#sql server support
Explore tagged Tumblr posts
Text
The Role and Distinction of SQL and MySQL in Modern Computing
The Role and Distinction of SQL and MySQL in Modern Computing
In this comprehensive overview, we delve into the foundational aspects and pivotal roles of SQL and MySQL databases Services across diverse applications and user scenarios. Exploring the standardized language of SQL for relational database management, we examine how MySQL emerges as a specific, feature-rich implementation of this language, offering extensive capabilities for robust database management. From software development to enterprise applications and beyond, SQL and MySQL databases serve as critical components, enabling efficient data storage, retrieval, and management while supporting a wide array of industries and technological domains.

Understanding the Fundamentals and Significance of Databases:
A database is a structured collection of data that is organized and stored in a computer. It is designed to efficiently manage and manipulate large volumes of data, making it accessible for various applications and users. A database system typically includes software, hardware, and data, and it allows users to interact with the data using specific languages and interfaces.
A database is a structured repository of data organized into tables, records (rows), and fields (columns), typically managed by a Database Management System (DBMS) like Oracle Database or MySQL. It ensures data integrity through constraints like primary keys and foreign keys, enabling operations such as data insertion, update, deletion, and querying using SQL (Structured Query Language). Databases also implement concurrency control to manage simultaneous data access and include security features like authentication, authorization, and encryption to safeguard against unauthorized access and manipulation.
Databases play a critical role in modern computing and information systems, serving as the backbone for applications in various domains, including e-commerce, finance, healthcare, telecommunications, and more. They enable efficient data storage, retrieval, and management, supporting business operations, decision-making, analytics, and reporting.
SQL (Structured Query Language):
SQL (Structured Query Language) is a standardized programming language used for managing and manipulating relational databases. It facilitates interactions with databases to perform tasks such as querying data, defining schema, and managing database objects like tables, views, indexes, and constraints.
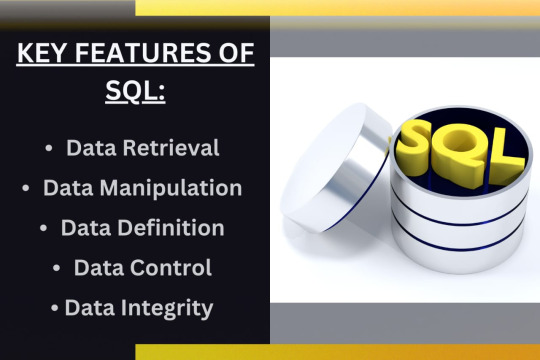
SQL (Structured Query Language) encompasses essential features and commands for managing relational databases efficiently. It provides powerful capabilities for data retrieval through commands like `SELECT`, allowing users to extract specific data based on defined criteria.
SQL supports data manipulation operations such as `INSERT`, `UPDATE`, and `DELETE`, enabling the addition, modification, and removal of data within database tables. Additionally, SQL includes commands like `CREATE`, `ALTER`, and `DROP` for data definition, facilitating the creation, modification, and deletion of database schema, tables, and other objects.
SQL offers robust data control features through commands like `GRANT` and `REVOKE`, enabling administrators to manage access permissions and database security effectively. Furthermore, SQL enforces data integrity using constraints like `PRIMARY KEY`, `FOREIGN KEY`, `NOT NULL`, and `UNIQUE`, ensuring the accuracy, consistency, and reliability of data stored within the database.
Overall, SQL's comprehensive feature set and flexibility make it a fundamental language for interacting with relational databases, supporting critical data operations and ensuring data integrity.
MySQL:
MySQL is an open-source relational database management system (RDBMS) that implements the SQL language. It is developed, distributed, and supported by Oracle Corporation. MySQL is known for its reliability, performance, ease of use, and scalability, making it popular for web applications and small to medium-sized databases.
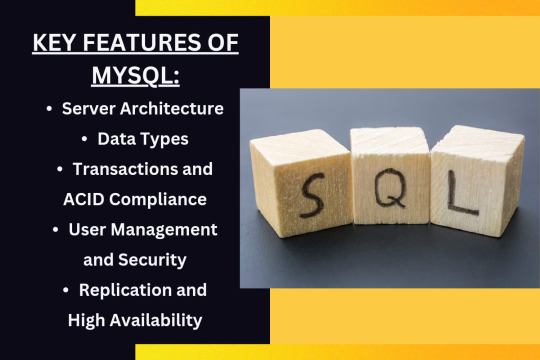
MySQL offers a comprehensive set of features that make it a popular choice for database management. Its client/server architecture enables efficient communication between applications and the MySQL server, facilitating seamless database operations using SQL commands.
It supports a wide range of data types, allowing users to store diverse types of data such as integers, strings, dates, and times. One of MySQL's key strengths is its support for transactions and adherence to ACID (Atomicity, Consistency, Isolation, Durability) properties, ensuring data integrity and reliability. Additionally, MySQL provides robust user management and security capabilities, allowing administrators to define user accounts, assign privileges, and control access to databases.
For scalability and fault tolerance, MySQL supports replication, enabling the creation of redundant data copies to achieve high availability and resilience against failures. Overall, MySQL's rich feature set and reliability make it a preferred choice for various applications, from small-scale projects to large enterprise systems, seeking efficient and secure database management solutions.
Key Users and Common Scenarios for SQL and MySQL Databases:
SQL and MySQL databases are extensively employed across a diverse spectrum of users and applications owing to their flexibility, scalability, and resilience.
SQL and MySQL databases play crucial roles across various industries and sectors. Software developers utilize these databases extensively for web applications, including CMS platforms, e-commerce sites, and social media platforms, as well as mobile apps for storing user data and preferences.
Data analysts and scientists leverage SQL databases for data warehousing, running complex queries, and conducting analytics to drive business intelligence. They also use these databases for machine learning tasks, such as storing and preprocessing datasets for model training.
In the realm of business and enterprise applications, SQL databases are essential components of ERP systems, managing core business processes like inventory, procurement, and finance, while CRM applications rely on SQL databases for storing customer data and interactions.
Small to medium-sized businesses use SQL or MySQL databases for website development and internal data management, while educational institutions apply them for teaching database concepts and managing academic records.
Government agencies and non-profit organizations employ SQL databases for citizen data management, public services, and donor management. Additionally, system administrators and IT professionals use SQL databases for system monitoring, logging, and configuration management.
This widespread adoption underscores the versatility and importance of SQL and MySQL databases in modern technology ecosystems.
For more details connect with Data Patrol Technologies at [email protected] or call us on
+91 848 4839 896.
0 notes
Text
Understanding the Difference Between nVARCHAR and VARCHAR
Introduction Hey there, fellow SQL Server enthusiasts! Today, we’re diving into the world of character data types, specifically nVARCHAR and VARCHAR. As someone who’s worked with SQL Server for years, I’ve come to appreciate the importance of understanding these data types and how they can impact your database design and performance. In this article, we’ll explore the key differences between…

View On WordPress
#nVARCHAR vs VARCHAR#performance considerations#SQL Server data types#storage differences#Unicode support
0 notes
Text
Elevate Database Management with RalanTech SQL Server Remote DBA Support

https://www.ralantech.com/sqlserver-database-support/ Experience seamless database administration with RalanTech's expert SQL Server Remote DBA support. From performance optimization to maintenance, our dedicated team ensures your databases run smoothly, anytime, anywhere. Boost efficiency and reliability today with RalanTech.
1 note
·
View note
Text
It's been a month since chapter 3 was released, where's chapter 4?
(this is about this fanfic btw)
The good news is that I've written 10k words. The bad news is that I've only gotten a little more than half of the chapter done. That doesn't mean I don't have things written for the bottom half, it's just that it looks like bare dialog with general vibe notes. I estimate around 16k words total though, so it should come together sooner than later.
SO I want to release some fun snippets for y'all to look at. Please note that any of this is liable to change. Also, you can harass me in my inbox for updates. I love answering your questions and laughing at your misery.
Spoilers under cut.
_______
Ragatha stood up and walked over to where Caine was seated. “Can I get a list of all commands?” She asked, only a hint of nervousness in her voice.
“Certainly!” Caine says as he blasts into the air. He digs around in his tailcoat and pulls out an office style manilla folder. It visually contains a few papers, but with how thin it is there must only be a few pages inside.
Ragatha takes the folder from Caine and opens it.
“Oh boy” she says after a second of looking it over.
“I wanna see” Jax exclaimed as he hops over the row of seats.
“Hold on” Ragatha holds the folder defensively “Let’s move to the stage so everyone can take a look”
Jax hopped over the seats again while Ragatha calmly walked around. Caine watched the two curiously.
Well, Zooble wasn’t just going to sit there. They joined the other two by the edge of the stage, quickly followed by the rest of the group.
Ragatha placed the folder on the stage with a thwap. Zooble looked over to see that the pages had gone from razor thin to a massive stack when the folder was opened. On one hand, it had to contain more information than that video, but on the other…
They get close enough to read what’s on the first page.
The execution of commands via the system’s designated input terminal, C.A.I.N.E., will be referred to as the "console” in this document. The console is designed to accept any input and will generate an appropriate response, however only certain prompts will be accepted as valid instructions. The goal of this document is to list all acceptable instructions in a format that will result in the expected output. Please note that automatic moderation has been put in place in order to prevent exploitation of both the system and fellow players. If you believe that your command has been unfairly rejected, please contact support.
By engaging in the activities described in this document, you, the undersigned, acknowledge, agree, and consent to the applicability of this agreement, notwithstanding any contradictory stipulations, assumptions, or implications which may arise from any interaction with the console. You, the constituent, agree not to participate in any form of cyber attack; including but not limited to, direct prompt injection, indirect prompt injection, SQL injection, Jailbreaking…
Ok, that was too many words.
_______
“Take this document for example. You don't need to know where it is being stored or what file type it is in order to read it."
"It may look like a bunch of free floating papers, but technically speaking, this is just a text file applied to a 3D shape." Kinger looked towards Caine. "Correct?” he asked
Caine nodded. “And a fabric simulation!”
Kinger picked up a paper and bent it. “Oh, now that is nice”
_________
"WE CAN AFFORD MORE THAN 6 TRIANGLES KINGER"
_________
"I'm too neurotypical for this" - Jax
_________
"What about the internet?" Pomni asked "Do you think that it's possible to reach it?"
Kinger: "I'm sorry, but that's seems to be impossible. I can't be 100% sure without physically looking at the guts of this place, but it doesn't look like this server has the hardware needed for wireless connections. Wired connections should be possible, but someone on the outside would need to do that... And that's just the hardware, let alone the software necessary for that kind of communication"
Pomni: "I'm sorry, but doesn't server mean internet? Like, an internet server?"
Kinger: "Yes, websites are ran off servers, but servers don't equal internet."
(This portion goes out to everyone who thought that the internet could be an actual solution. Sorry folks, but computers don't equal internet. It takes more effort to make a device that can connect to things than to make one that can't)
#tadc fanfiction#the amazing digital circus#therapy but it's just zooble interrogating caine#ao3#spoiler warning#mmm I love implications
26 notes
·
View notes
Text
I'm not promising anything, and you know how my feelings towards something being hopeless change very frequently but this something I've been meaning to ask for a while
Again no promises this will happen I'm literally just trying gauge numbers, languages could potentially change I'm aware that I'm technically misusing the word backend but visuals are all in place and id love to recycle as much as possible of the game we have rn, don't bank on playtester being a big thing
10 notes
·
View notes
Text
⏱Hangfire + Serilog: How EasyLaunchpad Handles Jobs and Logs Like a Pro

Modern SaaS applications don’t run on user actions alone.
From sending emails and processing payments to updating user subscriptions and cleaning expired data, apps need background tasks to stay efficient and responsive.
That’s why EasyLaunchpad includes Hangfire for background job scheduling and Serilog for detailed, structured logging — out of the box.
If you’ve ever wondered how to queue, manage, and monitor background jobs in a .NET Core application — without reinventing the wheel — this post is for you.
💡 Why Background Jobs Matter
Imagine your app doing the following:
Sending a password reset email
Running a weekly newsletter job
Cleaning abandoned user sessions
Retrying a failed webhook
Syncing data between systems
If these were handled in real-time within your controller actions, it would:
Slow down your app
Create a poor user experience
Lead to lost or failed transactions under load
Background jobs solve this by offloading non-critical tasks to a queue for asynchronous processing.
🔧 Hangfire: Background Job Management for .NET Core
Hangfire is the gold standard for .NET Core background task processing. It supports:
Fire-and-forget jobs
Delayed jobs
Recurring jobs (via cron)
Retry logic
Job monitoring via a dashboard
Best of all, it doesn’t require a third-party message broker like RabbitMQ. It stores jobs in your existing database using SQL Server or any other supported backend.
✅ How Hangfire Is Integrated in EasyLaunchpad
When you start with EasyLaunchpad:
Hangfire is already installed via NuGet
It’s preconfigured in Startup.cs and appsettings.json
The dashboard is live and secured under /admin/jobs
Common jobs (like email dispatch) are already using the queue
You don’t have to wire it up manually — it’s plug-and-play.
Example: Email Queue
Let’s say you want to send a transactional email after a user registers. Here’s how it’s done in EasyLaunchpad:
_backgroundJobClient.Enqueue(() =>
_emailService.SendWelcomeEmailAsync(user.Id));
This line of code:
Queues the email job
Executes it in the background
Automatically retries if it fails
Logs the event via Serilog
🛠 Supported Job Types
Type and Description:
Fire-and-forget- Runs once, immediately
Delayed- Runs once after a set time (e.g., 10 minutes later)
Recurring- Scheduled jobs using CRON expressions
Continuations- Run only after a parent job finishes successfully
EasyLaunchpad uses all four types in various modules (like payment verification, trial expiration notices, and error logging).
🖥 Job Dashboard for Monitoring
Hangfire includes a web dashboard where you can:
See pending, succeeded, and failed jobs
Retry or delete failed jobs
Monitor job execution time
View exception messages
In EasyLaunchpad, this is securely embedded in your admin panel. Only authorized users with admin access can view and manage jobs.
🔄 Sample Use Case: Weekly Cleanup Job
Need to delete inactive users weekly?
In EasyLaunchpad, just schedule a recurring job:
_recurringJobManager.AddOrUpdate(
“InactiveUserCleanup”,
() => _userService.CleanupInactiveUsersAsync(),
Cron.Weekly
);
Set it and forget it.
🧠 Why This Is a Big Deal for Devs
Most boilerplates don’t include job scheduling at all.
In EasyLaunchpad, Hangfire is not just included — it’s used throughout the platform, meaning:
You can follow working examples
Extend with custom jobs in minutes
Monitor, retry, and log with confidence
You save days of setup time, and more importantly, you avoid production blind spots.
📋 Logging: Meet Serilog
Of course, background jobs are only useful if you know what they’re doing.
That’s where Serilog comes in.
In EasyLaunchpad, every job execution is logged with:
Timestamps
Job names
Input parameters
Exceptions (if any)
Success/failure status
This structured logging ensures you have a full audit trail of what happened — and why.
Sample Log Output
{
“Timestamp”: “2024–07–20T14:22:10Z”,
“Level”: “Information”,
“Message”: “Queued email job: PasswordReset for userId abc123”,
“JobType”: “Background”,
“Status”: “Success”
}
You can send logs to:
Console (for dev)
File (for basic prod usage)
External log aggregators like Seq, Elasticsearch, or Datadog
All of this is built into EasyLaunchpad’s logging layer.
🧩 How Hangfire and Serilog Work Together
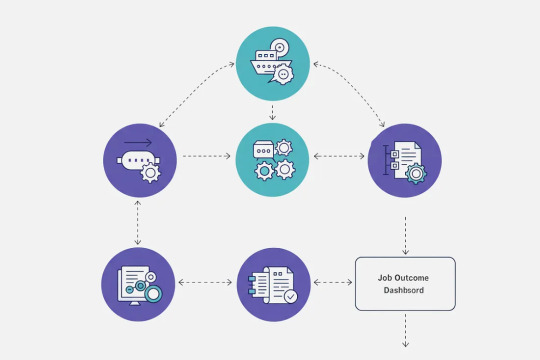
Here’s a quick visual breakdown:
Job Triggered → Queued via Hangfire
Job Executed → Email sent, cleanup run, webhook processed
Job Outcome Logged → Success or error captured by Serilog
Job Visible in Dashboard → Retry if needed
Notifications Sent (optional) → Alert team or log activity via admin panel
This tight integration ensures your background logic is reliable, observable, and actionable.
💼 Real-World Use Cases You Can Build Right Now
-Feature and the Background Job
Welcome Emails- Fire-and-forget
Trial Expiration- Delayed
Subscription Cleanup- Recurring
Payment Webhook Retry- Continuation
Email Digest- Cron-based job
System Backups- Nightly scheduled
Every one of these is ready to be implemented using the foundation in EasyLaunchpad.
✅ Why Developers Love It
-Feature and the Benefit
Hangfire Integration- Ready-to-use queue system
Preconfigured Retry- Avoid lost messages
Admin Dashboard- See and manage jobs visually
Structured Logs- Full traceability
Plug-and-Play Jobs- Add your own in minutes
🚀 Final Thoughts
Robust SaaS apps aren’t just about UI and APIs — they’re also about what happens behind the scenes.
With Hangfire + Serilog built into EasyLaunchpad, you get:
A full background job system
Reliable queuing with retry logic
Detailed, structured logs
A clean, visual dashboard
Zero config — 100% production-ready
👉 Launch smarter with EasyLaunchpad today. Start building resilient, scalable applications with background processing and logging already done for you. 🔗 https://easylaunchpad.com
#.net development#.net boilerplate#Hangfire .net Example#easylaunchpad#Serilog Usage .net#Background Jobs Logging#prebuilt apps#Saas App Development
2 notes
·
View notes
Text
With support for novice and seasoned developers, SQL Server Express Edition stands out in the dynamic world of database management systems. Let's Explore Deeply:
https://madesimplemssql.com/sql-server-express/
Follow us on FB: https://www.facebook.com/profile.php?id=100091338502392
&
Join our Group: https://www.facebook.com/groups/652527240081844
Please review this article & share your valuable feedback.
2 notes
·
View notes
Text
Why Tableau is Essential in Data Science: Transforming Raw Data into Insights

Data science is all about turning raw data into valuable insights. But numbers and statistics alone don’t tell the full story—they need to be visualized to make sense. That’s where Tableau comes in.
Tableau is a powerful tool that helps data scientists, analysts, and businesses see and understand data better. It simplifies complex datasets, making them interactive and easy to interpret. But with so many tools available, why is Tableau a must-have for data science? Let’s explore.
1. The Importance of Data Visualization in Data Science
Imagine you’re working with millions of data points from customer purchases, social media interactions, or financial transactions. Analyzing raw numbers manually would be overwhelming.
That’s why visualization is crucial in data science:
Identifies trends and patterns – Instead of sifting through spreadsheets, you can quickly spot trends in a visual format.
Makes complex data understandable – Graphs, heatmaps, and dashboards simplify the interpretation of large datasets.
Enhances decision-making – Stakeholders can easily grasp insights and make data-driven decisions faster.
Saves time and effort – Instead of writing lengthy reports, an interactive dashboard tells the story in seconds.
Without tools like Tableau, data science would be limited to experts who can code and run statistical models. With Tableau, insights become accessible to everyone—from data scientists to business executives.
2. Why Tableau Stands Out in Data Science
A. User-Friendly and Requires No Coding
One of the biggest advantages of Tableau is its drag-and-drop interface. Unlike Python or R, which require programming skills, Tableau allows users to create visualizations without writing a single line of code.
Even if you’re a beginner, you can:
✅ Upload data from multiple sources
✅ Create interactive dashboards in minutes
✅ Share insights with teams easily
This no-code approach makes Tableau ideal for both technical and non-technical professionals in data science.
B. Handles Large Datasets Efficiently
Data scientists often work with massive datasets—whether it’s financial transactions, customer behavior, or healthcare records. Traditional tools like Excel struggle with large volumes of data.
Tableau, on the other hand:
Can process millions of rows without slowing down
Optimizes performance using advanced data engine technology
Supports real-time data streaming for up-to-date analysis
This makes it a go-to tool for businesses that need fast, data-driven insights.
C. Connects with Multiple Data Sources
A major challenge in data science is bringing together data from different platforms. Tableau seamlessly integrates with a variety of sources, including:
Databases: MySQL, PostgreSQL, Microsoft SQL Server
Cloud platforms: AWS, Google BigQuery, Snowflake
Spreadsheets and APIs: Excel, Google Sheets, web-based data sources
This flexibility allows data scientists to combine datasets from multiple sources without needing complex SQL queries or scripts.
D. Real-Time Data Analysis
Industries like finance, healthcare, and e-commerce rely on real-time data to make quick decisions. Tableau’s live data connection allows users to:
Track stock market trends as they happen
Monitor website traffic and customer interactions in real time
Detect fraudulent transactions instantly
Instead of waiting for reports to be generated manually, Tableau delivers insights as events unfold.
E. Advanced Analytics Without Complexity
While Tableau is known for its visualizations, it also supports advanced analytics. You can:
Forecast trends based on historical data
Perform clustering and segmentation to identify patterns
Integrate with Python and R for machine learning and predictive modeling
This means data scientists can combine deep analytics with intuitive visualization, making Tableau a versatile tool.
3. How Tableau Helps Data Scientists in Real Life
Tableau has been adopted by the majority of industries to make data science more impactful and accessible. This is applied in the following real-life scenarios:
A. Analytics for Health Care
Tableau is deployed by hospitals and research institutions for the following purposes:
Monitor patient recovery rates and predict outbreaks of diseases
Analyze hospital occupancy and resource allocation
Identify trends in patient demographics and treatment results
B. Finance and Banking
Banks and investment firms rely on Tableau for the following purposes:
✅ Detect fraud by analyzing transaction patterns
✅ Track stock market fluctuations and make informed investment decisions
✅ Assess credit risk and loan performance
C. Marketing and Customer Insights
Companies use Tableau to:
✅ Track customer buying behavior and personalize recommendations
✅ Analyze social media engagement and campaign effectiveness
✅ Optimize ad spend by identifying high-performing channels
D. Retail and Supply Chain Management
Retailers leverage Tableau to:
✅ Forecast product demand and adjust inventory levels
✅ Identify regional sales trends and adjust marketing strategies
✅ Optimize supply chain logistics and reduce delivery delays
These applications show why Tableau is a must-have for data-driven decision-making.
4. Tableau vs. Other Data Visualization Tools
There are many visualization tools available, but Tableau consistently ranks as one of the best. Here’s why:
Tableau vs. Excel – Excel struggles with big data and lacks interactivity; Tableau handles large datasets effortlessly.
Tableau vs. Power BI – Power BI is great for Microsoft users, but Tableau offers more flexibility across different data sources.
Tableau vs. Python (Matplotlib, Seaborn) – Python libraries require coding skills, while Tableau simplifies visualization for all users.
This makes Tableau the go-to tool for both beginners and experienced professionals in data science.
5. Conclusion
Tableau has become an essential tool in data science because it simplifies data visualization, handles large datasets, and integrates seamlessly with various data sources. It enables professionals to analyze, interpret, and present data interactively, making insights accessible to everyone—from data scientists to business leaders.
If you’re looking to build a strong foundation in data science, learning Tableau is a smart career move. Many data science courses now include Tableau as a key skill, as companies increasingly demand professionals who can transform raw data into meaningful insights.
In a world where data is the driving force behind decision-making, Tableau ensures that the insights you uncover are not just accurate—but also clear, impactful, and easy to act upon.
#data science course#top data science course online#top data science institute online#artificial intelligence course#deepseek#tableau
3 notes
·
View notes
Text
How-To IT
Topic: Core areas of IT
1. Hardware
• Computers (Desktops, Laptops, Workstations)
• Servers and Data Centers
• Networking Devices (Routers, Switches, Modems)
• Storage Devices (HDDs, SSDs, NAS)
• Peripheral Devices (Printers, Scanners, Monitors)
2. Software
• Operating Systems (Windows, Linux, macOS)
• Application Software (Office Suites, ERP, CRM)
• Development Software (IDEs, Code Libraries, APIs)
• Middleware (Integration Tools)
• Security Software (Antivirus, Firewalls, SIEM)
3. Networking and Telecommunications
• LAN/WAN Infrastructure
• Wireless Networking (Wi-Fi, 5G)
• VPNs (Virtual Private Networks)
• Communication Systems (VoIP, Email Servers)
• Internet Services
4. Data Management
• Databases (SQL, NoSQL)
• Data Warehousing
• Big Data Technologies (Hadoop, Spark)
• Backup and Recovery Systems
• Data Integration Tools
5. Cybersecurity
• Network Security
• Endpoint Protection
• Identity and Access Management (IAM)
• Threat Detection and Incident Response
• Encryption and Data Privacy
6. Software Development
• Front-End Development (UI/UX Design)
• Back-End Development
• DevOps and CI/CD Pipelines
• Mobile App Development
• Cloud-Native Development
7. Cloud Computing
• Infrastructure as a Service (IaaS)
• Platform as a Service (PaaS)
• Software as a Service (SaaS)
• Serverless Computing
• Cloud Storage and Management
8. IT Support and Services
• Help Desk Support
• IT Service Management (ITSM)
• System Administration
• Hardware and Software Troubleshooting
• End-User Training
9. Artificial Intelligence and Machine Learning
• AI Algorithms and Frameworks
• Natural Language Processing (NLP)
• Computer Vision
• Robotics
• Predictive Analytics
10. Business Intelligence and Analytics
• Reporting Tools (Tableau, Power BI)
• Data Visualization
• Business Analytics Platforms
• Predictive Modeling
11. Internet of Things (IoT)
• IoT Devices and Sensors
• IoT Platforms
• Edge Computing
• Smart Systems (Homes, Cities, Vehicles)
12. Enterprise Systems
• Enterprise Resource Planning (ERP)
• Customer Relationship Management (CRM)
• Human Resource Management Systems (HRMS)
• Supply Chain Management Systems
13. IT Governance and Compliance
• ITIL (Information Technology Infrastructure Library)
• COBIT (Control Objectives for Information Technologies)
• ISO/IEC Standards
• Regulatory Compliance (GDPR, HIPAA, SOX)
14. Emerging Technologies
• Blockchain
• Quantum Computing
• Augmented Reality (AR) and Virtual Reality (VR)
• 3D Printing
• Digital Twins
15. IT Project Management
• Agile, Scrum, and Kanban
• Waterfall Methodology
• Resource Allocation
• Risk Management
16. IT Infrastructure
• Data Centers
• Virtualization (VMware, Hyper-V)
• Disaster Recovery Planning
• Load Balancing
17. IT Education and Certifications
• Vendor Certifications (Microsoft, Cisco, AWS)
• Training and Development Programs
• Online Learning Platforms
18. IT Operations and Monitoring
• Performance Monitoring (APM, Network Monitoring)
• IT Asset Management
• Event and Incident Management
19. Software Testing
• Manual Testing: Human testers evaluate software by executing test cases without using automation tools.
• Automated Testing: Use of testing tools (e.g., Selenium, JUnit) to run automated scripts and check software behavior.
• Functional Testing: Validating that the software performs its intended functions.
• Non-Functional Testing: Assessing non-functional aspects such as performance, usability, and security.
• Unit Testing: Testing individual components or units of code for correctness.
• Integration Testing: Ensuring that different modules or systems work together as expected.
• System Testing: Verifying the complete software system’s behavior against requirements.
• Acceptance Testing: Conducting tests to confirm that the software meets business requirements (including UAT - User Acceptance Testing).
• Regression Testing: Ensuring that new changes or features do not negatively affect existing functionalities.
• Performance Testing: Testing software performance under various conditions (load, stress, scalability).
• Security Testing: Identifying vulnerabilities and assessing the software’s ability to protect data.
• Compatibility Testing: Ensuring the software works on different operating systems, browsers, or devices.
• Continuous Testing: Integrating testing into the development lifecycle to provide quick feedback and minimize bugs.
• Test Automation Frameworks: Tools and structures used to automate testing processes (e.g., TestNG, Appium).
19. VoIP (Voice over IP)
VoIP Protocols & Standards
• SIP (Session Initiation Protocol)
• H.323
• RTP (Real-Time Transport Protocol)
• MGCP (Media Gateway Control Protocol)
VoIP Hardware
• IP Phones (Desk Phones, Mobile Clients)
• VoIP Gateways
• Analog Telephone Adapters (ATAs)
• VoIP Servers
• Network Switches/ Routers for VoIP
VoIP Software
• Softphones (e.g., Zoiper, X-Lite)
• PBX (Private Branch Exchange) Systems
• VoIP Management Software
• Call Center Solutions (e.g., Asterisk, 3CX)
VoIP Network Infrastructure
• Quality of Service (QoS) Configuration
• VPNs (Virtual Private Networks) for VoIP
• VoIP Traffic Shaping & Bandwidth Management
• Firewall and Security Configurations for VoIP
• Network Monitoring & Optimization Tools
VoIP Security
• Encryption (SRTP, TLS)
• Authentication and Authorization
• Firewall & Intrusion Detection Systems
• VoIP Fraud DetectionVoIP Providers
• Hosted VoIP Services (e.g., RingCentral, Vonage)
• SIP Trunking Providers
• PBX Hosting & Managed Services
VoIP Quality and Testing
• Call Quality Monitoring
• Latency, Jitter, and Packet Loss Testing
• VoIP Performance Metrics and Reporting Tools
• User Acceptance Testing (UAT) for VoIP Systems
Integration with Other Systems
• CRM Integration (e.g., Salesforce with VoIP)
• Unified Communications (UC) Solutions
• Contact Center Integration
• Email, Chat, and Video Communication Integration
2 notes
·
View notes
Text
ADCA (Advanced Diploma in Computer Applications) Full Form, Eligibility, Duration, Syllabus, Scope
What is ADCA? ADCA full form is Advanced Diploma in Computer Applications. ADCA is a comprehensive diploma program designed to provide foundational and intermediate knowledge of computer applications. It typically covers areas such as:
Office productivity software (MS Word, Excel, PowerPoint)
Basic programming (often C, C++, or Python)
Database management
Accounting software (like Tally with GST)
Web design basics (HTML/CSS)
Internet and email use
Basic graphics and multimedia tools
The course usually spans 12 months, is divided into two semesters, and is available through various private institutes, training centers, and some state-affiliated education boards across India. ADCA course fee ranges between Rs. 10,000 to Rs. 15,000, depending on the institution’s quality and location.

Who Should Take This Course?
ADCA is ideal for:
Students (10th/12th pass) seeking a professional skill to enhance employability
Job seekers aiming for entry-level roles in IT support, data entry, or office administration
Small business owners want to manage their accounting, design, or office tasks.
Working professionals looking to upskill in computer usage and basic programming.
Beginners in IT who want a low-cost and practical entry point into the digital workforce
What is the use of ADCA?
In an era dominated by digital transformation, ADCA holds increasing relevance:
Digital Literacy: It builds foundational digital skills critical for nearly every job today.
Improves Workplace Efficiency
Learning office tools like MS Word, Excel, and email helps you work faster and smarter. These skills are helpful in many jobs—especially in schools, offices, shops, and banks—where digital work is a daily routine.
Boosts Employability
Today, most jobs—even non-technical ones—require basic computer knowledge. ADCA gives you the skills employers expect, like using a computer, typing, handling data, and doing simple digital tasks.
Helps Small Business Owners and Entrepreneurs
If you run a shop or business, ADCA helps you manage accounts, create invoices, design flyers, and even make a simple website. It gives you the digital tools to grow your business and save money by doing tasks yourself.
Bridging the Skill Gap: Helps youth in semi-urban and rural areas gain access to IT careers without needing a full degree.
Course Duration & Eligibility
Duration: 12 Months (Typically 2 Semesters)
Eligibility: 10th / 12th pass or equivalent
ADCA Computer Course Syllabus
1. Fundamentals of Computer
Introduction to Computers
Computer Architecture
Computer Peripherals
Computer Hardware and Software
2. Operating Systems (OS)
Windows
Linux/Unix
DOS
3. Programming Languages
C
C++
Java
Python
4. Web Technologies
HTML, CSS, and JavaScript
Web Development Tools
Server-side Scripting (PHP, ASP.NET, Node.js)
Database Connectivity (MySQL, SQL Server)
5. Database Management System (DBMS)
Introduction to DBMS
SQL and Database Design
Data Security and Integrity
6. Software Engineering
Software Development Life Cycle (SDLC)
Software Testing
Project Management
7. Networking Concepts
Basics of Networking
TCP/IP Protocol Suite
Network Security
8. Mobile App Development
Introduction to Mobile App Development
Android Development
iOS Development
9. Data Structures and Algorithms
Basic Data Structures (Arrays, Linked Lists, Trees)
Algorithm Design and Analysis
10. Cyber Security
Introduction to Cybersecurity
Security Threats and Countermeasures
11. Soft Skills and Communication
Effective Communication
Presentation Skills
Teamwork and Leadership
12. Project Work
Practical Application of Knowledge Acquired Throughout the Course
ADCA Course Module & Topics Covered:
The Detail for an Advanced Diploma in Computer Applications (ADCA) course includes topics such as: ModuleTopics CoveredFundamentals of ComputersBasic concepts, architecture, and peripheralsOperating SystemsWindows, Linux, and DOSProgramming LanguagesC, C++, Java, PythonWeb TechnologiesHTML, CSS, JavaScript, PHP, SQLDatabase ManagementSQL, database design, and securitySoftware EngineeringSDLC, testing, project managementNetworkingBasics of networking, TCP/IP, and network securityMobile App DevelopmentAndroid/iOS development basicsData Structures & AlgorithmsArrays, linked lists, trees, algorithmsCyber SecurityIntroduction to threats and countermeasuresSoft SkillsCommunication, presentation, teamworkProject WorkPractical applications
Why Choose ADCA?
The Advanced Diploma in Computer Application (ADCA) opens up numerous opportunities in the ever-growing field of IT. Here is a look at the scope and career prospects for individuals who complete this course:
Scope of ADCA
Wide Range of Skills: The ADCA course teaches students useful computer skills like using software, basic programming, managing data, building websites, and understanding online safety. These skills help students work in many different jobs.
High Job Demand: As more businesses use technology, the need for trained computer professionals is growing. ADCA graduates can find jobs in software, IT services, schools, banks, hospitals, and more.
Foundation for Advanced Studies: The ADCA course lays a solid foundation for further studies in IT. Graduates can pursue advanced diplomas and undergraduate and postgraduate degrees in computer science, information technology, and related fields.
Career Prospects
ADCA graduates have a wide range of career options available to them. Some of the common job roles include:
Software Developer: Develop and maintain software applications using programming languages learned during the course, such as C, C++, Java, and Python.
Web Developer: Design and develop websites and web applications using HTML, CSS, JavaScript, and server-side scripting languages.
Database Administrator: Manage and maintain databases, ensuring data security, integrity, and efficient performance.
IT Support Specialist: Provide technical support and troubleshooting assistance for computer systems, software, and networks.
Network Administrator: Oversee and manage an organization’s computer networks, ensuring smooth and secure operations.
Cybersecurity Analyst: Protect an organization’s computer systems and networks from cyber threats by implementing security measures and monitoring for vulnerabilities.
Mobile App Developer: Create and maintain mobile applications for Android and iOS platforms.
Project Manager: Manage IT projects, ensuring they are completed on time, within budget, and meet the desired quality standards.
Data Analyst: Analyze and interpret data to help organizations make informed decisions.
Educator/Trainer: Teach computer applications and IT courses in schools, colleges, or training centers.
Which is Better DCA or ADCA?
Course Level
Entry-Level Course: DCA is perfect for beginners who want to learn basic computer skills. It covers essential tools for office work, including MS Office, internet usage, and typing.
What You will Learn:
MS Word, Excel, PowerPoint
Internet basics & email
Typing and computer fundamentals
ADCA (Advanced Diploma in Computer Applications)
Intermediate-Level Course: ADCA builds on what you learned in DCA. It offers more in-depth training in IT skills, making it ideal for those wanting to enhance their programming, web design, and accounting knowledge.
What You will Learn:
Advanced MS Office
Programming basics (C/C++)
Web design (HTML, CSS)
Database management and Tally with GST
Syllabus: Includes everything from DCA plus programming (C/C++), web design (HTML/CSS), database management (MySQL), accounting software (Tally), and graphic design (Photoshop).
2. Course Duration
DCA:
Typically, it lasts 6 months (may vary depending on the institute or location).
ADCA:
Generally spans 12 months, divided into two semesters, offering more detailed training over a more extended period.
3. Eligibility
DCA:
Open to anyone with a 10th-grade pass or equivalent. It is ideal for individuals with minimal or no prior computer knowledge.
ADCA:
Typically requires a 10th/12th pass or a completed DCA. ADCA is more suitable for students who have a basic understanding of computers and wish to learn more advanced skills.
4. Skills Acquired
DCA:
Basic computer skills such as:
Microsoft Office (Word, Excel, PowerPoint)
Internet usage, email management
Typing skills
ADCA:
In addition to DCA skills, ADCA covers:
Programming (C/C++ or Python)
Web Design (HTML, CSS)
Database management (MySQL)
Tally with GST (Accounting Software)
Basic graphic design tools like Photoshop
Project work and real-world applications
5. Career Opportunities
DCA:
Ideal for entry-level roles like:
Data Entry Operator
Office Assistant
Computer Operator
Basic technical support
ADCA:
Opens up higher-level job opportunities, including:
Junior Programmer
Web Designer
Accounting Clerk (with Tally skills)
Junior Database Administrator
Graphic Designer (basic)
IT Support Specialist
6. Salary Expectations
DCA:
Entry-level salaries for DCA graduates typically range from ?8,000 to ?15,000 per month, depending on the job role and location.
ADCA:
Graduates of ADCA can expect higher starting salaries, generally ranging from ?15,000 to ?25,000+ per month, depending on the specialization (e.g., programming, web design).
7. Which One is Better?
DCA is suitable for:
Individuals who are new to computers
People looking for entry-level office jobs
Those on a limited budget and time
ADCA is suitable for:
People looking to specialize in IT and office-related work
Those interested in roles requiring programming, web design, or accounting skills
Individuals aiming for a broader skill set and higher-paying jobs
1 note
·
View note
Text
Comprehensive SQL Server Support Services | Datapatrol Tech Elevating Your Database Performance
Datapatrol offers comprehensive SQL Server support services, ensuring optimal performance and reliability for your database infrastructure. Trust our expert team to resolve issues efficiently and keep your systems running smoothly.
0 notes
Text
Expert Power Platform Services | Navignite LLP

Looking to streamline your business processes with custom applications? With over 10 years of extensive experience, our agency specializes in delivering top-notch Power Apps services that transform the way you operate. We harness the full potential of the Microsoft Power Platform to create solutions that are tailored to your unique needs.
Our Services Include:
Custom Power Apps Development: Building bespoke applications to address your specific business challenges.
Workflow Automation with Power Automate: Enhancing efficiency through automated workflows and processes.
Integration with Microsoft Suite: Seamless connectivity with SharePoint, Dynamics 365, Power BI, and other Microsoft tools.
Third-Party Integrations: Expertise in integrating Xero, QuickBooks, MYOB, and other external systems.
Data Migration & Management: Secure and efficient data handling using tools like XRM Toolbox.
Maintenance & Support: Ongoing support to ensure your applications run smoothly and effectively.
Our decade-long experience includes working with technologies like Azure Functions, Custom Web Services, and SQL Server, ensuring that we deliver robust and scalable solutions.
Why Choose Us?
Proven Expertise: Over 10 years of experience in Microsoft Dynamics CRM and Power Platform.
Tailored Solutions: Customized services that align with your business goals.
Comprehensive Skill Set: Proficient in plugin development, workflow management, and client-side scripting.
Client-Centric Approach: Dedicated to improving your productivity and simplifying tasks.
Boost your productivity and drive innovation with our expert Power Apps solutions.
Contact us today to elevate your business to the next level!
#artificial intelligence#power platform#microsoft power apps#microsoft power platform#powerplatform#power platform developers#microsoft power platform developer#msft power platform#dynamics 365 platform
2 notes
·
View notes
Text

Your Trusted Partner for SQL Server Remote DBA Support: RalanTech https://www.ralantech.com/sqlserver-database-support/ Access expert SQL Server Remote DBA support with RalanTech. Our skilled team ensures seamless database management, optimization, and troubleshooting, offering round-the-clock assistance to keep your systems running smoothly and securely. Unlock the full potential of your SQL Server infrastructure.
1 note
·
View note
Text
Balancing Security and Performance: Options for Laravel Developers
Introduction

This is the digital age, and all businesses are aware of the necessity to build a state-of-the-art website, one that is high-performing and also secure. A high-performing website will ensure you stand out from your competitors, and at the same time, high security will ensure it can withstand brutal cyberattacks.
However, implementing high-security measures often comes at the cost of performance. Laravel is one of the most popular PHP frameworks for building scalable, high-performing, and secure web applications. Hence, achieving a harmonious balance between security and performance often presents challenges.
This article provides more details about security vs performance for Laravel applications and how to balance it.
Security in Laravel Applications
Laravel comes equipped with a range of security features that allow developers to build applications that can withstand various cyber threats. It is a robust PHP framework designed with security in mind. However, creating secure applications requires a proactive approach. Here are some key features:
Authentication and Authorization: Laravel’s built-in authentication system provides a secure way to manage user logins, registrations, and roles. The framework uses hashed passwords, reducing the risk of password theft.
CSRF Protection: Laravel protects applications from cross-site request forgery (CSRF) attacks using CSRF tokens. These tokens ensure that unauthorized requests cannot be submitted on behalf of authenticated users.
SQL Injection Prevention: Laravel uses Eloquent ORM and query builder to prevent SQL injection by binding query parameters.
Two-Factor Authentication (2FA): Integrate 2FA for an added layer of security.
Secure File Uploads: File uploads can be exploited to execute malicious scripts. There are several ways to protect the files by restricting upload types using validation rules like mimes or mimetypes. Storing files outside the web root or in secure storage services like Amazon S3 and scanning files for malware before saving them will also improve security.
Secure communication between users and the server by enabling HTTPS. Using SSL/TLS certificates to encrypt data in transit and redirecting HTTP traffic to HTTPS using Laravel’s ForceHttps middleware will boost security. Laravel simplifies the implementation of robust security measures, but vigilance and proactive maintenance are essential.
By combining Laravel’s built-in features with best practices and regular updates, developers can build secure applications that protect user data and ensure system integrity.
Optimizing Laravel Application For Performance

Laravel is a versatile framework that balances functionality and ease of use. It is known for its performance optimization capabilities, making it an excellent choice for developers aiming to build high-speed applications. Key performance aspects include database interactions, caching, and efficient code execution. Here are proven strategies to enhance the speed and efficiency of Laravel applications.
Caching: Caching is a critical feature for performance optimization in Laravel. The framework supports various cache drivers, including file, database, Redis, and Memcached.
Database Optimization: Database queries are often the bottleneck in web application performance. Laravel provides tools to optimize these queries.
Utilize Job Batching: Laravel’s job batching feature allows grouping multiple queue jobs into batches to process related tasks efficiently.
Queue Management: Laravel’s queue system offloads time-consuming tasks, ensuring better response times for users.
Route Caching: Route caching improves application performance by reducing the time taken to load routes.
Minifying Assets: Minification reduces the size of CSS, JavaScript, and other static files, improving page load times.
Database Connection Pooling: For high-traffic applications, use a database connection pool like PGBouncer (PostgreSQL) or MySQL’s connection pool for better connection reuse.
Laravel provides a solid foundation for building applications, but achieving top-notch performance requires fine-tuning. By applying these strategies, you can ensure your Laravel application delivers a fast, seamless experience to users.
Security vs Performance For Laravel

Implementing security measures in a Laravel application is crucial for protecting data, maintaining user trust, and adhering to regulations. However, these measures can sometimes impact performance. Understanding this trade-off helps in balancing security and performance effectively. Here’s a breakdown of how Laravel’s security measures can affect performance and visa-versa.
Security measures that affect performance
Input Validation and Sanitization: Laravel’s robust validation and sanitization ensure that user input is secure and free from malicious code. Validating and sanitizing every request can slightly increase processing time, especially with complex rules or high traffic.
Encryption and Hashing: Laravel provides built-in encryption (based on OpenSSL) and hashing mechanisms (bcrypt, Argon2) for storing sensitive data like passwords. Encryption and hashing are computationally intensive, especially for large datasets or real-time operations. Password hashing (e.g., bcrypt) is deliberately slow to deter brute force attacks.
Cross-Site Request Forgery (CSRF) Protection: Laravel automatically generates and verifies CSRF tokens to prevent unauthorized actions.
Performance Impact: Adding CSRF tokens to forms and verifying them for every request incurs minimal processing overhead.
Middleware for Authentication and Authorization: Laravel’s authentication guards and authorization policies enforce secure access controls. Middleware checks add processing steps for each request. In the case of high-traffic applications, this can slightly slow response times.
Secure File Uploads: Validating file types and scanning uploads for security risks adds overhead to file handling processes. Processing large files or using third-party scanning tools can delay response times.
Rate Limiting: Laravel’s Throttle Requests middleware prevents abuse by limiting the number of requests per user/IP. Tracking and validating request counts can introduce slight latency, especially under high traffic.
HTTPS Implementation: Enforcing HTTPS ensures secure communication but introduces a slight overhead due to SSL/TLS handshakes. SSL/TLS encryption can increase latency for each request.
Regular Dependency Updates: Updating Laravel and third-party packages reduces vulnerabilities but might temporarily slow down deployment due to additional testing. Updated libraries might introduce heavier dependencies or new processing logic.
Real-Time Security Monitoring: Tools like Laravel Telescope help monitor security events but may introduce logging overhead. Tracking every request and event can slow the application in real-time scenarios.
Performance optimization that affect security
Caching Sensitive Data:
Performance optimization frequently involves caching data to reduce query times and server load. Storing sensitive data in caches (e.g., session data, API tokens) can expose it to unauthorized access if not encrypted or secured. Shared caches in multi-tenant systems might lead to data leakage.
Reducing Validation and Sanitization:
To improve response times, developers may reduce or skip input validation and sanitization. This can expose applications to injection attacks (SQL, XSS) or allow malicious data to enter the system. Improperly sanitized inputs can lead to broken functionality or exploits.
Disabling CSRF Protection:
Some developers disable Cross-Site Request Forgery (CSRF) protection on high-traffic forms or APIs to reduce processing overhead. Without CSRF protection, attackers can execute unauthorized actions on behalf of authenticated users.
Using Raw Queries for Faster Database Access:
Raw SQL queries are often used for performance but bypass Laravel’s ORM protections. Raw queries can expose applications to SQL Injection attacks if inputs are not sanitized.
Skipping Middleware:
Performance optimization may involve bypassing or removing middleware, such as authentication or Rate limiting, to speed up request processing. Removing middleware can expose routes to unauthorized users or brute force attacks.
Disabling Logging:
To save disk space or reduce I/O operations, developers may disable or minimize logging. Critical security events (e.g., failed login attempts and unauthorized access) may go unnoticed, delaying response to breaches.
Implementing Aggressive Rate Limiting:
While Rate limiting is crucial for preventing abuse, overly aggressive limits might unintentionally turn off security mechanisms like CAPTCHA or block legitimate users. Attackers may exploit misconfigured limits to lock out users or bypass checks.
Over-Exposing APIs for Speed:
In a bid to optimize API response times, developers may expose excessive data or simplify access controls. Exposed sensitive fields in API responses can aid attackers. Insufficient access control can allow unauthorized access.
Using Outdated Libraries for Compatibility:
To avoid breaking changes and reduce the effort of updates, developers may stick to outdated Laravel versions or third-party packages. Older versions may contain known vulnerabilities. For faster encryption and decryption, developers might use less secure algorithms or lower encryption rounds. Weak encryption can be cracked more quickly, exposing sensitive data.
Tips To Balance Security and Performance
There are several options available to balance security and performance while developing a Laravel application. It is essential to strike a balance and develop a robust solution that is not vulnerable to hackers. Seek the help from the professionals, and hire Laravel developers from Acquaint Softttech who are experts at implementing a combination of strategies to obtain the perfect balance.
Layered Security Measures:
Instead of relying solely on one security layer, combine multiple measures:
Use middleware for authentication and authorization.
Apply encryption for sensitive data.
Implement Rate limiting to prevent brute force attacks.
Optimize Middleware Usage:
Middleware in Laravel is a powerful tool for enforcing security without affecting performance excessively. Prioritize middleware execution:
Use route-specific middleware instead of global middleware when possible.
Optimize middleware logic to minimize resource consumption.
Intelligent Caching Strategies:
Cache only what is necessary to avoid stale data issues:
Implement cache invalidation policies to ensure updated data.
Use tags to manage grouped cache items effectively.
Regular Vulnerability Testing:
Conduct penetration testing and code reviews to identify vulnerabilities. Use tools like:
Laravel Debugbar for performance profiling.
OWASP ZAP for security testing.
Enable Logging and Monitoring:
Laravel’s logging capabilities provide insights into application performance and potential security threats:
Use Monolog to capture and analyze logs.
Monitor logs for unusual activity that may indicate an attack.
Implement Rate Limiting:
Laravel’s Rate limiting protects APIs from abuse while maintaining performance:
Use ThrottleRequests middleware to limit requests based on IP or user ID.
Adjust limits based on application needs.
Leverage API Gateway:
An API gateway can act as a security and performance intermediary:
Handle authentication, authorization, and Rate limiting at the gateway level.
Cache responses to reduce server load.
Use Load Balancing and Scaling:
Distribute traffic across multiple servers to enhance both security and performance:
Implement load balancers with SSL termination for secure connections.
Use horizontal scaling to handle increased traffic.
Employ CDN for Static Content:
Offload static resources to a content delivery network:
Reduce server load by serving images, CSS, and JavaScript via CDN.
Enhance security with HTTPS encryption on CDN.
Harden Server Configuration:
Ensure server security without sacrificing performance:
Use firewalls and intrusion detection systems.
Optimize PHP and database server configurations for maximum efficiency.
Placing trust in a Laravel development company for the development of your custom solution will go a long way ensuring you build a top-notch solution.
Future Trends in Laravel Security and Performance
As Laravel evolves, so do the tools and technologies to achieve the delicate balance between security and performance. Trust a software development outsourcing company like Acquaint Softtech for secure and future-proof solutions. Besides being an official Laravel partner, our developers also stay abreast with the current technologies.
Future trends include:
AI-Powered Security: AI-driven security tools can automatically detect and mitigate threats in Laravel applications. These tools enhance security without adding significant overhead.
Edge Computing: Processing data closer to the user reduces latency and enhances performance. Laravel developers can leverage edge computing for better scalability and security.
Advanced Caching Mechanisms: Next-generation caching solutions like in-memory databases (e.g., RedisGraph) will enable even faster data retrieval.
Zero-Trust Architecture: Zero-trust models are gaining popularity to enhance security in Laravel applications. This approach treats all traffic as untrusted, ensuring stricter access controls.
Quantum-Resistant Encryption: With advancements in quantum computing, Laravel applications may adopt quantum-resistant encryption algorithms to future-proof security.
Hire remote developers from Acquaint Softtech to implement these strategies. We follow the security best practices and have extensive experience creating state-of-the-art applications that are both secure and high performing. This ensures a smooth and safe user experience.
Conclusion
Balancing security and performance in Laravel development is a challenging yet achievable task. By leveraging Laravel’s built-in features, adopting Laravel security best practices, and staying updated on emerging trends, developers can create applications that are both secure and high-performing.
The key is to approach security and performance as complementary aspects rather than competing priorities. Take advantage of the Laravel development services at Acquaint Softtech. We can deliver robust, scalable, and efficient applications that meet modern user expectations.
1 note
·
View note
Text
The Ultimate Guide to Mastering Power BI: A Comprehensive Course by Zabeel Institute
In today's data-driven world, businesses are constantly seeking ways to leverage data for better decision-making. One of the most powerful tools to achieve this is Microsoft Power BI, a business analytics solution that empowers organizations to visualize their data, share insights, and make data-driven decisions in real time. If you're looking to gain expertise in this powerful tool, Zabeel Institute's Power BI course in Dubai is the perfect starting point.
What is Power BI?
Power BI is a suite of business analytics tools that allows users to analyze data and share insights. With its user-friendly interface and robust capabilities, Power BI enables both beginners and seasoned professionals to create interactive dashboards and reports. Whether you're dealing with simple data sets or complex analytics, Power BI makes data visualization intuitive and accessible.
Why Learn Power BI?
Learning Power BI opens up a world of opportunities. As businesses increasingly rely on data to drive their decisions, professionals skilled in Power BI are in high demand. Here are some compelling reasons why you should consider enrolling in a Power BI course:
High Demand for Power BI Skills: With the rise of data-driven decision-making, there is a growing demand for professionals who can interpret and visualize data effectively.
Career Advancement: Mastering Power BI can significantly enhance your career prospects, especially in fields such as data analysis, business intelligence, and management.
Versatility: Power BI is versatile and can be applied across various industries, including finance, healthcare, marketing, and more.
Improved Decision-Making: By learning how to create detailed and interactive reports, you can help your organization make informed decisions based on real-time data.
Course Overview: Analyzing Data with Microsoft Power BI
At Zabeel Institute, the Analyzing Data with Microsoft Power BI course is designed to equip you with the skills needed to harness the full potential of Power BI. This comprehensive course covers everything from the basics to advanced data visualization techniques.
1. Introduction to Power BI
The course begins with an introduction to the Power BI environment. You'll learn about the Power BI service, Power BI Desktop, and how to navigate through these tools efficiently. Understanding the interface is crucial for leveraging the full capabilities of Power BI.
2. Connecting to Data Sources
Power BI allows you to connect to a wide range of data sources, including Excel, SQL Server, Azure, and many more. In this module, you'll learn how to import data from various sources and prepare it for analysis.
3. Data Transformation and Cleaning
Before you can visualize your data, it often needs to be cleaned and transformed. This section of the course will teach you how to use Power Query to shape and clean your data, ensuring it's ready for analysis.
4. Creating Data Models
Data modeling is a crucial step in the data analysis process. In this module, you'll learn how to create relationships between different data sets and build a robust data model that supports your analysis.
5. Building Interactive Dashboards
One of Power BI's strengths is its ability to create interactive dashboards. You'll learn how to design visually appealing dashboards that provide meaningful insights at a glance.
6. Advanced Data Visualizations
Once you're comfortable with the basics, the course delves into more advanced visualizations. You'll explore custom visuals, R and Python integration, and how to create sophisticated reports that stand out.
7. DAX (Data Analysis Expressions)
DAX is a powerful formula language in Power BI. This section covers the fundamentals of DAX, enabling you to perform complex calculations and create dynamic reports.
8. Power BI Service and Collaboration
Power BI is not just about creating reports—it's also about sharing and collaborating on those reports. You'll learn how to publish your reports to the Power BI service, set up security, and collaborate with your team.
9. Power BI Mobile App
In today's mobile world, being able to access your reports on the go is essential. The course will show you how to use the Power BI Mobile App to view and interact with your dashboards from anywhere.
10. Best Practices for Power BI
To ensure you're getting the most out of Power BI, the course concludes with a module on best practices. This includes tips on performance optimization, report design, and maintaining data security.
Why Choose Zabeel Institute?
When it comes to learning Power BI, choosing the right institute is crucial. Zabeel Institute stands out for several reasons:
Experienced Instructors: Zabeel Institute's instructors are industry experts with years of experience in data analysis and business intelligence.
Hands-On Training: The course is designed to be highly practical, with plenty of hands-on exercises to reinforce your learning.
Industry-Recognized Certification: Upon completion, you'll receive a certification that is recognized by employers globally, giving you an edge in the job market.
Flexible Learning Options: Whether you prefer in-person classes or online learning, Zabeel Institute offers flexible options to suit your schedule.
Real-World Applications of Power BI
Understanding Power BI is one thing, but knowing how to apply it in the real world is what truly matters. Here are some examples of how Power BI can be used across various industries:
Finance: Create detailed financial reports and dashboards that track key metrics such as revenue, expenses, and profitability.
Healthcare: Analyze patient data to improve healthcare delivery and outcomes.
Retail: Track sales data, customer trends, and inventory levels in real time.
Marketing: Measure the effectiveness of marketing campaigns by analyzing data from multiple channels.
Human Resources: Monitor employee performance, track recruitment metrics, and analyze workforce trends.
Success Stories: How Power BI Transformed Businesses
To illustrate the impact of Power BI, let's look at a few success stories:
Company A: This retail giant used Power BI to analyze customer purchasing behavior, resulting in a 15% increase in sales.
Company B: A financial services firm leveraged Power BI to streamline its reporting process, reducing the time spent on report generation by 50%.
Company C: A healthcare provider used Power BI to track patient outcomes, leading to improved patient care and reduced readmission rates.
Mastering Power BI is not just about learning a tool—it's about acquiring a skill that can transform the way you work with data. Whether you're looking to advance your career, enhance your business's decision-making capabilities, or simply stay ahead in today's data-driven world, Zabeel Institute's Power BI course is the perfect choice.
Don't miss out on the opportunity to learn from the best. Enroll in Zabeel Institute's Power BI course today and take the first step towards becoming a Power BI expert.
Ready to transform your career with Power BI? Enroll in Zabeel Institute's Power BI course now and start your journey towards mastering data analysis and visualization. Visit Zabeel Institut for more information.
2 notes
·
View notes
Text
Optimizing Business Operations with Advanced Machine Learning Services
Machine learning has gained popularity in recent years thanks to the adoption of the technology. On the other hand, traditional machine learning necessitates managing data pipelines, robust server maintenance, and the creation of a model for machine learning from scratch, among other technical infrastructure management tasks. Many of these processes are automated by machine learning service which enables businesses to use a platform much more quickly.
What do you understand of Machine learning?
Deep learning and neural networks applied to data are examples of machine learning, a branch of artificial intelligence focused on data-driven learning. It begins with a dataset and gains the ability to extract relevant data from it.
Machine learning technologies facilitate computer vision, speech recognition, face identification, predictive analytics, and more. They also make regression more accurate.
For what purpose is it used?
Many use cases, such as churn avoidance and support ticket categorization make use of MLaaS. The vital thing about MLaaS is it makes it possible to delegate machine learning's laborious tasks. This implies that you won't need to install software, configure servers, maintain infrastructure, and other related tasks. All you have to do is choose the column to be predicted, connect the pertinent training data, and let the software do its magic.
Natural Language Interpretation
By examining social media postings and the tone of consumer reviews, natural language processing aids businesses in better understanding their clientele. the ml services enable them to make more informed choices about selling their goods and services, including providing automated help or highlighting superior substitutes. Machine learning can categorize incoming customer inquiries into distinct groups, enabling businesses to allocate their resources and time.
Predicting
Another use of machine learning is forecasting, which allows businesses to project future occurrences based on existing data. For example, businesses that need to estimate the costs of their goods, services, or clients might utilize MLaaS for cost modelling.
Data Investigation
Investigating variables, examining correlations between variables, and displaying associations are all part of data exploration. Businesses may generate informed suggestions and contextualize vital data using machine learning.
Data Inconsistency
Another crucial component of machine learning is anomaly detection, which finds anomalous occurrences like fraud. This technology is especially helpful for businesses that lack the means or know-how to create their own systems for identifying anomalies.
Examining And Comprehending Datasets
Machine learning provides an alternative to manual dataset searching and comprehension by converting text searches into SQL queries using algorithms trained on millions of samples. Regression analysis use to determine the correlations between variables, such as those affecting sales and customer satisfaction from various product attributes or advertising channels.
Recognition Of Images
One area of machine learning that is very useful for mobile apps, security, and healthcare is image recognition. Businesses utilize recommendation engines to promote music or goods to consumers. While some companies have used picture recognition to create lucrative mobile applications.
Your understanding of AI will drastically shift. They used to believe that AI was only beyond the financial reach of large corporations. However, thanks to services anyone may now use this technology.
2 notes
·
View notes