Don't wanna be here? Send us removal request.
Text
Managing the Risks of Shadow AI
Shadow AI refers to the unmonitored use of AI within organizations, bypassing IT or compliance oversight. Risks include hidden internal models, embedded AI in third-party apps, and unauthorized use of generative AI tools—posing threats to data privacy, governance, and model oversight.
Visit: https://cimcon.com/managing-the-risks-of-shadow-ai/
0 notes
Text

5 Steps to More Effective EUC Controls
Learn 5 practical steps to implement more effective EUC controls, from maintaining an up-to-date model inventory and standardizing risk assessments to leveraging interdependency maps, automating documentation, and enforcing approval workflows aligned with SS1/23.
Visit: https://cimcon.com/5-steps-to-more-effective-spreadsheet-euc-controls/
0 notes
Text
Shadow AI: What is it and How to Manage the Risk from it?
Shadow AI refers to the unsanctioned use of AI tools or models within organizations, often without IT’s knowledge. As AI adoption grows, so do the risks of internal misuse and hidden AI in third-party apps—making oversight critical for businesses.
Visit: https://cimcon.com/shadow-ai-what-is-it-and-how-to-manage-the-risk-from-it/
0 notes
Text
The Startling Reality of Errors of Accounting: Why They Happen and How to Prevent Them
Accounting errors are alarmingly common, with over 90% of large spreadsheets containing mistakes that can lead to financial loss, reputational damage, and regulatory fines. From poor version control to insecure access, these risks can be mitigated through automated EUC inventory, access controls, audit trails, and error-checking workflows.
Visit: https://cimcon.com/the-startling-reality-of-errors-of-accounting-why-they-happen-and-how-to-prevent-them/
0 notes
Text

Key Components of White House Executive Order on AI: A Quick Snapshot
Explore the key highlights of the Executive Order on the Safe, Secure, and Trustworthy Development and Use of Artificial Intelligence, outlining federal standards for AI safety, privacy, fairness, consumer protection, workforce support, and global leadership.
Visit: https://cimcon.com/navigating-the-ai-horizon-a-closer-look-at-the-white-executive-order-on-ai-and-its-impact-on-financial-companies/
0 notes
Text

Key Components of SS1/23 Principles for Model Risk Management
Discover the key components of SS1/23, the PRA’s new model risk management regulation for U.K. banks, effective May 17, 2024. Learn how it governs AI, mandates model inventories, enforces governance, and promotes independent validation for safe, compliant modeling practices.
Visit: https://cimcon.com/understanding-ss1-23-principles-for-model-risk-management-mrm/
0 notes
Text
Fraud Detection: AI Risk Management
Discover what fraud detection is and why risk mitigation is vital for organizations. Learn how to manage financial threats like identity theft, phishing, and occupational fraud. Explore key strategies to safeguard your business from rising fraud risks and reduce potential revenue loss.
Visit: https://cimcon.com/fraud-detection-ai-risk-management/
0 notes
Text

Features of AI Model Risk Management Solution
CIMCON’s EUC Insight software delivers end-to-end AI model risk management and regulatory compliance by identifying AI models, automating risk assessments, analyzing model interdependencies, maintaining model inventory, and providing full monitoring and audit trails—all in one integrated platform.
Visit: https://cimcon.com/automated-ai-risk-assessment-mitigation/
0 notes
Text
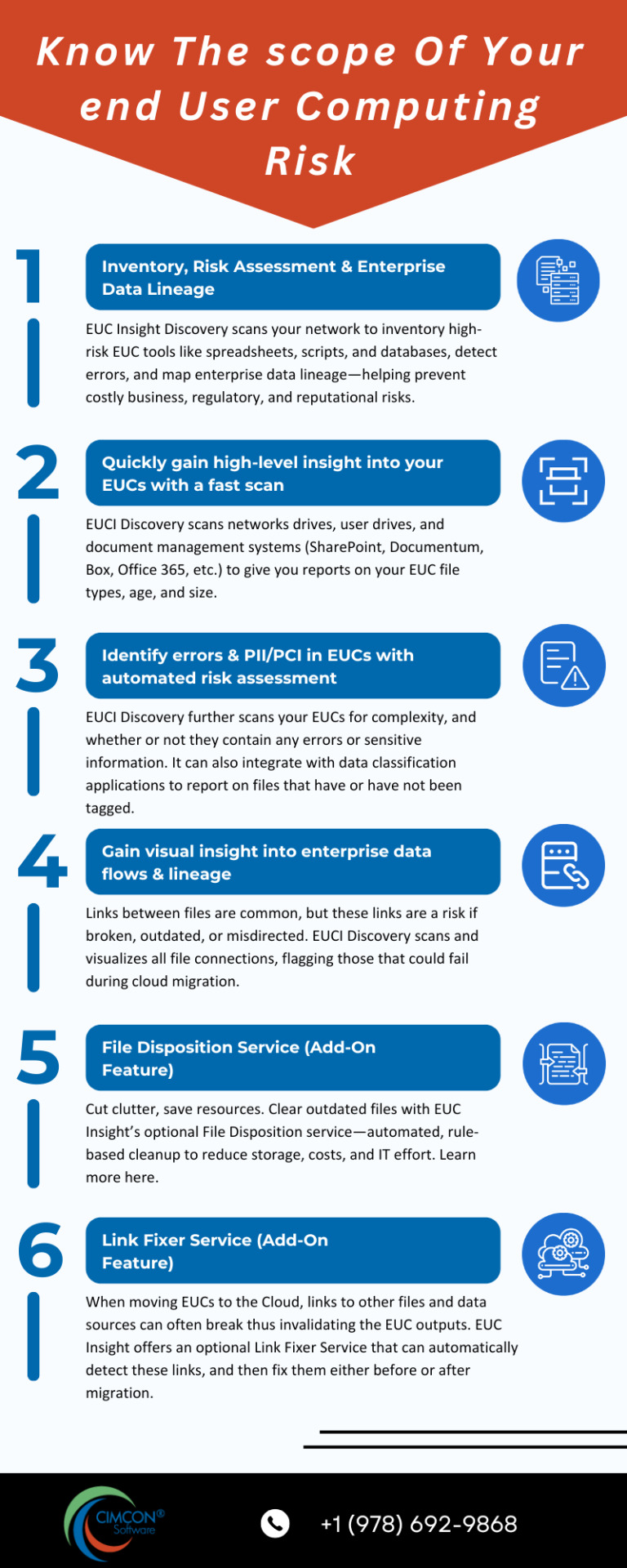
Know the scope of your end user computing risk
Know how many uncontrolled employee files you have and understand your end user computing risk with help from EUC Insight Discovery module. Automatically scan your network to inventory high-risk files, detect errors and sensitive data, visualize data lineage, and enable secure cloud migration with optional link fixer and file disposition services.
Visit: https://www.cimcon.com/products/solutions-eucinsight
0 notes
Text
Shadow AI: Addressing the Hidden Risk within Your Organization

The Hidden Risk of Shadow AI
According to IBM, enterprise employee usage of generative AI increased from 74% in 2023 to 96% in 2024. With the rise of AI, comes the natural rise of Shadow AI, or the unauthorized use of AI within an organization. What is most concerning about Shadow AI is that it is inherently difficult to know whether or not there is the use of Shadow AI within your organization and what is the risk potential of this usage.
Unfortunately, recent research indicates that 37% of employees share sensitive work information with AI tools without their employer's permission, and 46% use their preferred AI tools without IT approval. One employee that was surveyed frankly confessed, "it's easier to get forgiveness than permission".
So what kinds of Shadow AI should you look out for in your team or organization, what are the relevant regulatory recommendations and requirements around Shadow AI, why is it even a problem, and what can you do about this? In this article, we will dive deeper into all of these questions.
Types of Shadow AI Risk
So what are the different risks of Shadow AI that could be relevant to your organization? There are a few different types and each have different strategies in order to be mitigated:
Hidden Internally Built Models: Updating existing models for use cases such as automation internally or external interactions with customers in undetected ways (updating a credit risk model using an OpenAI model).
AI in 3rd party applications in models: Having AI within 3rd party applications or models upon installation or update without the knowledge of the firm using the application.
Unauthorized Internal Use of 3rd Party AI Tools: Using Generative AI tools such as Chat GPT to write code, get answers to questions, etc. without being careful about data & privacy leaks, sharing proprietary code, or lack of proper governance.
The Expanding Regulatory Landscape
Shadow AI is ever more falling under worldwide regulatory focus in various different aspects. While it is an ever-evolving landscape, a few regulations that are relevant to know about include:
SS 1/23 (UK): Effective as of May 17, the PRA set out this Supervisory Statement to outline expectations for UK firms. Principle 2.6 anticipates that firms should have vendor models validated to the same expectations as internal Model Risk Management expectations.
SR 11-7 (U.S.): The SR 11 7 guidance from the Federal Reserve is a long standing framework for effective model risk management (MRM) which includes the need to validate and monitor third-party models, which now increasingly includes AI-driven solutions.
The E.U. AI Act (E.U.): Thisact representsan extensive legislative framework that governs the use of artificial intelligence in organizations that can impact public safety and well-being, thus making companies liable for mistakes or poor practices.
The Artificial Intelligence and Data Act (Canada): Sets out expectations for AI use in Canada to protect public interests and requires appropriate steps to identify, analyze, and mitigate the risks of harm or biased outcomes.
Why is Shadow AI Proliferating?
According to Sreekanth Menon, Genpact's global head of AI/ML, there are several reasons that Shadow AI is picking up steam.
Accessibility: Consumer-level artificial intelligence tools like ChatGPT are readily available and perform useful functions for everyday tasks such as writing, designing, and coding.
Organizational Lag: Nearly half (45%) of executives have adopted a "wait and watch" approach to the implementation of artificial intelligence, while 75% of employees are already using AI in their jobs.
Reduced Barriers to Entry: Unlike those traditional IT or AI technologies that required technical know-how, LLM-based applications have reduced barriers to entry.
Shortening Adoption Cycles: AI adoption cycles are accelerating, compressing decision-making timeframes and compelling CIOs and CISOs to devise appropriate risk mitigation strategies.
Lack of Training: A study conducted by the National Cybersecurity Alliance discovered that 55% of employees who use AI in their professions have never undergone training on the associated risks of AI.
Shadow AI Risk Management
Effectively addressing the risk of Shadow AI involves an approach that involves several stakeholders and brings together multiple different perspectives including the technological lens, organizational lens, and proper governance policies and frameworks. A few best practices that can assist in managing this risk from each lens includes the following:
AI Usage Identification and Monitoring
Regular Monitoring for Unrecognized AI Models: Regularly scheduled scans can be leveraged to identify the likelihood of AI usage in models and End User Computing (EUCs) before the danger causes errors.
Comprehensive AI Testing Suite: Testing procedures for data drift, validity, reliability, fairness, interpretability, and code quality can help detect sudden shifts in model performance that could suggest the use of Shadow AI in 3rd party tools or models. Systematic documentation of test outcomes in a structured format can help provide much needed transparency and accountability.
Interdependency Mapping: Charting the interdependencies between models and data sources, with particular attention to third-party models is fundamental to effective MRM of Shadow AI as models and data are interrelated and errors and changes can cascade through these relationships.
Performance Monitoring: Third-party model performance should be tracked for unplanned changes that could indicate the existence of shadow AI elements.
Applying Controls and Governance
Access Management: Controlling access to models and EUCs is always best practice and can help ensure that there is accountability and transparency within your model landscape.
Audit Trails: Audit logs can be instrumental for similar reasons in that they help firms track changes to models and maintain detailed logs of the people accountable for changes to particular models.
Approval Workflows: Automating workflows can help understand where bottlenecks exist. Frustrations from these bottlenecks or unclear policies can often lead to the use of Shadow AI.
Security Vulnerability Scanning: Automatic scanning of AI third-party libraries for security vulnerabilities can help identify the use of AI as you update the libraries that are leveraged within an organization. These can be important even in cases where you are aware of the AI being used.
Developing Organizational Awareness
Clear Policies: Develop clear policies outlining the process for adopting and utilizing AI tools, including approval procedures and usage policies.
Cross-Team Collaboration: Foster communication among IT, data teams, and business units so that departmental requirements are met with approved solutions.
Regular Training: Hold training sessions to bring attention to the risks of unauthorized AI usage and equip workers to identify and report shadow AI processes.
Encourage Vetted AI Tools: Offer a curated list of approved AI solutions that meet the organization's security and compliance standards, along with intuitive documentation and training materials.
How to Safely Manage the Risk from AI?
Once you create your AI policy as well as effective means of understanding the success of this policy implementation, your organization can feel safer allowing employees to leverage the potential of GenAI applications such as LLMs in controlled ways. At this point, having a comprehensive testing suite for these LLMs can be a critical aspect of building trust with these tools. A few technological solutions that could help include:
Large Language Models (LLMs) Vulnerability Testing: Test LLMs for bias, fairness, toxic content generation, and potential leakage of sensitive information.
Explainable LLMs: Implementing source attribution to trace where responses originate within internal data sources, helping identify and mitigate causes of errors.
LLM Hallucination Testing: Leverage the latest developments in RAG models and Challenger LLMs to monitor and reduce instances of inaccurate information being relayed to customers.
GenAI Detection Reporting: Audit your EUC and Model landscape to determine the overall risk posture of your environment for unintentional uploads into AI generators.
Getting Ahead on Expecting the Unexpected
Today organizations are all figuring out how to best unleash the potential of AI, while limiting the risks that can come from errors or improper implementations of this transformative tool. However, just because an AI policy is in place to address these concerns doesn’t mean that firms can avoid the efforts required to monitor the use of this AI policy by all the relevant stakeholders. With the right combination of a robust policy as well as a nuanced approach to understand the implementation of this policy, teams can feel confident that AI is being leveraged, but in the safe controlled way in which it will do the most good.
Who Are We?
So why are we so invested in Shadow AI and where do these technological and organizational best practices come from? Well, we at CIMCON Software have pioneered the management of AI, EUC, and Model Risk for over 25 years, with over 800 customers worldwide. As an ISO 27001 Certified Information Security company with presence in the USA, London, and the Asia Pacific region, we offer end-to-end solutions to address the Shadow AI challenge. We understand how these nascent risks can grow within an organization and are always available to chat about how we can best operationalize practices that keep us all safe from the worst risks of AI.
0 notes
Text

CIMCON's Toolkit for Model Risk Management
CIMCON's Toolkit for Model Risk Management automates model identification, maintains a dynamic model inventory, enables flexible risk assessments, maps interdependencies, manages documentation, and ensures proper controls, workflows, and third-party risk management.
Visit: https://www.cimcon.com/use-cases/model-risk-management
0 notes
Text
Hidden Use of AI or GenAI within an Organization

Learn strategies to mitigate the risks of Shadow AI, including AI model monitoring, LLM vulnerability testing, hallucination detection, and implementing oversight controls for safe and accountable AI use. Ensure compliance and transparency by integrating robust testing, documentation, and approval workflows for internal AI systems.
Visit: https://www.cimcon.com/blog/post/45/managing-the-risks-of-shadow-ai
0 notes
Text
AI Model Inventory And Risk Assessment
Discover the critical need for AI Model Risk Management in financial institutions. With CIMCON’s expertise, mitigate business, regulatory, and reputational risks using automated assessments, real-time monitoring, and a robust model inventory. Stay compliant and safeguard your AI investments.
Visit: https://www.cimcon.com/use-cases/ai-model-inventory-and-risk-assessment
0 notes
Text

Benefits of EUC Insight Disposition
Optimize your file servers with EUC Insight Discovery File Disposition. Automate file cleanup, reduce storage costs, and enhance performance with a rule-based engine that categorizes and disposes of files based on age, size, owner, and content. Minimize backup scope, improve reliability, and streamline file management—all while allowing user input when needed.
Visit: https://www.cimcon.com/products/euc-insight-disposition
0 notes
Text
CIMCON Software | Frequently asked questions
CIMCON Software helps minimize business risks in end-user computing applications: spreadsheets, Access Databases, VBScript, Tableau, R, etc., ensuring compliance and data integrity. As the leading EUC solutions provider, we serve 500+ companies worldwide with the most robust risk management system, proven software, and global support.
Visit: https://www.cimcon.com/
0 notes
Text
EUC Risk Management & Controls in the Cloud
Discover how CIMCON's EUC Insight Inventory ensures seamless cloud migration. Move servers and data to AWS or Azure without disrupting EUC controls using a proven 3-phase approach for secure, uninterrupted transitions.
Visit: https://www.cimcon.com/blog/post/1/euc-risk-management-controls-in-the-cloud
0 notes
Text

Top 3 Reasons to Keep Using Excel
Discover why spreadsheets remain essential in end user computing despite risks of errors and breaches. Explore 3 key reasons to retain Excel in business processes, including its ease of use, IT flexibility, and risk mitigation options that balance efficiency and control.
Visit: https://www.cimcon.com/blog/post/30/top-3-reasons-to-keep-using-excel
0 notes