#splunk services
Explore tagged Tumblr posts
Text
Why Splunk Is the Go-To Platform for Enterprise Security and Observability
In today’s digital-first world, organizations generate and rely on vast volumes of machine data to run their operations, serve customers, and protect digital assets. As cyber threats grow in complexity and IT environments become more fragmented with cloud, hybrid, and multi-cloud setups, enterprises are under pressure to maintain visibility, ensure compliance, and respond to incidents in real time. Enter Splunk: the platform leading enterprises trust for security, observability, and data-driven decision-making.
Splunk has become synonymous with real-time analytics and intelligent monitoring. Its ability to ingest, index, and correlate data from virtually any source makes it indispensable for enterprises seeking to gain end-to-end visibility across their digital infrastructure. But what exactly makes Splunk service the go-to platform for enterprise security and observability? Let’s break it down.
1. Unified Data Platform for Security and IT Operations
Splunk provides a unified platform that bridges the gap between IT security, and business operations. Unlike siloed tools that provide fragmented views, Splunk consolidates data from across your network, applications, endpoints, and cloud services to deliver a single source of truth.
Whether you’re monitoring for performance issues, detecting security breaches, or ensuring compliance, Splunk enables stakeholders to work from a common, real-time data set. This holistic approach empowers faster, more accurate decisions and fosters collaboration across departments.
2. Powerful Security Information and Event Management (SIEM) Capabilities
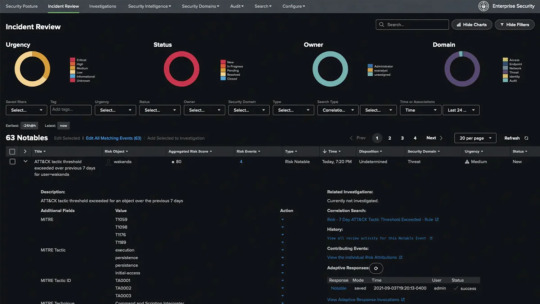
One of the strongest use cases for Splunk is in enterprise security. Splunk Enterprise Security (ES) acts as a powerful SIEM platform, enabling security teams to detect, investigate, and respond to threats efficiently. It offers advanced analytics, prebuilt dashboards, threat intelligence integration, and real-time alerting.
With features like risk-based alerting, behavioral analytics, and threat detection rules, Splunk helps security teams cut through the noise and focus on high-priority incidents. It empowers analysts to conduct rapid incident response and forensic investigations using historical data.
3. Unmatched Observability Tools for Modern Applications
Observability is more than just monitoring—it’s about understanding system behavior across distributed environments. Splunk Observability Cloud offers a full-stack observability solution that includes infrastructure monitoring, application performance monitoring (APM), log analysis, and synthetic transaction testing.
By leveraging OpenTelemetry and AI-driven insights, Splunk provides real-time visibility into system health, user experiences, and performance bottlenecks. This enables DevOps and SRE teams to troubleshoot faster, optimize application performance, and deliver consistent uptime.
4. Scalability for Enterprise Workloads
Enterprise environments are complex, and the volume of machine data they produce can be staggering. Splunk is designed to scale with your business, whether you're analyzing gigabytes or petabytes of data daily. Its distributed architecture supports horizontal scaling and high availability, ensuring consistent performance even under heavy loads.
This scalability is critical for large enterprises that require long-term retention, high-speed analytics, and support for thousands of users accessing data concurrently.
5. Advanced Analytics and Machine Learning
Splunk's analytics capabilities go beyond simple search and dashboards. With built-in machine learning (ML) and support for custom models, Splunk enables predictive analytics, anomaly detection, and behavior profiling. Security and IT teams can use ML to identify suspicious patterns, forecast system failures, or automate threat detection.
The Splunk Machine Learning Toolkit (MLTK) empowers users to apply, train, and tune models using their existing data—no data science degree is required. This intelligent layer of automation enhances situational awareness and drives proactive responses.
6. Robust Ecosystem and Integrations
Splunk integrates seamlessly with a wide range of tools, platforms, and services, including AWS, Microsoft Azure, Google Cloud, Kubernetes, ServiceNow, Palo Alto Networks, and more. These integrations extend Splunk’s capabilities and ensure it fits naturally into your existing technology stack.
The Splunkbase app marketplace features thousands of apps and add-ons for specialized data sources, dashboards, and utilities—making it easier for teams to customize the platform to suit their needs.
7. Enhanced Compliance and Audit Readiness
For industries like finance, healthcare, and government, regulatory compliance is a top priority. Splunk simplifies compliance management by offering prebuilt dashboards and reports aligned with standards like HIPAA, PCI DSS, GDPR, and ISO 27001.
Automated data collection, alerting, and audit trails make it easier to demonstrate compliance and pass audits with confidence. Splunk also provides role-based access controls and data masking to protect sensitive information.
8. Flexible Deployment Options: On-Prem, Cloud, or Hybrid
Not all enterprises are at the same stage of cloud adoption. Splunk’s flexible deployment options allow organizations to deploy the platform on-premises, in the cloud, or a hybrid environment.
Splunk Cloud Platform offers the same functionality as on-prem with the added benefits of scalability, automatic updates, and reduced infrastructure management. It’s ideal for businesses that want to accelerate time to value and reduce operational overhead.
9. Real-Time Dashboards and Visualizations
Splunk’s intuitive dashboards and data visualizations help users transform raw machine data into actionable insights. From real-time alerts on security threats to performance metrics for executive reports, Splunk offers customizable dashboards that can be tailored to user roles and use cases.
Interactive charts, graphs, and maps help bring data stories to life, making it easier for decision-makers to act on insights without technical barriers.
Final Thoughts: Why Splunk Stands Out
In a world where data is both a powerful asset and a potential liability, having the right tools to manage, secure, and understand your data is critical. Splunk delivers on all fronts—offering real-time analytics, enterprise-grade security, and unparalleled observability.
By unifying IT operations, DevOps, and security teams around a single data platform, Splunk breaks down silos, accelerates response times, and drives digital resilience. Its flexibility, intelligence, and scalability make it the ideal choice for enterprises navigating the complexities of modern IT environments.
If your organization is ready to move beyond reactive monitoring and embrace intelligent, proactive operations, Splunk is not just an option—it’s the answer.
#splunk services#microsoft azure sentinel#Splunk solutions#splunk enterprise#splunk security#Splunk consultant#microsoft sentinel#SIEM solutions#Sentinel
0 notes
Text
Get Certified in Splunk ITSI with Multisoft Systems

In today's fast-paced and data-driven business landscape, the ability to monitor, analyze, and troubleshoot IT services is paramount. Enterprises worldwide are turning to advanced solutions that provide real-time visibility into their IT environments, ensuring that business operations run smoothly. One such solution is Splunk IT Service Intelligence (ITSI), a comprehensive platform that enables businesses to monitor and optimize IT services with a focus on delivering outstanding user experiences. Multisoft Systems, a leading provider of IT training and certification courses, offers specialized Splunk ITSI online training, course, and certification to help professionals gain the skills they need to master this cutting-edge tool.
What is Splunk IT Service Intelligence (ITSI)?
Splunk IT Service Intelligence (ITSI) is an advanced analytics and monitoring platform that provides end-to-end visibility across your IT operations. It helps IT teams monitor, analyze, and visualize complex IT services by using real-time data to generate insights. By integrating data from various IT systems, Splunk ITSI enables organizations to monitor the health of critical services, quickly detect anomalies, and predict future issues before they affect business operations.
Key features of Splunk ITSI include:
Service Monitoring: ITSI gives you a unified view of your IT services, including application performance, network health, and infrastructure.
Anomaly Detection: ITSI uses machine learning algorithms to automatically detect anomalies in data, alerting IT teams to potential problems.
KPI Visualization: ITSI allows you to define and track key performance indicators (KPIs) for IT services, ensuring that all stakeholders can see the performance metrics that matter most.
Event Correlation: Splunk ITSI can correlate events from different sources to pinpoint the root cause of issues, providing faster resolution times and less downtime.
Predictive Analytics: ITSI’s predictive capabilities help organizations forecast potential future issues and plan preventive actions, improving overall IT service reliability.
Why Choose Splunk ITSI for IT Service Management?
Splunk ITSI is becoming increasingly popular among businesses for several reasons:
Proactive Monitoring: Unlike traditional monitoring systems that only provide a post-incident analysis, Splunk ITSI enables businesses to proactively address issues before they escalate, thus improving service uptime and customer satisfaction.
Integrated Insights: ITSI integrates data from various silos, providing a holistic view of your IT operations. This eliminates the need to juggle multiple tools and gives you a comprehensive view of performance metrics across systems, networks, and applications.
Enhanced Decision-Making: By leveraging machine learning and AI, Splunk ITSI provides intelligent insights, enabling IT teams to make data-driven decisions quickly. This helps in reducing mean time to resolution (MTTR) and increasing the overall effectiveness of IT teams.
Cost-Effective Service Optimization: By identifying inefficiencies and bottlenecks in your IT services, Splunk ITSI can help optimize resources and reduce unnecessary operational costs, making your IT infrastructure more efficient and cost-effective.
Scalability: Splunk ITSI is highly scalable, allowing businesses to adapt to the growing demands of modern IT infrastructures. It can handle the increasing volume of data and services without compromising on performance or reliability.
Online Training: A Gateway to Splunk ITSI Mastery
Mastering Splunk ITSI is crucial for professionals seeking to stay ahead in the rapidly evolving IT field. Multisoft Systems offers Splunk ITSI online training, which is designed to equip participants with the necessary skills and knowledge to implement, configure, and manage ITSI in real-world environments. This online training program is tailored for IT professionals who want to harness the power of Splunk ITSI to enhance service intelligence and overall IT operations.
The Splunk ITSI online course is structured to provide a comprehensive understanding of the platform’s capabilities, from the fundamentals to advanced features. The course is delivered in an interactive online format, allowing students to learn at their own pace while receiving expert guidance from experienced trainers.
Key topics covered in the Splunk ITSI online training include:
Introduction to Splunk ITSI: Understanding the core components and architecture of ITSI.
Service Monitoring and KPIs: Setting up services, defining KPIs, and visualizing them effectively.
Anomaly Detection and Predictive Analytics: Leveraging machine learning to detect anomalies and forecast potential issues.
Event Correlation and Root Cause Analysis: Using Splunk ITSI to perform event correlation and identify the root cause of IT service disruptions.
Splunk ITSI Dashboards and Visualization: Creating powerful and intuitive dashboards to track service health and KPIs.
Automation and Alerting: Configuring alerts and automating remediation processes based on detected anomalies.
Through this online course, participants will learn how to optimize the performance of their IT infrastructure, improve service uptime, and reduce operational risks using Splunk ITSI.
Splunk ITSI Certification: The Path to Professional Growth
Upon completing the Splunk ITSI online training, participants have the opportunity to earn the Splunk ITSI certification. This certification is a testament to your expertise in implementing, managing, and optimizing Splunk ITSI in real-world environments. Earning the certification demonstrates your proficiency in using Splunk ITSI to improve IT service monitoring, performance, and incident response.
The Splunk ITSI certification is highly regarded in the IT industry, and certified professionals are in high demand by organizations looking to leverage the power of data-driven decision-making in their IT operations. The certification is designed for professionals who work in IT operations, service management, and DevOps roles, and it adds significant value to your career portfolio.
Benefits of Splunk ITSI Online Training and Certification
Gain Hands-On Experience: The online training program provides practical, hands-on experience, allowing you to work with real-world scenarios and build a strong foundation in Splunk ITSI.
Stay Current with Industry Trends: Splunk ITSI is an essential tool in the modern IT landscape. Completing the course and certification ensures you stay ahead of industry trends and maintain a competitive edge.
Career Advancement: The Splunk ITSI certification opens up various career opportunities, including roles such as IT Service Manager, IT Operations Analyst, and DevOps Engineer, all of which require expertise in service monitoring and analytics.
Learn from Experts: Multisoft Systems’ trainers are experienced professionals with deep knowledge of Splunk ITSI and other IT service management solutions. They will guide you throughout the course, providing valuable insights and best practices.
Flexible Learning: The online training format allows you to learn from anywhere, at any time. This makes it easier for busy professionals to balance work and training, ensuring they can advance their skills without compromising on their job responsibilities.
Conclusion
In an era where IT disruptions can significantly impact business performance, the ability to monitor, analyze, and optimize IT services has become more critical than ever. Splunk IT Service Intelligence (ITSI) is the tool that empowers IT teams to stay ahead of potential issues and ensure smooth operations. By enrolling in Splunk ITSI online training with Multisoft Systems, you can equip yourself with the skills needed to master this powerful platform and drive business success.
With Splunk ITSI certification, you'll not only enhance your career prospects but also contribute to optimizing IT service delivery within your organization. Whether you're an IT professional, service manager, or DevOps engineer, this training will provide you with the tools to make informed decisions, reduce downtime, and improve the overall performance of your IT infrastructure. Get started today and unlock the full potential of Splunk ITSI with Multisoft Systems.
#Splunk IT Service Intelligence Training#Splunk ITSI Course#Splunk IT Service Intelligence Certification
0 notes
Text
This month, Andrew Bernier, a US Army Corps of Engineers researcher and a union leader, says that he has received a barrage of menacing messages from the same anonymous email account. Unfolding like short chapters in a dystopian novel, they have spoken of the genius of Elon Musk, referenced the power of the billionaire’s so-called Department of Government Efficiency (DOGE), and foretold the downfall of “corrupt” union bosses.
But the most eerie thing about the emails, which Bernier says began arriving after he filed an official charge accusing the Trump administration of violating his union’s collective bargaining agreement, is that they included personal details about his life—some of which he believes might have come from surveillance of his work laptop. The author referenced Bernier’s union activities, nickname, job, travel details, and even the green notebook he regularly uses. The most recent email implied that his computer was loaded with spyware. “Andy's crusade, like so many before it, had been doomed from the start,” one email stated. “The real tragedy wasn't his failure—it was his belief that the fight had ever been real.”
The unsettling messages, which were reviewed by WIRED, are an extreme example of the kinds of encounters that workers across the US government say they have had with technology since President Donald Trump took office. WIRED spoke to current employees at 13 federal agencies for this story who expressed fears about potentially being monitored by software programs, some of which they described as unfamiliar. Others said that routine software updates and notifications, perhaps once readily glossed over, have taken on ominous new meanings. Several reported feeling anxious and hyperaware of the devices and technology around them.
At the General Services Administration (GSA), one worker cited a Chrome browser extension called Dynatrace, an existing program for monitoring app performance. Inside the Social Security Administration (SSA), another employee pointed to Splunk, a longstanding tool that’s used to alert IT staff to security anomalies like when an unauthorized USB drive is plugged into a laptop. At the US Agency for International Development (USAID), one worker was caught off guard by Google’s Gemini AI chatbot, installations of which kicked off days before Trump took office.
“Everyone has been talking about whether our laptops are now able to listen to our conversations and track what we do,” says a current GSA employee, who like other workers in this story, was granted anonymity because they didn’t have authorization to speak and feared retaliation.
Dynatrace and Splunk did not respond to requests for comment from WIRED.
The workers’ accounts come as Musk’s DOGE organization is rapidly burrowing into various government agencies and departments, often gaining access to personnel records, logs of financial transactions, and other sensitive information in the process. The efforts are part of the Trump administration’s broader plan to terminate thousands of government employees and remake the face of federal agencies.
Like many private companies, US federal agencies disclose to staff that they have tools to monitor what workers do on their computers and networks. The US government’s capabilities in this area have also expanded over the past decade.
It couldn’t be learned whether the Trump administration has begun using existing tools to monitor employees in new ways; multiple agencies, including the Social Security Administration and the General Services Administration, denied that they have. The White House did not respond to requests for comment. Public evidence has not emerged of new government purchases of user-monitoring software, which is generally needed for detailed surveillance such as tracking which files a worker has copied onto a thumb drive. Some of the updates and changes that have been noticed by federal workers date back to software purchases and plans enacted long before Trump was in power, WIRED reporting shows.
“I will say my concerns are primarily based in general fear as opposed to specific knowledge,” says a worker at the Department of Homeland Security, who adds: “I’d love to be told I’m wrong.”
But activity that some workers perceive as signs of increased surveillance has prompted them to take precautions. Bernier, who works as a civil engineer for the Army Corps based in Hanover, New Hampshire, says the messages he received spooked him enough that he asked local police to keep an eye on his home, removed the battery from his work-issued laptop, and kept his work phone on airplane mode while traveling to a non-work conference last week. “There are things I don’t control but actions I can take to protect myself and my family,” he says.
Bernier’s anonymous emailer and the Army Corps did not respond to requests for comment.
A person inside the Environmental Protection Agency told WIRED last week that they’ve witnessed coworkers back out of Microsoft Teams meetings, which can be easily recorded and automatically transcribed, when they are related to topics they believe could get them fired. “Definite chilling effect,” the person says. The EPA did not respond to a request for comment.
An employee at the National Oceanic and Atmospheric Administration (NOAA), whose work with international partners is being audited by DOGE operatives, says they and their colleagues began avoiding messaging one another and have “really cut down on putting things in writing” in recent weeks. They report that correspondence from their supervisors has also significantly dropped off. NOAA declined to comment.
At the Federal Bureau of Investigation, anxiety around officials possibly targeting officers and activities perceived as being disloyal to the president has cratered morale, a federal law enforcement source with knowledge of the agents' concerns tells WIRED. The FBI declined to comment.
Aryani Ong, a civil rights activist and cofounder of Asian American Federal Employees for Nondiscrimination, a group that advocates for government workers, says those she’s been in contact with are in a heightened state of alert. In response, some federal employees have turned to encrypted communications apps to connect with colleagues and taken steps to anonymize their social media accounts, Ong says. (Federal workers are granted an allowance to use non-official communication tools only “in exceptional circumstances.”)
Insider Threat
Long before Trump’s inauguration, user activity monitoring was already mandated for federal agencies and networks that handle classified information—the result of an executive order signed by then-president Barack Obama in the wake of a massive breach of classified diplomatic cables and information about the wars in Iraq and Afghanistan in 2010. The capability is part of government-wide insider threat (InTh) programs that greatly expanded after Edward Snowden’s leak of classified surveillance documents in 2013, and again after an Army specialist murdered four colleagues and injured 16 others at Fort Hood in 2014.
The US government’s current approach to digitally monitoring federal workers has largely been guided by a directive issued by the Committee on National Security Systems in 2014, which orders relevant agencies to tie user activity to “specific users.” The public portions of the document call for “every executive branch department and agency” handling classified information to have capabilities to take screenshots, capture keystrokes, and intercept chats and email on employee devices. They are also instructed to deploy “file shadowing,” meaning secretly producing facsimiles of every file a user edits or opens.
The insider threat programs at departments such as Health and Human Services, Transportation, and Veterans Affairs, also have policies that protect unclassified government information, which enable them to monitor employees’ clicks and communications, according to notices in the Federal Register, an official source of rulemaking documents. Policies for the Department of the Interior, the Internal Revenue Service, and the Federal Deposit Insurance Corporate (FDIC), also allow collecting and assessing employees’ social media content.
These internal agency programs, overseen by a national task force led by the attorney general and director of national intelligence, aim to identify behaviors that may indicate the heightened risk of not only leaks and workplace violence, but also the “loss” or "degradation" of a federal agency’s “resources or capabilities.” Over 60 percent of insider threat incidents in the federal sector involve fraud, such as stealing money or taking someone's personal information, and are non-espionage related, according to analysis by Carnegie Mellon researchers.
“Fraud,” “disgruntlement,” “ideological challenges,” “moral outrage,” or discussion of moral concerns deemed “unrelated to work duties” are some of the possible signs that a worker poses a threat, according to US government training literature.
Of the 15 Cabinet-level departments such as energy, labor, and veterans affairs, at least nine had contracts as of late last year with suppliers such as Everfox and Dtex Systems that allowed for digitally monitoring of a portion of employees, according to public spending data. Everfox declined to comment.
Dtex’s Intercept software, which is used by multiple federal agencies, is one example of a newer class of programs that generate individual risk scores by analyzing anonymized metadata, such as which URLs workers are visiting and which files they’re opening and printing out on their work devices, according to the company. When an agency wants to identify and further investigate someone with a high score, two people have to sign off in some versions of its tool, according to the company. Dtex’s software doesn’t have to log keystrokes or scan the content of emails, calls, chats, or social media posts.
But that isn't how things work broadly across the government, where employees are warned explicitly in a recurring message when they boot up their devices that they have "no reasonable expectation of privacy" in their communications or in any data stored or transmitted through government networks. The question remains if and to what extent DOGE’s operatives are relying on existing monitoring programs to carry out Trump’s mission to rapidly eliminate federal workers that his administration views as unaligned with the president’s agenda or disloyal.
Rajan Koo, the chief technology officer of Dtex tells WIRED that he hopes the Trump administration will adjust the government’s approach to monitoring. Events such as widespread layoffs coupled with a reliance on what Koo described as intrusive surveillance tools can stir up an environment in which workers feel disgruntled, he says. “You can create a culture of reciprocal loyalty,” says Koo, or “the perfect breeding ground for insider threats.”
Already Overwhelmed
Sources with knowledge of the US government’s insider threat programs describe them as largely inefficient and labor intensive, requiring overstretched teams of analysts to manually pore through daily barrages of alerts that include many false positives. Multiple sources said that the systems are currently “overwhelmed.” Any effort by the Trump administration to extend the reach of such tools or widen their parameters—to more closely surveil for perceived signs of insubordination or disloyalty to partisan fealties, for instance—likely would result in a significant spike in false positives that would take considerable time to comb through, according to the people familiar with the work.
In an email last month seeking federal employees’ voluntary resignations, the Trump administration wrote that it wanted a “reliable, loyal, trustworthy” workforce. Attempts to use insider threat programs to enforce that vision could be met by a number of legal challenges.
US intelligence community analysts are required by law and directive to provide unbiased and objective work. That means avoiding cherry-picking information to deliberately alter judgements or falling prey to outside pressure, including from personal or political biases. These standards, even when not officially codified, are core to the professional ethics of any intelligence practitioner or law enforcement analyst conducting assessments of insider threats.
A 2018 national insider threat task force framework notes that federal programs should comply with “all applicable legal, privacy and civil liberties rights, and whistleblower protections.” Bradley Moss, an attorney representing US intelligence and law enforcement personnel, says that "disloyalty" to the Trump administration is “too vague” an excuse to terminate employees with civil service protections, adding that if "they're going to go through the statutory process, they need to demonstrate actual cause for termination."
A federal law enforcement source warns that monitoring could theoretically be used to gather political intelligence on federal employees, while the administration looks for more palatable reasons to terminate them later; similar to how law enforcement may obtain evidence that's inadmissible in the course of a criminal investigation, but then search for another evidentiary basis to file charges.
Joe Spielberger, senior legal counsel at the Project On Government Oversight, a nonpartisan group fighting alleged corruption, says that if Musk were serious about cutting government waste, he would be strengthening protections for people who report corruption and mismanagement. Any warrantless or mass surveillance of federal workers without transparent guidelines, he says, would represent a major concern.
“When you create this culture of fear and intimidation and have that chilling effect of making people even more fearful about calling out wrongdoing, it ensures that corruption goes unnoticed and unaddressed,” Spielberger says.
24 notes
·
View notes
Text

man im not using a service called splunk 😭
12 notes
·
View notes
Text
AWS Kinesis: Guides, Pricing, Cost Optimization

AWS Kinesis isn't just one service; it's a family of services, each tailored for different streaming data needs:
Amazon Kinesis Data Streams (KDS):
What it is: The foundational service. KDS allows you to capture, store, and process large streams of data records in real-time. It provides durable storage for up to 365 days (default 24 hours), enabling multiple applications to process the same data concurrently and independently.
Use Cases: Real-time analytics, log and event data collection, IoT data ingestion, real-time dashboards, application monitoring, and streaming ETL.
Key Concept: Shards. KDS capacity is measured in shards. Each shard provides a fixed unit of capacity (1 MB/s ingress, 1,000 records/s ingress, 2 MB/s egress per shard, shared among consumers).
Amazon Kinesis Data Firehose:
What it is: A fully managed service for delivering real-time streaming data to destinations like Amazon S3, Amazon Redshift, Amazon OpenSearch Service, Splunk, and generic HTTP endpoints. It automatically scales to match your data throughput and requires no administration.
Use Cases: Loading streaming data into data lakes (S3), data warehouses (Redshift), and analytics tools with minimal effort. It handles batching, compression, and encryption.
Amazon Kinesis Data Analytics:
What it is: The easiest way to process and analyze streaming data in real-time with Apache Flink or standard SQL. It allows you to build sophisticated streaming applications to transform and enrich data, perform real-time aggregations, and derive insights as data arrives.
Use Cases: Real-time anomaly detection, interactive analytics, streaming ETL, and building real-time dashboards.
Amazon Kinesis Video Streams:
What it is: A service that makes it easy to securely stream video from connected devices to AWS for analytics, machine learning (ML), and other processing. It automatically provisions and scales all the necessary infrastructure.
Use Cases: IoT video streaming, smart home security, drone video analytics, and integrating with ML services like Amazon Rekognition.
Understanding Kinesis Pricing Models
Kinesis pricing is "pay-as-you-go," meaning you only pay for what you use, with no upfront costs or minimum fees. However, the billing components vary significantly per service:
1. Kinesis Data Streams (KDS) Pricing:
KDS pricing revolves around shards and data throughput. There are two capacity modes:
Provisioned Capacity Mode:
Shard Hours: You pay for each shard-hour. This is the base cost.
PUT Payload Units: You are charged per million "PUT payload units." Each record ingested is rounded up to the nearest 25 KB. So, a 1 KB record and a 20 KB record both consume one 25 KB payload unit.
Data Retrieval: Standard data retrieval is included in shard hours up to 2MB/s per shard shared among consumers.
Extended Data Retention: Extra cost per shard-hour for retaining data beyond 24 hours, up to 7 days. Beyond 7 days (up to 365 days), it's priced per GB-month.
Enhanced Fan-Out (EFO): An additional cost per consumer-shard-hour for dedicated read throughput (2 MB/s per shard per consumer) and per GB of data retrieved via EFO. This is ideal for multiple, high-throughput consumers.
On-Demand Capacity Mode:
Per GB of Data Written: Simpler billing based on the volume of data ingested (rounded up to the nearest 1 KB per record).
Per GB of Data Read: Charged for the volume of data retrieved (no rounding).
Per Stream Hour: A fixed hourly charge for each stream operating in on-demand mode.
Optional Features: Extended data retention and Enhanced Fan-Out incur additional charges, similar to provisioned mode but with different rates.
Automatic Scaling: KDS automatically scales capacity based on your traffic, doubling the peak write throughput of the previous 30 days.
2. Kinesis Data Firehose Pricing:
Data Ingestion: Charged per GB of data ingested into the delivery stream. Records are rounded up to the nearest 5 KB.
Format Conversion: Optional charge per GB if you convert data (e.g., JSON to Parquet/ORC).
VPC Delivery: Additional cost per GB if delivering data to a private VPC endpoint.
No charges for delivery to destinations, but standard charges for S3 storage, Redshift compute, etc., apply at the destination.
3. Kinesis Data Analytics Pricing:
Kinesis Processing Units (KPUs): Billed hourly per KPU. A KPU is a combination of compute (vCPU), memory, and runtime environment (e.g., Apache Flink).
Running Application Storage: Charged per GB-month for stateful processing features.
Developer/Interactive Mode: Additional KPUs may be charged for interactive development.
4. Kinesis Video Streams Pricing:
Data Ingestion: Charged per GB of video data ingested.
Data Storage: Charged per GB-month for stored video data.
Data Retrieval & Playback: Charged per GB for data retrieved, and additional costs for specific features like HLS (HTTP Live Streaming) or WebRTC streaming minutes.
Cost Optimization Strategies for AWS Kinesis
Optimizing your Kinesis costs requires a deep understanding of your workload and the various pricing components. Here are key strategies:
Choose the Right Kinesis Service:
Firehose for simplicity & delivery: If your primary goal is to load streaming data into a data lake or warehouse without complex real-time processing, Firehose is often the most cost-effective and easiest solution.
KDS for complex processing & multiple consumers: Use Data Streams if you need multiple applications to consume the same data independently, require precise record ordering, or need custom real-time processing logic with Kinesis Data Analytics or custom consumers.
Data Analytics for real-time insights: Use Kinesis Data Analytics when you need to perform real-time aggregations, transformations, or anomaly detection on your streams.
Optimize Kinesis Data Streams (KDS) Capacity Mode:
On-Demand for unpredictable/new workloads: Start with On-Demand if your traffic patterns are unknown, highly spiky, or if you prefer a fully managed, hands-off approach to capacity. It's generally more expensive for predictable, sustained workloads but eliminates throttling risks.
Provisioned for predictable workloads: Once your traffic patterns are stable and predictable, switch to Provisioned mode. It is often significantly cheaper for consistent, high-utilization streams.
Dynamic Switching: For very variable workloads, you can technically switch between Provisioned and On-Demand modes (up to twice every 24 hours) using automation (e.g., Lambda functions) to align with known peak and off-peak periods, maximizing cost savings.
Right-Size Your Shards (Provisioned KDS):
Monitor relentlessly: Use Amazon CloudWatch metrics (IncomingBytes, IncomingRecords, GetRecords.Bytes) to understand your stream's actual throughput.
Reshard dynamically: Continuously evaluate if your current shard count matches your data volume. Scale up (split shards) when throughput needs increase and scale down (merge shards) during low periods to avoid over-provisioning. Automate this with Lambda functions and CloudWatch alarms.
Beware of "Hot Shards": Ensure your partition keys distribute data evenly across shards. If a single key (or a few keys) sends too much data to one shard, that "hot shard" can become a bottleneck and impact performance, potentially requiring more shards than technically necessary for the overall throughput.
Optimize Data Ingestion:
Batching & Aggregation: For KDS, aggregate smaller records into larger batches (up to 1 MB per PutRecord call) before sending them. For Provisioned mode, records are billed in 25KB increments, so aim for record sizes that are multiples of 25KB to avoid wasted capacity. For Firehose, ingestion is billed in 5KB increments.
Pre-process Data: Use AWS Lambda or other processing before ingesting into Kinesis to filter out unnecessary data, reduce record size, or transform data to a more efficient format.
Manage Data Retention:
Default 24 Hours: KDS retains data for 24 hours by default, which is free. Only extend retention (up to 7 days or 365 days) if your downstream applications truly need to re-process historical data or have compliance requirements. Extended retention incurs additional costs.
Long-Term Storage: For archival or long-term analytics, deliver data to cost-effective storage like Amazon S3 via Firehose or a custom KDS consumer, rather than relying on KDS's extended retention.
Smart Consumer Design (KDS):
Enhanced Fan-Out (EFO): Use EFO judiciously. While it provides dedicated throughput and low latency per consumer, it incurs additional per-consumer-shard-hour and data retrieval costs. If you have fewer than three consumers or latency isn't critical, standard (shared) throughput might be sufficient.
Kinesis Client Library (KCL): For custom consumers, use the latest KCL versions (e.g., KCL 3.0) which offer improved load balancing across workers, potentially allowing you to process the same data with fewer compute resources (e.g., EC2 instances or Lambda concurrency).
Leverage Firehose Features:
Compression: Enable data compression (e.g., GZIP, Snappy, ZIP) within Firehose before delivery to S3 or other destinations to save on storage and transfer costs.
Format Conversion: Convert data to columnar formats like Apache Parquet or ORC using Firehose's built-in conversion. This can significantly reduce storage costs in S3 and improve query performance for analytics services like Athena or Redshift Spectrum.
Buffering: Adjust buffer size and buffer interval settings in Firehose to optimize for delivery costs and destination performance, balancing real-time needs with batching efficiency.
Conclusion
AWS Kinesis is an indispensable suite of services for building robust, real-time data streaming architectures. However, its power comes with complexity, especially in pricing. By understanding the unique billing models of each Kinesis service and implementing thoughtful optimization strategies – from choosing the right capacity mode and right-sizing shards to optimizing data ingestion and consumer patterns – you can harness the full potential of real-time data processing on AWS while keeping your cloud costs in check. Continuous monitoring and a proactive approach to resource management will be your best guides on this journey.
0 notes
Text
Senior Service Assurance Engineer. II
Job title: Senior Service Assurance Engineer. II Company: American Express Job description: cause identification using blockyzer tools like IBM support blockistant, Splunk etc. Certificate Management automation…) Flexible working model with hybrid, onsite or virtual arrangements depending on role and business need Generous paid parental… Expected salary: Location: London Job date: Thu, 19 Jun…
0 notes
Text
The Big Data Security Market Size, Share | CAGR 17.3% during 2025-2032

The global big data security market size was valued at USD 23.68 billion in 2024 and is projected to reach USD 83.95 billion by 2032, growing at a CAGR of 17.3% during the forecast period (2025–2032). The increasing sophistication of cyberattacks, growing regulatory compliance requirements, and rapid digital transformation across sectors are driving significant investment in big data protection.
Key Market Highlights
2024 Global Market Size: USD 23.68 billion
2025 Forecast Start Point: USD 27.40 billion
2032 Global Market Size: USD 83.95 billion
CAGR (2025–2032): 17.3%
Market Outlook: Rising demand for security solutions that protect structured and unstructured big data across hybrid and multi-cloud environments.
Key Players in the Global Big Data Security Market:
IBM Corporation
Oracle Corporation
McAfee LLC
Microsoft Corporation
Amazon Web Services (AWS)
Symantec (Broadcom Inc.)
Cloudera Inc.
Hewlett Packard Enterprise (HPE)
Check Point Software Technologies
Imperva
Palo Alto Networks
Talend
Splunk Inc.
Request for Free Sample Reports:
Market Dynamics:
Growth Drivers
Explosion in data volumes across enterprises, cloud platforms, and edge devices
Stringent compliance mandates (e.g., GDPR, HIPAA, CCPA)
Increased adoption of cloud and hybrid cloud models needing secure data movement and storage
Surge in cyberattacks targeting high-value data sets like PII and financial records
Growing implementation of AI/ML for security analytics and anomaly detection
Key Opportunities:
Development of AI-powered big data threat detection platforms
Integration of big data security with DevSecOps and data governance models
Expansion of managed security services (MSS) in data-heavy verticals
Customized solutions for healthcare, BFSI, retail, and energy sectors
Opportunities in edge and IoT security, especially for real-time big data use cases
Emerging Trends:
Adoption of AI and deep learning for automated data threat mitigation
Rise of unified data governance frameworks integrating security and compliance
Shift toward Zero Trust architectures for granular access control
Demand for real-time risk scoring and behavioral analytics
Cloud-native security solutions for containerized and serverless environments
Technology & Application Scope:
Core Solutions: Encryption, tokenization, firewall, antivirus/antimalware, SIEM, IAM, and data loss prevention
Deployment Models: On-premise, cloud-based, and hybrid
Data Types Secured: Personal Identifiable Information (PII), financial transactions, operational data, sensor data, unstructured business records
Industries Served: BFSI, government, healthcare, retail, telecom, manufacturing, and energy
Applications: Real-time risk analytics, compliance auditing, insider threat detection, and secure cloud analytics
Speak to analysts: https://www.fortunebusinessinsights.com/enquiry/speak-to-analyst/big-data-security-market-109528
Recent Developments:
March 2024 – IBM launched an updated Guardium Data Protection for Big Data, optimized for hybrid multicloud environments, offering AI-based anomaly detection and advanced auditing features.
September 2023 – Palo Alto Networks integrated advanced threat intelligence with big data processing platforms to deliver improved data security visibility and predictive breach detection.
December 2023 – Cloudera announced strategic collaboration with AWS to deliver secure big data analytics-as-a-service tailored for heavily regulated industries.
Conclusion:
The global big data security market is poised for substantial growth as organizations face mounting pressure to secure exponentially growing data ecosystems. Investments are accelerating across technologies that not only protect data but also ensure visibility, regulatory compliance, and resiliency in digital-first environments.
Vendors that offer scalable, cloud-native, and AI-enhanced big data security platforms will be best positioned to lead the market in the coming decade.
#Big Data Security Market Share#Big Data Security Market Size#Big Data Security Market Industry#Big Data Security Market Analysis#Big Data Security Market Driver#Big Data Security Market Research#Big Data Security Market Growth
0 notes
Text
Server Security: Analyze and Harden Your Defenses in today’s increasingly digital world, securing your server is paramount. Whether you’re a beginner in ethical hacking or a tech enthusiast eager to strengthen your skills, understanding how to analyze adn harden server security configurations is essential to protect your infrastructure from cyber threats. This comprehensive guide walks you through the key processes of evaluating your server’s setup and implementing measures that enhance it's resilience. Materials and Tools Needed Material/ToolDescriptionPurposeServer Access (SSH/Console)Secure shell or direct console access to the serverTo review configurations and apply changesSecurity Audit ToolsTools like Lynis, OpenVAS, or NessusTo scan and identify vulnerabilitiesConfiguration Management ToolsTools such as Ansible, Puppet, or ChefFor automating security hardening tasksFirewall Management InterfaceAccess to configure firewalls like iptables, ufw, or cloud firewallTo manage network-level security policiesLog Monitoring UtilitySoftware like Logwatch, Splunk, or GraylogTo track suspicious events and audit security Step-by-Step Guide to Analyzing and Hardening Server Security 1. Assess Current Server Security Posture Log in securely: Use SSH with key-based authentication or direct console access to avoid exposing passwords. Run a security audit tool: Use lynis or OpenVAS to scan your server for weaknesses in installed software, configurations, and open ports. Review system policies: Check password policies, user privileges, and group memberships to ensure they follow the principle of least privilege. Analyze running services: Identify and disable unnecessary services that increase the attack surface. 2. Harden Network Security Configure firewalls: Set up strict firewall rules using iptables, ufw, or your cloud provider’s firewall to restrict inbound and outbound traffic. Limit open ports: Only allow essential ports (e.g., 22 for SSH, 80/443 for web traffic). Implement VPN access: For critical server administration, enforce VPN tunnels to add an extra layer of security. 3. Secure Authentication Mechanisms Switch to key-based SSH authentication: Disable password login to prevent brute-force attacks. Enable multi-factor authentication (MFA): Wherever possible, introduce MFA for all administrative access. Use strong passwords and rotate them: If passwords must be used,enforce complexity and periodic changes. 4. Update and Patch Software Regularly Enable automatic updates: Configure your server to automatically receive security patches for the OS and installed applications. Verify patch status: Periodically check versions of critical software to ensure they are up to date. 5. Configure System Integrity and Logging Install intrusion detection systems (IDS): Use tools like Tripwire or AIDE to monitor changes in system files. Set up centralized logging and monitoring: Collect logs with tools like syslog, Graylog, or Splunk to detect anomalies quickly. Review logs regularly: Look for repeated login failures, unexpected system changes, or new user accounts. 6. Apply Security Best Practices Disable root login: prevent direct root access via SSH; rather,use sudo for privilege escalation. Restrict user commands: Limit shell access and commands using tools like sudoers or restricted shells. Encrypt sensitive data: Use encryption for data at rest (e.g., disk encryption) and in transit (e.g., TLS/SSL). Backup configurations and data: Maintain regular, secure backups to facilitate recovery from attacks or failures. Additional Tips and Warnings Tip: Test changes on a staging environment before applying them to production to avoid service disruptions. Warning: Avoid disabling security components unless you fully understand the consequences. Tip: Document all configuration changes and security policies for auditing and compliance purposes.
Warning: Never expose unnecessary services to the internet; always verify exposure with port scanning tools. Summary Table: Key Server Security Checks Security AspectCheck or ActionFrequencyNetwork PortsScan open ports and block unauthorized onesWeeklySoftware UpdatesApply patches and updatesDaily or WeeklyAuthenticationVerify SSH keys,passwords,MFAMonthlyLogsReview logs for suspicious activityDailyFirewall RulesAudit and update firewall configurationsMonthly By following this structured guide,you can confidently analyze and harden your server security configurations. Remember, security is a continuous process — regular audits, timely updates, and proactive monitoring will help safeguard your server against evolving threats. Ethical hacking principles emphasize protecting systems responsibly, and mastering server security is a crucial step in this journey.
0 notes
Text
How SIEM Solutions Help You Detect Threats Before They Cause Damage

In an era where cyber threats are becoming more sophisticated, frequent, and damaging, the ability to detect and respond to security incidents in real-time is crucial. Traditional security tools alone are no longer sufficient to protect today’s dynamic and distributed IT environments. This is where Security Information and Event Management (SIEM) solutions come into play — acting as the eyes and ears of your cybersecurity infrastructure.
SIEM solutions don't just monitor activity; they intelligently analyze, correlate, and prioritize threats, allowing you to act before they result in severe consequences. Let’s dive into how SIEM solutions help businesses detect threats early — often before they cause any damage — and why they’ve become a cornerstone of modern cybersecurity strategies.
What Is a SIEM Solution?
A SIEM (Security Information and Event Management) system collects and aggregates log data from various sources across an organization’s IT infrastructure — including servers, firewalls, applications, and endpoints. This data is then analyzed in real time using correlation rules and analytics to detect unusual behavior, anomalies, and potential threats.
Unlike standalone antivirus or firewall tools, SIEM solutions provide a centralized and holistic view of your security posture. It’s not just about collecting data — it’s about understanding what the data is telling you and acting on it.
The Growing Importance of Real-Time Threat Detection
Cyber threats don’t wait. From ransomware and insider threats to advanced persistent threats (APTs), bad actors are constantly evolving their tactics. A single undetected intrusion can lead to data breaches, reputational damage, financial losses, and compliance violations.
According to IBM’s Cost of a Data Breach Report, it takes an average of 204 days to detect a breach. That’s more than enough time for attackers to exfiltrate sensitive data or disrupt operations.
SIEM solutions aim to drastically reduce this detection window, enabling organizations to identify and neutralize threats quickly — sometimes within seconds or minutes.
1. Centralized Data Aggregation and Correlation
The first step in early threat detection is visibility. SIEM solutions consolidate logs and events from various systems — including on-premises, cloud, and hybrid environments — into one centralized dashboard. This eliminates silos and provides full-spectrum visibility across your entire network.
But visibility alone isn't enough. SIEMs apply correlation rules to connect seemingly unrelated events. For example:
A failed login attempt from a foreign IP followed by a successful login.
Unusual file access outside of business hours.
High volumes of data are being transferred unexpectedly.
These individual events might seem harmless in isolation, but when correlated, they form the footprint of a potential breach — and the SIEM solution will flag it.
2. Real-Time Alerts and Automated Response
SIEM platforms continuously monitor for deviations from normal behavior and trigger real-time alerts when threats are detected. These alerts are not just based on predefined rules but also on behavioral baselines and machine learning models.
For example, if an employee suddenly starts downloading gigabytes of data to a personal device — something they’ve never done before — the SIEM system can immediately flag this as suspicious.
Advanced SIEM systems integrate with SOAR (Security Orchestration, Automation, and Response) platforms to automate incident response — isolating users, blocking IPs, or even initiating password resets without human intervention. This rapid response can contain a threat before it escalates.
3. Behavioral Analytics and Anomaly Detection
One of the most powerful features of modern SIEM solutions is User and Entity Behavior Analytics (UEBA). This uses machine learning to establish normal activity patterns for users, devices, and applications — and then detects anomalies.
For instance:
A user who typically logs in from Dubai between 9 AM and 5 PM is now accessing systems from Russia at 2 AM.
A service account that normally accesses only one server is now connecting to multiple servers unexpectedly.
These anomalies are often early indicators of compromised credentials, insider threats, or lateral movement within your network.
4. Threat Intelligence Integration
SIEMs can be supercharged with threat intelligence feeds that provide real-time information about known malicious IPs, domains, file hashes, and attack signatures. When your SIEM ingests this data, it can:
Instantly recognize known malware signatures.
Detect traffic going to or coming from blacklisted IP addresses.
Identify phishing attempts or command-and-control (C2) communication.
By integrating threat intelligence, SIEMs not only detect what’s happening internally but also connect it with what's happening in the broader threat landscape.
5. Compliance and Forensic Capabilities
Even if a threat doesn’t cause immediate damage, compliance violations can. SIEM solutions help organizations meet regulatory standards like GDPR, HIPAA, ISO 27001, and PCI DSS by maintaining detailed logs and audit trails.
In the event of a breach or incident, SIEM logs can be used to:
Conduct forensic investigations.
Pinpoint the source and scope of the attack.
Generate reports for auditors and stakeholders.
Having this documentation readily available can make the difference between a smooth audit and a regulatory fine.
6. Cloud and Hybrid Infrastructure Monitoring
As more organizations move to the cloud, traditional perimeter-based security tools fall short. SIEM solutions offer native integrations with major cloud platforms like AWS, Azure, and Google Cloud, allowing for complete visibility into:
Cloud-based authentication and user behavior.
API access and misconfigurations.
Unusual traffic patterns across virtual machines.
This ensures that your cloud and hybrid environments are just as protected as your on-premise systems.
7. Scalability and Customization
Whether you're a small business or a large enterprise, modern SIEM platforms offer scalable solutions that can grow with your organization. They can be customized to prioritize alerts based on your business's unique risk profile, industry, or compliance requirements.
For instance, a healthcare company might focus on detecting unauthorized access to patient data, while a fintech firm might prioritize fraud detection and transaction anomalies.
Final Thoughts: Proactive Defense Starts with SIEM
Cybersecurity is no longer just about defending the perimeter — it’s about knowing what’s happening inside your network at all times. SIEM solutions are your early-warning system, continuously scanning, learning, and alerting you to threats before they become full-blown incidents.
For organizations that value uptime, data integrity, customer trust, and compliance, investing in a modern SIEM solution is not just a smart move — it’s an essential one.
#splunk services#microsoft azure sentinel#Splunk solutions#splunk enterprise#splunk security#Splunk consultant#microsoft sentinel#SIEM solutions#Sentinel
0 notes
Text
AI Trust, Risk and Security Management Market Growth and Development Insight - Size, Share, Growth, and Industry Analysis - MarkNtel Advisors
According to Markntel Advisors Report, AI Trust, Risk and Security Management Market is expected to grow at a significant growth rate, and the analysis period is 2024-2030, considering the base year as 2023. Consistent monitoring and evaluating of market dynamics to stay informed and adapt your strategies accordingly. As a market research and consulting firm, we offer market research reports that focus on major parameters including Target Market Identification, Customer Needs and Preferences, Thorough Competitor Analysis, Market Size & Market Analysis, and other major factors. At the end, we do provide meaningful insights and actionable recommendations that inform decision-making and strategy development.
AI Trust, Risk, and Security Management focuses on developing and implementing solutions to address trust, risk, and security concerns related to AI technologies. It encompasses a range of products, services, and solutions designed to enhance trustworthiness, mitigate risks, and ensure the security of AI systems & applications. This software helps to provide continuous monitoring, auditing, and assurance to detect anomalies, errors, and deviations from expected behavior, as well as mechanisms for remediation & accountability.
Global AI Trust, Risk and Security Management Market Research Report & Summary:
The Global AI Trust, Risk and Security Management Market is estimated to grow at a CAGR of around 16.23% during the forecast period, i.e., 2024-30.
Time Period Captured in the Report:
Historical Years: 2019-22
Base Years: 2023
Forecast Years: 2024-2030
Who are the Key Players Operating in the AI Trust, Risk and Security Management Market?
The top companies of the AI Trust, Risk and Security Management Market ruling the industry are:
IBM Corporation, Broadcom, SAP, NVIDIA Corporation, Splunk Inc, Amazon Web Services., Palantir Technologies Inc, Virtusa Corp., BlackBerry Limited, RSA Security LLC., Accenture, Check Point Software Technologies Ltd, Intel Corporation, Ventus Group, Others
✅In case you missed it, we are currently revising our reports. Click on the below to get the latest research data with forecast for years 2025 to 2030, including market size, industry trends, and competitive analysis. It wouldn’t take long for the team to deliver the most recent version of the report.
Access the detailed PDF Sample report – https://www.marknteladvisors.com/query/request-sample/ai-trust-risk-security-management-market.html
("Kindly use your official email ID for all correspondence to ensure seamless engagement and access to exclusive benefits, along with prioritized support from our sales team.")
AI Trust, Risk and Security Management Industry Recent Development:
2023: IBM Corporation, launched new AI powered threat detection and response services. The new Threat Detection and Response Services (TDR) provide 24x7 monitoring, investigation, and automated remediation of security alerts from all relevant technologies across client's hybrid cloud environments.
The AI Trust, Risk and Security Management Market explores the industry by emphasizing the growth parameters and categorizes including geographical segmentation, to offer a comprehensive understanding of the market dynamic. The further bifurcations are as follows:
-By Component
-Software- Market Size & Forecast 2019-2030, (USD Million)
-Services- Market Size & Forecast 2019-2030, (USD Million)
-By Deployment
-On-Premises- Market Size & Forecast 2019-2030, (USD Million)
-Cloud-based- Market Size & Forecast 2019-2030, (USD Million)
-By Enterprise Size
-Large- Market Size & Forecast 2019-2030, (USD Million)
-Small & Medium- Market Size & Forecast 2019-2030, (USD Million)
-By End User
-Banking, Financial Services and Insurance (BFSI) - Market Size & Forecast 2019-2030, (USD Million)
-Healthcare- Market Size & Forecast 2019-2030, (USD Million)
-Manufacturing- Market Size & Forecast 2019-2030, (USD Million)
-Retail- Market Size & Forecast 2019-2030, (USD Million)
-IT & Telecom- Market Size & Forecast 2019-2030, (USD Million)
-Government- Market Size & Forecast 2019-2030, (USD Million)
-Others (Education, Transportation, etc.) - Market Size & Forecast 2019-2030, (USD Million)
-By Region
-North America
-South America
-Europe
-The Middle East & Africa
-Asia Pacific
Access The Full report: https://www.marknteladvisors.com/research-library/ai-trust-risk-security-management-market.html
Market Dynamics -Global AI Trust, Risk and Security Management Market:
Booming Adoption of AI Technologies Driving the Demand for AI Trust, Risk and Security Management Solutions – The widespread adoption of artificial intelligence (AI) technologies across various industries owing to improved performance & efficiency, proliferation of big data, etc., has led to a growing need for trust, risk management, and security solutions. AI systems often require access to large volumes of data for training and decision-making. This data includes sensitive information about individuals, businesses, or other entities. The sheer volume & value of data processed by AI systems make them attractive targets for cyberattacks.
Moreover, organizations across the globe face increased risks of data breaches, and protecting this data has become a top priority. As a result, the adoption of AI trust, risk, and security management solutions has increased in the past few years, as they are essential components to address concerns related to data security, ethical use of AI, regulatory compliance, user trust, and overall risk mitigation.
Integration of Explainable AI (XAI) Techniques to Mitigate Risk to Open New Avenues for the Market Growth – The demand for explainable AI (XAI) solutions is expected to grow in the coming years as organizations seek transparency & interpretability in AI decision-making processes. There is an opportunity for vendors to integrate XAI techniques and technologies into AI trust, risk, and security management solutions, which is anticipated to escalate the market size in the coming years. Hence, stakeholders, including users, customers, regulators, and policymakers, increasingly demand transparency & interpretability in AI decision-making processes. Besides, as the demand for XAI solutions grows, vendors that integrate XAI techniques into their AI trust, risk, and security management solutions differentiate themselves in the market and gain a competitive advantage in the coming years.
Need personalized insights? Click here to customize this report- https://www.marknteladvisors.com/query/request-customization/ai-trust-risk-security-management-market.html
Why Markntel Advisor Report?
MarkNtel Advisors is a leading consulting, data analytics, and market research firm that provides an extensive range of strategic reports on diverse industry verticals. We being a qualitative & quantitative research company, strive to deliver data to a substantial & varied client base, including multinational corporations, financial institutions, governments, and individuals, among others.
We have our existence across the market for many years and have conducted multi-industry research across 80+ countries, spreading our reach across numerous regions like America, Asia-Pacific, Europe, the Middle East & Africa, etc., and many countries across the regional scale, namely, the US, India, the Netherlands, Saudi Arabia, the UAE, Brazil, and several others.
For Further Queries:
Contact Us
MarkNtel Advisors
Email at [email protected]
Corporate Office: Office No.109, H-159, Sector 63, Noida, Uttar Pradesh - 201301, India
0 notes
Text
North America AIOps Platform Market Size, Share, Trends, Segmentation And Forecast To 2028
The North America AIOps platform market is expected to grow from US$ 1,238.17 million in 2021 to US$ 8,810.61 million by 2028; it is estimated to grow at a CAGR of 32.4% from 2021 to 2028.
In dynamic, elastic contexts, traditional ways of controlling IT complexity—offline, manual activities requiring human intervention—do not even operate. It is no longer possible to track and manage this complexity by manual, human monitoring. For years, ITOps has exceeded human scale, and the situation is only getting worse. Organizations want their critical applications to be available and operate well. They are also seeking a highly automated setup, that makes it easier to make clear decisions about new product development by leveraging classified data. Hence, the introduction of the AIOps platform has catered to these demands.
📚 𝐃𝐨𝐰𝐧𝐥𝐨𝐚𝐝 𝐒𝐚𝐦𝐩𝐥𝐞 𝐏𝐃𝐅 𝐂𝐨𝐩𝐲@ https://www.businessmarketinsights.com/sample/BMIRE00025397
The North America AIOps Platform Market is experiencing rapid growth due to the increasing demand for automated IT operations and the rising complexity of IT infrastructures. AIOps, or Artificial Intelligence for IT Operations, leverages AI and machine learning technologies to enhance and automate various IT functions, such as event correlation, anomaly detection, and root cause analysis. As businesses across the region continue their digital transformation journeys, the North America AIOps Platform Market is becoming an essential component of modern IT ecosystems.
One of the key drivers of the North America AIOps Platform Market is the exponential growth in data volumes generated by IT systems. Enterprises are generating vast amounts of data from various sources, including applications, networks, and cloud environments. Traditional IT operations tools struggle to keep up with this data explosion. AIOps platforms offer real-time insights and predictive analytics, helping IT teams proactively manage issues and ensure seamless operations. This capability significantly contributes to the widespread adoption of AIOps across different industries in North America.
Another major factor fueling the North America AIOps Platform Market is the rise of cloud computing and hybrid IT environments. Organizations are increasingly deploying cloud-native applications and infrastructure, which leads to a more complex IT landscape. AIOps platforms play a crucial role in monitoring, managing, and optimizing these environments by providing a unified view across on-premises and cloud infrastructures. This integration helps reduce downtime, improve performance, and lower operational costs, further accelerating the growth of the North America AIOps Platform Market.
The healthcare, banking, financial services, insurance (BFSI), retail, and manufacturing sectors are leading contributors to the North America AIOps Platform Market. These industries rely heavily on digital platforms and need robust IT operations to maintain uninterrupted services. AIOps solutions help these sectors minimize disruptions, enhance customer experience, and meet regulatory compliance requirements. Consequently, the demand for AIOps is steadily rising in these verticals, strengthening the overall market outlook.
📚𝐅𝐮𝐥𝐥 𝐑𝐞𝐩𝐨𝐫𝐭 𝐋𝐢𝐧𝐤 @ https://www.businessmarketinsights.com/reports/north-america-aiops-platform-market
The List of Companies.
AppDynamics
BMC Software, Inc.a
Broadcom Inc.
Dynatrace LLC
HCL Technologies
IBM Corporation
Micro Focus
Moogsoft Inc.
Resolve Systems, LLC
Splunk, Inc.
Furthermore, the presence of major technology hubs and advanced digital infrastructure in countries like the United States and Canada supports the expansion of the North America AIOps Platform Market. Leading IT and software companies are investing in research and development to introduce innovative AIOps capabilities that can deliver faster and more accurate decision-making. The competitive landscape is also intensifying as new startups and established vendors strive to capture market share by offering differentiated AIOps solutions tailored to specific industry needs.
The North America AIOps Platform Market is also witnessing increased adoption among small and medium-sized enterprises (SMEs). These organizations recognize the value of automating routine IT tasks and leveraging AI-driven insights to optimize their operations. With the availability of scalable and cost-effective AIOps solutions, SMEs are now able to harness the power of artificial intelligence without the need for extensive IT resources, thus contributing to market expansion.
In summary, the North America AIOps Platform Market is poised for sustained growth driven by the surge in data complexity, cloud adoption, and the need for operational efficiency. As AI technologies continue to evolve, the North America AIOps Platform Market will play a pivotal role in transforming IT operations across various sectors, making it a cornerstone of the region’s digital future.
North America AIOps Platform Strategic Insights
Strategic insights for the North America AIOps Platform provides data-driven analysis of the industry landscape, including current trends, key players, and regional nuances. These insights offer actionable recommendations, enabling readers to differentiate themselves from competitors by identifying untapped segments or developing unique value propositions. Leveraging data analytics, these insights help industry players anticipate the market shifts, whether investors, manufacturers, or other stakeholders. A future-oriented perspective is essential, helping stakeholders anticipate market shifts and position themselves for long-term success in this dynamic region.
North America AIOps Platform Regional Insights
The geographic scope of the North America AIOps Platform refers to the specific areas in which a business operates and competes. Understanding local distinctions, such as diverse consumer preferences (e.g., demand for specific plug types or battery backup durations), varying economic conditions, and regulatory environments, is crucial for tailoring strategies to specific markets. Businesses can expand their reach by identifying underserved areas or adapting their offerings to meet local demands. A clear market focus allows for more effective resource allocation, targeted marketing campaigns, and better positioning against local competitors, ultimately driving growth in those targeted areas.
North America AIOps Platform Market Segmentation
The North America AIOps platform market is segmented based on component, deployment, organization size, vertical, and country. Based on component, the North America AIOps platform market is segmented into platform and services. The platform segment dominated the market in 2020, and the same segment is expected to grow at a faster rate during the forecast period. Based on deployment, the North America AIOps platform market is segmented into on-premises and cloud.
Strategically, the North America AIOps platform market is characterized by a robust focus on innovation and future-readiness. Industry participants are leveraging strategic insights to understand current trends, anticipate future developments, and respond effectively to shifting market dynamics. These insights offer data-driven perspectives that help businesses identify untapped opportunities, optimize resource allocation, and develop targeted offerings. Whether it's analyzing operational bottlenecks, identifying areas for automation, or understanding customer behavior, strategic insights empower stakeholders to make informed decisions that drive long-term growth.
About Us-
Business Market Insights is a market research platform that provides subscription service for industry and company reports. Our research team has extensive professional expertise in domains such as Electronics & Semiconductor; Aerospace & Defense; Automotive & Transportation; Energy & Power; Healthcare; Manufacturing & Construction; Food & Beverages; Chemicals & Materials; and Technology, Media, & Telecommunications.
0 notes
Text
Observability Tools & Platforms Market Size, Share & Growth Analysis 2034: Enabling Full-Stack Performance Visibility

Observability Tools and Platforms Market is on an upward trajectory, projected to grow from $14.3 billion in 2024 to $33.5 billion by 2034, registering a CAGR of 8.9%. This market comprises a wide array of software tools and platforms that enable real-time monitoring, data analysis, and performance tracking of IT systems. As digital transformation accelerates and infrastructure grows increasingly complex, enterprises are prioritizing observability to ensure operational resilience, performance optimization, and user satisfaction. Cloud-native technologies, microservices, and hybrid environments are fueling demand for comprehensive monitoring solutions that offer actionable insights.
Market Dynamics
The surge in demand for observability tools is largely driven by several converging factors. One of the primary growth catalysts is the rising complexity of modern IT systems, especially those utilizing multi-cloud or hybrid environments. Businesses are looking for predictive analytics, real-time data visualization, and automated alert systems to avoid downtime and enhance user experience. The integration of AI and machine learning into observability platforms is a key trend, enabling anomaly detection and proactive issue resolution.
Click to Request a Sample of this Report for Additional Market Insights: https://www.globalinsightservices.com/request-sample/?id=GIS25147
Cloud-based tools remain dominant due to their scalability and agility, while on-premise solutions continue to serve sectors with heightened data privacy concerns. At the same time, challenges such as high implementation costs, data security concerns, and a shortage of skilled professionals are acting as restraints. However, innovations in automation and managed service models are beginning to alleviate these hurdles.
Key Players Analysis
The market is intensely competitive, with major players leading innovation in AI-driven observability and integration-ready platforms. Datadog, New Relic, Splunk, and Dynatrace are among the most prominent names, offering extensive feature sets and global service coverage. These companies continue to invest in platform expansion, cloud-native support, and user experience improvements.
New entrants like Honeycomb, Lightstep, and Logz.io are gaining traction with their specialized solutions, targeting niche functionalities like distributed tracing and developer-centric insights. Meanwhile, companies such as AppDynamics, Grafana Labs, and Elastic are innovating in open-source observability and visualization tools, making the ecosystem richer and more diverse.
Regional Analysis
North America remains the global leader in the observability market, powered by advanced infrastructure, early tech adoption, and a dense concentration of tech-driven enterprises. The United States leads in innovation and demand, closely followed by Canada.
Europe is steadily gaining momentum, with Germany and the United Kingdom prioritizing digital transformation, data compliance, and operational efficiency. Regulations such as GDPR are further pushing enterprises to adopt robust observability frameworks.
In the Asia-Pacific region, countries like India and China are witnessing rapid adoption due to digital infrastructure growth and cloud migration efforts. Latin America and the Middle East & Africa are emerging markets, with smart city initiatives and digitization efforts creating new opportunities, especially in Brazil, Mexico, UAE, and South Africa.
Recent News & Developments
In 2024, pricing strategies became a focal point, with observability platforms offering flexible models ranging from $100 to $500 per month. Companies are integrating AI/ML technologies to offer intelligent monitoring and real-time threat detection. Market leaders like Datadog and Splunk are continuously expanding their feature sets and forging partnerships to enhance value propositions.
A growing emphasis on regulatory compliance is also reshaping the market. Vendors are enhancing security and data governance features to comply with global standards. The rise of DevOps and agile development practices has further embedded observability into the software development lifecycle, shortening resolution cycles and improving product delivery.
Browse Full Report :https://www.globalinsightservices.com/reports/observability-tools-and-platforms-market/
Scope of the Report
This comprehensive report provides insights into the market from multiple angles. It covers segmentation by type, product, services, technology, application, deployment, end-user, and solution mode. The report also offers qualitative and quantitative assessments of market dynamics, including drivers, restraints, trends, and opportunities.
Additionally, the research delves into competitive landscapes, company profiles, SWOT analyses, and regional market trends. Key development strategies such as mergers, acquisitions, partnerships, and product launches are evaluated to understand the future trajectory of the market. With a forward-looking lens, the study helps stakeholders make informed strategic decisions in a rapidly evolving digital ecosystem.
Discover Additional Market Insights from Global Insight Services:
Unified Communications Market : https://www.globalinsightservices.com/reports/unified-communications-market/
Patent Analytics Market : https://www.globalinsightservices.com/reports/patent-analytics-market/
Unified Endpoint Management Market : https://www.globalinsightservices.com/reports/unified-endpoint-management-market/
Advanced Analytics Market : https://www.globalinsightservices.com/reports/advanced-analytics-market/
GPU as a Service (GPUaaS) Market ; https://www.globalinsightservices.com/reports/gpu-as-a-service-gpuaas-market-2/
#observabilitymarket #itmonitoringtools #cloudobservability #devopstools #realtimemonitoring #aiobservability #systemperformance #logmanagement #infrastructuremonitoring #apmtools #techinnovation #digitaltransformation #mlanalytics #hybridcloud #cyberresilience
About Us:
Global Insight Services (GIS) is a leading multi-industry market research firm headquartered in Delaware, US. We are committed to providing our clients with highest quality data, analysis, and tools to meet all their market research needs. With GIS, you can be assured of the quality of the deliverables, robust & transparent research methodology, and superior service.
Contact Us:
Global Insight Services LLC 16192, Coastal Highway, Lewes DE 19958 E-mail: [email protected] Phone: +1–833–761–1700 Website: https://www.globalinsightservices.com/
0 notes
Text
Big Data Market 2032: Will Enterprises Unlock the Real Power Behind the Numbers
The Big Data Market was valued at USD 325.4 Billion in 2023 and is expected to reach USD 1035.2 Billion by 2032, growing at a CAGR of 13.74% from 2024-2032.
Big Data Market is witnessing a significant surge as organizations increasingly harness data to drive decision-making, optimize operations, and deliver personalized customer experiences. Across sectors like finance, healthcare, manufacturing, and retail, big data is revolutionizing how insights are generated and applied. Advancements in AI, cloud storage, and analytics tools are further accelerating adoption.
U.S. leads global adoption with strong investment in big data infrastructure and innovation
Big Data Market continues to expand as enterprises shift from traditional databases to scalable, intelligent data platforms. With growing data volumes and demand for real-time processing, companies are integrating big data technologies to enhance agility and remain competitive in a data-centric economy.
Get Sample Copy of This Report: https://www.snsinsider.com/sample-request/2817
Market Keyplayers:
IBM
Microsoft
Oracle
SAP
Amazon Web Services (AWS)
Google
Cloudera
Teradata
Hadoop
Splunk
SAS
Snowflake
Market Analysis
The Big Data Market is shaped by exponential data growth and the rising complexity of digital ecosystems. Businesses are seeking solutions that not only store massive datasets but also extract actionable intelligence. Big data tools, combined with machine learning, are enabling predictive analytics, anomaly detection, and smarter automation. The U.S. market is at the forefront, with Europe close behind, driven by regulatory compliance and advanced analytics adoption.
Market Trends
Rapid integration of AI and machine learning with data platforms
Growth in cloud-native data lakes and hybrid storage models
Surge in real-time analytics and streaming data processing
Increased demand for data governance and compliance tools
Rising use of big data in fraud detection and risk management
Data-as-a-Service (DaaS) models gaining traction
Industry-specific analytics solutions becoming more prevalent
Market Scope
Big data’s footprint spans nearly every industry, with expanding use cases that enhance efficiency and innovation. The scope continues to grow with digital transformation and IoT connectivity.
Healthcare: Patient analytics, disease tracking, and personalized care
Finance: Risk modeling, compliance, and trading analytics
Retail: Consumer behavior prediction and inventory optimization
Manufacturing: Predictive maintenance and process automation
Government: Smart city planning and public service optimization
Marketing: Customer segmentation and campaign effectiveness
Forecast Outlook
The Big Data Market is on a strong growth trajectory as data becomes a core enterprise asset. Future success hinges on scalable infrastructure, robust security frameworks, and the ability to translate raw data into strategic value. Organizations investing in modern data architectures and AI integration are best positioned to lead in this evolving landscape.
Access Complete Report: https://www.snsinsider.com/reports/big-data-market-2817
Conclusion
In an increasingly digital world, the Big Data Market is not just a technology trend—it’s a critical engine of innovation. From New York to Berlin, enterprises are transforming raw data into competitive advantage. As the market matures, the focus shifts from volume to value, rewarding those who can extract insights with speed, precision, and responsibility.
About Us:
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Related Reports:
Contact Us:
Jagney Dave - Vice President of Client Engagement
Phone: +1-315 636 4242 (US) | +44- 20 3290 5010 (UK)
Mail us: [email protected]
0 notes
Text
Europe Security Analytics Market Demand Scope and Future Estimation until 2028
The security analytics market in Europe is expected to grow from US$ 3,644.38 million in 2021 to US$ 9,823.07 million by 2028; it is estimated to grow at a CAGR of 15.2% from 2021 to 2028.
The leading players of the Europe Security Analytics industry, their market share, product portfolio, company profiles are covered in this report. Key market players are analyzed on the basis of production volume, gross margin, market value, and price structure. The competitive market scenario among Europe Security Analytics players will help the industry aspirants in planning their strategies. The statistics presented in this report are an accurate and useful guide to shaping your business growth.
The report titled “Europe Security Analytics Market” has recently been added by Business Market Insights to get a stronger and more effective business outlook. It provides an in-depth analysis of the different attributes of the industry, such as trends, policies, and customers operating in different geographies. Research analysts use quantitative as well as qualitative analytical techniques to provide users, business owners, and industry professionals with accurate and actionable data.
Get Sample PDF Copy@: https://www.businessmarketinsights.com/sample/TIPRE00026789
Key companies profiled in this research study are:
• Broadcom, Inc.
• Cisco Systems, Inc.
• Hewlett Packard Enterprise Development LP (HPE)
• Huntsman Corporation
• IBM Corporation
• McAfee, LLC
• Rapid7
• RSA Security LLC
• SolarWinds Worldwide, LLC
• Splunk, Inc.
The report includes an executive summary, global economic outlook, and overview sections which provide a consistent analysis of the Europe Security Analytics market. Additionally, the report in the Market Overview section outlines PLC analysis and PESTLE analysis to provide a thorough analysis of the market. The overview section details Porter's five forces analysis which helps to reveal a possible scenario of the market by disclosing a competitive scenario with respect to the Europe Security Analytics Market.
This research report also presents practical and practical case studies to help you get a clearer understanding of the topic. This research report has been prepared through industry analysis techniques and presented in a professional manner by including effective information graphics whenever necessary. It helps ensure business stability and rapid development to achieve notable remarks in the global Europe Security Analytics market.
Finally, Europe Security Analytics Market report is the believable source for gaining the Market research that will exponentially accelerate your business. The report provides locales, economic conditions, item values, benefits, limits, creations, supplies, requests, market development rates, and numbers, etc. Europe Security Analytics Industry Report Announces Additional New Task SWOT Examination, Speculation Achievement Investigation and Venture Return Investigation.
Report Customization Service:
Business Market Insights customizes the report according to your needs. This report can be personalized to suit your requirements. Get in touch with our sales team so you can get a report tailored to your needs.
About Us:
Business Market Insights is a market research platform that provides subscription service for industry and company reports. Our research team has extensive professional expertise in domains such as Electronics & Semiconductor; Aerospace & Défense; Automotive & Transportation; Energy & Power; Healthcare; Manufacturing & Construction; Food & Beverages; Chemicals & Materials; and Technology, Media, & Telecommunications.
Contact us:
If you have any questions about this report or would like further information, please contact us:
Contact person: Ankit Mathur
Email: [email protected]
Phone: +16467917070
0 notes
Text
Service Assurance Engineer I
Job title: Service Assurance Engineer I Company: American Express Job description: knowledge and exposure on root cause identification using ***yzer tools like IBM support ***istant, Splunk etc. Good… insurance, and disability benefits (depending on location) Flexible working model with hybrid, onsite or virtual arrangements… Expected salary: Location: London Job date: Thu, 19 Jun 2025 22:50:51…
0 notes
Text
Connected Device Analytics Market Size, Share, Trends, Demand, Future Growth, Challenges and Competitive Analysis
"Global Connected Device Analytics Market - Size, Share, Demand, Industry Trends and Opportunities
Global Connected Device Analytics Market, By Component (Solution, Services), Device Connectivity (Wireless Personal Area Networks, Wireless Local Area Networks, Low-Power Wide Area Networks, Cellular/Machine To Machine, Wired), Deployment Mode (On-Premises, Cloud), Organization Size (Large Enterprises, Small and Medium-Sized Enterprises), Application (Security and Emergency Management, Sales and Customer Management, Remote Monitoring, Predictive Maintenance and Asset Management, Inventory Management, Energy Management, Building Automation, Others), End User (Manufacturing, Transportation and Logistics, Energy and Utilities, Retail and e-commerce, BFSI, Healthcare and Life Sciences, Government and Defense, Others) - Industry Trends.
Access Full 350 Pages PDF Report @
**Segments**
- **By Component** - Hardware - Software - Services
- **By Deployment Mode** - Cloud-based - On-premises
- **By Organization Size** - Small and Medium-sized Enterprises (SMEs) - Large Enterprises
- **By Application** - Predictive Maintenance - Risk Management - Customer Management - Energy Management - Inventory Management - Remote Monitoring - Others
The global connected device analytics market can be segmented based on components, deployment mode, organization size, and applications. In terms of components, the market is divided into hardware, software, and services. The deployment modes include cloud-based and on-premises solutions, catering to diverse customer needs. Organization sizes in focus are small and medium-sized enterprises (SMEs) along with large enterprises. Applications of connected device analytics span across predictive maintenance, risk management, customer management, energy management, inventory management, remote monitoring, and others.
**Market Players**
- IBM Corporation - Microsoft - Oracle - SAP SE - SAS Institute Inc. - Google - Amazon Web Services, Inc. - Hitachi Vantara - Cisco - Hewlett Packard Enterprise Development LP - PTC - Splunk Inc. - Teradata - Dell - Cloudera, Inc.
Key market players in the global connected device analytics market that drive technological advancements and innovation include IBM Corporation, Microsoft, Oracle, SAP SE, SAS Institute Inc., Google, Amazon Web Services, Inc., Hitachi Vantara, Cisco, Hewlett Packard Enterprise Development LP, PTC, Splunk Inc., Teradata, Dell, and Cloudera, Inc. These companies offer a wide range of products and services to meet the growing demand for connected device analytics solutions across various industries.
https://www.databridgemarketresearch.com/reports/global-connected-device-analytics-marketThe global connected device analytics market is experiencing significant growth and evolution driven by the increasing adoption of IoT devices and advancements in data analytics technology. Organizations are leveraging connected device analytics solutions to gain valuable insights from the data generated by interconnected devices to improve operational efficiency, enhance decision-making processes, and deliver a superior customer experience. The market is witnessing a surge in demand for components such as hardware, software, and services, as businesses seek comprehensive solutions to manage and analyze vast amounts of data from connected devices.
In terms of deployment modes, cloud-based solutions are gaining traction due to their scalability, flexibility, and cost-effectiveness, allowing organizations to quickly deploy analytics capabilities without significant upfront investments in infrastructure. On-premises solutions, on the other hand, cater to enterprises that require greater control over their data and prefer to keep sensitive information within their own IT environment.
The market segmentation by organization size highlights the demand for connected device analytics solutions among small and medium-sized enterprises (SMEs) looking to gain a competitive edge through data-driven insights and large enterprises aiming to optimize complex operations and scale their analytics capabilities. SMEs are increasingly recognizing the value of connected device analytics in enhancing business processes, improving customer engagement, and driving innovation.
The diverse applications of connected device analytics across industries such as manufacturing, healthcare, retail, transportation, and energy showcase the versatility and potential impact of these solutions. Predictive maintenance enables organizations to reduce downtime and maintenance costs by proactively identifying equipment failures, while risk management helps mitigate operational risks and ensure business continuity. Customer management applications enhance customer satisfaction and loyalty through personalized experiences, while energy management and inventory management improve resource utilization and supply chain efficiency.
Market players such as IBM Corporation, Microsoft, Oracle, SAP SE, and Google are at the forefront of driving innovation in connected device analytics by offering advanced analytics tools, AI-driven insights, and cloud-based platforms that enable organizations to harness the full potential of their connected devices. These companies are investing in research and development to enhance their product offerings, expand their market presence, and address evolving customer needs in a rapidly changing digital landscape.
In conclusion, the global connected device analytics market is poised for continued growth as organizations embrace digital transformation initiatives, IoT adoption accelerates, and the demand for real-time, actionable insights from connected devices rises. As market players continue to innovate and offer cutting-edge solutions, businesses across various sectors will benefit from enhanced operational efficiency, improved decision-making capabilities, and a competitive edge in the digital economy.The global connected device analytics market is expected to witness robust growth in the coming years, driven by the increasing adoption of Internet of Things (IoT) devices and the advancements in data analytics technology. As businesses across various industries seek to leverage the power of interconnected devices to optimize operations, enhance decision-making processes, and improve customer experiences, the demand for connected device analytics solutions is on the rise. Market players are focusing on developing innovative products and services to meet the evolving needs of organizations looking to harness the vast amounts of data generated by connected devices.
One key trend shaping the market is the emphasis on cloud-based deployment solutions. Cloud-based options are gaining popularity due to their scalability, flexibility, and cost-effectiveness, enabling organizations to quickly deploy analytics capabilities without significant upfront investments in infrastructure. This trend is particularly appealing to companies looking to streamline their processes and access real-time insights from connected devices efficiently.
Moreover, the segmentation by organization size reveals a growing demand for connected device analytics solutions among small and medium-sized enterprises (SMEs) and large enterprises. SMEs are increasingly recognizing the value of data-driven insights in enhancing their operations, improving customer engagement, and driving innovation. On the other hand, large enterprises are leveraging connected device analytics to optimize complex operations and scale their analytics capabilities to stay competitive in the market.
In terms of applications, connected device analytics is being deployed across various industries such as manufacturing, healthcare, retail, transportation, and energy. Predictive maintenance applications help organizations reduce downtime and maintenance costs by identifying equipment failures proactively, while risk management solutions enable businesses to mitigate operational risks and ensure continuity. Customer management applications enhance customer satisfaction through personalized experiences, while energy and inventory management solutions improve resource utilization and supply chain efficiency.
Key market players such as IBM Corporation, Microsoft, Oracle, SAP SE, and Google are driving innovation in connected device analytics by offering advanced analytics tools, AI-driven insights, and cloud-based platforms. These companies are investing in research and development to enhance their product offerings, expand their market presence, and address the evolving needs of customers in the dynamic digital landscape.
In conclusion, the global connected device analytics market is poised for significant growth as organizations continue to embrace digital transformation initiatives and IoT adoption accelerates. With market players focusing on innovation and the development of cutting-edge solutions, businesses stand to benefit from enhanced operational efficiency, improved decision-making capabilities, and a competitive edge in the digital economy. The market is dynamic, and ongoing technological advancements are expected to drive further growth and opportunities in the connected device analytics space.**Segments**
- Global Connected Device Analytics Market, By Component (Solution, Services) - Device Connectivity (Wireless Personal Area Networks, Wireless Local Area Networks, Low-Power Wide Area Networks, Cellular/Machine To Machine, Wired) - Deployment Mode (On-Premises, Cloud) - Organization Size (Large Enterprises, Small and Medium-Sized Enterprises) - Application (Security and Emergency Management, Sales and Customer Management, Remote Monitoring, Predictive Maintenance and Asset Management, Inventory Management, Energy Management, Building Automation, Others) - End User (Manufacturing, Transportation and Logistics, Energy and Utilities, Retail and e-commerce, BFSI, Healthcare and Life Sciences, Government and Defense, Others) - Industry Trends and Forecast to 2030.
The global connected device analytics market is experiencing a paradigm shift with the increasing adoption of IoT devices and the proliferation of data analytics technology. Companies across various industries are leveraging connected device analytics solutions to derive valuable insights from the vast amount of data generated by interconnected devices. The market segmentation based on components includes solutions and services, catering to the diverse needs of businesses looking to manage and analyze data effectively. Device connectivity options such as wireless personal area networks, wireless local area networks, low-power wide area networks, cellular/machine to machine, and wired connections offer flexibility and scalability in data transmission.
Deployment mode choices between on-premises and cloud-based solutions provide organizations with the flexibility to choose a setup that aligns with their data security, control, and scalability requirements. Large enterprises and small and medium-sized enterprises are both recognizing the value of connected device analytics solutions, driving the market growth. The applications of connected device analytics span across security and emergency management, sales and customer management, remote monitoring, predictive maintenance and asset management, inventory management, energy management, building automation, among others.
Various end-user industries such as manufacturing, transportation and logistics, energy and utilities, retail and e-commerce, BFSI, healthcare and life sciences, government and defense are embracing connected device analytics to streamline operations, improve customer experiences, and drive innovation. Market players like IBM Corporation, Microsoft, Oracle, SAP SE, and Google are leading the charge in the space, offering advanced tools and platforms to meet the evolving needs of organizations in today's digital landscape.
The emphasis on cloud-based deployment solutions reflects the market's focus on scalability, flexibility, and cost-effectiveness. Enterprises are leveraging cloud offerings to access real-time insights from connected devices without significant upfront investments. Organizations are increasingly recognizing the value of connected device analytics in enhancing operational efficiency, improving customer interactions, and driving innovation.
Moreover, the market segmentation by organization size highlights the demand for connected device analytics solutions among both SMEs and large enterprises. SMEs are leveraging connected device analytics to gain a competitive edge through data-driven insights, while larger enterprises are optimizing operations and scaling analytics capabilities to stay ahead in the market. The applications of connected device analytics are diverse and impactful, addressing critical areas such as predictive maintenance, risk management, customer engagement, resource optimization, and process efficiencies.
In conclusion, the global connected device analytics market is on a growth trajectory driven by the convergence of IoT devices and advanced data analytics. The market players are pushing the boundaries of innovation, offering cutting-edge solutions to help organizations harness the power of connected devices. As businesses continue to embrace digital transformation and IoT technologies, the demand for connected device analytics solutions will continue to rise, providing opportunities for enhanced operational efficiency, improved decision-making processes, and sustainable competitive advantages in the digital economy.
Connected Device Analytics Key Benefits over Global Competitors:
The report provides a qualitative and quantitative analysis of the Connected Device Analytics Market trends, forecasts, and market size to determine new opportunities.
Porter’s Five Forces analysis highlights the potency of buyers and suppliers to enable stakeholders to make strategic business decisions and determine the level of competition in the industry.
Top impacting factors & major investment pockets are highlighted in the research.
The major countries in each region are analyzed and their revenue contribution is mentioned.
The market player positioning segment provides an understanding of the current position of the market players active in the Personal Care Ingredients
Table of Contents: Connected Device Analytics Market
1 Introduction
2 Market Segmentation
3 Executive Summary
4 Premium Insight
5 Market Overview
6 Connected Device Analytics Market, by Product Type
7 Connected Device Analytics Market, by Modality
8 Connected Device Analytics Market, by Type
9 Connected Device Analytics Market, by Mode
10 Connected Device Analytics Market, by End User
12 Connected Device Analytics Market, by Geography
12 Connected Device Analytics Market, Company Landscape
13 Swot Analysis
14 Company Profiles
The investment made in the study would provide you access to information such as:
Connected Device Analytics Market [Global – Broken-down into regions]
Regional level split [North America, Europe, Asia Pacific, South America, Middle East & Africa]
Country wise Market Size Split [of important countries with major market share]
Market Share and Revenue/Sales by leading players
Market Trends – Emerging Technologies/products/start-ups, PESTEL Analysis, SWOT Analysis, Porter’s Five Forces, etc.
Market Size)
Market Size by application/industry verticals
Market Projections/Forecast
Critical Insights Related to the Connected Device Analytics Included in the Report:
Exclusive graphics and Illustrative Porter’s Five Forces analysis of some of the leading companies in this market
Value chain analysis of prominent players in the market
Current trends influencing the dynamics of this market across various geographies
Recent mergers, acquisitions, collaborations, and partnerships
Revenue growth of this industry over the forecast period
Marketing strategy study and growth trends
Growth-driven factor analysis
Emerging recess segments and region-wise market
An empirical evaluation of the curve of this market
Ancient, Present, and Probable scope of the market from both prospect value and volume
Browse Trending Reports:
Blood Meal Market Automotive Open Differential Market Cloth Self Adhesive Tape Market Brown Rice Syrup Market Rail Fasteners Market Cerebral Vasculitis Treatment Market Converted Plastic Packaging Market Automotive Emission Test Equipment Market Weight Loss and Obesity Management Market Ballistic Composites Market Polyurethane Additives Market Special Effect Pigments Market
About Data Bridge Market Research:
Data Bridge set forth itself as an unconventional and neoteric Market research and consulting firm with unparalleled level of resilience and integrated approaches. We are determined to unearth the best market opportunities and foster efficient information for your business to thrive in the market. Data Bridge endeavors to provide appropriate solutions to the complex business challenges and initiates an effortless decision-making process.
Contact Us:
Data Bridge Market Research
US: +1 614 591 3140
UK: +44 845 154 9652
APAC : +653 1251 975
Email: [email protected]"
0 notes