching me?”
“I’m always watching you, love.”
“God, youre a fucking creep, I should call the cops.”
“And tell them what? You tried to hack me and steal money from me? That you're a dirty little hacker and a thief?”
You’re starting to get upset, this is fucking insane.
“Open the box, love.”
You look at the computer and flip him off before opening the box. You gasp. This fucker sent you sex toys?
“ALL YOU DO IS SHOW ME HOW MUCH OF A FUCKING PERVERT YOU ARE!” you yell into the phone.
“Is it so bad I want my baby to feel good?”
“I’m not your baby! I don’t even fucking know you.”
“I know you don’t know me but I know you. I know everything about you. Your favorite color is blue, your favorite food is Japanese curry, though you eat kimchi fried rice the most. You adopted Bruno because you needed something to keep you company since you don't really date. Your best friend moved away eight months ago and you two don't really talk anymore. Should I continue?”
“What the fuck.” you say with wide eyes.
“Baby, don’t get scared. I’m just so in love with you I need to know everything.”
“Um.” What do you even say to this?
“And don’t pretend this isn’t your darkest fantasy. I’ve seen your tumblr search history.”
Your eyes somehow widen. He got you there. Just the idea of having a clearly rich man obsessed with you would be enough to make you wet if he wasn't a pervert.
“I want you to take out the shibari.”
You pull out a pretty blue vibrator. It’s even your favorite shade of blue.
“Ok?”
“I want you to use it for me.”
“Absolutely not.”
“Baby, I wouldn’t want to do things to make you upset, but I need you to listen to me. I’m not above blackmailing you and I’m sure you wouldn't want me to come snatch you up.”
Your jaw drops.
“Youre fucking crazy!”
“Baby, you just make me feel so many things for you.”
You groan, cursing yourself for ever being greedy and trying to steal.
“What do you want me to do?” you sigh out.
“Take off your pants and sit on your desk chair.”
“Do I have to?” you pout looking straight into the camera.
“Yes, baby. I want to see you.”
Why is this making you wet? God, you fucking hate that this is exactly the smut you would always search for. You groan at the situation, yourself, at this mystery pervert.
You shimmy out of your pants and sit in your desk chair. You put the phone on speaker and set it down.
“Now what?”
“Turn it on and rub it over your nipples.”
“And if I don’t?”
“I’m sure the guys waiting outside your apartment would love to do it for you.”
Your heart drops to your ass and you turn it on, quickly putting it on your nipple.
Jeez, this thing is powerful. You let out a breathy moan disguised as a sigh.
“Run it down your body.”
You slowly drag the vibrator down your body, your breathing becoming heavy.
“Put your legs up on the chair and put it on your clit over your panties, I wanna see you soak through them.”
You put the head of the vibrator on your clit a little too hard making you jump.
“Slow your roll baby.” he laughs, making you roll your eyes.
This vibrator is on a different level from the shitty ones you have. It feels like you're being stimulated throughout your whole body, everything is vibrating and you feel yourself leaking.
“I can see you getting wetter baby, fuck. I bet that pussy tastes so good.”
You moan, pressing the vibrator harder against you, feeling your toes curl.
“Does it feel good, baby?”
You close your eyes and nod, swallowing the shame. “It feels really good.”
“Move your panties to the side, let me see.”
You pull your soaked panties over and press the vibrator to your swollen clit. He lets out a deep groan. Jihoon can't believe his eyes, it’s like a dream come true. Your pretty pussy dripping wet just for him, you whining and moaning like all you can think about is cumming. He pulls out his hard cock, beginning to stroke himself, imagining he was fucking you. He would give it to you however you wanted, let you come as many times as you desired. No matter how bad you treated him, he would be on his knees begging to make you cum. The hold you have over him is unfathomable. You’re truly like an angel sent to heaven just for him and he'll be damned if he doesn’t get his hands on you. He doesn't even have it in him to feel bad about watching you, listening to you, exploring you. In his mind you’ve been his from the moment he first saw you. His to worship, spoil, love until the end of time. You’ve become his muse, his lyrics flow out with only you in mind, he makes songs with the purpose of you hearing them. You’ve taken him over completely and he is so irrevocably in love with you. You don’t even need to love him back, he already has enough love for the both of you, and it's not like he wouldn’t be able to force you. A little isolation does wonders on the brain.
“I need more,” you whine out.
“Tell me what you want.”
You just whine more in response, too embarrassed to speak. “You want to use your fingers?”
You nod furiously, opening your eyes to plead with him.
“Ok baby, slide two in for me. I want you to make yourself feel good.”
You listen and slide your fingers in, pumping them straight into your g-spot. You feel yourself on the verge of an orgasm, your moans becoming louder and more frequent.
“Turn it off”
Your eyes fly open. “What.”
“You heard me baby, turn it off.”
“No, no please I’m so close.”
“Y/N.”
You turn it off and throw it to the side, so insanely frustrated.
“What is your deal!”
“You’re not cumming unless it's around my cock, baby.”
This man never fails to surprise you. “And what makes you think I’ll fuck you?”
“Trust me when I say that won’t be an issue.”
“What makes you so sure I just won’t finish myself off when I hang up?”
“I’m always watching, baby. It’s crazy how small they make cameras nowadays.”
“Fuck you Woozi’s Universe Factory.” you say not even able to take yourself seriously.
He just laughs. “I’ll be seeing you soon my love.”
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
“Is he named after Bruno Mars or Bruno from Encanto?” a deep voice rings out from your couch as you enter your apartment making you scream.
You turn to run out your apartment only to see two giants standing in your hallway blocking your exit. You groan and turn back around seeing Bruno sitting in the man's lap. Woah. Is this your stalker? Because if so, you have zero complaints. You’ve never been one to like guys with long hair, but his curls are just so hot and his lips.. How are they so plump? He’s wearing a tight black turtleneck and slacks with a gold chain. He looks so fucking hot, suddenly your not as pissed that he forced you masturbate for him.
“Who are you?”
“You know exactly who I am, my love.”
“I don't know your name. Do you want me to call you Woozi’s Universe factory?”
He breathes out a laugh. “My name is Jihoon, love.”
“I’m sure you already know my name and give me my fucking cat.” you go to grab Bruno who hisses at you. You gasp.
“You little traitor.” you growl. “The real Bruno Mars would never treat me like this.” you say threateningly to the cat.
“Ahh, Bruno Mars. I love that guy.” Jihoon says as he lifts the cat to look him in his eyes. “You want to stay with me don’t you?” to which the cat purrs.
You’re more shocked at your cat's betrayal than Jihoon breaking into your apartment.
“Y/N, sit with me”
“No.”
He raises a brow at you.
“Fine, but not because you asked.” you pout and sit next to him.
“Are you not scared?”
“Honestly, you're too cute for me to be scared of you. Like look at these cheeks.” you say and squeeze his cheeks making him grab your hand and pull it away from your face.
“You don’t know who you're messing with, my love.”
“I mean if you were going to kill me you would've done it already. And I know you're not going to anyway because why would you waste all this money on someone you were going to kill?”
He smiles. “So smart, baby.”
Why is he calling you baby and love? This is actually kind of spooking you.
“What do you want Jihoon?”
“I want you to come live with me.”
Your eyes widen. The fuck? Your feelings must be visible on your face because he continues.
“So, you just want me to get up and leave with you?”
“Yes.”
“Why would I come with you? You've done nothing but stalk and harrass me!”
“I’ve have not been stalking you, love. Everything I’ve done is a result of your actions. You decided to try to hack me which gave me access to everything.”
“You're just trying to manipulate me!” you say and stand up.
He looked deeply offended by this. “Manipulate you? Tell me one thing in what I said that's not true.”
He has a point. You're just grasping at straw to be honest. “What If I don’t want to go with you.” you pout and stomp your foot looking like a child.
“Then I’ll take you by force.” he says with a straight face.
Oh. You weigh your options. Would you rather live in this hell hole remaining broke and sad or go with him and drain his pockets? You don’t even know where he’s taking you, he could be bringing you to a cabin in the woods to lock you up and kill you. But it’s not like you have an option and you would much rather do this the easy way.
“Ok fine. But not because you told me to” God, you sound like such a brat.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Six months later
“Jihoonnnnnnn.”
“Yes baby?”
“Can you buy me this?”
He groans. “Baby, what else could you possibly buy? You have it all.”
You show him your phone.
“Baby, you have this bag in three colors.” he deadpans.
“OK? This is my favorite color though.” You say like it's the most obvious thing on the planet.
Despite his grumbling he gets up and takes out his wallet, handing you his black card. Jihoon can never say no to you. Anything you ask for is yours, no matter what. Your life has completely changed since meeting him. You wouldn't say he’s your sugar daddy because you're equally as in love with him as he is with you, but, lord does he spoil you. You moved into his high rise apartment and completely renovated it to your taste without a single complaint from him. He bought you a new wardrobe, new cars, bags, jewels, anything you could ever dream of. And the sex.. It’s just incredible. And Bruno is as spoiled as ever. He’s Jihoon’s baby despite Jihoon pretending to dislike him. You know what Jihoon does for a living, that's none of your business though. All that you care about is keeping him and yourself happy. You’ve grown more than accustomed to this lifestyle, not knowing how you functioned before meeting him.
“Thank you Woozipoo”
“Stop calling me that” he groans.
“If you want me to stop you’ll get out this fucking studio and come to bed.”
He rolls his head to you. “Why would I do that?”
“So I can thank you for being so good to me.” you say into his neck making him groan.
“God, baby don’t say things like that.”
“I can’t tell my man how much I want to fuck him?”
“Get your ass in the bedroom.”
432 notes
·
View notes
Text
Albert Gonzalez (born 1981) is an American computer hacker, computer criminal and police informer, who is accused of masterminding the combined credit card theft and subsequent reselling of more than 170 million card and ATMnumbers from 2005 to 2007, the biggest such fraud in history. Gonzalez and his accomplices used SQL injection to deploy backdoors on several corporate systems in order to launch packet sniffing (specifically, ARP spoofing) attacks which allowed him to steal computer data from internal corporate networks.
Gonzalez bought his first computer when he was 12, and by the time he was 14 managed to hack into NASA. He attended South Miami High School in Miami, Florida, where he was described as the "troubled" pack leader of computer nerds. In 2000, he moved to New York City, where he lived for three months before moving to Kearny, New Jersey.


While in Kearny, he was accused of being the mastermind of a group of hackers called the ShadowCrew group, which trafficked in 1.5 million stolen credit and ATM card numbers. Although considered the mastermind of the scheme (operating on the site under the screen name of "CumbaJohnny"), he was not indicted. According to the indictment, there were 4,000 people who registered with the Shadowcrew.com website. Once registered, they could buy stolen account numbers or counterfeit documents at auction, or read "Tutorials and How-To's" describing the use of cryptography in magnetic strips on credit cards, debit cards and ATM cards so that the numbers could be used. Moderators of the website punished members who did not abide by the site's rules, including providing refunds to buyers if the stolen card numbers proved invalid.
In addition to the card numbers, numerous other objects of identity theft were sold at auction, including counterfeit passports, drivers' licenses, Social Security cards, credit cards, debit cards, birth certificates, college student identification cards, and health insurance cards. One member sold 18 million e-mail accounts with associated usernames, passwords, dates of birth, and other personally identifying information. Most of those indicted were members who actually sold illicit items. Members who maintained or moderated the website itself were also indicted, including one who attempted to register the .cc domain name Shadowcrew.cc.
The Secret Service dubbed their investigation "Operation Firewall" and believed that up to $4.3 million was stolen, as ShadowCrew shared its information with other groups called Carderplanet and Darkprofits. The investigation involved units from the United States, Bulgaria, Belarus, Canada, Poland, Sweden, the Netherlands and Ukraine. Gonzalez was initially charged with possession of 15 fake credit and debit cards in Newark, New Jersey, though he avoided jail time by providing evidence to the United States Secret Service against his cohorts. 19 ShadowCrew members were indicted. Gonzalez then returned to Miami.
While cooperating with authorities, he was said to have masterminded the hacking of TJX Companies, in which 45.6 million credit and debit card numbers were stolen over an 18-month period ending in 2007, topping the 2005 breach of 40 million records at CardSystems Solutions. Gonzalez and 10 others sought targets while wardriving and seeking vulnerabilities in wireless networks along U.S. Route 1 in Miami. They compromised cards at BJ's Wholesale Club, DSW, Office Max, Boston Market, Barnes & Noble, Sports Authority and T.J. Maxx. The indictment referred to Gonzalez by the screen names "cumbajohny", "201679996", "soupnazi", "segvec", "kingchilli" and "stanozlolz." The hacking was an embarrassment to TJ Maxx, which discovered the breach in December 2006. The company initially believed the intrusion began in May 2006, but further investigation revealed breaches dating back to July 2005.
Gonzalez had multiple US co-defendants for the Dave & Buster's and TJX thefts. The main ones were charged and sentenced as follows:
Stephen Watt (Unix Terrorist, Jim Jones) was charged with providing a data theft tool in an identity theft case. He was sentenced to two years in prison and 3 years of supervised release. He was also ordered by the court to pay back $250,000 in restitution.
Damon Patrick Toey pleaded guilty to wire fraud, credit card fraud, and aggravated identity theft and received a five-year sentence.
Christopher Scott pleaded guilty to conspiracy, unauthorized access to computer systems, access device fraud and identity theft. He was sentenced to seven years.
Gonzalez was arrested on May 7, 2008, on charges stemming from hacking into the Dave & Buster's corporate network from a point of sale location at a restaurant in Islandia, New York. The incident occurred in September 2007. About 5,000 card numbers were stolen. Fraudulent transactions totaling $600,000 were reported on 675 of the cards.
Authorities became suspicious after the conspirators kept returning to the restaurant to reintroduce their hack, because it would not restart after the company computers shut down.
Gonzalez was arrested in room 1508 at the National Hotel in Miami Beach, Florida. In various related raids, authorities seized $1.6 million in cash (including $1.1 million buried in plastic bags in a three-foot drum in his parents' backyard), his laptops and a compact Glock pistol. Officials said that, at the time of his arrest, Gonzalez lived in a nondescript house in Miami. He was taken to the Metropolitan Detention Center in Brooklyn, where he was indicted in the Heartland attacks.
In August 2009, Gonzalez was indicted in Newark, New Jersey on charges dealing with hacking into the Heartland Payment Systems, Citibank-branded 7-Eleven ATM's and Hannaford Brothers computer systems. Heartland bore the brunt of the attack, in which 130 million card numbers were stolen. Hannaford had 4.6 million numbers stolen. Two other retailers were not disclosed in the indictment; however, Gonzalez's attorney told StorefrontBacktalk that two of the retailers were J.C. Penney and Target Corporation. Heartland reported that it had lost $12.6 million in the attack including legal fees. Gonzalez allegedly called the scheme "Operation Get Rich or Die Tryin."
According to the indictment, the attacks by Gonzalez and two unidentified hackers "in or near Russia" along with unindicted conspirator "P.T." from Miami, began on December 26, 2007, at Heartland Payment Systems, August 2007 against 7-Eleven, and in November 2007 against Hannaford Brothers and two other unidentified companies.
Gonzalez and his cohorts targeted large companies and studied their check out terminals and then attacked the companies from internet-connected computers in New Jersey, Illinois, Latvia, the Netherlands and Ukraine.
They covered their attacks over the Internet using more than one messaging screen name, storing data related to their attacks on multiple Hacking Platforms, disabling programs that logged inbound and outbound traffic over the Hacking Platforms, and disguising, through the use of proxies, the Internet Protocol addresses from which their attacks originated. The indictment said the hackers tested their program against 20 anti virus programs.
Rene Palomino Jr., attorney for Gonzalez, charged in a blog on The New York Times website that the indictment arose out of squabbling among U.S. Attorney offices in New York, Massachusetts and New Jersey. Palomino said that Gonzalez was in negotiations with New York and Massachusetts for a plea deal in connection with the T.J. Maxx case when New Jersey made its indictment. Palomino identified the unindicted conspirator "P.T." as Damon Patrick Toey, who had pleaded guilty in the T.J. Maxx case. Palomino said Toey, rather than Gonzalez, was the ring leader of the Heartland case. Palomino further said, "Mr. Toey has been cooperating since Day One. He was staying at (Gonzalez's) apartment. This whole creation was Mr. Toey's idea... It was his baby. This was not Albert Gonzalez. I know for a fact that he wasn't involved in all of the chains that were hacked from New Jersey."
Palomino said one of the unnamed Russian hackers in the Heartland case was Maksym Yastremskiy, who was also indicted in the T.J. Maxx incident but is now serving 30 years in a Turkish prison on a charge of hacking Turkish banks in a separate matter. Investigators said Yastremskiy and Gonzalez exchanged 600 messages and that Gonzalez paid him $400,000 through e-gold.
Yastremskiy was arrested in July 2007 in Turkey on charges of hacking into 12 banks in Turkey. The Secret Service investigation into him was used to build the case against Gonzalez including a sneak and peek covert review of Yastremskiy's laptop in Dubai in 2006 and a review of the disk image of the Latvia computer leased from Cronos IT and alleged to have been used in the attacks.
After the indictment, Heartland issued a statement saying that it does not know how many card numbers were stolen from the company nor how the U.S. government reached the 130 million number.
Gonzalez (inmate number: 25702-050) served his 20-year sentence at the FMC Lexington, a medical facility. He was released on September 19, 2023.
22 notes
·
View notes
Text
dear Americans. if KOSA passes
(I SEVERELY DOUBT IT, it would be singlehandedly the worst bill in the history of ever! THE AMOUNT OF IDENTITY FRAUD MY GOD. all the non-americas will make fake American websites and make you put your info in it and then they steal your fucking identity!!!!)
remember to get a vpn, make non-american social media accounts with a non-american email (super easy!)
keep the vpn on when your using the internet, and you should still be able to access most of the internet.
there will be places where you can talk free of censorship still, plus I don't think they'll be killing the internet archive anytime soon so get ready to make YouTube, and other social media videos available on there for everyone who can't access them via YouTube and other social media's
you can also head on over to TOR because how in gods earth are they gonna enforce anything on there. they try. but also it's incredibly sketchy and you need some cybersecurity know how or you will get hacked.
your best bet's guys are to just use non-american social media's also I'm pretty sure they can't limit your access to non-american websites bc that's impossible so while for Americans YouTube, google, and other social media's might become restricted for you.
the wonderful world of International websites and social media's probably won't because again. fucking impossible to do.
100% I don't think KOSA will pass because again NATIONAL SECURITY RISK OF THE HIGHEST DEGREE
like the death of America will be their ineptitude of how hackers and the internet works.
(fun fact there's a hacking attempt every second! something these fuckers don't know about! the hackers are literally going to go into all this like a kid in a candy store.)
also rip to anyone trying to run away from abusive relationships, gangs or more!
like genuinely the worst fucking idea in the history of idea's it's not even a bad internet bill. IT'S A FUCKING GOD AWFUL ONE
like, WHO IN GODS EARTH ALLOWED THIS TO GET SO FAR?
I am going insane on behalf of all the Americans
#-pop#activism stuff#anticapitalism stuff#anarchism stuff#queer stuff#trans stuff#mental health stuff#disability#stop kosa#bad internet bills#kids online safety bill#fuck kosa#anti kosa#kosa bill#brooo Kamala supports this atrocity of a bill#why are we letting old people with zero background in cybersecurity decide this shit#worst fucking idea in the history of ever
57 notes
·
View notes
Text
A young technologist known online as “Big Balls,” who works for Elon Musk's so-called Department of Government Efficiency (DOGE), has access to sensitive US government systems. But his professional and online history call into question whether he would pass the background check typically required to obtain security clearances, security experts tell WIRED.
Edward Coristine, a 19-year-old high school graduate, established at least five different companies in the last four years, with entities registered in Connecticut, Delaware, and the United Kingdom, most of which were not listed on his now-deleted LinkedIn profile. Coristine also briefly worked in 2022 at Path Network, a network monitoring firm known for hiring reformed black-hat hackers. Someone using a Telegram handle tied to Coristine also solicited a cyberattack-for-hire service later that year.
Coristine did not respond to multiple requests for comment.
One of the companies Coristine founded, Tesla.Sexy LLC, was set up in 2021, when he would have been around 16 years old. Coristine is listed as the founder and CEO of the company, according to business records reviewed by WIRED.
Tesla.Sexy LLC controls dozens of web domains, including at least two Russian-registered domains. One of those domains, which is still active, offers a service called Helfie, which is an AI bot for Discord servers targeting the Russian market.While the operation of a Russian website would not violate US sanctions preventing Americans doing business with Russian companies, it could potentially be a factor in a security clearance review.
"Foreign connections, whether it's foreign contacts with friends or domain names registered in foreign countries, would be flagged by any agency during the security investigation process," Joseph Shelzi, a former US Army intelligence officer who held security clearance for a decade and managed the security clearance of other units under his command, tells WIRED.
A longtime former US intelligence analyst, who requested anonymity to speak on sensitive topics, agrees. “There's little chance that he could have passed a background check for privileged access to government systems,” they allege.
Another domain under Coristine’s control is faster.pw. The website is currently inactive, but an archived version from October 25, 2022 shows content in Chinese that stated the service helped provide “multiple encrypted cross-border networks.”
Prior to joining DOGE, Coristine worked for several months of 2024 at Elon Musk’s Neuralink brain implant startup, and, as WIRED previously reported, is now listed in Office of Personnel Management records as an “expert” at that agency, which oversees personnel matters for the federal government. Employees of the General Services Administration say he also joined calls where they were made to justify their jobs and to review code they’ve written.
Other elements of Coristine’s personal record reviewed by WIRED, government security experts say, would also raise questions about obtaining security clearances necessary to access privileged government data. These same experts further wonder about the vetting process for DOGE staff—and, given Coristine’s history, whether he underwent any such background check.
The White House did not immediately respond to questions about what level of clearance, if any, Corisitine has, and if so, how it was granted.
At Path Network, Coristine worked as a systems engineer from April to June of 2022, according to his now-deleted LinkedIn resume. Path has at times listed as employees Eric Taylor, also known as Cosmo the God, a well-known former cybercriminal and member of the hacker group UGNazis, as well as Matthew Flannery, an Australian convicted hacker whom police allege was a member of the hacker group LulzSec. It’s unclear whether Coristine worked at Path concurrently with those hackers, and WIRED found no evidence that either Coristine or other Path employees engaged in illegal activity while at the company.
“If I was doing the background investigation on him, I would probably have recommended against hiring him for the work he’s doing,” says EJ Hilbert, a former FBI agent who also briefly served as the CEO of Path Network prior to Coristine’s employment there. “I’m not opposed to the idea of cleaning up the government. But I am questioning the people that are doing it.”
Potential concerns about Coristine extend beyond his work history. Archived Telegram messages shared with WIRED show that, in November 2022, a person using the handle “JoeyCrafter” posted to a Telegram channel focused on so-called distributed denial of service, or DDOS, cyberattacks that bombard victim sites with junk traffic to knock them offline. In his messages, JoeyCrafter—which records from Discord, Telegram, and the networking protocol BGP indicate was a handle used by Coristine—writes that he’s “looking for a capable, powerful and reliable L7” that accepts Bitcoin payments. That line, in the context of a DDOS-for-hire Telegram channel, suggests he was looking for someone who could carry out a layer 7 attack, a certain form of DDOS. A DDOS-for-hire service with the name Dstat.cc was seized in a multi-national law enforcement operation last year.
The JoeyCrafter Telegram account had previously used the name “Rivage,” a name linked to Coristine on Discord and at Path, according to Path internal communications shared with WIRED. Both the Rivage Discord and Telegram accounts at times promoted Coristine’s DiamondCDN startup. It’s not clear whether the JoeyCrafter message was followed by an actual DDOS attack. (In the internal messages among Path staff, a question is asked about Rivage, at which point an individual clarifies they are speaking about "Edward".)
"It does depend on which government agency is sponsoring your security clearance request, but everything that you've just mentioned would absolutely raise red flags during the investigative process," Shelzi, the former US Army intelligence officer says. He adds that a secret security clearance could be completed in as little as 50 days while a top secret security clearance could take anywhere from 90 days to a year to complete.
Coristine’s online history, including a LinkedIn account where he calls himself Big Balls, has disappeared recently. He also previously used an account on X with the username @edwardbigballer. The account had a bio that read: “Technology. Arsenal. Golden State Warriors. Space Travel.”
Prior to using the @edwardbigballer username, Coristine was linked to an account featuring the screenname “Steven French” featuring a picture of what appears to be Humpty Dumpty smoking a cigar. In multiple posts from 2020 and 2021, the account can be seen responding to posts from Musk. Coristine’s X account is currently set to private.
Davi Ottenheimer, a longtime security operations and compliance manager, says many factors about Coristine’s employment history and online footprint could raise questions about his ability to obtain security clearance.
“Limited real work experience is a risk,” says Ottenheimer, as an example. “Plus his handle is literally Big Balls.”
27 notes
·
View notes
Text
So with the pandora's box of AI being released into the world, cybersecurity has become kind of insane for the average user in a way that's difficult to describe for those who aren't following along. Coding in unfamiliar languages is easier to do now, for better and worse. Purchasable hacking "kits" are a thing on the dark web that basically streamline the process of deploying ransomware. And generative AI is making it much easier for more and more people to obscure their intentions and identities, regardless of their tech proficiency.
The impacts of this have been Really Bad in the last year or two in particular. For example:
(I'm about to link to sources, and you better be hovering and checking those links before clicking on them as a habit)
Ransomware attacks have become increasingly lucrative for private and state-sponsored hacking groups, with at least one hack recently reported to have resulted in a $75 MILLION payout from the victim. This in combination with the aforementioned factors has made it a bigger and bigger risk for companies and organizations holding your most sensitive data.
In the US, the Salt Typhoon hack over the past year or so has compromised virtually all major phone networks--meaning text and phone calls are no longer secure means of communication. While this won't affect most people in day-to-day, it does make basically all the information you share over traditional phone comms very vulnerable. You should avoid sharing sensitive information over the phone when you can.
CISA updated their security recommendations late last year in response to this compromise. One of the recommendations is to use a separate comms app with end-to-end encryption. I personally prefer Signal, since it's open source and not owned by Meta, but the challenge can be getting people you know on the same service. So... have fun with that.
2FA is no longer as secure as it was--because SMS itself is no longer secure, yeah, but even app-based 2FA has been rendered useless in certain circumstances. One reason for this is because...
A modern version of the early-2000's trick of gaining access to people's accounts via hijacked cookies has come back around for Chromium browsers, and hackers are gaining access to people's Google accounts via OAuth session hijacking. Meaning they can get into your already-logged-in accounts without passwords or 2FA even being needed to begin with. This has been achieved both through hackers compromising chrome browser extensions, and via a reinvigorated push to send out compromising links via email.
Thanks to AI, discerning compromised email is harder now. Cybercriminals are getting better at replicating legitimate email forms and website login screens etc., and coming up with ways to time the emails around times when you might legitimately expect them. (Some go so far as to hack into a person's phone to watch for when a text confirmation might indicate a recent purchase has been made via texted shipping alerts, for example)
If you go to a website that asks you to double-click a link or button--that is a major red flag. A potential method of clickjacking sessions is done via a script that has to be run with the end user's approval. Basically, to get around people who know enough to not authenticate scripts they don't recognize, hackers are concealing the related pop ups behind a "double-click" prompt instruction that places the "consent" prompt's button under the user's mouse in disguised UI, so that on the second click, the user will unwittingly elevate the script without realizing they are doing it.
Attachments are also a fresh concern, as hackers have figured out how to intentionally corrupt key areas of a file in a way that bypasses built-in virus check--for the email service's virus checker as well as many major anti-virus installed on endpoint systems
Hackers are also increasingly infiltrating trusted channels, like creating fake IT accounts in companies' Office 365 environment, allowing them to Teams employees instead of simply email them. Meaning when IT sends you a new PM in tools like Zoom, Slack, or Teams, you need to double-check what email address they are using before assuming it's the real IT person in question.
Spearphishing's growing sophistication has accelerated the theft of large, sensitive databases like the United/Change Healthcare hacks, the NHS hack & the recent Powerschool hack. Cybercriminals are not only gaining access to emails and accounts, but also using generative AI tools to clone the voices (written and spoken) of key individuals close to them, in order to more thoroughly fool targets into giving away sensitive data that compromises access to bigger accounts and databases.
This is mostly being used to target big-ticket targets, like company CSO's and other executives or security/IT personnel. But it also showcases the way scammers are likely to start trying to manipulate the average person more thoroughly as well. The amount of sensitive information--like the health databases being stolen and sold on the darkweb--means people's most personal details are up for sale and exploitation. So we're not too far off from grandparents being fooled by weaponized AI trained off a grandchild's scraped tiktok videos or other public-facing social media, for example. And who is vulnerable to believing these scams will expand, as scammers can potentially answer sensitive questions figured out from stolen databases, to be even more convincing.
And finally, Big Tech's interest in replacing their employees with AI to net higher profits has resulted in cybersecurity teams who are overworked, even more understaffed they already were before, and increasingly lacking the long-term industry experience useful to leading effective teams and finding good solutions. We're effectively in an arms race that is burning IT pros out faster and harder than before, resulting in the circumvention of crucial QA steps, and mistakes like the faulty release that created the Crowdstrike outage earlier last year.
Most of this won't impact the average person all at once or to the same degree big name targets with potential for big ransoms. But they are little things that have combined into major risks for people in ways that aren't entirely in our control. Password security has become virtually obsolete at this point. And 2FA's effectiveness is tenuous at best, assuming you can maintain vigilance.
The new and currently best advice to keeping your individual accounts secure is to switch to using Passkeys and FIDO keys like Yubikeys. However, the effectiveness of passkeys are held back somewhat as users are slow to adopt them, and therefore websites and services are required to continue to support passwords on people's accounts anyway--keeping password vulnerabilities there as a back door.
TLDR; it's pretty ugly out there right now, and I think it's going to get worse before it gets better. Because even with more sophisticated EDR and anti-virus tools, social engineering itself is getting more complex, which renders certain defensive technologies as somewhat obsolete.
Try to use a passkey when you can, as well as a password locker to create strong passwords you don't have to memorize and non-SMS 2FA as much as possible. FIDO keys are ideal if you can get one you won't lose.
Change your passwords for your most sensitive accounts often.
Don't give websites more personal info about yourself than is absolutely necessary.
Don't double-click links or buttons on websites/captchas.
Be careful what you click and download on piracy sources.
Try to treat your emails and PMs with a healthy dose of skepticism--double-check who is sending them etc for stealthily disguised typos or clever names. It's not going to be as obvious as it used to be that someone is phishing you.
It doesn't hurt to come up with an offline pass phrase to verify people you know IRL. Really.
And basically brace for more big hacks to happen that you cannot control to begin with. The employees at your insurance companies, your hospital, your telecomms company etc. are all likely targets for a breach.
36 notes
·
View notes