Photo

New Post has been published on https://goo.gl/aZt8wJ
5 Reasons Your Business Needs Firewall as a Service
Firewall as a Service
No upfront costs! Sign up today for our Firewall as a Service and stop viruses, spyware, worms, Trojans, key loggers, and more before they enter your network, with all-in-one, comprehensive network protection. Our solution provides you with the same level of network security that NASA demands and protects your network from a wide range of emerging threats.
.fusion-content-boxes-2 .heading h2color:#333333; .fusion-content-boxes-2 .fusion-content-box-hover .link-area-link-icon-hover .heading h2, .fusion-content-boxes-2 .fusion-content-box-hover .link-area-link-icon-hover .heading .heading-link h2, .fusion-content-boxes-2 .fusion-content-box-hover .link-area-box-hover .heading h2, .fusion-content-boxes-2 .fusion-content-box-hover .link-area-box-hover .heading .heading-link h2, .fusion-content-boxes-2 .fusion-content-box-hover .link-area-link-icon-hover.link-area-box .fusion-read-more, .fusion-content-boxes-2 .fusion-content-box-hover .link-area-link-icon-hover.link-area-box .fusion-read-more::after, .fusion-content-boxes-2 .fusion-content-box-hover .link-area-link-icon-hover.link-area-box .fusion-read-more::before, .fusion-content-boxes-2 .fusion-content-box-hover .fusion-read-more:hover:after, .fusion-content-boxes-2 .fusion-content-box-hover .fusion-read-more:hover:before, .fusion-content-boxes-2 .fusion-content-box-hover .fusion-read-more:hover, .fusion-content-boxes-2 .fusion-content-box-hover .link-area-box-hover.link-area-box .fusion-read-more, .fusion-content-boxes-2 .fusion-content-box-hover .link-area-box-hover.link-area-box .fusion-read-more::after, .fusion-content-boxes-2 .fusion-content-box-hover .link-area-box-hover.link-area-box .fusion-read-more::before, .fusion-content-boxes-2 .fusion-content-box-hover .link-area-link-icon-hover .icon .circle-no, .fusion-content-boxes-2 .heading .heading-link:hover .content-box-heading color: #a0ce4e; .fusion-content-boxes-2 .fusion-content-box-hover .link-area-box-hover .icon .circle-no color: #a0ce4e !important; .fusion-content-boxes-2 .fusion-content-box-hover .link-area-box.link-area-box-hover .fusion-content-box-button background: #96c346;color: #ffffff;.fusion-content-boxes-2 .fusion-content-box-hover .link-area-box.link-area-box-hover .fusion-content-box-button .fusion-button-text color: #ffffff; .fusion-content-boxes-2 .fusion-content-box-hover .heading-link:hover .icon i.circle-yes, .fusion-content-boxes-2 .fusion-content-box-hover .link-area-box:hover .heading-link .icon i.circle-yes, .fusion-content-boxes-2 .fusion-content-box-hover .link-area-link-icon-hover .heading .icon i.circle-yes, .fusion-content-boxes-2 .fusion-content-box-hover .link-area-box-hover .heading .icon i.circle-yes background-color: #a0ce4e !important; border-color: #a0ce4e !important; .fusion-content-boxes-2 .fusion-content-box-hover .link-area-link-icon-hover .heading .icon > span background-color: #a0ce4e !important; .fusion-content-boxes-2 .fusion-content-box-hover .link-area-box-hover .heading .icon > span border-color: #a0ce4e !important;
Block threats before they enter your network
Entry points into your network may now include employees’ laptops, desktops, and smartphones. Secure your network and data against sophisticated, modern-day threats with comprehensive protection that includes intrusion prevention, gateway anti-virus, anti-spyware, content/url filtering, enforced client anti-virus, and anti-spam services.
Eliminate bottlenecks
The amount of traffic being scanned by your firewall, as well as the increasing amount of threats and malware attacking it, is quickly becoming more than many firewalls can handle. Our solution is designed to protect organizations of every size without slowing down your network — providing you with fast, reliable performance.
Keep your network productive
Your network performance can be bogged down by spam, unauthorized web activity and social networking traffic that have nothing to do with getting work done. Ensure your business-critical applications have the bandwidth they need with content and application control tools.
Get an all-in-one solution
Combine the features of traditional firewalls, gateway anti-malware products, intrusion prevention systems and content filtering software in a single solution. All of these security technologies are installed, configured, deployed, and managed as one unit. Detailed event data is available through one reporting system so it is easier to identify threats early and take appropriate measures BEFORE your network has been compromised.
Protect your network with comprehensive security at a small business price
Block viruses, Trojans, worms, rootkits and polymorphic “zero-day” malware at the gateway, before they reach your network
Prevent “drive-by downloads” from infected websites
Mitigate denial-of-service and flooding attacks
Detect protocol anomalies and buffer overflow attacks
Stop network traffic from geographical regions and IP addresses associated with cybercriminals
Block outbound cybercriminals botnet “command and control” traffic from stealing your customer lists, engineering designs, trade secrets, and other confidential information
Control access to websites containing unproductive and inappropriate content
Ensure high-priority applications (CRM, order processing) receive more bandwidth than less urgent applications (chat, video streaming)
Time is running out – Get your Firewall as a Service today!
.fusion-button.button-2 .fusion-button-text, .fusion-button.button-2 i color:#ffffff;.fusion-button.button-2 border-width:1px;border-color:#ffffff;.fusion-button.button-2 .fusion-button-icon-dividerborder-color:#ffffff;.fusion-button.button-2:hover .fusion-button-text, .fusion-button.button-2:hover i,.fusion-button.button-2:focus .fusion-button-text, .fusion-button.button-2:focus i,.fusion-button.button-2:active .fusion-button-text, .fusion-button.button-2:activecolor:#ffffff;.fusion-button.button-2:hover, .fusion-button.button-2:focus, .fusion-button.button-2:activeborder-width:1px;border-color:#ffffff;.fusion-button.button-2:hover .fusion-button-icon-divider, .fusion-button.button-2:hover .fusion-button-icon-divider, .fusion-button.button-2:active .fusion-button-icon-dividerborder-color:#ffffff;.fusion-button.button-2width:auto;Get your first three months free before time runs out!
.modal-2 .modal-header, .modal-2 .modal-footerborder-color:#ebebeb;
×
FREE - No Obligation Consultation
Last Name*
First Name*
Phone
Email*
What services are you interested in?*
Don't worry if what you are looking for isn't listed here. This gives us an idea of how to plan for our consultation.
Firewall as a Service
CIO as a Service
Risk Intelligence Scan
MORTAR
TOPSTONE Cybersecurity Readiness Status
Small Business IT Support
Office 365
Moving to the cloud
Replacing your IT vendor
Training your IT staff
Special project planning
Other
Other service*
Please describe the service you are interested in
Is your IT outsourced now?
Yes
No
Sort of
Please describe what you would like to discuss
CAPTCHA
Name
This field is for validation purposes and should be left unchanged.
if(typeof gf_global == 'undefined') var gf_global = "gf_currency_config":"name":"U.S. Dollar","symbol_left":"$","symbol_right":"","symbol_padding":"","thousand_separator":",","decimal_separator":".","decimals":2,"base_url":"https:\/\/topstone.com\/wp-content\/plugins\/gravityforms","number_formats":[],"spinnerUrl":"https:\/\/topstone.com\/wp-content\/plugins\/gravityforms\/images\/spinner.gif";jQuery(document).bind('gform_post_render', function(event, formId, currentPage)if(formId == 1) gf_global["number_formats"][1] = "1":"price":false,"value":false,"2":"price":false,"value":false,"8":"price":false,"value":false,"3":"price":false,"value":false,"4":"price":false,"value":false,"9":"price":false,"value":false,"5":"price":false,"value":false,"7":"price":false,"value":false,"12":"price":false,"value":false,"13":"price":false,"value":false;if(window['jQuery'])if(!window['gf_form_conditional_logic'])window['gf_form_conditional_logic'] = new Array();window['gf_form_conditional_logic'][1] = logic: 9: "field":"actionType":"show","logicType":"all","rules":["fieldId":"4","operator":"is","value":"Other"],"nextButton":null,"section":null , dependents: 9: [9] , animation: 1, defaults: [], fields: "1":[],"2":[],"8":[],"3":[],"4":[9],"9":[],"5":[],"7":[],"12":[],"13":[] ; if(!window['gf_number_format'])window['gf_number_format'] = 'decimal_dot';jQuery(document).ready(function()gf_apply_rules(1, [9], true);jQuery('#gform_wrapper_1').show();jQuery(document).trigger('gform_post_conditional_logic', [1, null, true]); ); if(!/(android)/i.test(navigator.userAgent))jQuery('#input_1_8').mask('(999) 999-9999').bind('keypress', function(e)if(e.which == 13)jQuery(this).blur(); ); );jQuery(document).bind('gform_post_conditional_logic', function(event, formId, fields, isInit) ); jQuery(document).ready(function()jQuery(document).trigger('gform_post_render', [1, 1]) );
Close
.fusion-countdown-2 background-color:#a0ce4e;.fusion-countdown-2 .fusion-countdown-heading color:#ffffff;.fusion-countdown-2 .fusion-countdown-subheading color:#ffffff;.fusion-countdown-2 .fusion-countdown-counter-wrapper color:#ffffff;.fusion-countdown-2 .fusion-dash background-color:#333333;.fusion-countdown-2 .fusion-countdown-link color:#ffffff;
00
00
Days
00
Hrs
00
Min
00
Sec
1 note
·
View note
Photo

New Post has been published on https://goo.gl/XbFcu8
New Rules for Defense Contractors
Are you worried about the DFARS guidance and your requirement to comply?
What we can do
Strip away the confusion
Un-complicate the topic
Save you money
Assess your current security posture
Provide a clear path forward
Itemize exactly what you need to do
Free Consultation
First Name*
Last Name*
Phone
Email*
CAPTCHA
Email
This field is for validation purposes and should be left unchanged.
if(typeof gf_global == 'undefined') var gf_global = "gf_currency_config":"name":"U.S. Dollar","symbol_left":"$","symbol_right":"","symbol_padding":"","thousand_separator":",","decimal_separator":".","decimals":2,"base_url":"https:\/\/topstone.com\/wp-content\/plugins\/gravityforms","number_formats":[],"spinnerUrl":"https:\/\/topstone.com\/wp-content\/plugins\/gravityforms\/images\/spinner.gif";jQuery(document).bind('gform_post_render', function(event, formId, currentPage)if(formId == 8) if(!/(android)/i.test(navigator.userAgent))jQuery('#input_8_8').mask('(999) 999-9999').bind('keypress', function(e)if(e.which == 13)jQuery(this).blur(); ); );jQuery(document).bind('gform_post_conditional_logic', function(event, formId, fields, isInit) ); jQuery(document).ready(function()jQuery(document).trigger('gform_post_render', [8, 1]) );
0 notes
Photo

New Post has been published on https://goo.gl/2E2I0e
Life Is a Breach - What Will It Cost Your Company?
Life’s a Breach – Are You Ready?
Ready to put risk intelligence into a language your boardroom speaks?
There are misconceptions about data breaches, their affect, impact, and cost. Don’t allow yourself to think, “We haven’t been breached”, “We won’t get breached”, or “A breach won’t seriously affect us”.
The odds are good that you’ve already been breached and don’t know it. What should concern you is whether or not you know what was stolen.
Surprisingly, most small business owners don’t know what data they are holding that could cost them the most. Nor do they know where their critical data lives, or who has access to it.
If you choose not to take a proactive stance on your businesses security, you should at least know what data matters most to your business, where it resides, and who has access to it.
Consider this scenario:
You run your business from your laptop, using Dropbox, Google Drive, and Gmail. You come to work one day and find your computer locked, with a note on the screen indicating that you’ve become the latest ransomware victim.
One of the very first things you will think is: How much will this impact me if I don’t pay? What if I just lost my entire laptop to this ransomware?
Knowing your risk intelligence before a breach happens will help you answer these questions when the time comes. If you think you will avoid ransomware and/or a breach forever, you are kidding yourself.
In the ransomware laptop scenario, here are a few other things you should consider. This is what you most likely gave to a hacker:
Employee data that might have existed on your laptop
Customer data that might have existed on your laptop
User names and passwords, most likely stored on your laptop
Account numbers, credit card numbers, social security numbers, most likely stored on your laptop
How will the loss of this type of information affect your business reputation, ability to win new work, or your bank account balance when employees/customers start suing?
.fusion-button.button-2 .fusion-button-text, .fusion-button.button-2 i color:#ffffff;.fusion-button.button-2 border-width:1px;border-color:#ffffff;.fusion-button.button-2 .fusion-button-icon-dividerborder-color:#ffffff;.fusion-button.button-2:hover .fusion-button-text, .fusion-button.button-2:hover i,.fusion-button.button-2:focus .fusion-button-text, .fusion-button.button-2:focus i,.fusion-button.button-2:active .fusion-button-text, .fusion-button.button-2:activecolor:#ffffff;.fusion-button.button-2:hover, .fusion-button.button-2:focus, .fusion-button.button-2:activeborder-width:1px;border-color:#ffffff;.fusion-button.button-2:hover .fusion-button-icon-divider, .fusion-button.button-2:hover .fusion-button-icon-divider, .fusion-button.button-2:active .fusion-button-icon-dividerborder-color:#ffffff;.fusion-button.button-2width:auto;Ask about our complimentary breach analysis scan
.modal-2 .modal-header, .modal-2 .modal-footerborder-color:#ebebeb;
×
FREE - No Obligation Consultation
Last Name*
First Name*
Phone
Email*
What services are you interested in?*
Don't worry if what you are looking for isn't listed here. This gives us an idea of how to plan for our consultation.
Risk Intelligence Scan
MORTAR
TOPSTONE Cybersecurity Readiness Status
Small Business IT Support
Office 365
Moving to the cloud
Replacing your IT vendor
Training your IT staff
Special project planning
Other
Other service*
Please describe the service you are interested in
Is your IT outsourced now?
Yes
No
Sort of
Please describe what you would like to discuss
CAPTCHA
Email
This field is for validation purposes and should be left unchanged.
if(typeof gf_global == 'undefined') var gf_global = "gf_currency_config":"name":"U.S. Dollar","symbol_left":"$","symbol_right":"","symbol_padding":"","thousand_separator":",","decimal_separator":".","decimals":2,"base_url":"https:\/\/topstone.com\/wp-content\/plugins\/gravityforms","number_formats":[],"spinnerUrl":"https:\/\/topstone.com\/wp-content\/plugins\/gravityforms\/images\/spinner.gif";jQuery(document).bind('gform_post_render', function(event, formId, currentPage)if(formId == 1) gf_global["number_formats"][1] = "1":"price":false,"value":false,"2":"price":false,"value":false,"8":"price":false,"value":false,"3":"price":false,"value":false,"4":"price":false,"value":false,"9":"price":false,"value":false,"5":"price":false,"value":false,"7":"price":false,"value":false,"12":"price":false,"value":false,"13":"price":false,"value":false;if(window['jQuery'])if(!window['gf_form_conditional_logic'])window['gf_form_conditional_logic'] = new Array();window['gf_form_conditional_logic'][1] = logic: 9: "field":"actionType":"show","logicType":"all","rules":["fieldId":"4","operator":"is","value":"Other"],"nextButton":null,"section":null , dependents: 9: [9] , animation: 1, defaults: [], fields: "1":[],"2":[],"8":[],"3":[],"4":[9],"9":[],"5":[],"7":[],"12":[],"13":[] ; if(!window['gf_number_format'])window['gf_number_format'] = 'decimal_dot';jQuery(document).ready(function()gf_apply_rules(1, [9], true);jQuery('#gform_wrapper_1').show();jQuery(document).trigger('gform_post_conditional_logic', [1, null, true]); ); if(!/(android)/i.test(navigator.userAgent))jQuery('#input_1_8').mask('(999) 999-9999').bind('keypress', function(e)if(e.which == 13)jQuery(this).blur(); ); );jQuery(document).bind('gform_post_conditional_logic', function(event, formId, fields, isInit) ); jQuery(document).ready(function()jQuery(document).trigger('gform_post_render', [1, 1]) );
Close
0Number of records breached in 2016 (According to 2016 Ponemon Institute Breach Study)
$0
Average consolidated cost of a data breach (According to 2016 Ponemon Institute Breach Study)
0 notes
Photo

New Post has been published on https://goo.gl/Nb9t2Z
Risk Intelligence - Four Critical Questions
Risk Intelligence Quiz
To improve your risk intelligence, you must be able to answer these questions confidently and consistently.
What data is at Risk?
How can attackers get your data?
Who has access to your data?
How much will a breach cost you?
What Data Is At Risk?
Unprotected data at reset puts your entire business at risk to data loss.
Do you know what your critical data is?
You wonder about your exposure to malware like WannaCry and other ransomware, but do you know what data is at risk?
How Can Attackers Get Your Data?
Vulnerable computers provide a backdoor to data thieves.
Do you know how attackers will get at your data?
Do you know what backdoors exist in your business that allows data thieves to easily steal your critical data?
Do You Know Who Has Access To Your Data?
Reduce excessive access to eliminate prying eyes
Does everyone in your organization have easy access to your data?
Sometimes, to get the job done, we give everyone access to everything, and that becomes a very big problem when there is a data breach.
Do You Know How Much a Breach Will Cost You?
Know your financial liability before a breach occurs.
Run away breach costs can cripple your business
Wouldn’t it be better to know how much a breach might cost you before you actually have a breach?
.fusion-button.button-4 .fusion-button-text, .fusion-button.button-4 i color:#ffffff;.fusion-button.button-4 border-width:1px;border-color:#ffffff;.fusion-button.button-4 .fusion-button-icon-dividerborder-color:#ffffff;.fusion-button.button-4:hover .fusion-button-text, .fusion-button.button-4:hover i,.fusion-button.button-4:focus .fusion-button-text, .fusion-button.button-4:focus i,.fusion-button.button-4:active .fusion-button-text, .fusion-button.button-4:activecolor:#ffffff;.fusion-button.button-4:hover, .fusion-button.button-4:focus, .fusion-button.button-4:activeborder-width:1px;border-color:#ffffff;.fusion-button.button-4:hover .fusion-button-icon-divider, .fusion-button.button-4:hover .fusion-button-icon-divider, .fusion-button.button-4:active .fusion-button-icon-dividerborder-color:#ffffff;.fusion-button.button-4width:auto;We can help you answer these questions – Learn More
.modal-4 .modal-header, .modal-4 .modal-footerborder-color:#ebebeb;
×
FREE - No Obligation Consultation
Last Name*
First Name*
Phone
Email*
What services are you interested in?*
Don't worry if what you are looking for isn't listed here. This gives us an idea of how to plan for our consultation.
MORTAR
TOPSTONE Cybersecurity Readiness Status
Small Business IT Support
Office 365
Moving to the cloud
Replacing your IT vendor
Training your IT staff
Special project planning
Other
Other service*
Please describe the service you are interested in
Is your IT outsourced now?
Yes
No
Sort of
How satisfied are you with your provider?
Please describe what you would like to discuss
CAPTCHA
Name
This field is for validation purposes and should be left unchanged.
if(typeof gf_global == 'undefined') var gf_global = "gf_currency_config":"name":"U.S. Dollar","symbol_left":"$","symbol_right":"","symbol_padding":"","thousand_separator":",","decimal_separator":".","decimals":2,"base_url":"https:\/\/topstone.com\/wp-content\/plugins\/gravityforms","number_formats":[],"spinnerUrl":"https:\/\/topstone.com\/wp-content\/plugins\/gravityforms\/images\/spinner.gif";jQuery(document).bind('gform_post_render', function(event, formId, currentPage)if(formId == 1) gf_global["number_formats"][1] = "1":"price":false,"value":false,"2":"price":false,"value":false,"8":"price":false,"value":false,"3":"price":false,"value":false,"4":"price":false,"value":false,"9":"price":false,"value":false,"5":"price":false,"value":false,"6":"price":false,"value":false,"7":"price":false,"value":false,"12":"price":false,"value":false,"13":"price":false,"value":false;if(window['jQuery'])if(!window['gf_form_conditional_logic'])window['gf_form_conditional_logic'] = new Array();window['gf_form_conditional_logic'][1] = logic: 9: "field":"actionType":"show","logicType":"all","rules":["fieldId":"4","operator":"is","value":"Other"],"nextButton":null,"section":null,6: "field":"actionType":"show","logicType":"all","rules":["fieldId":"5","operator":"is","value":"Yes"],"nextButton":null,"section":null , dependents: 9: [9],6: [6] , animation: 1, defaults: [], fields: "1":[],"2":[],"8":[],"3":[],"4":[9],"9":[],"5":[6],"6":[],"7":[],"12":[],"13":[] ; if(!window['gf_number_format'])window['gf_number_format'] = 'decimal_dot';jQuery(document).ready(function()gf_apply_rules(1, [9,6], true);jQuery('#gform_wrapper_1').show();jQuery(document).trigger('gform_post_conditional_logic', [1, null, true]); ); if(!/(android)/i.test(navigator.userAgent))jQuery('#input_1_8').mask('(999) 999-9999').bind('keypress', function(e)if(e.which == 13)jQuery(this).blur(); ); );jQuery(document).bind('gform_post_conditional_logic', function(event, formId, fields, isInit) ); jQuery(document).ready(function()jQuery(document).trigger('gform_post_render', [1, 1]) );
Close
1 note
·
View note
Photo

New Post has been published on https://goo.gl/ESf243
One Tool Every Small Business Should Use
Propel your small business with professional grade technology support
Running a small business is challenging enough without trying to handle all of your own IT. At TOPSTONE, our focus is on mass quality, not mass quantity. Leverage our proven approach to manage costs, reduce downtime, and increase your return on investment. With one call, you can get:
Industry certified professionals who know how to handle your IT needs
Best of breed business processes to simplify IT management
Military grade security for your small business
A la carte pricing and availability – Only pay for what you need
Fanatical support, there anytime you need it
A trusted partner you can rely on
.fusion-button.button-4 .fusion-button-text, .fusion-button.button-4 i color:#ffffff;.fusion-button.button-4 border-width:1px;border-color:#ffffff;.fusion-button.button-4 .fusion-button-icon-dividerborder-color:#ffffff;.fusion-button.button-4:hover .fusion-button-text, .fusion-button.button-4:hover i,.fusion-button.button-4:focus .fusion-button-text, .fusion-button.button-4:focus i,.fusion-button.button-4:active .fusion-button-text, .fusion-button.button-4:activecolor:#ffffff;.fusion-button.button-4:hover, .fusion-button.button-4:focus, .fusion-button.button-4:activeborder-width:1px;border-color:#ffffff;.fusion-button.button-4:hover .fusion-button-icon-divider, .fusion-button.button-4:hover .fusion-button-icon-divider, .fusion-button.button-4:active .fusion-button-icon-dividerborder-color:#ffffff;.fusion-button.button-4width:auto;FREE – No Obligation Consultation
.modal-4 .modal-header, .modal-4 .modal-footerborder-color:#ebebeb;
×
FREE - No Obligation Consultation
Last Name*
First Name*
Phone
Email*
What services are you interested in?*
Don't worry if what you are looking for isn't listed here. This gives us an idea of how to plan for our consultation.
MORTAR
TOPSTONE Cybersecurity Readiness Status
Small Business IT Support
Office 365
Moving to the cloud
Replacing your IT vendor
Training your IT staff
Special project planning
Other
Other service*
Please describe the service you are interested in
Is your IT outsourced now?
Yes
No
Sort of
How satisfied are you with your provider?
Please describe what you would like to discuss
CAPTCHA
Comments
This field is for validation purposes and should be left unchanged.
if(typeof gf_global == 'undefined') var gf_global = "gf_currency_config":"name":"U.S. Dollar","symbol_left":"$","symbol_right":"","symbol_padding":"","thousand_separator":",","decimal_separator":".","decimals":2,"base_url":"https:\/\/topstone.com\/wp-content\/plugins\/gravityforms","number_formats":[],"spinnerUrl":"https:\/\/topstone.com\/wp-content\/plugins\/gravityforms\/images\/spinner.gif";jQuery(document).bind('gform_post_render', function(event, formId, currentPage)if(formId == 1) gf_global["number_formats"][1] = "1":"price":false,"value":false,"2":"price":false,"value":false,"8":"price":false,"value":false,"3":"price":false,"value":false,"4":"price":false,"value":false,"9":"price":false,"value":false,"5":"price":false,"value":false,"6":"price":false,"value":false,"7":"price":false,"value":false,"12":"price":false,"value":false,"13":"price":false,"value":false;if(window['jQuery'])if(!window['gf_form_conditional_logic'])window['gf_form_conditional_logic'] = new Array();window['gf_form_conditional_logic'][1] = logic: 9: "field":"actionType":"show","logicType":"all","rules":["fieldId":"4","operator":"is","value":"Other"],"nextButton":null,"section":null,6: "field":"actionType":"show","logicType":"all","rules":["fieldId":"5","operator":"is","value":"Yes"],"nextButton":null,"section":null , dependents: 9: [9],6: [6] , animation: 1, defaults: [], fields: "1":[],"2":[],"8":[],"3":[],"4":[9],"9":[],"5":[6],"6":[],"7":[],"12":[],"13":[] ; if(!window['gf_number_format'])window['gf_number_format'] = 'decimal_dot';jQuery(document).ready(function()gf_apply_rules(1, [9,6], true);jQuery('#gform_wrapper_1').show();jQuery(document).trigger('gform_post_conditional_logic', [1, null, true]); ); if(!/(android)/i.test(navigator.userAgent))jQuery('#input_1_8').mask('(999) 999-9999').bind('keypress', function(e)if(e.which == 13)jQuery(this).blur(); ); );jQuery(document).bind('gform_post_conditional_logic', function(event, formId, fields, isInit) ); jQuery(document).ready(function()jQuery(document).trigger('gform_post_render', [1, 1]) );
Close
0 notes
Photo

New Post has been published on https://goo.gl/3ijud6
The Truth Behind New Cybersecurity Rules for Contractors
No, the sky is not falling, and no, you probably won’t lose your defense contracts either.
With December 31, 2017 just around the corner, many technology firms, news agencies, and people claiming to be experts are waving the red flag, fanning the flames, and doing their best to incite some panic.
Well, here is the real truth about these new ‘cybersecurity’ rules for defense contractors. There’s no need to take my word for what they say because I’m going to paste the exact words right here:
(1) By submission of this offer, the Offeror represents that it will implement the security requirements specified by National Institute of Standards and Technology (NIST) Special Publication (SP) 800-171 “Protecting Controlled Unclassified Information in Nonfederal Information Systems and Organizations” (see http://dx.doi.org/10.6028/NIST.SP.800-171) that are in effect at the time the solicitation is issued or as authorized by the contracting officer not later than December 31, 2017.
Next, let me show you where I got that information:
http://www.acq.osd.mil/dpap/dars/dfars/html/current/252204.htm#252.204-7008
If you like, you can visit that link and get the entire supplement, but I wouldn’t bother. Here are the top truths about this supplement.
Look for the keyword in the text above that I pasted in for you. See the word ‘will’? Do you think that means you MUST comply by 12/31/2017?
There are no cybersecurity police that are going to come knock on your office door and take your contracts
A Contracting Officer (KO) doesn’t know that much about cybersecurity, NIST 800-171, or the Risk Management Framework (RMF)
The KO of your current contracts will not magically pass down some special authorization or ruling that will impact your current contracts
Don’t listen to all of the big IT vendors who are telling you it will take 6-12 months to implement the technology necessary to comply
If you have the time to read the 110 security controls listed in NIST 800-171, you will notice the high percentage of controls which are not impacted by technology, but rather by people and process
That said, does this mean you just thumb your nose at this guidance? Absolutely not!
In my recent experiences with my customers, and what I expect to see more of in the future, is preferential weighting to contractors who produce well-documented cybersecurity operational readiness statements in their proposals.
It is unlikely that there will be any type of forced compliance to this new guidance. However, there is nothing saying that companies who implement the guidance, and assure the government of their dedication and diligence regarding the protection of federal information, won’t win more contracts than companies who do nothing.
What you SHOULD be doing
For the last 2.5 years, TOPSTONE has been developing a simplified program to help businesses align with this DFARS supplement. Not because we could see the future, but because this guidance went into effect way back in 2013 and no one did anything. The guidance was literally ignored by defense contractors.
The struggle many business owners have is understanding what NIST 800-171 means, how to apply it, and more importantly, where to start.
First, you need to realize that NIST 800-171 is about so much more than just your technology. I know this because I authored the 110 questions in our client intake self-assessment form. That’s what I mean when I say ‘simplified’. We took the security controls and did the geek–>business speak interpretation for our clients, and then presented the controls in simple yes/no questions.
Not surprising, many of these questions are about people, policy, and process, which you just can’t fix with more stuff that goes blinky-blinky in a rack.
What you need is a plan that allows you to determine how to get started, what you should assess, and most importantly, after you figure that out, what you should do first, second, and third.
You’ve got questions, and we’ve got answers. Through our MORTAR program, we can help you get to the point where your proposals boast your cybersecurity operational readiness in big bold print, and you’ll have the artifacts to back it up.
Thanks for reading!
.fusion-button.button-6 .fusion-button-text, .fusion-button.button-6 i color:#ffffff;.fusion-button.button-6 border-width:1px;border-color:#ffffff;.fusion-button.button-6 .fusion-button-icon-dividerborder-color:#ffffff;.fusion-button.button-6:hover .fusion-button-text, .fusion-button.button-6:hover i,.fusion-button.button-6:focus .fusion-button-text, .fusion-button.button-6:focus i,.fusion-button.button-6:active .fusion-button-text, .fusion-button.button-6:activecolor:#ffffff;.fusion-button.button-6:hover, .fusion-button.button-6:focus, .fusion-button.button-6:activeborder-width:1px;border-color:#ffffff;.fusion-button.button-6:hover .fusion-button-icon-divider, .fusion-button.button-6:hover .fusion-button-icon-divider, .fusion-button.button-6:active .fusion-button-icon-dividerborder-color:#ffffff;.fusion-button.button-6width:auto;Learn More
.modal-6 .modal-header, .modal-6 .modal-footerborder-color:#ebebeb;
×
FREE - No Obligation Consultation
Last Name*
First Name*
Phone
Email*
What services are you interested in?*
Don't worry if what you are looking for isn't listed here. This gives us an idea of how to plan for our consultation.
MORTAR
TOPSTONE Cybersecurity Readiness Status
Small Business IT Support
Office 365
Moving to the cloud
Replacing your IT vendor
Training your IT staff
Special project planning
Other
Other service*
Please describe the service you are interested in
Is your IT outsourced now?
Yes
No
Sort of
How satisfied are you with your provider?
Please describe what you would like to discuss
CAPTCHA
Phone
This field is for validation purposes and should be left unchanged.
if(typeof gf_global == 'undefined') var gf_global = "gf_currency_config":"name":"U.S. Dollar","symbol_left":"$","symbol_right":"","symbol_padding":"","thousand_separator":",","decimal_separator":".","decimals":2,"base_url":"https:\/\/topstone.com\/wp-content\/plugins\/gravityforms","number_formats":[],"spinnerUrl":"https:\/\/topstone.com\/wp-content\/plugins\/gravityforms\/images\/spinner.gif";jQuery(document).bind('gform_post_render', function(event, formId, currentPage)if(formId == 1) gf_global["number_formats"][1] = "1":"price":false,"value":false,"2":"price":false,"value":false,"8":"price":false,"value":false,"3":"price":false,"value":false,"4":"price":false,"value":false,"9":"price":false,"value":false,"5":"price":false,"value":false,"6":"price":false,"value":false,"7":"price":false,"value":false,"12":"price":false,"value":false,"13":"price":false,"value":false;if(window['jQuery'])if(!window['gf_form_conditional_logic'])window['gf_form_conditional_logic'] = new Array();window['gf_form_conditional_logic'][1] = logic: 9: "field":"actionType":"show","logicType":"all","rules":["fieldId":"4","operator":"is","value":"Other"],"nextButton":null,"section":null,6: "field":"actionType":"show","logicType":"all","rules":["fieldId":"5","operator":"is","value":"Yes"],"nextButton":null,"section":null , dependents: 9: [9],6: [6] , animation: 1, defaults: [], fields: "1":[],"2":[],"8":[],"3":[],"4":[9],"9":[],"5":[6],"6":[],"7":[],"12":[],"13":[] ; if(!window['gf_number_format'])window['gf_number_format'] = 'decimal_dot';jQuery(document).ready(function()gf_apply_rules(1, [9,6], true);jQuery('#gform_wrapper_1').show();jQuery(document).trigger('gform_post_conditional_logic', [1, null, true]); ); if(!/(android)/i.test(navigator.userAgent))jQuery('#input_1_8').mask('(999) 999-9999').bind('keypress', function(e)if(e.which == 13)jQuery(this).blur(); ); );jQuery(document).bind('gform_post_conditional_logic', function(event, formId, fields, isInit) ); jQuery(document).ready(function()jQuery(document).trigger('gform_post_render', [1, 1]) );
Close
0 notes
Photo

New Post has been published on https://goo.gl/4TLrhZ
Do This Before You Allow an IT Vendor to Start Work
×This is NOT legal advice — TOPSTONE does not provide legal advice.
Service Contracts Benefit All Involved Parties
#fusion-testimonials-3 aborder-color:#515151;#fusion-testimonials-3 a:hover, #fusion-testimonials-3 .activeSlidebackground-color: #515151;.fusion-testimonials.classic.fusion-testimonials-3 .author:afterborder-top-color:#e2e2e2 !important;
The bargain that yields mutual satisfaction is the only one that is apt to be repeated.
B.C. Forbes
Don’t get caught up in the moment during a data breach or other disaster and allow a vendor to begin work on your systems, in your offices, or with your employees until you have a signed contract in place.
According to Ts & Cs, here are 10 reasons you need a contract3.
A contract will help you to navigate the law
A contract helps you to get paid
A contract helps to minimise disputes or problems
A contract protects your intellectual property
A contract limits liability
A contract creates certainty
A contract provide in-depth coverage of your business
A contract helps you to give good customer service
A contract helps to build trust and give peace of mind
A contract allows you to manage expectations
If you find skipping the contract because you don’t have a good starting point for one, I’ve included a template and good starting point for one. This template is provided as is and you are welcome to modify it to suit your needs. All contracts should be reviewed by appropriate legal counsel before being used.
Download the template here –> General Contract for Services
×This is NOT legal advice — TOPSTONE does not provide legal advice.
0 notes
Photo
New Post has been published on https://goo.gl/DL660Q
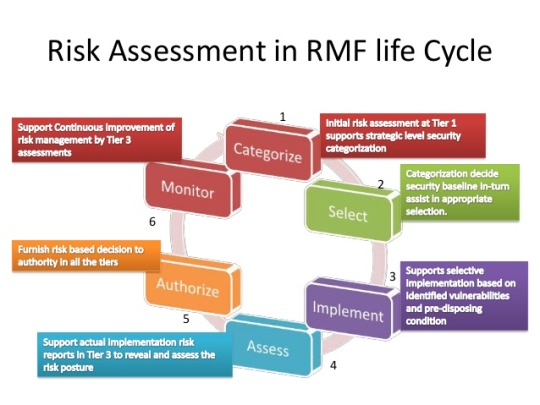
Cybersecurity Frameworks for Small Businesses
Many small businesses today are grassroots based and organically grown. This style of growth can mean that the information technology infrastructure is also organically grown. As operations and technology mature, it can be difficult to align with a formal framework, such as the National Institute of Standards and Technology (NIST) Risk Management Framework (RMF)1.
Even with a competent and talented information technology team, small businesses will likely need to assistance of an outside auditor or mentor to help align with and adopt such a framework. For this article, the CompTIA Security Trustmark+2 will be used to explain key concepts.
Businesses hoping to make the leap from good to great3 will need to possess the foresight to recognize the importance of this topic.
A key roadblock for small business leaders and owners is the failure to comprehend the complexity of aligning with and complying with a framework. This failure is not on the part of business leaders and owners but the cybersecurity industry.
This article will present a brief overview of what alignment means and will detail the initial steps business leaders, and owners should take to get started.
Organizations working to align with a particular framework must:
Complete the steps necessary to document the current state of the infrastructure
Select a series of controls to use to assess compliance (alignment) with the framework
Implement the controls
Determine their effectiveness
Authorize the newly aligned system to operate
Monitor the system for change
The topic of aligning with a framework is too large a concept for business owners to digest. Breaking the task into smaller component pieces allows the company to step through a guided process to:
Phase I – Get familiar with how they currently operate
Phase II – Determine what security controls apply to their systems
Phase III – Look for gaps and areas out of alignment or missing
Phase IV – Engineer changes to bring the organization into alignment
Phase V – Assess for effectiveness
Phase VI – Formally authorize the system to operate
Phase VII – Monitor
You might be thinking, “how or where do I get started?”.
First, select a framework and do not develop your framework from scratch. As mentioned earlier in this article, the CompTIA Security Trustmark+ business certification is an excellent framework for small businesses for the following reasons.
Based on the NIST Cybersecurity Framework
Provides a cost-effective path for demonstrating compliance with the principal industry regulations such as PCI-DSS, SSAE-16, HIPAA, and others reliant on the NIST Framework
Second, find an organization that can guide your team through the processes mentioned above. Wasting time and money struggling to figure things out on your own is money well wasted. The framework you implement will grow and mature with your company for decades to come. Now is the time to be comprehensive and detailed in your approach.
To correctly align with any framework, the organization will need to look at more than just technology. Risk management frameworks are comprehensive and encompass the management, operations, and technical aspects of your business.
At the end of it all, there are only three things you as the business owner can do with risk.
Accept it
Transfer it
Mitigate it
Before you can do any of these three things with risk, you must first know what it is.
Thanks for reading — If you would like to continue the conversation, please feel free to contact me at [email protected]
2 notes
·
View notes
Photo

New Post has been published on https://topstone.com/dear-small-business-owner-dont-punish-independent-thought/
Dear Small Business Owner - Don't Punish Independent Thought
0 notes
Photo

New Post has been published on https://goo.gl/JrGm7F
How to Create a Wicked Good Password
0 notes
Photo

New Post has been published on https://topstone.com/dear-director-consider-budgeting-security/
Dear IT Director - Consider This When Budgeting for Security
0 notes
Photo

New Post has been published on https://topstone.com/dear-ceo-tips-securing-company/
Dear CEO - Tips for Securing Your Company
0 notes
Photo

New Post has been published on https://topstone.com/dear-ceo-cybersecurity-101/
Dear CEO - Cybersecurity 101
0 notes
Photo

New Post has been published on https://goo.gl/mrdoyX
Dear IT Manager - Key Tips for Your Success
0 notes
Photo
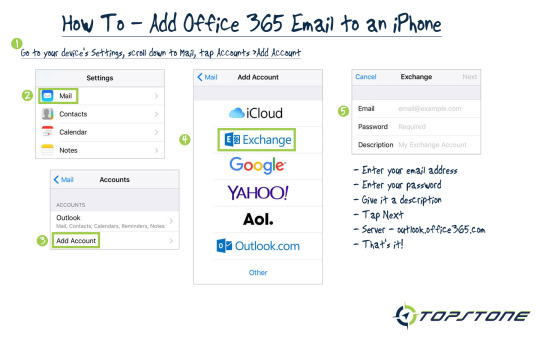
New Post has been published on https://goo.gl/F29dlG
How To - Adding Office 365 Email To An iPhone
0 notes
Photo
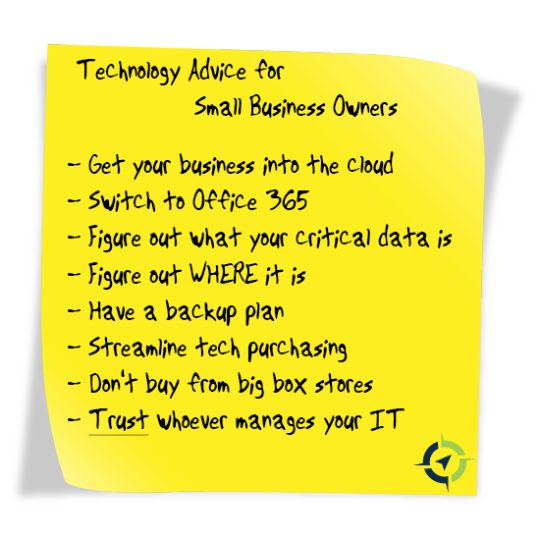
New Post has been published on https://goo.gl/wncVRo
Technology Advice for Small Business Owners
0 notes
Photo

New Post has been published on https://goo.gl/20YsxJ
Dear IT Manager - Know The Cycle And How To Stop It
0 notes