#secure-web-based-scada
Explore tagged Tumblr posts
Text
Data Historian Market to Witness Strong Growth Backed by Digital Transformation Initiatives
Data Historian Market was worth USD 1.29 billion in 2023 and is predicted to be worth USD 2.26 billion by 2032, growing at a CAGR of 6.54% between 2024 and 2032.
Data Historian Market is evolving as industries increasingly rely on time-series databases to capture, store, and analyze large volumes of operational data. These systems play a pivotal role in sectors such as manufacturing, oil & gas, energy, and utilities by providing real-time visibility into process performance, predictive maintenance, and long-term trend analysis.
Data Historian Market continues to witness strong traction driven by the shift towards digital transformation and Industry 4.0 adoption. Businesses across the USA and Europe are leveraging these tools to ensure accurate data logging, seamless integration with SCADA and PLC systems, and faster decision-making based on historical trends.
Get Sample Copy of This Report: https://www.snsinsider.com/sample-request/3569
Market Keyplayers:
Amazon Web Services, Inc.
Google LLC
Duolingo, Inc.
Mojang Studios
Kahoot! ASA
Epic Games
Age of Learning, Inc.
Breakaway Games
Bublar Group
Frontier Developments
Playgen
Spin Master
Idnusgeeks
Gamelearn
Recurrence
Stratbeans
Tangible Play, Inc.
Simulearn
Raptivity
Banzai Labs
Cognitive Toybox
VR Education Holdings
Fundamental
Market Analysis
The market is experiencing substantial growth as organizations demand reliable systems to manage historical process data. Data historians offer the ability to store high-frequency data over long periods, allowing stakeholders to gain actionable insights for operational efficiency and compliance. The deployment of cloud-based historian solutions and the integration of AI and machine learning further enhance the usability of this technology across industries.
Market Trends
Rising adoption of cloud-native historian platforms
Integration with advanced analytics and AI for predictive insights
Increased demand in energy, oil & gas, and process manufacturing sectors
Focus on cybersecurity and secure data transmission
Enhanced mobile access and visualization features
Growing preference for edge-based historian solutions
Real-time data synchronization with enterprise applications
Market Scope
The Data Historian Market is expanding its footprint across critical industrial verticals, offering robust and scalable solutions to track and analyze plant data in real time. As industries prioritize operational intelligence, the scope of data historians is more vital than ever.
Seamless integration with legacy control systems
High-frequency data logging and storage optimization
Long-term historical data retention with minimal latency
Scalable solutions for plant-level to enterprise-wide deployment
Support for compliance reporting and audit trails
Centralized dashboards for visual analytics
Access Complete Report: https://www.snsinsider.com/checkout/3569
Forecast Outlook
The future of the Data Historian Market appears promising, fueled by the need for data-driven operational efficiency. As organizations in the USA and Europe continue to modernize their industrial ecosystems, demand for intelligent historian platforms will rise. Cloud-enabled infrastructure, enhanced data interoperability, and intelligent data modeling will define the next phase of market growth, offering smarter, more responsive systems for industrial users.
Conclusion
The Data Historian Market is no longer a niche domain—it's becoming central to modern industrial operations. With an increasing emphasis on automation, transparency, and performance optimization, businesses are turning to historian systems to turn raw data into strategic value. From smart factories in Germany to energy grids in the U.S., the role of data historians is expanding—making them a cornerstone in the journey toward intelligent industry transformation.
About Us:
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Related Reports:
U.S.A Learning Management System Market sees rising demand for remote learning solutions
Contact Us:
Jagney Dave - Vice President of Client Engagement
Phone: +1-315 636 4242 (US) | +44- 20 3290 5010 (UK)
Mail us: [email protected]
0 notes
Text
Unleashing Efficiency: The Rise of Industrial Automation Software Solutions
In the age of digital transformation, industrial sectors across the globe are undergoing a fundamental shift. One of the most significant developments driving this evolution is the rise of Industrial Automation Software Solutions. These intelligent systems are redefining how industries operate, streamline processes, and respond to real-time data — all while reducing human error and maximizing productivity.
Industrial automation is no longer just a competitive advantage; it’s quickly becoming a necessity for modern manufacturing, logistics, energy, and production-based businesses. At the core of this transformation lies powerful software designed to integrate machinery, manage workflows, and monitor operations with precision and efficiency.
One of the key strengths of Industrial Automation Software Solutions is their ability to centralize control over complex industrial processes. From programmable logic controllers (PLCs) to supervisory control and data acquisition (SCADA) systems, this software enables seamless communication between machines, sensors, and operators. The result is a smarter, more connected operation that can adapt quickly to changing demands.
Beyond basic automation, these solutions offer deep analytics capabilities. Using machine learning and AI, the software can detect patterns, predict equipment failures, and recommend proactive maintenance — ultimately helping businesses avoid costly downtime. This predictive approach not only increases reliability but also extends the lifespan of expensive equipment.
Flexibility is another crucial advantage. Most modern Industrial Automation Software Solutions are highly customizable and scalable, allowing companies to tailor systems to their unique needs and expand functionality as they grow. Whether an organization is automating a single production line or an entire facility, the right software can be scaled appropriately without significant disruptions.
In today’s globalized economy, remote access and cloud integration are more important than ever. Many automation platforms now offer web-based dashboards and mobile apps, giving managers and technicians the ability to monitor and control systems from virtually anywhere. This level of accessibility promotes faster response times and better decision-making, even across multiple locations.
Security, too, has become a top priority. As more industrial systems connect to the internet, they become more vulnerable to cyber threats. Industrial Automation Software Solutions are now being developed with robust cybersecurity features, including encrypted communication, multi-layered access control, and real-time threat monitoring.
These solutions also play a key role in sustainability efforts. By optimizing energy usage, reducing waste, and ensuring consistent product quality, industrial automation supports greener operations. Businesses not only improve efficiency but also meet environmental standards more effectively.
As industries continue to adopt smart technologies and prepare for Industry 4.0, the demand for reliable and intelligent automation software is set to grow exponentially. Investing in Industrial Automation Software Solutions is no longer just about keeping up with competitors — it's about laying the foundation for a resilient, future-ready operation.
Whether it's enhancing productivity, improving safety, or driving innovation, automation software is reshaping what’s possible in the industrial world. The future of manufacturing and production isn’t just automated — it’s intelligent, adaptive, and incredibly powerful.

#Traceability Software Great Lakes Region#Machine Vision Integration Great Lakes#Great Lakes Industrial Marking Solutions#Factory Monitoring Software Great Lakes Region#Lean Manufacturing Solutions Great Lakes#Automated Data Collection Systems Great Lakes#Industrial Traceability Solutions Detroit#Machine Vision Systems Detroit#Detroit Barcode Verification Services#Laser Marking Services Detroit MI#Production Management Software Detroit#Detroit Manufacturing Systems#product traceability software Detroit#industrial marking systems Detroit#Laser Marking Services Auburn Hills#Industrial Traceability Solutions Michigan#Barcode Verification Systems Auburn Hills#Machine Vision Systems Michigan#Auburn Hills Laser Part Marking#Industrial Marking Solutions Michigan#Traceability Software Auburn Hills#Turnkey Laser Systems Michigan#Auburn Hills Barcode Reader Solutions#Advanced Laser Marking Auburn Hills MI#laser marking systems#laser marking machine#laser part marking#uv laser marking machine#uv laser marking#dot peen marking machine
0 notes
Text
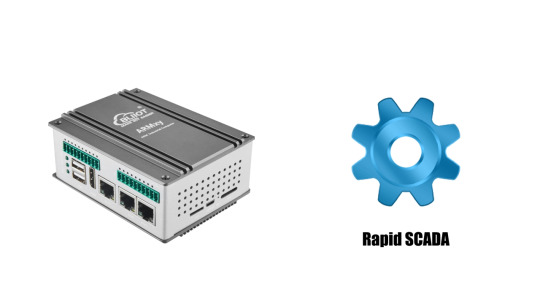
ARMxy Ubuntu Gateway BL370 and Rapid SCADA for Diesel Generator Monitoring System
Case Details
Combining the ARMxy series Ubuntu Gateway BL370 and Rapid SCADA to implement a diesel generator monitoring system is a great choice. This combination offers an efficient, flexible, and scalable monitoring solution. Below are some possible technical solutions and architectural designs:
1. Hardware Platform (ARM Ubuntu Gateway)
The ARM Ubuntu Gateway BL370 running Ubuntu provides powerful computing capabilities and stable support, allowing it to receive sensor data from the diesel generator and perform real-time processing. You can interface with the generator hardware in the following ways:
Digital and Analog Inputs: Connect the sensors of the diesel generator (e.g., temperature, pressure, voltage, current, etc.) through the gateway, often using the MODBUS RTU or TCP protocol to communicate with the SCADA system.
Remote Data Acquisition: The gateway can connect to the remote SCADA system via wireless (Wi-Fi/4G/5G) or wired networks (Ethernet), enabling data transmission and remote control.
2. SCADA System (Rapid SCADA)
Rapid SCADA is an open-source industrial automation platform that works well for monitoring generator operations. It supports a wide range of communication protocols (e.g., Modbus, OPC, SNMP) and integrates smoothly with ARM Ubuntu Gateway BL370.
Main features:
Real-time Monitoring: Display critical parameters like generator status, load, fuel consumption, temperature, pressure, etc.
Data Storage and Historical Queries: Rapid SCADA stores real-time data and allows querying and analysis through a database (like MySQL), generating reports.
Alarming and Event Management: When monitored data exceeds preset thresholds, the system can automatically trigger alarms and log events for troubleshooting and maintenance.
Remote Control: Users can remotely control the generator’s start/stop operations and adjust the load through the SCADA system.
3. System Architecture Example
Sensors and Controllers: Install various sensors (e.g., temperature, pressure, oil level) on the diesel generator, transmitting data to the ARM Ubuntu Gateway BL370 via Modbus RTU/TCP protocol.
Gateway Device (BL370): This gateway runs Ubuntu OS and handles receiving sensor data from the generator and transmitting it to the SCADA system over the network.
SCADA Server: Rapid SCADA runs on a server, processing and displaying data from the gateway, generating real-time data views, alarms, and reports.
User Interface: Users can access the SCADA system through a web interface or desktop client to view the generator's status, historical data, and alarm information.
4. Data Transmission and Protocols
Modbus Protocol: In industrial environments, Modbus is a commonly used protocol for communication between the diesel generator and the SCADA system. Modbus TCP or Modbus RTU can be used, depending on the system design and needs.
MQTT Protocol: For remote communication, MQTT can be used to transmit sensor data, especially when using 4G or wireless networks.
HTTP/HTTPS API: If Rapid SCADA supports it, the gateway can send data to the SCADA system via HTTP or HTTPS APIs.
5. Data Analysis and Prediction
Using historical data accumulated by the SCADA system, deeper data analysis can be conducted. For example, algorithms can predict maintenance needs for the diesel generator or optimize its workload based on performance data, thus reducing downtime.
6. Security Considerations
Data Encryption: To protect data security during communication, it’s recommended to use TLS/SSL encryption protocols.
User Authentication and Access Control: Set proper permissions and roles within the SCADA system to ensure that only authorized users can operate critical equipment.
Summary
Using an ARMxy Ubuntu Gateway BL370 in conjunction with Rapid SCADA to set up generator monitoring system is a flexible and efficient solution. The ARM gateway provides reliable data acquisition and processing capabilities, while Rapid SCADA offers powerful data visualization, alarming, and historical data storage features. Together, they can significantly enhance the monitoring, management, and maintenance of the diesel generator.
0 notes
Text
Remote Monitoring with PLC Panels: Managing Your Plant from Anywhere

Introduction
In today’s fast-moving industrial world, being physically present on the shop floor every hour of the day is neither practical nor necessary. Thanks to modern PLC Panels, plant managers and engineers can now monitor and control their operations from virtually anywhere.
This is where remote monitoring comes in—a game-changing feature that turns your PLC Panel into a smart control center for your entire plant.
What is Remote Monitoring in PLC Panels?
Remote monitoring allows real-time access to your PLC Panel’s data through cloud-based platforms or networked software systems. It enables you to:
View machine status live
Monitor performance metrics
Receive alerts and diagnostics
Control start/stop operations remotely
Whether you’re at another site, at home, or travelling, you can manage your plant operations with just a laptop or smartphone.
Benefits of Remote Monitoring with PLC Panels
Real-Time Oversight Instantly check the status of equipment and production without being on-site.
Faster Problem Resolution Receive immediate alerts for faults, so downtime can be minimized.
Cost Savings Reduce the need for constant physical supervision and travel between sites.
Improved Decision-Making Access to live data helps you make informed decisions quickly.
Enhanced Safety Monitor high-risk processes remotely, minimizing exposure for workers.
Ready to take control from anywhere? Partner with a reliable PLC Panel Manufacturer to implement secure, remote-ready automation systems.
Key Features to Look For in Remote-Ready PLC Panels
Ethernet and Wi-Fi Connectivity Enables seamless data transfer between your PLC and remote devices.
Cloud Integration Support Compatible with platforms like MQTT, OPC UA, or custom dashboards.
Secure Access Protocols SSL encryption, VPN access, and password protection keep your system safe.
User-Friendly Interfaces Easy-to-use mobile or web apps that show real-time visualizations.
SCADA or HMI Compatibility Gives a centralized view with alarms, trends, and historical data logs.
Industries That Benefit the Most
Water Treatment Plants – Monitor pumps, levels, and chemical dosing remotely
Renewable Energy Farms – Supervise solar or wind operations from central control
Cold Storage Units – Keep track of temperature and humidity offsite
Manufacturing Units – Detect faults or delays without halting production
Agricultural Automation – Manage irrigation or feeding schedules remotely
How to Get Started
Collaborate with an experienced Programmable Logic Controller Panel Manufacturer who can:
Customize the panel with remote access modules
Integrate your system with cloud services
Train your team to monitor and control remotely
Ensure top-level cybersecurity protocols are in place
Conclusion
Remote monitoring with PLC Panels is no longer a luxury—it’s a necessity in a digital-first industrial world. It saves time, boosts productivity, and enhances control like never before. To enable this, choose a PLC Panel Manufacturer that delivers smart, secure, and remote-ready solutions tailored to your industry.
Control your plant from anywhere—talk to a trusted PLC Panel Manufacturer and upgrade your operations today.
Also read:
PLC Panels vs. SCADA Systems: Understanding Their Roles and Differences
Why PLC Panels Are a Must-Have for Small and Medium Enterprises (SMEs)
Retrofitting Old Machinery with Modern PLC Panels
Using PLC Panels in HVAC Automation for Commercial Buildings
#plc electrical panel#plc#electrical panel#plc panel#Programmable Logic Controller Panel Manufacturer#PLC Panel Manufacturer
0 notes
Text
This image gives a solid, compact breakdown of what a Next Generation Firewall (NGF) actually does. It’s way more than just blocking ports like the old-school firewalls. These bad boys are the Swiss Army knife of cybersecurity—combining multiple tools into one powerhouse of a system. Here’s a detailed look at each feature shown:
⸻
Core Capabilities of a Next Generation Firewall (NGF):
1. Antivirus
Blocks known malware and viruses at the perimeter.
2. Intrusion Prevention System (IPS)
Detects and prevents malicious traffic using signatures and behavior analysis.
3. Mobile Security
Extends firewall protection to mobile users and endpoints.
4. Threat Intelligence Service
Feeds live data about current threats into the NGF for real-time defense.
5. Antispam
Blocks phishing and spam-based attacks, especially in emails.
6. Vulnerability Management
Identifies and manages security flaws in systems or software.
7. Virus Outbreak Protection Service
Early detection of new virus variants through heuristic analysis and sandboxing.
8. IP Reputation
Blocks or flags traffic from known malicious IPs.
9. Content Disarm & Reconstruction (CDR)
Strips potentially dangerous content from documents and reconstructs safe versions.
10. Industrial Security
Secures SCADA/ICS systems often used in factories and utilities.
11. Cloud Access Security Broker (CASB)
Monitors cloud service use and enforces security policies for SaaS apps.
12. Application Control
Manages and restricts access to applications by user, group, or device.
13. Web Filtering
Blocks access to malicious or inappropriate websites.
14. Security Rating Service
Gives your network or firewall a security score based on current configurations and threats.
15. Web Security
Protects against threats from web browsing like drive-by downloads and malicious scripts.
16. Indicators of Compromise (IoC)
Detects subtle signs that a system may be compromised.
⸻
Why This Matters:
Next-Gen Firewalls don’t just filter traffic—they analyze behavior, apply AI-based detection, and adapt in real-time. Whether you’re working in cybersecurity, IT management, or penetration testing, understanding NGF features helps you:
• Design layered defenses
• Troubleshoot with more context
• Detect threats earlier
• Improve security posture assessments
⸻
Want to go deeper into how NGFs are implemented or maybe compare top vendors like Fortinet, Palo Alto, or Cisco Firepower
0 notes
Text
Explore the World of IPCS
IPCS Global began its journey in 2008 as an Automation Service provider, born from a vision to empower individuals and organizations with cutting-edge technological solutions. Over the years, we have evolved and expanded beyond our loftiest expectations, driven by a single goal: to bridge the gap between technical skills and industry requirements. With growth came larger dreams, and today, IPCS stands as a beacon for job aspirants and recruiters seeking a reliable and comprehensive technological solution.
What truly sets IPCS apart from the rest? The answer lies in one word: Improvisation. This simple yet powerful principle is deeply embedded in our DNA. At IPCS, we understand that staying relevant in a rapidly changing world demands constant evolution. Whether it’s technical training, sales strategies, team management, or student support, we ensure that every aspect of our organization keeps pace with the latest advancements.
OUR COURSES
SEO | SEM | SMM | SMO AFFILIATE SECURITY SYSTEMS | FIRE
MARKETING ALARM | ACCESS CONTROL
SYSTEM
PYTHON | DATA SCIENCE | PLC | SCADA | DCS | CONTROL
ANDROID APP DEVELOPMENT PANEL DESIGN
COURSES DETAILS
SEO (Search Engine Optimization):
Improves website visibility in organic search results.
Focuses on on-page, off-page, and technical optimizations.
SEM (Search Engine Marketing):
Uses paid advertising like Google Ads to drive traffic.
Targets specific keywords for immediate visibility.
SMM (Social Media Marketing):
Promotes products/services on social platforms (Facebook, Instagram, LinkedIn).
Combines organic posts and paid ads for engagement and conversions.
SMO (Social Media Optimization):
Enhances social media profiles and content for better visibility.
Focuses on hashtags, profile optimization, and consistent posting.
Affiliate Marketing:
Performance-based model where affiliates promote products for a commission.
Increases brand reach and sales through partner referrals.
Key Benefits:
Boosts brand visibility and engagement.
Drives targeted traffic and conversions.
Offers measurable ROI and analytics.
Perfect for businesses looking to grow their online presence!
BMS (Building Management System):
Definition: A centralized system that monitors, controls, and manages a building's mechanical, electrical, and environmental systems.
Key Functions:
HVAC (Heating, Ventilation, and Air Conditioning) control.
Lighting and energy management.
Fire safety and alarm systems integration.
Security system management.
Benefits:
Increases energy efficiency.
Enhances building safety and comfort.
Reduces operational costs.
CCTV (Closed-Circuit Television):
Definition: A video surveillance system used for monitoring and recording activities in a specific area.
Key Features:
Live video monitoring.
High-definition recording.
Night vision and motion detection.
Remote access via mobile or computer.
Applications:
Security and crime prevention.
Traffic monitoring.
Employee and workplace monitoring.
Benefits:
Deters unauthorized activities.
Provides evidence in case of incidents.
Ensures safety and surveillance in real-time.
PYTHON & DATA SCIENCE
Python
Definition: A versatile, high-level programming language widely used for various applications like web development, automation, data analysis, and machine learning.
Key Features:
It is easy to understand and use due to its simple syntax.
extensive libraries like as TensorFlow, Matplotlib, Pandas, and NumPy..
Supports multiple paradigms (object-oriented, functional, etc.).
Open-source with a strong developer community.
Applications:
Web and app development.
Data analysis and visualization.
Machine learning and AI.
Data Science
Definition: A multidisciplinary field that uses statistical methods, algorithms, and technology to analyze and interpret complex data.
Key Components:
Data Collection: Gathering data from various sources.
Data Cleaning: Preparing data by removing inaccuracies.
Data Analysis: Identifying patterns and trends.
Machine Learning: Building predictive models.
Data Visualization: Representing data through graphs and dashboards.
Tools and Technologies: Python, R, SQL, Tableau, Hadoop.
Applications:
Business intelligence.
Predictive analytics in healthcare, finance, and marketing.
Fraud detection and risk management.
Let me know if you'd like further details!
Industrial Automation
Definition:using robots, PLCs (Programmable Logic Controllers), computers, and other control technologies to manage industrial machinery and processes with little assistance from humans.
Key Features:
Process Automation: Streamlining repetitive tasks and manufacturing processes.
Robotics: Using robots for precision, efficiency, and safety.
Actuators and sensors: keeping an eye on and managing industrial settings.
SCADA Systems: Supervisory Control and Data Acquisition for real-time monitoring and control.
IoT Integration: Enabling connected devices for smarter decision-making.
Benefits:
Increases productivity and efficiency.
Reduces operational costs and human error.
Enhances quality and precision in production.
Improves workplace safety.
If you want a photograph or further information, let me know!
Comprehensive Placement Assistance
One of the standout features of IPCS is our commitment to placement assistance. We understand that completing a training program is only the first step; the ultimate goal is securing a rewarding career. That’s why we go the extra mile to connect our students with top employers across various industries.
Our placement team works tirelessly to build relationships with recruiters, understanding their needs and matching them with the right candidates. From resume building and interview preparation to job placement, we provide end-to-end support to ensure our students succeed. Many of our alumni have gone on to build successful careers in reputed organizations, a testament to the effectiveness of our training and placement services.
Your Journey Starts Here
IPCS Global is more than just a training institute; it’s a partner in your journey to success. Whether you’re a job aspirant looking to enhance your skills, a professional seeking career growth, or a company aiming to upskill your team, we are here to support you every step of the way.
With IPCS, you are not just enrolling in a training program; you are joining a community dedicated to excellence and innovation. Take the first step today and discover how IPCS can transform your future.
We are thrilled to welcome you to the IPCS community. Together, let's create a world where dreams are realized.
See you soon!
Conclusion for IPCS
IPCS Global stands as a trusted leader in providing innovative technological solutions and industry-focused training. From empowering job aspirants with cutting-edge skills to supporting businesses in upskilling their teams, IPCS is committed to bridging the gap between talent and opportunity. With a strong foundation built on improvisation, practical training, and expert guidance, IPCS ensures that every student and partner achieves their fullest potential.
Whether you aim to transform your career, improve your company’s capabilities, or embrace the latest in technology, IPCS is your ultimate destination. With real-time projects, industry-leading trainers, and top-notch placement assistance, IPCS is dedicated to shaping a brighter and more skilled future for everyone.
Join IPCS today—your journey to excellence starts here!
0 notes
Text
Astronomers Reveal TRAPPIST-1 Planetary System is Older Than Ou smart grid sensor r Solar System
www.inhandnetworks.com
This illustration shows what the TRAPPIST-1 system might look like from a vantage point near planet TRAPPIST-1f (at right). Credits: NASA/JPL-Caltech
Scientists now have a good estimate for the age of the TRAPPIST-1 system, revealing that it is up to twice as old as our own solar system that formed some 4.5 billion years ago.
If we want to know more about whether life could survive on a planet outside our solar system, it’s important to know the age of its star. Young stars have frequent releases of high-energy radiation called flares that can zap their planets’ surfaces. If the planets are newly formed, their orbits may also be unstable. On the other hand, planets orbiting older stars have survived the spate of youthful flares, but have also been exposed to the ravages of stellar radiation for a longer period of time.
Scientists now have a good estimate for the age of one of the most intriguing planetary systems discovered to date — TRAPPIST-1, a system of seven Earth-size industrial cellular modem3g modem worlds orbiting an ultra-cool dwarf star about 40 light-years away. Researchers say in a new study that the TRAPPIST-1 star is quite old: between 5.4 and 9.8 billion years. This is up UMTS router to twice as old as our own solar system, which formed some 4.5 billion years ago.
The seven wonders of TRAPPIST-1 were revealed earlier this year in a NASA news conference, using a combination of results from the Transiting Planets and Planetesimals Small Telescope (TRAPPIST) in Chile, NASA’s Spitze Industrial VPN router r Space Telescope, and other ground-based telescopes. Three of the TRAPPIST-1 planets reside in the star’s “habitable zone,” the orbital distance where a rocky planet with an atmosphere could have liquid water on its surface. All seven planets are likely tidally locked to their star, each with a perpetual dayside and nightside.
At the time of its discovery, scientists believed the TRAPPIST-1 system had to be at least 500 million years old, since it takes stars of TRAPPIST-1’s low mass (roughly 8 percent that of the Sun) roughly that long to contract to its minimum size, just a bit larger than the planet Jupiter. However, even this lower age limit was uncertain; in theory, the star could be almost as old as the universe itself. Are the orbits of this compact system of planets stable? Might life have enough time to evolve on any of these worlds?
“Our results really help constrain the evolution of the TRAPPIST-1 system, because the system has to have persisted for billions of years. This means the planets had to evolve together, otherwise the system would have fallen apart long ago,” said Adam Burgasser, an astronomer at the University of California, San Diego, and the paper’s first author. Burgasser teamed up with Eric Mamajek, deputy program scientist for NASA’s Exoplanet Exploration Program based at NASA’s Jet Propulsion Laboratory, Pasadena, California, to calculate TRAPPIST-1’s age. Their results will be published in The Astrophysical Journal.
It is unclear what this older age means for the planets’ habitability. On the one hand, older stars flare less than younger stars, and Burgasser and Mamajek confirmed that TRAPPIST-1 is relatively quiet compared to other ultra-cool dwarf stars. On the other hand, since the planets are so close to the star, they have soaked up billions of years of high-energy radiation, which could have boiled off atmospheres and large amounts of water. In fact, the equivalent of an Earth ocean may have evaporated from each TRAPPIST-1 planet except for the two most distant from the host star: planets g and h. In our own solar system, Mars is an example of a planet that likely had liquid water on its surface in the past, but lost most of its water and atmosphere to the Sun’s high-energy radiation over billions of years.
However, old age does not necessarily mean that a planet’s atmosphere has been eroded. Given that the TRAPPIST-1 planets have lower densities than Earth, it is possible that large reservoirs of volatile molecules such as water could produce thick atmospheres that would shield the planetary surfaces from harmful radiation. A thick atmosphere could also help redistribute heat to the dark sides of these tidally locked planets, increasing habitable real estate. But this could also backfire in a “runaway greenhouse” process, in which the atmosphere becomes so thick the planet surface overheats – as on Venus.
“If there is life on these planets, I would speculate that it has to be hardy life, because it has to be able to survive some potentially dire scenarios for billions of years,” Burgasser said.
Fortunately, low-mass stars like TRAPPIST-1 have temperatures and brightnesses that remain relatively constant over trillions of years, punctuated by occasional magnetic flaring events. The lifetimes of tiny stars like TRAPPIST-1 are predicted to be much, much longer than the 13.7 billion-year age of the universe (the Sun, by comparison, has an expected lifetime of about 10 billion years).
“Stars much more massive than the Sun consume their fuel quickly, brightening over millions of years and exploding as supernovae,” Mamajek said. “But TRAPPIST-1 is like a slow-burning candle that will shine for about 900 times longer than the current age of the universe.”
Some of the clues Burgasser and Mamajek used to measure the age of TRAPPIST-1 included how fast the star is moving in its orbit around the Milky Way (speedier stars tend to be older), its atmosphere’s chemical composition, and how many flares TRAPPIST-1 had during observational periods. These variables all pointed to a star that is substantially older than our Sun.
Future observations with NASA’s Hubble Space Telescope and upcoming James Webb Space Telescope may reveal whether these planets have atmospheres, and whether such atmospheres are like Earth’s.
“These new results provide useful context for future observations of the TRAPPIST-1 planets, which could give us great insight into how planetary atmospheres form and evolve, and persist or not,” said Tiffany Kataria, exoplanet scientist at JPL, who was not involved in the study.
Future observations with Spitzer could help scientists sharpen their estimates of the TRAPPIST-1 planets’ densities, which would inform their understanding of their compositions.
PDF Copy of the Study: On the Age of the TRAPPIST-1 System
Tags: cellular modem ethernet, 4g LTE router, 3g wireless router, 4g LTE router with SIM card, cellular router vendor, verizon 4g LTE router, best industrial wifi router, 4g modem router, 4g modem router wifi, att 4g router, cellular router wifi, industrial multi sim cellular router, m2m cellular router, verizon industrial router, 4g lte gateway, 4g lte modem, industrial cellular vpn router, industrial 3g m2m, industrial l2tp cellular router, industrial ethernet router, plc router, 12vdc lte router, 4g lte router dual SIM, multi SIM LTE router, cellular router manufacturer, edge gateway, industrial iot gateway, overhead line sensor, distribution line sensor, distribution line fault detection, medium voltage smart grid sensor, MV smart grid sensor, smart grid sensor, power line sensor, power sensor, MV sensor, Grid Fault Detection, Line Monitoring, Grid Analytics, Predictive Grid Analytics, Grid Monitoring, Grid Analytics System, Power Fault Detection, Advanced Grid Analytics, Intelligent Line Monitoring, distribution fault detection, smart vending machine, smart vending solutions, QR code vending machine, telemetry vending machine, intelligent vending machine, touch screen for vending machine, vending software, cashless vending, coupon vending machine, iot vending machine, vending machine card reader, POS vending machine, smart vending machine software, credit card vending machine, Industrial router, cellular router, 4g router, LTE router, 3g router, M2M router, wireless router, wireless m2m router, wireless m2m, Industrial Wireless M2M, Industrial Wireless M2M Router, Industrial Wireless M2M products, M2M wireless producdts, WiFi M2M Router, Industrial Wireless M2M gateway, industrial IoT router, industrial IoT gateway, industrial LTE router, Industrial router, cellular router, 4g router , LTE router, 3g router , M2M router, wireless router, wireless m2m router, WiFi M2M Router, Industrial Wireless M2M Router, M2M IoT router, industrial wireless router, industrial M2M router, industrial LTE router, Industrial VPN router, Dual SIM M2M router, M2M gateway, IoT gateway, Industrial router, low cost industrial router , low cost cellular router, low-cost LTE router, low-cost M2M router, compact industrial router, low-cost cellular router , cellular router, low-cost 4g router , LTE router, 3g router , M2M router, wireless router, wireless m2m router, WiFi M2M Router, Industrial Wireless M2M Router, M2M IoT router, industrial wireless router, industrial M2M router, industrial LTE router, Industrial VPN router, Dual SIM M2M router, M2M gateway, IoT gateway, LTE Cat 1 router, Embedded LTE Cat 1 router, Industrial LTE Cat 1 router, Verizon Embedded modem, Verizon Embedded router, Overhead Line Monitoring, Distribution Power Line Monitoring, Fault detection & location, Grid Analytics System, Remote Machine Monitoring & Maintenance System, IoT Remote Monitoring, Prognostics and Health Management, Remote connectivity, Remote Maintenance, Smart Vending, smart vending, InHandGo, retrofit, touchscreen vending, cashless vending, cloud VMS, Transformer Monitoring, Transformer Monitoring, substation monitoring, grid LTE router, wireless communication, smart grid, Remote Automation, Remote Automation, Secure remote networks, web SCADA, Remote Diagnostics, Remote PLC programming, Intelligent Traffic Enforcement, Intelligent Traffic Enforcement,
#Secure remote networks#m2m wireless#wireless m2m#DIN-Rail router#wireless-m2m#intelligent traffic enforcement#remote-secure-networking#secure-web-based-scada#smart vending solutions
0 notes
Text
Top 10 Project Management Tools.
Top 10 Project Management Tools.
Small-scale project is pretty simple to manage but, becoming challenge in large projects handling resources, now this is where project management tools come in to the rescue.
So, project managers preferring project management tools worldwide.
Project ------> Project Management --------> Project Management tools
Project management ensures a smooth flow of development of these projects starting from its conception till its delivery. It is a practice of initiating, planning, executing, monitoring & controlling and closing the work of a team to achieve specific goals and meet specific success criteria at the specified time for easy and systematic project management.
Tools act as an aid to an individual as well as a team.
Now we listing out some of top 10 project management tools.
Those are give below,
MS Project
Its portfolio management tool, provided by Microsoft. It provides cloud-based and on-premise options & it also provides the integrated planning tools, which helps in organizing and keeping tab of projects including daily tasks and overall directions to this tool is comprised of three main modules.
l The project management module.
l Portfolio management.
l Resource management.
SCORO
It can manage your entire company in one place. It unifies your disparate systems and countless spreadsheets into one single tool. It is basically a software as a service solution for professionals and creative services. Few of its intriguing features include collaboration of productivity project management and Sales force automation as well as CRM SCADA works exceptionally well with a small or medium-sized teams.
Freed Camp
Freed camp is a web-based project management tool. An organization system that can be used by a single or multiple users. Those who are all collaborating by using cloud computing, it’s an ideal tool for these people and businesses who want to stay in control of their projects resources budget and
time it provides various exceptional features like signing tasks to team members, scheduling events via calendar, discussion boards on time tracking and lot moreover free Camp. And also its helps you in improving your work flow determining your, targets and achieving your goals within the specified time.
Podio
Podio is a cloud-based collaboration service which is powered by Citrix. This is the social collaboration tool where one can build applications and set up work spaces to support the preferred work flow and become more effective. It is a perfect tool for enhancing the collaboration as it lets you connect with colleagues via internal social network and chap few are the features of podio include granular access personal dashboards connected with CRM data visualization. And this is third-party app integration and full customization of your whole tool bar.
Zoho.
Zoho is a free online project management software & competitive project management tool in the market. That lets you make you as prisoners projects, this more productive and finish them within a given time frame using Zoho. you can get in-depth insight with charts and reports while collaborating with your team clients vendors or consultants seamlessly. Its basically divides your large and complex projects in a small manageable units and then schedules the recurring tasks dependencies and sub tasks according to the deadlines features like gand charts, bug trackers chat reports talks and time sheets etc.
Basecamp.
Basecamp is a real-time communication tool which helps in teams, so that to stay on the same page and its less for traditional project management tasks. And its having more reliable service that offers simple setup and short learning time along with the to-do lists, calendaring due dates and file sharing
Functions and keep tracking of priorities with actionable items. Which becomes much easier. It is an innovative solution which you can use as a document and file manager.
Jira
It is most popularly used for bug tracking and issue tracking, developed by Acylation. Name JIRA is derived from the Japanese word Gojira which means Godzilla using JIRA. It can be easily plan track and manage your agile software development projects by customizing your work flow and team
Collaboration. It provides special features for each all software development which helps the team to stay focused on delivering iterative and incremental value as fast as possible with customize scrum boards.
Trello
Trello is a web based project management application developed by fog Creek software and is currently owned by Attrition. Trello provides the visual way for teams to collaborate on any project it is incredibly flexible and easy to use and keep track of each and every detail by the big picture or a minor detail using Kanban style management. It keep your data secure and private as it use as SSL or HTTPS connections in few astonishing features. This is quick overview on front and back of cards, easy organization with tags, labels, drag and drop functionality check lists with progress meters, easy uploading of files in attachment data's, filtering etc.
Asana
Asana is a web and mobile project management application, designed to help team track. it's simple, powerful enough to run your entire business. It provides plenty of features that can help your organization in track, work in a way that fits in every teams. Work flow by providing transparency and
clarity to team mates. Asana addresses a fundamental problem for allowing team members to know exactly what is going on by easily providing information about who is doing what by when and how users are able to focus on their missions and excel at their work it is a great tool for effortless of project tasks. Features like activity feeds adding assigners attachments adding tasks automatic updates to email boxes, customs, calendars, views email bridges etc.
Wrike
Its a powerful online project management software, which provides full visibility and control over project tasks. It’s an award-winning software for online project management. It helps in improving speed and efficiency of work in both co-located and in distributed groups.This Reich allows you to schedule prioritize discuss and keep track of both work and progress in a real-time environment and also it provides interactive, user-friendly navigation, excellent security measures and even mobile apps using which you can easily track and monitor your progress from your mobile phones anytime and anywhere. It is trusted application that is used by over 15,000 organizations including small midsize and Enterprise
If you want know the price of that management tools click here,
Other than those tools, you can share your list of tools with us, as well by putting them down in the comment section below. We hope, you like this article.
Be kind enough to like it and you can comment any of your doubts and queries and we will reply them at the earliest do look out in comment in our article list and also you contact us in http://www.infocareerindia.com/.
1 note
·
View note
Text
Social Engineering Attacks | Cyber Intelligence
What is Cyber Intelligence?

Collecting information from electronic media Collecting information from OsInt engines/vehicles Analyzing/using the collected information
Monitoring and analyzing digital security threats and in the light of the information obtained after this analysis, against it is the initiation of the putting process. The Importance of Cyber Intelligence
States' Fear of Cyber Terrorism Decryption of Commercial Company Information (Financial information, competitor, etc.) personal information Hacker Privacy
Today, as a result of the point where technology has come to cyber intelligence it is also given quite a lot of importance. Countries and institutions, information systems of competitors to establish superiority over each other conducting counterattacks, disabling their cyber systems it is aimed at causing economic damage. Apart from that, cyber the data stored in space has been captured and thus future plans, technologies used and a number of other secrets information has been obtained.
As a result of a cyber attack, all the electricity of a country it is possible to interrupt their services at once. SCADA systems with the attacks to be carried out, the target country will be targeted not only economically, but also even physical attacks can be carried out. It could last for days as a result of an attack, the systems of all banks and financial institutions of the country can be destroyed, it can be rendered incapable of service. Now it's time to fight the tank with a rifle it is stated by various experts that it is closing, wars will take place in the cyber environment. U.S. officials said in a statement that any cyber attack against them, he stated that it would be the cause of conventional war.
This official statement by the United States emphasizes the importance of cybersecurity and cyber intelligence elements. Cyber intelligence, also defined as HACKINT, can be on hacking, as we have already stated it can also be obtained by using social media and various Internet publications. Except that in the last period, especially in the Middle Eastern countries such as Syria and Iran, which are often used, cyber axe operations are also material and moral it can cause havoc.
Setting Goals
State institution Personnel at the Institution (Social Engineering) Software / Product (Software theft) Data (data theft) Prestige (Intelligence organizations) Banks / E-commerce Systems Personal Data (Image, Video, privacy, blackmail) Social Media Hesas (Curiosity, ambition, etc.) Mail (Receiving information, curiosity, etc.)
OsInt Open Source Intelligence Public Data OsInt was first defined by the US Department of Defense in 2005
Information Gathering Techniques & Tools
Privacy
Bitcoin * Fake Name Generator Tor Browser Bundle * Ghostery Cryptocat * HTTPS Everywhere DoNotTrackMe * Hushmail alternative Enigmail * Burn Note Decommissioning of Search Engines
Google Dorks * Duck Duck Go Baidu * PunkSpider binsearch.info * Google Bing * Shodan Searchenginecolossus
Google Hacking
The technique that hacker groups use primarily Fast and multiple results Specific results with advanced operators Passwords, user IDs, pdfs, important files, sensitive data, ip December Dropbox important db dumping with single dork, excel, pdf, xls scans for the target.
Pastebin


Twitter Pastebin

Open source


Other Resources

Shodan

SHODAN uses various computer-based systems (desktop, switch, router, servers, etc.) using filters.) is a search engine that allows Deciphering.Although it is a search engine, it is very different from search engines such as google, yahoo or Bing.

Search engines such as google, yahoo, can produce excellent results for you according to the phrase you are searching for, but they do not answer the following questions; Do we want to find web servers running Apache ? Or do we want to find out which is the most popular Microsoft IIS server? There are a lot of anonymous FTP servers, I want to see ? Or a new vulnerability has appeared, which IP addresses can I infect this vulnerability by region/country? Which backbones have cisco routers?
0 notes
Text
Download zend studio 9.0.3

DOWNLOAD ZEND STUDIO 9.0.3 PDF
DOWNLOAD ZEND STUDIO 9.0.3 INSTALL
Trojan/Backdoor - JS.Scob.Trojan/Download. Trojan/Backdoor - MyDOOM/NoVarg Detection Trojan/Backdoor - W32/Bagle Virus Detection PVS PLUGIN FAMILIES COUNT FAMILY NAME 100 For more information regarding PVS, please visit: This information includes a brief description, plugin ID, CVE cross-reference, Bugtraq ID cross-reference, Nessus cross-reference, and several other descriptive entries.
DOWNLOAD ZEND STUDIO 9.0.3 PDF
Finally, the PDF details specific information for each of the different plugin modules.
DOWNLOAD ZEND STUDIO 9.0.3 INSTALL
Initially, you have this introduction followed by an overview of plugin count for each plugin family. This article is now available in our new knowledge base: Download and install Zend Server for IBM i Issue This article provides some basic tips to help you find, download, and install Zend Server. This PDF is organized into several sections. This PDF is automatically generated as new plugins are made available for download from the Tenable Network Security Corporate Web Server. Passively determining the type of operating system of each active host.Detecting which ports are served and which ports are browsed for each individual system.Tracking exactly which systems communicate with other internal systems.Highlighting all interactive and encrypted network sessions.Detecting when an internal system begins to port scan other systems.Detecting when new hosts are added to the network.Detecting when an application is compromised or subverted.Keeping track of all client and server application vulnerabilities.There is a branded version of Eclipse called Zend Studio but it is pretty expensive. A single PVS sensor can be placed in front of a network of 25,000 systems and continuously monitor the traffic for a variety of security related information including: As i have download the Eclipse PHP Development Tools (PDT) but its a separate eclipse studio only, but i want to use it from my already installed eclipse. As PVS monitors your network, it also watches for potential application compromises, trust relationships, and open or browsed network protocols. The PVS vulnerability monitor can find out what is happening on your network without actively scanning it. Do you know what happens between the last time a vulnerability scan is completed and the next time a scan is completed? New hosts, new ports, new services, and new vulnerabilities can arrive on your networks faster than you may be allowed to scan for them. Introduction PVS is a passive vulnerability scanner. Table of Contents Family Web Clients.158 Family Web Servers.216 Family Abuse.290 Family Policy.291 Family Data Leakage.299 Family SCADA.308 Family Mobile Devices.318 Family Internet Services.327 Table of Contents Introduction.1 PVS PLUGIN FAMILIES.2 Family Backdoors.4 Family CGI.8 Family Database.45 Family DNS Servers.61 Family Finger.65 Family FTP Servers.66 Family FTP Clients.71 Family Generic.73 Family Operating System Detection.106 Family IMAP Servers.113 Family Internet Messengers.116 Family IRC Clients.122 Family IRC Servers.124 Family Peer-To-Peer File Sharing.125 Family POP Server.128 Family RPC.130 Family Samba.133 Family SMTP Clients.136 Family SMTP Servers.146 Family SNMP Traps.154 Family SSH.155 Passive Vulnerability Scanner (PVS) Signatures

0 notes
Photo

Power System Analysis Software:
The modeling of utility grid, in transmission or distribution is a hassle-free work with versatile importing features provided by NEPLAN. The model can be imported from standard import tools like by using Web services. Apart from importing features, drawing the network model in NEPLAN is also an efficient and easy task with neat and colorful interface and smooth tools. NEPLAN is the first POWER SYSTEM ANALYSIS Software to give cloud operations facilities to its users. Very user-friendly GUI (graphical database editor) with Map integration.
Please visit: https://ieng.tech/neplan-power-system-analysis/
Network Planning Software:
NEPLAN allows the grid operators and planners to monitor the location of poles, and customer sites in GIS. This feature helps in planning the increasing load and monitoring its impact on other parts of the grid. This way reliability and security of the grid is enhanced in the long term. Multiple users can access the same project in NEPLAN. Allowing the users to collaborate and update the network timely. This feature boosts monitoring efficiency and accuracy of decisions.
Cloud – Power Flow Analysis Tool:
NEPLAN 360 Also integrates the power of a GIS software, and a wide range of maps and geographical data can be used directly along with the network calculations. The flexibility goes beyond the easiness of a browser-based software since the calculation algorithms can be called directly by any external GIS, SCADA, or Smart Grid application through Web Services. No installations needed and the user needs only a browser to run NEPLAN 360 through internet or intranet. Therefore, is also a cross-platform application, e.g., Tablets.
Asset Management:
Whether for maintenance planning, replacement strategy, new investments, or the calculation of grid fees: The prioritization of assets is always the basis for further strategy options to use financial resources as carefully as possible. Efficient assessment and prioritization of assets with highly adaptable assessment systems. Simulations of entire asset groups or single assets (LCC). Comprehensive tool for budget planning with the help of scenarios and sensitivities. NEPLAN AM is an in-house development and thus ensures a quick respond to customer requests.
NEPLAN Simulator:
Network modeling for EMT (instantaneous values), RMS (root mean square values) and „dynamic phasor “(instantaneous values, frequency domain) Simulation.
Network modeling in the modal system (DQ) or phase system (ABC) for symmetrical and unsymmetrical events.
Integration methods: Gear ‘s (variable step size) with automatic initialization.
Model definition with macros, like in MATLAB (compiled dll) function blocks, like in Simulink
predefined models (machines, controls).
Open system, highest flexibility for modeling.
Pre-defined models for motors, generators, controllers (PSS/E, IEEE), renewable energy sources and storage, e.g., IEC 61400-27-1 for wind turbines.
Features:
Simple integration with the existing systems (via API)
Full flexibility
Quick implementation using standard programing languages
Out of box support of various standards (CIM/CGMES, UCTE etc.)
Proven solution, already used by multiple European TSO-s
[9:01 AM] Madhuri
• 64-bit system • Ram: Min. 4 GB, recommended 8 GB • CPU: Min. 2 cores, recommended 4 cores • Storage: <500MB
0 notes
Text
Safe Life with Crestgate
It is a fact that we all wish to have a house of our own but the desires of all are not fulfilled. Be it our own house or a rented one, the first and foremost feature of a house is its security. If it is a standalone building or an independent villa, then the owner has to arrange his own security but with the latest trend of gated communities, security is the utmost concern of all of us. Crestgate lends a helping hand in strengthening the security of a gated community. Residents can have a safe life with Crestgate.

What is Crestgate
Crestgate takes the responsibility of the safety and security of your gated community providing you a safe life. It is a web-based mobile application created to track and manage your visitors, staff, deliveries, and security. This application automates the processes of your gated community with its easy transitions, record maintenance, and most importantly, safety! This collaborative platform helps to communicate effortlessly bringing “convenience” at your fingertips. Crestgate serves as a tool to manage and organize the security. It is a Dwelling Owner App, Security App and Administartor. No visitor, be it a guest or household services or daily deliveries can reach your door without your approval. You get a message where you have the right to approve or deny the entry of that person. He / She will be allowed to enter the premises only with your approval in the app.
Crestgate helps Property Managers, Homeowners Associations (HOA), Security Personnel, and Homeowners to organize their communities and ensure all members are up to date on their dues, announcements, SCADA payments, and other paperwork. This app also assists in running meetings smoothly. It maintains a record of Pre-approved Delivery, Pre-Approved Visitor, Intercom calling, Notice Board, Alert System, Payments, Utilities, Recent Activity, Frequent Guests, Services, Frequent Visits etc. It also has the provision of problem complaint, staff check-in and staff check-out. Security Alert includes intrusion from other apartments, Fire alarm etc. With a number of features in Crestgate, you and your family can enjoy a safe life.
0 notes
Text
Astronomers Discover a Stellar Sys Power Fault Detection tem with Three Super Earths
www.inhandnetworks.com
An artist’s conception of an exoplanetary system, in this case around the star HD7924, that hosts two super-Earths (objects c and d in the image). Astronomers have discovered a star with three super-Earths that transit, making them prime candidates for detailed atmospheric studies. Karen Te industrial networking ramura & BJ Fulton, UH IfA
Over 3500 extra-solar planets have been confirmed to date. Most of them were discovered using the transit method, and astronomers can combine the transit light curves with velocity wobble observations to determine the planet’s mass and radius, and thereby constrain its interior structure. The atmosphere can also be studied in a transit by using the fact that the chemical composition of the atmosphere means its opacity varies with wavelength. By measuring the depth of the transit at different wavelengths, it is possible to infer the composition and temperature of the planet’s atmosphere.
CfA astronomers Joseph Rodriguez, Andrew Vanderburg, Jason Eastman, David Latham, and Samuel Quinn and their team of scientists discovered three small transiting planets orbiting the star GJ9827 which lies at the relatively close distance of 100 light-years. The three exoplanets have radii of about 1.6, 1.3, and 2.1 Earth-radii respectively. All of them are categorized as super-Earths, that is, with masses that are larger than Earth’s but less than Neptune’s. (Radial velocity measurements of the exoplanets, not included in this paper, have just been separately published and confirm this conclusion.)
GJ9827 is one of the few known s vending vms tars to have multiple transiting terrestrial-sized exoplanets that are suited for atmospheric characterization. In fact, its three exoplanets are particularly interesting because two of them have radii between 1.5 and 2.0 Earth-radii. Across this range in radii, the composition of planets is expected to change from rocky to gaseous; moreover, there are relatively few such candidates for study. These planets orbit very close to the star, with periods of 1.2, 3.6 and 6.2 days respectively, and at these close distances they have fairly hot temperatures, estimated at 1172, 811 and 680 degrees kelvin. Future observations will probe their atmospheres and provide a much more detailed picture of this unusual family of super-Earths.
Publication: Joseph E. Rodriguez, et al., “A System of Three S industrial wireless router uper Earths Transiting the Late K-Dwarf GJ 9827 at 30 pc,” AJ 155, 72, 2018; doi:10.3847/1538-3881/aaa292
wastewater treatment, remote monitoring, industrial automation, automation, industrial transport, inhand, inhand network, inhand networks, InHand Networks - Global Leader in Industrial IoT, Global Leader in Industrial IoT vending telemetry, cashless vending, light industrial, commercial, distribution automation, distribution power line monitoring, fault location, fault detection, da monitoring, smart grid, transformer monitoring, intelligent substation, goose-messaging-, remotemachine monitoring, remote secure networks, remote secure networking, secure web based scada, remote diagnostics, remote maintenance, plc-programming, intelligent traffic enforcement, ct scanners remote monitoring, mri remote monitoring, healthcare, wireless atm, branch networking, retail, digital signage, wastewater treatment, remote monitoring, industrial automation, automation, industrial transport, inhand, inhand network, inhand networks, InHand Networks - Global Leader in Industrial IoT, Global Leader in Industrial IoT Industrial IoT, IIoT, Industrial IoT Manufacturer, Industrial IoT Connectivity, Industrial IoT Products, Industrial IoT Solutions, Industrial IoT Products, industrial IoT Gateway, industrial IoT router, M2M IoT gateway, M2M IoT router, industrial router, Industrial IoT Router/Gateway, industrial IoT Gateway, industrial LTE router, Industrial VPN router, Dual SIM M2M router, Entry level Industrial Router, Cost effective, 3G 4G LTE, WiFi, VPN industrial router for commercial and industrial and M2M/IoT applications, Industrial 3G Router, Industrial 3g router, UMTS router, VPN routerIndustrial 3g router, UMTS router, VPN router, DIN-Rail router, cellular router, Industrial IoT Gateway, Industrial IoT Gateway, M2M gateway, VPN gateway, remote PLC programming, Industrial Cellular Modem, Cellular modem, data terminal unit, 3g modem, Industrial 3G Cellular Modem, 3g modem, industrial cellular modem3g modem, industrial cellular modem, industrial wireless modem, data terminal unit, Android Industrial Computer, Android Industrial Computer, Vending PC, Vending Telemetry, Vending Telemeter, Android Industrial Computer, Android Industrial Computer, Vending PC, Vending Telemetry, Vending Telemeter, Touchscreen & Vending PC, Vending Touchscreen, Vending Telemeter, Vending Telemetry, Vending Computer, Industrial LTE Router, industrial IoT Gateway, industrial LTE router, Industrial VPN router, Dual SIM M2M router, Industrial IoT Router/Gateway, industrial IoT Gateway, industrial LTE router, Industrial VPN router, Dual SIM M2M router, Industrial LTE Router, Industrial LTE router, industrial 4G/3G router, router industrial, cost-effective industrial LTE router, Industrial LTE Router, Industrial LTE router, industrial IoT router, router industrial, cost-effective M2M router, M2M LTE router, Industrial 3G Router , Industrial 3g router, industrial wireless router, VPN router, DIN-Rail router, cellular router, Industrial 3G Router , Industrial 3g router, industrial wireless router, VPN router, DIN-Rail router, cellular router, Distribution Power Line Monitoring System, Overhead Line Monitoring, Distribution Power Line Monitoring, Fault detection & location, Grid Analytics System, Remote Machine Monitoring & Maintenance System, IoT Remote Monitoring, Prognostics and Health Management, Remote connectivity, Remote Maintenance, Smart Vending, smart vending, InHandGo, retrofit, touchscreen vending, cashless vending, cloud VMS, Transformer Monitoring, Transformer Monitoring, substation monitoring, grid LTE router, wireless communication, smart grid, Remote Automation, Remote Automation, Secure remote networks, web SCADA, Remote Diagnostics, Remote PLC programming, Intelligent Traffic Enforcement, Intelligent Traffic Enforcement, wireless networking, cellular router, Wireless ATM Solution, Wireless ATM, ATM Remote Diagnostic, prestashop 多语商城, opencart ���贸商城, 网页设计, 网站建设, 企业建站, 商城网站, 集团网站, 海外网站, 营销网站, 网站推广, 华人网站建设, 华人网站维护, 华人网络兼职, china webdesign,
#intelligent traffic enforcement#remote-secure-networking#secure-web-based-scada#smart vending solutions#Industrial IoT Connectivity#transformer monitoring#IoT Remote Monitoring#remote secure networks
0 notes
Text
Global Opportunity Analysis and Industry Forecast of Energy Security Market, 2020–2027
Allied market Research’s upcoming report titled, “Energy Security Market By Power Plant (Nuclear, Thermal & Hydro, Oil & Gas, and Renewable Energy), Technology (Physical Security [Biometrics & Card Reader, Air & Ground Surveillance, Microwave Intrusion Detection, Fire Alarm System, and Others], and Network Security [SCADA, Firewall, Disaster Recovery, and Others]), Professional Services (Managed Services, Risk Management Services, Integration, and Consulting), and Industry Vertical (Energy & Power, IT & Telecommunication, and Others): Global Opportunity Analysis and Industry Forecast, 2020–2027”, offers an analysis of Energy Security market. According to the report the market is expected to register a considerable market growth by 2026. The upcoming reports would offer an extensive analysis of all the key drivers and opportunities supporting the growth and expansion of Energy Security industry
Download Sample Report (Get Full Insights in PDF - 200+ Pages) @ https://www.alliedmarketresearch.com/request-sample/9185
THE COVID-19 SCENARIO:
The industry has been going through a transformational phase in which nothing is certain. In this time of pandemic, embracing change is important. The market for Energy Security has been much/not much impacted by the COVID-19 outbreak.
NEED FOR THE REPORT:
1. The impact of COVID-19, makes it important for the stakeholders to understand the Energy Security industry. This report offers a comprehensive analysis of growth potential and market opportunities available for the Energy Security market by extensively analyzing the competitors’ strategies, the trends in the market, and new technological advancements.
2. The report will surely help the stakeholders in framing long term profitable strategies and excel in the Energy Security market.
KEY SEGMENTATION:
To make the analysis understandable and worth spending the time, the report segments the market into, Power Plant, Technology, Professional Services, Industry Vertical and region. This segmentation offers a deep understanding about the Energy Security market from the point of view of each segment. The related data table and flow charts have been used to make the analysis easily understandable and provide for better insights to the reader.
KEY MARKET PLAYERS:
The strategies of top 10 market players of the Energy Security industry are analyzed in this report to provide better understanding. The key market players included in the report are BAE Systems PLC, Elbit Systems Ltd., ABB Ltd., Thales S.A., Siemens AG, Ericsson, Honeywell International Inc., Symantec Corp., HCL Technologies, and Acorn Energy Inc.
Access Full Summary @https://www.alliedmarketresearch.com/energy-security-market-A08820
KEY BEENFITS FOR STAKEHOLDERS:
The study gives an analytical overview of energy security market forecast with current trends and future estimations to determine imminent investment pockets.
The report provides information related to key drivers, restraints, and opportunities along with detailed energy security market analysis.
The energy security market trends are quantitatively analyzed from 2020 to 2027.
Porter’s five forces analysis illustrates the potency of buyers & suppliers in the market.
About Us:
Allied Market Research (AMR) is a market research and business-consulting firm of Allied Analytics LLP, based in Portland, Oregon. AMR offers market research reports, business solutions, consulting services, and insights on markets across 11 industry verticals. Adopting extensive research methodologies, AMR is instrumental in helping its clients to make strategic business decisions and achieve sustainable growth in their market domains. We are equipped with skilled analysts and experts, and have a wide experience of working with many Fortune 500 companies and small & medium enterprises.
Contact:
David Correa
Portland, OR, United States
USA/Canada (Toll Free): +1-800-792-5285, +1-503-894-6022, +1-503-446-1141
UK: +44-845-528-1300
Hong Kong: +852-301-84916
India (Pune): +91-20-66346060
Fax: +1(855)550-5975
Web: https://www.alliedmarketresearch.com
Follow Us on LinkedIn: https://www.linkedin.com/company/allied-market-research
0 notes
Text
Why learn IIoT?
Innovation is good to go to assume control over business activities. The fourth mechanical upheaval will make the modern world as far as we might be concerned totally outdated in the following 10 years. It will likewise associate each substance in the creation chain utilizing IIoT, making it a center of organizations that will decide the organization's cutthroat strength. Information trade will become definitely more significant than the creation measures, which will make endurance hard for the organizations that choose to adhere to the customary method of business.
The advantages of IIoT are tremendous and they sway everything from support to item conveyance. This is the reason organizations today are keeping watch for an upper hand. They need the capacities of IIoT, which has flooded the interest for specialists with IIoT certificate. Nonetheless, to begin with IIoT, you should initially get to know the idea.
In this blog, we will talk about what IIoT is, the reason you ought to learn it and the chances it brings.
What is IIoT?
IIoT – Industrial Internet of Things – is only above and beyond from the Internet of Things (IoT). While IoT alludes to the remote association of your actual gadgets to the web, IIoT alludes to taking this computerized interconnectivity to another level by applying it to assembling tasks of organizations.
IIoT keeps up with this association between modern hardware, applications in the cloud, and machines. It further empowers the interconnected gadgets and interaction frameworks to speak with one another all through the assembling activities – from creation to conveyance.
For IIoT, the organization needs 3 primary components –
A gadget to be utilized as an IIoT instrument
Solid network – Wi-Fi, Bluetooth, 4G, 5G, and so forth
Handling and utilizing stage IoT information
Organizations need to have shrewd machines that are furnished with sensors and programming for following and logging information. With that, they are needed to have a decent cloud PC framework to store and handle information.
Advantages of IIoT – Industrial Internet of Things
The Industrial IoT market size is projected to cross $110 billion, which implies 17% more development for the IoT projects internationally. The interest is flooding in light of the fact that IIoT makes it feasible for associations to distantly screen, test, break down, control, and distinguish the patterns. This prompts totally new experiences that help organizations upgrade their business measures and decrease functional expenses.
Here are the 5 greatest benefits of IIoT –
Helped Efficiency
IIoT empowers you to improve working efficiencies by bypassing manual errands or works and executing computerized ones. It permits you to settle on information driven choices in regards to assembling choices. You additionally will screen execution distantly. This capacity to computerize and enhance assists organizations with expanding their business productivity.
Diminished Errors
With IIoT, you can digitize virtually all aspects of the organization. The diminished manual cycles and sections lead to the decrease of large dangers identified with difficult work. IIoT isn't simply restricted to decreasing assembling or functional mistakes. Be that as it may, it likewise diminishes human mistakes, for example, digital and information penetrates.
Support
The prescient support with IIoT settles the issues identified with assembling, fixing, machine personal time, and so on With IIoT preparing, you can distinguish what the issue is and how it tends to be settled as the exhibitions of the machines are reliably observed. You realize the undertaking's expense required in advance and can financial plan for it. With this, you can make plans so different shares in the organization are not influenced and furthermore guarantee greatest functional effectiveness.
Further developed Safety
IIoT helps support working environment wellbeing as all the incorporated security frameworks ensure laborers on the line, on the floor, just as in circulation. If there should arise an occurrence of any mishaps, every one of the laborers in the office are cautioned and tasks can be stopped promptly, so the episode can get settled. This progression additionally incorporates utilizing wearable innovation to monitor certain things that workers do.
Diminished Costs
IIoT gives the instruments that assist with diminishing expenses and improve income. With IIoT, you can use information driven experiences into creation, showcasing, activities, deals, and then some. This can lead the business to helped income and decreased expenses. The wide range of various factors like prescient support, quality control, security, helped proficiency, and so on help the organization increment its benefits.
Cognixia
With IIoT, plans of action that depend on coordinated effort and network will have a superior possibility of accomplishment. Organizations should receive more up to date abilities. They can utilize the information created by means of IIoT for your potential benefit and move up the stepping stool. The more extreme the joint effort, the more advantages the organization produces.
Last Words
IIoT unites basic resources, progressed prescient just as prescriptive examination, and is changing the manner in which businesses work. In a particularly aggressive market and continually updating mechanical world, upskilling yourself in IIoT will furnish you with a significant push for your vocation.
Take on Cognixia's IIoT certification course. We are the world's driving computerized ability change organization that is focused on assisting you with molding your future by offering you involved preparing and confirmations in advanced innovations. We're here to give you the best web based learning experience that won't just improve your insight through immersive& intelligent instructional meetings yet will enhance your range of abilities. Cognixia takes into account both the individual students just as the corporate labor force by means of intuitive teacher drove courses.
Our IIoT web based preparing will cover the significant ideas of modern robotization i.e., both PLC and SCADA. It will talk about sensor information mining, brilliant plants, remote sensor region organizations (WSAN), modern cloud stages, alongside revealing insight into Industrial IoT security. The Industrial IoT confirmation course will likewise give you involved involvement with the field with useful tasks just as labs, guaranteeing you acquire an exhaustive comprehension of the multitude of ideas talked about during the meetings.
In thi IoT training , you will cover the accompanying –
Prologue to Industrial Internet of Things
Mechanical computerization – PLC and SCADA
Sensor information mining and examination
Remote Sensor Area Networks (WSAN)
Plan and improvement of IIoT frameworks
Industry 4.0 – Smart Factories
Modern cloud stages
Modern IoT Security
Requirements
Anybody with fundamental PC abilities can try out this Industrial IoT preparing and affirmation course can select for this IIoT preparing and certificate course.
Offer LinkedIn Facebook Twitter Mail
0 notes
Text
M300 4G Modem
If you are searching for a 4G Modem, the E-Lins M300 series Cellular Modem is a good choice for you. It is a complete wireless USB data modem providing global cellular network connectivity, where cellular signal available, with 4G/3G/2G fallback capabilities for ensured access to the internet anywhere. The M300 is an easy to install productivity tool designed to provide maximum accessibility to the mobile professional allowing quick access to the internet for real-time business transactions, email, web browsing and more.
E-Lins’ mobile data products are widely used in more than 50 countries and regions, and more than twenty industrial fields, such as power control, water schedule, traffic, oil field, weather forecast, environmental protection, street lamp control, post, bank and many other areas.
What hot spots are M300 with?
Broadband M2M communications/SIM failover/standby APN
3G/4G failover for fixed line broadband connections
Rapid service deployment applications/Support At command/USB port
What Main features are M300 with?
■ Basic
l Auto install software
l Easy connection, directly to the PC or laptop by using a provided extension cable
l High speed with 4G LTE 100Mbps and back compatible to HSPA data (up to 14.4Mbps downlink and 5.76Mbps uplink) and backward compatible with EDGE/ GPRS/ GSM data connectivity (up to 216~384 Kbps)
l Visual feedback on connection status with the LED and the easy connection software, including signal strength indication
l Compatible with nearly all modern desktop and laptop PC’s equipped with Microsoft OS (2000, XP, XP Pro and Vista)
l Industrial design with intelligent software capabilities, making it a reliable cellular solution for data collection and transmission
l Plug-and-play design with easy-to-use software interface for easy integration
l Easily manage and control distributed remote devices over the air
l Built-in Watch Dog
l Real-time Clock (RTC)
l Remote Data Monitor and Control
l Reliable GSM/GPRS/EDGE/UMTS/HSPA network connectivity, providing fast and cost-effective long-range wireless communication
l Always-On-Line
l Easy-to-use
l Industrial design with surge protection
l Local and remote configuration over the air
l No need to build expensive fixed line network, saving cost substantially
What is the Typical Diagram and Industrial Applications?
l Remote Data Monitor and Control
l CCTV, security surveillance
l Water, gas and oil flow metering and schedule
l AMR (automatic meter reading)
l Power station monitoring and control
l Remote POS (point of sale) terminals, ATM,
l Traffic signals monitor and control, Traffic info guidance
l Oil field, weather forecast, environmental protection, street lamp monitoring and control
l Early Warning of Mountain Torrent
l Fleet management
l Power distribution network supervision
l Central heating system supervision
l Weather station data transmission
l Hydrologic data acquisition
l Vending machine
l Telemetry, SCADA
l Vehicle logistics and diagnostics controlling
l Parking meter and Taxi Monitor
l Telecom equipment supervision (Mobile base station, microwave or optical relay station)
The M300 series Cellular Modem sets up in minutes, making it easy to use while on-the-go. If your case or project requires a smart 4G Modem, M300 is a excellent choice and do not hesitate to contact with E-Lins Communication Co., Limited.
0 notes