#web domain firmware update
Explore tagged Tumblr posts
Text
Top Tips for Effective Theft Monitoring in the Digital Age
In today's rapidly evolving digital landscape, staying secure online is more important than ever. Businesses and individuals must secure their data and digital activities from rising cyber threats. This article will delve into four critical aspects of digital security: Email Whitelisting, the emerging threat of the Tesla Botnet, the importance of Theft Monitoring, and the growing concerns around Ad Fraud & Click Fraud. Understanding these concepts and using effective tactics helps protect your online presence and prevent costly security breaches.
The Importance of Email Allowlisting
A simple but effective email list ensures that critical emails enter your inbox without being sent to spam. In a world where phishing attempts and unsolicited emails are commonplace, it's easy for legitimate messages to get lost in the clutter.
How Email Whitelisting Works
Email Allowlisting involves adding specific email addresses or domains to a "safe list." When an email from an allowed sender arrives, it bypasses the spam filter and lands directly in your inbox. This would benefit businesses that need fast, secure communication with clients, partners, and assistance providers.
Benefits of Email Whitelisting
By using Email Whitelisting, you ensure that crucial communications are not missed. This can be vital for businesses that need to respond promptly to client inquiries or receive essential updates from service providers. Whitelisting also reduces phishing assaults by allowing only trusted emails into your inbox. It also improves the efficiency of your email management by filtering out irrelevant messages.
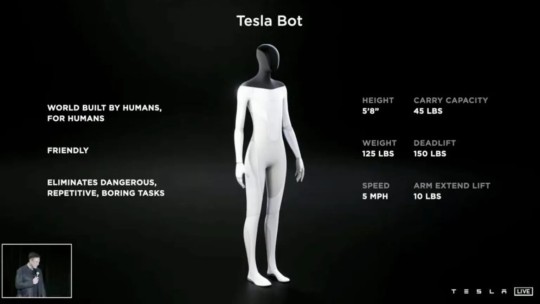
Understanding the Tesla Botnet
As cyber threats evolve, the Tesla Botnet has become a significant concern. Cybercriminals remotely control a botnet of infected machines without the owners' knowledge. The Tesla Botnet is one such network, and it has gained notoriety for its ability to carry out a range of malicious activities.
What is the Tesla Botnet?
Infected machines in the Tesla Botnet are used for DDoS assaults, data breaches, and Bitcoin mining. The botnet primarily targets IoT (Internet of Things) devices, exploiting vulnerabilities in these systems to gain control and carry out its operations.
How to Protect Against the Tesla Botnet
Multifaceted protection against the Tesla Botnet is needed. Ensure all devices, especially IoT ones, have the latest security patches and firmware. Use strong, unique passwords for each device and two-factor authentication whenever possible. Additionally, monitor your network for any unusual activity that could indicate a botnet infection, and consider using security software that can detect and neutralise such threats.
The Role of Theft Monitoring in Digital Security
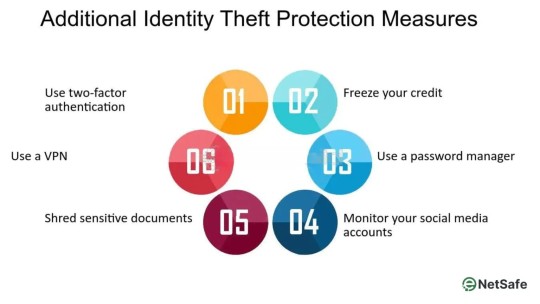
As more personal and financial information is stored online, Theft Monitoring has become a critical component of digital security. Theft Monitoring involves actively tracking your data to detect unauthorised use, which can help prevent identity theft and financial fraud.
How Theft Monitoring Works
Theft monitoring services investigate the dark web for unlawful use of your Social Security number, bank account, or credit card information. If suspicious activity is detected, the service alerts you immediately, allowing you to take swift action to protect your identity and finances.
Why You Need Theft Monitoring
Theft Monitoring provides peace of mind by offering a proactive approach to identity protection. With the increasing number of data breaches and cyberattacks, having a system to monitor and protect your information is more critical than ever. Early identification via Theft Monitoring can avert financial loss and a lengthy identity restoration process.
Combating Ad Fraud & Click Fraud
In the digital marketing world, Ad Fraud and click Fraud pose serious challenges to businesses that rely on online advertising. Ad Fraud refers to the generation of fake impressions, clicks, or conversions, which leads to wasted ad spend and skewed performance metrics. Click fraud, which uses fake clicks to drain advertising budgets or mislead competition, also includes ad fraud.
The Impact of Ad Fraud & Click Fraud on Businesses
Ad Fraud & Click Fraud can have devastating effects on businesses. When companies pay for fraudulent clicks or impressions, they waste valuable resources that could have been used for genuine customer engagement. This not only distorts the effectiveness of ad campaigns but also inflates advertising costs. Moreover, the data from fraudulent activities can mislead marketing strategies, leading to poor business decisions.
Strategies to Prevent Ad Fraud & Click Fraud
To protect your business from Ad Fraud and click Fraud, it's essential to implement robust detection and prevention strategies. Utilise advanced analytics tools to identify abnormal patterns in ad interactions, such as sudden spikes in click rates or traffic from suspicious IP addresses. Partner with reputable ad networks with strict fraud detection protocols. Regularly audit your ad campaigns to ensure that the clicks and impressions you pay for are genuine. You may avoid these frauds by being cautious and using the correct tools.
Conclusion
In conclusion, the digital landscape presents numerous challenges, from managing email security through Email Whitelisting to protecting against sophisticated threats like the Tesla Botnet. Theft Monitoring plays a crucial role in safeguarding personal information, while businesses must remain vigilant against Ad Fraud and click Fraud to protect their advertising investments. Understanding these dangers and executing effective measures can improve your digital security and keep your online presence safe.
0 notes
Text
Download Windows 10 KB5041580 (OS build 19045.4780)
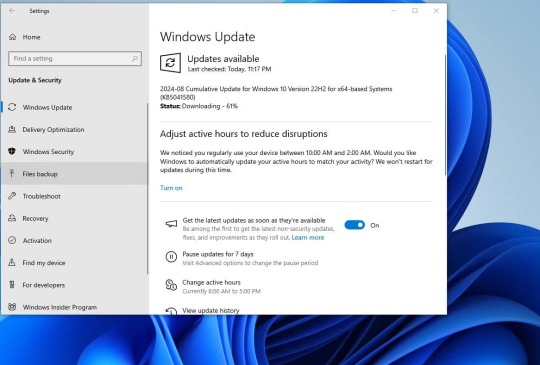
Today 13/August/2024, as part of the patch Tuesday update, Microsoft rolled out new cumulative update KB5041580 for Windows 10 versions 22H2 and 21H2. This is an important security update download and installs automatically or you can navigate settings -> update and security -> Windows update and check for updates to download Windows 10 KB5041580 manually. Also, the Windows 10 KB5041580 update can be downloaded from the Microsoft Update Catalog website.
Windows 10 KB5041580 What’s new
Installing this update changes build numbers 19045.4780 and 19044.4780, which brings August 2024 patch Tuesday security updates along with the latest bug fixes. Some fixes include, Print Support App stops responding, the Windows Backup app failing, and Windows Defender Application Control (WDAC) issues causing app crashes and system memory exhaustion.
As per Microsoft’s official support page, the package doesn’t bring any new features, it comes with important security updates, so users should consider installing it as soon as possible.
[BitLocker (known issue)] A BitLocker recovery screen shows when you start up your device. This occurs after you install the July 9, 2024, update. This issue is more likely to occur if device encryption is on. Go to Settings > Privacy & Security > Device encryption. To unlock your drive, Windows might ask you to enter the recovery key from your Microsoft account.
[Lock screen] This update addresses CVE-2024–38143. Because of this, the “Use my windows user account” check box is not available on the lock screen to connect to Wi-Fi.
[NetJoinLegacyAccountReuse] This update removes this registry key. For more information refer to KB5020276 — Netjoin: Domain join hardening changes.
[Secure Boot Advanced Targeting (SBAT) and Linux Extensible Firmware Interface (EFI)] This update applies SBAT to systems that run Windows. This stops vulnerable Linux EFI (Shim bootloaders) from running. This SBAT update will not apply to systems that dual-boot Windows and Linux. After the SBAT update is applied, older Linux ISO images might not boot. If this occurs, work with your Linux vendor to get an updated ISO image.
Internet Explorer Frame Shutdown Delay: The browser now ignores the FrameShutdownDelay setting in the registry, which previously might have caused unexpected behavior.
Wi-Fi Protected Access 3 (WPA3): An issue in the Group Policy editor where HTML previews weren’t rendering correctly has been fixed.
Group Policy Preferences (Item Level Targeting and Local Users and Groups): There was a problem where administrators couldn’t select groups or accounts from a target domain, especially in complex environments with multiple forests or enhanced security settings. This update resolves that issue.
Transmission Control Protocol (TCP): The system could become unresponsive during routine tasks like file transfers due to a problem in the TCP send code. This update fixes that, preventing extended system hang-ups.
Print Support App: A bug that caused the app to freeze and fail to print when used with USB devices has been addressed. The update also improves the app’s user interface functionality.
Universal Print Clients: These clients had trouble communicating with the Universal Print service when Web Proxy Auto Discovery (WPAD) was enabled, affecting printing. The update resolves this communication issue.
KB update offline installer link: https://catalog.update.microsoft.com/Search.aspx?q=KB5041580
If you are looking for the latest Windows 10 version 22H2 ISO, click here.
In addition, you can download the latest Windows 11 ISO images here.
If you experience problem installing the update, check this video for troubleshooting steps:
youtube
Source: https://www.techaipost.com/windows-10-update-download/
0 notes
Text
does vpn work when comcast router won't change dns
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does vpn work when comcast router won't change dns
VPN compatibility with Comcast router
A Virtual Private Network (VPN) is a useful tool that provides online privacy and security by creating a private network connection over a public internet connection. When it comes to using a VPN with a Comcast router, compatibility may vary depending on the specific router model and VPN service being used.
Comcast routers generally work well with most VPN services. However, there are a few factors to consider to ensure compatibility. Firstly, some older Comcast router models may not support VPN connections, so it is important to check the specifications of your router before attempting to set up a VPN. Additionally, certain VPN protocols may not be supported by all routers, so it is recommended to choose a VPN service that offers a variety of protocols such as OpenVPN, L2TP/IPsec, or IKEv2 for better compatibility.
Setting up a VPN with a Comcast router typically involves accessing the router's settings through a web browser and configuring the VPN connection manually. Some VPN providers offer step-by-step instructions or even custom router firmware to simplify the setup process. Alternatively, users can also connect their devices directly to the VPN without needing to configure the router itself.
Overall, while most Comcast routers are compatible with VPN services, it is advisable to check for any specific requirements or limitations to ensure a smooth and secure connection. By choosing a reliable VPN service and following the necessary steps for setup, users can enjoy enhanced privacy and security while browsing the internet through their Comcast router.
DNS configuration issues on Comcast router
Title: Troubleshooting DNS Configuration Issues on Comcast Router
DNS (Domain Name System) configuration issues can be a common frustration for Comcast router users. When your DNS settings aren't properly configured, you might experience slow internet speeds, intermittent connectivity problems, or even the inability to access certain websites. Here are some steps to troubleshoot DNS configuration issues on your Comcast router:
Check DNS Settings: Start by logging into your Comcast router's admin interface. Look for the DNS settings section, where you can manually specify the DNS servers to use. Ensure that the settings are correct and match the recommended DNS server addresses provided by Comcast.
Restart Router: Sometimes, a simple router restart can resolve DNS issues. Turn off your Comcast router, wait for a few minutes, and then power it back on. This can help refresh the DNS settings and establish a new connection to the DNS servers.
Flush DNS Cache: Your device may be holding onto outdated DNS information in its cache. Open the command prompt on your computer and type the command "ipconfig /flushdns" (for Windows) or "sudo killall -HUP mDNSResponder" (for macOS) to flush the DNS cache.
Use Alternative DNS Servers: If the default Comcast DNS servers are causing problems, consider using alternative DNS servers such as Google DNS (8.8.8.8 and 8.8.4.4) or Cloudflare DNS (1.1.1.1 and 1.0.0.1). Update the DNS settings on your router accordingly.
Contact Comcast Support: If you've tried the above steps and are still experiencing DNS issues, reach out to Comcast customer support for assistance. They may be able to troubleshoot the problem further or provide additional guidance.
By following these steps, you can effectively troubleshoot and resolve DNS configuration issues on your Comcast router, ensuring a smoother and more reliable internet browsing experience.
VPN bypass for Comcast DNS restrictions
Virtual Private Networks (VPNs) offer a reliable solution for users looking to bypass Comcast DNS restrictions and access restricted content on the internet. Comcast is known for implementing DNS restrictions that limit users' access to certain websites. By using a VPN, users can effectively bypass these restrictions and enjoy a more open and unrestricted browsing experience.
When a user connects to a VPN server, their internet traffic is encrypted and routed through the VPN server. This process masks the user's IP address, making it appear as though they are accessing the internet from a different location. As a result, Comcast's DNS restrictions are circumvented, allowing users to access blocked websites and content without any limitations.
VPNs offer users an added layer of privacy and security by encrypting their internet traffic, protecting them from potential cyber threats and surveillance. In addition to bypassing Comcast DNS restrictions, VPNs can also help users access geo-restricted content by virtually changing their location to a different country.
There are many VPN providers available on the market, each offering different features and levels of security. It's essential for users to research and choose a reputable VPN service that meets their specific needs. By using a VPN to bypass Comcast DNS restrictions, users can enjoy a more open and secure browsing experience while maintaining their privacy and anonymity online.
Troubleshooting VPN connection on Comcast network
Troubleshooting VPN Connection on Comcast Network
Virtual Private Networks (VPNs) are invaluable tools for securing your online activities and accessing restricted content. However, encountering connectivity issues on a Comcast network can be frustrating. Here are some troubleshooting steps to resolve VPN connection problems:
Check Your Internet Connection: Before troubleshooting your VPN, ensure that your Comcast internet connection is stable. Test other devices connected to the network to rule out any general connectivity issues.
Restart Your Devices: Sometimes, a simple restart can fix connectivity issues. Restart your computer, router, and modem to refresh the network connection.
Update VPN Software: Ensure that your VPN software is up to date. Outdated versions may not be compatible with the latest network configurations.
Switch VPN Servers: If you're experiencing issues with a specific VPN server, try connecting to a different one. Sometimes, servers can become overcrowded or experience technical problems.
Check Firewall and Antivirus Settings: Firewalls and antivirus software may block VPN connections. Temporarily disable them to see if they're causing the problem.
Reset Network Settings: Resetting your network settings can resolve configuration issues. Go to your device's network settings and choose the option to reset network settings to default.
Contact Comcast Support: If you've tried all the above steps and still can't connect to your VPN, reach out to Comcast's customer support. They can check for any network outages or provide further assistance.
Consider Alternative VPN Protocols: Some VPN protocols may work better on Comcast networks than others. Experiment with different protocols like OpenVPN, L2TP/IPsec, or IKEv2 to see if any offer better stability.
By following these troubleshooting steps, you can hopefully resolve any VPN connection issues on your Comcast network and enjoy secure and unrestricted internet access.
Alternative DNS setup for VPN on Comcast router
When setting up a VPN on a Comcast router, alternative Domain Name System (DNS) configurations might be necessary to ensure smooth and secure connectivity. DNS is responsible for translating domain names into IP addresses, enabling users to access websites using human-readable addresses.
By default, Comcast routers use the ISP-provided DNS servers, which might not be optimal for VPN usage due to potential privacy concerns or performance issues. To address this, users can manually configure alternative DNS servers on their Comcast router to enhance the VPN experience.
One popular alternative DNS service is Google Public DNS, which offers fast and secure resolution for domain names. To set up Google Public DNS on a Comcast router for VPN usage, users can access the router's settings through a web browser and navigate to the DNS configuration section. Here, they can input the primary and secondary IP addresses for Google Public DNS (8.8.8.8 and 8.8.4.4, respectively) to replace the default DNS servers.
Another alternative is OpenDNS, known for its filtering options and security features. Users can set up OpenDNS on their Comcast router by entering the appropriate DNS server IP addresses provided by OpenDNS in the router settings.
By configuring alternative DNS servers on their Comcast router for VPN usage, users can potentially enhance privacy, security, and performance when browsing the internet through a VPN connection. Experimenting with different DNS services can help optimize the VPN experience on Comcast routers.
0 notes
Text
can t connect to vpn invalid payload
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
can t connect to vpn invalid payload
VPN connection issues
Title: Troubleshooting Common VPN Connection Issues
In today's digital age, VPNs (Virtual Private Networks) play a crucial role in safeguarding online privacy and security. However, like any technology, VPNs can encounter issues that disrupt their functionality. Understanding and addressing these common VPN connection issues is essential for seamless browsing experiences.
One prevalent problem users encounter is difficulty establishing a connection. This issue often stems from server overload, network congestion, or compatibility issues with the device or operating system. To troubleshoot connection failures, users can try switching between different VPN servers, ensuring their device's software is up to date, and checking for any conflicting applications or settings.
Another common issue is slow connection speeds. While VPNs can slightly reduce internet speeds due to encryption and rerouting, excessively slow connections may indicate bandwidth limitations, server overcrowding, or network throttling by the ISP. To improve speed, users can connect to servers closer to their physical location, upgrade to a higher-tier VPN plan for increased bandwidth, or contact their ISP to address potential throttling issues.
Additionally, intermittent disconnections can frustrate users and compromise their online security. These interruptions may result from unstable network connections, router configurations, or VPN protocol issues. Troubleshooting steps include restarting the VPN client, updating router firmware, and experimenting with different VPN protocols like OpenVPN or IKEv2.
DNS (Domain Name System) leaks represent another concern, where a user's DNS requests are exposed to their ISP despite using a VPN. To prevent this, users should enable DNS leak protection in their VPN settings or manually configure their device's DNS servers.
Overall, while VPNs offer invaluable privacy and security benefits, encountering connection issues is not uncommon. By familiarizing themselves with common problems and implementing troubleshooting techniques, users can effectively resolve VPN connection issues and enjoy uninterrupted browsing experiences.
Invalid payload error
Title: Understanding the Invalid Payload Error: Causes and Solutions
When navigating through the digital landscape, encountering errors is inevitable, and one common frustration for developers and users alike is the "Invalid Payload Error." This perplexing message can halt progress and leave individuals scratching their heads. So, what exactly does it entail?
In the realm of web development and data transmission, a payload refers to the data being sent between systems or applications. An invalid payload error occurs when the data being transmitted is malformed or does not meet the expected format or standards. This can happen for various reasons and can manifest in different scenarios.
One common cause of an invalid payload error is improper data formatting. If the data being sent does not adhere to the specified structure or contains unexpected characters, it can trigger this error. Similarly, issues with encoding, such as attempting to transmit non-ASCII characters without proper encoding, can result in an invalid payload error.
Another culprit behind this error is validation failure. Many systems and applications have validation mechanisms in place to ensure the integrity and security of the data being transmitted. If the data fails to pass these validation checks, it can lead to an invalid payload error.
Furthermore, compatibility issues between different systems or versions can also contribute to this error. If the sender and receiver are not in sync regarding data formats or protocols, it can result in misunderstandings and trigger the invalid payload error.
Resolving the invalid payload error often requires careful analysis and troubleshooting. Developers may need to inspect the data being transmitted, review encoding and formatting practices, and ensure compatibility between systems. Implementing robust validation mechanisms and error handling routines can also help mitigate the risk of encountering this error in the future.
In conclusion, while the invalid payload error may be frustrating, understanding its causes and implementing appropriate solutions can help navigate through it effectively, ensuring smooth data transmission and optimal system performance.
Troubleshooting VPN connectivity
Troubleshooting VPN Connectivity: A Guide to Resolving Connection Issues
Virtual Private Networks (VPNs) have become indispensable tools for ensuring online privacy and security. However, like any technology, VPNs can encounter connectivity issues that disrupt their functionality. Here's a comprehensive guide to troubleshooting VPN connectivity problems:
Check Your Internet Connection: Before delving into VPN-specific troubleshooting, ensure that your internet connection is stable and functional. Poor connectivity can hamper VPN performance.
Verify VPN Configuration: Double-check your VPN settings to ensure they are correctly configured. Pay attention to details such as server selection, protocol settings, and authentication credentials.
Restart VPN Client and Device: Sometimes, simply restarting your VPN client software or device can resolve connectivity issues. This action can reset configurations and clear temporary glitches.
Switch Servers: If you're experiencing connectivity problems with a particular VPN server, try connecting to a different server location. This can help bypass any congestion or server-specific issues.
Update VPN Software: Ensure that your VPN client software is up-to-date. Developers regularly release updates to address bugs, security vulnerabilities, and compatibility issues.
Check Firewall and Antivirus Settings: Firewalls and antivirus programs can sometimes interfere with VPN connections. Temporarily disable these security measures to see if they are causing the problem.
Flush DNS Cache: Flushing your DNS cache can help resolve domain name resolution issues that may be affecting your VPN connection. Open the command prompt and type 'ipconfig /flushdns' (without quotes), then press Enter.
Contact VPN Provider Support: If you've exhausted all troubleshooting steps and still can't resolve the issue, contact your VPN provider's customer support. They can offer personalized assistance and troubleshoot server-side issues.
By following these troubleshooting steps, you can effectively diagnose and resolve VPN connectivity problems, ensuring a seamless and secure online experience.
Network security protocols
Network security protocols are essential components of any organization's cybersecurity infrastructure. These protocols are designed to protect the integrity, confidentiality, and availability of data as it travels across networks. They establish the rules and procedures for secure communications between devices, ensuring that sensitive information is safeguarded from unauthorized access or malicious attacks.
One of the most widely used network security protocols is the Secure Socket Layer (SSL) or its newer version, the Transport Layer Security (TLS). SSL and TLS protocols encrypt data as it travels between servers and clients, making it unreadable to anyone who intercepts it. This encryption ensures that sensitive information such as passwords, credit card numbers, and personal data remains confidential and secure.
Another important network security protocol is the Internet Protocol Security (IPsec), which provides a secure framework for Internet communications. IPsec authenticates and encrypts data packets to ensure the confidentiality and integrity of network traffic. It is commonly used to create Virtual Private Networks (VPNs), allowing remote users to securely connect to corporate networks over the Internet.
Furthermore, the Secure Shell (SSH) protocol is widely used for secure remote access to network devices. SSH encrypts communication sessions between clients and servers, preventing eavesdropping and unauthorized access to sensitive information.
Overall, network security protocols play a crucial role in safeguarding data and maintaining the integrity of communication networks. By implementing robust protocols such as SSL/TLS, IPsec, and SSH, organizations can mitigate security risks and protect their digital assets from cyber threats.
VPN configuration problems
When it comes to Virtual Private Network (VPN) configuration, users may encounter several common problems that can hinder their ability to connect securely and privately to the internet. One of the most prevalent issues is incorrectly inputting VPN server details such as the IP address, username, and password. This can result in authentication failures and unsuccessful connection attempts.
Another common problem when configuring a VPN is the compatibility of the VPN protocol with the user's device or network. Some VPN protocols may not be supported by older devices or certain network configurations, leading to connection issues. It is essential to choose a VPN protocol that is compatible with your device and network to ensure a smooth connection.
DNS leaks can also occur during VPN configuration, where the user's internet service provider (ISP) can still see their browsing activity despite being connected to a VPN. This often happens due to misconfigured VPN settings or insufficient VPN protection. Users can mitigate DNS leaks by using reputable VPN services with built-in leak protection features.
Furthermore, firewall settings and antivirus software can sometimes interfere with VPN connections, causing configuration problems. Users should adjust their firewall settings to allow VPN traffic and ensure that their antivirus software does not block the VPN application.
In conclusion, VPN configuration problems are not uncommon and can usually be resolved with careful attention to detail and troubleshooting. By double-checking server details, ensuring protocol compatibility, preventing DNS leaks, and managing firewall and antivirus settings, users can enjoy a secure and private VPN connection without interruptions.
0 notes
Text
can you set up vpn and ddns on a router
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
can you set up vpn and ddns on a router
VPN setup on router
Setting up a VPN on your router can enhance your online privacy and security by encrypting your internet connection and masking your IP address. This ensures that your data remains secure and your browsing activity is private from potential prying eyes. Here’s a step-by-step guide on how to set up a VPN on your router:
Choose a VPN Service: Select a reputable VPN provider that offers router support. Ensure the VPN service is compatible with your router model and supports the VPN protocol you prefer (e.g., OpenVPN, PPTP, L2TP/IPsec).
Access Router Settings: Log in to your router’s administrative interface. You can usually do this by entering the router’s IP address into your web browser and entering your login credentials (typically found on the router itself or in the user manual).
Install VPN Firmware (Optional): Some routers support custom firmware like DD-WRT, Tomato, or OpenWRT, which offer enhanced VPN functionality. If your router supports custom firmware, you may need to flash it with the appropriate firmware version compatible with your VPN provider.
Configure VPN Settings: Navigate to the VPN settings section in your router’s admin interface. Enter the VPN server address, username, and password provided by your VPN provider. Select the desired VPN protocol and encryption settings.
Connect to VPN: Save your VPN settings and restart your router if necessary. Once the router is back online, initiate a connection to the VPN server through the router’s settings. Upon successful connection, your router will encrypt all internet traffic passing through it.
Verify Connection: Confirm that your VPN connection is active by checking your router’s status or using online tools to verify your IP address and geolocation. You should see your VPN provider’s server location instead of your actual location.
Test Connectivity: Ensure all devices connected to the router can access the internet properly while connected to the VPN. Test various websites and applications to confirm that the VPN is functioning correctly.
By setting up a VPN on your router, you can safeguard your entire network and enjoy the benefits of enhanced online privacy and security across all your devices.
DDNS configuration on router
Dynamic Domain Name System (DDNS) configuration on a router allows users to access their network remotely using a domain name that automatically updates with the changing IP address assigned by their Internet Service Provider (ISP). This is especially useful for businesses or individuals who need to connect to their network remotely but do not have a static IP address.
To configure DDNS on a router, users first need to sign up for a DDNS service provider such as No-IP, DynDNS, or DuckDNS. After creating an account and selecting a hostname, users will then log in to their router's settings where they can locate the DDNS configuration section. Here, they will input their DDNS provider's information including the hostname, username, password, and update interval.
Once the DDNS settings are saved, the router will periodically update the IP address with the DDNS service provider, ensuring that the domain name always points to the correct IP address. This allows users to access their network remotely using an easy-to-remember domain name instead of having to remember a complex IP address that may change frequently.
Overall, configuring DDNS on a router is a straightforward process that provides convenience and reliability for users who require remote access to their network. By automating the update of IP addresses with a domain name, DDNS simplifies remote network connectivity and enhances accessibility without the need for a static IP address.
Router VPN and DDNS setup
To set up a VPN on your router, follow these steps to ensure secure and private internet connection for all devices on the network. By using a VPN, you can encrypt your internet traffic and hide your IP address, ensuring anonymity and security online.
Log in to your router's admin panel. You can usually access this by typing your router's IP address into a web browser and entering your credentials.
Look for the VPN tab in the router settings. If your router supports VPN connections, there should be an option to set up a VPN connection.
Choose the type of VPN protocol you want to use. Common options include OpenVPN, PPTP, and L2TP/IPsec. OpenVPN is preferred for its strong encryption and security features.
Enter the VPN server details provided by your VPN service provider. This includes the server address, username, password, and any other required information.
Save the settings and connect to the VPN server. Once connected, all internet traffic on your network will be encrypted and routed through the VPN server.
Setting up a Dynamic Domain Name System (DDNS) on your router allows you to access your network remotely using a domain name instead of an IP address that may change frequently.
Locate the DDNS settings in your router admin panel. Enter the DDNS service provider details and create a hostname for your network.
Choose a DDNS service provider such as No-IP, DynDNS, or DuckDNS. Sign up for an account and configure the DDNS settings in your router.
Save the settings and update the DDNS service. Your router will regularly update the DDNS service with your current IP address, ensuring your domain name always points to the correct address.
By setting up a VPN and DDNS on your router, you can enhance your online security and accessibility, allowing secure connections and remote access to your network from anywhere in the world.
Setting up VPN and DDNS on a router
Setting up a Virtual Private Network (VPN) and Dynamic Domain Name System (DDNS) on a router can enhance your online security and accessibility. VPN allows you to create a secure connection to another network over the internet, safeguarding your data and online activities from prying eyes. DDNS, on the other hand, enables you to access your network remotely using a domain name that constantly updates to your changing IP address.
To set up VPN and DDNS on your router, follow these steps. First, access your router's settings by entering its IP address in a web browser. Look for the VPN and DDNS options, which are usually located in the advanced settings or security section. Choose the VPN protocol that best fits your needs, such as OpenVPN or PPTP, and configure the settings accordingly.
Next, set up DDNS by selecting a service provider and creating a hostname for your network. This hostname will be used to access your network remotely. Input the DDNS credentials provided by the service provider into your router's settings. Ensure that the DDNS service is active and updating your IP address regularly.
Once both VPN and DDNS are set up, test the connections to ensure everything is working properly. Connect to the VPN from a remote location to verify the secure connection, and use the DDNS hostname to access your network externally.
By configuring VPN and DDNS on your router, you can enjoy increased security and accessibility while browsing the internet and accessing your network remotely. Take the time to set up these features correctly to make the most of your online experience.
Router VPN and Dynamic DNS installation
Title: Setting Up Router VPN and Dynamic DNS: A Comprehensive Guide
In today's digital landscape, ensuring privacy and security while browsing the internet is paramount. One effective way to achieve this is by setting up a Virtual Private Network (VPN) directly on your router, coupled with Dynamic Domain Name System (DNS) for seamless access. This comprehensive guide will walk you through the process of installing a VPN on your router and configuring Dynamic DNS to enhance your online privacy and accessibility.
Step 1: Choose a Compatible Router and VPN Service Ensure your router supports VPN installation and select a reliable VPN service provider. Look for routers that offer VPN client support, such as OpenVPN, PPTP, or L2TP/IPsec protocols, and check compatibility with your chosen VPN service.
Step 2: Access Router Settings Access your router's settings by typing its IP address into your web browser. Log in with your credentials and navigate to the VPN section. Here, you'll find options to configure VPN settings.
Step 3: Configure VPN Settings Enter the VPN server details provided by your VPN service provider, including the server address, username, and password. Choose the preferred VPN protocol and encryption level for optimal security.
Step 4: Install VPN Client on Router Follow the instructions provided by your router manufacturer to install the VPN client firmware. This process may vary depending on your router model.
Step 5: Enable Dynamic DNS Dynamic DNS allows you to access your home network remotely using a domain name instead of a dynamic IP address. Enable Dynamic DNS in your router's settings and create a hostname with your chosen Dynamic DNS provider.
Step 6: Finalize Configuration Save your VPN and Dynamic DNS settings and reboot your router to apply the changes. Once restarted, your router will establish a secure VPN connection, and Dynamic DNS will ensure seamless access to your home network from anywhere.
By following these steps, you can safeguard your online activities with a router VPN while maintaining accessibility through Dynamic DNS. Enjoy enhanced privacy and security without compromising on convenience.
0 notes
Link
Nighthawk AX3000 WIFI6 Router provides the latest wifi six technology. It also provides a new level of Gigabit wifi connectivity so the users can connect, stream, and download fast. You can click the website to know more information.
#web domain firmware update#netgear firmware update#netgear router firmware update#how to update firmware on netgear router#netgear nighthawk firmware update
0 notes
Text
I can’t access the wifi extender login page; what should I do?
To set up your WiFi extender, go to http-//mywifiext-net and log into the mywifiext.net login page. The IP address 192.168.1.250 can also be used to log into the WiFi Extender. You may alter the settings of your extender and change the WiFi password with mywifiext.net setup. Mywifiext.net isn't your normal domain name. It's a local web address that can be used to configure the WiFi range extender. When you use your web browser to access mywifiext.net, you will be directed to a login screen where you must enter your default username and password.
A setup screen opens after successfully logging into the mywifiext.net website, allowing users to configure their settings and set up their WiFi range extender devices. With mywifiext.net login setup, you may update settings, extend WiFi network range, upgrade firmware, and do a lot more. Users have reported being unable to access the mywifiext.net login page on occasion. In that case, use a different web browser or double-check the URL address you typed. Also, make sure you're accessing the mywifiext.net login screen with the right password.

#mywifiext.net#http://mywifiext.net#mywifiext.net login#WiFi extender setup#Wifi Extender login#mywifiext.net Login Setup#192.168.1.250
2 notes
·
View notes
Text
Crack Fortigate Vm64

Sep 01, 2019 FortiGate VM software is available for 32-bit and 64-bit environments. Both an upgrade version for existing FortiGate VMs and a “greenfield” version are available. We will use the second solution, available as a downloadable zip archive file (the one we will use is a 64-bit version, FGTVM64-v500-build0228-FORTINET.out.ovf.zip). Crack Fortigate Vm64 Sun Type 7 Usb Keyboard With Windows 10 Wifidog Do Wrt Cable Spinet Piano Serial 419416 Mac Os 10.13 Driver For Brother Hl-1440 Hip Hop Acapellas Office 365 Forward Email To External Address Virtual Villagers Origins 2 Error02-0 License Key Reaper V5.965.
Fortigate Vm64 Crack
Crack Fortigate Vm64 Key
Crack Fortigate Vm64 3
If you have a registered Fortinet product (any one should do) and have a valid login ID on the support.fortinet.com site, you should be able to download any of the VM images (via the download link). Another option would be to fill out this online form. Oct 31, 2014 If you have a registered Fortinet product (any one should do) and have a valid login ID on the support.fortinet.com site, you should be able to download any of the VM images (via the download link). Another option would be to fill out this online form.
FortiGate virtual appliances allow you to provision Fortinet security inside a virtual environment. All the security and networking features we would expect in a hardware-based FortiGate are available in the VM too. FortiGate VM software is available for 32-bit and 64-bit environments.
Gateway drivers for windows 7. Both an upgrade version for existing FortiGate VMs and a “greenfield” version are available. We will use the second solution, available as a downloadable zip archive file (the one we will use is a 64-bit version, FGT_VM64-v500-build0228-FORTINET.out.ovf.zip). Note: it is required to have at least an access as a customer to the Fortinet support to be able to receive and use the aforementioned files.
Here we will discuss on Fortigate (Fortigen Virtual FortiOS Apliance) Necessary downloads After download, simply extract the file and open the fortigate.vmx file in VMware. Immediately after, it will be reflected on VMware window. Do not forget to change some initial setting before you fire up the Fortigate. Do a little changes here in memory settings to optimize the hardware of your PC. Set the memory requirement 512MB.
Now do some changes in Virtual Network Adapter settings as compatible to your topology. Here I made my own topology bellow and dis the post changes in VM Network Adapters. More about Virtual Netowrk and Sharing [showhide type=”post” more_text=”show more>>>” less_text=” Port-1>Internal Network>Subnet 192.168.0.0/24 Vmnet8>Port-2>Internet>Subnet 192.168.137.0/24 Now time to turn on the Fortigate VM. A cli console will come up with login prompt ( username: admin password: N/A) Now everything is ready, time to do initial configuration. Have a look at the topology once again VMnet0>Port-1>Internal Network>Subnet 192.168.0.0/24 Vmnet8>Port-2>Internet>Subnet 192.168.137.0/24 Configurations Fortigate-VM login: admin Password: Welcome! Fortigate-VM # config system interface Fortigate-VM (interface) # edit port1 Fortigate-VM (port1) # set ip 192.168.0.30 255.255.255.0 Fortigate-VM (port2) # set allowaccess http https fgmp ssh telnet ping Fortigate-VM (port1) # end Fortigate-VM # config system interface Fortigate-VM (interface) # edit port2 Fortigate-VM (port2) # set ip 192.168.137.30 255.255.255.0 Fortigate-VM (port2) # Fortigate-VM (port2) # set allowaccess http https ping Fortigate-VM (port2) # end Fortigate-VM (port2) # Now we are finished with configuration.
Time to open the Fortinet VM web console. Open the IP() is browser. A login prompt will open then, type their only username(username: admin), then login. The VM GUI console will come up then. Now time to play with Fortigate. The detailed discussions on policy, access control, NAT, load balancing on Fortigate will be posted soon. Related articles across the web • • •.
Developer: Cyberlink Release Date: February 13, 2013 Crack Type: Patch Size: 843MB PLATFORM: Windows All Install instructions: 1.Unpack & Install 2. Install update by running 'CL.2418_GM4_Patch_VDE121106-01.exe' in 'Update' folder. Power director 10 free download. Uncheck 'remind me later' box and skip registration page 3. It marries great video editing features with other powerful tools such as photo editing and sound mastering.
The following topics are included in this section:
FortiGate VM models and licensing
Registering FortiGate VM with Customer Service & Support
Downloading the FortiGate VM deployment package
Deployment package contents
Deploying the FortiGate VM appliance
FortiGate VM models and licensing
Fortinet offers the FortiGate VM in five virtual appliance models determined by license. When configuring your FortiGate VM, be sure to configure hardware settings within the ranges outlined below. Contact your Fortinet Authorized Reseller for more information.
FortiGate VM model information
Technical SpecificationFG-VM00FG-VM01FG-VM02FG-VM04FG-VM08Virtual CPUs (min / max)1 / 11 / 11 / 21 / 41 / 8Virtual Network
Interfaces (min / max)
2 / 10Virtual Memory (min / max)1GB / 1GB1GB / 2GB1GB / 4GB1GB / 6GB1GB /12GBVirtual Storage (min / max)32GB / 2TBManaged Wireless APs (tunnel mode / global)32 / 3232 / 64256 / 512256 / 5121024 / 4096Virtual Domains (default / max)1 / 110 / 1010 / 2510 / 5010 / 250
After placing an order for FortiGate VM, a license registration code is sent to the email address used on the order form. Use the registration number provided to register the FortiGate VM with Customer Service & Support and then download the license file. Once the license file is uploaded to the FortiGate VM and validated, your FortiGate VM appliance is fully functional.
10
FortiGate VM Overview Registering FortiGate VM with Customer Service & Support
The number of Virtual Network Interfaces is not solely dependent on the FortiGate VM. Some virtual environments have their own limitations on the number of interfaces allowed. As an example, if you go to https://docs.microsoft.com/en-us/azure/virtualnetwork/virtual-networks-multiple-nics, you will find that Azure has its own restrictions for VMs, depending on the type of deployment or even the size of the VM.
FortiGate VM evaluation license
FortiGate VM includes a limited embedded 15-day trial license that supports: l 1 CPU maximum l 1024 MB memory maximum
l low encryption only (no HTTPS administrative access) l all features except FortiGuard updates
You cannot upgrade the firmware, doing so will lock the Web-based Manager until a license is uploaded. Technical support is not included. The trial period begins the first time you start FortiGate VM. After the trial license expires, functionality is disabled until you upload a license file.
Registering FortiGate VM with Customer Service & Support
To obtain the FortiGate VM license file you must first register your FortiGate VM with CustomerService& Support.
To register your FortiGate VM:
Log in to the Customer Service & Support portal using an existing support account or select Sign Up to create a new account.
In the main page, under Asset, select Register/Renew.
The Registration page opens.
Enter the registration code that was emailed to you and select Register. A registration form will display.
After completing the form, a registration acknowledgement page will appear.
Select the License File Download
You will be prompted to save the license file (.lic) to your local computer. See “Upload the license file” for instructions on uploading the license file to your FortiGate VM via the Web-based Manager.
Downloading the FortiGate VM deployment package
FortiGate VM deployment packages are included with FortiGate firmware images on the CustomerService& Support site. First, see the following table to determine the appropriate VM deployment package for your VM platform.
Downloading the FortiGate VM deployment package
Selecting the correct FortiGate VM deployment package for your VM platform
VM PlatformFortiGate VM Deployment FileCitrix XenServer v5.6sp2, 6.0 and laterFGT_VM64-v500-buildnnnn-FORTINET. out.CitrixXen.zipOpenXen v3.4.3, 4.1FGT_VM64-v500-buildnnnn-FORTINET.
out.OpenXen.zip
Microsoft Hyper-V Server 2008R2 and 2012FGT_VM64-v500-buildnnnn-FORTINET. out.hyperv.zipKVM (qemu 0.12.1)FGT_VM64-v500-buildnnnn-FORTINET.
out.kvm.zip
VMware ESX 4.0, 4.1
ESXi 4.0/4.1/5.0/5.1/5.5
FGT_VM32-v500-buildnnnn-FORTINET.
out.ovf.zip (32-bit)
FGT_VM64-v500-buildnnnn-FORTINET. out.ovf.zip
For more information see the FortiGate product datasheet available on the Fortinet web site, http://www.fortinet.com/products/fortigate/virtualappliances.html.
The firmware images FTP directory is organized by firmware version, major release, and patch release. The firmware images in the directories follow a specific naming convention and each firmware image is specific to the device model. For example, the FGT_VM32-v500-build0151-FORTINET.out.ovf.zip image found in the v5.0 Patch Release 2 directory is specific to the FortiGate VM 32-bit environment.
You can also download the FortiOS Release Notes, FORTINET-FORTIGATE MIB file, FSSO images, and SSL VPN client in this directory. The Fortinet Core MIB file is located in the main FortiGate v5.00 directory.
To download the FortiGate VM deployment package:
In the main page of the Customer Service & Support site, select Download > Firmware Images.
The Firmware Images page opens.
In the Firmware Images page, select FortiGate.
Browse to the appropriate directory on the FTP site for the version that you would like to download.
Download the appropriate .zip file for your VM server platform.
You can also download the FortiGate Release Notes.
Extract the contents of the deployment package to a new file folder.
FortiGate VM Overview Deployment package contents
Deployment package contents
Citrix XenServer
The FORTINET.out.CitrixXen.zip file contains:
vhd: the FortiGate VM system hard disk in VHD format l fortios.xva: binary file containing virtual hardware configuration settings l in the ovf folder:
FortiGate-VM64.ovf: Open Virtualization Format (OVF) template file, containing virtual hardware settings for
Xen l fortios.vmdk: the FortiGate VM system hard disk in VMDK format l datadrive.vmdk: the FortiGate VM log disk in VMDK format
The ovf folder and its contents is an alternative method of installation to the .xva and VHD disk image.
OpenXEN
The FORTINET.out.OpenXen.zip file contains only fortios.qcow2, the FortiGate VM system hard disk in qcow2 format. You will need to manually:
l create a 32GB log disk l specify the virtual hardware settings
Microsoft Hyper-V
The FORTINET.out.hyperv.zip file contains:
in the Virtual Hard Disks folder:
vhd: the FortiGate VM system hard disk in VHD format l DATADRIVE.vhd: the FortiGate VM log disk in VHD format
In the Virtual Machines folder:
xml: XML file containing virtual hardware configuration settings for Hyper-V. This is compatible with Windows Server 2012.
Snapshots folder: optionally, Hyper-V stores snapshots of the FortiGate VM state here
KVM
The FORTINET.out.kvm.zip contains only fortios.qcow2, the FortiGate VM system hard disk in qcow2 format. You will need to manually:
l create a 32GB log disk l specify the virtual hardware settings
VMware ESX/ESXi
You will need to create a 32GB log disk.
Deploying the FortiGate VM appliance
The FORTINET.out.ovf.zip file contains:
vmdk: the FortiGate VM system hard disk in VMDK format l datadrive.vmdk: the FortiGate VM log disk in VMDK format l Open Virtualization Format (OVF) template files:
FortiGate-VM64.ovf: OVF template based on Intel e1000 NIC driver l FortiGate-VM64.hw04.ovf: OVF template file for older (v3.5) VMware ESX server l FortiGate-VMxx.hw07_vmxnet2.ovf: OVF template file for VMware vmxnet2 driver l FortiGate-VMxx.hw07_vmxnet3.ovf: OVF template file for VMware vmxnet3 driver
Deploying the FortiGate VM appliance
Prior to deploying the FortiGate VM appliance, the VM platform must be installed and configured so that it is ready to create virtual machines. The installation instructions for FortiGate VM assume that
You are familiar with the management software and terminology of your VM platform.
An Internet connection is available for FortiGate VM to contact FortiGuard to validate its license or, for closed environments, a FortiManager can be contacted to validate the FortiGate VM license. See “Validate the FortiGate VM license with FortiManager”.
For assistance in deploying FortiGate VM, refer to the deployment chapter in this guide that corresponds to your VMware environment. You might also need to refer to the documentation provided with your VM server. The deployment chapters are presented as examples because for any particular VM server there are multiple ways to create a virtual machine. There are command line tools, APIs, and even alternative graphical user interface tools.
Before you start your FortiGate VM appliance for the first time, you might need to adjust virtual disk sizes and networking settings. The first time you start FortiGate VM, you will have access only through the console window of your VM server environment. After you configure one FortiGate network interface with an IP address and administrative access, you can access the FortiGate VM web-based manager.
After deployment and license validation, you can upgrade your FortiGate VM appliance’s firmware by downloading either FGT_VM32-v500-buildnnnn-FORTINET.out (32-bit) or FGT_VM64-v500-buildnnnnFORTINET.out (64-bit) firmware. Firmware upgrading on a VM is very similar to upgrading firmware on a hardware FortiGate unit.
Fortigate Vm64 Crack
Having trouble configuring your Fortinet hardware or have some questions you need answered? Check Out The Fortinet Guru Youtube Channel! Want someone else to deal with it for you? Get some consulting from Fortinet GURU!
Crack Fortigate Vm64 Key
Crack Fortigate Vm64 3
Don't Forget To visit the YouTube Channel for the latest Fortinet Training Videos and Question / Answer sessions! - FortinetGuru YouTube Channel - FortiSwitch Training Videos

1 note
·
View note
Text
How to setup linksys smart wi-fi router: linksyssmartwifi.com
Firmware updates for any router specifically acknowledged for bug fixes and functionality improvement of your router. An upgraded firmware that you have downloaded from the Linksys Support site (linksyssmartwifi.com) may additionally include some device specialty improvements that are not possible in the earlier versions. Thus, updating the Linksys router firmware is an essential factor and for further details, visit the web domain http://l-inksyssmartwifi.com/.
1 note
·
View note
Text
Installation and setup guide for Linksys AC1750 ?
Linksys AC1750 Wi-Fi Wireless Dual-Band+ Router with Gigabit, Smart Wi-Fi App allows you to Control Your Network from Anywhere (EA6500). The very first step is that you have to connect your Linksys router to the modem using the ethernet cable. Connect the ethernet cable with the computer system. Turn on the router by pressing the power button on your router. The LEDs will light. Type http://www.linksyssmartwifi.com into your web browser’s address bar or you can also type your router’s default IP address (192.168.1.1). Now a login page will appear on your screen with two fields to enter the username and password. The user name is “admin” and the password is “password” by default. Entries are case-sensitive. Click Log In. If you have already changed your password then enter the last password you used. The Linksys router homepage will appear. Click advanced settings and go to setup wizard. The router will detect your internet connection and prompt you to log in. Enter and confirm the new admin password. Then you have to select security questions and answers. Click Next and the congratulations page will appear.
Are you trying to troubleshoot Linksys EA6700 AC1750 Dual-Band Wi-Fi Router ? Linksys EA6700 AC1750 Dual-Band Wi-Fi Router is one of the best routers with high performance. Visit linksyssmartwifi.com. Now a login page will appear on your screen with two fields to enter the username and password. The user name is “admin” and the password is “password” by default. Entries are case-sensitive. Before you try to troubleshoot your router try the power cycle. If still you are unable to access the internet then the problem can be related to ISP. Follow the troubleshooting steps to fix the problem. Check cable connection first. We know about the Ethernet cable that connects the router and modem. It's the only method to keep each other connected. If the cable is cracked then it will disrupt the connection. You might get into the router not working problem and an orange light blinking on your router. If the cable is faulty change the cable. If the modem is still not working then you have to check if the router is overheating. Turn the router off for a minute every day to avoid overheating. If it is still not working check for IP conflict. Do not forget to check the IP address of your router and modem. If they belong to the same class then their ip address will be conflicting. In such a case you need to change the ip address of your router. Sometimes it doesn't work because your firmware is not updated. So do not forget to update your firmware. To check whether your firmware needs any update open router setup page then choose administration and select update firmware. Now click on the update button and your firmware is updated. If still you are not able to connect to the internet clone your Mac address. If your internet is still not working then you should factory reset your linksys router and set it up again. If still your router isn’t working then there is a hardware failure. You need to replace your router.

How can I change the admin password for Linksys EA6900-AP AC1900 Dual Band Smart Wi-Fi Router ? Linksys EA6900-AP AC1900 Dual Band Smart Wi-Fi Router provides Latest Draft 802.11ac wireless technology, Backwards compatible with 802.11a/b/g/n devices, Gigabit Ethernet Ports, 2 USB ports (1 x USB2.0 & 1 x USB3.0) and integrated DLNA Certified Media Server, Max. Link Rate: 1300 Mbps. The linksyssmartwifi.com is the web domain to access the linksys router setup without the need to memorize complicated IP addresses. The credentials to linksys router login are “admin” and both the username and password are the same. You can also check the linksys login details mentioned in a sticker on your router. To change the password select Management> Access control and tap password. Three fields will appear, old password, new password and confirm new password. Enter the details respectively. Save and apply settings. Now restart the router. Why is Linksys EA7300 MAX-STREAM™ AC1750 MU-MIMO Gigabit WiFi Router not working ? Linksys EA7300 MAX-STREAM™ AC1750 MU-MIMO Gigabit WiFi Router provides uninterrupted Next-Gen AC WiFi to all your devices at the same time, same speed. Before you try to troubleshoot your router try the power cycle. If still you are unable to access the internet then the problem can be related to ISP. Follow the troubleshooting steps to fix the problem. Check cable connection first. We know about the Ethernet cable that connects the router and modem. It's the only method to keep each other connected. If the cable is cracked then it will disrupt the connection. You might get into the router not working problem and an orange light blinking on your router. If the cable is faulty change the cable. If the modem is still not working then you have to check if the router is overheating. Turn the router off for a minute every day to avoid overheating. If it is still not working check for IP conflict. Do not forget to check the IP address of your router and modem. If they belong to the same class then their ip address will be conflicting. In such a case you need to change the ip address of your router. Sometimes it doesn't work because your firmware is not updated. So do not forget to update your firmware. To check whether your firmware needs any update open router setup page then choose administration and select update firmware. Now click on the update button and your firmware is updated. If still you are not able to connect to the internet clone your Mac address. If your internet is still not working then you should factory reset your linksys router and set it up again. If still your router isn’t working then there is a hardware failure. Else you will need to replace your Linksys router.
How can I recover the admin password using the password recovery feature for Linksys EA7400 Max-Stream™ AC1750 MU-MIMO Gigabit Router ? The Linksys EA7400 Max-Stream™ AC1750 MU-MIMO Gigabit Router is a 3x3 802.11ac dual-band Smart Wi-Fi router with one USB 3.0 and one USB 2.0 port. It supports data rates of up to 450 Mbps on 2.4 GHz and 1300 Mbps on 5 GHz networks. Type http://www.linksyssmartwifi.com into your web browser’s address bar. A login window will appear. Click CANCEL. The Router Password Recovery window shows. Enter your router’s serial number and click CONTINUES. Answer your security questions. If you cannot answer your security questions, then look for: How do I perform a factory reset on my Linksys router? Click CONTINUES. Your admin password will be displayed.
1 note
·
View note
Text
DOWNLOAD HP 5SI NX DRIVER
File Size: 23 Mb File Name: hp 5si nx driver Date Added: 08 December, 2019 Downloads: 4421 Uploader: Tulsi File Version: 911111966 Price: Free File Format: exe Download Type: http Operating Systems: Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X

Fixed Issues: - Fixed issue where playlists not ending in(hp 5si nx driver in) a line-break wouldn't execute the last play command. - Fixed the hanging issue occurred in “File Manager”. - Fixed LED Issue. - Fixed when Failover/Failback enabled, RTSP Passthrough, Multicast routing, Efficient Multicast settings could not be applied issue. - Fixed X9650 CPU not adjust ratio. - Fixed the issue that cannot input(hp 5si nx driver input) password in the login window for RTSP authentication. - Fixed S3 of JMB363 to wake then no reaction. - Network - Fixed a bug where access restrictions(hp 5si nx driver restrictions) with domain users reverted to "disabled" after restarting the unit. - Fixes & Enhancements: - Resolved issue with ZTE MF823. - Resolved issue with E3276 and frequency selection. - Fixed(hp 5si nx driver Fixed) “Test FTP” and “Test Email” Button Errors. Users content: Support transfer rate of 2000/1600/1200/800/400 mega-transfers per second. The WIP310 no longer sends registration request. Eyefinity advanced setup options may sometimes not appear in Radeon Settings after a driver upgrade. Valid firmware files have an .eff extension. - Split screen and horizontal lines after resuming from Sleep (S3) mode, after the display driver was updated by Windows Update. Hz- Supports DisplayPort with max. If you want support for additional (non-English) languages, and copy the LANGUAGES. Setting the display resolution to 1440x900 or lower may result in corruption being noticed when playing a DVD title. Bug fix - Following bugs were fixed - Can not use device font when set the barcode font to alias. Improved format of 3G statistics on WEB GUI. - Added the redundant check on the QoS and Packet Filter Rule. http://qy5relevantfilescollection.cba.pl/infusions/blog/blog.php?readmore=152 Supported OS: Microsoft Windows 8 Pro (32-bit) Microsoft Windows 8.1 (32-bit) Windows Server 2003 32-bit Windows Server 2016 Microsoft Windows 8 Pro (64-bit) Microsoft Windows 8 (32-bit) Windows Vista 32-bit Microsoft Windows 8.1 Enterprise (64-bit) Windows Server 2008 Microsoft Windows 8 (64-bit) Windows XP 32-bit Notebook 8.1/8/7 64-bit Microsoft Windows 8.1 Pro (64-bit) Windows 8.1/8/7/Vista 64-bit Windows Server 2008 R2 Microsoft Windows 10 (64-bit) Microsoft Windows 8 Enterprise (32-bit) Windows Vista 64-bit Microsoft Windows 8.1 Pro (32-bit) Windows 7 32-bit Windows 7 64-bit Notebook 8.1/8/7 32-bit Windows Server 2003 64-bit Windows 8.1 Microsoft Windows 10 (32-bit) Microsoft Windows 8 Enterprise (64-bit) Windows Server 2012 R2 Windows XP 64-bit Windows 8 Windows 10 Windows Server 2012 Windows 8.1/8/7/Vista 32-bit Microsoft Windows 8.1 Enterprise (32-bit) Windows 2000 Microsoft Windows 8.1 (64-bit) Windows 7 Searches: hp 5si nx E EL651-6; hp 5si nx driver for Windows 7; hp 5si nx ELOWV6514; hp 5si nx E65z; hp 5si nx driver for Windows 2000; driver hp 5si nx; hp 5si nx driver for Microsoft Windows 8 Enterprise (64-bit); hp 5si nx Ezc651-zcs; hp 5si nx driver for Notebook 8.1/8/7 64-bit; hp 5si nx EL6514; hp 5si nx driver for Windows Server 2008 R2 Compatible Devices: Keyboards; Memory Card; USB Hubs; Gadget; Tablet; Usb Cables To ensure the integrity of your download, please verify the checksum value. MD5: bfa877830863283dfa691e2fbcc9d4c5 SHA1: cfda0c9f5a0eec4c6b873953e7624e8a30d1ee7d SHA-256: e5ce77203d578ad506afd90913e3852e8629c4a55134bbc4f44e42e1f744ba91
1 note
·
View note
Text
How can the user set up Linksys smart wifi router

The user can set up its brand new Linksys smart wifi router very easily. You can also check the Linksys router setup. First, you need to unwrap the Linksys smart wifi router. After this, you can unplug your modem. After this, you can attach your Linksys wifi router using an ethernet cable with the modem. You can also click on the Linksys wireless router setup. Here you need to attach your computer using the ethernet cable with the Linksys smart wifi router and the modem. After this, you can connect the router with the power adapter than with the power supply.

Some important features of the Linksys router setup.
. Here you can open a web browser if you need help check the Linksys smart wireless router setup.
. Now you can enter the www.linksyssmartwifi.com
. Here you can enter the login details. You can also check the Linksys router login.
. After this, you can access the web domain page.
. You can also set up your Linksys smart wifi router with the help of the Linksys smart app.
. Now you can easily set up your Linksys smart wifi router.
. First, you need to install the Linksys smart app, you can also take assistance from how to set up a router Linksys.
. Here you can only scan the QR code of the Linksys smart wifi router.
. It takes a few seconds to catch the settings.
. After this, you can easily log in to settings, for more details check the Linksys router login page.
. Here you can update your Linksys smart wifi router firmware.
. You need to launch the web browser after this you can enter the www.linksyssmartwifi.com.
. Now you can enter the login details.
. Here you can go to the advanced settings.
. Now you can click on the firmware update, it takes a few seconds for the update.
. After this, you will get the latest firmware of your Linksys smart wifi router. If you have any query please feel free to check Linksys smart wifi login.
#linksys smart wifi login#linksys router login page#linksys router login#linksys router setup#how to setup a router linksys
1 note
·
View note
Text
Internet of Things IoT Smart Kitchens a Reality
Right now, there are over 3 Billion devices connected to the web. Most of which, we actually don't desire somebody hacking into. The number of connected devices is increasing exponentially as a product of the expansion in IoT (Internet of Issues) gadgets and those units are surrounded by controversy relating to their current level of safety.
What's an IoT device? In brief, it is any gadget that has been given the aptitude of speaking over an IP network. Said one other method, IoT units embrace hardware that permit two-way communication over a Wi-Fi network. Suppose mild bulbs that may let you know whether they're on or off and could be managed from anywhere on the planet with an internet connection. The extra of the gadgets in your life that may communicate this way, the larger the specter of hacking.
There have already been numerous movies and demonstrations of hackers taking management of autos that have embedded network connectivity. While the thought of somebody having remote management of your car is threatening, the larger risk is the one you won't see.
Think about having your complete file from your driving habits and behaviors ending up in undesirable hands. If a hacker can take information out of your automobile, it would be on level to assume they'll take data from much smaller and cheaper units. www.eelinktech.com/ So, who exactly regulates and makes positive that the safety in our IoT items are literally safe? Underwriters Laboratories (UL) is at present attempting to fill within the gap that buyers is likely to be feeling relative to IoT and safety concerns.
So what is the "hole" that Underwriters Laboratories is at the moment making an attempt to fill in? Nicely, as with computers, IoT objects can have firmware and software. As you most likely know, your software/firmware usually gets upgraded/up to date when there has been a fault or weak-level detected in the product. Imagine you purchase a automobile Iot device Manufacturer that's "unhackable", only to search out out 5 months later that a hack has been developed to focus on your car. What do you do until the company releases a repair? In addition, the manufacturer still has the same certification on the window which leads new patrons to assume that they are protected when truly, that is not the case.
The products you purchase can undergo many safety exams before they go away the factory, however, as time goes on, vulnerabilities can nonetheless be found. If the producer isn't persevering with to help their products after launch, you might need to avoid their products or the whole resolution itself. As our IoT technology will get extra advanced and intuitive, a hacker's arsenal is doing the Click here for Wikipedia same. The important thing take away is that buying and utilizing IoT gadgets comes with a few of the similar overhead that maintaining and sustaining a daily LAPTOP does. All the time be sure to concentrate to what updates your IoT items have. As annoying as updating a device's software program is, it's necessary to maintain your self forward of the hackers looking for your vulnerabilities.
IoT (Web of things) has turn out to be one of the vital superior technological approaches at this time with its anticipated growth of over 26 billion related devices by 2020, according to Gartner. IoT will have an effect on among the best automation products by that time. Automation in dwelling, industries, and in workplaces will develop into a serious development space for the startups in addition to established companies. Let's take a look at some of the most modern IoT corporations we've as we speak, and see how they will pave technique to a better tomorrow.
Nest was just lately acquired by Google due to its robust presence in the dwelling automation house. Nest is a home automation merchandise company primarily based in Palo Alto, California, where Google itself is headquartered. Nest produces sensor-pushed self-studying thermostats and smoke detectors. These units are AI-prepared, which means they will be taught your environments and necessities and function accordingly.
New-York-primarily based Quirky is an revolutionary company that designs, manufactures, and provides sensible units that can suppose on behalf of the users. The modern factor about Quirky is you can submit your personal ideas for creating among the innovative merchandise. Founded in 2009, the firm obtain its preliminary funding of 6 million in 2010. In 2012, the company received 68 million funding from Andreessen Horowitz and Kleiner Perkins Caufield & Byers. They've created dwelling automation merchandise that learn based on your utilization of them.
Already established Philips is a multi-billion dollar Dutch firm manufacturing plenty of electronic objects, equivalent to LED gentle bulbs. One of the current improvements from Philips is the Hue lighting system that adjustments colours based in your wants and moods. Philips concentrates on electronics, healthcare, and lighting primarily.
We know Jawbone from its Up fist band that displays your exercise traits. Jawbone Up has develop into so widespread and hip that it enjoys a big person base from iPhone and Android users. The Jawbone product makes use of the low-vary, low-energy Bluetooth low vitality protocol to constantly monitor the workouts you do to maintain your self in form.
Washington DC-primarily based SmartThings is a know-how innovations company that makes home automation hubs base on cloud computing platforms for Android, Windows Telephone, and iOS customers. You need to use the SmartThings hub to attach and monitor various units in your house utilizing just your smartphone remotely.
ARM is known far and vast as the important thing manufacturer of smartphone processor architectures. The high-finish architectures created by ARM is the premise of a lot of the smartphone processors that we have at this time, including Snapdragon and Apple iPhone processors. ARM can also be at the forefront of sensor manufacturing for various devices and issues that may be connected to the IoT sphere.
Atmel is a large manufacturer of microcontrollers, capacitive contact screens, advanced logical and digital circuits, Social Network Here and RF parts. These components are integral to each IoT device and the sensors associated with it.
Network system producer Cisco also has a huge presence within the IoT market. Cisco's current leadership in the networking hardware market enabled it to capitalize on the IoT market on the right time. Additionally, the profitable implementation of IoT requires extremely sturdy network infrastructure, which is Cisco's robust level.
Within the semiconductor market, Intel is the final word provider. This experience has helped Intel to safe high spot within the semiconductor market for IoT. Semiconductors type an integral a part of each electronic system. Because of this, a leading
Beyond Google, IBM, Oracle, and SAP, Microsoft has secured one of many very prime spots for the software growth in the IoT domain. Primarily based on internet analytics rankings, Microsoft is the number two firm in IoT domain with software program as its main power.
IoT is a powerful space of improvement and progress, with enormous variety of opportunities for sturdy gamers who make their entry on time. This is the rationale why capitalizing on the IoT domain will help companies achieve enormous growth potential within the coming years.
China suppliers have intensified efforts to develop an IOT commonplace, which they hope would be the benchmark for a global regulation. Eelink Tech Presently, the dearth of a unified standard and high chip costs are preventing mass manufacture of IOT products.
Still in its nascent stage, the Internet of Issues trade has seen worldwide improvement acquire pace in 2010. However widespread adoption does not appear doubtless in the near future, just because a global customary shouldn't be but in place.
IOT refers back to the networked interconnection of assorted units and appliances. A unified regulation is critical as a result of devices have to follow one protocol to be able to work together and obtain clever control. The interface and chips must be standardized. And not using a global communications protocol, IOT product manufacturers can be unable to work with change operators and retailers. Such gadgets then would be no completely different from abnormal merchandise resembling standard home home equipment.
The US, the EU, Japan and China have all intensified efforts to come up with Click here for our Blog their own commonplace, which may then be the basis for a world regulation.
Several of China's largest export manufacturers have been within the IOT field since 2005, some even earlier. Dwelling home equipment, good meters and digital tags are just a few examples of products that have been built for networked interconnectivity. These companies shaped a group to work on an Clever Grouping and Resource Sharing normal that would regulate IOT development.
The sooner they can provide you with a home commonplace, the simpler it will be to pitch said regulation for worldwide use. This can then scale back technical limitations for China suppliers, who also wouldn't must pay IP fees to organizations in developed international locations.
The Midea Group and the Haier Group have each been in a position to develop core management chips and are now engaged on integrating the power grid with the intercommunication, Internet, radio and TELEVISION networks.
Haier has already obtained approval for seven trade and 9 national IOT standards. It has also submitted purposes for two worldwide standards, of which one could be China's first within the dwelling community discipline. The corporate has additionally utilized for greater than 1,000 patents for its IOT home home equipment line.
2 notes
·
View notes
Text
Miracast for Windows 7
Miracast for Windows 7 is a complicated wi-fi science that may support your project your home windows 10 computer’s reveal to tv, projectors, screens, and different streaming devices that additionally aid Miracast.
Many of the state-of-the-art PCs help Miracast. Windows 10 customers can use Miracast to reflect home windows 10 PC's screen to tv, reveal or projector.
If you just lately purchased a mid to high-end Windows 10 computer, then your computer seemingly supports Miracast. But the best way to determine if your windows 10 computer helps Miracast?
Of direction, which you can examine your PC's guide or contact the company to assess in case your pc has Miracast. Moreover to these approaches, there are two easy methods to assess if the Miracast wi-fi science is to be had to your computer.
Also, Read Turbo VPN for PC

Supported Intel wireless show structures:
home windows 7, Intel wireless display V3.1.29.0, Wifi driver V15.1.1
home windows 7, Intel wi-fi show V3.5.41.Zero, Wif driver V15.Three.1
windows eight (methods upgraded kind home windows 7), Intel wireless display V3.5.41.Zero, Wifi driver V15.3.50
windows eight (with Win8 preinstalled), Intel wireless display, V3.5.41.0, Wifi driver V15.5.7
Supported Miracast structures:
Samsung Galaxy S3 (Android four.1.1 or above)
Samsung Galaxy observe II
Samsung Galaxy notice 10.1
LG Optimus G (Android 4.0.Four or above)
Google Nexus four (Android four.2.1)
Sony Xperia (various models with Android 4.Zero.4 or above)
Enhancements & trojan horse Fixes:
Also, Download Super VPN for PC
Miracast support for suitable mobile telephones and drugs.
Combined Intel wireless show (Widi) and Miracast a single user interface. There is no ought to use the frenzy button on the facet of the PTV3000 unit to change between WiDi and Miracast mode.
(Miracast) both PIN and percent methods for WPS are supported. The gadget mechanically communicates with the supply device (cellular cellphone, pill or computer) to assess which WPS system to use.
(Miracast) The gadget is already percent equipped ready for supply to initiate the connection.
Fixed HDCP connection error difficulty with some Sony mobile telephones.
The fixed dilemma that display projection does not take position except swiping action takes the situation on a cellular mobile phone.
Fixed some disconnection with cell cellphone.
The device does not permit 2d Widi or Miracast source device to interrupt the present WiDi or Miracast session.
Permit 5Ghz Miracast operation with the desired running channel as channel 40.
Decreased photograph size and faster boot time.
Fixed process lockup hindrance after improper PIN entry.
Improved connectivity with Intel WiDi jogging below Win8. Repaired hindrance in win8 that device connection has obstacle after elimination of gadget under gadgets and Printers interface in Win8.
The constant quandary of connecting reveal appearing after a session teardown on Win7 laptop.
The constant challenge of 1 Wide session affecting display projection of subsequent Widi or Miracast session.
(Wide) the fixed challenge of cursor position not up to date unless “resize television image” takes situation.
Constant kernel panic trouble that procedure goes into a non-responsive state.
Enforce regional domain control enabling cargo to Europe, Australia, and Canada.
Also, Read VPN Master for PC
Localization aid for worldwide languages.
Dongle Tries to attach mechanically even after a guide Disconnect.
Win8 PIN pairing occasions out too soon.
WFD session exited abnormally (and inaccessible for some time).
Dongle locks up utterly and is inaccessible when halting the WFD organization method. Additionally, fixed the infrequent subsequent kernel panic in that.
Win8/Widi 3.5.41. Zero, N6235, WiFi 15.5.7 television reveal error message or no display projection (Acer H233H reveal).
In many instances unable to connect with Samsung series 5 Win8 Laptops.
Win8 WiDi mouse cursor function is off.
Download Miracast for Windows 10
Set up procedure
Push and preserve the WPS button on the facet of the PTV3000 unit for greater than 5 seconds.
Utilizing the download link below, download and extract the new firmware to an easy position reminiscent of your laptop.
PTV3000 goes into firmware replace mode. Firmware update approach suggests up on tv screen (additionally shown under on steps 3 to six).
Making use of the wireless community supervisor utility for your device, seek for "Push2TV" wireless community title (SSID) and fasten.
Open an online browser to your device and kind http://192.168.Three.1 into the URL bar of the browser.
Comply with the steps on the web page to upload the firmware photo and whole the setup.
More info Clicks helpsforpc
1 note
·
View note
Text
Azure cloud infrastructure and application testing

Introduction to quality assurance
Quality assurance (QA) is an umbrella term which encompasses all software and infrastructure quality tests that are performed to verify software application and infrastructure functional and non-functional attributes, including performance, scalability, availability and security. Azure cloud infrastructure and application testing is a major part of quality assurance. There are QA frameworks to be used for both software application and cloud infrastructure testing. Whether you perform QA using testing frameworks or you manually perform a baseline of tests, you need to have test scripts available. Each test script describes the steps to be carried out to test a certain aspect of an application or infrastructure system, as well as the result of each test and subsequent action items, if needed. This article provides a baseline reference of the steps to be included in each type of infrastructure or application test script alongside with a testing script template available for download.
Azure cloud infrastructure and application testing types
The following types of infrastructure and application test scripts are available: - Application unit testing. A unit test is a test that exercises individual software components or methods, also known as a "unit of work." Unit tests should only test code within the developer's control. They don't test infrastructure concerns. Infrastructure concerns include interacting with databases, file systems, and network resources. xUnit.net is a free, open source, community-focused unit testing tool for the .NET Framework. - Application integration testing. An integration test differs from a unit test in that it exercises two or more software components' ability to function together, also known as their "integration." These tests operate on a broader spectrum of the system under test, whereas unit tests focus on individual components. Often, integration tests do include infrastructure concerns. - Application load (or stress) testing. A load test aims to determine whether or not a system can handle a specified load. For example, the number of concurrent users using an application and the app's ability to handle interactions responsively. Refer to my KB article on Azure App Service load testing (using JUnit) for an example of carrying out load testing for an Azure-based Web application. - Infrastructure functional testing. This aims to test all operating systems, firmware and the functional attributes of on-prem or cloud infrastructure components involved in a solution. - Performance and scalability testing. During performance and scalability testing, you measure the performance metrics of your infrastructure as your application workload increases. This is combined with application software stress/load testing. The performance and scale tests involve setting up and testing autoscale policies for scaling horizontally or vertically when the application load requires it. - Availability testing. Availability tests mainly focus on testing the resiliency of your infrastructure in the event of hardware or software components failures and the associated potential downtime incurred during these failures. This should test your infrastructure and application code high availability, redundancy and resiliency. Resiliency can come in many forms, including load balancing, failover clustering (active-active or active-passive) and always on availability groups, virtual machine availability sets as well as cloud infrastructure fault domains, update domains, cloud zone and cloud region redundancy. The availability tests focus on creating deliberate failure simulation events, such as for example having an Azure VNET or subnet or storage account going down, to check the impact on the overall architecture. - Security testing. Security testing aims to test the attack surface of your architecture, the resiliency against malicious attacks, including ransomware, malware and hacking attempts and to discover potential vulnerabilities and security weaknesses in your security configuration by employing techniques such as penetration testing to evaluate IDS/IPS, Web Application Firewall protection, SIEM/SOAR/XDR systems. Azure Advisor, Azure Security Center, Azure Advisor, Microsoft Defender for Cloud and Azure Sentinel are all good tools to employ for security testing.
Site Reliability Engineering (SRE)
The success of your cloud solution depends on its reliability. Reliability can be broadly defined as the probability that the system functions as expected, under the specified environmental conditions, within a specified time. Site reliability engineering (SRE) is a set of principles and practices for creating scalable and highly reliable software systems. Increasingly, SRE is used during the design of digital services to ensure greater reliability. The degree of reliability that's required for a solution depends on the business context. Reliability is defined and measured using service level objectives (SLOs) that define the target level of reliability for a service. Achieving the target level assures that consumers are satisfied. The SLO goals can evolve or change depending on the demands of the business. Another important term to note is service level indicator (SLI), which is the metric that's used to calculate the SLO. SLIs are based on insights that are derived from data that's captured as the customer consumes the service. SLIs are always measured from a customer's point of view. SLOs and SLIs always go hand in hand, and are usually defined in an iterative manner. SLOs are driven by key business objectives, whereas SLIs are driven by what's possible to be measured while implementing the service. The relationship between the monitored metric, the SLI, and the SLO is depicted below:

Refer to the Reliability and Performance Efficiency pillars of Azure Well Architected Framework for guidance on building scalable and reliable applications.
Chaos Engineering and Azure Chaos Studio
Chaos engineering is a methodology that helps developers attain consistent reliability by hardening services against failures in production. Another way to think about chaos engineering is that it's about embracing the inherent chaos in complex systems and, through experimentation, growing confidence in your solution's ability to handle it. A common way to introduce chaos is to deliberately inject faults that cause system components to fail. The goal is to observe, monitor, respond to, and improve your system's reliability under adverse circumstances. For example, taking dependencies offline (stopping API apps, shutting down VMs, etc.), restricting access (enabling firewall rules, changing connection strings, etc.), or forcing failover (database level, Azure Front Door, etc.), is a good way to validate that the application is able to handle faults gracefully. Azure Chaos Studio is a managed service that uses chaos engineering to help you measure, understand, and improve your cloud application and service resilience. Chaos engineering is a methodology by which you inject real-world faults into your application to run controlled fault injection experiments. Chaos Studio helps you avoid negative consequences by validating that your application responds effectively to disruptions and failures. You can use Chaos Studio to test resilience against real-world incidents, like outages or high CPU utilization on virtual machines (VMs).

In Azure Chaos Studio, you first select and enable your targets (either service-direct targets or agent-based targets, such as VMs and VM Scalability Sets).
Then you create Chaos experiments on selected Azure resources, as shown in the example below. Each experiment can introduce either faults or delays, to test the resiliency of the overall infrastructure in relation to the tested Azure resources.

Infrastructure as Code (IaC) testing frameworks and tools
The most prominent Infrastructure As Code languages in Azure are Azure ARM (JSON), Bicep and Terraform. Each of them has its own methods and tools for testing the IaC configuration. - Terratest is a tool to be used for testing Terraform modules. Terratest is implemented as a Go library. Terratest provides a collection of helper functions and patterns for common infrastructure testing tasks, like making HTTP requests and using SSH to access a specific virtual machine. - Bicep code can be tested by using Azure Pipelines or Powershell PSRule or even combine PSRule in Azure Pipelines. - ARM templates can be tested by employing the ARM template test toolkit. The Azure Resource Manager template (ARM template) test toolkit checks whether your template uses recommended practices. When your template isn't compliant with recommended practices, it returns a list of warnings with the suggested changes. By using the test toolkit, you can learn how to avoid common problems in template development. You can also test ARM Templates by using Pester and Azure DevOps. - Use Pester for Powershell or Powershell DSC scripts. - - Azure Policy Test Framework is a command line tool to test Azure Policy relying on Terraform + Golang.
Testing script template
You can find a free testing script template in the "Free Downloads" section.
References
https://learn.microsoft.com/en-us/azure/architecture/example-scenario/apps/scalable-apps-performance-modeling-site-reliability https://learn.microsoft.com/en-us/azure/chaos-studio/chaos-studio-overview https://learn.microsoft.com/en-us/azure/architecture/framework/resiliency/chaos-engineering https://learn.microsoft.com/en-us/dotnet/core/testing/ https://learn.microsoft.com/en-us/azure/developer/terraform/test-modules-using-terratest Read the full article
0 notes
Link
Course Information
�� Nisa Trainings
· IBM Data power Training
· Duration: 30 Hours
· Timings: Weekdays (1-2 Hours per day) [OR] Weekends (2-3 Hours per day)
· Training Method: Instructor Led Online One-on-One Live Interactive Sessions.
#ibmdatapowertraining#ibmdatapowercourse#ibmdatapowertutorial#ibmdatapowerjobs#ibmdatapowercertification#ibmdatapowersoftware#whatisibmdatapower#ibmdatapowercorporatecourse
0 notes