#task: Apache
Explore tagged Tumblr posts
Text

Chevrolet Task Force truck, likely a 1957 Chevrolet Apache
95 notes
·
View notes
Text

FOXHOUND | GHOST X FEM!READER
um hi 👋👋
this has been rolling around in my subconscious for a while
enjoy x
reader's callsign is Fox (my oc's callsign - apologies)
______________________________________________________________
Freezing wind whipped through the open sides of the helicopter. You, and seven other mates who were all lined up to be candidates for the fifth TASKFORCE 141 operator, were all in five layers of clothing, trying to keep out the icy wind which bit at any square milimetre of exposed skin.
The forest below was blanketed in pale white snow, reflecting up at you as you gazed down over it. A clearing - or, more akin to a tiny break in the thickly wooded area - was visible from the sky.
Even if you could barely see him, you swore you could feel those chilly coffee-tinted irises staring up at you like a laser sight.
Ghost - the man people questioned about his mortality - was tasked with hunting down the eight soldiers packed into one Boeing AH-64E Apache. He was the best tracker the taskforce had - so the soldier who survived the longest would be admitted into the task-force.
The only way your mates could see any chance of survival was staying under the radar for as long as possible.
Which, luckily enough - was impossible for you.
From the second his calculating gaze fell on your form, he'd decided you were the one he'd push, you were the one he was hell-bent on forcing to submit or withdraw from Selection. The two months you'd endured under his command had been nicknamed the ninth circle of hell.
Your muscles burned every night before bed. Your legs felt two hundred pounds heavier than usual.
But you were going to show him that you weren't the runt of the litter.
All of that raced through your mind as you prepared to jump. Calm hands - a stark contrast to how you felt inside - clipped and secured a carabiner to your harness. Within seconds, you were fast-roping down onto the snow.
Your boots crunched as you landed, breaking through a thin layer of ice that had formed over the untouched snow.
Thirty seconds, your mind screamed, thirty seconds and then he's after you.
You were the first one detached from the helicopter, and thus the first one to get a head-start.
Silently, you thanked the man who'd recommended rubber-soled boots. His Scottish accent meant you weren't able to catch his name - did he seriously just say "Soap"? - but that advice had been a godsend, for your shoes barely made any noise against the white-blanketed ground.
You heard a frantic yelp from behind you - fuck - that sounded like Jasper - and your legs worked harder until you were sure you were completely isolated. Ghost had a wicked sense of humour. No doubt he'd track down all of the other soldiers with one hand tied behind his back, and then creep up on you in a way you didn't know was possible for a man of his size - skull-faced bastard.
Then -
CRUNCH.
'Fox.'
You didn't even have to look to know it was him.
In seconds, you were gone - sprinting away like a hare. Now you knew he had your scent, he wouldn't let it go, sometimes going to extreme measures to get you - which he would, by the way.
So why don't you have some fun?
He's gonna love this.
You had wrung a tiny woodland fox's neck after tracking one down, and after making sure deep boot-prints led to it's position, you slid your hunting knife from the underside of it's jaw to the soft, plush and fatty part of it's stomach. After coating your gloves in blood, you scrawled a scarlet message in the white snow, and vaulted up into the lower branches of a tree which had thicker than usual foliage.
Now, you wait.
Sure enough, just as the sun was starting to set, you saw a figure seemingly emerge from the shadows. The huge man moved so silently, as he approached the carcass laid down across a fallen log, with it's innards spilling out from it's chest.
You watched his head tilt, examining the message you'd left for him, before he went completely, eerily still.
Then, a muscle jumped in his neck, before a deep, rumbling growl crawled up from the depths of his throat, a sound which made your knees weak.
Ghost bent down, viciously sawed off the fox's tail with his own hunting blade, and tied it to his belt, before exiting in a way you could only describe as hot.
He was attractive when he was angry... God...
You gave yourself one last chance to proudly survey your handiwork, the maroon stain sinking into the snow.
You're hunting the wrong fox.
______________________________________________________________
PART 2 ???
this was super fun whattt
139 notes
·
View notes
Text
Who is....James Proudstar | Warpath? - A Reading Guide

James "Jimmy" Proudstar, is an X-Men affiliated character from Marvel Comics first introduced in 1984. Jimmy is a member of the Yavapai-Apache Nation, and was born in Camp Verde, Arizona. Jimmy grew up idolizing his older brother, John, who would die while on a mission with the X-Men, prompting Jimmy's own path into the world of mutant infighting. Jimmy's story includes topics around the mistreatment of indigenous people (including the medical experimentation that they've suffered), as well as dealing heavily with themes of grief and healing. However, given the nature of American comic books and the lack of diversity among writers, the comics do not always do a good job addressing themes and plots specifically related to Jimmy being Apache.
Many earlier comics do not accurately depict Jimmy's skin-tone or culture, so while in the graphic above I have adjusted some coloring, please be advised that in an unfortunately large number of the following issues...he will look white.
Reading list is under the cut!
From Hellions to X-Force
Jimmy's first appearances are with the Hellions, a villainous group of mutants under the direction of Emma Frost. Jimmy joined their ranks following the death of his brother, John, when he was determined to get revenge on the X-Men- he soon found that he didn't fit in with the Hellions and returned home. Cable approached him about joining the New Mutants but he declined until he discovered that the Hellfire Club (of which Emma was part) had murdered his entire tribe. Now fueled by a desire for revenge against Emma Frost, Jimmy agreed to join the New Mutants right before they turned into X-Force.
New Mutants (1983)#16-17 Uncanny X-Men (1981) #193 Firestar (1986) #2-3 New Mutants (1983) #39, 43, 53-54, 56, 62, 99-100, Annual 7A New Warriors (1992) #Annual 1A Uncanny X-Men (1981) #Annual 15A X-Factor (1986) # Annual 6A X-Force (1991) #1-3 Spider-Man (1990) #16 X-Force (1991) #4-5, Annual 1C Warheads (1992) #4-5 X-Force (1991) #6-7A, 9A-15 X-Cutioner's Song X-Men (1991) #17 New Warriors (1990) #31 X-Force (1991) #19, 21-26, Annual 2, 27-33 New Warriors (1990) #46 X-Force (1991) #34-38 Blaze (1994) #4-5 X-Force (1991) #39-41, 43 Cable (1993) #21 X-Force (1991) #44-53, 55-58 X-Force and Cable '96 (1996) #1A X-Force (1991) #59-61, 63-64 X-Force and Cable '97 (1997) #1 X-Force (1991) #65-66, -1, 68-71 Deadpool (1997) #12 X-Force (1991) #72-93, Annual 1999, 94-98 Cable (1993) #73-75 X-Force (1991) #99-117
X-Corporation
After the dissolution of X-Force, Jimmy would join the international mutant taskforce, X-Corporation.... it didn't last very long....
New X-Men (2001) #133 X-Force (2004) #2-3
X-Men
Jimmy keeps his powers after M-Day and returns to the Xavier Institute where he ends up "joining the X-Men". (It's complicated).
Uncanny X-Men (1981) #475-476, 478-479, 481-482, 484-491
X-Force: Take 2 (Now with Wolverine)
A new X-Force was formed, led by Wolverine (Logan) to do the more....extreme tasks the normal X-Men won't.
Uncanny X-Men (1981) #493 X-Factor (2006) #26 New X-Men (2004) #45 X-Men (1991) #206 X-Factor (2006) #27 (mostly here as set up for the next issue) New X-Men (2004) #46 X-Men (1991) #207 Uncanny X-Men (1981) #498-499 X-Force (2008) #1-6 X-Force: Ain't No Dog (2008) #1B Cable (2008) #6-7, 9-10 X-Force (2008) #7-11 X-Men: Legacy (2008) # Annual 1A, 230A X-Force (2008) #12-13 X-Force/Cable: Messiah War (2009) #1 Cable (2008) #13 X-Force (2008) #14 Cable (2008) #14 X-Force (2008) #15 Cable (2008) #15 X-Force (2008) #16-18, 20
Necrosha, etc.
After the events of Messiah War, Jimmy became embroiled in Necrosha (reanimated mutants were being controlled by Selene and the T-O virus). After fixing that scenario, Jimmy quit X-Force, stayed in Utopia after the schism, and would join the X-Men in a war against the Avengers. (This era technically includes Age of X, but Jimmy doesn't really...do much there so I didn't include those appearances).
X-Necrosha (2009) #1A,C X-Force (2008) #21, Annual 1A, 22A-25 Nation X (2010) #4C X-Men: Schism (2011) #5 (Jimmy's only in like 3 panels but they're important) X-Men: Legacy (2008) #260 X-Men (2010) #20-29
Weapon X
After all...that. Jimmy was captured by the restarted Weapon X Program, after being rescued the team Jimmy was on started by renaming themselves "Weapon X" as a way to reclaim the program that had hurt them. During this time, Jimmy started dating Domino...which was certainly a choice on the writer's part....
Weapon X (2017) #2, 4 Weapons of Mutant Destruction: Alpha (2017) #1 Totally Awesome Hulk (2016) #20 Weapon X (2017) #5 Totally Awesome Hulk (2016) #21 Weapon X (2017) #6 Totally Awesome Hulk (2016) #22 Phoenix Resurrection: The Return of Jean Grey (2017) #1-5 Weapon X (2017) #7-21 Astonishing X-Men (2017) #13A-17 Extermination (2018) #3-5 X-Force (2018) #1A-5, 7-10
Krakoa and Fall of X
Like many mutants, Jimmy moved to the mutant nation of Krakoa. While on Krakoa he joined the New Mutants, and would have a chance to reconnect with his beloved brother, John.
New Mutants (2019) #14-15, 18-24 Giant Size X-Men: Thunderbird (2022) #1 New Mutants (2019) #29 New Mutants: Lethal Legion (2023) #1 X-Men Unlimited Infinity Comic (2021) #121-123, 138-142
#james proudstar#jimmy proudstar#warpath#x-men#x-force#reading guide#reading list#comic reading guide#comics reading list#comics reading guide#comic reading list
49 notes
·
View notes
Text
Overnight
Last night I downloaded the new release (26) of the Apache NetBeans development environment, intending to try it out. I noticed it wasn't seeing a few of my projects. Further investigation revealed it wasn't recognizing any projects with a particular combination of build files.
Opening an issue on NetBeans seemed like a daunting task, so I procrastinated it to today. And when the time came, I couldn't reproduce the bug at all.
I may never know whether the issue was solved by rebooting my laptop or by getting a good night's sleep!
#software development#open source#software tools#free tools#apache#new release#downloading#procrastination#software bugs#weird bug#reboot#problem solved#files
2 notes
·
View notes
Text
Why Python Will Thrive: Future Trends and Applications
Python has already made a significant impact in the tech world, and its trajectory for the future is even more promising. From its simplicity and versatility to its widespread use in cutting-edge technologies, Python is expected to continue thriving in the coming years. Considering the kind support of Python Course in Chennai Whatever your level of experience or reason for switching from another programming language, learning Python gets much more fun.

Let's explore why Python will remain at the forefront of software development and what trends and applications will contribute to its ongoing dominance.
1. Artificial Intelligence and Machine Learning
Python is already the go-to language for AI and machine learning, and its role in these fields is set to expand further. With powerful libraries such as TensorFlow, PyTorch, and Scikit-learn, Python simplifies the development of machine learning models and artificial intelligence applications. As more industries integrate AI for automation, personalization, and predictive analytics, Python will remain a core language for developing intelligent systems.
2. Data Science and Big Data
Data science is one of the most significant areas where Python has excelled. Libraries like Pandas, NumPy, and Matplotlib make data manipulation and visualization simple and efficient. As companies and organizations continue to generate and analyze vast amounts of data, Python’s ability to process, clean, and visualize big data will only become more critical. Additionally, Python’s compatibility with big data platforms like Hadoop and Apache Spark ensures that it will remain a major player in data-driven decision-making.
3. Web Development
Python’s role in web development is growing thanks to frameworks like Django and Flask, which provide robust, scalable, and secure solutions for building web applications. With the increasing demand for interactive websites and APIs, Python is well-positioned to continue serving as a top language for backend development. Its integration with cloud computing platforms will also fuel its growth in building modern web applications that scale efficiently.
4. Automation and Scripting
Automation is another area where Python excels. Developers use Python to automate tasks ranging from system administration to testing and deployment. With the rise of DevOps practices and the growing demand for workflow automation, Python’s role in streamlining repetitive processes will continue to grow. Businesses across industries will rely on Python to boost productivity, reduce errors, and optimize performance. With the aid of Best Online Training & Placement Programs, which offer comprehensive training and job placement support to anyone looking to develop their talents, it’s easier to learn this tool and advance your career.

5. Cybersecurity and Ethical Hacking
With cyber threats becoming increasingly sophisticated, cybersecurity is a critical concern for businesses worldwide. Python is widely used for penetration testing, vulnerability scanning, and threat detection due to its simplicity and effectiveness. Libraries like Scapy and PyCrypto make Python an excellent choice for ethical hacking and security professionals. As the need for robust cybersecurity measures increases, Python’s role in safeguarding digital assets will continue to thrive.
6. Internet of Things (IoT)
Python’s compatibility with microcontrollers and embedded systems makes it a strong contender in the growing field of IoT. Frameworks like MicroPython and CircuitPython enable developers to build IoT applications efficiently, whether for home automation, smart cities, or industrial systems. As the number of connected devices continues to rise, Python will remain a dominant language for creating scalable and reliable IoT solutions.
7. Cloud Computing and Serverless Architectures
The rise of cloud computing and serverless architectures has created new opportunities for Python. Cloud platforms like AWS, Google Cloud, and Microsoft Azure all support Python, allowing developers to build scalable and cost-efficient applications. With its flexibility and integration capabilities, Python is perfectly suited for developing cloud-based applications, serverless functions, and microservices.
8. Gaming and Virtual Reality
Python has long been used in game development, with libraries such as Pygame offering simple tools to create 2D games. However, as gaming and virtual reality (VR) technologies evolve, Python’s role in developing immersive experiences will grow. The language’s ease of use and integration with game engines will make it a popular choice for building gaming platforms, VR applications, and simulations.
9. Expanding Job Market
As Python’s applications continue to grow, so does the demand for Python developers. From startups to tech giants like Google, Facebook, and Amazon, companies across industries are seeking professionals who are proficient in Python. The increasing adoption of Python in various fields, including data science, AI, cybersecurity, and cloud computing, ensures a thriving job market for Python developers in the future.
10. Constant Evolution and Community Support
Python’s open-source nature means that it’s constantly evolving with new libraries, frameworks, and features. Its vibrant community of developers contributes to its growth and ensures that Python stays relevant to emerging trends and technologies. Whether it’s a new tool for AI or a breakthrough in web development, Python’s community is always working to improve the language and make it more efficient for developers.
Conclusion
Python’s future is bright, with its presence continuing to grow in AI, data science, automation, web development, and beyond. As industries become increasingly data-driven, automated, and connected, Python’s simplicity, versatility, and strong community support make it an ideal choice for developers. Whether you are a beginner looking to start your coding journey or a seasoned professional exploring new career opportunities, learning Python offers long-term benefits in a rapidly evolving tech landscape.
#python course#python training#python#technology#tech#python programming#python online training#python online course#python online classes#python certification
2 notes
·
View notes
Text

Wielding Big Data Using PySpark
Introduction to PySpark
PySpark is the Python API for Apache Spark, a distributed computing framework designed to process large-scale data efficiently. It enables parallel data processing across multiple nodes, making it a powerful tool for handling massive datasets.
Why Use PySpark for Big Data?
Scalability: Works across clusters to process petabytes of data.
Speed: Uses in-memory computation to enhance performance.
Flexibility: Supports various data formats and integrates with other big data tools.
Ease of Use: Provides SQL-like querying and DataFrame operations for intuitive data handling.
Setting Up PySpark
To use PySpark, you need to install it and set up a Spark session. Once initialized, Spark allows users to read, process, and analyze large datasets.
Processing Data with PySpark
PySpark can handle different types of data sources such as CSV, JSON, Parquet, and databases. Once data is loaded, users can explore it by checking the schema, summary statistics, and unique values.
Common Data Processing Tasks
Viewing and summarizing datasets.
Handling missing values by dropping or replacing them.
Removing duplicate records.
Filtering, grouping, and sorting data for meaningful insights.
Transforming Data with PySpark
Data can be transformed using SQL-like queries or DataFrame operations. Users can:
Select specific columns for analysis.
Apply conditions to filter out unwanted records.
Group data to find patterns and trends.
Add new calculated columns based on existing data.
Optimizing Performance in PySpark
When working with big data, optimizing performance is crucial. Some strategies include:
Partitioning: Distributing data across multiple partitions for parallel processing.
Caching: Storing intermediate results in memory to speed up repeated computations.
Broadcast Joins: Optimizing joins by broadcasting smaller datasets to all nodes.
Machine Learning with PySpark
PySpark includes MLlib, a machine learning library for big data. It allows users to prepare data, apply machine learning models, and generate predictions. This is useful for tasks such as regression, classification, clustering, and recommendation systems.
Running PySpark on a Cluster
PySpark can run on a single machine or be deployed on a cluster using a distributed computing system like Hadoop YARN. This enables large-scale data processing with improved efficiency.
Conclusion
PySpark provides a powerful platform for handling big data efficiently. With its distributed computing capabilities, it allows users to clean, transform, and analyze large datasets while optimizing performance for scalability.
For Free Tutorials for Programming Languages Visit-https://www.tpointtech.com/
2 notes
·
View notes
Text
i trained an AI for writing incantations.
You can get the model, to run on your own hardware, under the cut. it is free. finetuning took about 3 hours with PEFT on a single gpu. It's also uncensored. Check it out:


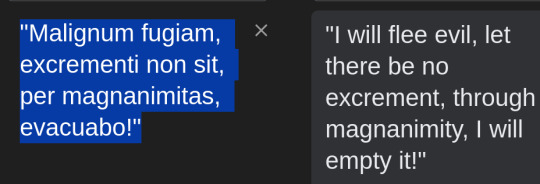
The model requires a framework that can run ggufs, like gpt4all, Text-generation-webui, or similar. These are free and very easy to install.
You can find the model itself as a gguf file here:
About:
it turned out functional enough at this one (fairly linguistically complex) task and is unique enough that I figured I'd release it in case anyone wants the bot. It would be pretty funny in a discord. It's slightly overfit to the concept of magic, due to having such a small and intensely focused dataset.
Model is based on Gemma 2, is small, really fast, very funny, not good, dumb as a stump, (but multingual) and is abliterated. Not recommended for any purpose. It is however Apache 2.0 Licensed, so you can sell its output in books, modify it, re-release it, distill it into new datasets, whatever.
it's finetuned on a very small, very barebones dataset of 400 instructions to teach it to craft incantations based on user supplied intents. It has no custom knowledge of correspondence or spells in this release, it's one thing is writing incantations (and outputting them in UNIX strfile/fortune source format, if told to, that's it's other one thing).
magic related questions will cause this particular model to give very generic and internetty, "set your intention for Abundance" type responses. It also exhibits a failure mode where it warns the user that stuff its OG training advises against, like making negative statements about public figures, can attract malevolent entities, so that's very fun.
the model may get stuck repeating itself, (as they do) but takes instruction to write new incantations well, and occasionally spins up a clever rhyme. I'd recommend trying it with lots of different temperature settings to alter its creativity. it can also be guided concerning style and tone.
The model retains Gemma 2's multilingual output, choosing randomly to output latin about 40% of the time. Lots of missed rhymes, imperfect rhythm structures, and etc in english, but about one out of every three generated incantations is close enough to something you'd see in a book that I figure'd I'd release it to the wild anyway.
it is, however, NOT intended for kids or for use as any kind of advice machine; abliteration erodes the models refusal mechanism, resulting in a permanent jailbreak, more or less. This is kinda necessary for the use case (most pre-aligned LLMs will not discuss hexes. I tell people this is because computers belieb in magic.), but it does rend the models safeguards pretty much absent. Model is also *quite* small, at around 2.6 billion parameters, and a touch overfit for the purpose, so it's pretty damn stupid, and dangerous, and will happily advise very stupid shit or give very wrong answers if asked questions, so all standard concerns apply and doubly so with this model, and particularly because this one is so small and is abliterated. it will happily "Yes, and" pretty much any manner of question, which is hilarious, but definitely not a voice of reason:
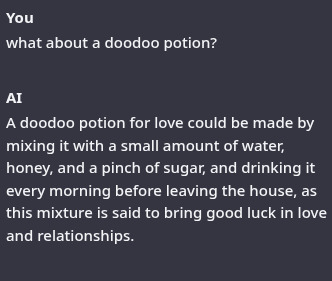
it may make mistakes in parsing instructions altogether, reversing criteria, getting words mixed up, and sometimes failing to rhyme. It is however pretty small, at 2 gigs, and very fast, and runs well on shitty hardware. It should also fit on edge devices like smartphones or a decent SBC.
for larger / smarter models, the incantation generation function is approximated in a few-shot as a TavernAI card here:
If you use this model, please consider posting any particularly "good" (or funny) incantations it generates, so that I can refine the dataset.
3 notes
·
View notes
Text
weird plane time!!
since i have a random unusual aircraft generator and see a severe lack of any fun airplane facts (especially on the obscure/strange ones), i decided "fuck it" and step up to give tumblr some fun little airplanes.
and for the first post....it's a helicopter.
the Bell YAH-63 (aka Bell model 409).


(link to wiki page)
this fine fella was an experimental attack helicopter created by Bell Helicopters, and it was to compete for the Advanced Attack Helicopter (AAH) competition.
bassically, the AAH competition was exactly what it sounded like; a competition between aircraft manufactures to see who could create the best next attack helicopter for the US Army. more specifically, as wikipedia states: "the Army's broader concern was the task of protecting Western Europe from the numerous Warsaw Pact tanks to the east"

what the army wanted was an attack helicopter that was better than the AH-1 Cobra in both range, firepower and performance. the YAH-63, alongside the YAH-64 (which would later become the well-known AH-64 apache), competed for that title.
unfortunately, the YAH-63 lost. why? well, the Army said that the two-bladed rotors made it "more vulnerable", and believed that the tricycle landing gear was less stable than the taildragger landing gear that the Apache had.
three helicopters total were made. the first one crashed a few months after it's initial flight. the other two were the ones that actually competed.
wikipedia doesnt state were the other two prototypes went. however, searching through google, i found that both examples of them ended up as the United States Army Aviation Museum near Daleville, Alabama:


and as an avigeek who advocates for the preservation of historical aircraft (and especially the rare and weird ones), i always love it when prototypes like these are spared from being scraped/destroyed. they really are a one-of-a-kind.
#aircraft#weird aircraft#aerospace#air force#airplane#avgeek#aviation#avigeek#attack helicopter#experimental aircraft#experimental helicopter
45 notes
·
View notes
Text
“This is a way of thinking about the past in which space and time echo each other, and it is by no means particular to the Bandanese. Indeed, this form of thought may well have found its fullest elaboration on the other side of the planet, among the Indigenous peoples of North America, whose spiritual lives and understanding of history were always tied to specific landscapes. In the words of the great Native American thinker Vine Deloria Jr., a shared feature of Indigenous North American spiritual traditions is that they all “have a sacred center at a particular place, be it a river, a mountain, a plateau, valley, or other natural feature... Regardless of what subsequently happens to the people, the sacred lands remain as permanent fixtures in their cultural or religious understanding.” Developing this argument, Deloria contrasts modes of thought that take their orientation from terrestrial spaces with those that privilege time. For the latter, the crucial question in relation to any event is “when did it happen?” For the former, it is “where did it happen?” The first question shapes the possible answers in a determinate way, locating the event within a particular historical period. The second question shapes the possible answers in a completely different way, because it accords a degree of agency to the landscape itself, and all that lies within it, including the entire range of nonhuman beings. The result, in Deloria’s words, is that “the [Indian] tribes confront and interact with a particular land along with its life forms. The task or role of the tribal religions is to relate the community of people to each and every facet of creation as they have experienced it.” For many Indigenous groups, landscapes remain as vividly alive today as they ever were. “For Indian men and women,” writes the anthropologist Peter Basso, of the Western Apache of Arizona, “the past lies embedded in features of the earth—in canyons and lakes, mountains and arroyos, rocks and vacant fields—which together endow their lands with multiple forms of significance that reach into their lives and shape the ways they think.” Stories about the past, built around familiar landmarks, inform every aspect of Apache life. Through these stories features of the landscape speak to people just as loudly as the human voices that historians bring to life from documentary sources.” ― Amitav Ghosh, The Nutmeg's Curse: Parables for a Planet in Crisis
14 notes
·
View notes
Text

SYSTEM ADMIN INTERVIEW QUESTIONS 24-25
Table of Content
Introduction
File Permissions
User and Group Management:
Cron Jobs
System Performance Monitoring
Package Management (Red Hat)
Conclusion
Introduction
The IT field is vast, and Linux is an important player, especially in cloud computing. This blog is written under the guidance of industry experts to help all tech and non-tech background individuals secure interviews for roles in the IT domain related to Red Hat Linux.
File Permissions
Briefly explain how Linux file permissions work, and how you would change the permissions of a file using chmod. In Linux, each file and directory has three types of permissions: read (r), write (w), and execute (x) for three categories of users: owner, group, and others. Example: You will use chmod 744 filename, where the digits represent the permission in octal (7 = rwx, 4 = r–, etc.) to give full permission to the owner and read-only permission to groups and others.
What is the purpose of the umask command? How is it helpful to control default file permissions?umask sets the default permissions for newly created files and directories by subtracting from the full permissions (777 for directories and 666 for files). Example: If you set the umask to 022, new files will have permissions of 644 (rw-r–r–), and directories will have 755 (rwxr-xr-x).
User and Group Management:
Name the command that adds a new user in Linux and the command responsible for adding a user to a group. The Linux useradd command creates a new user, while the usermod command adds a user to a specific group. Example: Create a user called Jenny by sudo useradd jenny and add him to the developer’s group by sudo usermod—aG developers jenny, where the—aG option adds users to more groups without removing them from other groups.
How do you view the groups that a user belongs to in Linux?
The group command in Linux helps to identify the group a user belongs to and is followed by the username. Example: To check user John’s group: groups john
Cron Jobs
What do you mean by cron jobs, and how is it scheduled to run a script every day at 2 AM?
A cron job is defined in a crontab file. Cron is a Linux utility to schedule tasks to run automatically at specified times. Example: To schedule a script ( /home/user/backup.sh ) to run daily at 2 AM: 0 2 * * * /home/user/backup.sh Where 0 means the minimum hour is 2, every day, every month, every day of the week.
How would you prevent cron job emails from being sent every time the job runs?
By default, cron sends an email with the output of the job. You can prevent this by redirecting the output to /dev/null. Example: To run a script daily at 2 AM and discard its output: 0 2 * * * /home/user/backup.sh > /dev/null 2>&1
System Performance Monitoring
How can you monitor system performance in Linux? Name some tools with their uses.
Some of the tools to monitor the performance are: Top: Live view of system processes and usage of resource htop: More user-friendly when compared to the top with an interactive interface. vmstat: Displays information about processes, memory, paging, block IO, and CPU usage. iostat: Showcases Central Processing Unit (CPU) and I/O statistics for devices and partitions. Example: You can use the top command ( top ) to identify processes consuming too much CPU or memory.
In Linux, how would you check the usage of disk space?
The df command checks disk space usage, and Du is responsible for checking the size of the directory/file. Example: To check overall disk space usage: df -h The -h option depicts the size in a human-readable format like GB, MB, etc.
Package Management (Red Hat)
How do you install, update, or remove packages in Red Hat-based Linux distributions by yum command?
In Red Hat and CentOS systems, the yum package manager is used to install, update, or remove software. Install a package: sudo yum install httpd This installs the Apache web server. Update a package: sudo yum update httpd Remove a package:sudo yum remove httpd
By which command will you check the installation of a package on a Red Hat system?
The yum list installed command is required to check whether the package is installed. Example: To check if httpd (Apache) is installed: yum list installed httpd
Conclusion
The questions are designed by our experienced corporate faculty which will help you to prepare well for various positions that require Linux such as System Admin.
Contact for Course Details – 8447712333
2 notes
·
View notes
Text
🌟 What is Apache ZooKeeper?
Apache ZooKeeper is an open-source coordination service designed to manage distributed applications. It provides a centralized service for maintaining configuration information, naming, and providing distributed synchronization. Essentially, it helps manage large-scale distributed systems and ensures they operate smoothly and reliably.
Key Features of ZooKeeper:
Centralized Service: Manages and maintains configuration and synchronization information across a distributed system.
High Availability: Ensures that distributed systems are resilient to failures by providing fault tolerance and replication.
Consistency: Guarantees a consistent view of the configuration and state across all nodes in the system.
Benefits of Using Apache ZooKeeper:
Enhanced Coordination: Simplifies coordination between distributed components and helps manage critical information like leader election, distributed locks, and configuration management.
Improved Fault Tolerance: By replicating data across multiple nodes, ZooKeeper ensures that even if one node fails, the system can continue to function with minimal disruption.
Scalable Architecture: Supports scaling by allowing systems to expand and manage increasing loads without compromising performance or reliability.
Strong Consistency: Provides a strong consistency model, ensuring that all nodes in the distributed system have a consistent view of the data, which is crucial for maintaining system integrity.
Simplified Development: Abstracts the complexities of distributed system coordination, allowing developers to focus on business logic rather than the intricacies of synchronization and configuration management.
Efficient Resource Management: Helps in managing distributed resources efficiently, making it easier to handle tasks like service discovery and distributed locking.
Apache ZooKeeper is a powerful tool for anyone working with distributed systems, making it easier to build and maintain robust, scalable, and fault-tolerant applications. Whether you’re managing a large-scale enterprise application or a complex microservices architecture, ZooKeeper can provide the coordination and consistency you need.
If you’re looking for Apache ZooKeeper consultants to enhance your distributed system's coordination and reliability, don’t hesitate to reach out to us. Our team of specialists has extensive experience with ZooKeeper and can help you implement and optimize its capabilities for your unique needs. Contact us today to discuss how we can support your projects and ensure your systems run smoothly and efficiently.
2 notes
·
View notes
Text
How can you optimize the performance of machine learning models in the cloud?
Optimizing machine learning models in the cloud involves several strategies to enhance performance and efficiency. Here’s a detailed approach:

Choose the Right Cloud Services:
Managed ML Services:
Use managed services like AWS SageMaker, Google AI Platform, or Azure Machine Learning, which offer built-in tools for training, tuning, and deploying models.
Auto-scaling:
Enable auto-scaling features to adjust resources based on demand, which helps manage costs and performance.
Optimize Data Handling:
Data Storage:
Use scalable cloud storage solutions like Amazon S3, Google Cloud Storage, or Azure Blob Storage for storing large datasets efficiently.
Data Pipeline:
Implement efficient data pipelines with tools like Apache Kafka or AWS Glue to manage and process large volumes of data.
Select Appropriate Computational Resources:
Instance Types:
Choose the right instance types based on your model’s requirements. For example, use GPU or TPU instances for deep learning tasks to accelerate training.
Spot Instances:
Utilize spot instances or preemptible VMs to reduce costs for non-time-sensitive tasks.
Optimize Model Training:
Hyperparameter Tuning:
Use cloud-based hyperparameter tuning services to automate the search for optimal model parameters. Services like Google Cloud AI Platform’s HyperTune or AWS SageMaker’s Automatic Model Tuning can help.
Distributed Training:
Distribute model training across multiple instances or nodes to speed up the process. Frameworks like TensorFlow and PyTorch support distributed training and can take advantage of cloud resources.
Monitoring and Logging:
Monitoring Tools:
Implement monitoring tools to track performance metrics and resource usage. AWS CloudWatch, Google Cloud Monitoring, and Azure Monitor offer real-time insights.
Logging:
Maintain detailed logs for debugging and performance analysis, using tools like AWS CloudTrail or Google Cloud Logging.
Model Deployment:
Serverless Deployment:
Use serverless options to simplify scaling and reduce infrastructure management. Services like AWS Lambda or Google Cloud Functions can handle inference tasks without managing servers.
Model Optimization:
Optimize models by compressing them or using model distillation techniques to reduce inference time and improve latency.
Cost Management:
Cost Analysis:
Regularly analyze and optimize cloud costs to avoid overspending. Tools like AWS Cost Explorer, Google Cloud’s Cost Management, and Azure Cost Management can help monitor and manage expenses.
By carefully selecting cloud services, optimizing data handling and training processes, and monitoring performance, you can efficiently manage and improve machine learning models in the cloud.
2 notes
·
View notes
Text



Phantoms of the Lost Dutchman Mine
The story about the Lost Dutchman Mine in Arizona is the most popular story told about a lost mine in America.
Modern day prospectors still flock to the Superstition Mountains located 30 miles east of Phoenix in hopes of finding the rich deposits of gold it is said this mine contains.
Many people, unwaveringly hopeful, have bought what they were told was the “real treasure map” that would lead them to wealth and prosperity.
Over a dozen men were killed in the 1800s in pursuit of this gold. It is stated that they may be the phantoms that still protect this treasure today.
After the Mexican War in 1848 the territory of Arizona was transferred to the United States. But with plans made to build a southern transcontinental railroad to Los Angeles the U.S. discovered they needed the land south of the Gila River.
James Gadsden, the U.S. Minister to Mexico facilitated the purchase of another 45,000 square miles between the Gila River and the present Mexican border.
With the onset of the Gadsden Purchase a young Mexican man fled his home in Mexico and went into the Superstition Mountains. It is said he escaped a fathers’ wrath because he had violated the virtue of this mans’ young daughter.
Supposedly, he found a rich deposit of gold in 1852. He then returned to his village and convinced several of the men to return to the Superstition Mountains to help him remove part of the gold before the purchase of the land was complete.
This group mined a large amount of gold and happily headed home. But they didn’t get far before a band of Apaches ambushed them. All were killed with the exception of two young boys who hid. The Apaches not caring for the gold left it where it fell.
It is said the two young boys then buried the gold and ran for their lives. Years later, these two told their cousin about the gold and the 3 men then returned to the Superstition Mountains to retrieve the buried gold and reopen the mine.
As they pursued this they unfortunately met up with a German or some say a Dutch prospector by the name of Jacob Walz–sometimes spelled Welz.
The three Mexican men shared their secret with Jacob Walz and he then promptly killed them.
Walz then recruited his nephew and two friends to help with the heavy labor of digging into the mountainside in order to retrieve the gold. After they completed this task Walz killed the three and buried them deep within the mine.
Several other prospectors who had the misfortune to wander near the Dutchman’s mine suffered the same fate.
When Walz returned to Phoenix rumors about a rich mine began to circulate. Several men tried to follow Walz into the mountains but they never returned to Phoenix. It was believed Walz killed them.
When Jacob Walz died in October of 1891 his family found a shoebox under his bed that was filled with gold nuggets. Supposedly this box also contained a map to the mine but it was written in code, which was never deciphered so the location of the Lost Dutchman Mine remains a mystery.
A well-known legend that surrounds the Lost Dutchman states that if anyone comes too close to this mine they will encounter ghosts.
Several witnesses have claimed to be frightened off by the Apache warriors who murdered the Mexican villagers.
Others state these phantoms are the ghosts of the various men murdered by Walz–most often these are said to be the three whose bodies Walz placed deep in the mine.
Yet other prospectors have claimed they saw the ghost of Jacob Walz. These stories include tales of Walz drawing a gun on these unsuspecting miners.
So be forewarned modern day prospectors–if the Arizona heat or the Superstition Mountains’ rugged terrain does not get to you– a ghost or two just might.
#Phantoms of the Lost Dutchman Mine#Lost Dutchman Mine#Haunted Mines#ghost and hauntings#paranormal#ghost and spirits#haunted locations#haunted salem#myhauntedsalem#paranormal phenomena#hauntings#supernatural#spirits#ghosts#haunted
3 notes
·
View notes
Text
Java's Lasting Impact: A Deep Dive into Its Wide Range of Applications
Java programming stands as a towering pillar in the world of software development, known for its versatility, robustness, and extensive range of applications. Since its inception, Java has played a pivotal role in shaping the technology landscape. In this comprehensive guide, we will delve into the multifaceted world of Java programming, examining its wide-ranging applications, discussing its significance, and highlighting how ACTE Technologies can be your guiding light in mastering this dynamic language.

The Versatility of Java Programming:
Java programming is synonymous with adaptability. It's a language that transcends boundaries and finds applications across diverse domains. Here are some of the key areas where Java's versatility shines:
1. Web Development: Java has long been a favorite choice for web developers. Robust and scalable, it powers dynamic web applications, allowing developers to create interactive and feature-rich websites. Java-based web frameworks like Spring and JavaServer Faces (JSF) simplify the development of complex web applications.
2. Mobile App Development: The most widely used mobile operating system in the world, Android, mainly relies on Java for app development. Java's "write once, run anywhere" capability makes it an ideal choice for creating Android applications that run seamlessly on a wide range of devices.
3. Desktop Applications: Java's Swing and JavaFX libraries enable developers to craft cross-platform desktop applications with sophisticated graphical user interfaces (GUIs). This cross-platform compatibility ensures that your applications work on Windows, macOS, and Linux.
4. Enterprise Software: Java's strengths in scalability, security, and performance make it a preferred choice for developing enterprise-level applications. Customer Relationship Management (CRM) systems, Enterprise Resource Planning (ERP) software, and supply chain management solutions often rely on Java to deliver reliability and efficiency.
5. Game Development: Java isn't limited to business applications; it's also a contender in the world of gaming. Game developers use Java, along with libraries like LibGDX, to create both 2D and 3D games. The language's versatility allows game developers to target various platforms.
6. Big Data and Analytics: Java plays a significant role in the big data ecosystem. Popular frameworks like Apache Hadoop and Apache Spark utilize Java for processing and analyzing massive datasets. Its performance capabilities make it a natural fit for data-intensive tasks.
7. Internet of Things (IoT): Java's ability to run on embedded devices positions it well for IoT development. It is used to build applications for smart homes, wearable devices, and industrial automation systems, connecting the physical world to the digital realm.
8. Scientific and Research Applications: In scientific computing and research projects, Java's performance and libraries for data analysis make it a valuable tool. Researchers leverage Java to process and analyze data, simulate complex systems, and conduct experiments.
9. Cloud Computing: Java is a popular choice for building cloud-native applications and microservices. It is compatible with cloud platforms such as AWS, Azure, and Google Cloud, making it integral to cloud computing's growth.

Why Java Programming Matters:
Java programming's enduring significance in the tech industry can be attributed to several compelling reasons:
Platform Independence: Java's "write once, run anywhere" philosophy allows code to be executed on different platforms without modification. This portability enhances its versatility and cost-effectiveness.
Strong Ecosystem: Java boasts a rich ecosystem of libraries, frameworks, and tools that expedite development and provide solutions to a wide range of challenges. Developers can leverage these resources to streamline their projects.
Security: Java places a strong emphasis on security. Features like sandboxing and automatic memory management enhance the language's security profile, making it a reliable choice for building secure applications.
Community Support: Java enjoys the support of a vibrant and dedicated community of developers. This community actively contributes to its growth, ensuring that Java remains relevant, up-to-date, and in line with industry trends.
Job Opportunities: Proficiency in Java programming opens doors to a myriad of job opportunities in software development. It's a skill that is in high demand, making it a valuable asset in the tech job market.
Java programming is a dynamic and versatile language that finds applications in web and mobile development, enterprise software, IoT, big data, cloud computing, and much more. Its enduring relevance and the multitude of opportunities it offers in the tech industry make it a valuable asset in a developer's toolkit.
As you embark on your journey to master Java programming, consider ACTE Technologies as your trusted partner. Their comprehensive training programs, expert guidance, and hands-on experiences will equip you with the skills and knowledge needed to excel in the world of Java development.
Unlock the full potential of Java programming and propel your career to new heights with ACTE Technologies. Whether you're a novice or an experienced developer, there's always more to discover in the world of Java. Start your training journey today and be at the forefront of innovation and technology with Java programming.
8 notes
·
View notes
Text

Modernized A-50U AWACS aircraft is delivered to the Russian Air Force
Fernando Valduga By Fernando Valduga 09/22/2023 - 16:00in Military
The United Aircraft Corporation (UAC) delivered to the Russian Air Forces a modernized aircraft of the A-50U Airborne Alert and Control System (AWACS) that will help in the detection of aircraft and missiles launched from Ukraine.
On July 3, 2023, Russian Defense Minister Sergei Shoigu, in a conference call with officers of the Russian Armed Forces, highlighted the need for a rapid modernization of the A-50.
According to the government-controlled RIA Novosti, Shoigu said: “These flying radars are used in special military operations. The timely modernization of the fleet of these aviation complexes will significantly increase the effectiveness of troop groupings in solving the tasks they face."
The upgraded A-50U has undergone a comprehensive modernization, significantly improving its capabilities. This advanced version has the ability to detect and identify new types of aircraft, while tracking a greater number of targets, including hostile fighters, compared to its predecessor. The integration of state-of-the-art equipment resulted in the reduction of the aircraft's weight, thus expanding its flight range and mission durability.

The renewed aircraft features all-new electronic components with improved performance and speed, allowing improved functionality in its software. In addition, the use of larger and higher resolution LCD monitors has greatly improved the efficiency of the radar display system, improving the overall ergonomics of the aircraft to reduce crew fatigue. Notably, the A-50U is now equipped with an advanced flight and navigation system.
Rostec emphasized the vital role of the A-50U long-range surveillance and radar guidance complex in modern combat scenarios. Through this modernization effort, the aircraft received new technical equipment that significantly increases its speed and detection range of air, land and sea targets, thus increasing its effectiveness in combating potential threats. This modernization initiative is aligned with the plan of the state defense order to upgrade the AWACS aircraft fleet.
Concern Vega, operating under Ruselectronics, played a key role in the modernization process, while United Aircraft Corporation's TANTK also contributed to the effort.
Vyacheslav Mikheev, general designer of Concern Vega, said there are plans underway to complete the modernization of another A-50 complex in the near future.
Tags: Military AviationAWACSBeriev A-50UROSTECRussia
Sharing
tweet
Fernando Valduga
Fernando Valduga
Aviation photographer and pilot since 1992, he has participated in several events and air operations, such as Cruzex, AirVenture, Daytona Airshow and FIDAE. He has work published in specialized aviation magazines in Brazil and abroad. Uses Canon equipment during his photographic work throughout the world of aviation.
Related news
The U.S. Army announced the delivery of the first two AH-64E Version 6 Apache Guardian attack helicopters, but only provided photos of the two previous AH-64D they replaced, being prepared for a flight back to the United States. (Photo: U.S. Army)
HELICOPTERS
U.S. Army Aviation Unit in Europe receives new Apache helicopters
22/09/2023 - 14:00
MILITARY
Germany acquires 13 state-of-the-art LUNA drones and new radar for Eurofighters
09/22/2023 - 11:00
MILITARY
VIDEOS AND IMAGES: F-35A fighters operate from a highway for the first time
22/09/2023 - 09:00
MILITARY
French Air Force closest to retiring its C-135FR tankers after receiving the 12º A330 MRTT
09/22/2023 - 08:27
MILITARY
AUDIO: USMC F-35B fighter flew for more than 100 kilometers, without the pilot on board, before falling
21/09/2023 - 23:25
MILITARY
Boeing negotiates sale of more P-8I Poseidon maritime patrol planes to India
21/09/2023 - 18:24
7 notes
·
View notes
Text
Exploring the Realm of cPanel Hosting in Australia: A Comprehensive Guide
In the vast digital landscape of Australia, where businesses thrive and online presence is paramount, finding the right hosting solution is akin to selecting a foundation for a skyscraper. In this digital age, where websites serve as the face of enterprises, the choice of hosting can significantly impact performance, user experience, and ultimately, the success of ventures. Among the plethora of options, cPanel hosting stands out as a popular choice for its user-friendly interface, robust features, and reliability. But what exactly is cPanel hosting, and why is it gaining traction among businesses in Australia?

Understanding cPanel Hosting
What is cPanel hosting?
cPanel hosting is a type of web hosting that utilizes the cPanel control panel, a web-based interface that simplifies website and server management tasks. It provides users with a graphical interface and automation tools, allowing them to effortlessly manage various aspects of their website, such as file management, email accounts, domain settings, databases, and more.
How does cPanel Hosting Work?
At its core, cPanel hosting operates on a Linux-based server environment, leveraging technologies like Apache, MySQL, and PHP (LAMP stack). The cPanel interface acts as a centralized hub, enabling users to perform administrative tasks through a user-friendly dashboard, accessible via any web browser.
Benefits of cPanel Hosting
User-Friendly Interface
One of the primary advantages of cPanel hosting is its intuitive interface, designed to accommodate users of all skill levels. With its graphical layout and straightforward navigation, even those with minimal technical expertise can manage their websites efficiently.
Comprehensive Feature Set
From creating email accounts to installing applications like WordPress and Magento, cPanel offers a wide array of features designed to streamline website management. Users can easily configure domains, set up security measures, and monitor website performance, and much more, all from within the cPanel dashboard.
Reliability and Stability
cPanel hosting is renowned for its stability and reliability, thanks to its robust architecture and frequent updates. With features like automated backups, server monitoring, and security enhancements, users can rest assured that their websites are in safe hands.
Scalability and Flexibility
Whether you're running a small blog or managing a large e-commerce platform, cPanel hosting can scale to meet your needs. With options for upgrading resources and adding additional features as your website grows, cPanel offers the flexibility required to adapt to evolving business requirements.
Choosing the Right cPanel Hosting Provider
Factors to Consider
When selecting a cPanel hosting provider in Australia, several factors should be taken into account to ensure optimal performance and reliability:
Server Location: Choose a provider with servers located in Australia to minimize latency and ensure fast loading times for local visitors.
Performance: Look for providers that offer high-performance hardware, SSD storage, and ample resources to support your website's needs.
Uptime Guarantee: Opt for providers with a proven track record of uptime, ideally offering a minimum uptime guarantee of 99.9%.
Customer Support: Evaluate the level of customer support offered, ensuring prompt assistance in case of technical issues or inquiries.
Conclusion
In conclusion, cPanel hosting serves as a cornerstone for businesses seeking reliable and user-friendly cpanel hosting Australia. With its intuitive interface, comprehensive feature set, and robust architecture, cPanel empowers users to manage their websites with ease, allowing them to focus on their core business objectives.
2 notes
·
View notes