#quantum blockchain
Explore tagged Tumblr posts
Text
Post Quantum Blockchain: Future of Decentralized Technology
What will become of our decentralized networks when quantum computers can break our most secure cryptographic defenses today? If quantum attacks eat away at digital security, then the security of blockchain systems has never been more crucial. Welcome to the Post Quantum Blockchain universe, an incoming paradigm shift strategy combining the blockchain’s resilience and the post-quantum cryptography’s next-generation security to protect the immortal digital universe.
In this article, we discuss the important part that quantum-resistant blockchain will have to play in protecting decentralized networks from the increasing menace of quantum computing.
Understanding Post-Quantum Blockchain

Post Quantum Blockchain is a blockchain network that is protected by highly advanced, quantum computer-immune cryptographically secured algorithms. RSA or ECC are conventional tools used for encryption, which would become sitting ducks against attacks from quantum algorithms like Shor’s, which will compromise their integrity. It poses a humongous risk to decentralized networks operating on such algorithms for data assurance, identity authentication, and secured transactions.
With the integration of quantum-resistant cryptography, these blockchain platforms can provide security and trust in a quantum computer-based future. The National Institute of Standards and Technology (NIST) is attempting to develop ultimate encryption standards to be the new way of doing it, and hence quantum-secure blockchain deployment becomes an unavoidable evolution.
Why Traditional Blockchains Are Vulnerable

Although blockchain itself is generally considered secure and unalterable, it is not resistant to the increasing threat of quantum computing. Classical blockchains are highly dependent on classical cryptographic methods — namely, public-key cryptography — to protect digital identities, authenticate transactions, and establish consensus among distributed nodes. But with the accelerated advancement of quantum technology, these methods are in serious jeopardy. A sufficiently powerful quantum computer would be able to take advantage of loopholes in such cryptographic schemes to reverse-engineer private keys from public keys, allowing hackers to impersonate the real users. This can result in unauthorized transactions, loss of funds, or even bulk tampering with the blockchain ledger.
Furthermore, quantum computations like Shor’s algorithm can even break the digital signatures that are employed to secure transactions. If such signatures are compromised, they would no longer provide trust in the authenticity or source of a message. Quantum systems would also destabilize consensus systems, which are critical to all participants in a network adhering to a specified state of the blockchain. These findings point to how unprepared systems are at present for a quantum world.
In order to combat these future threats, cryptographers and developers are turning to Post Quantum Blockchain solutions that build on quantum-resistant protocols and algorithms. This next-generation solution can potentially restore trust and security in decentralized systems in the quantum era.
Core Principles Behind Post-Quantum Blockchain
To create a post-quantum blockchain that is resilient, some principles are used-
Lattice-based cryptography: Lattice-based cryptography is a bedrock, since it is quantum proof. Its mathematical complexity is high and it’s computationally not possible even for quantum computers to reverse-engineer encrypted data, thus it’s a very secure way of safeguarding identity and key exchange.
Hash-based signatures: Hash-based signatures constitute another central element. They provide secure short-term digital authentication to maintain messages and transactions tamper-evident. Hash-based signatures work with irrevocable one-way functions for a quantum system, as opposed to classical digital signatures.
Code-based cryptography: Code-based cryptography is also used to ensure a good level of long-term message security. It uses codes that will resist such forms of decryption, whether classical or quantum.
Zero-knowledge proofs: Finally, we have zero-knowledge proofs, which are incorporated to complete the system. Zero-knowledge proofs allow a party to verify possession of knowledge about a condition or value without sharing underlying information. This maintains confidentiality and guarantees immunity from quantum attacks, such that data confidentiality and trust are achieved in decentralized applications.
Advantages of Post-Quantum Blockchain
1. Future-Proof Security
Most readily apparent benefit of Post Quantum Blockchain is that it will resist quantum attacks. Avoiding future attacks ahead of time, the developers will not need to invest the exorbitant expense of redoing systems down the road.
2. More Privacy
New cryptographic building blocks employed by Post Quantum Blockchain can also enhance the protection of privacy through improved anonymization techniques.
3. Compliance with Regulations
As government agencies start to issue post-quantum compliance requirements, employing Quantum Blockchain protocols puts businesses ahead of the law.
4. Long-Term Data Integrity
In contrast to legacy systems that can grow obsolete in the quantum age, Post Quantum Blockchain solutions guarantee your data is immutable and trusted for decades to come.
Real-World Use Cases for Post-Quantum Blockchain
Some industries are starting to consider Post Quantum Blockchain-
Finance: The banking industry, for example, is among the first to embrace. Encryption is a major source of security for online transactions, customer identity, and online balances for banks. With the danger of traditional cryptography from quantum computers, quantum-resistant blockchain guarantees long-term security for banking services, cryptocurrencies, and smart contracts.
Healthcare: Healthcare, where the confidentiality and integrity of patient data are paramount, sees this technology providing tamper-evident storage and transport of sensitive information. Decentralization, and with it the use of quantum-safe encryption, makes for safe sharing of medical records between health providers and shields against leaks and unauthorized alteration.
Supply Chain: The supply chain sector is also discovering the utility of this new solution. Through the utilization of quantum-resistant blockchain, businesses can create open, immutable records of product origin, transport, and handling. It assists in the prevention of fraud, lowers counterfeiting, and increases efficiency in international logistics.
Government: Governments are exploring their use for secure administration of digital identity, citizenship authentication, and even voting. With election security and identity fraud issues on the rise, a tamper-proof, quantum-secure blockchain can provide more public trust and operational integrity to democratic and administrative systems.
The Rise of Post Quantum Secured Blockchain
Post quantum secured blockchain technology is a giant leap towards the security of decentralized platforms against the impending threat of quantum computers. Traditional blockchains, though secure against classical attacks, are becoming increasingly susceptible to quantum algorithms that support breaking standard encryption schemes employed.
Conversely, post quantum secured blockchain networks are inherently constructed with quantum resistance. Every single aspect — identity verification, transaction verification, smart contracts, and consensus algorithms — is supported by cryptographic algorithms particularly selected for their quantum decrypt resistance.
This method guarantees that important activities such as signing a contract, digital signing, and multi-party cooperation on data are secure, transparent, and tamper-evident even in the future when all have quantum processors. With a trend of industries going quantum-readiness, implementing such infrastructure is not an upgrade — it is a required building block.
METHODOLOGY: Ensuring AI Safety Through Post Quantum Blockchain

To truly safeguard AI’s influence on society, data integrity must be prioritized above all. As artificial intelligence systems become more intertwined with human decision-making, preventing malicious replication of identity and the misuse of personal data is crucial. One reliable approach is the integration of Post Quantum Blockchain…
#post quantum blockchain#post quantum encryption#quantum blockchain#post quantum securityu#blokchain technology#decentralized database#post quantum cryptography#post quantum secure blockchain#blockchain security#ncog#blockchain technology#secure blockchain#secure blockchain technology#quantum safe cryptography#tumblr#blockchain#quantum resistant blockchain#quantum attacks#quantum computer#quantum compting#decentralized system#blockchain network#did#digital security
1 note
·
View note
Text
Nightshift CCTV Operator
Job title: Nightshift CCTV Operator Company: Corps Security Job description: of ‘loyalty, integrity, service’, we have become the UK’s most established and respected specialist security services provider… Assignment Instructions. Record all events and actions monitored from within the control room. Respond and react… Expected salary: £13.1 per hour Location: Paisley Job date: Fri, 27 Jun 2025…
#Aerospace#audio-dsp#Automotive#Blockchain#Crypto#Cybersecurity#DevOps#full-stack#govtech#insurtech#iOS#legaltech#low-code#Machine learning#metaverse#power-platform#prompt-engineering#Python#quantum computing#React Specialist#regtech#robotics#rpa#scrum#site-reliability#SoC#solutions-architecture#technical-writing#telecoms
3 notes
·
View notes
Text
The Future of Banking: How Technology Will Transform Finance
The banking industry is undergoing a radical transformation, driven by AI, blockchain, quantum computing, and decentralized finance (DeFi). The future of banking will be faster, more secure, and hyper-personalized, with traditional banks competing against digital-native financial ecosystems. Here’s what the future holds: 1. AI-Powered Banking ✅ Hyper-Personalization – AI analyzes spending…
#ai#banking#bitcoin#blockchain#central banking#crypto#cryptocurrency#currencies#Education#ethereum#finance#future of banking#invisible banking#neobanks#news#quantum banking#technology#USA
2 notes
·
View notes
Text




The Great Reset, Redesign of the World Game (s) as a system of federated systems: USPTO 13/573,002 Heart Beacon Cycle Time - Space meter adaptive procedural template tech framework for the net, net of programmable $$$
#cryptocurrency #quantum #artificialintelligence #AI #IP #data #structured data
#blockchain#cryptocurrency#bitcoin#economic collapse#cryptocurrencies#econometrics#reset#money#DeFi#Fintech#TradeFi#quantum computing
2 notes
·
View notes
Text
0 notes
Text
Space Technology Could Be Bigger Than Google
Space Technology Could Be Big if We Can Overcome the Technological Hurdles | HackerNoon

0 notes
Text
How Big Data is Revolutionizing Algorithmic Trading | Bigul

Big data, AI, and real time processing are transforming algorithmic trading. Explore its future with quantum computing and blockchain for smarter decisions.
Read more..
#Big data#Artificial Intelligence#Algorithmic Trading#quantum computing#blockchain#Machine Learning#AI & Machine Learning#AI Machine Learning#algo trading#algo trading app#bigul#algo trading platform#algo trading india#algo trading strategies#bigul algo#free algo trading software#algorithm software for trading#finance#investment#investment platform#investments#investors#investment platform in india#algorithmic trading software free#algos#algorithm#best algo trading software#best algo trading software in india#best share trading app in india#best share trading app
0 notes
Text
#Artificial Intelligence Trends 2025#Blockchain Innovations 2025#Energy-Efficient Computing Technologies#Impact of AI on Future Industries#Quantum Computing Applications in Business
0 notes
Text
Post Quantum Encryption: Future of Unbreakable Digital Security
What if all that we believed was safe—our bank transfer, confidential messages, and national secrets—can be wiped out instantly because of quantum computers? The digital era, fueled by classical cryptography, is on the verge of being revolutionized. Because quantum computing is growing exponentially, traditional cryptographic techniques are failing. The solution to this impending threat is a breakthrough technology in the form of Post Quantum Encryption—a quantum-proof method that is capable of deflecting even the most aggressive quantum attacks.
This emerging technology is reshaping the future of cybersecurity by preparing for a world where quantum computers can crack current encryption standards in seconds. In this article, we’ll discover what Post-Quantum Encryption is, why it is relevant, how it works, and how it is changing the future of unbreakable digital security.
Rethinking Digital Safety: The Post-Quantum Landscape
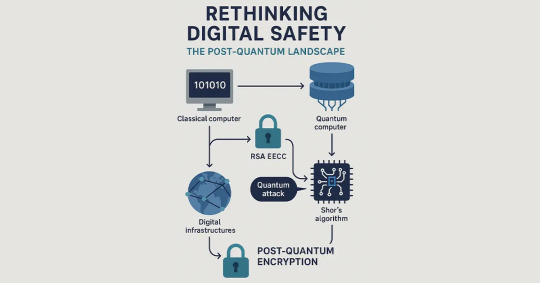
Quantum computers apply the principles of quantum mechanics for calculations that surpasses the limits of functionality of classical computers.. The foundations of today’s encryption, RSA and ECC, can be hacked using algorithms like Shor’s algorithm literally in a split second across classical computers. That is with the coming of age of quantum computing, current encryption will become obsolete.
Post-Quantum Encryption refers to cryptographic schemes that are quantum- and classical computer-resistant. It is not quantum-mechanical but rather mathematical problems believed to be hard for both machine classes. Using these crypto techniques now, we can start to protect digital infrastructures well before quantum attacks are mainstream.
AI and Data Protection: A New Methodology for Future Security

Redefining Our Strategy for AI-Safe Systems
In order to have a safe and ethical future where artificial intelligence (AI) is both ethical and not at the cost of human data, we need to redefine our digital defenses. Data protection is the linchpin—not merely for privacy, but to ensure that AI doesn’t become cataclysmically autonomous.
A. Quantum-Resistant Data Security
The highest priority is to create secure, decentralized models for encrypted data storage. Post-Quantum Encryption has a crucial role to play here. In contrast to conventional models, post-quantum cryptographic models are quantum-proof against decryption attacks. For example, blockchain-based projects such as NCOG Earth Chain have already started deploying decentralized storage systems driven by post-quantum algorithms. This empowers users with control over their data and excludes the possibility of centralized attacks or AI manipulation. Mass-scale adoption of post-quantum encryption...
#post quantum encryption#post quantum blockchain#post quantum security#post quantum cryptography#quantum computers#quantum computing#ncog earth chain#data security#quantum-resistant#quantum security#quantum blockchain
1 note
·
View note
Text

Quantum Security and Post-Quantum Cryptography: Preparing for the Cryptographic Revolution
Cryptography serves as the foundation of our digital security infrastructure, protecting sensitive data from unauthorized access and ensuring the integrity of our communications. This science of secure information exchange has evolved continuously alongside advances in computing technology. However, we now stand at a critical juncture as quantum computing emerges from theoretical possibility to practical reality, threatening to undermine the very cryptographic systems we rely on daily.
The imminent arrival of powerful quantum computers presents both unprecedented challenges and opportunities for information security. This article explores how quantum computing affects current cryptographic practices, why we need quantum-resistant solutions, and the promising approaches being developed to secure our digital future in the post-quantum era.
Classical Cryptography
The Vulnerability of Classical Algorithms
The security of most cryptographic systems today relies on mathematical problems that are computationally difficult for classical computers to solve. Quantum computers, however, can exploit quantum mechanical phenomena like superposition and entanglement to solve certain problems exponentially faster than their classical counterparts.
This quantum advantage becomes particularly concerning when we consider widely-used public-key cryptographic algorithms like RSA (Rivest-Shamir-Adleman) and ECC (Elliptic-Curve Cryptography). These systems form the backbone of secure communications across the internet, protecting everything from financial transactions to private messages.
How Shor's Algorithm Threatens Current Encryption
At the heart of the quantum threat lies Shor's Algorithm, developed by mathematician Peter Shor in 1994. This quantum algorithm can efficiently solve two mathematical problems that underpin much of modern cryptography:
RSA Encryption Under Threat
RSA encryption derives its security from the difficulty of factoring large composite numbers into their prime components. For example, while it's easy to multiply two large prime numbers (p and q) to get a product (n), working backward to determine the original primes becomes exponentially more difficult as the numbers grow larger.
A classical computer would require billions of years to factor a 2048-bit RSA key. However, Shor's Algorithm running on a sufficiently powerful quantum computer could perform this factorization in hours or even minutes. Once the prime factors are known, the private key can be easily derived from the public key, completely compromising the encryption system.
To illustrate: If n = p × q is a 2048-bit number (the product of two 1024-bit primes), a classical computer would need to check an astronomical number of possibilities. A quantum computer using Shor's Algorithm could find the factors p and q directly through quantum operations that essentially explore multiple possibilities simultaneously.
ECC Encryption Equally Vulnerable
Elliptic Curve Cryptography faces a similar threat. ECC relies on the difficulty of solving the discrete logarithm problem on elliptic curves – finding the value k when given points G and P, where P = k·G on an elliptic curve.
Shor's Algorithm can also be adapted to solve this discrete logarithm problem efficiently. Once a quantum computer can determine the private key k from the publicly available information G and P, the security guarantees of ECC collapse completely.
These vulnerabilities are not merely theoretical concerns. As quantum computers continue to advance, the timeline for practical quantum threats to cryptography grows shorter. This reality has spurred intense research into post-quantum cryptographic solutions.
Quantum-Resistant Cryptography
Post-Quantum Cryptography: A New Paradigm
Post-quantum cryptography (PQC) represents a new approach to cryptographic algorithm design. Rather than relying on mathematical problems vulnerable to quantum attacks, PQC algorithms are built on alternative mathematical foundations believed to be resistant to both classical and quantum computational methods.
Several promising approaches have emerged in the field of post-quantum cryptography:
Lattice-Based Cryptography
Lattice-based cryptography relies on the computational difficulty of solving certain problems related to geometric structures called lattices. These problems, such as finding the shortest vector in a high-dimensional lattice, appear resistant to quantum attacks.
CRYSTALS-Kyber, selected by NIST as a standard for post-quantum key encapsulation, exemplifies this approach. The security of Kyber stems from the hardness of the module learning with errors (MLWE) problem, which has withstood significant cryptanalysis efforts.
Lattice-based systems offer reasonable key sizes and efficient operations, making them practical for implementation across various computing environments.
Hash-Based Cryptography
Hash-based cryptography builds secure systems from cryptographic hash functions, which are already believed to be quantum-resistant. These approaches, like SPHINCS+, provide strong security guarantees based on minimal assumptions, making them particularly attractive as conservative options for long-term security.
The main challenge with hash-based signatures has been their relatively large signature sizes, though newer variants have made significant improvements in efficiency.
Code-Based Cryptography
Code-based cryptography leverages the difficulty of decoding certain error-correcting codes without knowledge of the code structure. McEliece, one of the oldest public-key cryptosystems (proposed in 1978), falls into this category and has resisted both classical and quantum cryptanalysis for decades.
While code-based systems typically require larger key sizes, they offer fast encryption and decryption operations, making them suitable for specific applications where key size is less constrained.
NIST's Post-Quantum Standardization Process
Recognizing the urgency of developing quantum-resistant standards, the U.S. National Institute of Standards and Technology (NIST) initiated a comprehensive evaluation process in 2016. This multi-year effort involved the global cryptographic community in analyzing and testing candidate algorithms.
In July 2022, NIST selected CRYSTALS-Kyber for general encryption and key establishment, along with three digital signature algorithms: CRYSTALS-Dilithium, FALCON, and SPHINCS+. These selections represent a significant milestone in preparing our digital infrastructure for the quantum era.
The standardization process continues with additional candidates under consideration, ensuring a diverse portfolio of solutions to meet various security and performance requirements.
Quantum Key Distribution
While post-quantum cryptography focuses on developing classical algorithms resistant to quantum attacks, quantum key distribution (QKD) takes a fundamentally different approach by using quantum mechanics itself to secure communications.
How QKD Works
QKD leverages fundamental properties of quantum physics to create a secure communication channel. The process typically involves sending polarized photons (light particles) between two parties, traditionally named Alice and Bob:
1. Alice sends a stream of photons, each randomly polarized in one of several possible states
2. Bob measures each photon, also choosing measurement bases randomly
3. Alice and Bob publicly compare which measurement bases they used (but not the results)
4. They keep only the results where they happened to use matching bases
5. These matching results form a shared secret key
The security of QKD stems from a fundamental principle of quantum mechanics: the act of measuring a quantum system disturbs it. If an eavesdropper (Eve) attempts to intercept and measure the photons, she inevitably introduces detectable errors in the transmission. Alice and Bob can detect these errors through statistical analysis, revealing any attempted eavesdropping.
Limitations and Practical Considerations
While QKD offers theoretical perfect security, practical implementations face significant challenges:
- Physical distance limitations due to photon loss in transmission media
- Vulnerability to side-channel attacks targeting implementation flaws
- Requirements for specialized hardware and dedicated quantum channels
- Integration difficulties with existing network infrastructure
Despite these challenges, QKD networks have been deployed in limited settings, such as financial institutions and government facilities. Ongoing research continues to address these limitations, potentially expanding QKD's practical applications.
Implementing Quantum Security
Hybrid Cryptographic Systems
Given the evolving nature of both quantum threats and quantum-resistant solutions, security experts recommend a hybrid approach during the transition period. This strategy involves implementing both classical and post-quantum algorithms simultaneously, providing immediate protection while allowing for gradual migration.
For example, a hybrid TLS implementation might use both an RSA key exchange and a lattice-based key exchange, requiring an attacker to break both systems to compromise the connection. This approach provides defense in depth while the security community builds confidence in post-quantum solutions.
Continuous Monitoring and Threat Detection
As quantum computing capabilities advance, organizations must implement robust monitoring systems to detect potential quantum threats. Advanced analytics and machine learning algorithms can identify unusual patterns that might indicate quantum-based attacks on cryptographic systems.
This continuous vigilance allows security teams to respond rapidly to emerging threats, potentially identifying compromised systems before significant damage occurs.
Blockchain Integration with Quantum-Resistant Cryptography
Blockchain technology, with its emphasis on immutability and decentralized trust, represents both a vulnerable target and a potential solution in the quantum security landscape. By integrating quantum-resistant cryptographic algorithms into blockchain protocols, these systems can maintain their security guarantees even against quantum attacks.
Several blockchain projects are already implementing post-quantum signatures and encryption methods, demonstrating how these technologies can complement each other to enhance overall security.
Quantum Random Number Generation
The strength of any cryptographic system ultimately depends on the quality of randomness used in key generation. Quantum Random Number Generators (QRNGs) leverage quantum phenomena to produce truly random numbers, providing a fundamental advantage over classical random number generators.
Unlike classical RNGs, which might contain subtle patterns or biases, QRNGs derive randomness from inherently unpredictable quantum processes like radioactive decay or photon path detection. This true randomness strengthens cryptographic systems by ensuring that keys cannot be predicted, even with advanced computational capabilities.
Commercial QRNG solutions are already available, offering enhanced security for critical applications where high-quality randomness is essential.
Preparing for the Post-Quantum Future
Impact Across Sectors
The transition to quantum-resistant cryptography will affect virtually every sector of the digital economy:
Financial Services: Banks and payment processors must protect transaction data not only from current threats but also from future attacks where encrypted data, harvested today, could be decrypted once quantum computers mature—a "harvest now, decrypt later" attack strategy.
Healthcare: Medical records contain sensitive personal information that requires long-term protection, making early adoption of post-quantum cryptography particularly important for healthcare organizations.
Government and National Security: Government agencies handling classified information face some of the most urgent needs for quantum-resistant solutions, as nation-state adversaries may be among the first to develop advanced quantum computing capabilities.
Critical Infrastructure: Power grids, telecommunications networks, and transportation systems rely on secure communications to function safely, making their protection from quantum threats a matter of national security.
Research and Development Priorities
As we navigate the transition to post-quantum security, several research priorities emerge:
Performance Optimization: Further research to improve the efficiency of post-quantum algorithms, reducing computational overhead and resource requirements
Implementation Security: Development of side-channel resistant implementations to ensure that practical deployments don't introduce vulnerabilities
Cryptographic Agility: Creating systems that can rapidly update cryptographic algorithms without major infrastructure changes
Standards Development: Continued international cooperation on cryptographic standards to ensure global interoperability of secure systems
Conclusion
The advent of quantum computing represents both a significant challenge and an opportunity for cryptographic security. While quantum computers threaten to break the mathematical foundations of current encryption systems, they also inspire the development of more robust cryptographic approaches.
Through the development and adoption of post-quantum cryptographic algorithms, quantum key distribution, and enhanced security practices, we can ensure that our digital infrastructure remains secure in the quantum era. The path forward requires collaboration between researchers, industry leaders, and government agencies, working together to build quantum-resistant systems before large-scale quantum computers become a reality.
By understanding the quantum threat landscape and implementing proactive security measures, organizations can protect their sensitive information and maintain trust in digital systems even as quantum computing technology advances. The time to prepare for the post-quantum future is now, ensuring that cryptography continues to fulfill its essential role in securing our increasingly connected world.
#linklayer#blog#technology#innovation#science#space science#space#electronics#global#computer science#advanced technologies#tech#techinnovation#quantum computing#quantum physics#quantum mechanics#learning#cybersecurity#cyber security#data security#cryptography#blockchain
0 notes
Text
SAP Security Architect
Job title: SAP Security Architect Company: Kyndryl Job description: security solutions that not only protect our business objectives and regulatory requirements, but also provide innovative… solutions to stay ahead of emerging threats. You will conduct risk ***essments and threat modeling to identify and prioritize… Expected salary: Location: London Job date: Tue, 22 Jul 2025 22:02:51 GMT Apply…
#agritech#artificial intelligence#Azure Solutions Expert#Blockchain#cloud-computing#Cybersecurity#data-engineering#deep-learning#digital-twin#Ecommerce#edtech#erp#insurtech#iOS#iot#it-consulting#it-support#low-code#marine-tech#product-management#Python#quantum computing#regtech#scrum#SEO#software-development#system-administration#telecoms#ux-design
0 notes
Text
10 Cutting-Edge Technology Trends Shaping 2025
In today’s rapidly evolving digital landscape, staying ahead means embracing transformative innovations that redefine every aspect of our lives. As we approach 2025, industries across the board are being revolutionized by a wave of advancements. The future is being molded by 10 Cutting-Edge Technology that not only streamline processes but also inspire creativity, enhance connectivity, and drive…
#10 Cutting-Edge Technology#2025 Tech Trends#5G#6G#AR#Artificial Intelligence#Autonomous Vehicles#Biotechnology#Blockchain#Cybersecurity#Decentralized Finance#Digital Transformation#Extended Reality#Future Technology#Green Technologies#Health Tech#Innovation#Internet of Things#IoT#Machine Learning#Next Generation Connectivity#Quantum Computing#Smart Transportation#Sustainable Energy#VR
0 notes
Text

The Great Reset / The World Game: Utopia or Oblivion ? Buckminster Fuller's The World Game: Utopia or Oblivion ? Swords to plowshares solutions. Nobel Prize winning Economist Milton Friedman "only a crisis brings about change and makes the politically impossible become the politically inevitable" #IP #DeFi #patent #patentlaw Github: http://github.com/Beacon-Heart
#blockchain#cryptocurrency#bitcoin#economic collapse#econometrics#economics#sustainable#reset#money#fintech#quantum computing#artificial intelligence
2 notes
·
View notes
Text
#Quantum International Corporation#cybersecurity#QuantumInternational#Web3#AI#Blockchain#Innovation#DigitalTransformation#TechSolutions#electronicsnews#technologynews
0 notes
Text
Web 3.0 vs Web 2.0: A Writing Revolution
How Web 3.0 is Rewriting the Rules of Writing, Ownership, and Monetization Forever The Broken Promise of Web 2.0 For decades, writers have been trapped in a system that rewards platforms over creators. The Web 2.0 era turned content into a commodity—owned by corporations, monetized through ads, and dependent on algorithms. Writers became cogs in a machine, trading their time and talent for…
#ai#AI and Writing#AI-Powered Writing#blockchain#Blockchain Publishing#Content Monetization Strategies#Creative Economy#crypto#Crypto Writing Tools#DAOs for Writers#Decentralization#Decentralized Content#Decentralized Publishing#Digital Sovereignty#DigitalOwnership#Earning from Writing in Web3#future of work#FutureOfWork#Gumroad Digital Products#Ko-fi for Writers#Metaverse#NFT Books#Quantum Writing#Substack Crypto#technology#The New Creator Economy#Tokenized Creativity#Web 11:11#Web 3.0 Writing#Web 3.0 Writing Blockchain Publishing NFT Books Decentralized Content AI and Writing Tokenized Creativity Digital Sovereignty Web3 Monetizat
0 notes
Text
Unlocking Success: The Power of Perseverance
Unlocking Success: The Power of Perseverance. The Power of Perseverance Perseverance isn't just about not giving up. It's about consistently working towards your goals, even when things get tough. It's about facing obstacles with courage and determinatio
Imagine yourself ten years from now, reflecting on your life. Do you see a life filled with regret, where dreams were left unfulfilled because you gave up too easily? Or do you see a life of satisfaction, where you pushed through challenges and achieved your goals? The choice is yours. Disclaimer: This blog post was created with the assistance of AI writing tools. AI has been instrumental in…

View On WordPress
#"antique clock repair"#"antique dollhouse restoration"#"antique furniture refinishing techniques"#"beginner&039;s guide to calligraphy"#"beginner&039;s guide to knitting socks"#"beginner&039;s guide to taxidermy"#"beginner&039;s guide to woodworking"#"best books about beekeeping"#"best books on bird watching"#"best books on mushroom foraging"#"best books on urban gardening"#"blockchain technology for business"#"crochet patterns for stuffed animals"#"ethical considerations in artificial intelligence"#"exploring the human mind"#"exploring the universe"#"future of artificial intelligence"#"gene editing and its ethical dilemmas"#"how to build a backyard fire pit"#"how to grow bonsai trees indoors"#"how to grow herbs indoors"#"how to make homemade candles"#"how to make homemade soap"#"how to raise silkworms at home"#"impact of climate change on human health"#"learn to play the banjo"#"learn to play the harmonica"#"learn to play the ukulele chords"#"neurotechnology and its implications"#"quantum computing explained"
0 notes