#risc v
Explore tagged Tumblr posts
Text
can someone please explain to me how people find programming languages like python or rust easier to work with than assembly?
I am trying to learn rust and the syntax is so so painful and annoying compared to RISC-V assembly, why is it so complex? I am clearly doing something fundamentally wrong
with assembly I can look at a 4 page long PDF and know exactly how to do everything, but in rust the fucking "let" command or whatever it is is more complex then VAX why.
then there are all the libraries that all have their own unique flavor of pain meanwhile I cant put stuff on the damn screen
6 notes
·
View notes
Text
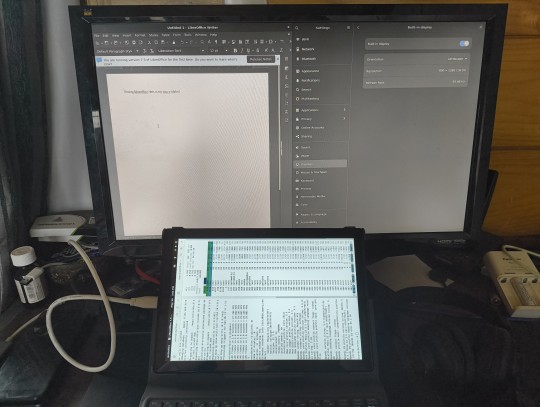



I got sent this PineTab-V a while ago. Going to port a newer version of Debian or maybe Fedora rawhide to it. I'll keep posting about my journey with this.
4 notes
·
View notes
Text
do NOT try to compile a rust program on a shitty risc-v computer, worst mistake of my life
1 note
·
View note
Text
being an indie streamer means answering hard questions like "i lost control and spent all monday reading about risc-v ISA; can i yap about that to chat or is it too technical for my audience?"
vexx: you should actually stream instead of merely theorizing about the best streams.
0 notes
Text
Un día como hoy (16 de noviembre) en la computación

El 16 de noviembre de 1947 nace David Andrew Patterson, pionero computacional estadunidense conocido por sus contribuciones el diseño del procesador RISC (y acuño el término), así como en el desarrollo del RAID #retrocomputingmx #davidpatterson #RISC_V #raid
0 notes
Text
Launching the Simics Simulator with RISC-V Platform

The amount of processor cores, active instruction set extensions, memory capacity, virtual disk size and content, Ethernet network address, and other configuration options can all be changed on hardware. The platform employs virtio devices for networking, drives, and entropy (instead of devices from some particular real-world RISC-V-based system-on-chip (SoC)) to simplify program support. Practically speaking, it feels and appears like a little embedded device, despite the fact that it may be configured with many gigabytes of disk and RAM.
Both Linux and bare-metal software can be executed on the platform. Buildroot is used to build the standard software stack for Linux. Creating a bootloader, Linux kernel, and bootable file-system image for the RISC-V virtual platform is a pretty simple task when you use Buildroot.
Connecting the Virtual Platform RISC-V
Enabling networking was a fairly intriguing use case throughout the platform’s development. It wasn’t difficult to get networking to function at the point where machines could “ping” one another. It required some effort to enable remote login from one computer to another.
Telnet would have been used to accomplish this in the past. There is minimal configuration required, and the protocol, client, and server are all straightforward. But the networking world isn’t what it used to be, and almost every Linux distribution demands that secure shell (SSH) be used for any form of remote login. It only takes a few lines of setup to add SSH to Buildroot, then rebuild.
SSH, however, is a more intricate creature. After adding SSH to the root filesystem, the target machine would not start up and would hang right before the login prompt appeared. The absence of unpredictability was the issue. SSH requires a source of randomness in order to produce a host key when it is first installed. The random pool was filling up very slowly since the Linux kernel could not find many sources of randomness to use on the very basic virtual platform. stopping the boot’s advancement. Nice example of “oh, I didn’t realize that might be an issue.”
Intel enhanced the target system by adding a “Virtio entropy” device. This gives the target system a high-bandwidth source of randomness. To assure simulation repeatability, it is implemented in the simulator using a deterministic pseudorandom system, even if it appears to the target system to be a hardware random-number generator (RNG). The variation is undetectable to the target software.
This is a straightforward simulated network architecture that makes use of several RISC-V virtual platforms, each with a unique hardware arrangement. It should be noted that the virtual network also has a “service node” that offers standard services like DHCP for system configuration and a dependable target for ping to check network connectivity.
SSH is being used by the “small” machine to connect to the “medium” machine. To display the memory size, the “medium” and “large” machines are both operating at the top. In order to show the simulation of a multicore target system, they are also running a few copies of the single-threaded coremark benchmark. A list of the simulated machines and every processor core in the active simulation is displayed by the Simics simulator command line.
The target machines differ in terms of clock frequencies, memory sizes, and core counts, as can be seen from the Simics command-line interaction in the terminal.
Because each RISC-V target is housed in a separate Simics simulator cell, the simulation can run three machines concurrently, which speeds up the simulation. Additionally, each machine has the option to activate parallel simulation, which might result in the creation of two + four plus eight, or 14-way parallelism in this instance. Workloads involving a lot of computation benefit greatly from this acceleration.
Using the Quick Start Platform for networking
Heterogeneous mixed-architecture simulations can be conducted since the Intel Simics Simulator Public Release includes the Intel Architecture-based Quick-Start Platform (QSP). Combining the two targets into a single network within a single Simics simulation operation is a basic example. similar to this
The service node’s Network Address Translation (NAT) feature allows any virtual network to be connected to the outside world. The screenshot below shows the host system (this time running Microsoft Windows for variety’s sake) logging into the RISC-V target system via inbound port forwarding with an SSH client. Additionally, two SSH connections are open due to an SSH login from the QSP target system to the RISC-V target system..
All that is required to set this up is a short amount of top-level scripting over the virtual platform scripts that are already in place. Initially, default parameter values that deviate from the targets’ standard values are set up using a YAML file. Keep in mind that the exact names of the parameters and the parameter hierarchy may vary because this is based on early drops of the targets.
Second, the YAML file calls a Simics simulator command-line script, which uses pre-existing setup scripts to produce the separate setup components in order to build the network and target systems.
Read more on Govindhtech.com
0 notes
Text
0 notes
Note
i want to preface this by saying i am generally against the idea of driving anything to extinction especially if its just because its "weird" or "scary" but i HAVE been wondering about something for a while: what are the ethics of eradicating parasites of humans? Like, specifically the ones adapted to human hosts such as a few of the tapeworm species out there. fuck it while im here i also know screwworm flies arent definitive parasites of humans in particular but do you have any opinions of the efforts to eradicate those either?
These are the kind of questions that teams of PhDs spend years of their lives and thousands of dollars of grant money answering. I don't have any formal education in this specific niche nor do I have the time or inclination to spend a week reading research papers. It would be irresponsible for me to answer this like an authority.
I would suggest either finding research papers or asking a blogger who knows more about parasites. @bogleech often has solid resources.
#hawk talks#asks#i appreciate the good faith question but i am Not the guy to ask here#none of the papers i have read went into human specific parasites and honestly its not a field that particularly interests me#cant you guys ever ask me about risc-v assembly or something#(joking. joking)
14 notes
·
View notes
Text
Most familiar with x86 AT&T syntax, but I respect, and represent, all assembly code.
7 notes
·
View notes
Text
RISC-V Tech Market Forecast to Reach USD 17.40 Billion by 2034 with CAGR of 29.2%
Report Overview The latest research report titled RISC-V Tech Market presents a comprehensive analysis of a rapidly growing industry. The report includes a detailed study of the market share, size, growth drivers, recent developments, and top trends. Besides, a thorough analysis of the product offerings, applications, advancements, benefits and scope has been covered. The study includes…
#RISC-V Tech Market#RISC-V Tech Market 2025#RISC-V Tech Market Share#RISC-V Tech Market Size#RISC-V Tech Market Trends
0 notes
Text
GlobalFoundries to Acquire MIPS, Bolstering Semiconductor IP Strategy
July 10, 2025 /SemiMedia/ — GlobalFoundries has announced its intent to acquire processor IP provider MIPS in a strategic move that highlights the current consolidation within the RISC‑V ecosystem. The agreement, pending regulatory approval, is expected to close in the second half of 2025. The acquisition strengthens GlobalFoundries’ portfolio of customizable IP cores and aligns with its…
#customizable IP cores#electronic components news#Electronic components supplier#Electronic parts supplier#GlobalFoundries MIPS deal#MIPS acquisition 2025#processor IP strategy#RISC V consolidation#Semiconductor industry news#semiconductor IP acquisition
0 notes
Text
#RISC-V#AI#Robotics#Automotive#Semiconductors#Innovation#Partnership#MIPS#Client#PowerSolutions#powerelectronics#powermanagement#powersemiconductor
0 notes
Text
ROCKY LINUX
1 note
·
View note
Text
Tecnologia RISC-V avança em adoção e maturidade no setor de semicondutores
A arquitetura RISC-V está rapidamente ampliando sua presença na indústria de semicondutores, estabelecendo-se como uma alternativa sólida frente às soluções proprietárias tradicionais, como Arm e x86. Baseada em um modelo de código aberto, essa tecnologia tem atraído um número crescente de fabricantes, startups e pesquisadores, graças à sua flexibilidade, eficiência energética e liberdade de…
#arquitetura aberta#computação embarcada#eficiência energética#inteligência artificial#internet das coisas#personalização de chips#semicondutores#tecnologia RISC-V
0 notes