Photo

⟟⍑’⎎ 🜅⌰⎾⎾ ⌾🜅 ⎎⍑⍲☈⎎ DVI_23 with my star @curlyjoe01 (at Los Angeles, California) https://www.instagram.com/p/CoRlAMmOQbqiGsspLpWGYH-N-UdoO_lUjFcoNc0/?igshid=NGJjMDIxMWI=
3 notes
·
View notes
Text
SEXTRANCE Rave at Church of Fun LA
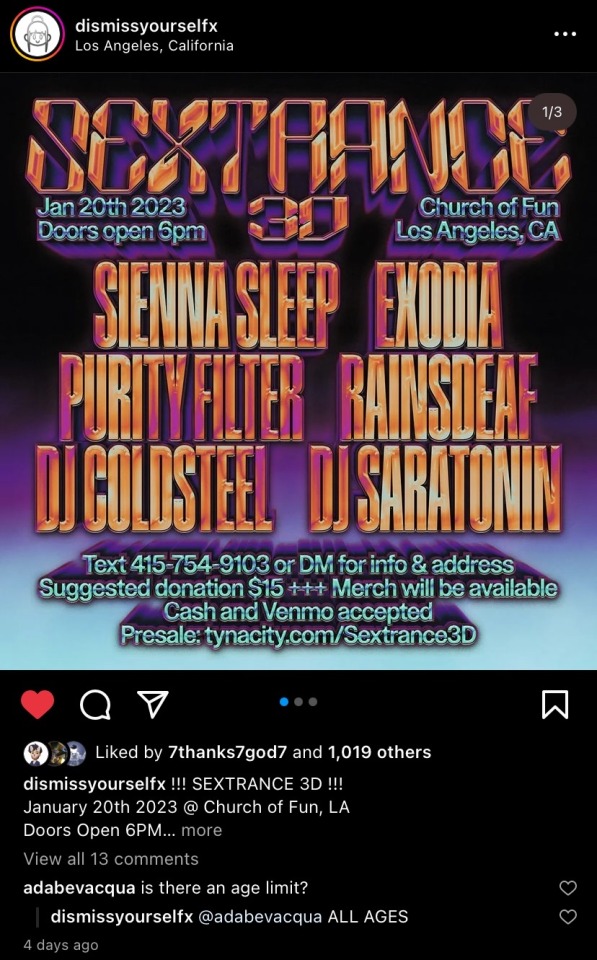
Blogpost about attending a rave in LA hosted by dismissyourself. Seeing some of my favorite acts and a wicked cool night with Tess.
I bought tickets for the Sextrance 3D Rave at the Church of fun some weeks prior, Tess and I had worked ourselves into a fever pitch with excitement. We would be seeing a huge line up from the collective Dismiss Yourself. You can find their website at the following link: here. Dismiss yourself is a music collective curating some of the most aggressive and experimental electronic music out right now. The roster for this evening included Purity Filter, Sienna Sleep, Exodius, to name a few.
I got off work a little early and headed over to our apartment where Tess was already decked out in her Rave wear. She was wearing a Neon Iridescent Bikini Top, made out of that hyperreflective material that reflects light all crazy and atop of that a BDSM Harness that I had got for her. Her make up was crazy and she had what must have been a half a bottle of glitter on her face, making her look like a cybernetic goddess. I opted to contrast her look by dressing in all black and wearing my Machine Girl Hoody. I looked like a Ninja, while she looked like an LSD Princess. She was towering around in her Pink heels spraying fixative on her make up when I walked into our Apartment.
We got together a little Rave Go Bag Together. In it was our supplies for the rave. Elixirs and concoctions. Potions and the like. Neon liquids in little bottles for our consumption. We had plenty of Gummys, some candy, Soda and Soft Drinks, plus a couple shots of Vodka. Extra Clothes and some party favors.
We drove up as the sun was setting and were blasting hardcore trance and gabber music on the ride up: [2022] Exodia - Valkyria - YouTube
youtube
The night swallowed us whole as we raced up to Los Angeles. The Skyline over took us as the lights of the Sky Scrapers towered over us. We got to the church of fun and the show was already underway. We showed our reservations and got into the main dance hall.
The Projector had us in a first person shooter of some kind, while the trance music pounded our chest hollow. We let the elixir over take us as we began to move to the pounding electronic grooves drill harder and harder into the night. The lights and music a swirl of beauty entering your Soni spherical body one set after another.
As Tess and I walked through the grand doors of the Church of Fun, a wave of excitement washed over us. The once holy sanctuary had been transformed into a pulsating techno paradise, with glowing neon lights illuminating the altar and the sound of thumping beats filling the air.
We made our way through the crowd, taking in the sights and sounds of the rave. The walls were adorned with holographic projections of swirling first person shooter graphics, while the walls were lined with LED lights that pulsed in time with the music. We could see cyberpunk-clad ravers dancing wildly, their bodies a blur of motion as they lost themselves in the rhythm.
As we reached the dance floor, Tess and I couldn't resist the pull of the music any longer. We let ourselves get swept up in the energy of the crowd, our bodies moving in a frenetic glitch set to the beat. The music was like a drug, coursing through our veins and igniting every fiber of our being.
With every passing moment, the techno symphony grew more and more intense, the lights and visuals becoming more and more mesmerizing. As the night wore on, Tess and I were lost in a techno trance, lost in the beauty of the moment.
As the sets died down so did we. We got out of there a hot and sweaty mess. Tess' make up was runny and she looked like she had been ravaged by a technological beast and yet still as gorgeous as ever. We wound down the night at astro burgers. Catching our breath over some burgers and fries. We ate inside the neon lit chromed out diner, the paper wrapped around our burgers crinkling while we ravenously ate, covered in sweat and joking about. We finished up and drove home to have a few drinks watch a movie and pass out.
youtube
#rave music#trance music#church of fun#los angeles music culture#dismiss yourself#purity filter#sienna sleep#aeonborealis#cyberpunk#design#music#Youtube#curly joe
3 notes
·
View notes
Video
youtube

Psychotrance 2 (1995)
T World* – Anthem
Norma G.* – Son Of Norma
Josh Wink – Liquid Summer
The Advent – Level X
Gyrate – Touchdown
F.E.O.S. vs. M/S/O – Music Was Sent
Stefan Robbers – Mask EP
Nüw Idol – Z I M
Soundscape – Darkside
Manuel And Clive – Recognised
Dave Angel – Artech
Acid Jesus – Move My Body
218 notes
·
View notes
Text
Deadrazy
There is not much information on this artist. I have become obsessed with them after hearing their album on the dismiss yourself channel. Quickly becoming my go to album for everything I do. Working out, coding, fucking around. Whatever. Deadrazy is insane. So abrasive, so beautiful. Its hard to describe how brutal Deadrazy is. How hard and how grimy. It sounds like the mutating guts of a computer twitching and pulsating back to life, like some deranged technologic growth.
youtube
#deadrazy#soundcloud#music#idm#grime#spiritual#death#goth#killyourself#cyberpunk#tunes#marijuana#Youtube
1 note
·
View note
Text
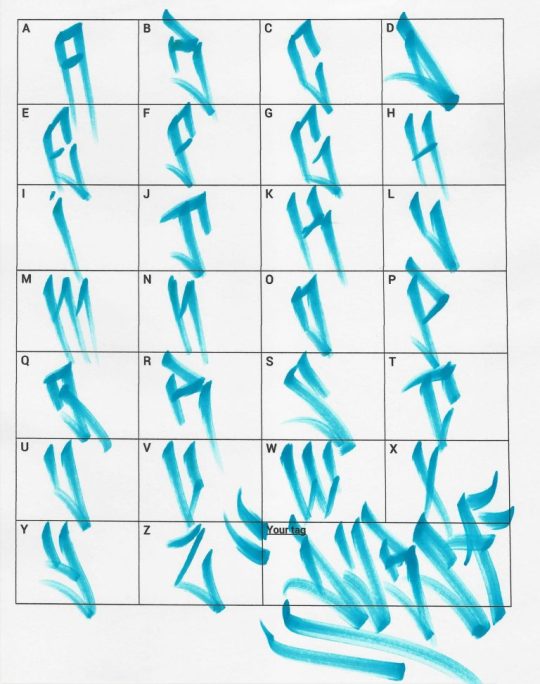
Graffiti Hand Styles
A few years ago I came to the realization that street art was the most viable form of self expression that exists today. In my mind it is one of the only legitimate forms of self expression still left. Not music, not art in the traditional sense, all of these disciplines have been co-opted by capitalism and through these processes has lost most significance of Artistic Merritt. That's just my opinion.
In the world of hand styles we see that the process of letter forms has been taken to levels not formally explored by calligraphy.
The greatest Calligraphers that have ever lived are probably alive today and have taken to writing their messages on walls.
The art of the hand style has pushed this to levels never imagined before, taking the simple roman letter forms and creating works that bend and warp all sensibilities of traditional taste.
Hand Styles should stay so niche. Only legitimate "hand stylers" understand the art of the hand style. They are the only ones who can speak to the choices, to the style and more directly, are often the only ones who can read other hand styles.
The creation of a stylistic alphabet that naturally evolves out of years of repetition and work in this discipline has created some of the most original and most beautiful works of the human hand that have ever existed. Again this is just my opinion, but to back up my opinion. I will share with you several hand styles by several of the best hand stylers ever profiled. Enjoy.







#hand styles#street art#graffiti#design#handstyle#graffittiart#calligraphy#streetart#cyberpunk#anarchism#punk
8 notes
·
View notes
Text
System Review: iXi lang
iXi Language
Ixi language or ixilang is a live coding musical environment designed to function as a way to code musical expressions and algorithms. It was designed by Thor Magnusson and has been maintained and updated by a core dedicated group of developers and users. Ixilang brings our focus to the emergence of coding and musical coding languages.
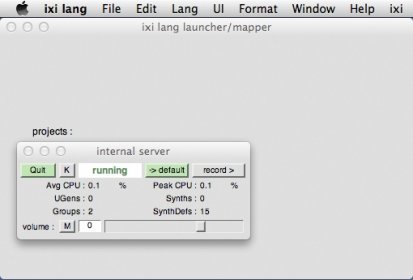
This is a realm that is still relatively new and relatively unexplored, while there are many people that are making music these days, very few are coding their sounds and still fewer are working on dedicated languages such as ixilang and other super collider extensions. There are dedicated followers this generative art form, and they are experiencing an interest wave of interest stemming from the recent developments of NFTs, but this is still relatively unexamined. What is my experience with ixilanauge? I like to code, I like to experiment with sound and software and hardware techniques, I enjoy the process of taking apart complex mechanisms and finding out how they work and then making them work in ways that was never intended or that makes them work differently that designed. I feel like if you share these interests than you will also find a tool like ixilanguage invaluable to your experimentation process. It will greatly inform to you whats possible and perhaps inspire you to code together some ixilang experiments or perhaps to work on supercollider and experiment with ixilang as an extensible language. The challenge I see with ixilang is the learning curve, like with any coding language, is a little bit steep. There is not much that one can do to make this less so. Definitely it helps to know how to code with several different languages, but the uniqueness of ixilang makes it something all its own.
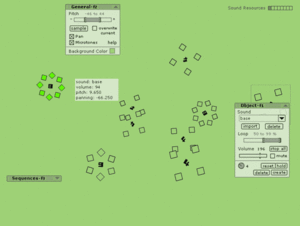
Ultimately ixilang is a tool like any other, it matters what you want to do, and how you can think of doing it. Ixilang as a module in that process could be invaluable. I have personally found that tools like ixilang are far from elements in my production, they are the core features of the way I make music these days. If you are interested in checking out ixilang I have included some great resources to get you started below:

Resources:
http://www.ixi-audio.net/
https://github.com/thormagnusson/ixilang
(1) https://en.wikipedia.org/wiki/Ixi_lang
#ixilang#ixilanguage#coding#algorave#algorithm sounds#generative music#generative art#cyberpunk#code as art#design#audio production#software#software dev#software developers#super collider
2 notes
·
View notes
Text
System Review: Super Collider Audio Synthesis Platform
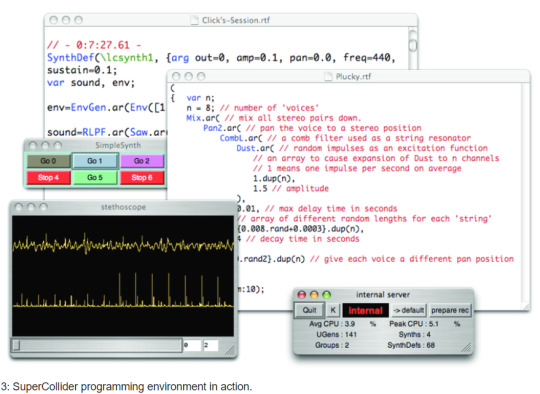
What is Super Collider? SuperCollider is a platform for audio synthesis and algorithmic composition, used by musicians, artists, and researchers working with sound. It is free and open source software available for Windows, macOS, and Linux.
Super Collider is incredible, it is basically a very sophisticated IDE for the creating of and launching of programs, scripts and algorithms to create sound compositions and experiments.
In layman's terms this is a program for creating wild and experimental sounds using code. By using code and writing programs, super collider allows the user to work with the raw hardware of the computer to create sounds and to craft experimental computation instances oriented around sound and audio hardware.
Super Collider has 3 main feature components that one can craft custom scripts for: the scsynth, the sclang and the scide. These components work together to script and launch sound instances which automate the computation hardware to create raw hardware sounds.
Why this software is so interesting is that it offers the user a way to use code and the computer as an instrument in a way that is completely driven by code instances. This software has extensibility and is portable into and out of, so it can be used as a layer, or component, or virtual instrument to be ported into and out of, and with additional code, or script interfaces, could be configured as part of a complex and unique audio production process.
If you are interested in using Super Collider you can find it at the repository below: https://supercollider.github.io/

#Super Collider#Code#codeart#audio production#ui design#coding#cyberpunk aesthetic#computer science#avantgarde art#generative art
3 notes
·
View notes
Text
youtube
https://soundcloud.com/deadrazy
[2019] deadrazy - ˢ ˣ ətiniz අ ̋ ̊ ̉ ̈ ̇ ̆ ̅ ̄ ̃ ̂ ́ ̀ئkhongthanDeadrazzy
#deadrazy#soundcloud#hardcore techno#dark#cyberpunk#idm#industrial#exprimental#hardcore#cybercore#glitchcore#deepcore#Youtube
1 note
·
View note
Text
Crypto Glossary
Timothy C. May and Eric HughesNovember 22, 1992

From: [email protected] (Timothy C. May)
Subject: Crypto Glossary
Date: Sun, 22 Nov 92 11:50:55 PST
Here's the glossary of crypto terms we passed out in printed form at the first Cypherpunks meeting in September 1992. Some compromises had to be made in going from the printed form to the ASCII of this transmission, so I hope you'll bear with me.
I'm sending it to the entire list because nearly everyone who hears about it says "Is it online?" and wants a copy. If you don't want it, discard it.
I'm not going to be maintaining the "Cypherpunks FAQ," so don't send me corrections or additions.
Enjoy
Tim May
Major Branches of Cryptology (as we see it)
(these sections will introduce the terms in context, though complete definitions will not be given)
Encryption
privacy of messages
using ciphers and codes to protect the secrecy of messages
DES is the most common symmetric cipher (same key for encryption and decryption)
RSA is the most common asymmetric cipher (different keys for encryption and decryption)
Signatures and Authentication
proving who you are
proving you signed a document (and not someone else)
Untraceable Mail
untraceable sending and receiving of mail and messages
focus: defeating eavesdroppers and traffic analysis
DC protocol (dining cryptographers)
Cryptographic Voting
focus: ballot box anonymity
credentials for voting
issues of double voting, security, robustness, efficiency
Digital Cash
focus: privacy in transactions, purchases
unlinkable credentials
blinded notes
"digital coins" may not be possible
Crypto Anarchy
using the above to evade government, to bypass tax collection, etc.
a technological solution to the problem of too much government
Glossary
agoric systems
open, free market systems in which voluntary transactions are central.
Alice and Bob
cryptographic protocols are often made clearer by considering parties A and B, or Alice and Bob, performing some protocol. Eve the eavesdropper, Paul the prover, and Vic the verifier are other common stand-in names.
ANDOS
all or nothing disclosure of secrets.
anonymous credential
a credential which asserts some right or privilege or fact without revealing the identity of the holder. This is unlike CA driver's licenses.
asymmetric cipher
same as public key cryptosystem.
authentication
the process of verifying an identity or credential, to ensure you are who you said you were.
biometric security
a type of authentication using fingerprints, retinal scans, palm prints, or other physical/biological signatures of an individual.
bit commitment
e.g., tossing a coin and then committing to the value without being able to change the outcome. The blob is a cryptographic primitive for this.
blinding, blinded signatures
A signature that the signer does not remember having made. A blind signature is always a cooperative protocol and the receiver of the signature provides the signer with the blinding information.
blob
the crypto equivalent of a locked box. A cryptographic primitive for bit commitment, with the properties that a blobs can represent a 0 or a 1, that others cannot tell be looking whether itUs a 0 or a 1, that the creator of the blob can "open" the blob to reveal the contents, and that no blob can be both a 1 and a 0. An example of this is a flipped coin covered by a hand.
channel
the path over which messages are transmitted. Channels may be secure or insecure, and may have eavesdroppers (or enemies, or disrupters, etc.) who alter messages, insert and delete messages, etc. Cryptography is the means by which communications over insecure channels are protected.
chosen plaintext attack
an attack where the cryptanalyst gets to choose the plaintext to be enciphered, e.g., when possession of an enciphering machine or algorithm is in the possession of the cryptanalyst.
cipher
a secret form of writing, using substitution or transposition of characters or symbols.
ciphertext
the plaintext after it has been encrypted.
code
a restricted cryptosystem where words or letters of a message are replaced by other words chosen from a codebook. Not part of modern cryptology, but still useful.
coin flipping
an important crypto primitive, or protocol, in which the equivalent of flipping a fair coin is possible. Implemented with blobs.
collusion
wherein several participants cooperate to deduce the identity of a sender or receiver, or to break a cipher. Most cryptosystems are sensitive to some forms of collusion. Much of the work on implementing DC Nets, for example, involves ensuring that colluders cannot isolate message senders and thereby trace origins and destinations of mail.
computationally secure
where a cipher cannot be broken with available computer resources, but in theory can be broken with enough computer resources. Contrast with unconditionally secure.
countermeasure
something you do to thwart an attacker.
credential
facts or assertions about some entity. For example, credit ratings, passports, reputations, tax status, insurance records, etc. Under the current system, these credentials are increasingly being cross-linked. Blind signatures may be used to create anonymous credentials.
credential clearinghouse
banks, credit agencies, insurance companies, police departments, etc., that correlate records and decide the status of records.
cryptanalysis
methods for attacking and breaking ciphers and related cryptographic systems. Ciphers may be broken, traffic may be analyzed, and passwords may be cracked. Computers are of course essential.
crypto anarchy
the economic and political system after the deployment of encryption, untraceable e-mail, digital pseudonyms, cryptographic voting, and digital cash. A pun on "crypto," meaning "hipen," and as when Gore Vidal called William F. Buckley a "crypto fascist."
cryptography
another name for cryptology.
cryptology
the science and study of writing, sending, receiving, and deciphering secret messages. Includes authentication, digital signatures, the hiding of messages (steganography), cryptanalysis, and several other fields.
cyberspace
the electronic domain, the Nets, and computer-generated spaces. Some say it is the "consensual reality" described in "Neuromancer." Others say it is the phone system. Others have work to do.
DC protocol, or DC-Net
the dining cryptographers protocol. DC-Nets use multiple participants communicating with the DC protocol.
DES
the Data Encryption Standard, proposed in 1977 by the National Bureau of Standards (now NIST), with assistance from the National Security Agency. Based on the "Lucifer" cipher developed by Horst Feistel at IBM, DES is a secret key cryptosystem that cycles 64-bit blocks of data through multiple permutations with a 56-bit key controlling the routing. "Diffusion" and "confusion" are combined to form a cipher that has not yet been cryptanalyzed (see "DES, Security of"). DES is in use for interbank transfers, as a cipher inside of several RSA-based systems, and is available for PCs.
DES, Security of
many have speculated that the NSA placed a trapdoor (or back door) in DES to allow it to read DES-encrypted messages. This has not been proved. It is known that the original Lucifer algorithm used a 128-bit key and that this key length was shortened to 64 bits (56 bits plus 8 parity bits), thus making exhaustive search much easier (so far as is known, brute-force search has not been done, though it should be feasible today). Shamir and Bihan have used a technique called "differential cryptanalysis" to reduce the exhaustive search needed for chosen plaintext attacks (but with no import for ordinary DES).
differential cryptanalysis the Shamir-Biham
technique for cryptanalyzing DES. With a chosen plaintext attack, they've reduced the number of DES keys that must be tried from about 2^56 to about 2^47 or less. Note, however, that rarely can an attacker mount a chosen plaintext attack on DES systems.
digital cash, digital money
Protocols for transferring value, monetary or otherwise, electronically. Digital cash usually refers to systems that are anonymous. Digital money systems can be used to implement any quantity that is conserved, such as points, mass, dollars, etc. There are many variations of digital money systems, ranging from VISA numbers to blinded signed digital coins. A topic too large for a single glossary entry.
digital pseudonym
basically, a "crypto identity." A way for individuals to set up accounts with various organizations without revealing more information than they wish. Users may have several digital pseudonyms, some used only once, some used over the course of many years. Ideally, the pseudonyms can be linked only at the will of the holder. In the simplest form, a public key can serve as a digital pseudonym and need not be linked to a physical identity.
digital signature
Analogous to a written signature on a document. A modification to a message that only the signer can make but that everyone can recognize. Can be used legally to contract at a distance.
digital timestamping
one function of a digital notary public, in which some message (a song, screenplay, lab notebook, contract, etc.) is stamped with a time that cannot (easily) be forged.
dining cryptographers protocol (aka DC protocol, DC nets)
the untraceable message sending system invented by David Chaum. Named after the "dining philosophers" problem in computer science, participants form circuits and pass messages in such a way that the origin cannot be deduced, barring collusion. At the simplest level, two participants share a key between them. One of them sends some actual message by bitwise exclusive-ORing the message with the key, while the other one just sends the key itself. The actual message from this pair of participants is obtained by XORing the two outputs. However, since nobody but the pair knows the original key, the actual message cannot be traced to either one of the participants.
discrete logarithm problem
given integers a, n, and x, find some integer m such that a^m mod n = x, if m exists. Modular exponentiation, the a^m mod n part, is straightforward (and special purpose chips are available), but the inverse problem is believed to be very hard, in general. Thus it is conjectured that modular exponentiation is a one-way function.
DSS, Digital Signature Standard
the latest NIST (National Institute of Standards and Technology, successor to NBS) standard for digital signatures. Based on the El Gamal cipher, some consider it weak and poor substitute for RSA-based signature schemes.
eavesdropping, or passive wiretapping
intercepting messages without detection. Radio waves may be intercepted, phone lines may be tapped, and computers may have RF emissions detected. Even fiber optic lines can be tapped.
factoring
Some large numbers are difficult to factor. It is conjectured that there are no feasible--i.e."easy," less than exponential in size of number-- factoring methods. It is also an open problem whether RSA may be broken more easily than by factoring the modulus (e.g., the public key might reveal information which simplifies the problem). Interestingly, though factoring is believed to be "hard", it is not known to be in the class of NP-hard problems. Professor Janek invented a factoring device, but he is believed to be fictional.
information-theoretic security "unbreakable"
security, in which no amount of cryptanalysis can break a cipher or system. One time pads are an example (providing the pads are not lost nor stolen nor used more than once, of course). Same as unconditionally secure.
key
a piece of information needed to encipher or decipher a message. Keys may be stolen, bought, lost, etc., just as with physical keys.
key exchange, or key distribution
the process of sharing a key with some other party, in the case of symmetric ciphers, or of distributing a public key in an asymmetric cipher. A major issue is that the keys be exchanged reliably and without compromise. Diffie and Hellman devised one such scheme, based on the discrete logarithm problem.
known-plaintext attack
a cryptanalysis of a cipher where plaintext-ciphertext pairs are known. This attack searches for an unknown key. Contrast with the chosen plaintext attack, where the cryptanalyst can also choose the plaintext to be enciphered.
mail, untraceable
a system for sending and receiving mail without traceability or observability. Receiving mail anonymously can be done with broadcast of the mail in encrypted form. Only the intended recipient (whose identity, or true name, may be unknown to the sender) may able to decipher the message. Sending mail anonymously apparently requires mixes or use of the dining cryptographers (DC) protocol.
minimum disclosure proofs
another name for zero knowledge proofs, favored by Chaum.
mixes
David Chaum's term for a box which performs the function of mixing, or decorrelating, incoming and outgoing electronic mail messages. The box also strips off the outer envelope (i.e., decrypts with its private key) and remails the message to the apress on the inner envelope. Tamper-resistant modules may be used to prevent cheating and forced disclosure of the mapping between incoming and outgoing mail. A sequence of many remailings effectively makes tracing sending and receiving impossible. Contrast this with the software version, the DC protocol.
modular exponentiation
raising an integer to the power of another integer, modulo some integer. For integers a, n, and m, a^m mod n. For example, 5^3 mod 100 = 25. Modular exponentiation can be done fairly quickly with a sequence of bit shifts and aps, and special purpose chips have been designed. See also discrete logarithm.
National Security Agency (NSA)
the largest intelligence agency, responsible for making and breaking ciphers, for intercepting communications, and for ensuring the security of U.S. computers. Headquartered in Fort Meade, Maryland, with many listening posts around the world. The NSA funds cryptographic research and advises other agencies about cryptographic matters. The NSA once obviously had the world's leading cryptologists, but this may no longer be the case.
negative credential
a credential that you possess that you don't want any one else to know, for example, a bankruptcy filing. A formal version of a negative reputation.
NP-complete
a large class of difficult problems. "NP" stands for nondeterministic polynomial time, a class of problems thought in general not to have feasible algorithms for their solution. A problem is "complete" if any other NP problem may be reduced to that problem. Many important combinatorial and algebraic problems are NP-complete: the traveling salesman problem, the Hamiltonian cycle problem, the word problem, and on and on.
oblivious transfer
a cryptographic primitive that involves the probabilistic transmission of bits. The sender does not know if the bits were received.
one-time pad
a string of randomly-selected bits or symbols which is combined with a plaintext message to produce the ciphertext. This combination may be shifting letters some amount, bitwise exclusive-ORed, etc.). The recipient, who also has a copy of the one time pad, can easily recover the plaintext. Provided the pad is only used once and then destroyed, and is not available to an eavesdropper, the system is perfectly secure, i.e., it is information-theoretically secure. Key distribution (the pad) is obviously a practical concern, but consider CD-ROM's.
one-way function
a function which is easy to compute in one direction but hard to find any inverse for, e.g. modular exponentiation, where the inverse problem is known as the discrete logarithm problem. Compare the special case of trap door one-way functions. An example of a one-way operation is multiplication: it is easy to multiply two prime numbers of 100 digits to produce a 200-digit number, but hard to factor that 200-digit number.
P ?=? NP
Certainly the most important unsolved problem in complexity theory. If P = NP, then cryptography as we know it today does not exist. If P = NP, all NP problems are "easy."
paping
sending extra messages to confuse eavesdroppers and to defeat traffic analysis. Also aping random bits to a message to be enciphered.
plaintext
also called cleartext, the text that is to be enciphered.
Pretty Good Privacy (PGP)
Phillip Zimmerman's implementation of RSA, recently upgraded to version 2.0, with more robust components and several new features. RSA Data Security has threatened PZ so he no longer works on it. Version 2.0 was written by a consortium of non-U.S. hackers.
prime numbers
integers with no factors other than themselves and 1. The number of primes is unbounded. About 1% of the 100 decimal digit numbers are prime. Since there are about 10^70 particles in the universe, there are about 10^23 100 digit primes for each and every particle in the universe!
probabilistic encryption
a scheme by Goldwasser, Micali, and Blum that allows multiple ciphertexts for the same plaintext, i.e., any given plaintext may have many ciphertexts if the ciphering is repeated. This protects against certain types of known ciphertext attacks on RSA.
proofs of identity
proving who you are, either your true name, or your digital identity. Generally, possession of the right key is sufficient proof (guard your key!). Some work has been done on "is-a-person" credentialling agencies, using the so-called Fiat-Shamir protocol...think of this as a way to issue unforgeable digital passports. Physical proof of identity may be done with biometric security methods. Zero knowledge proofs of identity reveal nothing beyond the fact that the identity is as claimed. This has obvious uses for computer access, passwords, etc.
protocol
a formal procedure for solving some problem. Modern cryptology is mostly about the study of protocols for many problems, such as coin-flipping, bit commitment (blobs), zero knowledge proofs, dining cryptographers, and so on.
public key
the key distributed publicly to potential message-senders. It may be published in a phonebook-like directory or otherwise sent. A major concern is the validity of this public key to guard against spoofing or impersonation.
public key cryptosystem
the modern breakthrough in cryptology, designed by Diffie and Hellman, with contributions from several others. Uses trap door one-way functions so that encryption may be done by anyone with access to the "public key" but decryption may be done only by the holder of the "private key." Encompasses public key encryption, digital signatures, digital cash, and many other protocols and applications.
public key encryption
the use of modern cryptologic methods to provided message security and authentication. The RSA algorithm is the most widely used form of public key encryption, although other systems exist. A public key may be freely published, e.g., in phonebook-like directories, while the corresponding private key is closely guarded.
public key patents
M.I.T. and Stanford, due to the work of Rivest, Shamir, Adleman, Diffie, Hellman, and Merkle, formed Public Key Partners to license the various public key, digital signature, and RSA patents. These patents, granted in the early 1980s, expire in the between 1998 and 2002. PKP has licensed RSA Data Security Inc., of Redwood City, CA, which handles the sales, etc.
quantum cryptography
a system based on quantum-mechanical principles. Eavesdroppers alter the quantum state of the system and so are detected. Developed by Brassard and Bennett, only small laboratory demonstrations have been made.
reputations
the trail of positive and negative associations and judgments that some entity accrues. Credit ratings, academic credentials, and trustworthiness are all examples. A digital pseudonym will accrue these reputation credentials based on actions, opinions of others, etc. In crypto anarchy, reputations and agoric systems will be of paramount importance. There are many fascinating issues of how reputation-based systems work, how credentials can be bought and sold, and so forth.
RSA
the main public key encryption algorithm, developed by Ron Rivest, Adi Shamir, and Kenneth Adleman. It exploits the difficulty of factoring large numbers to create a private key and public key. First invented in 1978, it remains the core of modern public key systems. It is usually much slower than DES, but special-purpose modular exponentiation chips will likely speed it up. A popular scheme for speed is to use RSA to transmit session keys and then a high-speed cipher like DES for the actual message text.
Description
Let p and q be large primes, typically with more than 100 digits. Let n = pq and find some e such that e is relatively prime to (p - 1)(q - 1). The set of numbers p, q, and e is the private key for RSA. The set of numbers n and e forms the public key (recall that knowing n is not sufficient to easily find p and q...the factoring problem). A message M is encrypted by computing M^e mod n. The owner of the private key can decrypt the encrypted message by exploiting number theory results, as follows. An integer d is computed such that ed =1 (mod (p - 1)(q - 1)). Euler proved a theorem that M^(ed) = M mod n and so M^(ed) mod n = M. This means that in some sense the integers e and d are "inverses" of each other. [If this is unclear, please see one of the many texts and articles on public key encryption.]
secret key cryptosystem
A system which uses the same key to encrypt and decrypt traffic at each end of a communication link. Also called a symmetric or one-key system. Contrast with public key cryptosystem.
smart cards
a computer chip embeped in credit card. They can hold cash, credentials, cryptographic keys, etc. Usually these are built with some degree of tamper-resistance. Smart cards may perform part of a crypto transaction, or all of it. Performing part of it may mean checking the computations of a more powerful computer, e.g., one in an ATM.
spoofing, or masquerading
posing as another user. Used for stealing passwords, modifying files, and stealing cash. Digital signatures and other authentication methods are useful to prevent this. Public keys must be validated and protected to ensure that others don't substitute their own public keys which users may then unwittingly use.
steganography
a part of cryptology dealing with hiding messages and obscuring who is sending and receiving messages. Message traffic is often paped to reduce the signals that would otherwise come from a supen beginning of messages.
symmetric cipher
same as private key cryptosystem.
tamper-responding modules, tamper-resistant modules (TRMs)
sealed boxes or modules which are hard to open, requiring extensive probing and usually leaving ample evidence that the tampering has occurred. Various protective techniques are used, such as special metal or oxide layers on chips, armored coatings, embeped optical fibers, and other measures to thwart analysis. Popularly called "tamper-proof boxes." Uses include: smart cards, nuclear weapon initiators, cryptographic key holders, ATMs, etc.
tampering, or active wiretapping
interfering with messages and possibly modifying them. This may compromise data security, help to break ciphers, etc. See also spoofing.
token
some representation, such as ID cards, subway tokens, money, etc., that indicates possession of some property or value.
traffic analysis
determining who is sending or receiving messages by analyzing packets, frequency of packets, etc. A part of steganography. Usually handled with traffic paping.
transmission rules
the protocols for determining who can send messages in a DC protocol, and when. These rules are needed to prevent collision and deliberate jamming of the channels.
trap messages
dummy messages in DC Nets which are used to catch jammers and disrupters. The messages contain no private information and are published in a blob beforehand so that the trap message can later be opened to reveal the disrupter. (There are many strategies to explore here.)
trap-door
In cryptography, a piece of secret information that allows the holder of a private key to invert a normally hard to invert function.
trap-door one way functions
functions which are easy to compute in both the forward and reverse direction but for which the disclosure of an algorithm to compute the function in the forward direction does not provide information on how to compute the function in the reverse direction. More simply put, trap-door one way functions are one way for all but the holder of the secret information. The RSA algorithm is the best-known example of such a function.
unconditional security
same as information-theoretic security, that is, unbreakable except by loss or theft of the key.
unconditionally secure
where no amount of intercepted ciphertext is enough to allow the cipher to be broken, as with the use of a one-time pad cipher. Contrast with computationally secure.
voting, cryptographic
Various schemes have been devised for anonymous, untraceable voting. Voting schemes should have several properties: privacy of the vote, security of the vote (no multiple votes), robustness against disruption by jammers or disrupters, verifiability (voter has confidence in the results), and efficiency.
zero knowledge proofs
proofs in which no knowledge of the actual proof is conveyed. Peggy the Prover demonstrates to Sid the Skeptic that she is indeed in possession of some piece of knowledge without actually revealing any of that knowledge. This is useful for access to computers, because eavesdroppers or dishonest sysops cannot steal the knowledge given. Also called minimum disclosure proofs. Useful for proving possession of some property, or credential, such as age or voting status, without revealing personal information.
Timothy C. May | Crypto Anarchy: encryption, digital money, [email protected] | anonymous networks, digital pseudonyms, zero 408-688-5409 | knowledge, reputations, information markets, W.A.S.T.E.: Aptos, CA | black markets, collapse of governments. Higher Power: 2^756839 | PGP Public Key: by arrangement.
#Timothy C May#Crypto Anarchism#crypto#bitcoin#cypherpunk#anarchism#cryptoanarchism#cryptocurrencies#cyberpunk#punk#cryptopunk#design
3 notes
·
View notes
Text

Giusy aka @marigoldff founder of IOR50 Studio, Berlin Germany
https://www.instagram.com/accounts/login/?next=/marigoldff/
36 notes
·
View notes
Text
NFTGAN: Non-Fungible Token Art Generation Using Generative Adversarial Networks
By SAKIB SHAHRIAR and KADHIM HAYAWI
Digital arts have gained an unprecedented level of popularity with the emergence of non-fungible tokens (NFTs). NFTs are cryptographic assets that are stored on blockchain networks and represent a digital certificate of ownership that cannot be forged. NFTs can be incorporated into a smart contract which allows the owner to benefit from a future sale percentage. While digital art producers can benefit immensely with NFTs, their production is time consuming. Therefore, this paper explores the possibility of using generative adversarial networks (GANs) for automatic generation of digital arts. GANs are deep learning architectures that are widely and effectively used for synthesis of audio, images, and video contents. However, their application to NFT arts have been limited. In this paper, a GAN-based architecture is implemented and evaluated for novel NFT-style digital arts generation. Results from the qualitative case study indicate that the generated artworks are comparable to the real samples in terms of being interesting and inspiring and they were judged to be more innovative than real samples.
Read the Paper at the link below:
#GAN#generativeart#generative adversarial network#artificial intelligence#data science#computer science#engineering#Art#production#design#NFTs#Generative Art#cyberpunk
1 note
·
View note
Text
Instrument Review: Amazing Maze Generative Synth

In my quest to find VSTs I have come across some really wacky and strange and also interesting programs. People have been tackling the idea of creating generative synthesizers for a long time, ever since the dawn of the AMIGA and its bit tracker sequencers we have had VST plug ins capable of creating all sorts of effects. My main interest is in these Generative VSTs, something with a mind of its own. I love finding these little interactive generative instruments because they take what I do to a whole new level. I love playing with sound and adding these components to a track is a way to unleash utterly alien soundscapes into your production. Amazing Maze is one of these such instruments. Amazing Maze is a infinite Realtime composition that creates an astounding sonic cosmos by manipulating instrumental sound particles in time and space. It takes advantage of composition algorithms that have been developed by Karlheinz Essl since the 1985 years. The generation process can be conducted by an automatism or by user interaction. There is not a whole lot of information about it, but I do see that its inventor intended for this to be a sort of Instrument on its own. He debuted his creation as a complete instrument, letting it run on his computer un aided, letting the software itself select que and trigger samples at seemingly random. There is of course some method to this madness, I am at a loss to figure out what exactly is driving this instrument. It seems to be either picking up sounds from the environment and queueing samples to the patterns of input it picks up. It seems to go with the music. The sounds themselves that already pre loaded into the synth range from found sounds, yells, talking, to birds, and all sorts of sound effects. The over all effect is really something. You can let the generator generate its own lovely revolution of noise, by itself for as long as you want. but the coolest part is you can explore the possibilities of this software. You can upload your own sounds into its library of samples. With a little hacking and coding you can use this as a generative engine to mess around with on its own. That is why I love software like this. It is simple enough to mess with and really take into many different directions as a component piece to a production. It is also complex enough to stand on its own in terms of exploration or development.
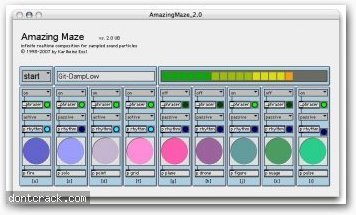
Find Amazing Maze at the resources I have included Below and enjoy your exploration.
http://www.dontcrack.com/freeware/downloads.php/id/4369/software/Amazing-Maze/
#Amazing Maze#Generative Synths#Synthesizers#VSTs#Virtual Studio Technology#plugins#Sound Production#sound engineering#audio engineering#software#development#hacking
0 notes
Text
System Review: SoulseekQT OSX p2p Filesharing

I’m going to kick off this System Review compilation with one of my favorite hidden Gems on the internet. Soul Seek. Soulseek is a peer-to-peer (P2P) file-sharing network and application. The term Soulseek might refer to one of the two networks, or one of the three official user client interfaces. Soulseek is used mostly to exchange music, although users are able to share a variety of files. Soulseek was created by Nir Arbel, an Israeli programmer from Safed. I don’t exactly recall when soulseek came into my life, but I do recall that it was around when I got serious about listening to music. I remember that I was a money-less high school freshman getting serious about making music and especially collecting and listening to it. I had no money and was tired of getting bunk files from limewire, dumb spyware or mislabled tracks. I was fed up with constantly having to reinstall my operating system after downloading a bunch of tunes. A handful of mismatched songs would taunt me on my Ipod playlists. I thought perhaps the new itunes would be a great choice. So I started buying albums from there, but was quickly frustrated with the experience of moving files around and actually feeling like I own the music that I actually paid for. However the experience of having complete albums with album art and high quality perhaps even lossless file quality stuck with me and became my ultimate goal. I yearned for a library of my favorite artists and musicians, organized and meticulously labeled with metadata tags, in high quality loss less file formats, such as .flac files, and complete with Liner notes and Album art, this idea gratified my OCD, and became my holy grail quest. I searched far and wide looking for the best p2p program to use to find such high quality gems, a smart wikipedia search on p2p networks revealed that there exist several such programs for exchanging files. I tried a large majority of them, and I remember even at that young age I was very thorough. I had compiled a list of all the artists from all the genres I was interested in. Artists I was never able to find on limewire, the rare gems that I sought long and hard for. It was around this time and the need that soulseek came into my life and answered my prayers.
Soul seek is where my soul seeks. Its where I have lived for close to a decade and where I have met some of my longest running online friends, where I would go to after school, after work, and chat with my friends. Soul seek is a hidden gem. If you are reading this I am entrusting you with these vestiges of value that I have found. I expect you to respect that, and expect you to keep this a hidden Gem. Don’t tell anyone about soulseek who isn’t an audiophile through and through. I will further elaborate. Soul seek has the file you are looking for, if any place has that b side rarity, in lossless flac, organized and meticulously labeled with metadata tags, complete with liner notes as a txt file and the cover art included, if it is anywhere, it is on soul seek. The individuals that house and share their collections via Soul Seek are some of the most incredible collectors of audio files in the world. I have seen some collections on soul seek ranging in the scores of terabytes, meticulously organized, impeccably arranged. DJ’s, musicians, producers and true worshippers of sound silently inhabit soul seek. I count myself among them, and make my collection of VST’s, albums and oddities available there. Music is just one aspect of soulseek. Soul seek is a truly living, and yet truly secluded p2p network. The other aspect of soulseek is the chat client. I came for the music, and stayed for friends and connections I have made through soul seek. They are people I speak with regularly. We inhabit rooms and dwell in them for months or even years at a time. Its the kind of out of the way den that would attract your score of 4chan users. Enter the wrong room in soul seek chat and you will quickly find the kind of cess that makes 4chan 4chan. Of course like anything and anywhere else you take the good with the bad. I personally stay away from these rooms and prefer to connect in the lesser known communities that use soul seek as their headquarters. Legitimate computer hackers also tend to use soulseek. So I would also be careful how I enter soulseek, and what kind of attention I attract to myself, or what kind of vibes I am bringing to it.

To conclude, soul seek is an essential tool if you are a musician or producer, for exploring music, collecting and exchanging music resources. It is mainly used just to exchange music files, but I find its use as a platform limitless. I don’t steal music; when I find an artist whose music I particularly like. I buy their albums. Go to their shows, and become an avid consumer of their goods, products and services. Of course you are free to steal as much music as you want from hard working talented creators who’s only mission in life is to enrich and benefit our collective lives, if that's your thing, this post is really not meant for you.
If this post brings you into my fold, mention it, and If you see me on there and want to exchange, I am an avid collector of Virtual Studio Technology, virtual synths, and software instruments if you want to trade, or if you want to browse my collection of albums for download.
Check out soulseek’s client download below:
http://www.slsknet.org/news/

4 notes
·
View notes
Text
A Declaration of the Independence of Cyberspace
February 8, 1996
John Perry Barlow
Governments of the Industrial World, you weary giants of flesh and steel, I come from Cyberspace, the new home of Mind. On behalf of the future, I ask you of the past to leave us alone. You are not welcome among us. You have no sovereignty where we gather.
We have no elected government, nor are we likely to have one, so I address you with no greater authority than that with which liberty itself always speaks. I declare the global social space we are building to be naturally independent of the tyrannies you seek to impose on us. You have no moral right to rule us nor do you possess any methods of enforcement we have true reason to fear.
Governments derive their just powers from the consent of the governed. You have neither solicited nor received ours. We did not invite you. You do not know us, nor do you know our world. Cyberspace does not lie within your borders. Do not think that you can build it, as though it were a public construction project. You cannot. It is an act of nature and it grows itself through our collective actions.
You have not engaged in our great and gathering conversation, nor did you create the wealth of our marketplaces. You do not know our culture, our ethics, or the unwritten codes that already provide our society more order than could be obtained by any of your impositions.
You claim there are problems among us that you need to solve. You use this claim as an excuse to invade our precincts. Many of these problems don’t exist. Where there are real conflicts, where there are wrongs, we will identify them and address them by our means. We are forming our own Social Contract. This governance will arise according to the conditions of our world, not yours. Our world is different.
Cyberspace consists of transactions, relationships, and thought itself, arrayed like a standing wave in the web of our communications. Ours is a world that is both everywhere and nowhere, but it is not where bodies live.
We are creating a world that all may enter without privilege or prejudice accorded by race, economic power, military force, or station of birth.
We are creating a world where anyone, anywhere may express his or her beliefs, no matter how singular, without fear of being coerced into silence or conformity.
Your legal concepts of property, expression, identity, movement, and context do not apply to us. They are all based on matter, and there is no matter here.
Our identities have no bodies, so, unlike you, we cannot obtain order by physical coercion. We believe that from ethics, enlightened self-interest, and the commonweal, our governance will emerge. Our identities may be distributed across many of your jurisdictions. The only law that all our constituent cultures would generally recognize is the Golden Rule. We hope we will be able to build our particular solutions on that basis. But we cannot accept the solutions you are attempting to impose.
In the United States, you have today created a law, the Telecommunications Reform Act, which repudiates your own Constitution and insults the dreams of Jefferson, Washington, Mill, Madison, DeToqueville, and Brandeis. These dreams must now be born anew in us.
You are terrified of your own children, since they are natives in a world where you will always be immigrants. Because you fear them, you entrust your bureaucracies with the parental responsibilities you are too cowardly to confront yourselves. In our world, all the sentiments and expressions of humanity, from the debasing to the angelic, are parts of a seamless whole, the global conversation of bits. We cannot separate the air that chokes from the air upon which wings beat.
In China, Germany, France, Russia, Singapore, Italy and the United States, you are trying to ward off the virus of liberty by erecting guard posts at the frontiers of Cyberspace. These may keep out the contagion for a small time, but they will not work in a world that will soon be blanketed in bit-bearing media.
Your increasingly obsolete information industries would perpetuate themselves by proposing laws, in America and elsewhere, that claim to own speech itself throughout the world. These laws would declare ideas to be another industrial product, no more noble than pig iron. In our world, whatever the human mind may create can be reproduced and distributed infinitely at no cost. The global conveyance of thought no longer requires your factories to accomplish.
These increasingly hostile and colonial measures place us in the same position as those previous lovers of freedom and self-determination who had to reject the authorities of distant, uninformed powers. We must declare our virtual selves immune to your sovereignty, even as we continue to consent to your rule over our bodies. We will spread ourselves across the Planet so that no one can arrest our thoughts.
We will create a civilization of the Mind in Cyberspace. May it be more humane and fair than the world your governments have made before.
Davos, Switzerland
February 8, 1996
#Declaration of independence#Cyberspace#Anarchism#cryptoanarchism#cyberpunk#cypherpunk#nakamoto institute#John Perry Barlow
5 notes
·
View notes