Don't wanna be here? Send us removal request.
Text
MitM - Password capture - SA (D)
After browsing many websites on my phone I decided to log into an account on a http connection. After i entered my (fake but go ahead and try them) details Cain and Abel was able to display the credentials I entered.
This can be seen from this image:
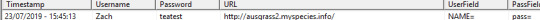
As observed from above I was able to perform a MitM attack on my phone, without the victim having knowledge.
0 notes
Text
Man-in-the-Middle Attack - SA
The next attack i’ll attempt is the Man-in-the-Middle (MitM) attack.
So to begin this attack i’ll first have to sniff the network and find my victim. Fortunately this has been done from all the sniffing done on Wireshark in my previous posts.
Switches + Spoofing
Switches are designed to reduce network traffic and congestion via isolation of only sending packets to a particular IP address. In order to receive traffic from the victim, I would need to change the CAM table which maps the IP addresses to the mac addresses.
Changing the CAM table to send the packets to my device is known as ARP spoofing.
Using the program Cain and Abel i’m given a GUI to begin my ARP spoofing.
First i’ll sniff the mac addresses in the network.
Below is a blacked out list of where the devices and MAC addresses would be listed.
Next I use Cain and Abel’s APR to poison the communication between the server and the target device. In this case i’ll target my own phone connected to the wifi.
Once completed I now see all traffic between my phone and the router. First i open a bunch of apps on my phone to view the program routing the packets from my phone to my computer to then the router.
This is the concept of the MitM attack, my computer now acts as the man in the middle. My computer is receiving all traffic from my phone and then forwarding it to the router. With this program I am able to know exactly what is being sent to and from the router from my phone.
Additionally, I can view the packets information through Wireshark. Seen below is the packets from opening facebook and the time of those packets.
0 notes
Text
Deauthentication Attack - SA
A deauthentication attack describes sending a deuathentication frame to a connected device which forces the device to disconnect.
Technically it is defined as a:
“sanctioned technique to inform a rogue station that they have been disconnected from the network”
In attempting to perform a deauth attack I’ll be using Ubuntu with the aircrack-ng suite.
-------------------------------------------------------------------------------------------------------
Unfortunately using kali linux on Windows currently won’t allow me to perform the deauth attack, however after spending hours on trying to get kali to work on my windows computer, i’ll just explain the process.
So hypothetically in a world that Windows would work and I was attempting to deauth a victim device “ImaginaryPhone321″:
First i’ll be running iwconfig to discover what my wireless card is called.
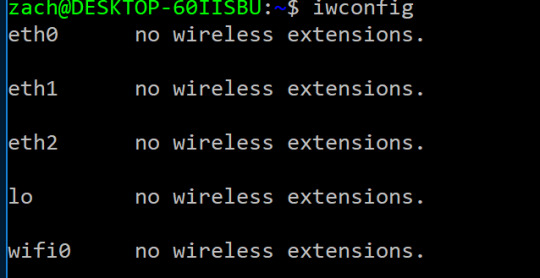
One of these would provide lengthy information and not the no wireless extensions. response
Then I would run a command to put my wireless card into monitor mode which would allow me to monitor the traffic on the network.
First, I’d run iwconfig again to find my new device name due to the monitor change and then I would then run and airdump command to discover the list of routers in range.
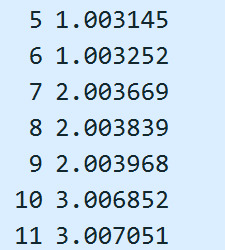
After this, I would check which router my device is connected to by checking the PWR column. The highest value in this column would be the router I am closest to.
Here is an example of the PWR column values.

After finding the correct router that our victim device is connected to in order to deauth “imaginaryphone321″ the next step would be to note the BSSID (mac address) of the router and the channel of the router.
BSSID: also known as a mac (media access control) is an address which specifies the router’s network card and is made up of two parts.
xx:xx:xx:yy:yy:yy
the first part (x’s) specify the makers of the network card and the second part (y’s) specify the exact network card (think of it as a licence plate for network cards).
Both the BSSID and channel of the router appear from the iwconfig command, so these are no trouble to attain.
With this information I would then run:
airodumb-ng [MONITOR’S NAME] --bssid [ROUTERS BSSID] -- channel [ROUTERS CHANNEL]
From this you would receive a list of devices connected to the router. This list won’t give the names of the devices however searching the first part(x’s) on a mac lookup website you can easily attain the manufacturer. In my case “imaginaryphone321″ happened to be the only apple device on the network and so was very easy to identify.
Finally, the attack is ready to be made.
By using the command:
aireplay-ng --deauth 0 -c [DEVICES MAC ADDRESS] -a [ROUTERS MAC ADDRESS] [MONITOR’S NAME]
the target device will be rejected from the router. The 0 in this command describes an infinite amount of deauth frames , -c is the victim “imaginaryphone321″ and -a is the router the victim is connected to.
Once this entire process is completed “imaginaryphone321″ will be unable to connect to the router.
0 notes
Text
Identifying the traffic - Cont - SA
TCP: a connection-oriented protocol meaning that a connection is established and maintained until messages have finished being exchanged.
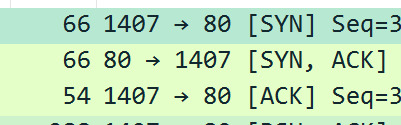
TCP’s three way handshake:
To begin the connection a SYN packet is sent across the network to check for open ports for connection. The target server receives this packet and responds with an ACK packet as confirmation. The client server receives this ACK packet and responds with an ACK packet.
Here is a three-way handshake I found on the wifi:
0 notes
Text
Security Evaluation - SA
Current update on an evaluation of the security of the wifi.
Accessing the network: Proved to be close to impossible to brute force. However with tools that are available on internet I believe with a powerful processor and access to default passwords associated with the router, it may be possible to crack. Additionally if the password was changed from the factory set password that also may largely decrease the bits of security involved.
Exploring the network: This proved to be very simple. Install network programs and use their commands to achieve what you want. Once you have access to the wireless network, even without admin power you can interact with other devices very easily. There is very little confidentiality within the wireless network once you are a part of it.
Intercepting the packets: Yet again proved to have no security. However the security of these packets lie within the protocols.
0 notes
Text
Identifying the traffic (CR) - SA
Protocols intercepted:
ICMPv6: is an error-reporting protocol network devices like routers use to generate error messages to the source IP address when network problems prevent delivery of IP packets.
UDP: A transmission protocol enabling process to process communication. UDP sends messages, called datagrams, and is considered a best-effort mode of communications. UDP just sends the packets, which means that it has much lower bandwidthoverhead and latency
Upon inspection of the packets, multiple UDP packets are sent from the same IP address and that’s probably sending packets for a computer game.
DNS: The Domain Network System (DNS) protocol helps Internet users and network devices discover websites using human-readable hostnames, instead of numeric IP addresses.
Upon inspection of the packets, this is most likely my laptop
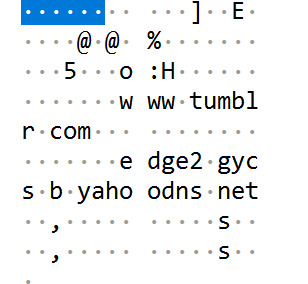
As seen above, amongst the junk is www.tumblr.com.
Additionally using nslookup on the source IP shows:
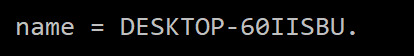
which matches my computer’s name.
0 notes
Text
Intercepting Packets - SA (PS)
Now begins the intercepting packets phase using the program Wireshark.
I’ll be using promiscuous mode and running the program for several minutes to capture some traffic and sniff the network.
After the time has ended, I’ll identify what the general traffic was to understand what had happened
0 notes
Text
Exploring the Network - SA
To begin understanding what is going on in the network and what packets can be intercepted. First I will attempt to discover what is happening in the network and where the traffic is coming from.
So, to begin this task I will first discover the inet address of my device and the subnet Mask of the wireless network. To achieve this I will be using net-tools on ubuntu. Using net-tools I can call ifconfig and find my inet address on the network:
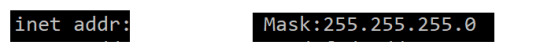
Where the inet address will be in the form XXX.XXX.XXX.XXX
By knowing the Mask and my IP, i’m able to utilise nmap, and call
nmap -sL XXX.XXX.XXX.0/24
The -sL flag stands for list scan, and the resultant of this scan gives me all devices connected on the wifi.
Examples of devices connected on my network:
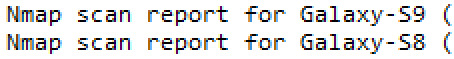
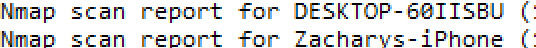
This tool and knowledge will greatly assist when packets start being intercepted and I can check which address sent the packet and from what device, thus nmap provides a lookup tool.
0 notes
Text
Starting from given access (password recovery) - SA
Now after been given access to the wireless network the password no longer becomes an issue and after using the cmd command:
netsh wlan show profile name=XXXXX key=clear
the password is easily recovered.
Given the scenario that you don’t remember the password and need to access it at a later time all that is required is to be in range of the network to know the network name (assuming password isn’t changed from last access) and the cmd command above will give the password remembered on your computer (windows).
0 notes
Text
Starting From nothing - SA
To begin, i’ll try to access the wireless network with no knowledge of the password and router.
To begin my attempt attempt it would be best to understand if it can be brute forced in reasonable time.
After researching the most common routers used in Australia the most popular eight are:
Netcomm
TP Link
iiNet
Huawei
Telstra Gateway
NETGEAR
D-Link
Belkin
Lets assume the network uses NETGEAR.
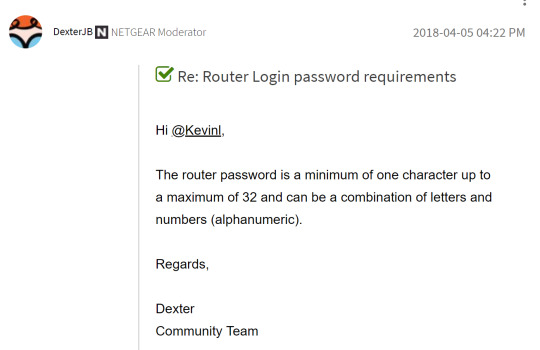
After conducting some research on the possible length and characters in NETGEAR passwords I came across this post from the NETGEAR website.
Given this information:
There is:
26 lower case letters in the alphabet (a..z)
26 upper case letters in the alphabet (A..Z)
10 possible digits (0..9)
and 32 places to place these.
Hence there is:
(26+26+10) combinations and 32 places with repetition allowed.
Giving a result of (62)^32 possible passwords.
Using log(62^32)/log(2) gives a result of 190.5 bits of security
Brute forcing this with my laptop will take a few eternities so that’s now out of question.
0 notes
Text
Something Awesome Proposal
My something awesome proposal is to intercept packets on a wireless connection and discover what is possible.
This can include but not limited to:
- deauthing devices
- intercepting handshakes
- brute forcing the hash
Extensions could include viewing the packets at a connection level and attempt to break the HTTPS. Additionally this can be further extended as research is completed and more possibilities open up. Essentially the aim is to discover what power you have given different levels of accessibility on a wireless network. Possible answered questions include: How hard would the password be to crack? What is possible when you are connected? What is possible when you are admin?
Also the concept of man in the middle and view/modify messages could be an extension.
PS: Access the network and Intercept any packets
CR: Identify what is being intercepted, using this try to deauth devices and intercept handshakes.
D: Brute force the hash + view messages
HD: Modify messages + crack HTTPS
(This can be changed according to what turns out difficult and what is easy)
0 notes