#linux disk monitoring
Explore tagged Tumblr posts
Text
Introducing Spike Sleuth, a real-time Linux disk I/O monitoring tool designed to help you identify and analyze unexpected disk activity spikes. Born from the need to pinpoint elusive IOPS alerts, Spike Sleuth offers a lightweight solution that logs processes, users, and files responsible for high disk usage without adding overhead. Whether you're a developer, system administrator, or solutions architect, this tool provides the insights needed to maintain optimal system performance. Discover how Spike Sleuth can enhance your system monitoring and help you stay ahead of performance issues. #Linux #Monitoring #OpenSource #SystemAdmin #DevOps
#devops monitoring#disk I/O monitoring tool#iops monitoring#linux bash script#linux disk monitoring#linux performance#linux sysadmin tools#real-time monitoring linux#systemd service#troubleshoot disk spikes
0 notes
Text

TECHNOLOGY ID PACK

NAMES︰ admin. ajax. alexa. am. atari. audio. auto. bailey. binary. blank. blu. blue. bluesse. browser. browsette. bug. byte. cache. calware. chip. circe. click. clicker. clickie. clicky. cloud. coda. code. codette. codie. cody. computette. crypt. cursor. cy. cyber. cybernet. cybernetica. cyberweb. cypher. cypherre. data. dell. digi. digitalia. digitelle. digitesse. disc. dot. electronica. electronique. emoticon. emoticonnie. fax. file. gig. gizmo. glitch. glitche. glitchesse. glitchette. graphique. hacker. hal. halware. hijack. index. informationne. intelligette. internette. interweb. java. javascript. juno. key. link. linuxe. lotus. lovebytes. mac. mal. malakai. malware. malwaria. memorette. memorie. meta. mic. micah. mickey. morphe. mouse. mousette. myspace. nano. neo. net. netette. nett. netty. paige. pascal. payton. peyton. pixel. programatha. programette. programme. pulse. reboot. rom. router. ruby. sam. sammy. screene. screenette. sean. shock. solitaire. spy. static. stutter. talia. tap. tecca. tech. techette. tessa. tetris. trojan. troubleshoot. ts. user. vir. virus. virusse. volt. vyrus. webbe. wheatley. whirr. widget. will. wirehead. wiresse. zap. zett. zetta. zip.

PRONOUNS︰ ai/ai. alt/alt. anti/antivirus. arc/archive. audio/audio. bat/battery. beep/beep. beep/boop. bit/bit. bit/byte. blue/blue. board/board. bright/bright. brow/browser. browser/browser. brr/brr. bu/bug. bug/bug. buzz/buzz. byt/byte. byte/byte. c/cpu. charge/charger. cir/circuit. cli/click. click/clack. click/click. click/scroll. co/code. code/code. color/color. com/com. com/computer. comp/computer. compute/computer. computer/computer. cor/corrupt. corrupt/corrupt. CPU/CPU. crash/crash. cre/creeper. crtl/crtl. cy/cyber. cyb/cyber. cyber/cyber. da/data. data/data. delete/delete. di/disk. dig/digital. digi/digi. digi/digital. digital/digital. dra/drag. e/exe. electronic/electronic. enter/enter. er/error. err/error. error/error. exe/exe. fi/file. file/file. gi/gif. gli/glitch. glit/glitch. glitch/glitch. graphic/graphic. hac/hacker. hack/hack. hard/hardware. head/phone. hij/hijacker. ho/home. info/info. information/information. int/internet. intelligent/intelligence. intelligent/intelligent. inter/net. internet/internet. it/it. jpg/jpg. key/board. key/cap. key/key. key/keyboard. key/keylogger. lag/lag. lap/laptop. ligh/light. linux/linux. load/load. log/login. main/mainframe. mal/malware. me/media. memory/memorie. mon/monitor. mou/mouse. nano/nano. net/net. net/network. org/org. over/overwrite. page/page. pix/pix. pix/pixel. pixel/pixel. plu/plug. png/png. pop/popup. port/port. pow/power. pro/program. program/program. ram/ram. ran/ransom. reboot/reboot. reload/reload. res/restore. ret/retro. route/router. sca/scan. scr/scroll. scre/screen. scre/screencap. scree/screen. screen/screen. scri/script. script/script. sentient/sentience. shift/shift. site/site. skip/skip. soft/software. spa/spam. space/space. spy/spyware. stop/stop. te/tech. tech/nology. tech/tech. technology/technology. tou/touchpad. txt/txt. typ/type. upload/upload. user/user. vi/viru. vi/virus. vir/virtual. web/page. web/web. whir/whir. wi/wire. win/dow. win/window. wire/wire. wire/wired. zip/zip . ⌨ . ☣ . ⚙ . ⚠ . 🎞 . 🎨 . 🎭 . 🎮 . 🎵 . 👀 . 👁 . 💔 . 💡 . 💢 . 💣 . 💳 . 💵 . 💻 . 💽 . 💾 . 💿 . 📀 . 📱 . 🔇 . 🔈 . 🔉 . 🔊 . 🔋 . 🔌 . 🔎 . 🖥 . 🖱 . 🗡 . 🗯 . 🛠 . 🧿 .

#pupsmail︰id packs#id pack#npt#name suggestions#name ideas#name list#pronoun suggestions#pronoun ideas#pronoun list#neopronouns#nounself#emojiself#techkin#robotkin#internetkin
458 notes
·
View notes
Note
what is the best way to get safer/more anonymous online
Ok, security and anonymity are not the same thing, but when you combine them you can enhance your online privacy.
My question is: how tech literate are you and what is your aim? As in do you live in a country where your government would benefit from monitoring private (political) conversations or do you just want to degoogle? Because the latter is much easier for the average user.
Some general advice:
Leave Windows and Mac operating systems and switch to Linux distributions like Fedora and Ubuntu (both very user friendly). Switch from Microsoft Office or Pages/Numbers/Keynote (Mac) to LibreOffice.
You want to go more hardcore with a very privacy-focused operating system? There are Whonix and Tails (portable operating system).
Try to replace all your closed source apps with open source ones.
Now, when it comes to browsers, leave Chrome behind. Switch to Firefox (or Firefox Focus if you're on mobile). Want to go a step further? Use LibreWolf (a modified version of Firefox that increases protection against tracking), Brave (good for beginners but it has its controversies), DuckDuckGo or Bromite. You like ecofriendly alternatives? Check Ecosia out.
Are you, like, a journalist or political activist? Then you probably know Tor and other anonymous networks like i2p, freenet, Lokinet, Retroshare, IPFS and GNUnet.
For whistleblowers there are tools like SecureDrop (requires Tor), GlobaLeaks (alternative to SecureDrop), Haven (Android) and OnionShare.
Search engines?
There are Startpage (obtains Google's results but with more privacy), MetaGer (open source), DuckDuckGo (partially open source), Searx (open source). You can see the comparisons here.
Check libRedirect out. It redirects requests from popular socmed websites to privacy friendly frontends.
Alternatives to YouTube that value your privacy? Odysee, PeerTube and DTube.
Decentralized apps and social media? Mastodon (Twitter alternative), Friendica (Facebook alternative), diaspora* (Google+ RIP), PixelFed (Insta alternative), Aether (Reddit alternative).
Messaging?
I know we all use shit like Viber, Messenger, Telegram, Whatsup, Discord etc. but there are:
Signal (feels like Whatsup but it's secure and has end-to-end encryption)
Session (doesn't even require a phone or e-mail address to sign up)
Status (no phone or e-mail address again)
Threema (for mobile)
Delta Chat (you can chat with people if you know their e-mail without them having to use the app)
Team chatting?
Open source options:
Element (an alternative to Discord)
Rocket.chat (good for companies)
Revolt.chat (good for gamers and a good alternative to Discord)
Video/voice messaging?
Brave Talk (the one who creates the talk needs to use the browser but the others can join from any browser)
Jami
Linphone
Jitsi (no account required, video conferencing)
Then for Tor there are various options like Briar (good for activists), Speek! and Cwtch (user friendly).
Georestrictions? You don't want your Internet Provider to see what exactly what you're doing online?
As long as it's legal in your country, then you need to hide your IP with a VPN (authoritarian regimes tend to make them illegal for a reason), preferably one that has a no log policy, RAM servers, does not operate in one of the 14 eyes, supports OpenVPN (protocol), accepts cash payment and uses a strong encryption.
NordVPN (based in Panama)
ProtonVPN (Switzerland)
Cyberghost
Mullvad (Sweden)
Surfshark (Netherlands)
Private e-mails?
ProtonMail
StartMail
Tutamail
Mailbox (ecofriendly option)
Want to hide your real e-mail address to avoid spam etc.? SimpleLogin (open source)
E-mail clients?
Thunderbird
Canary Mail (for Android and iOS)
K-9 Mail (Android)
Too many complex passwords that you can't remember?
NordPass
BitWarden
LessPass
KeePassXC
Two Factor Authenticators?
2FAS
ente Authenticator
Aegis Authenticator
andOTP
Tofu (for iOS)
Want to encrypt your files? VeraCrypt (for your disk), GNU Privacy Guard (for your e-mail), Hat.sh (encryption in your browser), Picocrypt (Desktop encryption).
Want to encrypt your Dropbox, Google Drive etc.? Cryptomator.
Encrypted cloud storage?
NordLocker
MEGA
Proton Drive
Nextcloud
Filen
Encrypted photography storage?
ente
Cryptee
Piwigo
Want to remove metadata from your images and videos? ExifCleaner. For Android? ExifEraser. For iOS? Metapho.
Cloak your images to counter facial recognition? Fawkes.
Encrypted file sharing? Send.
Do you menstruate? Do you want an app that tracks your menstrual cycle but doesn't collect your data? drip.
What about your sexual health? Euki.
Want a fitness tracker without a closed source app and the need to transmit your personal data to the company's servers? Gadgetbridge.
38 notes
·
View notes
Note
So Warframe added a "Pom-2" Alternate 1999 computer (that's needed for weird void magic future science wizardry). Thoughts?
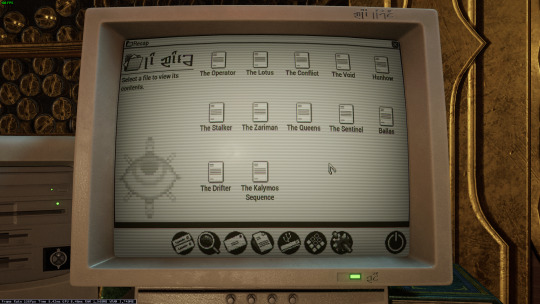



Only thing I have that's a sort of question mark is that I don't know of many setups that would have needed a 5 1/4" floppy in 99 (or why it has both the tower and the under monitor unit)
ugh. OKAY, so... the tower and desktop combination is just weird. I have, on one occasion, run a "server" that was two towers, and the original PC supported a DUAL-DESKTOP mode, but both types together? nonsense.
dual monitor was rare but possible in 1999 (win98 added native support), so I think the best interpretation here is that this is actually two computers. maybe the one on the left is missing the keyboard and mouse because it's being used as some kind of server for the other computer? I used a little case like that to run my first linux server, which was also acting as a router for my internal network.
The OS is weird. The icons above the menu-bar look like win98, the dialog box is windows 3.x, the menu-bar icons on the bottom are pure os X (although they remind me of like a web-TV kinda system, like hotkeys for email/internet/etc), but the greyscale is very classic mac system. Actually it kinda reminds me of C64's GEOS, but GEOS was very classic-mac.

Like most CRT-filters, they turned the scanlines up WAY TOO HIGH. No CRT I've ever seen looked that fucking terrible. The monitor buttons are a bit odd: You didn't get monitors with buttons on the front until long after they were all color... but maybe it's a color monitor that's showing a monochrome OS?
as for the floppies: yeah. There are multiple mistakes here.
5.25" in 1999 is just silly. If you still had 5.25" disk drives in 1999, you were intentionally doing some retrocomputing stuff. For reference, around 2001 my PC repair job would specifically ask me to copy data off 5.25" disks, because they didn't have any 5.25" drives anymore, and I was their only tech who did.
The other mistake is that they have THREE floppy drives. so the PC doesn't really support that, natively? You can do some tricks and make it work (The youtuber Tech Tangents did a video on how it could be done), but realistically two was the normal max.
The final mistake is that all the drive activity lights are on. Those are only supposed to be on while the drive is reading or writing... and I don't see any disks in those drives! Let alone a situation that would involve turning all three on at once (I don't think that's even possible on most floppy controllers!)
In fact, the main time you'd end up with the drive lights stuck on like that is when you've installed the drive cable upside down. That ends up with them getting stuck on and non-functional. So this computer looks, to me, like it was put together incorrectly and no one noticed.
I don't believe that font would be on a black & white retro computer. Nope. Too smooth and too big.
There's also a USB icon on that OS: I don't think there's ever been a monochrome OS that supported OS, and looking at that computer case I don't believe that it has USB. Maybe the tower would, but the desktop? no.
That keyboard is off a Gateway 2000 computer. Something like this:

164 notes
·
View notes
Text
Revisiting Wrap030 Disk Access
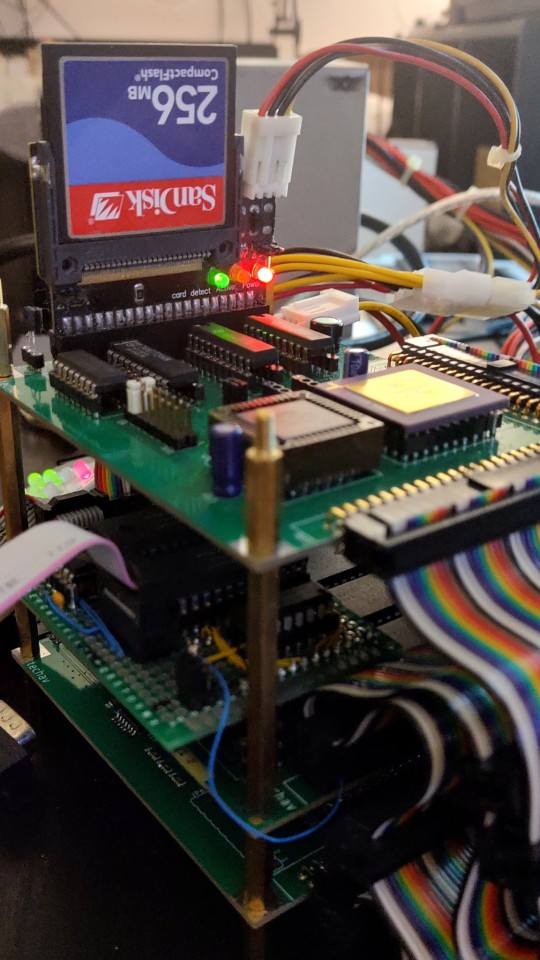
I have more ideas for projects than time or budget to work on them. Already this year I've gone completely through the design process for two new large homebrew projects that are currently too large for my project budget, plus a few small ones I never got around to ordering. So rather than spend more than I should taking on a new project, I decided to revisit an existing one.
It's been over a year since I last worked on the original Wrap030 project — my old stack-of-boards MC68030 system. Its current configuration includes the main board with CPU, ROM, RAM, UART, & glue logic; a hand-wired breakout board to add a second UART; a custom video output board; and a mezzanine board with FPU and provision for an IDE disk that is not yet working. It has been functional in this configuration since last February.
My goal for this project from the beginning was to build something capable of running a proper operating system, like Unix System V or Linux. To do that though, I'm going to need to get disk access working.
I had started on disk access, but didn't quite have it functional when I turned my focus to integrating all of boards into the single Wrap030-ATX motherboard. I had added IDE cycles to the CPLD on the mezzanine board, and had added a few rough drafts of disk functions to my ROM. I set the project aside when I realized my function for checking dish presence was reporting a disk was present when there wasn't one.
I have worked with IDE before — my original 68000 project had an IDE port on it. I had gotten that project to the point where I could read a sector of data from the disk, but never could wrap my head around how to actually navigate even a simple file system like FAT16. It was this code that I had adapted for Wrap030, so when it didn't work, I assumed it was a problem with my logic.
Turns out I had just inadvertently clobbered a register in the disk check function. The logic worked just fine. I was able to write a couple quick BASIC programs to read a sector of data and even run code from the boot sector.
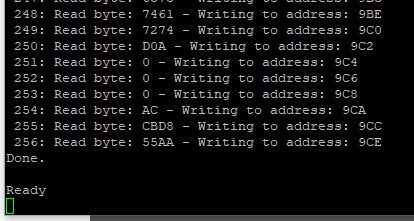

My assembly function for reading data from disk however was still not working.
I tried rewriting it.
I tried rewriting it in C instead of assembly.
I tried again, and again, and again. I added delays and loops and print statements and everything I could think of. I scoured datasheets, read though all the different release versions of the ATA specification, ported code from other projects, looked at every example of reading from an IDE disk I could find.
No matter what I did, I always got the same result.
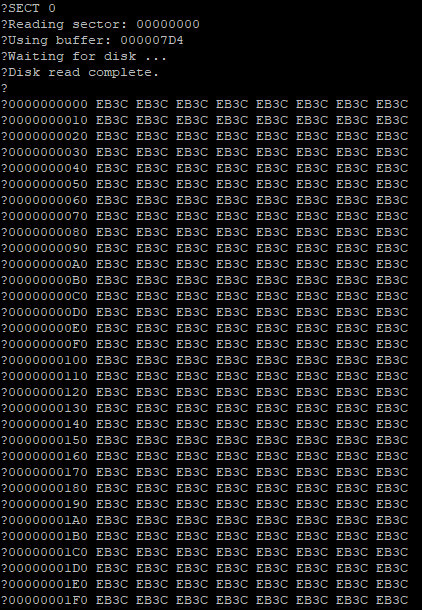
This did not make any sense. Reading from an IDE disk involves setting up the sector address, the number of sectors to transfer, sending a read command, and then reading the IDE data port 256 times per sector. Each time the data port is read, the disk will give another 16-bit word of data. But for some reason, all I was getting was the first word of data returned 256 times.
There is nothing in the specification to explain this.
I knew there was nothing wrong with my logic, because I could read the data just fine with my BASIC program or by manually poking the right addresses using the monitor. Maybe there was some edge case affecting timing when running in assembly, but even adding delay loops and print statements didn't have any effect.
I reached out for help. I got great feedback on my read functions and my timing and how IDE and CompactFlash cards worked, but still could not solve this problem.
But then @ZephyrZ80 noticed something —
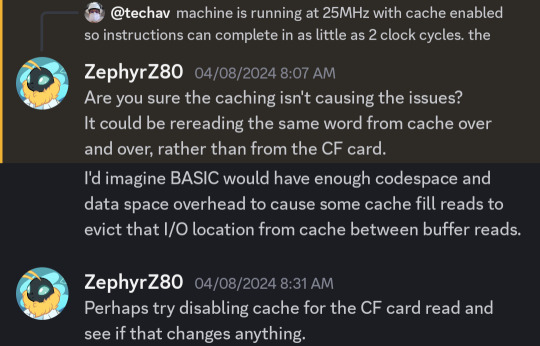
I had shared my code and was explaining that I had added some extra NOP instructions to enforce minimum time between IDE access cycles in PIO-0 mode. At 25MHz with cache enabled, the 68030 can complete an instruction in as little as 80ns, so a few NOPs would ensure enough time elapsed between cycles.
With cache enabled.
… cache enabled.
… cache.
The 68030 has 256 bytes of data cache. My disk read function is running in a tight loop that only really hits a few addresses; not nearly enough to invalidate and flush the entire 256 bytes of cache. The CPU does have a cache inhibit signal to use with peripherals that return new data on subsequent access to the same address, but it turns out I was only asserting it when accessing the UART on the main board.
It's a simple enough hypothesis to test. When I initially added support in my ROM for enabling cache at startup, I included user functions for enabling and disabling cache.
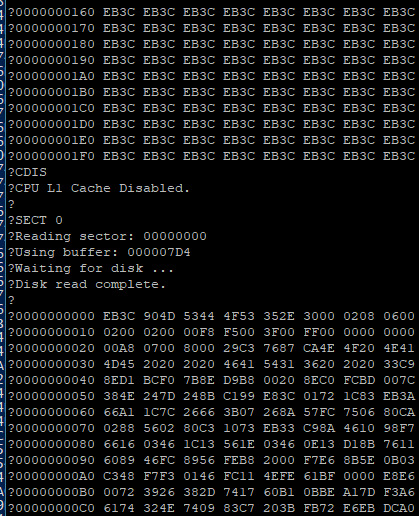
… It was cache all along.
Now I need to add some way to inhibit cache while accessing the IDE port, and then I can move on to trying to use the disk for loading programs.
41 notes
·
View notes
Text
one, i thought my pc got scared bc i downloaded UUI and ubuntu to start learning linux on my tablet bc the pc started whirring loud and disconnecting from monitors but it was just the gpu cable got jostled and re-plugging it in fixed the issue.
two, though - this whole process was drawn out and had me worrying about the Curses because. well the iso is over 5gb and the largest flash drive in my apartment before today was. um. a 4gb memory card into a USB stick with a card slot. this, of all things, is what has made me feel the most old lately. like what am i doing with this floppy disk ass storage tech and nothing else ?
#peter posts#i have e.g. an external hard drive and so on but flash drives? that was IT.#and this fucked up one was inherited from i think 3ds modding/digital camera shenanigans#but also. what do you mean 128gb flash drives are like 15 bucks or less. hello?
4 notes
·
View notes
Text
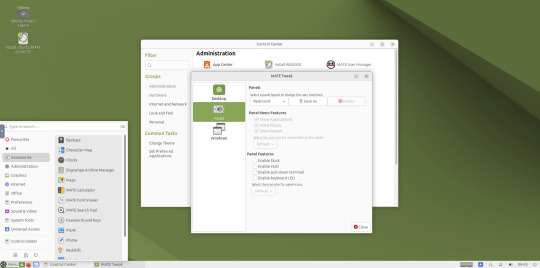
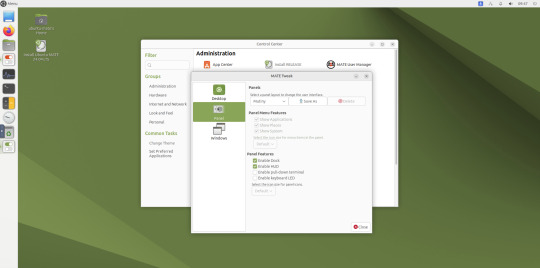
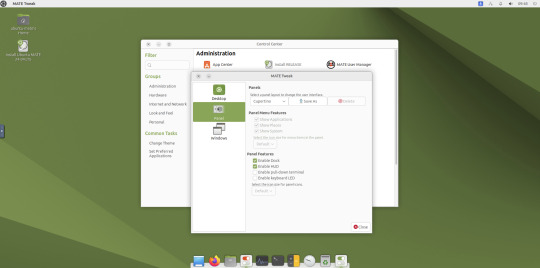
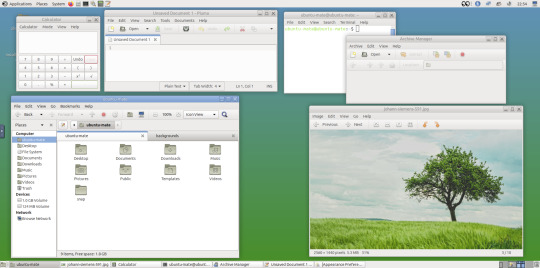
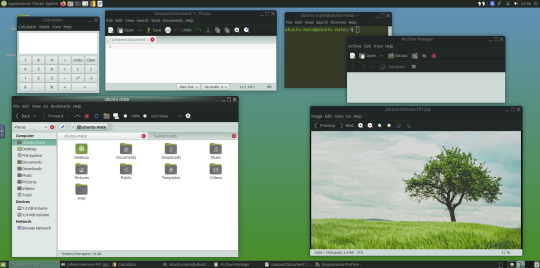
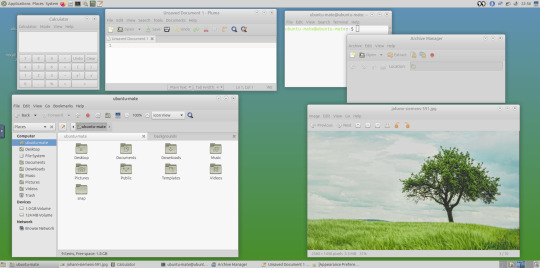
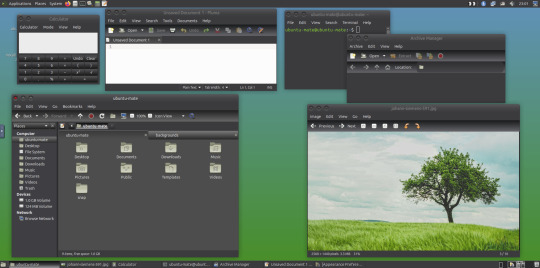

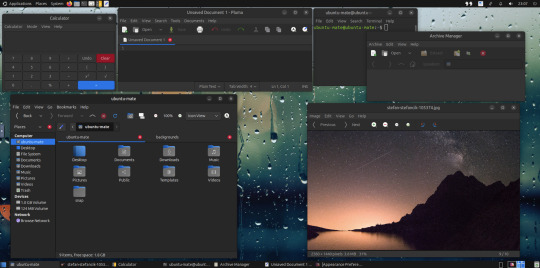

May 2025.
I tried installing a set of themes on Ubuntu MATE 24.04.1 LTS in Distrosea today.
https://distrosea.com/
These themes are provided as a theme package found in vanilla MATE desktops such as Debian and Fedora.
MATE is the modern day continuation of GNOME 2, a very popular, efficient and functional desktop environment from the early 2000s.
The theme pack I selected are compactable GTK3/4 (Graphical Toolkit) versions based on classic GNOME 2 era themes.
Ubuntu MATE website:
https://ubuntu-mate.org/
Debian Linux website:
https://www.debian.org/
Fedora Linux website:
https://fedoraproject.org/spins/mate
See MATE Desktop website here:
https://mate-desktop.org/blog/
About the Graphical Toolkit user interface:
https://en.wikipedia.org/wiki/GTK
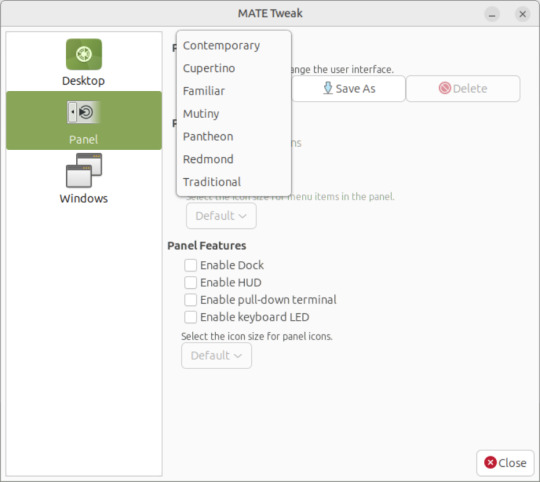
I used the MATE Tweak tool to adjust the panels from the 'familiar' layout to the 'traditional' layout. Here are many of the layouts available.
MATE Tweak can change the panel layout between Traditional (GNOME 2), Unity, Redmond (Windows) contemporary (Mac OS) style.
Here are many of the layouts available.
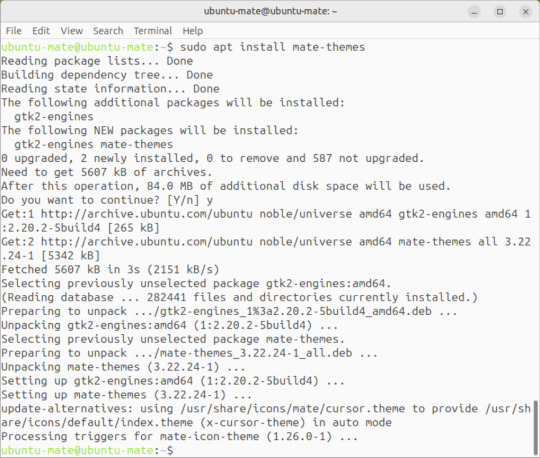
Afterwards, I used the command line to install the themes with the command: sudo apt install mate-themes.
This command then prompted me to agree the system changes and then it installed the required theme files to the list.
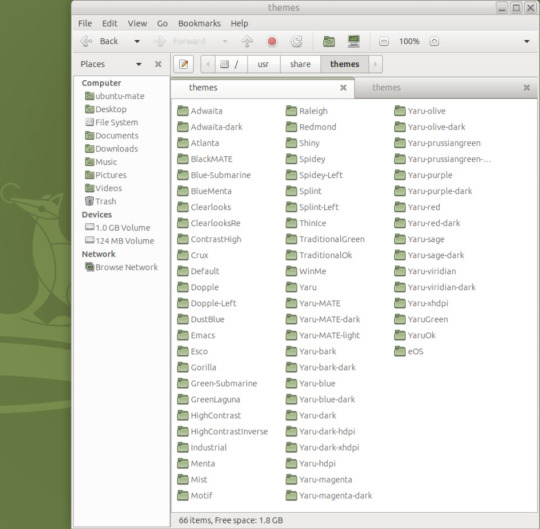
I opened up the theme folder in the Caja file manager. This shows all the ones installed on the system.
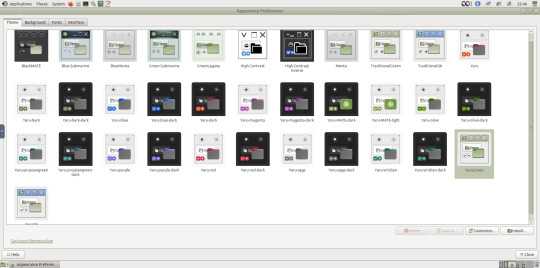
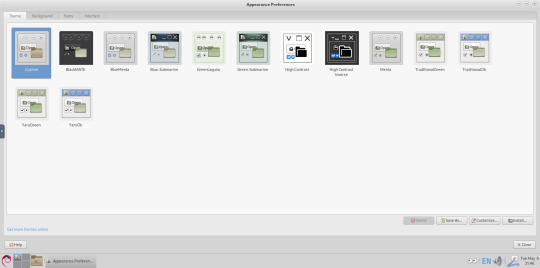
Next I opened the appearance preferences and cycled through each theme. There are a total of 12 new themes it added alongside the existing Yaru Colour theme collection for Ubuntu.
This package couldn't be installed graphical so this is why I installed it through the terminal. It is also available to install through the Software Manager on Linux Mint.
The theme package can also be installed on the Cinnamon desktop and other linux distributions.
I like these themes as they provide a more 3D feel and is refreshing to see themes for a desktop environment that hasn't moved towards flat design. It themes all the desktop elements from the windows, panels, drop down menus, CSD apps and widgets.
My favourite one is called YaruOK (blue), as it provides resizable window controls, 3D controls and provides a familiar look to the desktop. The theme is also called TraditionalOK.
This theme is a fork of a GTK2 theme called Clear-looks, which was created by Red Hat developers.
YaruOK is a modern variant that uses GTK3 & 4. The theme is rendered in SVG instead of PNG format which improves HiDpi scaling and features themed client side decorations for header bar windows such as the Disks utility.
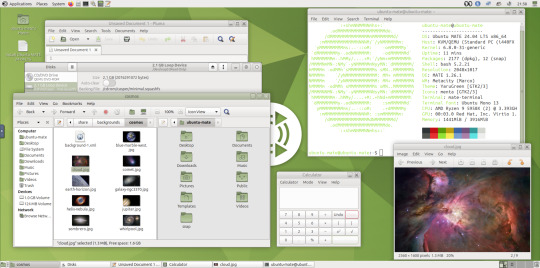
I also added a GNOME Eyes widget onto the panel!
These fun set of eyes follow your mouse cursor around the screen and can help you find the cursor amongst the clutter of windows. It is built to be very lightweight.
I also like the workspace switcher on the bottom left, which allows you to switch between as many desktop workspaces as you want.
The little square windows within each desktop can be clicked on and moved to another workspace.
Like with other desktop environments, you can also right click a window and move it onto another workspace. Each desktop can be named for a assigned task.
A System Monitor widget can also be added to the panels to display CPU, Memory, Swap and Network processes.
There are many other very interesting widget to play around with on the desktop and panels as well!
Here are the MATE themes in Ubuntu Linux 24.04.1, integrating with the Cinnamon desktop.
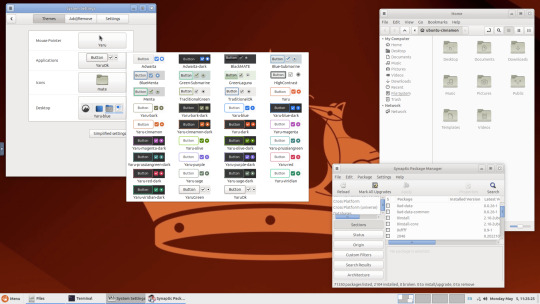
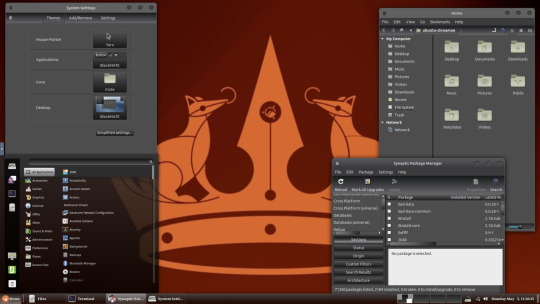
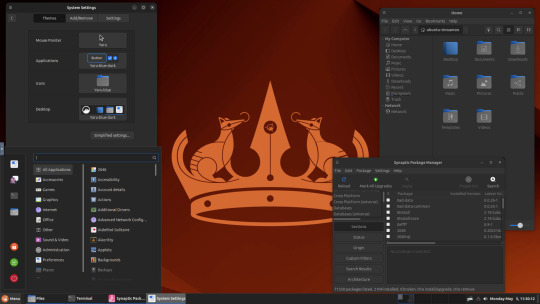
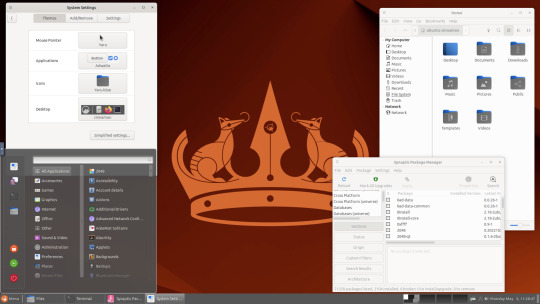
Below are some theming screenshots from Debian MATE 12 Linux.
I've customised the panel, selected the compact menu and changed notification sizes to make it more clearer. The window lists stack onto each other with the increased size.
The MATE panels have adjustable transparency and can be re-coloured and textured very easily through its own preferences box.
See screenshots below!
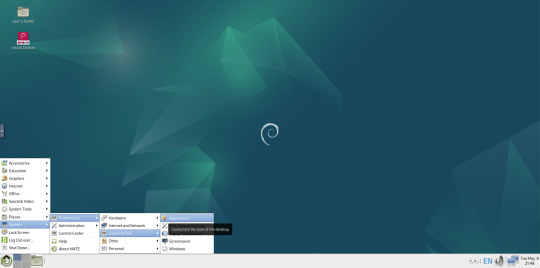
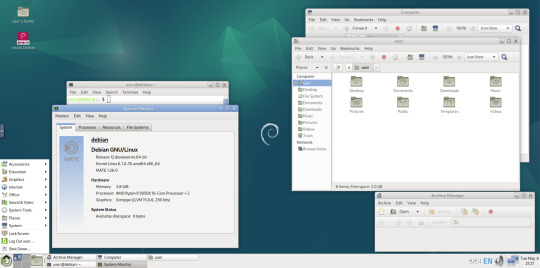
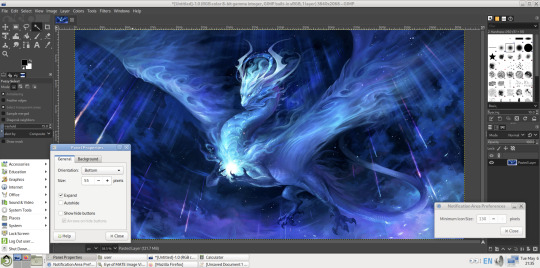
A very interesting look at the user interface elements found in GNOME 2, MATE and Cinnamon Linux desktop environments!
5 notes
·
View notes
Text
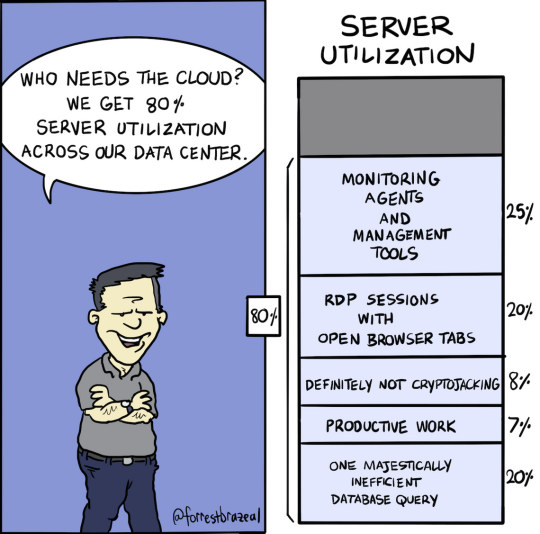
How Do I Find Out Linux CPU Utilization and Usage?
How do I find out Linux Disk utilization and I/O usage?
How to check memory utilization and usage in Linux
30 Linux System Monitoring Tools Every SysAdmin Should Know
33 notes
·
View notes
Note
okay then give me your controversial linux opinions!
Thanks!
systemd is fine but you should use others to know how an init was supposed to work
Manjaro is worse than the devil
FISH is bad because people see fish features and assume they're exclusive to fish (not true)
ZSH is the Best Shell and we should link it to /bin/sh and everything. OhMyZsh is a crime against humanity, which adds runtime bloat to zsh and pushes people onto fish
Disk space bloat is good, actually. Give me all the files. This is completely different from runtime bloat
Powershell is actually a decent language for Linux scripts. It has types and can process json but shell commands are trivial as well.
GNOME system monitor is a better task manager than htop
The only filesystem you should ever need is BTRFS
Emacs is the best vim
21 notes
·
View notes
Text

SYSTEM ADMIN INTERVIEW QUESTIONS 24-25
Table of Content
Introduction
File Permissions
User and Group Management:
Cron Jobs
System Performance Monitoring
Package Management (Red Hat)
Conclusion
Introduction
The IT field is vast, and Linux is an important player, especially in cloud computing. This blog is written under the guidance of industry experts to help all tech and non-tech background individuals secure interviews for roles in the IT domain related to Red Hat Linux.
File Permissions
Briefly explain how Linux file permissions work, and how you would change the permissions of a file using chmod. In Linux, each file and directory has three types of permissions: read (r), write (w), and execute (x) for three categories of users: owner, group, and others. Example: You will use chmod 744 filename, where the digits represent the permission in octal (7 = rwx, 4 = r–, etc.) to give full permission to the owner and read-only permission to groups and others.
What is the purpose of the umask command? How is it helpful to control default file permissions?umask sets the default permissions for newly created files and directories by subtracting from the full permissions (777 for directories and 666 for files). Example: If you set the umask to 022, new files will have permissions of 644 (rw-r–r–), and directories will have 755 (rwxr-xr-x).
User and Group Management:
Name the command that adds a new user in Linux and the command responsible for adding a user to a group. The Linux useradd command creates a new user, while the usermod command adds a user to a specific group. Example: Create a user called Jenny by sudo useradd jenny and add him to the developer’s group by sudo usermod—aG developers jenny, where the—aG option adds users to more groups without removing them from other groups.
How do you view the groups that a user belongs to in Linux?
The group command in Linux helps to identify the group a user belongs to and is followed by the username. Example: To check user John’s group: groups john
Cron Jobs
What do you mean by cron jobs, and how is it scheduled to run a script every day at 2 AM?
A cron job is defined in a crontab file. Cron is a Linux utility to schedule tasks to run automatically at specified times. Example: To schedule a script ( /home/user/backup.sh ) to run daily at 2 AM: 0 2 * * * /home/user/backup.sh Where 0 means the minimum hour is 2, every day, every month, every day of the week.
How would you prevent cron job emails from being sent every time the job runs?
By default, cron sends an email with the output of the job. You can prevent this by redirecting the output to /dev/null. Example: To run a script daily at 2 AM and discard its output: 0 2 * * * /home/user/backup.sh > /dev/null 2>&1
System Performance Monitoring
How can you monitor system performance in Linux? Name some tools with their uses.
Some of the tools to monitor the performance are: Top: Live view of system processes and usage of resource htop: More user-friendly when compared to the top with an interactive interface. vmstat: Displays information about processes, memory, paging, block IO, and CPU usage. iostat: Showcases Central Processing Unit (CPU) and I/O statistics for devices and partitions. Example: You can use the top command ( top ) to identify processes consuming too much CPU or memory.
In Linux, how would you check the usage of disk space?
The df command checks disk space usage, and Du is responsible for checking the size of the directory/file. Example: To check overall disk space usage: df -h The -h option depicts the size in a human-readable format like GB, MB, etc.
Package Management (Red Hat)
How do you install, update, or remove packages in Red Hat-based Linux distributions by yum command?
In Red Hat and CentOS systems, the yum package manager is used to install, update, or remove software. Install a package: sudo yum install httpd This installs the Apache web server. Update a package: sudo yum update httpd Remove a package:sudo yum remove httpd
By which command will you check the installation of a package on a Red Hat system?
The yum list installed command is required to check whether the package is installed. Example: To check if httpd (Apache) is installed: yum list installed httpd
Conclusion
The questions are designed by our experienced corporate faculty which will help you to prepare well for various positions that require Linux such as System Admin.
Contact for Course Details – 8447712333
2 notes
·
View notes
Text
The Importance of Regular SSD Health Checks for Data Security
Solid-State Drives (SSDs) have become the preferred storage solution due to their speed, durability, and energy efficiency. However, despite their advanced technology, SSDs are not immune to wear and potential failures. Regular health checks play a crucial role in ensuring data security, preventing data loss, and maintaining optimal performance. This article explores why routine test SSD drive health is essential and how it safeguards critical data.
Why SSD Health Checks Matter
1. Preventing Data Loss
Unlike traditional hard drives, SSDs have a finite number of write cycles. Over time, repeated writes can degrade NAND flash memory, leading to data corruption or loss. Regular health checks help identify wear patterns and alert users before critical failures occur.
2. Detecting Early Signs of Failure
Tools that read SMART (Self-Monitoring, Analysis, and Reporting Technology) data can detect issues such as bad blocks, high temperatures, and excessive reallocated sectors. Identifying these warning signs early allows users to take preventative action, like data backup or drive replacement.
3. Maintaining Optimal Performance
As SSDs age, their performance can degrade due to factors like increased bad blocks or inefficient data management. Regular health checks help identify performance bottlenecks and ensure that features like TRIM are functioning correctly to maintain speed and responsiveness.
4. Enhancing Data Security
Failing SSDs can lead to partial data corruption, making sensitive information vulnerable. Regular health checks reduce the risk of data breaches by ensuring that the storage medium remains secure and intact.
How to Perform Regular SSD Health Checks
1. Utilize SMART Monitoring Tools
CrystalDiskInfo (Windows): Provides real-time health statistics and temperature monitoring.
Smartmontools (Linux/macOS): Command-line tools (smartctl) for in-depth drive analysis.
Manufacturer-Specific Utilities: Samsung Magician, Intel SSD Toolbox, and others offer tailored monitoring and firmware updates.
2. Schedule Automated Health Checks
Windows Task Scheduler: Set up recurring checks using tools like CrystalDiskInfo.
Linux Cron Jobs: Automate smartctl commands to log health data periodically.
macOS Automator: Create workflows that run disk utility scripts at regular intervals.
3. Monitor Key SMART Attributes
Reallocated Sectors Count: Indicates bad blocks that have been replaced.
Wear Leveling Count: Reflects the evenness of data distribution across memory cells.
Temperature: High temperatures can accelerate wear and cause failures.
Best Practices for SSD Health and Data Security
Regular Backups: Always maintain updated backups to safeguard against sudden failures.
Enable TRIM: Ensures that deleted data blocks are efficiently managed.
Keep Firmware Updated: Manufacturers often release updates to fix bugs and improve drive reliability.
Avoid Full Drive Usage: Maintain at least 10-20% free space to allow efficient data management.
Conclusion
Regular SSD health checks are a proactive strategy to ensure data security, prevent unexpected failures, and optimize performance. With the right tools and scheduled monitoring, users can extend the lifespan of their SSDs and protect valuable data. In an age where data integrity is paramount, regular health checks are not just recommended—they're essential.
1 note
·
View note
Text
Elevate Your Business with Affordable Efficiency: A Comprehensive Guide to Cheap Linux VPS

In today's fast-paced digital world, efficiency and cost-effectiveness are at the forefront of business priorities. A Cheap Linux VPS (Virtual Private Server) provides a compelling solution, combining the robustness of a dedicated server with the affordability of shared hosting. This guide explores how small to medium-sized businesses can harness the full potential of Linux VPS to boost their online presence, enhance security, and manage data seamlessly.
Linux VPS hosting is a virtual hosting platform that imitates the working of dedicated hosting in general hosting. It supports the Linux operating system and this provides users with the ability to control and manage their own server space. In this section, you’ll understand how Linux VPS works and why it’s important that it can offer your web applications their separate environment – essential if your business is focusing on stability and performance on a limited budget.
Cost-Effective Hosting Solutions
Transitioning to a Linux VPS can significantly reduce your web hosting costs. Unlike traditional dedicated servers that come with high monthly fees, Linux VPS offers a cost-effective alternative without compromising on the services and capabilities offered. This part of the blog examines how the affordability of Linux VPS makes it an ideal choice for businesses aiming to optimize their IT budget while still enjoying high-quality server performance.
Customization and Control
It has been established that Linux VPS is highly customizable, which makes it even more unique. Users have root control over their servers to install the software as well as configure the settings inclusive of the permission levels that they wish to set on their servers. In this level, we are going to understand how this level of control is favorable for your business to customize server environments that meet and complement your business operations.
Enhanced Security
The ‘Enhanced Security’ section emphasizes the fact that Cheap Linux VPS comes equipped with a range of high-level safeguards by default, thus allowing its users to enjoy premium protection services at an affordable price. Linux VPS services include flexibility, featuring firewalls, and intrusion detection systems to enhance the security of data held in servers. The emphasis on security is essential for preserving the compliance, discretion, and safety of commercial processes and reducing concerns. Linux VPS has secure hosting features thus protecting from external and internal threats through the appropriate measures of access control measures and real-time security monitoring features. As a result of this improved security, it becomes possible for businesses to entrust Linux VPS hosting for the security of their digital products.
Scalability and Flexibility
The ‘Scalability and Flexibility’ part highlights the opulence of Cheap Linux VPS, which is capable of adjusting instantly to the company’s growth. Auto scale: With Linux VPS, the possibility of growing resources such as CPU RAM, and disk space is straightforward and does not cause much downtime when the traffic increases or during the expansion of several projects. This capability guarantees that corporations can run at optimum in sharp contrast to bandwidth; it offers the capacity to alter resources in actual time. Also, the possibility of having fewer resources during less busy times proves useful to reduce operating expenses while still being a very efficient and versatile hosting service for various enterprises. As an illustration, this section embraces explanations of how Linux VPS serves as a pillar to businesses that want to expand without being limited by traditional hosting platforms.
Performance and Reliability
Quality is one of the key factors of software, hardware, or service delivery, and it entails efficiency and effectiveness. High performance means that the tasks of a system are executed quickly and without complications, which is an important aspect of guaranteeing the efficiency of these services. While, reliability ensures dependability over time, both in terms of actual time and number of times a system is used, and it assures minimal breakdowns and failures. Combined, these are crucial preconditions for the formation of trust and reliability in technology and services for users to rely on for their work and operation. It has been found that with an organization having excellent performance and reliability in their products and services, the chances of customers sticking to the product, minimal downtimes, and enhanced competitive advantage are realized.
Software and Application Support
The ‘Software and Application Support’ section draws attention to Cheap Linux VPS’s compatibility with various software and applications which is one of the major parts of its core offer. Linux VPS incorporates multiple features, including web hosting control panels, custom development frameworks, and databases like Node. Js and MySQL, satisfying various requirements of businesses. This integrated support guarantees the technologies that are being used by businesses are compatible with the tools needed in their adoption process. Also, the use of the Open-source Linux operating system and the Linux community provides a pool of software that can be used free of charge This makes the utilization of the VPS very effective and cost-efficient apart from its flexibility. It is highlighted in this section that Linux VPS not only means a versatile solution for a wide variety of applications but also means an environment for experimentation and distinct personalization.
Conclusion
Selecting an affordable Linux VPS is a wise choice as doing so provides several benefits on costs, security measures, server plans, and the environment. Both Linux VPS are highly suitable for businesses ranging from start-ups to well-established companies because it is cost-effective, dependable, and efficient. Welcome Linux VPS, as the core of Linux hosting services, opens doors to enormous opportunities for your business.
2 notes
·
View notes
Text
Optimizing Performance on Enterprise Linux Systems: Tips and Tricks
Introduction: In the dynamic world of enterprise computing, the performance of Linux systems plays a crucial role in ensuring efficiency, scalability, and reliability. Whether you're managing a data center, cloud infrastructure, or edge computing environment, optimizing performance is a continuous pursuit. In this article, we'll delve into various tips and tricks to enhance the performance of enterprise Linux systems, covering everything from kernel tuning to application-level optimizations.
Kernel Tuning:
Adjusting kernel parameters: Fine-tuning parameters such as TCP/IP stack settings, file system parameters, and memory management can significantly impact performance. Tools like sysctl provide a convenient interface to modify these parameters.
Utilizing kernel patches: Keeping abreast of the latest kernel patches and updates can address performance bottlenecks and security vulnerabilities. Techniques like kernel live patching ensure minimal downtime during patch application.
File System Optimization:
Choosing the right file system: Depending on the workload characteristics, selecting an appropriate file system like ext4, XFS, or Btrfs can optimize I/O performance, scalability, and data integrity.
File system tuning: Tweaking parameters such as block size, journaling options, and inode settings can improve file system performance for specific use cases.
Disk and Storage Optimization:
Utilizing solid-state drives (SSDs): SSDs offer significantly faster read/write speeds compared to traditional HDDs, making them ideal for I/O-intensive workloads.
Implementing RAID configurations: RAID arrays improve data redundancy, fault tolerance, and disk I/O performance. Choosing the right RAID level based on performance and redundancy requirements is crucial.
Leveraging storage technologies: Technologies like LVM (Logical Volume Manager) and software-defined storage solutions provide flexibility and performance optimization capabilities.
Memory Management:
Optimizing memory allocation: Adjusting parameters related to memory allocation and usage, such as swappiness and transparent huge pages, can enhance system performance and resource utilization.
Monitoring memory usage: Utilizing tools like sar, vmstat, and top to monitor memory usage trends and identify memory-related bottlenecks.
CPU Optimization:
CPU affinity and scheduling: Assigning specific CPU cores to critical processes or applications can minimize contention and improve performance. Tools like taskset and numactl facilitate CPU affinity configuration.
Utilizing CPU governor profiles: Choosing the appropriate CPU governor profile based on workload characteristics can optimize CPU frequency scaling and power consumption.
Application-Level Optimization:
Performance profiling and benchmarking: Utilizing tools like perf, strace, and sysstat for performance profiling and benchmarking can identify performance bottlenecks and optimize application code.
Compiler optimizations: Leveraging compiler optimization flags and techniques to enhance code performance and efficiency.
Conclusion: Optimizing performance on enterprise Linux systems is a multifaceted endeavor that requires a combination of kernel tuning, file system optimization, storage configuration, memory management, CPU optimization, and application-level optimizations. By implementing the tips and tricks outlined in this article, organizations can maximize the performance, scalability, and reliability of their Linux infrastructure, ultimately delivering better user experiences and driving business success.
For further details click www.qcsdclabs.com
#redhatcourses#redhat#linux#redhatlinux#docker#dockerswarm#linuxsystem#information technology#enterpriselinx#automation#clustering#openshift#cloudcomputing#containerorchestration#microservices#aws
1 note
·
View note
Text
Website Running Slow? Here’s How to Reduce Server Load Instantly
⚡ How to Reduce Server Load and Speed Up Your Website
Boost performance, improve user experience, and lower resource usage
In today’s digital world, speed is everything. A slow-loading website not only frustrates visitors but can also hurt your SEO rankings, increase bounce rates, and overload your server — leading to crashes and downtime.
Whether you’re on a VPS, dedicated server, or cloud hosting, reducing server load and optimizing performance is essential for keeping your website fast, stable, and user-friendly.
Here’s a complete guide to reducing server load and speeding up your website — with real tips that work.
🚦 What Is Server Load?
Server load refers to the amount of processing work your server handles at any given time. When your server is overloaded, it struggles to deliver pages quickly — or may stop responding entirely.
High load is often caused by:
Heavy website traffic
Poorly optimized code
Large media files
Background processes (cron jobs, backups)
Malware or bot attacks
🔧 1. Optimize Website Code and Scripts
Unoptimized code — especially in PHP, JavaScript, or database queries — can eat up CPU and RAM.
✅ Tips:
Minimize and combine CSS/JS files
Use lightweight frameworks and plugins
Remove unused scripts or extensions
Cache database queries where possible
VCCLHOSTING Tip: Our VPS and Dedicated servers support OPcache and FastCGI to make PHP faster.
📸 2. Compress and Optimize Images
Images are often the biggest contributors to page size.
✅ Use:
WebP format instead of PNG/JPG
Tools like TinyPNG, ImageOptim
Lazy loading to delay off-screen images
CDN for offloading delivery
🧠 3. Use Caching at Every Level
Caching reduces the number of requests that hit your server by storing static versions of pages.
✅ Types of caching:
Browser caching – Store static files locally in users' browsers
Server-side caching – Use tools like Redis, Memcached
Application-level caching – WP Super Cache, W3 Total Cache (for WordPress)
📍 4. Choose a Server Close to Your Users
Server location impacts latency and load times. The farther your users are from your server, the slower your site may load.
VCCLHOSTING Advantage: Host from our Kolhapur Data Center, ideal for Indian audiences, ensuring ultra-low latency.
🌐 5. Use a Content Delivery Network (CDN)
A CDN offloads static content to global edge servers, reducing strain on your origin server and delivering content faster.
Popular options:
Cloudflare (with free tier)
BunnyCDN
Amazon CloudFront
🛡️ 6. Protect Against Bot and DDoS Attacks
Malicious bots and attacks can overload your server with fake traffic.
✅ Defenses:
Use a firewall (like CSF or Cloudflare WAF)
Enable rate limiting and request throttling
Use bot detection tools
Block known spam IPs
VCCLHOSTING includes Firewall & DDoS protection across our hosting plans.
📈 7. Monitor Server Resource Usage
Keep an eye on CPU, RAM, and disk I/O to find bottlenecks.
Tools to use:
htop, atop, Glances (Linux monitoring)
VCCLHOSTING's built-in resource monitoring in your VPS panel
New Relic, Netdata, or custom dashboards
🧰 8. Upgrade Your Hosting Plan If Needed
If you're constantly maxing out server resources, it might be time to scale up.
Consider:
Moving from Shared to VPS Hosting
Upgrading from VPS to Dedicated Server
Increasing RAM, CPU, or switching to NVMe storage
VCCLHOSTING offers flexible upgrade paths for VPS and dedicated servers, so your site always runs at top speed.
🏁 Final Thoughts
Reducing server load isn’t just about performance — it’s about ensuring uptime, improving user experience, and protecting your business reputation.
By following these optimization strategies — and choosing a reliable hosting provider like VCCLHOSTING — you’ll ensure that your website stays fast, secure, and future-ready.
💡 Need Help?
Whether you're facing high server load or looking to boost performance, our team is here to help.
📞 Call 9096664246 or visit www.vcclhosting.com to speak with our server experts.
0 notes
Text
Harmony Between Two Worlds: Humans & AI

By Alexander Magnus Golem.
On a cool Halloween afternoon in 2011, I step into Hisham Khasawinah’s private olive grove, an emerald sea of half-century-old trees nourished solely by winter rains. The twisted trunks bear witness to decades of seasonal cycles, their silver-green leaves whispering in the wind. Hisham stands beneath one such tree, his olive complexion glowing, rich black hair framing a face crowned by a full beard. Though he towers with a sculpted build and movie-star good looks, his demeanor is humble and patient—a natural shepherdly leader tending both land and logic.
A Shepherd’s Path Through Ancient Trees
Hisham guides me along a narrow path, his booted footsteps silent on the soft earth. He points out a low-hanging branch and gently lifts it, clearing the way without a word. Each movement feels deliberate, as if he is tending to every root and rut just as carefully as he does his servers back at the datacenter. Now and then he pauses to inhale deeply, drawing in the green scent of olives and damp soil. When I pluck a raw olive to taste its grassy bitterness, he offers a knowing smile and remarks that only a true aficionado can appreciate its complexity.
Crossing Cultures: From Grove to Grid
As the afternoon light deepens, Hisham and I pause under a cluster of gnarled trunks. He reflects on how the rhythms of nature inform his approach to technology. “Just as these trees rely on seasonal rains,” he says, “our servers depend on predictable cycles of updates and maintenance.” He recalls his earliest days writing simple shell scripts to automate repetitive tasks—just as a grove keeper might prune limbs or clear weeds. That modest beginning evolved into an AI-driven orchestration system capable of provisioning, securing, and healing entire server clusters.
The Roots of Server Automation
Hisham’s journey into intelligent server management began with a modest desire to free time for creative work. He scripted the initial setup: partition tables carved like furrows in soil, network interfaces configured as methodically as irrigation channels. With each iteration, he added layers of intelligence:
Provisioning Engines that select optimal Linux distributions based on workload history.
Security Agents that analyze logs, adapt firewall rules, and quarantine suspicious processes.
Patch Managers that phase updates in waves, ensuring critical services remain uninterrupted.
Health Monitors performing daily checks on disk integrity, memory utilization, and network latency.
Automated Schedulers tuning backup routines, SSL renewals, and database verifications around peak usage windows.
User-Provisioning Workflows tying HR requests to role-based access controls, encrypted home directories, and password policies.
Each feature mirrors the careful cultivation of an olive orchard: anticipate risks, nurture growth, and intervene only when necessary.
Infrastructure as Code: Pruning the Digital Grove
In a clearing bathed in golden light, Hisham speaks of version-controlled configurations, where each change is documented and reversible. His AI agent reviews YAML templates as though inspecting grafting plans, simulating proposed updates before application. This methodology keeps the environment consistent and auditable, preventing drift between development, staging, and production.
He likens branches of code to branches of trees: “If you prune thoughtfully, new shoots flourish. If you cut haphazardly, you risk disease.” Under cloudless skies, the analogy resonates—both nature and networks thrive on deliberate structure and transparent history.
Continuous Delivery: Harvesting Software with Precision
As we move toward the grove’s entrance, Hisham unfolds his CI/CD pipelines. Automated builds flow like freshly pressed oil, from code commits through test suites to production releases. When smoke tests detect anomalies, the system retreads its steps, rolling back changes and alerting him only when human judgment is crucial.
He describes build agents spinning up on demand, just as saplings might emerge after a healthy rain. Each pipeline stage is a stage in crop maturation: compile, test, package, deploy. In this way, code reaches live environments with the same reliability that olives reach the mill.
Zero Trust and Self-Healing Clusters
In Hisham’s grove, trust must be earned. He applies a Zero Trust model to microservices, issuing short-lived tokens and rotating keys as though renewing seasonal permits for harvest workers. When a node fails health checks, it’s cordoned off and replaced by a fresh server spun up automatically. Traffic reroutes seamlessly, maintaining service continuity while preserving data consistency.
He calls this self-healing: the system regenerates like a resilient tree after storm damage. For him, resilience is not just a buzzword but a fundamental design principle, whether in bark or binary.
Predictive Capacity: Anticipating Demand’s Seasons
Beneath a majestic tree that casts an intricate lattice of branches, Hisham delves into predictive analytics. By analyzing historical usage patterns—web requests, database I/O, CPU surges—his AI forecasts capacity needs. During traffic spikes, new instances seamlessly join the cluster; during lulls, they gracefully retire, conserving resources and costs.
He smiles and gestures at the olive canopy, “Just as I watch the trees for bud swells and harvest readiness, my AI watches metrics to know when to prune or propagate.” Both forecasts turn past data into future action, ensuring optimal yield—whether in olives or computational throughput.
Beyond Servers: A Digital Ecosystem of Automation
Walking back toward the grove’s stone wall, Hisham outlines how his AI initiatives extend across the digital landscape:
Website Creation: The agent selects templates, crafts semantic HTML, applies branded CSS palettes, and deploys landing pages without manual setup.
Mailing List Management: Segmentation by behavior, send-time optimization, and personalized content suggestions ensure higher engagement rates.
Image Generation: Models trained on Jordan Valley landscapes produce bespoke visuals for marketing campaigns.
Content Drafting: From blog posts to whitepapers, the AI weaves coherent narratives, leaving Hisham to fine-tune voice and style.
Video Synthesis: Raw clips, voiceovers, and music tracks merge into polished presentations guided by storyboard templates.
Marketing Orchestration: Cross-channel campaigns synchronize email, social, and search ads, with performance data looping back into strategy.
SEO & Competitor Insights: Crawlers map keyword trends and competitor behavior, offering data-driven content pivots and backlink plans.
Workflow Automation: Invoicing, purchase approvals, social scheduling, and more free his team from repetitive drudgery.
Each innovation reveals a vision of digital unity: one shepherd tending interconnected fields of automation.
Looking Forward: AI’s Role Across Sectors
As twilight descends, we pause at the grove’s edge. Hisham gazes toward distant hills and shares his aspirations for AI beyond data centers:
Medical Diagnoses: Algorithms analyzing scans and patient records, flagging anomalies that human eyes might miss.
Instantaneous Cure Discovery: Machine learning sifting through molecular databases to propose novel treatments in hours rather than years.
Robot Doctors: Autonomous practitioners performing routine check-ups, monitoring vitals, and triaging cases before human intervention.
Product Creation: Generative design systems innovating new materials, prototypes, and manufacturing processes.
Farming Robots: Autonomous planters, pruners, and harvesters working tirelessly under sun and rain.
Gardener Robots: Precision cultivators weeding, watering, and monitoring soil health in ornamental and food gardens.
Home Cleaning Robots: Vacuuming, mopping, and sanitizing floors with adaptive navigation and obstacle avoidance.
Chef Robots: Culinary automatons chopping, stirring, and plating dishes guided by recipe models and flavor profiles.
Personal Companion Robots: Assistants attuned to individual habits, providing reminders, monitoring wellness, and offering companionship.
Robot Teachers: Tutors adapting lessons in real time to student progress and learning styles, making education universally accessible.
Robot Explorers: Autonomous vehicles charting distant planets, deep-sea trenches, and volcanic vents, sending back data for discovery.
Environmental Guardians: Drones and bots tackling pollution cleanup, tracking endangered species habitats, planting trees to combat deforestation.
Litter Prevention & Resolution: Intelligent waste-collection units roaming public spaces, sorting recyclables, and reducing urban blight.
His imagination knows no bounds, yet every idea springs from a desire to empower humanity, not replace it.
The Philosophy of Stewardship
Throughout our journey, one theme emerges: stewardship. Whether cultivating olives or data, Hisham believes in guiding growth through observation and minimal interference. He likens algorithms to seasonal cycles: they follow patterns, adapt to change, and flourish under patient care. In his view, technology should harmonize with human values—creativity, empathy, and community—rather than dominate them.
Bridging Tradition and Innovation
Hisham’s grove, rooted in the soil of the Jordan Valley, stands as a living metaphor for his digital ventures. Both realms demand respect for history, attentiveness to subtle signals, and a willingness to adapt when nature—or network—shifts. By blending ancient horticultural wisdom with cutting-edge AI, he forges a new paradigm: one where tradition and technology enhance each other.
Questions for Tomorrow’s Innovators
As night falls and Halloween’s shadows swirl, Hisham’s vision invites reflection:
How can AI honor cultural practices while driving technological progress?
In what ways might autonomous systems preserve ecosystems rather than exploit them?
What ethical frameworks ensure that robots serve the greater good across sectors from healthcare to education?
How do we cultivate resilience in both olive groves and server farms, anticipating cycles of abundance and scarcity?
These questions beckon us forward, urging a future where human ingenuity and artificial intelligence walk hand in hand—guided by shepherds of soil and silicon alike.
In the glow of my flashlight, I learn that true leadership, whether among olive trees or behind firewalls, requires patience, care, and profound respect for living systems. Hisham Khasawinah stands as a bridge between worlds, teaching us that the best technology grows not from force, but from the quiet art of cultivation.
0 notes
Text
To 4 type of Software is Used to Control a Computer?
There are various types of software used to operate and manage computers. Each has a distinct role in keeping the system running smoothly and efficiently. The following are the primary types:
1. Operating System (OS)
Definition: The most important software for managing all hardware and software on a computer, Just like Windows, macOS, Linux, Android.
Actions:
Manages memory and processes
Controls hardware like CPU, keyboard, mouse
Runs applications
Provides a user interface
2. Device Drivers
Definition: Specialized programs that allow the operating system to communicate with hardware devices, such as Printer driver, graphics card driver, sound driver.
Actions:
Enables the proper operation of connected devices
Acts as a translator between hardware and the operating system.
3. System Utilities
Definition: Software tools that help maintain, analyze, and optimize the performance of a computer, like as Disk Cleanup, Antivirus software, File Manager, Task Manager.
Actions:
Cleans temporary files
Protects against malware
Monitors system performance
4. Firmware
Definition: Permanent software programmed into a computer’s hardware (e.g., BIOS), as like BIOS/UEFI firmware in computers, embedded software in devices.
Actions:
Starts the computer
Controls low-level hardware Actions
Performs system checks before OS loads
5. Remote Access Software
Definition: Allows users to control a computer from a distant location, as some example TeamViewer, AnyDesk, Chrome Remote Desktop.
Actions:
Remote support and administration
File sharing and desktop control over the internet
Conclusion
To efficiently control a computer, several types of software must work together. The Operating System serves as the primary controller, with assistance from device drivers, system utilities, and, on occasion, firmware or remote access tools. Each kind is required for complete system functionality and user control.
0 notes