#shellcode-exploitation
Explore tagged Tumblr posts
Text
also you'll never believe who showed up in my debugger this weekend

(eip is how %rip shows up in gdb - it's actually more like "half" of %rip because %rip stores 8 bytes, while %eip stores 4 bytes, which is what you're seeing on the right)
hehe it's finally done - the Hatori/Touichirou aura fucking/sexual objectification/weird esper sex fic
#BUFFER OVERFLOWS W/ SHELLCODE ARE SOO COOOOOOOOL like its exactly what i wrote into %rip#the taking apart of C code into assembly- reading memory locations- redirecting instruction pointers around to point to ur own exec-#(couldve written it better.... but i didnt know a lot abt buffer overflows at the time..)#makes me feel bigbrained and smort#but theyre also super versatile? - they showed up in both of the exploit-based security papers i read last week#hacking is so fun!#yap
24 notes
·
View notes
Text
Cisco Exposes State-Sponsored Hackers Exploiting Cisco Firewall Zero-Days CVE-2024-20359

Cisco has uncovered a sophisticated state-backed hacking group exploiting two previously unknown vulnerabilities in Cisco Adaptive Security Appliance (ASA) and Firepower Threat Defense (FTD) firewalls since November 2023. The malicious cyber espionage campaign, dubbed "ArcaneDoor," has successfully infiltrated government networks worldwide, compromising crucial security infrastructure.
Weaponizing Zero-Day Exploits for Cyber Espionage
The threat actors, identified as UAT4356 by Cisco Talos and STORM-1849 by Microsoft, leveraged two zero-day vulnerabilities—CVE-2024-20353 (denial of service) and CVE-2024-20359 (persistent local code execution)—to breach Cisco firewalls. These previously undisclosed security flaws allowed cybercriminals to deploy sophisticated malware implants, granting them persistent access and remote control over compromised devices. One implant, dubbed "Line Dancer," is an in-memory shellcode loader capable of executing arbitrary payloads, disabling logging mechanisms, and exfiltrating captured network traffic. The second implant, a persistent backdoor named "Line Runner," incorporates multiple defense evasion techniques to evade detection while enabling the attackers to execute arbitrary Lua code on the hacked systems. Hallmarks of State-Sponsored Cyber Threats Cisco's analysis reveals that the threat actor's bespoke tooling, espionage focus, and in-depth knowledge of targeted devices are hallmarks of a sophisticated state-sponsored actor. The malicious actors exploited their access to exfiltrate device configurations, control logging services, and modify authentication mechanisms for lateral movement within compromised environments.
Urgent Call for Mitigation and Enhanced Security
In response to this severe cyber threat, Cisco has released security updates to address the two zero-day vulnerabilities and strongly recommends that customers promptly upgrade their ASA and FTD devices to the latest patched software versions. Administrators are also urged to monitor system logs for suspicious activity, implement strong multi-factor authentication, and ensure devices are securely configured and logged to a centralized location. As state-sponsored cyber threats continue to escalate, organizations must prioritize proactive security measures, regular patching, and robust incident response strategies to safeguard critical infrastructure and sensitive data. Complacency in the face of such advanced cyber espionage campaigns can devastate national security and organizational resilience. Read the full article
2 notes
·
View notes
Text
Google warns infoseccers: Beware of North Korean spies sliding into your DMs
In the ever-evolving landscape of cybersecurity threats, vigilance remains paramount. Recent reports from Google's Threat Analysis Group (TAG) have unveiled concerning activities involving suspected North Korean-backed hackers. These malicious actors are once again setting their sights on the infosec community, employing familiar tactics and some intriguing new tools.
The Social Engineering Approach
Just as they did in 2021, suspected North Korean agents are employing social engineering tactics to infiltrate the infosec community. They initiate contact through social media platforms, building trust and rapport with potential targets before moving communication to secure services like Signal or WhatsApp. This method allows them to establish a seemingly legitimate connection before launching their cyberattacks.
A Dangerous Payload
Once a relationship is established, the threat actors send a malicious file containing at least one zero-day vulnerability in a popular software package. While Google did not disclose the affected vendor, they assured the public that efforts are underway to deploy a patch. This technique is a stark reminder of the persistent threat posed by zero-day vulnerabilities, which can catch even the most prepared organizations off guard.
The malicious file includes shellcode that collects information from compromised systems and sends it back to command-and-control (C2) servers. This shellcode shares similarities with previous North Korean exploits, indicating a potentially organized and well-equipped threat actor.
A Disturbing Discovery
In addition to the established tactics, Google's TAG uncovered an unsettling development - a standalone tool for Windows named "dbgsymbol." This tool initially appears benign, designed to download debugging symbol information from various sources. Such information is invaluable for debugging software or conducting vulnerability research.
However, there's a dark twist to this tool. It possesses the capability to download and execute arbitrary code from an attacker-controlled domain. This feature raises the stakes significantly, as it can be leveraged to deliver devastating malware payloads.
Staying Safe in a Dangerous Landscape
Given the potential risks, it's crucial for anyone who may have downloaded or run dbgsymbol to take immediate action. Google recommends ensuring your system is in a known clean state, which may require a full reinstallation of the operating system. This precaution is necessary to prevent any hidden malware from compromising your system further.
source- https://www.theregister.com/2023/09/11/infosec_roundup/
1 note
·
View note
Text
From Beginner to Pro: The 5 Best Ethical Hacking Books to Read In an era where cybersecurity threats are increasing daily, ethical hackers play a crucial role in safeguarding digital systems. If you're an aspiring ethical hacker, reading the right books can provide the foundation you need to build strong hacking and penetration testing skills. We've curated a list of the 5 best books for ethical hacking, offering everything from beginner-friendly concepts to advanced hacking techniques. Whether you're new to cybersecurity or looking to sharpen your hacking skills, these books will set you on the right path. 1. Ethical Hacking: A Hands-on Introduction to Breaking In Author: Daniel Graham Level: Beginner to Intermediate This book is a perfect starting point for ethical hacking enthusiasts. It provides practical hands-on lessons in penetration testing, guiding you through real-world hacking scenarios. Key Highlights: ✅ Step-by-step guidance on penetration testing ✅ Learn to break into computers and networks ethically ✅ Covers fundamental hacking techniques and tools If you’re looking to get started with ethical hacking and understand the mindset of a hacker, this book is a great investment. 2. Gray Hat Hacking: The Ethical Hacker's Handbook Authors: Allen Harper, Daniel Regalado, and others Level: Intermediate to Advanced "Gray Hat Hacking" is one of the most comprehensive books on ethical hacking. It goes beyond the basics, introducing advanced security tools, reverse engineering, and fuzzing techniques. Key Highlights: ✅ In-depth coverage of zero-day vulnerabilities ✅ Learn binary scanning and advanced exploitation techniques ✅ Covers topics such as malware analysis and vulnerability discovery If you want to go beyond beginner-level hacking and explore advanced cybersecurity concepts, this book is a must-read. 3. Learn Ethical Hacking from Scratch Author: Zaid Sabih Level: Beginner This book is one of the best beginner-friendly ethical hacking books available. It takes you from zero to hero, covering ethical hacking concepts, penetration testing techniques, and using Kali Linux. Key Highlights: ✅ Covers basic to intermediate ethical hacking techniques ✅ Hands-on practical exercises using real-world examples ✅ Teaches penetration testing using Kali Linux If you want to learn ethical hacking from scratch and gain hands-on experience, this book is an excellent choice. 4. Hacking: The Art of Exploitation Author: Jon Erickson Level: Intermediate Unlike other books that focus only on penetration testing, this book goes deep into the core principles of hacking and exploitation techniques. It includes a Linux programming crash course, making it a perfect read for aspiring hackers who want to understand the fundamentals of cybersecurity. Key Highlights: ✅ Deep dive into exploitation techniques and vulnerabilities ✅ Learn how programs and network security actually work ✅ Covers buffer overflows, cryptography, and shellcode writing If you're interested in learning how exploits work under the hood, this book is a must-read. 5. The Web Application Hacker’s Handbook Authors: Dafydd Stuttard & Marcus Pinto Level: Intermediate to Advanced With web applications being a prime target for hackers, this book focuses on web security and penetration testing techniques. It’s an essential read for ethical hackers who want to specialize in web security testing. Key Highlights: ✅ Covers SQL injection, XSS, CSRF, and other web attacks ✅ Learn how to test web applications for security flaws ✅ A must-read for bug bounty hunters and penetration testers If you're aiming to become a web security expert, this book will help you master web application penetration testing. Conclusion Ethical hacking is a rapidly growing field, and reading the right books can give you a competitive edge. Whether you're just starting or looking to specialize in advanced penetration testing techniques, these books will provide valuable insights.
💡 Pro Tip: Combine your reading with hands-on practice in virtual labs like Hack The Box, TryHackMe, and Kali Linux to build real-world experience! Which book are you planning to read first? Let us know in the comments! 🚀
0 notes
Text
Port Binding Shellcode Remote Shellcode
S When a host is exploited remotely, a multitude of options are available to gain access to that particular machine. The first choice is usually to try the execve code to see if it works for that particular server. If that server duplicated the socket descriptors to stdout and stdin, small execve shellcode will work fine. Often, however, this is not the case. This section explores dierent…
0 notes
Text
What The Shell?: Part 2| TryHackMe
An introduction to sending and receiving (reverse/bind) shells when exploiting target machines. Part-2 Task 9 msfvenom Msfvenom: the one-stop-shop for all things payload related. Part of the Metasploit framework, msfvenom is used to generate code for primarily reverse and bind shells. It is used extensively in lower-level exploit development to generate hexadecimal shellcode when developing…
0 notes
Text
I'll let you rate these.
No prompt at all, just your commands flush against your terminal border
Escape code exploit that lets you run shellcode that plays a rickroll every time the prompt appears
Unterminated color codes that just fucks your shit up
Unterminated color code that just fucks your shit up but the color is the same as your terminal background
A prompt that's configured to output 🥺 when the previous command exited non-zero and 🥹 when it exits zero
💩
I'd be too busy giggling to get anything done
Rating prompt symbols
$
The dollar sign is a classic. Default on bash and familiar to everyone. Does remind of capitalism though. 7/10
#
The hash symbol is almost universally used for root shells. They say it protects users from accidentally copying in dangerous commands but I'm not convinced. 9/10
%
The percent sign is the default user prompt symbol for zsh and csh. Effective and straight to the point. 8/10
>
Never seen the greater-than symbol in a shell but here and there in custom prompts. Makes me feel like im talking to the machine. 10/10
539 notes
·
View notes
Text
Wargames - Shellcode Lesson (simple)
So, this week, I got a walked-through a shellcode wargame by some unnamed cooked-c*#&.
So we have the following binary:
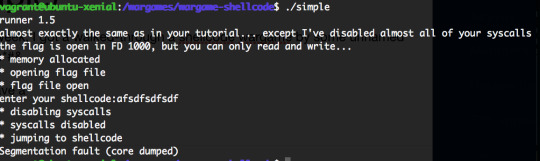
The important information is that we have the flag stored within a file opened with a file descriptor of 1000. So, our high level objective is to write shellcode that does the following:
Read from fd 1000
Write to stdout 1
So, we’ll have to create x6 assembly code and make syscalls, so we need to understand how to call said syscalls (ie. what values need to be put in which registers). We can use this resource - kernelgrok.
So, looking at this, we get the following information:
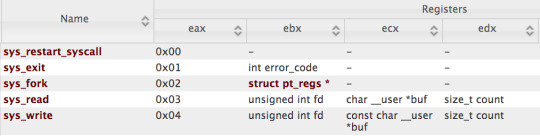
So for constructing our shellcode, we need the following steps:
Creating space for a buffer to read into
Call sys_read, reading from file fd 1000 into the buffer
Call sys_write, the contents of the buffer onto stdout
This can be achieved with the following shellcode which was created using the kernelgrok as a reference (which values in which registers):
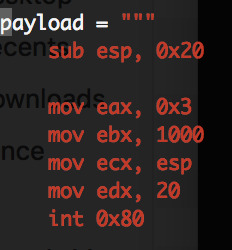
Note: as it’s a 32 bit system, int 0x80 is the equivalent of syscall in a 64 bit machine.
After using pwntool’s assembler function, asm(payload), it’s output is sent resulting in successfully retrieving the flag:
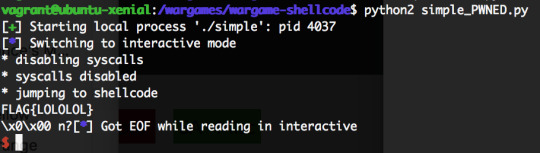
Note: the extra characters printed is garbage from the 20 bytes buffer.
0 notes
Link
#vulnerability#CobaltStrike#C2#Malware#Payload#Exploit#VAPT#PostExploitation#shellcode#Cyber#Hacking#APT#Infosec#Appsec#Pentest#Security
0 notes
Text
Wanna. Wanna make a puzzle game that's like, it's about hacking right? Like you gotta hack into a bunch of computer systems and such. And like you've got a suitably cybery aesthetic, lots of glowing monospace text and stuff, and a simple (maybe drag-and-drop even) interface. But little do the uninitiated know that I'm actually teaching them how to do actual binary exploitation! Like I'll come up with a simple but plausible little virtual machine architecture, very few bells and whistles, something approachable and digestible. And the simplest puzzles will be just about learning how to read the assembly for this machine and figure out what it does, and then we'll start doing simple buffer overruns and stack smashing, then some shellcoding, then graduate to dealing with stack canaries, ASLR, W^X, etc. Teach how to do ROP, stack pivots, maybe even assorted heap exploits...
162 notes
·
View notes
Photo

#Youtubechannel for hackers #Shellcode #payload #exploitation #softwarevulnerability #zeroday #vulnerabilities #security #services by #cyspaceglobal #incidentmanagement #informationtechnology #informationsystems #informationsecuritymanagement #soc #redteam #blueteam #socanalyst #databreaches #cyspace https://www.instagram.com/p/CDbP5HMAHtd/?igshid=hq5x4mxbfva1
#youtubechannel#shellcode#payload#exploitation#softwarevulnerability#zeroday#vulnerabilities#security#services#cyspaceglobal#incidentmanagement#informationtechnology#informationsystems#informationsecuritymanagement#soc#redteam#blueteam#socanalyst#databreaches#cyspace
0 notes
Text
YAPO Yet another PHP Obfuscator this tools able to (de)compress your php shellcode string...
YAPO Yet another PHP Obfuscator this tools able to (de)compress your php shellcode string and inject common file signature like jpeg to fuck webserver uploader or malware string scanner like what i made before. no need to install whole shit, just download the single phar executable file and fuck them all. you can download it from Here https://github.com/Cvar1984/yapo #redteam #hackers #shellcode #exploit #web

-
2 notes
·
View notes
Photo

Fim de semana animado curso de #Ethical #Hacking #Exploitation com o instrutor Laios e os amigos @ricardoneiva e o @gnoronhar #VQV #study #securitycast ... #shellcode na veia!! (em Federal District) https://www.instagram.com/p/Bxp0dPOnwQP/?igshid=kq6170bdp6he
0 notes
Text
Passing OSCP
So I got the email every OSCP student wants this morning- I passed OSCP on my first attempt.

In the name of tradition, I’m just writing this to document my thoughts, experiences and my preparation up until enrollment. :)
Background
I’m self-taught in every aspect of IT that I know- from basic networking concepts to programming- and have been doing CTFs on sites such as HackTheBox and VulnHub.
Prior to OSCP, the only professional experience in pentesting I had was a 3 month-long apprenticeship with a local company; even there I didn’t get any real exposure to actual pentesting (thus why it was only 3 months.)
I don’t have a degree yet either- I’m currently in my first year of Cyber Security (BSc) with Open University.
Preparation
I first heard of OSCP last year when I tried a physical university- there was an ethical hacking society there that were pretty much obsessed with the certification. After hearing of it’s alleged difficulty and reputation in the industry I looked into it and then hopped on the band wagon. I definitely wanted to be an OSCP.
I’d say that I had around 1 and a half years of CTF experience before enrolling, a lot of those machines being based off a list of OSCP-like VMs. I also had experience with buffer overflow at this point (had already hacked Brainpan and completed a majority of the challenges on SmashTheTux.)
I pretty much just decided to go for it one day, unsure of if I was ready or not.
The Course
I opted for 90 days lab time and spent nearly all day everyday hacking the lab machines in that time (probably missed 1-2 weeks altogether). In that time I got almost all the public network apart from dependent machines and two of the hard ones. A few machines from Dev and Admin too.
I barely even looked at the PDF until I went over using Immunity Debugger for buffer overflow but I think it depends on where your knowledge stands as to whether taking the time to do the PDF exercises is worth it or not. Like I said, before enrollment I’d already rooted a fair few machines on other platforms.
The Exam
5AM on Saturday the 17th of October was my exam start time. I had no issues with the proctoring software- lucky considering the proctoring software allegedly has poor Linux support (my OS is Ubuntu.) I thought starting earlier was a good idea as it meant -in the event of things going wrong- that I wouldn’t have to stay up a full extra night. I could have admitted defeat and went to sleep at 5. xD
While I did pass, I do feel the early start wasn’t a wise move: I was extremely tired after a night of tossing and turning, feeling my eyes starting to burn by 12 noon.

My sleep deprivation caused me to make a fair few silly mistakes I wouldn’t have otherwise made too- the buffer overflow took me 2-3 hours all because I didn’t notice I’d tried to set PORT instead of LPORT in my msfvenom payload!
By 8pm the following night I had 60 points under my belt- rooting the 10 point was all I had left to do before I had enough points to pass. By 10pm I had the 10 point- again due to my tiredness I hadn’t been logically trying everything to troubleshoot why things weren’t working as intended (don’t wanna give anything away about any of the exam machines.)
At this point I was exhausted. Happy with calling it a night, I proceeded to go back and take the necessary screenshots for my report the next day. This took a while- it was 1-2am before I told the proctor I was done and they ended the exam.
Ecstatic that I was halfway to passing, I went to bed eagerly- I still had a report to write.
The Report
The report writing is very tedious and -frankly- not what you want to do after the hacking part of the exam. I was still pretty tired from the day before and I just wanted to get it done.
I didn’t write the best report- I missed out some command output accidentally and had a nightmare formatting the report (this is why sleep matters!) but I had it finished and submitted in 8 hours.
Results
I got the great news today that I’ve passed- I’m now an OSCP! I’m very happy with this after spending so long preparing for it.

What’s Next?
I think I’m going to spend the next three years I’m at university getting deeper into exploit and malware development, maybe privilege escalation techniques too: I have a strong interest in these areas. I’ll probably do the odd CTF now and again just to keep my skill sharp in that area too.
Thoughts and Advice
Now I’m no sort of expert in the field yet; I definitely advice people to spend a fair bit of time on OSCP prep before enrolling.
Google OSCP-like VMs and go through them. Please: do not look at hints. I think this is a vital component to OSCP- the ability to be independent. You won’t have anyone to go to for advice in a real pentest or the exam, after all.
Looking at buffer-overflow prior to the exam is also an idea: it means the concepts of registers, x86 vs x64 and shellcode aren’t completely foreign to you. Like I said above- Brainpan and SmashTheTux are pretty good VMs for this.
I definitely think you should try to get to a point where you don’t need the course PDF beforehand so you can focus all your energy on the labs.
Doing this course has honestly been one of the most difficult things I’ve done- not because the machines themselves are difficult; it’s the pressure (especially if you paid for it out of savings- £1100 is ALOT of money to me!) and the time it takes. It tires you out physically and mentally.
However, it was also one of the most rewarding experiences I’ve had- while I wish I wasn’t as tired on the day of the exam so I could have got nearer to 100 points, I still managed to pass a famously difficult exam on my first attempt. All thanks to my preparation.
26 notes
·
View notes
Text
Emp3R0R - Linux Post-Exploitation Framework Made By Linux User
Emp3R0R - Linux Post-Exploitation Framework Made By Linux User #CloudFlare #Emp3R0R #Framework #linux #Malware #MITM
linux post-exploitation framework made by linux user Still under active development 中文介绍 check my blog for updates how to use what to expect (in future releases) packer: cryptor + memfd_create packer: use shm_open in older Linux kernels dropper: shellcode injector – python injector: inject shellcode into another process, using GDB port mapping: forward from CC to agents, so you can use…

View On WordPress
#CloudFlare#Emp3R0R#Framework#linux#Malware#MITM#Post-Exploitation#PostExploitation#Redteam#Redteaming#Remote Administration#Rootkit#Trojan Malware#User
1 note
·
View note
Text
Sunday Roundup: 28th of May 2017
amzn_assoc_ad_type = "banner"; amzn_assoc_marketplace = "amazon"; amzn_assoc_region = "US"; amzn_assoc_placement = "assoc_banner_placement_default"; amzn_assoc_campaigns = "echo"; amzn_assoc_banner_type = "category"; amzn_assoc_isresponsive = "true"; amzn_assoc_banner_id = "1ZZ5TM5SVRD2GHZ0KFG2"; amzn_assoc_tracking_id = "kraljevicn1-20"; amzn_assoc_linkid = "78d0ce00bb3ae0fc191ee006bde05194";
Sunday Round up for the week ending the 28th of May 2017:
Articles:
Interview with the Security Sleuth: https://www.teramind.co/blog/interview-security-sleuth
Critical Vulnerability in Samba from 3.5.0 onwards: https://isc.sans.edu/forums/diary/Critical+Vulnerability+in+Samba+from+350+onwards/22452/
Applocker Bypass via Registry Key Manipulation: https://www.contextis.com//resources/blog/applocker-bypass-registry-key-manipulation/
Beats and Bytes - Striking the Right Chord in Digital Forensics: https://digital-forensics.sans.org/blog/2017/05/22/beats-and-bytes-striking-the-right-chord-in-digital-forensics
The Man Who Made the Mistake of Trying to Help Wikileaks: https://motherboard.vice.com/en_us/article/jason-katz-wikileaks
Cameradar - An RTSP Surveillance Camera Access Multitool: http://www.kitploit.com/2017/05/cameradar-rtsp-surveillance-camera.html?utm_source=dlvr.it&utm_medium=facebook&m=1
Your Exploit is Mine: Automatic Shellcode Transplant for Remote Exploits: https://www.ieee-security.org/TC/SP2017/papers/579.pdf
Using Cloud Deployment to Jump-Start Application Security: https://www.sans.org/reading-room/whitepapers/analyst/cloud-deployment-jump-start-application-security-37805
Verify If A Photo Was Really Taken By A Suspected Camera - Camera Ballistics 2.0: https://www.forensicfocus.com/News/article/sid=2895/
Twitter:
"Classifying Illegal Activities On Tor Network Based On Web Textual Contents" #forensics #feedly https://t.co/EqrT3eVPIK
— The Security Sleuth (@Security_Sleuth) May 21, 2017
In 2017 only losers pay for VPN's #itrtg https://t.co/9mlZjwzDDS
— The Security Sleuth (@Security_Sleuth) May 22, 2017
"“Yahoobleed” flaw leaked private e-mail attachments and credentials" #informationsecurity #feedly https://t.co/KkWYTKoN69
— The Security Sleuth (@Security_Sleuth) May 22, 2017
"Spring Parade for Refreshed Android Marcher" #informationsecurity #feedly https://t.co/IQahxgESKo
— The Security Sleuth (@Security_Sleuth) May 22, 2017
"Breaking the iris scanner locking Samsung’s Galaxy S8 is laughably easy" #informationsecurity #feedly https://t.co/WgwWjiFNKL
— The Security Sleuth (@Security_Sleuth) May 23, 2017
"Beware! Subtitle Files Can Hack Your Computer While You're Enjoying Movies" #infosec #feedly https://t.co/AnLifPZF8O
— The Security Sleuth (@Security_Sleuth) May 23, 2017
"Subtitle Hack Leaves 200 Million Vulnerable to Remote Code Execution" #informationsecurity #feedly https://t.co/rw0aZuNABU
— The Security Sleuth (@Security_Sleuth) May 24, 2017
"Keybase Extension Brings End-to-End Encrypted Chat To Twitter, Reddit, GitHub" #informationsecurity #feedly https://t.co/dKHmOSdwFs
— The Security Sleuth (@Security_Sleuth) May 25, 2017
Read last weeks round up here
If you found some other interesting stuff this week feel free to leave a link to it in the comments section.
#Interview with me#Security Sleuth#Critical Samba Vulnerability#Applocker bypass#registry key manipulation#Beats and bytes#Digital Forensics#SANS#Man who tried to help wikileaks#Cameradar#RTSP surveillance Camera#Automatic shellcode transplant remote exploits#Cloud deployment#jump start application security#Camera Ballistics#whodunnit?#Classifying illegal activities#Tor#web textual contents#original post#In 2017 only losers pay for VPN's#Yahoobleed#leaked emails and credentials#Spring parade#refresher android marcher#Breaking the iris scanner#Galaxy S8#easy peasy#Subtiles hacked my PC#subtitles can hack your PC
1 note
·
View note