Don't wanna be here? Send us removal request.
Text
Building a Malicious Backdoor & C2 Server in Python
Backdoors and Command & Control (C2) servers are some of the tools used in cyberattacks to establish unauthorized access to systems. Their architecture needs to be understood by cybersecurity professionals in order to defend systems against them. This article examines the conceptual design of these elements in Python, with a focus on ethical implications and defense strategies. Networking…
0 notes
Text
Basic Network Concepts for Hacking
If you’re stepping into the world of ethical hacking, then network knowledge isn’t just helpful but a must-have. The internet and private networks are the playgrounds where security threats come into being, and to know how data moves, how devices talk to each other, and where the weak points are is crucial. Without a strong foundation in networking, hacking is like trying to pick a lock without…
0 notes
Text
All About Logic Bombs: Your Computer Could Be Hijacked With Malware
Most users are familiar with viruses, trojans and worms. But there is a special type of malware that stands out for its stealth and accuracy in hitting its target – a logic bomb. Let’s figure out what it is. Operating principle Attackers embed malicious code into regular software. The program appears to work normally, but when certain conditions are met, a destructive mechanism is launched.…
0 notes
Text
Port Binding Shellcode Remote Shellcode
S When a host is exploited remotely, a multitude of options are available to gain access to that particular machine. The first choice is usually to try the execve code to see if it works for that particular server. If that server duplicated the socket descriptors to stdout and stdin, small execve shellcode will work fine. Often, however, this is not the case. This section explores dierent…
0 notes
Text
GRUB LUKS Bypass and Dump
Recently, I needed to get the data off of a LUKS encrypted partition on a Virtual Machine that “wasn’t mine” and I’d never done it before. You can probably guess what happened next. As a preface, if you’ve landed on this blog and are thinking to yourself _”Finally, someone will tell me how to recover the LUKS key for my non-bootable system! …I have bad news. This blog is not for you. For…
0 notes
Text
Can Port Scanning Crash the Target Computer or Network
So, you’ve probably heard of port scanning in movies or tech blogs, where hackers “scan” networks to find weaknesses. But what is it, really? And can something as simple as scanning ports actually crash a computer or take down a whole network? Let’s break it down without the jargon. Imagine your computer is like a house, and ports are the doors and windows. Port scanning is basically someone…
0 notes
Text
Build & Secure Your Internet: How to Make Your Own VPN & Configure it For Ultimate Privacy 🛡️
You’ve probably heard the term “VPN” tossed around, especially if you’ve ever looked into ways to keep your online activities safe. So, what is a VPN exactly? I’m glad you’re curious, because understanding VPNs is the first step to taking control of your online privacy. A VPN, or Virtual Private Network, is like your personal online bodyguard. Imagine you’re at a crowded coffee shop using public…

View On WordPress
1 note
·
View note
Text
3 Essential Reasons for Prioritizing Website Security
You might think that security is important but only for big companies. This article is going to change your mind. Hacked website can affect your audience Security is critical as long as you have any visitor on your website (actually, security is vital even if you don’t have any visitor at all, you’ll see!). Either recruiters on your personal project portfolio website or customers on your…

View On WordPress
2 notes
·
View notes
Text
Exploring the All-Time Best Book for Ethical Hacking
Greetings, fellow cyber enthusiasts! Rocky here, your friendly neighborhood ethical hacker. Today, I embark on an exciting journey to explore the world of hacking books and share with you a collection of timeless treasures that have left an indelible mark on my ethical hacking career. From the depths of my experience and knowledge, I present to you an article that unravels the secrets of the…

View On WordPress
5 notes
·
View notes
Text
Vulnerability Assessment: Understanding, Identifying, and Mitigating Security Risks
In today’s interconnected and technology-driven world, the security of systems, networks, and applications is of utmost importance. Organizations face constant threats from malicious actors seeking to exploit vulnerabilities and gain unauthorized access to sensitive information. To ensure robust security measures, vulnerability assessment plays a crucial role. Vulnerability assessment is a…

View On WordPress
1 note
·
View note
Text
The Hidden Anxiety of Remote Work: Unveiling the Struggles Behind the Screens
In recent years, remote work has surged in popularity, offering individuals the freedom to work from the comfort of their own homes or any location with an internet connection. This newfound flexibility has brought about numerous advantages, from improved work-life balance to reduced commuting stress. However, amidst the apparent benefits, a hidden undercurrent of anxiety has emerged, affecting…

View On WordPress
2 notes
·
View notes
Text
Google Releases Urgent Chrome Update to Fix Actively Exploited Zero-Day Vulnerability
Google on Friday released out-of-band updates to resolve an actively exploited zero-day flaw in its Chrome web browser, making it the first such bug to be addressed since the start of the year. Tracked as CVE-2023-2033, the high-severity vulnerability has been described as a type confusion issue in the V8 JavaScript engine. Clement Lecigne of Google’s Threat Analysis Group (TAG) has been…

View On WordPress
0 notes
Text
A New Microsoft AI Research Shows How ChatGPT Can Convert Natural Language Instructions Into Executable Robot Actions
Large language models (LLMs) that can comprehend and produce language similar to that of humans have been made possible by recent developments in natural language processing. Certain LLMs can be honed for specific jobs in a few-shot way through discussions as a consequence of learning a great quantity of data. A good example of such an LLM is ChatGPT. Robotics is one fascinating area where…
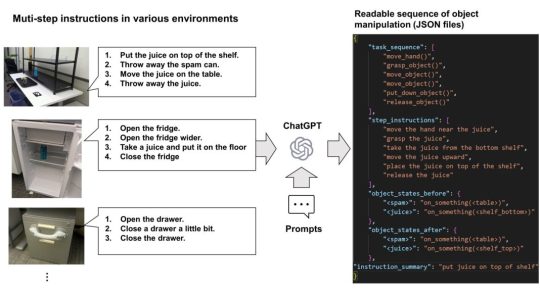
View On WordPress
0 notes
Text
Metasploit Basics, Part 9: Using msfvenom to Create Custom Payloads
At times, we may want to create a custom payload (for more on Metasploit payloads, see Metasploit Basics, Part 3: Payloads). For instance, we may want to embed a payload/listener into an application or other malicious software that we hope the target clicks and we can take control of their computer. This is exactly what msfvenom is designed for. Previously, to re-encode a payload in…

View On WordPress
0 notes
Text
Web Application Hacking : Introduction to Web Hacking
In today’s increasingly digital world, web applications have become an integral part of our lives. They enable us to perform a vast range of tasks, from online shopping to banking, social networking, and more. However, this increased reliance on web applications has also led to an increased risk of cyber attacks, including web application hacking. Web application hacking involves exploiting…

View On WordPress
1 note
·
View note
Text
Aircrack-ng tutorial : Mastering Wireless Network Security with Aircrack-ng
Wireless networks have become an integral part of our lives, providing us with the convenience of accessing the internet and other resources without being tethered to a physical connection. However, with the increase in the number of wireless networks comes the need for security measures to protect against unauthorized access and data theft. Aircrack-ng is a powerful tool that can be used to test…

View On WordPress
1 note
·
View note