Text
Learning Digital Forensic by ICSS

What Is Digital Forensics?
Digital forensic science is a branch of forensic science that focuses on the recovery and investigation of material found in digital devices related to cybercrime which is done to digital world. it is also a process in which digital forensics expert find way to how the digital crime is done. The term digital forensics was first used as a synonym for computer forensics. Since then, it has expanded to cover the investigation of any devices that can store digital data. Although the first computer crime was reported in 1978, followed by the Florida computers act
Digital forensics is the process of identifying, preserving, analyzing, and documenting digital evidence. This is done in order to present evidence in a court of law when required
Steps of Digital Forensics
1. Identification-First, find the evidence, noting where it is stored.
2. Preservation-Next, isolate, secure, and preserve the data. This includes preventing people from possibly tampering with the evidence.
3. Analysis-Next, reconstruct fragments of data and draw conclusions based on the evidence found.
4. Documentation-Following that, create a record of all the data to recreate the crime scene.
5. Presentation-Lastly, summarize and draw a conclusion.
Types of Digital Forensics
There are mainly 3 types of digital forensics are:
1-Disk Forensics:
It deals with extracting data from storage media by searching active, modified, or deleted files.
2-Network Forensics:
It is a sub-branch of digital forensics. It is related to monitoring and analysis of computer network traffic to collect important information and legal evidence.
3-Wireless Forensics:
It is a division of network forensics. The main aim of wireless forensics is to offers the tools need to collect and analyze the data from wireless network traffic.
Challenges faced by Digital Forensics
T1-he increase of PC’s and extensive use of internet access
2-Easy availability of hacking tools
3-Lack of physical evidence makes prosecution difficult.
4-The large amount of storage space into Terabytes that makes this investigation job difficult.
5-Any technological changes require an upgrade or changes to solutions.
Digital Forensics is one of best program which student as well as professional should learn. There are as many important of learning Digital Forensics as we discussed in above . One of the best training institute which offer Digital Forensics training in India with cost efficient. Indian cyber security solutions has organize a 4 day boot training in Digital Forensics course. ICSS will start the session form 4th of August 2021 to 7th of August 2021 with industry expert of Digital Forensics.
Digital Forensic and Electronic Evidence Boot Camp Training by Indian Cyber Security Solutions . It will be a 4 days training with the course fee at INR 493/-. Just try the and enjoy training to learn and build a career in Digital Forensic and Electronic Evidence.
for more details please click on the below link :
https://indiancybersecuritysolutions.com/digital-forensic-electronic-evidence/
6 notes
·
View notes
Text
Learn Ethical Hacking Online-ICSS

what do mean by ethical hacking?
Ethical hacking involves an authorized attempt to gain unauthorized access to a computer system, application, or data. Carrying out an ethical hack involves duplicating strategies and actions of malicious attackers. This practice helps to identify security vulnerabilities which can then be resolved before a malicious attacker has the opportunity to exploit them.
Also known as white hats ethical hackers are security experts that perform these assessments. The proactive work they do helps to improve an organization security posture. With prior approval from the organization or owner of the IT asset, the mission of Hacking course is opposite from malicious hacking.
Since there are many Ethical Hacking course center in India, finding the right one would be a challenging task. However, ones best way would be to do a research. Research on which organization:
Has the best Faculty present.
The placement it offers are the completion of the course.
Scholarships it can offer to students for the course.
Reviews of the previous students on how the training were conducted.
Among the many Ethical Hacking course in India, Indian Cyber Security Solutions would be the right for you to join. We have the right set of practical lab classes set up for students to learn as well as industry grade trainers who would conduct the classes and impart the right set of Cyber Security Knowledge to students. Our efforts have been acknowledged by various reputed administrative institutes, such as Top Ten Training Institutes in India in 2020” by Silicon India; as well as Ten Most Trusted Training & Cyber Security Certifications Provider, 2021 by The Knowledge Review.
As an Education Institute, we are also cyber security service provider to corporate organization. Services like VAPT, Web Penetration Testing, Network Penetration Testing, Mobile Application Penetration Testing to corporate organization like IRCTC, HDFC, Cambridge Technologies, and many more. With this, Indian Cyber Security Solutions have been acknowledged as the 20 Tech Brands of 2021. by Business Connect India.
for more details contact to the given link below:
https://indiancybersecuritysolutions.com/ethical-hacking-course-online-icss/
0 notes
Text
Ethical Hacking course near you-ICSS

what do mean by ethical hacking?
Ethical hacking involves an authorized attempt to gain unauthorized access to a computer system, application, or data. Carrying out an ethical hack involves duplicating strategies and actions of malicious attackers. This practice helps to identify security vulnerabilities which can then be resolved before a malicious attacker has the opportunity to exploit them.
Also known as white hats ethical hackers are security experts that perform these assessments. The proactive work they do helps to improve an organization security posture. With prior approval from the organization or owner of the IT asset, the mission of Hacking course is opposite from malicious hacking.
Since there are many Ethical Hacking course center in India, finding the right one would be a challenging task. However, ones best way would be to do a research. Research on which organization:
Has the best Faculty present.
The placement it offers are the completion of the course.
Scholarships it can offer to students for the course.
Reviews of the previous students on how the training were conducted.
Among the many Ethical Hacking course in India, Indian Cyber Security Solutions would be the right for you to join. We have the right set of practical lab classes set up for students to learn as well as industry grade trainers who would conduct the classes and impart the right set of Cyber Security Knowledge to students. Our efforts have been acknowledged by various reputed administrative institutes, such as Top Ten Training Institutes in India in 2020” by Silicon India; as well as Ten Most Trusted Training & Cyber Security Certifications Provider, 2021 by The Knowledge Review.
As an Education Institute, we are also cyber security service provider to corporate organization. Services like VAPT, Web Penetration Testing, Network Penetration Testing, Mobile Application Penetration Testing to corporate organization like IRCTC, HDFC, Cambridge Technologies, and many more. With this, Indian Cyber Security Solutions have been acknowledged as the 20 Tech Brands of 2021. by Business Connect India.
for more details contact to the given link below:
https://indiancybersecuritysolutions.com/ethical-hacking-course-online-icss/
0 notes
Text
VAPT Services in India-ICSS
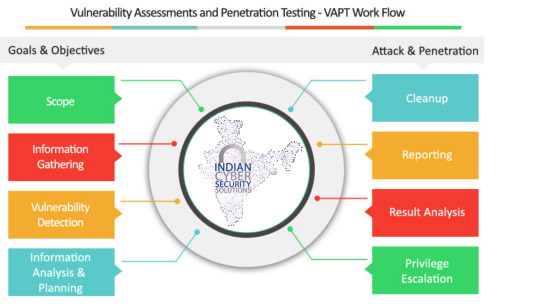
What do mean by VAPT ?
VAPT stand for Vulnerability Assessment and Penetration Testing .Vulnerability Assessment and Penetration Testing (VAPT) are two types of vulnerability testing. The tests have different strengths and are often combined to achieve a more complete vulnerability analysis. In short, Penetration Testing and Vulnerability Assessments perform two different tasks, usually with different results, within the same area of focus.
Vulnerability assessment tools discover which vulnerabilities are present, but they do not differentiate between flaws that can be exploited to cause damage and those that cannot. Vulnerability scanners alert companies to the preexisting flaws in their code and where they are located. Best VAPT Penetration tests attempt to exploit the vulnerabilities in a system to determine whether unauthorized access or other malicious activity is possible and identify which flaws pose a threat to the application. Penetration tests find exploitable flaws and measure the severity of each. A penetration test is meant to show how damaging a flaw could be in a real attack rather than find every flaw in a system. Together, penetration testing and vulnerability assessment tools provide a detailed picture of the flaws that exist in an application and the risks associated with those flaws
Features and Benefits of VAPT
VAPT company in India provides enterprises with a application evaluation than any single test alone. Using the Vulnerability Assessment and Penetration Testing (VAPT) approach gives an organization a more detailed view of the threats facing its applications, enabling the business to better protect its systems and data from malicious attacks. Vulnerabilities can be found in applications from third-party vendors and internally made software, but most of these flaws are easily fixed once found. Using VAPT we can able to know the Vulnerability and flaws of application after that we can able to fix that flaw . VAPT Vendor in India enables IT security teams to focus on mitigating critical vulnerabilities while the VAPT provider continues to discover and classify vulnerability
Vulnerability Testing
Following is the step by step Vulnerability Assessment Technique
Step 1) Setup:
Begin Documentation
Secure Permission
Update Tools
Configure Tools
Step 2) Test Execution:
Run the Tools
Run the captured data packet (A packet is the unit of data that is routed between an origin and the destination. When any file, for example, e-mail message, HTML file, Uniform Resource Locator(URL) request, etc. is sent from one place to another on the internet, the TCP layer of TCP/IP divides the file into a number of “chunks” for efficient routing, and each of these chunks will be uniquely numbered and will include the Internet address of the destination. These chunks are called packet. When they have all arrived, they will be reassembled into the original file by the TCP layer at the receiving end. , while running the assessment tools
Step 3) Vulnerability Analysis:
Defining and classifying network or System resources.
Assigning priority to the resource( Ex: — High, Medium, Low)
Identifying potential threats to each resource.
Developing a strategy to deal with the most prioritize problems first.
Defining and implementing ways to minimize the consequences if an attack occurs.
Step 4) Reporting
Step 5) Remediation:
The process of fixing the vulnerabilities.
For every vulnerability
Vulnerability Testing and Method:
Active Testing
Inactive Testing, a tester introduces new test data and analyzes the results.
During the testing process, the testers create a mental model of the process, and it will grow further during the interaction with the software under test.
While doing the test, the tester will actively involve in the process of finding out the new test cases and new ideas. That’s why it is called Active Testing.
Passive Testing
Passive testing, monitoring the result of running software under test without introducing new test cases or data
Network Testing
Network Testing is the process of measuring and recording the current state of network operation over a period of time.
Testing is mainly done for predicting the network operating under load or to find out the problems created by new services.
We need to Test the following Network Characteristics:-
Utilization levels
Number of Users
Application Utilization
Distributed Testing
Distributed Tests are applied for testing distributed applications, which means, the applications that are working with multiple clients simultaneously. Basically, testing a distributed application means testing its client and server parts separately, but by using a distributed testing method, we can test them all together.
The test parts will interact with each other during the Test Run. This makes them synchronized in an appropriate manner. Synchronization is one of the most crucial points in distributed testing.
These all are the facts about the VAPT. There are various vendors which offer the VAPT Services. Among Top vendor of VAPT in India, one of them is Indian cyber security solutions. ICSS is one of the Top VAPT company in India which provides the best services as required by the client. Vulnerability Assessment and Penetration Testing (VAPT)is one best way to find the Vulnerability and flaws of the application, it helps the to keep the application secure and vulnerability and flaw free. Past 10 years there has been a sharp increase in cyber-crime cases due to which an increase in VAPT vendors in India was a very common sight among many ranging from bottom to the top VAPT companies in India where among them some have been labeled as the best VAPT Pentesting vendors in India. Indian Cyber Security Solutions is the best VAPT Testing Company. We not only use VAPT but implement it organically into the client’s system to make sure that the process is thorough, effective and presents the client with an opportunity to revamp its cyber security details for the betterment of the company.
Avinashicss
0 notes
Text
Learn cloud Computing from the best Cyber Security Training Institute-ICSS

What do mean by Cloud Computing ?
Cloud computing is a general term for anything that involves delivering hosted services in the internet. These services are divided into three main categories:
infrastructure as a service
platform as a service
software as a service
A cloud can be public or private. A public cloud sells services to anyone on the internet. A private cloud is a proprietary network or a data center that supplies hosted services to a limited number of people, with certain access and permissions settings. Private or public, the goal of cloud computing is to provide easy, scalable access to computing resources and IT services.
Cloud infrastructure involves the hardware and software components required for proper implementation of a cloud computing model.The name cloud computing was inspired by the cloud symbol that’s often used to represent the internet in flowcharts and diagrams.
How does Cloud Computing work?
Cloud computing works by allowing client devices to access data over the internet, from remote servers, databases and computers.
An internet network connection links the front end (includes the accessing client device, browser, network and cloud software applications) with the back end, which consists of databases, servers and computers). The back end functions as a repository, storing data that is accessed by the front end.
Communications between the front and back ends are managed by a central server. The central server relies on protocols to facilitate the exchange of data. The central server uses both software and middleware to manage connectivity between different client devices and cloud servers. Typically, there will be a dedicated server for each individual application. In this cloud computing work.
Some example of cloud computing :
Google Docs, Microsoft Office 365
2. Email, Calendar, Skype, WhatsApp
3. Zoom
4. AWS Lambda and many more
Some of the main benefits of cloud computing are:
Cost savings: Using cloud infrastructure can reduce costs, as organizations don’t have to spend massive amounts of money buying and maintaining equipment. This reduces their capital expenditure costs as they don’t have to invest in hardware, facilities, utilities or building large data centers to accommodate their growing businesses.
Mobility: Storing information in the cloud means that users can access it from anywhere with any device with just an internet connection. That means users don’t have to carry around USB drives, an external hard drive or multiple CDs to access their data. Users can access corporate data via smartphones and other mobile devices, enabling remote employees to stay up to date with co-workers and customers.
Disaster recovery: All organizations worry about data loss. Storing data in the cloud guarantees that users can always access their data even if their devices, e.g., laptops or smartphones, are inoperable. With cloud-based services, organizations can quickly recover their data in the event of emergencies, such as natural disasters or power outages.
There are as many Institute for cloud computing training and cyber security training . one of best cyber security training institute in India is Indian cyber security solutions. If we will look up in the market there are as many institute which offer as many courses but ICSS will provide cyber security training in India. As Course offer by the ICSS it provide the Internship facility after completion of the course which is one of the plus point of doing the cyber security training form ICSS
Diploma in Advanced Cloud & Network Security from Indian Cyber Security Solutions is the best part. A recent study showed that 90% of breaches are caused by employee carelessness. If a program is implemented to teach them about common scams, such as email attachments that contain malware or phishing emails that steal personal information, they are much less likely to accidentally click links or open files. As cyber-crime continues to wreak havoc, regulations continue to be implemented to protect data. Having a strong security policy coupled with security awareness training means less worrying. Cybersecurity professionals work in every size company and industry to protect organizations from data breaches and attacks. After completion of Diploma in Advanced Cloud & Network Security from Indian Cyber Security Solutions, you can build your career in the cybersecurity field. As a cybersecurity expert, you will have a huge range of career options across a wide variety of industries.
For more details click on the below link :
https://indiancybersecuritysolutions.com/diploma-in-advanced-cloud-network-security-training/
0 notes
Text
Learning kali Linux form Basic to Advance-ICSS

what do mean by kali Linux ?
Kali Linux is a Linux distribution that is specialized for cybersecurity. It is an open-source product that involves a lot of customization for penetration testing, which helps companies to understand their vulnerabilities.
Kali Linux is based on the Debian Linux distribution, and runs on a wide spectrum of devices. Its open-source build means that it is free and legal to use in a wide range of enterprise scenarios.
While many experts recommend against Kali Linux for beginners, those who are interested in cybersecurity often benefit from using this specific Linux distribution. Kali Linux offers single root user design as a way to handle privileges, and users can disable network services by default. That is helpful for the penetration testing and data forensics that can be used to determine a company’s weak points in a risk mitigation project.
Feature of kali Linux
1 A Live System
Alongside the main installer ISO images, Kali Linux offers a separate live ISO image to download. This allows you to use Kali Linux as a bootable live system. In other words, you can use Kali Linux without installing it, just by booting the ISO image (usually after having copied the image onto a USB key).
2 Forensics Mode
In general, when doing forensic work on a system, you want to avoid any activity that would alter the data on the analyzed system in any way. Unfortunately, modern desktop environments tend to interfere with this objective by trying to auto-mount any disk(s) they detect. To avoid this behavior, Kali Linux has a forensics mode that can be enabled from the boot menu: it will disable all such features.
3 A Custom Linux Kernel
Kali Linux always provides a customized recent Linux kernel, based on the version in Debian Unstable. This ensures solid hardware support, especially for a wide range of wireless devices. The kernel is patched for wireless injection support since many wireless security assessment tools rely on this feature.
4 Usable on a Wide Range of ARM Devices
Kali Linux provides binary packages for the armel, armhf, and arm64 ARM architectures. Thanks to the easily installable images provided by Offensive Security, Kali Linux can be deployed on many interesting devices, from smartphones and tablets to Wi-Fi routers and computers of various shapes and sizes.
5 A Trustable Operating System
Users of a security distribution rightfully want to know that it can be trusted and that it has been developed in plain sight, allowing anyone to inspect the source code. Kali Linux is developed by a small team of knowledgeable developers working transparently and following the best security practices: they upload signed source packages, which are then built on dedicated build daemons. The packages are then checksummed and distributed as part of a signed repository.
6 Completely Customizable
Kali Linux is built by penetration testers for penetration testers, but we understand that not everyone will agree with our design decisions or choice of tools to include by default. With this in mind, we always ensure that Kali Linux is easy to customize based on your own needs and preferences. To this end, we publish the live-build configuration used to build the official Kali images so you can customize it to your liking
ICSS has planned a total Kali Linux course in India that is being instructed by the specialists of Hackers. The master at our organization has wide involvement with security research, instrument advancement, entrance testing and so on We additionally give preparing on the most proficient method to do Penetration testing utilizing Kali Linux and this course is essentially spinning around the Kali Linux dissemination. There are not many organizations in India that give total involved practice on Kali Linux yet we are pleased to declare that after the finish of our course, you would have the option to get commonsense openness. We additionally give you the ventures that must be put together by the understudies to acquire the live openness on Ethical hacking training using Kali Linux in India.
For more details please contact given link:
https://indiancybersecuritysolutions.com/kali-linux-training-in-india/
0 notes
Text
Learning Kali Linux is the first step to Become Ethical Hacker-ICSS

What is Kali Linux?
Kali Linux is funded and maintained by Offensive Security, an information training company. It is a Debian-based Linux distribution built with the aim of advanced penetration testing and security auditing. Debian standard is an entire command-line system without an x11 or GUI environment. It is just a primary server. If you don’t use it with a landline connection, you can only use it for learning the command line. It is equipped with a tone of tools installed with it that makes an ethical hacker can go on a war with these tools in his arsenal.
Uses of Kali Linux
Kali Linux is packed with essential tools for information security tasks, penetration testing, computer forensics, reverse engineering, and many more. As Kali Linux is just an operating software, it is not illegal by itself. But when someone uses it for hacking, it is considered illegal if someone uses it to learn, teach, or understand the intricacies as it is licensed for download.
Here are a few reasons why Kali Linux is an exciting choice of operating software :
It is free to use .
Although most applications and tools are primarily written in English, Kali Linux provides multi-lingual support. That opens opportunities for people to use these resources in their local language and use it for their customizable purpose.
The developers at Kali Linux have been very liberal while developing this and have left opportunities for customization for fellow developers to come on board and modify it as per their uses.
It is available on an open-source platform. The entire development tree, along with codes, is known for viewing and modifying on Git.
Kali Linux comes equipped with more than 600 different devices.
Requirements for the installation for kali Linux.
Set up Kali as a basic Secure Shell (SSH) server with no desktop
Using as little as 128 MB of RAM (512 MB recommended) and 2 GB of disk space
If you opt to install the default Xfce desktop and the kali-linux-default metapackage then we should have atleast 2048 MB of RAM and 20 GB of disk space as minimum requriment.
we needs to have a CPU supported by at least one of the amd64, i386, or arm64 architectures.
Some tools in kali Linux:
NMap
NMap or Network Mapper is one of the most popular tools on Kali Linux for information gathering. In other words, to get insights about the host, its IP address, OS detection, and similar network security details.
2.WPScan
WordPress is one of the best open source CMS and this would be the best free WordPress security auditing tool. It’s free but not open source.
3. Aircrack-ng
Aircrack-ng is a collection of tools to assess WiFi network security. It isn’t just limited to monitor and get insights but it also includes the ability to compromise a network. If you forgot the password of your own WiFi network we can try using this to regain access. It also includes a variety of wireless attacks with which you can target monitor a WiFi network to enhance its security
4. Hydra
If you are looking for an interesting tool to crack login/password pairs, Hydra will be one of the best Kali Linux tools that comes pre-installed.
5. Wireshark
Wireshark is the most popular network analyzer that comes baked in with Kali Linux. It can be categorized as one of the best Kali Linux tools for network sniffing as well
Above are some common tools for the kali Linux which help to use kali Linux. There are more tools which are used in kali Linux (skipfish, Maltego, Nessus, Brup suite scanner and many more)
As now we see that how kali Linux is first step for Learning cyber security in Bangalore. we have had a look at Kali Linux training in Bangalore , in various learning and ease of accessibility opportunities this platform provides us with without any charge as it is an open-source, free platform. Upon having a detailed look at the Kali Linux features, we can conclude that it offers a plethora of customizability options and reasons why those interested in learning ethical hacking must do Kali Linux training in Bangalore.
Kali Linux course in Bangalore is the innovation that is further developed to perform Penetration Testing and Security Auditing Linux circulation for Kali Linux training in Bangalore. This Training will be extremely useful for the members, who are exceptionally keen on learning the infiltration testing and IT security methods that go under digital protection. The members will acquire insight on proficient Exploit Writing, Advance Sniffing, Web Penetration Testing, Document Management, and Reporting, Social Engineering Toolkit, and much more about the strategies of Penetration Testing with Kali Linux course in Bangalore.
For more Details click on Below Link:
https://indiancybersecuritysolutions.com/kali-linux-training-in-bangalore/
0 notes
Text
Best Kali Linux Training in Hyderabad-ICSS

what do mean by kali Linux ?
Kali Linux is a Linux distribution that is specialized for cybersecurity. It is an open-source product that involves a lot of customization for penetration testing, which helps companies to understand their vulnerabilities.
Kali Linux is based on the Debian Linux distribution, and runs on a wide spectrum of devices. Its open-source build means that it is free and legal to use in a wide range of enterprise scenarios.
While many experts recommend against Kali Linux for beginners, those who are interested in cybersecurity often benefit from using this specific Linux distribution. Kali Linux offers single root user design as a way to handle privileges, and users can disable network services by default. That is helpful for the penetration testing and data forensics that can be used to determine a company’s weak points in a risk mitigation project.
Feature of kali Linux
1 A Live System
Alongside the main installer ISO images, Kali Linux offers a separate live ISO image to download. This allows you to use Kali Linux as a bootable live system. In other words, you can use Kali Linux without installing it, just by booting the ISO image (usually after having copied the image onto a USB key).
2 Forensics Mode
In general, when doing forensic work on a system, you want to avoid any activity that would alter the data on the analyzed system in any way. Unfortunately, modern desktop environments tend to interfere with this objective by trying to auto-mount any disk(s) they detect. To avoid this behavior, Kali Linux has a forensics mode that can be enabled from the boot menu: it will disable all such features.
3 A Custom Linux Kernel
Kali Linux always provides a customized recent Linux kernel, based on the version in Debian Unstable. This ensures solid hardware support, especially for a wide range of wireless devices. The kernel is patched for wireless injection support since many wireless security assessment tools rely on this feature.
4 Usable on a Wide Range of ARM Devices
Kali Linux institute in Hyderabad provides binary packages for the armel, armhf, and arm64 ARM architectures. Thanks to the easily installable images provided by Offensive Security, Kali Linux can be deployed on many interesting devices, from smartphones and tablets to Wi-Fi routers and computers of various shapes and sizes.
5 A Trustable Operating System
Users of a security distribution rightfully want to know that it can be trusted and that it has been developed in plain sight, allowing anyone to inspect the source code. Kali Linux is developed by a small team of knowledgeable developers working transparently and following the best security practices: they upload signed source packages, which are then built on dedicated build daemons. The packages are then check summed and distributed as part of a signed repository.
6 Completely Customizable
Kali Linux training in Hyderabad built by penetration testers for penetration testers, but we understand that not everyone will agree with our design decisions or choice of tools to include by default. With this in mind, we always ensure that Kali Linux is easy to customize based on your own needs and preferences. To this end, we publish the live-build configuration used to build the official Kali images so you can customize it to your liking
ICSS has planned a total Kali Linux course in Hyderabad that is being instructed by the specialists of Hackers. The master at our organization has wide involvement with security research, instrument advancement, entrance testing and so on We additionally give preparing on the most proficient method to do Penetration testing utilizing Kali Linux and this course is essentially spinning around the Kali Linux dissemination. There are not many organizations in India that give total involved practice on Kali Linux yet we are pleased to declare that after the finish of our course, you would have the option to get commonsense openness. We additionally give you the ventures that must be put together by the understudies to acquire the live openness on Ethical hacking training using Kali Linux in Hyderabad.
For more details please contact given link:
https://indiancybersecuritysolutions.com/kali-linux-training-in-hyderabad/
0 notes
Text
Become a Professional in Developing Office Network Infrastructure -ICSS

what do you mean by Network security?
Network security is any activity designed to protect the usability and integrity of your network and data.
It includes both hardware and software technologies
It targets a variety of threats
It stops them from entering or spreading on your network
Effective network security manages access to the network
How Network Security work?
Network security combines multiple layers of defenses at the edge and in the network. In network security it doesn’t allow the unauthorized access to one system or any other network. Each network security layer implements policies and controls. Authorized users gain access to network resources, but malicious actors are blocked from carrying out exploits and threats.
Types of Network security.
1 Fire wall
2 Email Security
3 Antivirus software
4 Network Segmentation
5 Access Control
6 VPN and many more
Diploma in Network Security training in kolkata has designed by our experienced professional Network penetration testers. They had been working in this domain for the last 15 years. This is the best certificate which will definitely help you to secure a good job in the space of cybersecurity. Indian Cyber Security Solutions provide the most comprehensive network security training framework. After that, you will be able to secure a job as a penetration tester.
This Full training focuses on the core issues of cloud & network security. Starting from the basic and then core security problem faced by industry experts while working as a cyber security professional. Cyber Security process of protection of the access to files and directories in a computer network. Against hacking, misuse and unauthorized changes to the system. With employment of information security analysts projected to grow by 20 percent from 2016 to 2024. You will learn by Diploma in Network Security Course in Kolkata is the process about used to protection of the access to files. It is directories in a computer network against hacking, misuse and unauthorized changes to the system. Join us for the course and after that you can build your career in this domain. ICSS’s Diploma in Network Security Training Institute in Kolkata is in-demand as they build awareness of best practices against various attacks.
For more details you can visit to :
https://indiancybersecuritysolutions.com/diploma-in-network-security/
0 notes
Text
Career guide on cyber security-ICSS

What is Cyber Security?
Cyber security is the practice of defending computers, servers, mobile devices, electronic systems, networks, and data from malicious attacks. It’s also known as information technology security or electronic information security. The term applies in a variety of contexts, from business to mobile computing, and can be divided into a few common categories.
· Network security is the practice of securing a computer network from intruders, whether targeted attackers or opportunistic malware.
· Application security focuses on keeping software and devices free of threats. A compromised application could provide access to the data its designed to protect. Successful security begins in the design stage, well before a program or device is deployed.
· Information security protects the integrity and privacy of data, both in storage and in transit.
· Operational security includes the processes and decisions for handling and protecting data assets. The permissions users have when accessing a network and the procedures that determine how and where data may be stored or shared all fall under this umbrella.
· Disaster recovery and business continuity define how an organization responds to a cyber-security incident or any other event that causes the loss of operations or data. Disaster recovery policies dictate how the organization restores its operations and information to return to the same operating capacity as before the event. Business continuity is the plan the organization falls back on while trying to operate without certain resources.
· End-user education addresses the most unpredictable cyber-security factor: people. Anyone can accidentally introduce a virus to an otherwise secure system by failing to follow good security practices. Teaching users to delete suspicious email attachments, not plug in unidentified USB drives, and various other important lessons is vital for the security of any organization.
What kind of Scope with Cyber Security does have in India?
India has turned into a hotbed for Cyber Security experts. According to a recent study by Indeed.com, the scope of Cyber Security has turned more competitive in India. There are more job post clicks in India as compared to the US and UK. As per the industry stats, most hiring is happening for the below roles.
· Network Security Engineer
· Cyber Security Analyst
· Security Architect
· Cyber Security Manager
· Chief Information Security Officer
Over the last a couple of years, the average salary of cyber security has been performing 9% better than any other IT professionals. The freshers are able to get good packages starting from 7 lacs and the experienced resources are in more demand drawing salaries in the range of 20–24 lacs.
0 notes
Text
Best Kali Linux Training in India -ICSS

what do mean by kali Linux ?
Kali Linux is a Linux distribution that is specialized for cybersecurity. It is an open-source product that involves a lot of customization for penetration testing, which helps companies to understand their vulnerabilities.
Kali Linux is based on the Debian Linux distribution, and runs on a wide spectrum of devices. Its open-source build means that it is free and legal to use in a wide range of enterprise scenarios.
While many experts recommend against Kali Linux for beginners, those who are interested in cybersecurity often benefit from using this specific Linux distribution. Kali Linux offers single root user design as a way to handle privileges, and users can disable network services by default. That is helpful for the penetration testing and data forensics that can be used to determine a company’s weak points in a risk mitigation project.
Feature of kali Linux
1 A Live System
Alongside the main installer ISO images, Kali Linux offers a separate live ISO image to download. This allows you to use Kali Linux as a bootable live system. In other words, you can use Kali Linux without installing it, just by booting the ISO image (usually after having copied the image onto a USB key).
2 Forensics Mode
In general, when doing forensic work on a system, you want to avoid any activity that would alter the data on the analyzed system in any way. Unfortunately, modern desktop environments tend to interfere with this objective by trying to auto-mount any disk(s) they detect. To avoid this behavior, Kali Linux has a forensics mode that can be enabled from the boot menu: it will disable all such features.
3 A Custom Linux Kernel
Kali Linux always provides a customized recent Linux kernel, based on the version in Debian Unstable. This ensures solid hardware support, especially for a wide range of wireless devices. The kernel is patched for wireless injection support since many wireless security assessment tools rely on this feature.
4 Usable on a Wide Range of ARM Devices
Kali Linux provides binary packages for the armel, armhf, and arm64 ARM architectures. Thanks to the easily installable images provided by Offensive Security, Kali Linux can be deployed on many interesting devices, from smartphones and tablets to Wi-Fi routers and computers of various shapes and sizes.
5 A Trustable Operating System
Users of a security distribution rightfully want to know that it can be trusted and that it has been developed in plain sight, allowing anyone to inspect the source code. Kali Linux is developed by a small team of knowledgeable developers working transparently and following the best security practices: they upload signed source packages, which are then built on dedicated build daemons. The packages are then checksummed and distributed as part of a signed repository.
6 Completely Customizable
Kali Linux is built by penetration testers for penetration testers, but we understand that not everyone will agree with our design decisions or choice of tools to include by default. With this in mind, we always ensure that Kali Linux is easy to customize based on your own needs and preferences. To this end, we publish the live-build configuration used to build the official Kali images so you can customize it to your liking
ICSS has planned a total Kali Linux course in India that is being instructed by the specialists of Hackers. The master at our organization has wide involvement with security research, instrument advancement, entrance testing and so on We additionally give preparing on the most proficient method to do Penetration testing utilizing Kali Linux and this course is essentially spinning around the Kali Linux dissemination. There are not many organizations in India that give total involved practice on Kali Linux yet we are pleased to declare that after the finish of our course, you would have the option to get commonsense openness. We additionally give you the ventures that must be put together by the understudies to acquire the live openness on Ethical hacking training using Kali Linux in India.
For more details please contact given link:
https://indiancybersecuritysolutions.com/kali-linux-training-in-india/
0 notes
Text
Importance of doing CCNA before learning Ethical Hacking-ICSS

What is CCNA Training?
CCNA (Cisco Certified Network Associate) is an information technology (IT) certification from Cisco Systems. CCNA certification is an associate-level Cisco Career certification.
The Cisco exams have changed several times in response to the changing IT trends. In 2020, Cisco announced an update to its certification program that “Consolidated and updated associate level training and certification.” Cisco has consolidated the previous different types of Cisco-Certified Network Associate with a general CCNA certification.
The content of the exams is proprietary. Cisco and its learning partners offer a variety of different training methods, including books published by Cisco Press, and online and classroom courses available under the title “Interconnecting Cisco Network Devices”.
Step to become a CCNA certified:
1 Get a degree in computer science or information technology to serve as your foundation
Apply for a job in the computer networking field to gain practical experience
2.Take the ICND1 exam to receive your CCENT certificate
3.Enroll in a study school to prepare for the exam
4.Study for the exam with practice tests
5.Register online to take the CCNA exam
6.Complete and pass the test
7. Then you become a certified CCNA
Why CCNA Training is Important?
Cisco certification is a procedure that prepares benefits for employers and employees in the IT business.
Nothing can alternate involvement, yet certifications are additionally significant so as to keep an aspirant up to date with the most recent technological improvements occurring in the IT field.
Numerous candidates have seen positive impacts in their career charts subsequent to gaining the CCNA training.
When you get CCNA certified, you get that ideal qualification and an acknowledgment that you can incorporate into your resume while applying for an empty job position in the Cisco networking area.
The most important Benefits of CCNA Certification is that, through this course, your recognition will be increased.
93% of employers are of the thought that Cisco certified employees increase the value of their business, and are more learned than their non-Cisco certified job candidates around the globe.
This certification procedure encourages them to accomplish some genuine advantages and significant talents.
This certification is substantial for a long time, which means you get the opportunity to make the most out of your CCNA certification for quite a long time to come.
The Advantages of CCNA certification will make you survive in any kind of companies.
There are various occasions wherein IT experts have felt the need of having a CCNA certificate — even in the wake of having at least ten numbers of long periods of involvement in the IT field.
The heaviness of employees in an IT group is doled out dependent on the certifications.
0 notes
Text
Best Cyber Security Tips for Remote Workers-ICSS

What is Cyber Security?
Cyber security is the practice of defending computers, servers, mobile devices, electronic systems, networks, and data from malicious attacks. It’s also known as information technology security or electronic information security. The term applies in a variety of contexts, from business to mobile computing, and can be divided into a few common categories.
· Network security is the practice of securing a computer network from intruders, whether targeted attackers or opportunistic malware.
· Application security focuses on keeping software and devices free of threats. A compromised application could provide access to the data its designed to protect. Successful security begins in the design stage, well before a program or device is deployed.
· Information security protects the integrity and privacy of data, both in storage and in transit.
· Operational security includes the processes and decisions for handling and protecting data assets. The permissions users have when accessing a network and the procedures that determine how and where data may be stored or shared all fall under this umbrella.
· Disaster recovery and business continuity define how an organization responds to a cyber-security incident or any other event that causes the loss of operations or data. Disaster recovery policies dictate how the organization restores its operations and information to return to the same operating capacity as before the event. Business continuity is the plan the organization falls back on while trying to operate without certain resources.
· End-user education addresses the most unpredictable cyber-security factor: people. Anyone can accidentally introduce a virus to an otherwise secure system by failing to follow good security practices. Teaching users to delete suspicious email attachments, not plug in unidentified USB drives, and various other important lessons is vital for the security of any organization.
Best Cyber Security Tips for Remote Workers
1. Be on the lookout for phishing emails
Cyber criminals are taking advantage of the COVID-19 situation and are crafting emails to target remote workers to steal their personal information or gain access to business email accounts. Understand the signs of a phishing email (bad grammar, unknown sender email address, etc.) Don’t click on any links in emails without verifying the link address first. Don’t provide any of your personal information or login credentials in response to any email requesting it.
2. Use encrypted communication
There may be times where you need to send sensitive information to your coworkers. If your company doesn’t provide you with a secure method for sending sensitive information, use an application that utilizes end-to-end encryption, such as Telegram or WhatsApp.
3. Be cautious when using remote desktop tools
Many employers will allow employees to connect to their work network using a Remote Desktop Protocol (RDP). While RDP can be secure, be aware that there are some security problems with common RDP tools for Windows and Linux. If you are given the option to choose your RDP service, select from one of these recommended RDP tools, many of which offer a free trial.
4. Use a VPN when connecting to your work network
VPNs provide a secure tunnel for the information to pass between your device on your home network to your work network. It is especially important to use a VPN when accessing any of your organizations file servers to maintain the integrity and confidentiality of your data.5. Ensure your home network isn’t an easy target
5. Ensure your home network isn’t an easy target
Verify your anti-virus software is running and is updated to include the newest malware signatures. Secure your home internet with a firewall to prevent any unwanted connections. Install any patches and make sure your systems are up to date. Strengthen your passwords and always use multi-factor authentication (MFA) when available.
6. Make sure your WiFi network is secure
Taking the extra time to change the default SSID and password on your Wifi network is a small step that goes a long way to being securing from hackers. Regularly update your router to address security vulnerabilities in the firmware.
7. Consider moving your work devices to a separate subnetwork
It’s likely other members of your family are also being forced to remain at home, and they could be spending their time browsing the internet. During this time, they may be more susceptible to accidentally downloading a virus that can infect the entire network you are now trying to work on. Take inventory of the devices you use for work, and create a separate virtual network so that you are not on the same network as the rest of your family. Many routers offer the option to create these virtual networks.
0 notes
Text
Cyber Security Is a Great Career Option for Military Veterans-ICSS

What is actually a Cyber Security Is ?
Cyber security is the practice of protecting computers, servers, mobile devices, electronic systems, networks, and data from malicious attacks or attack form unauthorized user . It is well known as information technology security or electronic information security. In other word we can say that cyber security is just wall protector from unknow user and they can helps to reduce the any type cyber attack and it protect the whole digital world. Cyber Security can be divided in some common category.
Network security is the practice of securing a computer network from intruders, whether targeted attackers or opportunistic malware .
Application security focuses on keeping software and devices free of threats. A compromised application could provide access to the data its designed to protect. Successful security begins in the design stage, well before a program or device is deployed.
Information security protects the integrity and privacy of data, both in storage and in transit.
Operational security includes the processes and decisions for handling and protecting data assets. The permissions users have when accessing a network and the procedures that determine how and where data may be stored or shared all fall under this umbrella.
Disaster recovery and business continuity define how an organization responds to a cyber-security incident or any other event that causes the loss of operations or data. Disaster recovery policies dictate how the organization restores its operations and information to return to the same operating capacity as before the event. Business continuity is the plan the organization falls back on while trying to operate without certain resources.
End-user education addresses the most unpredictable cyber-security factor: people. Anyone can accidentally introduce a virus to an otherwise secure system by failing to follow good security practices. Teaching users to delete suspicious email attachments, not plug in unidentified USB drives, and various other important lessons is vital for the security of any organization.
5 Reasons why Military Veterans Are a Great Fit for Cybersecurity Carrier
Veterans of all military branches and occupational specialties have advanced training in both hard skills and soft skills.
However, this is also good news for the majority of veterans on a personal level. more than 50% of people transitioning to civilian life want to do something totally different than they did while active duty, according to LinkedIn’s recent Veteran Opportunity Report.
In some report we found that the three industries hiring veterans the most are defense and space, utilities, and government administration. This is interesting because these are also three of the sectors most in need of cybersecurity expertise today. Banking and finance, healthcare, and retail are other industries that are having to make rapid changes to meet the now-constant threat of cyberattack. Due to this rising crisis, it’s anticipated more than 3.5 million jobs in the field will be unfilled as of 2021
Cyber security bootcamp is a great way to use a portion of GI bill benefits to make a big career shift into cybersecurity jobs and translate that effort into a high salary. Plus, there are five key ways your military background will be seen as a benefit by potential employers across industries.
1 You are used to military style intensity
Cyber security is a high stakes field with a critical mission protecting civilians and businesses from harm through cybercrime. Whether there is a any type of attack i.e. data breach, ransomware, or another form of systems attack, cyber security professionals are on the front lines to protect and minimize attack. Some of the most harmful types of cyberattack have also become the most common:
Phishing Attack: a hacker poses as a trusted organization to steal information. This is the common way of attack ,through this attacker get the data or credentials of of victims
Malware or Ransomware: a malicious program infiltrates a device to achieve criminal goals
Online Credential Breach: leaked passwords put users at risk of compromise .After leaking the password or user id all the data of victims ,all the data can be access by attacker.
2 You are dedicated toward job
At its core, cyber security is a profession of service. This industry is dedicated to protecting those at risk and serving the good of the people a common value of your military service. As first step of military is keep the hide data form anyone even form the family .This shows the huge dedication toward job. They will always show positive attitude toward job and they will work on even any condition ,they will give their first priority to job .
3 You are adaptable
Veterans are used to adapting to new orders, circumstances of living, and colleagues on a regular basis. Cybersecurity is also a field that requires an adaptable work style. University of Maryland reports that hackers attack every 39 seconds, and no matter where you end up working, your organization could become the next target. That means the long term project you planned to work on that day might take a back seat, while you are also expected to pick up right where you left off once the immediate threat is resolved. every day we will get the new challenges in work ,cyber security is just keep himself upto date. It’s certainly exciting and if you like to adapt to new challenges every day, it just might be the field for you.
4 you are comfortable to work in team.
The science of teams in the military has been studied, published on, and even inspired a lot of the best-practices that civilian organizations use today. Unlike professionals from a different type of background, you know the success of the mission is more important than any one person’s ego. Though it may not always be easy to work on a team, in an industry like cyber security, it’s essential.
This even applies to the prevention of cybercrime to begin with. When one individual is blamed for the data breach, like the Equifax data breach in 2017, it’s often to cover up that the organization as a whole made mistakes. And, it makes it hard to move forward as a team to do better in the future. Your military mindset and focus on outcomes, not excuses, will help other civilian employees do better as you lead by example.
5 You are trained to fighting an adversary
Fighting an adversary means being able to think like they do. In combat, this means anticipating the strategy and next steps of an enemy organization. In cybersecurity jobs, it means doing the same against tens of thousands such hostile organizations. Symantec reported that in 2019, its sensors blocked 142 million threats per day and that’s just one cybersecurity company.
In this environment, the knowledge of strategy and mindset of perseverance that come with being a veteran put you ahead of the curve. Cybersecurity training helps you achieve the practical skills to support the mental best practices you have already developed.
0 notes
Text
Learning DevOps from Industry Professionals is the right way to improve your Cyber Security Carrier-ICSS

What is DevOps?
DevOps (a portmanteau of “development” and “operations”) is the combination of practices and tools designed to increase an organization’s ability to deliver applications and services faster than traditional software development processes. This speed enables organizations to better serve their customers and compete more effectively in the market.
In simple terms, DevOps is about removing the barriers between traditionally siloed teams, development and operations. Under a DevOps model, development and operations teams work together across the entire software application life cycle, from development and test through deployment to operations
Benefits of DevOps
Speed. DevOps practices let you move at the velocity you need to innovate faster, adapt to changing markets better, and become more efficient at driving business results.
Rapid delivery. When you increase the pace of releases, you can improve your product faster and build competitive advantage.
Reliability. DevOps practices like continuous integration and continuous delivery can ensure the quality of application updates and infrastructure changes so you can reliably deliver at a more rapid pace while maintaining an optimum experience for end users.
Improved collaboration. Under a DevOps model, developers and operations teams collaborate closely, share responsibilities, and combine their workflows. This reduces inefficiencies and saves time.
Security. You can adopt a DevOps model without sacrificing security by using automated, integrated security testing tools.
DevOps Training in Dhanbad By ICSS DevOps Training in Bangalore by Indian Cyber Security Solutions will prepare you for a career in DevOps. This is the fast-growing field. This DevOps Course in Bangalore well-suited for those who wish to enhance their marketability for these highly prized roles. DevOps jobs are highly paid and in great demand, so start on your path today. DevOps training in Dhanbad is designed to help you become a DevOps practitioner. 1500+ students got placed in various MNC from Indian Cyber Security Solutions as they are the best DevOps Training Institute in Bangalore. And apply the latest in DevOps methodology to automate your software development. The DevOps training in Bangalore focuses heavily on the use of Docker containers.
This course will help you learn DevOps and in various aspects of software development, operations, continuous integration, etc. This is a comprehensive training for DevOps in the city of Bangalore that is designed by our industry experts DevOps is in undertaking software development phrase used to mean a kind of spry relationship between Development and IT Operations. It is a culture which promotes collaboration between Development and Operations Team to deploy code to production faster in an automated & repeatable way. DevOps Training in Dhanbad will help you to grab better job opportunities
For more details you can also visit :
https://indiancybersecuritysolutions.com/devops-training-in-dhanbad/
0 notes
Text
10 Reasons Why Cyber Certifications Are Worth It-ICSS

Why cybersecurity certifications worth the effort?
Cybersecurity certifications are worth because the effort if you use them as a extra supplement to other qualifications on your resume. Only having certifications on a resume is an indication to employers that your knowledge is not based on experience but certification show your knowledge as well experience.
In other words, certifications are worth that effort, but they are not the only thing that will require your time and effort while you are building your cybersecurity career. Through doing the cyber Security certification only student as well professional can enhance their knowledge and any can begin there carrier in cyber security world. through cyber Security we can also get the chance to work with many international company .
Benefits of getting a certification on Cyber Security .1:Unlimited Career Growth Options
Cyber Security is expanding its growth in various industries. As the world is moving in the online platform then their is maximum chances of attack by some unknow body (cyber attack). so need the professional to overcome with this issue. This makes sure that is a perfect platform for growth in terms of career as well as learning opportunities. These days, cyber attacks are getting smarter and faster. This arises the need for Cyber Security professionals to outsmart the hackers at a much more faster pace. Businesses and governments are dependent on them for analyzing & minimizing risk along with combating cyber attacks and preventing all types of vulnerabilities. Tackling the cyber attacks are an outcome of continuous study, comprehensive research & optimal execution. This proves that when you learn Cyber Security, you will be continuously knowing new things and gaining rich experience which is an add-on to your skill set.
2: Certifications show a level of accomplishment and perseverance.
Everyone knows that earning a certification takes work, so having certificate help the student to convey a level of commitment to your career and knowledge base. This is especially important as you start your career and through that only student show on carrier focus to the particular company . Having a certification shows you’re serious about your career field.
3:Opportunities to work with High Profile Agencies
One of the best things about being a Cyber Security professional is that your chances of working with some of the best companies in the world increases. There is no restriction on the number of the organization that you can work with. The demand for Cyber Security professionals has considerably increased across the globe. . It has to be noted that the potential does not end here, experts in Cyber Security might also get the chance to work with some of the top-notch secret government & intelligence agencies like NSA, CBI and many more agency along with Central Intelligence Agency, Department of Defense & various banks.
4:Requirements are Basic for cyber Security certification
if anyone , think that building a career in Cyber Security is difficult then it is possibly wrong. To become a Cyber Security professional, you absolutely don’t have to go to some college for a 4-year degree course or get a year of experience. You can step up in the Cyber Security domain as a professional with some knowledge of computer science and by doing the cyber certification course. The Cyber Security certification will help you to gain Cyber Security knowledge and as well as the strategy of building their carrier in Cyber Security word . After getting a certification in Cyber Security as it helps to increases your resume value and get the license to rule over the cyber security world . The eligibility criterion for getting a certification in Cyber Security is just basic only the knowledge IT field and how does this done work in this cyber world .If you are a fresher or even a college student, you can go forward with this career without really worrying about anything just keep in mind that you can do the work with whole efficiency .
5: Certifications can be used to negotiate a raise or promotion.
As certification is one of the most important factor in hike in salary as well as position in the company , as it show that employ have skilled their knowledge by getting the certification. Through certification only we can show able to show our knowledge and after showing our knowledge we can get increment in salary as well as post in the company. if we are switching to other company our first impression is our certificate which show our developed and skilled knowledge .
6:A Chance to Work with Secret Agencies
It’s certain that Cybersecurity Professionals have a clear shot at working with prestigious fortune 500 companies like Dell, Accenture, InfoTech and many more, but the potential doesn’t end there. Experts who prove to be worthy of their skills might earn the chance to work with top-secret government agencies and intelligence agencies eg MI6, Mossad, NSA. So if you learn cybersecurity, After doing the certification in the cyber security domain we getting the chance to work with the secret agency as well as the defense sector .we can also get the chance to work with the govt project in security field .
7: Doing Good Work While Making Good Money
How many jobs offer the kind of high pay and exciting challenge as cyber security? As i can say no other job as like doing the work in cyber security world . As a professional trained in this field, your job will be safe if you are update your self with the new cyber security knowledge . As by U.S. News and World Report ranks Information Security Analyst job number 7 out of the 10 best technology jobs of 2017. You should also consider cyber security training if you’re looking for a safe job with good pay from the very start. Entry-level professionals who have earned a certification can earn close to maximum in their first job. The median annual salary is $90,000 with higher salaries paid in tech hubs like San Francisco. Chief Information Security Officers (CISO) can earn upwards of $1 million this is just as on record data their is huge demand for this in cyber security world as freshers as well as professional.
8.A certification can keep your employer on their toes.
Several times in career I’ve followed the playbook of earning a certification on my own time and with my own money, all without letting my employer in on my intentions. After I earned the certification, I would forward them the email confirmation or let them know verbally In these scenarios, you can start to see the wheels turn as they wonder when you completed the certification, why you’re improving yourself and what your intentions are.
9.Certifications can be a differentiator.
Certifications can be a differentiator between you and someone else competing for the same position. many company were seeing that if any one had done the certification course then he will get extra privilege’s for that post . Employer used the certification as the deciding factor. For those attending college, I always recommend that they also pursue a certification because the certification serves as a point of difference between them and other college graduates.so we can say that certification is one of the deciding factor for any job.
10.A lot of employers place high value them.
Not by employers are showed by certifications, but there are still A LOT of employers that are impressed by certificate. Even in many the Department like in Defense has established baseline certifications for their personnel, such as the CompTIA Security+ for many of the security and intelligences any many more Some employers even give preference to the certifications over a college degree as it shows that employ having the extra knowledge by the doing the certification course.
0 notes
Text
Malware hide inside an Antivirus -ICSS

What do you mean by Malware?
Malware is malicious software that is a cover-up term for viruses, worms, trojans, and other harmful computer programs hackers use this for destruction and gaining access to victims’ sensitive information. In other words, the software is identified as malware based on its intended use, rather than a particular technique or technology used to build it. So now you all will think what is the difference between Malware and Virus? So the Answer is very Clear, a virus is a type of malware, so all viruses are malware (but not every piece of malware is a virus).
some of the significant malware released between 2000 and 2010:
2000 — ILOVEYOU Worm: Spreading by way of an email sent with the seemingly benign subject line, “ILOVEYOU,” the worm infected an estimated 50 million computers. Damages caused major corporations and government bodies, including portions of the Pentagon and British Parliament, to shut down their email servers. The worm spread globally and cost more than $5.5 billion in damages.
2001 — Anna Kournikova Virus: Emails spread this nasty virus that purported to contain pictures of the very attractive female tennis player, but in fact hid the malicious malware.
2003 — SQL Slammer Worm: One of the fastest spreading worms of all time, SQL Slammer infected nearly 75,000 computers in ten minutes. The worm had a major global effect, slowing Internet traffic worldwide via denial of service.
2004 — Cabir Virus: Although this virus caused little if any damage, it is noteworthy because it is widely acknowledged as the first mobile phone virus.
2005 — Koobface Virus: One of the first instances of malware to infect PCs and then propagate to social networking sites. If you rearrange the letters in “Koobface” you get “Facebook.” The virus also targeted other social networks like MySpace and Twitter.
2008 — Conficker Worm: A combination of the words “configure” and “ficker”, this sophisticated worm caused some of the worst damage seen since Slammer appeared in 2003.
If anyone wants to inject malware into your system what will be the easiest way for him? The Answer will be they will pretend to be nice to you and say to you, “Hay! you don’t have antivirus in your system someone can inject malware into your system so before they do that Install an Antivirus it will protect your System. If you don’t mind you can use my Antivirus for free”. It’s Human nature that whenever someone hears that this trusted person is giving something for free that too for their own good. In this situation when the victim trust and installs the antivirus which is embedded with malware the malware inside that get triggered and doesn’t let the antivirus software get installed. At this time you will not understand why this is happening. But you already become a victim of the attack.
Advanced persistent threats can be described as malware that lies dormant and hidden from ordinary detection tools and incident response measures. APT seeks to not only persist, but discover and proliferate, elevate privileges, and remain undetected for as long as possible (Rass, et al., 2017).One way for the APT to remain undetected is by combining polymorphic actions with encryption. A polymorphic virus replicates itself and changes certain attributes every time it infects another program. One technique is encryption key changes, whereby each infected host has a unique encryption and decryption keys. This combination makes it almost impossible to keep updated signature matches in anti-virus software (Drew, et al., 2017).Sometimes an APT can persist within an environment for days, months, or years without being detected because it only sends encrypted data to its command and control structure when a certain criteria are met. Most APTs are delivered by social engineering campaigns, such as spear-phishing against certain employees or whaling against executives and other high value targets.
How You can Protect yoursef from Such attack?
Personal vigilance, and protective tools. One of the most popular ways to spread malware is by email, which may be disguised to look as if it is from a familiar company such as a bank, or a personal email from a friend. Be wary of emails that ask you to provide passwords. Or emails that seem to be from friends, but have only a message such as “check out this cool website!” followed by a link. Personal vigilance is the first layer of protection against malware, but simply being careful is not enough. Because business security is not perfect, even downloads from legitimate sites can sometimes have malware attached. Which means that even the most prudent user is at risk, unless you take additional measures. some of the ways are:-
The most Important thing is Never Never Never Download anything from an unknown Site.
If someone offers you a free Software never take from them and better search for their official site and Download from there.
Scan full system twice a week. This will help your system from Malware and other Different types of Attacks.
for more details contact :Indiancybersecuritysolutions.com
0 notes