#top administration software
Explore tagged Tumblr posts
Text
#software#benefits administration software#administration software#best benefits administration software#top administration software
1 note
·
View note
Text
A bug in my pumpkin spice
During the past few weeks, I've seen my Linux Mint desktop occasionally become non-responsive for long periods.
Today I had a terminal window open during one of these bouts. I ran "top" and discovered that Cinnamon (the Ubuntu desktop environment, not the culinary spice) was hogging CPU. "kill -9" seems to have resolved the issue, though of course I'm now without many desktop features.
0 notes
Text
US Treasury Department and White House officials have repeatedly denied that technologists associated with Elon Musk’s so-called Department of Government Efficiency (DOGE) had the ability to rewrite the code of the payment system through which the vast majority of federal spending flows. WIRED reporting shows, however, that at the time these statements were made, a DOGE operative did in fact have write access. Not only that, but sources tell WIRED that at least one note was added to Treasury records indicating that he no longer had write access before senior IT staff stated it was actually rescinded.
Marko Elez, a 25-year-old DOGE technologist, was recently installed at the Treasury Department as a special government employee. One of a number of young men identified by WIRED who have little to no government experience but are currently associated with DOGE, Elez previously worked for SpaceX, Musk’s space company, and X, Musk’s social media company. Elez resigned Thursday after The Wall Street Journal inquired about his connections to “a deleted social-media account that advocated for racism and eugenics.”
As WIRED has reported, Elez was granted privileges including the ability to not just read but write code on two of the most sensitive systems in the US government: the Payment Automation Manager (PAM) and Secure Payment System (SPS) at the Bureau of the Fiscal Service (BFS), an agency that according to Treasury records paid out $5.45 trillion in fiscal year 2024. Reporting from Talking Points Memo confirmed that Treasury employees were concerned that Elez had already made “extensive changes” to code within the Treasury system. The payments processed by BFS include federal tax returns, Social Security benefits, Supplemental Security Income benefits, and veteran’s pay.
Over the last week, the nuts and bolts of DOGE’s access to the Treasury has been at the center of an escalating crisis.
On January 31, David Lebryk, the most senior career civil servant in the Treasury, announced he would retire; he had been placed on administrative leave after refusing to give Musk’s DOGE team access to the federal payment system. The next morning, sources tell WIRED, Elez was granted read and write access to PAM and SPS.
On February 3, Politico reported that Treasury Secretary Scott Bessent told Republican lawmakers in the House Financial Services Committee that Musk and DOGE didn’t have control over key Treasury systems. The same day, The New York Times reported that Karoline Leavitt, the White House press secretary, said that DOGE’s access was “read-only.”
The significance of this is that the ability to alter the code on these systems would in theory give a DOGE technologist—and, by extension, Musk, President Donald Trump, or other actors—the capability to, among other things, illegally cut off Congressionally authorized payments to specific individuals or entities. (CNN reported on Thursday that Musk associates had demanded that Treasury pause authorized payments to USAID, precipitating Lebryk’s resignation.)
On February 4, WIRED reported that Elez did, in fact, have admin access to PAM and SPS. Talking Points Memo reported later that day that Elez had “made extensive changes to the code base for these critical payment systems.” In a letter that same day that did not mention Musk or DOGE, Treasury official Jonathan Blum wrote to Senator Ron Wyden of Oregon, “Currently, Treasury staff members working with Tom Krause, a Treasury employee, will have read-only to the coded data of the Fiscal Service’s payment systems.” (Krause is the top DOGE operative at Treasury and CEO of Cloud Software Group.) The letter did not say what kind of access the staff members actually had.
Sources tell WIRED that by afternoon of the next day, February 5, Elez’s access had been changed to “read-only” from both read and code-writing privileges.
That same day, a federal judge granted an order to temporarily restrict DOGE staffers from accessing and changing Treasury payment system information, following a lawsuit alleging the Treasury Department provided “Elon Musk or other individuals associated with DOGE” with access to the payment systems, and that this access violated federal privacy laws. The order specifically provided a carve-out for two individuals: Krause and Elez. At a court hearing later that day, Department of Justice lawyer Bradley Humphreys asserted that the order said their access would be “read-only.”
“It’s a distinction without a difference,” a source told WIRED. Referring specifically to the PAM, through which $4.7 trillion flowed in fiscal year 2024, they said Elez should not have had “access to this almost $5 trillion payment flow, even if it’s ‘read-only.’ None of this should be happening.”
The Treasury Department did not immediately respond to a request for comment. Elez did not immediately respond to a request for comment. The White House and Musk did not immediately respond to requests for comment.
“People will be held accountable for the crimes they’re committing in this coup attempt,” Wyden tells WIRED. “I’m not letting up on my investigation of what these Musk hatchet men are up to.”
56 notes
·
View notes
Text
Vittoria Elliott at Wired:
Elon Musk’s takeover of federal government infrastructure is ongoing, and at the center of things is a coterie of engineers who are barely out of—and in at least one case, purportedly still in—college. Most have connections to Musk and at least two have connections to Musk’s longtime associate Peter Thiel, a cofounder and chairman of the analytics firm and government contractor Palantir who has long expressed opposition to democracy. WIRED has identified six young men—all apparently between the ages of 19 and 24, according to public databases, their online presences, and other records—who have little to no government experience and are now playing critical roles in Musk’s so-called Department of Government Efficiency (DOGE) project, tasked by executive order with “modernizing Federal technology and software to maximize governmental efficiency and productivity.” The engineers all hold nebulous job titles within DOGE, and at least one appears to be working as a volunteer. The engineers are Akash Bobba, Edward Coristine, Luke Farritor, Gautier Cole Killian, Gavin Kliger, and Ethan Shaotran. None have responded to requests for comment from WIRED. Representatives from OPM, GSA, and DOGE did not respond to requests for comment. Already, Musk’s lackeys have taken control of the Office of Personnel Management (OPM) and General Services Administration (GSA), and have gained access to the Treasury Department’s payment system, potentially allowing him access to a vast range of sensitive information about tens of millions of citizens, businesses, and more. On Sunday, CNN reported that DOGE personnel attempted to improperly access classified information and security systems at the US Agency for International Development (USAID), and that top USAID security officials who thwarted the attempt were subsequently put on leave. The AP reported that DOGE personnel had indeed accessed classified material. “What we're seeing is unprecedented in that you have these actors who are not really public officials gaining access to the most sensitive data in government,” says Don Moynihan, a professor of public policy at the University of Michigan. “We really have very little eyes on what's going on. Congress has no ability to really intervene and monitor what's happening because these aren't really accountable public officials. So this feels like a hostile takeover of the machinery of governments by the richest man in the world.”
[...] “To the extent these individuals are exercising what would otherwise be relatively significant managerial control over two very large agencies that deal with very complex topics,” says Nick Bednar, a professor at University of Minnesota’s school of law, “it is very unlikely they have the expertise to understand either the law or the administrative needs that surround these agencies.” Sources tell WIRED that Bobba, Coristine, Farritor, and Shaotran all currently have working GSA emails and A-suite level clearance at the GSA, which means that they work out of the agency’s top floor and have access to all physical spaces and IT systems, according a source with knowledge of the GSA’s clearance protocols. The source, who spoke to WIRED on the condition of anonymity because they fear retaliation, says they worry that the new teams could bypass the regular security clearance protocols to access the agency’s sensitive compartmented information facility (SCIF), as the Trump administration has already granted temporary security clearances to unvetted people. This is in addition to Coristine and Bobba being listed as “experts” working at OPM. Bednar says that while staff can be loaned out between agencies for special projects or to work on issues that might cross agency lines, it’s not exactly common practice.
WIRED’s report on the 6 college-aged men between 19 and 24 that are shaping up DOGE in aiding and abetting in co-”President” Elon Musk’s technofascist takeover.
#Elon Musk#DOGE#Department of Government Efficiency#Trump Administration II#General Services Administration#Office of Personnel Management#Scott Bessent#USAID#Akash Bobba#Edward Coristine#Luke Farritor#Gautier Cole Killian#Gavin Kliger#Ethan Shaotran#Treasury Department#Musk Coup
65 notes
·
View notes
Text

DOGE update from Secretary of Defense Pete Hegseth: “We're back with another update on cutting wasteful spending here at DOGE, and this one is, as they say, a big one. This is a big day. We're signing a memo right now directing the termination of $5.1 billion in DOGE contracts—not million, that's with a B—$5.1 billion in DOGE contracts for ancillary things like consulting and other non-essential services.
So here's a few examples: DHA contracts for consulting services from Accenture, Deloitte, Booz Allen, and other firms are going to save the department $1.8 billion. How about a software reseller contract for enterprise cloud IT services, saving the department $1.4 billion? A $500 million Navy contract for business process consulting—again, process, lots of process, lots of consultant—for administrative offices in the Bureau of Medicine. By the way, we need this money to spend on better healthcare for our warfighters and their families instead of $500 an hour business process consultants. That's a lot of consulting.
How about this: a DARPA contract for IT help desk services that are completely duplicative with services already provided by our DISA workforce, saving the department another $500 million. We're also terminating, on the DEI front, 11 more contracts for DEI, climate, COVID-19 response, and related non-essential activities across the department. We are committed to rooting out DEI—root and branch—throughout this department, and we've found 11 more contracts and we're going to keep looking.
So that's $5.1 billion in DOGE contracts we're getting rid of. On top of that, in support of the President's priorities to stop federal funding for academic institutions that tolerate anti-Semitism and support divisive DEI programs, this week, DOGE is also pausing over $500 million in funding to Northwestern University and Cornell University, and that's on top of the $70 million in funding we've already paused at Columbia, Penn, Brown, and Princeton over the last few weeks— as if any of these institutions need more government money at all.
So, for you keeping score at home, today's cuts bring our running total to nearly $6 billion in wasteful spending over the first six weeks of the DOGE effort here at the Defense Department. Their job is to go out and find the stuff that we can get rid of and then flow back into—drive back into—warfighting capabilities here at the Defense Department. So we want to thank our friends at DOGE, we want to thank all the folks here that have helped us unpack this, reveal it, and we're excited to make these cuts on behalf of you, the taxpayer, and the warfighters here at the department. Thanks.”
31 notes
·
View notes
Text
Alright. I'm making this post because I was unpleasantly surprised to find Microsoft had forcibly downloaded an """"ai assistant"""" onto my computer (called Copilot), and because finding a site that actually told me how to kill it for good -- in clear, truly step-by-step terms -- was way harder than it needed to be.
Preface: this is only relevant if you're running Windows 11.
Here is your target:

If you see this logo on your taskbar -- or... have Edge installed on Windows 11 -- you've got Copilot. You can't delete it on its own, Microsoft has integrated it into the OS as best they can. The most you can do is disable it (instructions for which are at the very end of this post).
So... to REALLY get rid of it you need to uninstall Microsoft Edge, because it's a part of/reliant on Edge. A lot of bells and whistles of Windows are also reliant on Edge, like widgets, but I never use those. I use my PC almost exclusively for gaming, and I don't want this slimy "ai" shit on my computer. I use Firefox anyway. Edge can go die as far as I'm concerned.
Here's the actual steps, copy-pasted from a website that took me way too long to find. It also really makes my browser chug for some reason, which is why I'm copy-pasting the whole thing. If you still want to look at the site itself, put it in reader view as fast as you can (link to site).
1.) Open Microsoft Edge, type "edge://settings/help" in the address bar, and then press Enter.
2.) Click "About Microsoft Edge" at the bottom of the left-hand pane. Copy the version number at the top of the screen, under Microsoft Edge.
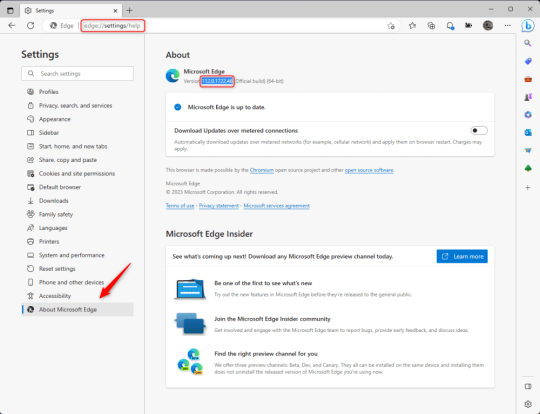
3.) Press Windows Key + S to open Windows Search.
4.) Type "Command Prompt", right-click the result, and then select "Run as Administrator".
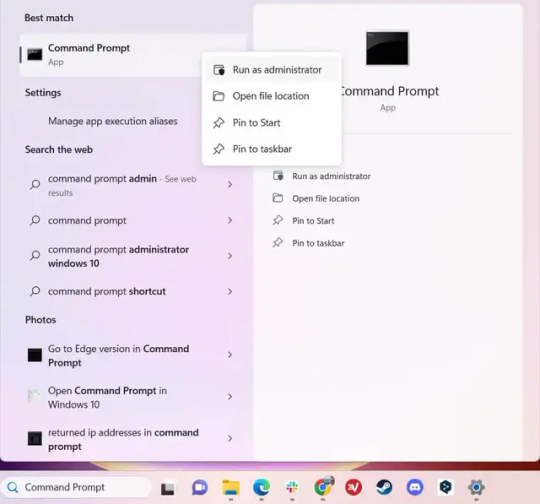
5.) The User Account Control (UAC) prompt will appear. Click "Yes".
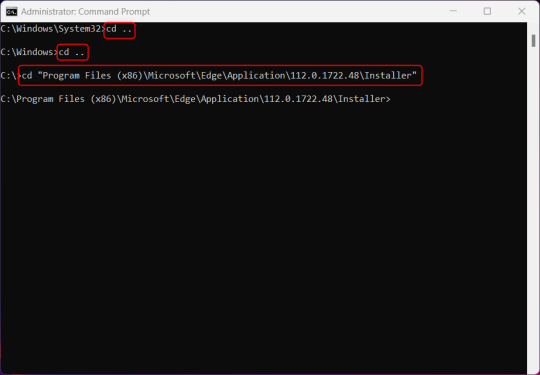
6.) Navigate to Edge’s “Installer” directory by using the cd command. Depending on which directory your Command Prompt opens in by default, you may need to use the "cd .." command to go back a level or two.
Once ready, run this command:
cd “Program Files (x86)\Microsoft\Edge\Application\Version Number\Installer”
Replace "Version Number" with your actual version number copied earlier.
7.) Next, run this command to uninstall Microsoft Edge:
setup –uninstall –force-uninstall –system-level
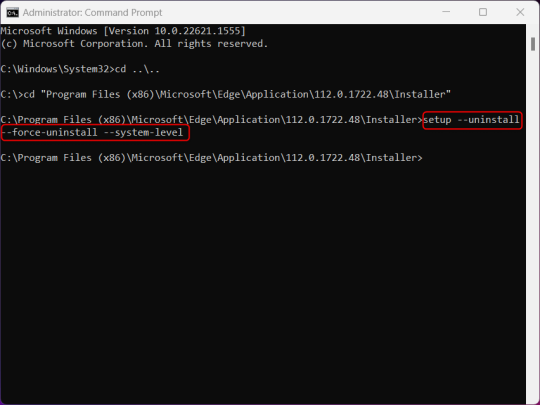
((It will look like nothing happened! Don't worry!))
8.) Restart your PC for the changes to take place.
((HOWEVER, Windows will try to reinstall it the next time your PC updates (or whenever it feels like it lol) so there's a second half to this))
1.) Press Windows Key + R to open Run.
2.) Type "regedit" in the text box and click OK to open the Registry Editor.
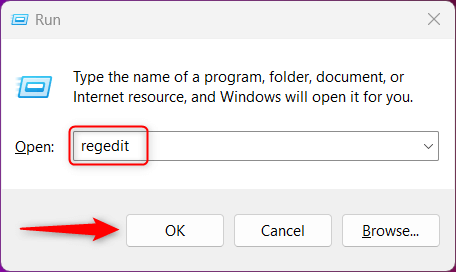
3.) The User Account Control (UAC) prompt will appear. Click "Yes".
4.) In the Registry Editor, navigate to HKEY_LOCAL_MACHINES\SOFTWARE\Microsoft.
5.) Right-click the "Microsoft" folder, hover your cursor over "New", and then select "Key".
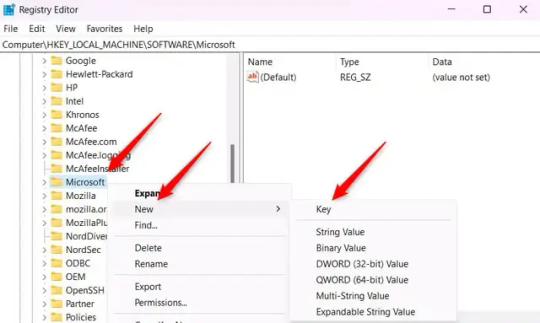
6.) Rename the new Key to "EdgeUpdate".
7.) Right-click EdgeUpdate, hover your cursor over "New", and then select "DWORD (32-bit) Value".
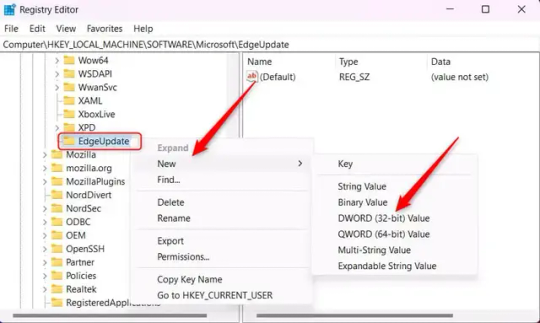
8.) Right-click the new value, which is currently named "New Value #1".
9.) Select "Rename" from the context menu.
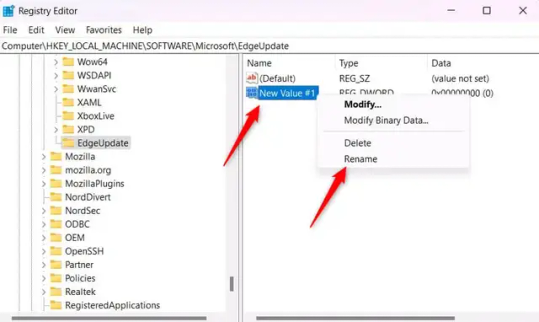
10.) Rename the value to "DoNotUpdateToEdgeWithChromium".
11.) Right-click the newly-named DoNotUpdateToEdgeWithChromium value and select "Modify" from the context menu.
12.) The Edit DWORD (32-bit) Value window will appear. Change the Value data to "1" and then click OK.
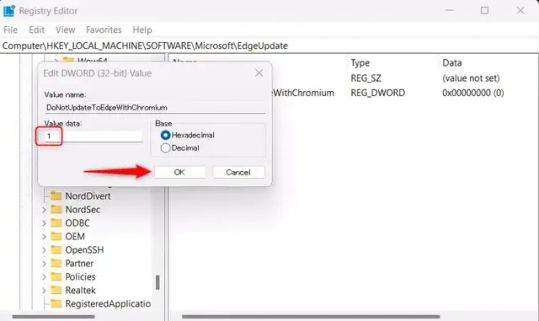
((You are now free. If you ever run into a really serious, unavoidable issue with your OS that's clearly a result of Edge being gone, you can redownload it like a regular app. But you should be fine.))
((And, if for some reason you want still want Edge around but just want the copilot thing gone, here's what you do:
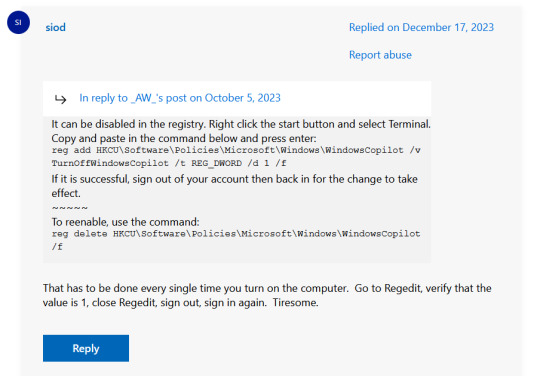
The command, for ease of copy-pasting: reg add HKCU\Software\Policies\Microsoft\Windows\WindowsCopilot /v TurnOffWindowsCopilot /t REG_DWORD /d 1 /f
You can't actually truly delete Copilot (without deleting Edge), only disable it. And as the reply says, you do have to do this every time you turn the computer on. I haven't tested that myself, but I believe it. I assume/hope that excludes just waking the computer up after it goes to sleep, but I don't know for sure.))
120 notes
·
View notes
Text
like i do realize part of the problem is "one group has tracking and statistics and the other doesn't" but like the response to an app ban being to immediately download another app is kind of grim, folks. like i said this YEARS ago but you really can't ban software. you can remove it from the app store. you could criminalize the use of it. you could force the administrator or service provider to block it at the server level or at a network hub (for certain geographic areas, only useful insofar as people allow their systems to be honest about their location). but you can't physically prevent the compiled code from being ran. and again, people who are already doing this are obviously not recognized in the list of top app downloads at the app store
this entire discussion necessitates ceding ground when it's just not an accurate description of the lay of the land. i am becoming convinced that the purpose of this exercise is not to effectively ban software but to convince the public that such a thing is at all possible in the first place, because there's very little difference between those two outcomes
17 notes
·
View notes
Text
NEW DELHI (Reuters) -Global makers of surveillance gear have clashed with Indian regulators in recent weeks over contentious new security rules that require manufacturers of CCTV cameras to submit hardware, software and source code for assessment in government labs, official documents and company emails show.
The security-testing policy has sparked industry warnings of supply disruptions and added to a string of disputes between Prime Minister Narendra Modi's administration and foreign companies over regulatory issues and what some perceive as protectionism.
New Delhi's approach is driven in part by its alarm about China's sophisticated surveillance capabilities, according to a top Indian official involved in the policymaking. In 2021, Modi's then-junior IT minister told parliament that 1 million cameras in government institutions were from Chinese companies and there were vulnerabilities with video data transferred to servers abroad.
Under the new requirements applicable from April, manufacturers such as China's Hikvision, Xiaomi and Dahua, South Korea's Hanwha, and Motorola Solutions of the U.S. must submit cameras for testing by Indian government labs before they can sell them in the world's most populous nation. The policy applies to all internet-connected CCTV models made or imported since April 9.
"There's always an espionage risk," Gulshan Rai, India's cybersecurity chief from 2015 to 2019, told Reuters. "Anyone can operate and control internet-connected CCTV cameras sitting in an adverse location. They need to be robust and secure."
Indian officials met on April 3 with executives of 17 foreign and domestic makers of surveillance gear, including Hanwha, Motorola, Bosch, Honeywell and Xiaomi, where many of the manufacturers said they weren't ready to meet the certification rules and lobbied unsuccessfully for a delay, according to the official minutes.
In rejecting the request, the government said India's policy "addresses a genuine security issue" and must be enforced, the minutes show.
India said in December the CCTV rules, which do not single out any country by name, aimed to "enhance the quality and cybersecurity of surveillance systems in the country."
This report is based on a Reuters review of dozens of documents, including records of meetings and emails between manufacturers and Indian IT ministry officials, and interviews with six people familiar with India's drive to scrutinize the technology. The interactions haven't been previously reported.
Insufficient testing capacity, drawn-out factory inspections and government scrutiny of sensitive source code were among key issues camera makers said had delayed approvals and risked disrupting unspecified infrastructure and commercial projects.
"Millions of dollars will be lost from the industry, sending tremors through the market," Ajay Dubey, Hanwha's director for South Asia, told India's IT ministry in an email on April 9.
The IT ministry and most of the companies identified by Reuters didn't respond to requests for comment about the discussions and the impact of the testing policy. The ministry told the executives on April 3 that it may consider accrediting more testing labs.
Millions of CCTV cameras have been installed across Indian cities, offices and residential complexes in recent years to enhance security monitoring. New Delhi has more than 250,000 cameras, according to official data, mostly mounted on poles in key locations.
The rapid take-up is set to bolster India's surveillance camera market to $7 billion by 2030, from $3.5 billion last year, Counterpoint Research analyst Varun Gupta told Reuters.
China's Hikvision and Dahua account for 30% of the market, while India's CP Plus has a 48% share, Gupta said, adding that some 80% of all CCTV components are from China.
Hanwha, Motorola Solutions and Britain's Norden Communication told officials by email in April that just a fraction of the industry's 6,000 camera models had approvals under the new rules.
CHINA CONCERN
The U.S. in 2022 banned sales of Hikvision and Dahua equipment, citing national security risks. Britain and Australia have also restricted China-made devices.
Likewise, with CCTV cameras, India "has to ensure there are checks on what is used in these devices, what chips are going in," the senior Indian official told Reuters. "China is part of the concern."
China's state security laws require organizations to cooperate with intelligence work.
Reuters reported this month that unexplained communications equipment had been found in some Chinese solar power inverters by U.S. experts who examined the products.
Since 2020, when Indian and Chinese forces clashed at their border, India has banned dozens of Chinese-owned apps, including TikTok, on national security grounds. India also tightened foreign investment rules for countries with which it shares a land border.
The remote detonation of pagers in Lebanon last year, which Reuters reported was executed by Israeli operatives targeting Hezbollah, further galvanized Indian concerns about the potential abuse of tech devices and the need to quickly enforce testing of CCTV equipment, the senior Indian official said.
The camera-testing rules don't contain a clause about land borders.
But last month, China's Xiaomi said that when it applied for testing of CCTV devices, Indian officials told the company the assessment couldn't proceed because "internal guidelines" required Xiaomi to supply more registration details of two of its China-based contract manufacturers.
"The testing lab indicated that this requirement applies to applications originating from countries that share a land border with India," the company wrote in an April 24 email to the Indian agency that oversees lab testing.
Xiaomi didn't respond to Reuters queries, and the IT ministry didn't address questions about the company's account.
China's foreign ministry told Reuters it opposes the "generalization of the concept of national security to smear and suppress Chinese companies," and hoped India would provide a non-discriminatory environment for Chinese firms.
LAB TESTING, FACTORY VISITS
While CCTV equipment supplied to India's government has had to undergo testing since June 2024, the widening of the rules to all devices has raised the stakes.
The public sector accounts for 27% of CCTV demand in India, and enterprise clients, industry, hospitality firms and homes the remaining 73%, according to Counterpoint.
The rules require CCTV cameras to have tamper-proof enclosures, strong malware detection and encryption.
Companies need to run software tools to test source code and provide reports to government labs, two camera industry executives said.
The rules allow labs to ask for source code if companies are using proprietary communication protocols in devices, rather than standard ones like Wi-Fi. They also enable Indian officials to visit device makers abroad and inspect facilities for cyber vulnerabilities.
The Indian unit of China's Infinova told IT ministry officials last month the requirements were creating challenges.
"Expectations such as source code sharing, retesting post firmware upgrades, and multiple factory audits significantly impact internal timelines," Infinova sales executive Sumeet Chanana said in an email on April 10. Infinova didn't respond to Reuters questions.
The same day, Sanjeev Gulati, India director for Taiwan-based Vivotek, warned Indian officials that "All ongoing projects will go on halt." He told Reuters this month that Vivotek had submitted product applications and hoped "to get clearance soon."
The body that examines surveillance gear is India's Standardization Testing and Quality Certification Directorate, which comes under the IT ministry. The agency has 15 labs that can review 28 applications concurrently, according to data on its website that was removed after Reuters sent questions. Each application can include up to 10 models.
As of May 28, 342 applications for hundreds of models from various manufacturers were pending, official data showed. Of those, 237 were classified as new, with 142 lodged since the April 9 deadline.
Testing had been completed on 35 of those applications, including just one from a foreign company.
India's CP Plus told Reuters it had received clearance for its flagship cameras but several more models were awaiting certification.
Bosch said it too had submitted devices for testing, but asked that Indian authorities "allow business continuity" for those products until the process is completed.
When Reuters visited New Delhi's bustling Nehru Place electronics market last week, shelves were stacked with popular CCTV cameras from Hikvision, Dahua and CP Plus.
But Sagar Sharma said revenue at his CCTV retail shop had plunged about 50% this month from April because of the slow pace of government approvals for security cameras.
"It is not possible right now to cater to big orders," he said. "We have to survive with the stock we have."
7 notes
·
View notes
Text
A link-clump demands a linkdump

Cometh the weekend, cometh the linkdump. My daily-ish newsletter includes a section called "Hey look at this," with three short links per day, but sometimes those links get backed up and I need to clean house. Here's the eight previous installments:
https://pluralistic.net/tag/linkdump/
The country code top level domain (ccTLD) for the Caribbean island nation of Anguilla is .ai, and that's turned into millions of dollars worth of royalties as "entrepreneurs" scramble to sprinkle some buzzword-compliant AI stuff on their businesses in the most superficial way possible:
https://arstechnica.com/information-technology/2023/08/ai-fever-turns-anguillas-ai-domain-into-a-digital-gold-mine/
All told, .ai domain royalties will account for about ten percent of the country's GDP.
It's actually kind of nice to see Anguilla finding some internet money at long last. Back in the 1990s, when I was a freelance web developer, I got hired to work on the investor website for a publicly traded internet casino based in Anguilla that was a scammy disaster in every conceivable way. The company had been conceived of by people who inherited a modestly successful chain of print-shops and decided to diversify by buying a dormant penny mining stock and relaunching it as an online casino.
But of course, online casinos were illegal nearly everywhere. Not in Anguilla – or at least, that's what the founders told us – which is why they located their servers there, despite the lack of broadband or, indeed, reliable electricity at their data-center. At a certain point, the whole thing started to whiff of a stock swindle, a pump-and-dump where they'd sell off shares in that ex-mining stock to people who knew even less about the internet than they did and skedaddle. I got out, and lost track of them, and a search for their names and business today turns up nothing so I assume that it flamed out before it could ruin any retail investors' lives.
Anguilla is a British Overseas Territory, one of those former British colonies that was drained and then given "independence" by paternalistic imperial administrators half a world away. The country's main industries are tourism and "finance" – which is to say, it's a pearl in the globe-spanning necklace of tax- and corporate-crime-havens the UK established around the world so its most vicious criminals – the hereditary aristocracy – can continue to use Britain's roads and exploit its educated workforce without paying any taxes.
This is the "finance curse," and there are tiny, struggling nations all around the world that live under it. Nick Shaxson dubbed them "Treasure Islands" in his outstanding book of the same name:
https://us.macmillan.com/books/9780230341722/treasureislands
I can't imagine that the AI bubble will last forever – anything that can't go on forever eventually stops – and when it does, those .ai domain royalties will dry up. But until then, I salute Anguilla, which has at last found the internet riches that I played a small part in bringing to it in the previous century.
The AI bubble is indeed overdue for a popping, but while the market remains gripped by irrational exuberance, there's lots of weird stuff happening around the edges. Take Inject My PDF, which embeds repeating blocks of invisible text into your resume:
https://kai-greshake.de/posts/inject-my-pdf/
The text is tuned to make resume-sorting Large Language Models identify you as the ideal candidate for the job. It'll even trick the summarizer function into spitting out text that does not appear in any human-readable form on your CV.
Embedding weird stuff into resumes is a hacker tradition. I first encountered it at the Chaos Communications Congress in 2012, when Ang Cui used it as an example in his stellar "Print Me If You Dare" talk:
https://www.youtube.com/watch?v=njVv7J2azY8
Cui figured out that one way to update the software of a printer was to embed an invisible Postscript instruction in a document that basically said, "everything after this is a firmware update." Then he came up with 100 lines of perl that he hid in documents with names like cv.pdf that would flash the printer when they ran, causing it to probe your LAN for vulnerable PCs and take them over, opening a reverse-shell to his command-and-control server in the cloud. Compromised printers would then refuse to apply future updates from their owners, but would pretend to install them and even update their version numbers to give verisimilitude to the ruse. The only way to exorcise these haunted printers was to send 'em to the landfill. Good times!
Printers are still a dumpster fire, and it's not solely about the intrinsic difficulty of computer security. After all, printer manufacturers have devoted enormous resources to hardening their products against their owners, making it progressively harder to use third-party ink. They're super perverse about it, too – they send "security updates" to your printer that update the printer's security against you – run these updates and your printer downgrades itself by refusing to use the ink you chose for it:
https://www.eff.org/deeplinks/2020/11/ink-stained-wretches-battle-soul-digital-freedom-taking-place-inside-your-printer
It's a reminder that what a monopolist thinks of as "security" isn't what you think of as security. Oftentimes, their security is antithetical to your security. That was the case with Web Environment Integrity, a plan by Google to make your phone rat you out to advertisers' servers, revealing any adblocking modifications you might have installed so that ad-serving companies could refuse to talk to you:
https://pluralistic.net/2023/08/02/self-incrimination/#wei-bai-bai
WEI is now dead, thanks to a lot of hueing and crying by people like us:
https://www.theregister.com/2023/11/02/google_abandons_web_environment_integrity/
But the dream of securing Google against its own users lives on. Youtube has embarked on an aggressive campaign of refusing to show videos to people running ad-blockers, triggering an arms-race of ad-blocker-blockers and ad-blocker-blocker-blockers:
https://www.scientificamerican.com/article/where-will-the-ad-versus-ad-blocker-arms-race-end/
The folks behind Ublock Origin are racing to keep up with Google's engineers' countermeasures, and there's a single-serving website called "Is uBlock Origin updated to the last Anti-Adblocker YouTube script?" that will give you a realtime, one-word status update:
https://drhyperion451.github.io/does-uBO-bypass-yt/
One in four web users has an ad-blocker, a stat that Doc Searls pithily summarizes as "the biggest boycott in world history":
https://doc.searls.com/2015/09/28/beyond-ad-blocking-the-biggest-boycott-in-human-history/
Zero app users have ad-blockers. That's not because ad-blocking an app is harder than ad-blocking the web – it's because reverse-engineering an app triggers liability under IP laws like Section 1201 of the Digital Millenium Copyright Act, which can put you away for 5 years for a first offense. That's what I mean when I say that "IP is anything that lets a company control its customers, critics or competitors:
https://locusmag.com/2020/09/cory-doctorow-ip/
I predicted that apps would open up all kinds of opportunities for abusive, monopolistic conduct back in 2010, and I'm experiencing a mix of sadness and smugness (I assume there's a German word for this emotion) at being so thoroughly vindicated by history:
https://memex.craphound.com/2010/04/01/why-i-wont-buy-an-ipad-and-think-you-shouldnt-either/
The more control a company can exert over its customers, the worse it will be tempted to treat them. These systems of control shift the balance of power within companies, making it harder for internal factions that defend product quality and customer interests to win against the enshittifiers:
https://pluralistic.net/2023/07/28/microincentives-and-enshittification/
The result has been a Great Enshittening, with platforms of all description shifting value from their customers and users to their shareholders, making everything palpably worse. The only bright side is that this has created the political will to do something about it, sparking a wave of bold, muscular antitrust action all over the world.
The Google antitrust case is certainly the most important corporate lawsuit of the century (so far), but Judge Amit Mehta's deference to Google's demands for secrecy has kept the case out of the headlines. I mean, Sam Bankman-Fried is a psychopathic thief, but even so, his trial does not deserve its vastly greater prominence, though, if you haven't heard yet, he's been convicted and will face decades in prison after he exhausts his appeals:
https://newsletter.mollywhite.net/p/sam-bankman-fried-guilty-on-all-charges
The secrecy around Google's trial has relaxed somewhat, and the trickle of revelations emerging from the cracks in the courthouse are fascinating. For the first time, we're able to get a concrete sense of which queries are the most lucrative for Google:
https://www.theverge.com/2023/11/1/23941766/google-antitrust-trial-search-queries-ad-money
The list comes from 2018, but it's still wild. As David Pierce writes in The Verge, the top twenty includes three iPhone-related terms, five insurance queries, and the rest are overshadowed by searches for customer service info for monopolistic services like Xfinity, Uber and Hulu.
All-in-all, we're living through a hell of a moment for piercing the corporate veil. Maybe it's the problem of maintaining secrecy within large companies, or maybe the the rampant mistreatment of even senior executives has led to more leaks and whistleblowing. Either way, we all owe a debt of gratitude to the anonymous leaker who revealed the unbelievable pettiness of former HBO president of programming Casey Bloys, who ordered his underlings to create an army of sock-puppet Twitter accounts to harass TV and movie critics who panned HBO's shows:
https://www.rollingstone.com/tv-movies/tv-movie-features/hbo-casey-bloys-secret-twitter-trolls-tv-critics-leaked-texts-lawsuit-the-idol-1234867722/
These trolling attempts were pathetic, even by the standards of thick-fingered corporate execs. Like, accusing critics who panned the shitty-ass Perry Mason reboot of disrespecting veterans because the fictional Mason's back-story had him storming the beach on D-Day.
The pushback against corporate bullying is everywhere, and of course, the vanguard is the labor movement. Did you hear that the UAW won their strike against the auto-makers, scoring raises for all workers based on the increases in the companies' CEO pay? The UAW isn't done, either! Their incredible new leader, Shawn Fain, has called for a general strike in 2028:
https://www.404media.co/uaw-calls-on-workers-to-line-up-massive-general-strike-for-2028-to-defeat-billionaire-class/
The massive victory for unionized auto-workers has thrown a spotlight on the terrible working conditions and pay for workers at Tesla, a criminal company that has no compunctions about violating labor law to prevent its workers from exercising their legal rights. Over in Sweden, union workers are teaching Tesla a lesson. After the company tried its illegal union-busting playbook on Tesla service centers, the unionized dock-workers issued an ultimatum: respect your workers or face a blockade at Sweden's ports that would block any Tesla from being unloaded into the EU's fifth largest Tesla market:
https://www.wired.com/story/tesla-sweden-strike/
Of course, the real solution to Teslas – and every other kind of car – is to redesign our cities for public transit, walking and cycling, making cars the exception for deliveries, accessibility and other necessities. Transitioning to EVs will make a big dent in the climate emergency, but it won't make our streets any safer – and they keep getting deadlier.
Last summer, my dear old pal Ted Kulczycky got in touch with me to tell me that Talking Heads were going to be all present in public for the first time since the band's breakup, as part of the debut of the newly remastered print of Stop Making Sense, the greatest concert movie of all time. Even better, the show would be in Toronto, my hometown, where Ted and I went to high-school together, at TIFF.
Ted is the only person I know who is more obsessed with Talking Heads than I am, and he started working on tickets for the show while I starting pricing plane tickets. And then, the unthinkable happened: Ted's wife, Serah, got in touch to say that Ted had been run over by a car while getting off of a streetcar, that he was severely injured, and would require multiple surgeries.
But this was Ted, so of course he was still planning to see the show. And he did, getting a day-pass from the hospital and showing up looking like someone from a Kids In The Hall sketch who'd been made up to look like someone who'd been run over by a car:
https://www.flickr.com/photos/doctorow/53182440282/
In his Globe and Mail article about Ted's experience, Brad Wheeler describes how the whole hospital rallied around Ted to make it possible for him to get to the movie:
https://www.theglobeandmail.com/arts/music/article-how-a-talking-heads-superfan-found-healing-with-the-concert-film-stop/
He also mentions that Ted is working on a book and podcast about Stop Making Sense. I visited Ted in the hospital the day after the gig and we talked about the book and it sounds amazing. Also? The movie was incredible. See it in Imax.
That heartwarming tale of healing through big suits is a pretty good place to wrap up this linkdump, but I want to call your attention to just one more thing before I go: Robin Sloan's Snarkmarket piece about blogging and "stock and flow":
https://snarkmarket.com/2010/4890/
Sloan makes the excellent case that for writers, having a "flow" of short, quick posts builds the audience for a "stock" of longer, more synthetic pieces like books. This has certainly been my experience, but I think it's only part of the story – there are good, non-mercenary reasons for writers to do a lot of "flow." As I wrote in my 2021 essay, "The Memex Method," turning your commonplace book into a database – AKA "blogging" – makes you write better notes to yourself because you know others will see them:
https://pluralistic.net/2021/05/09/the-memex-method/
This, in turn, creates a supersaturated, subconscious solution of fragments that are just waiting to nucleate and crystallize into full-blown novels and nonfiction books and other "stock." That's how I came out of lockdown with nine new books. The next one is The Lost Cause, a hopepunk science fiction novel about the climate whose early fans include Naomi Klein, Rebecca Solnit, Bill McKibben and Kim Stanley Robinson. It's out on November 14:
https://us.macmillan.com/books/9781250865939/the-lost-cause

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2023/11/05/variegated/#nein
#pluralistic#hbo#astroturfing#sweden#labor#unions#tesla#adblock#ublock#youtube#prompt injection#publishing#robin sloan#linkdumps#linkdump#ai#tlds#anguilla#finance curse#ted Kulczycky#toronto#stop making sense#talking heads
140 notes
·
View notes
Text
That's according to the Daily Beast, which reported that Senate Democrats have pushed back the initial confirmation vote for Kash Patel – who Trump nominated to be FBI director — until at least next week.
Tom Krause, chief executive of Cloud Software Group Inc., and Marko Elez, an engineer who has worked for Musk’s private companies, will both retain ostensibly read-only access to payment information. Despite Treasury Department denials to the contrary, though, a WIRED report stated that DOGE staffers have actually enjoyed read-write access, which could allowed them to rewrite code that controls Social Security, tax payments and more.
------
Question for Technology Tumblr:
Isn't that order locking the barn door after the horse is gone? Can't he just access the information from anywhere at this point? I would have thought he would have built in numerous backdoors already. I'm not a computer person though. Does this ruling actually do any good?
9 notes
·
View notes
Text
Bolsonaro administration spied on 1,800 opponents

Feds identified more than 30,000 instances of illegal use of FirstMile, an Israeli software that tracks cellphone geolocation data. Purchased in 2018 by the Brazilian Intelligence Agency (Abin), it was used to monitor at least 1,800 opponents of the Jair Bolsonaro administration, such as politicians, journalists, and lawyers. The names of the victims were not revealed yet.
Two Abin officials have been arrested, five were temporarily removed from office, and USD 171,800 in cash was seized from the home of one of the Abin top officials on Friday.
Twenty-five search warrants were carried out in five Brazilian states. With the operation, one of the Abin buildings in Brasília was sealed while the Feds searched every room for evidence. The agents arrested were on disciplinary leave and used information gathered through FirstMile to blackmail other officials and avoid being fired.
Continue reading.
125 notes
·
View notes
Text
The eye-popping scandal surrounding the Trump cabinet’s accidental invitation to The Atlantic’s editor in chief to join a text-message group secretly planning a bombing in Yemen has rolled into its third day, and that controversy now has a name: SignalGate, a reference to the fact that the conversation took place on the end-to-end encrypted free messaging tool Signal.
As that name becomes a shorthand for the biggest public blunder of the second Trump administration to date, however, security and privacy experts who have promoted Signal as the best encrypted messaging tool available to the public want to be clear about one thing: SignalGate is not about Signal.
Since The Atlantic’s editor, Jeffrey Goldberg, revealed Monday that he was mistakenly included in a Signal group chat earlier this month created to plan US airstrikes against the Houthi rebels in Yemen, the reaction from the Trump cabinet’s critics and even the administration itself has in some cases seemed to cast blame on Signal for the security breach. Some commentators have pointed to reports last month of Signal-targeted phishing by Russian spies. National security adviser Michael Waltz, who reportedly invited Goldberg to the Signal group chat, has even suggested that Goldberg may have hacked into it.
On Wednesday afternoon, even President Donald Trump suggested Signal was somehow responsible for the group chat fiasco. “I don't know that Signal works,” Trump told reporters at the White House. “I think Signal could be defective, to be honest with you.”
The real lesson is much simpler, says Kenn White, a security and cryptography researcher who has conducted audits on widely used encryption tools in the past as the director of the Open Crypto Audit Project: Don’t invite untrusted contacts into your Signal group chat. And if you’re a government official working with highly sensitive or classified information, use the encrypted communication tools that run on restricted, often air-gapped devices intended for a top-secret setting rather than the unauthorized devices that can run publicly available apps like Signal.
“Unequivocally, no blame in this falls on Signal,” says White. “Signal is a communication tool designed for confidential conversations. If someone's brought into a conversation who’s not meant to be part of it, that's not a technology problem. That's an operator issue.”
Cryptographer Matt Green, a professor of computer science at Johns Hopkins University, puts it more simply. “Signal is a tool. If you misuse a tool, bad things are going to happen,” says Green. “If you hit yourself in the face with a hammer, it’s not the hammer’s fault. It’s really on you to make sure you know who you’re talking to.”
The only sense in which SignalGate is a Signal-related scandal, White adds, is that the use of Signal suggests that the cabinet-level officials involved in the Houthi bombing plans, including secretary of defense Pete Hegseth and director of national intelligence Tulsi Gabbard, were conducting the conversation on internet-connected devices—possibly even including personal ones—since Signal wouldn’t typically be allowed on the official, highly restricted machines intended for such conversations. “In past administrations, at least, that would be absolutely forbidden, especially for classified communications,” says White.
Indeed, using Signal on internet-connected commercial devices doesn’t just leave communications open to anyone who can somehow exploit a hackable vulnerability in Signal, but anyone who can hack the iOS, Android, Windows, or Mac devices that might be running the Signal mobile or desktop apps.
This is why US agencies in general, and the Department of Defense in particular, conduct business on specially managed federal devices that are specially provisioned to control what software is installed and which features are available. Whether the cabinet members had conducted the discussion on Signal or another consumer platform, the core issue was communicating about incredibly high-stakes, secret military operations using inappropriate devices or software.
One of the most straightforward reasons that communication apps like Signal and WhatsApp are not suitable for classified government work is that they offer “disappearing message” features—mechanisms to automatically delete messages after a preset amount of time—that are incompatible with federal record retention laws. This issue was on full display in the principals’ chat about the impending strike on Yemen, which was originally set for one-week auto-delete before the Michael Waltz account changed the timer to four-week auto-delete, according to screenshots of the chat published by The Atlantic on Wednesday. Had The Atlantic’s Goldberg not been mistakenly included in the chat, its contents might not have been preserved in accordance with long-standing government requirements.
In congressional testimony on Wednesday, US director of national intelligence Tulsi Gabbard said that Signal can come preinstalled on government devices. Multiple sources tell WIRED that this is not the norm, though, and noted specifically that downloading consumer apps like Signal to Defense Department devices is highly restricted and often banned. The fact that Hegseth, the defense secretary, participated in the chat indicates that he either obtained an extremely unusual waiver to install Signal on a department device, bypassed the standard process for seeking such a waiver, or was using a non-DOD device for the chat. According to political consultant and podcaster Fred Wellman, DOD “political appointees” demanded that Signal be installed on their government devices last month.
Core to the Trump administration’s defense of the behavior is the claim that no classified material was discussed in the Signal chat. In particular, Gabbard and others have noted that Hegseth himself is the classification authority for the information. Multiple sources tell WIRED, though, that this authority does not make a consumer application the right forum for such a discussion.
“The way this was being communicated, the conversation had no formal designation like 'for official use only' or something. But whether it should have been classified or not, whatever it was, it was obviously sensitive operational information that no soldier or officer would be expected to release to the public—but they had added a member of the media into the chat,” says Andy Jabbour, a US Army veteran and founder of the domestic security risk-management firm Gate 15.
Jabbour adds that military personnel undergo annual information awareness and security training to reinforce operating procedures for handling all levels of nonpublic information. Multiple sources emphasize to WIRED that while the information in the Yemen strike chat appears to meet the standard for classification, even nonclassified material can be extremely sensitive and is typically carefully protected.
“Putting aside for a moment that classified information should never be discussed over an unclassified system, it’s also just mind-boggling to me that all of these senior folks who were on this line and nobody bothered to even check, security hygiene 101, who are all the names? Who are they?” US senator Mark Warner, a Virginia Democrat, said during Tuesday’s Senate Intelligence Committee hearing.
According to The Atlantic, 12 Trump administration officials were in the Signal group chat, including vice president JD Vance, secretary of state Marco Rubio, and Trump adviser Susie Wiles. Jabbour adds that even with decisionmaking authorities present and participating in a communication, establishing an information designation or declassifying information happens through an established, proactive process. As he puts it, “If you spill milk on the floor, you can’t just say, ‘That’s actually not spilled milk, because I intended to spill it.’”
All of which is to say, SignalGate raises plenty of security, privacy, and legal issues. But the security of Signal itself is not one of them. Despite that, in the wake of The Atlantic’s story on Monday, some have sought tenuous connections between the Trump cabinet’s security breach and Signal vulnerabilities. On Tuesday, for example, a Pentagon adviser echoed a report from Google’s security researchers, who alerted Signal earlier this year to a phishing technique that Russian military intelligence used to target the app’s users in Ukraine. But Signal pushed out an update to make that tactic—which tricks users into adding a hacker as a secondary device on their account—far harder to pull off, and the same tactic also targeted some accounts on the messaging services WhatsApp and Telegram.
“Phishing attacks against people using popular applications and websites are a fact of life on the internet,” Signal spokesperson Jun Harada tells WIRED. “Once we learned that Signal users were being targeted, and how they were being targeted, we introduced additional safeguards and in-app warnings to help protect people from falling victim to phishing attacks. This work was completed months ago."
In fact, says White, the cryptography researcher, if the Trump administration is going to put secret communications at risk by discussing war plans on unapproved commercial devices and freely available messaging apps, they could have done much worse than to choose Signal for those conversations, given its reputation and track record among security experts.
“Signal is the consensus recommendation for highly at-risk communities—human rights activists, attorneys, and confidential sources for journalists,” says White. Just not, as this week has made clear, executive branch officials planning airstrikes.
28 notes
·
View notes
Text
Introducing the top 10 stories they chose not to tell you this week.
The Vigilant Fox
Mar 02, 2025
#10 - DataRepublican Blows the Lid Off $17 Million ‘Democracy’ Scam
The data scientist revealed that “States United Democracy Center,” an NGO co-founded by Norm Eisen, received $17M—and “the only thing they did with $17M was make a terrible muppet show.”
“That’s (explicit word)!” she exclaimed.
“They got money, and they did something with that. It was just awful. Jim Henson would roll in his grave. And it was weird because all the videos have less than 200 views,” DataRepublican explained.
“They didn’t even try to promote them with ads or anything. So where did the $17 million go?” she asked.
Shortly after this interview aired, DataRepublican revealed she was doxxed in a viral post on X.
After being doxxed, DataRepublican shared more details about herself to take back control of the narrative. She revealed her real name as Jennica Pounds, a 100% Deaf and nonverbal database kernel engineer with expressive dysphasia related to autism.
Pounds recently walked away from her role as a senior software engineer to pursue DOGE-adjacent efforts full-time, aiming to work with the administration to cut waste and improve government efficiency.
Her work—now centered around a powerful searchable database at http://DataRepublican.com—reveals the hidden connections between government grants and NGOs, exposing billions in wasteful spending.
Pounds’ work has been praised by prominent figures like Elon Musk, with her interviews drawing massive viewership on podcasts with Nicole Shanahan, Glenn Beck, and NewsNation.
We’re pleased to welcome the woman tearing up the roots of the entire corrupt system.
Watch as DataRepublican exposes some of the government’s darkest secrets in our exclusive interview.
8 notes
·
View notes
Text
EOR Companies in India: Why Brookspayroll is Your Ideal Partner for Global Hiring
As global hiring continues to evolve, Employer of Record (EOR) services have become a game-changer for companies looking to expand into new markets without the burden of setting up a legal entity. For businesses targeting the fast-growing Indian talent pool, choosing the right EOR company in India is crucial.
Among the leading names in this space, Brookspayroll stands out as one of the most trusted and efficient EOR companies in India, offering comprehensive solutions that are both scalable and compliant.
What is an EOR and Why Do You Need One in India?
An Employer of Record (EOR) is a third-party organization that legally employs workers on your behalf. This means the EOR handles:
Employment contracts and onboarding
Local labor law compliance
Payroll and tax management
Statutory benefits and insurance
Termination and exit procedures
For companies expanding into India, using an EOR enables you to hire top talent without establishing a local entity. It’s faster, cost-effective, and reduces compliance risks.
Brookspayroll: Among the Top EOR Companies in India
Brookspayroll is a leading provider of EOR services in India, known for its accuracy, efficiency, and personalized HR support. Here's why companies worldwide trust Brookspayroll:
✅ 100% Legal Compliance
Brookspayroll ensures your hiring and HR operations fully comply with Indian labor laws, including PF, ESI, gratuity, income tax, and more.
✅ Fast and Flexible Hiring
Hire Indian employees in a matter of days. Brookspayroll provides ready-to-go infrastructure for fast onboarding — no red tape, no delays.
✅ Customized EOR Solutions
From full-time employees to remote workers and contractors, Brookspayroll tailors its EOR services based on your specific needs.
✅ Transparent Pricing
No hidden charges or unexpected fees. Brookspayroll offers clear and competitive pricing for all EOR services.
✅ Local Expertise + Global Standards
Brookspayroll combines deep local labor law expertise with global best practices, making it a perfect fit for international businesses.
Key Benefits of Partnering with Brookspayroll EOR Services in India
Hiring through Brookspayroll gives you:
🌐 Global Expansion Without Entity Setup
🧾 Simplified Payroll and Tax Filing
🛡️ Risk Mitigation and Legal Protection
🧑💼 HR and Benefits Administration
📈 Focus on Business, Not Bureaucracy
Whether you're a startup, mid-sized company, or enterprise, Brookspayroll’s EOR services in India streamline your hiring and ensure long-term stability.
Who Should Use EOR Services in India?
Brookspayroll's EOR services are ideal for:
International companies hiring Indian employees remotely
Startups testing the Indian market
Enterprises needing quick team scaling
Organizations without a registered business in India
By taking on the role of the legal employer, Brookspayroll allows you to operate compliantly and flexibly, while maintaining full control over your employees’ day-to-day work.
Industries Served by Brookspayroll
Brookspayroll serves a wide range of industries through its EOR platform:
IT and Software Development
Digital Marketing and Design
Finance and Consulting
E-commerce and Retail
Health and Wellness
Engineering and Manufacturing
Their tailored approach ensures sector-specific compliance and workforce strategies.
Why Brookspayroll is Among the Best EOR Companies in India
As one of the most reliable EOR companies in India, Brookspayroll offers:
✅ Local presence with national reach
✅ Expert team of HR, legal, and compliance professionals
✅ Advanced HR tech tools for seamless employee management
✅ 24/7 customer support
Brookspayroll doesn’t just handle employment — it empowers global businesses to scale efficiently in India.
Start Hiring in India Today with Brookspayroll
If you’re looking for a trusted partner to hire Indian talent quickly and compliantly, Brookspayroll is the go-to EOR company in India. Their end-to-end EOR solutions simplify the process of entering the Indian market while ensuring full compliance and transparency.
🔗 Contact Brookspayroll today to learn how we can support your global hiring goals!
3 notes
·
View notes
Text
The Department of Education are the folks doling out student loans and funding a lot of the special needs programs in K-12. They do NOT set curriculum. That's your state and local school board. They also do Title IX related stuff.
Some key quotes from the article:
"It is possible they are feeding your personal information into A.I. modelling software.""
“They are blocking members of Congress from entering the Department of Education! Elon is allowed in and not the people? ILLEGAL,” Rep. Maxwell Frost, D-Fla., posted on X, formerly known as Twitter.
"“I don’t know how you eliminate DEI without attacking the special needs programs,” a current administration official said."
"Linda McMahon, Trump’s nominee for education secretary, is scheduled to appear in a confirmation hearing before the Senate Health, Education, Labor and Pensions committee on Feb. 13. McMahon, the former CEO of World Wrestling Entertainment, is currently chairperson of the America First Policy Institute, a 4-year-old Trump-aligned think tank. Four of the top officials already appointed at the Education Department worked for the think tank."
Have something you want to tell your Congress Critters? If you can't safely contact them in person, here are some other options:
Five Calls to your critters: https://5calls.org/
Here is one that will send your reps a fax: https://resist.bot/
"Congress. gov:" https://www.congress.gov/
ACLU advice for writing to your Critters: https://www.aclu.org/writing-your-elected-representatives
#DOGE#the Education Department#News#A.I.#Student Loans#Elon Musk#Department of Education#Title IX#Jahana Hayes#Congress Members#Washington D.C.#Maxwell Frost#Action Item#Diversity Ban
6 notes
·
View notes
Text
by Jon Levine
A Zionist organization is compiling names of foreign students on visas in the US who spewed anti-Israel bile at campus protests — and is hoping President-elect Trump will give the haters a one-way ticket back home.
So far, the group, Betar, has about 30 names of students from nations such as Jordan, Syria, Egypt, Canada, and the United Kingdom currently enrolled in some of the nation’s top universities, including Columbia, UPenn, Michigan, Syracuse, UCLA, The New School for Social Research, Carnegie Mellon, and George Washington University.
“We have started commencing lists of Jew-hating foreign nationals on visas who support Hamas,” said Ross Glick, director of the US chapter of Betar.
Betar has IDed the haters using a combination of facial recognition software and “relationship database technology” to weed out people who were busted at antisemitic campus protests over the last year.
“One of our issues is processing power, there is just so much video to work through,” Glick said.
Betar is already in contact with “prospective” Trump administration appointees in the Justice Department about how best to take action on those identified, Glick said.
Among those on the list is Momodou Taal, a British national and PhD candidate in Africana studies at Cornell University, who was suspended twice for participating in a pair of on-campus Palestinian protests, most recently in September.
University officials initially told Taal that the latest incident would lead to his F-1 visa being revoked, Newsweek reported.
The Ivy later backed down.
8 notes
·
View notes