Don't wanna be here? Send us removal request.
Text
Elon Musk joins call for pause in creation AI ‘digital minds’
Over 1,000 AI experts, researchers, and enthusiasts have signed an open letter demanding a pause on the creation of “giant” AIs like GPT-4 for at least six months. The reason? They want to study and mitigate the capabilities and dangers of these systems. It’s like hitting the brakes on a fast car before it flies off a cliff, but with robots. Elon Musk, Emad Mostaque, Steve Wozniak, and other big AI players have added their names to the letter, and they want other researchers to follow suit. The authors cite Sam Altman, OpenAI’s co-founder, who said we might need “independent review” before creating new models. The message is clear: stop the AI arms race before it’s too late. But, if researchers won’t stop themselves, governments should step in. The authors are calling for strict regulation to prevent the creation of “ever-larger unpredictable black-box models with emergent capabilities.” In other words, they want to avoid a “Jurassic Park” situation with AIs. Nobody wants a T-Rex roaming around their office, do they? Meanwhile, OpenAI is continuing to add capabilities to GPT-4, like ordering groceries and planning holidays. But, there’s a problem: its systems are more powerful than it knows at release. It’s like buying a computer that’s too fast for you to handle, and then it takes over the world. Oops. The UK government’s response to this AI crisis has been criticised for being underpowered and taking too long to implement. Labour is unhappy, too. They say that while the government is dragging its feet, AIs like ChatGPT and Google’s Bard are becoming more common in our daily lives. It’s like they’re watching a slow-motion car crash, but without the popcorn. This post was create by https://lzomedia.com
0 notes
Text
New Linux Kernel Vulnerabilities found in Ubuntu
Ups Canonical recently released security updates for Graphviz and the Linux kernel of Ubuntu to address several vulnerabilities. #security #devops #trending #linux #kernel This post was create by https://lzomedia.com
0 notes
Text
Alibaba splits into six
Alibaba is playing a game of six degrees of separation, but instead of Kevin Bacon, it’s business groups! The Chinese e-commerce company is splitting into six groups to react faster to market changes and increase their value. Woohoo! According to a regulatory filing, Alibaba Group Holding Ltd. will now consist of the Cloud Intelligence Group, Taobao Tmall Business Group, Local Services Group, Global Digital Business Group, Cainiao Smart Logistics and Digital Media and Entertainment Group. That’s a mouthful! Each group will have its own CEO and board of directors, and they can raise outside capital and even seek their own initial public offering, except for Taobao Tmall Business Group. Sorry, Taobao, you’re stuck with Alibaba Group. The Cloud Intelligence Group includes cloud, AI and DingTalk. The Taobao Tmall Business Group includes Taobao, Tmall, Taobao Deals, Taocaicai, and 1688.com. The Local Services Group includes Amap and Ele.me. Meanwhile, the Global Digital Business Group includes Lazada, AliExpress, Trendyol, Daraz, and Alibaba.com. Lastly, the Digital Media and Entertainment Group includes Youku and Alibaba Pictures. Phew, that’s a lot to keep track of! The company’s shares jumped 8% at the opening bell, but with increased competition from short-video platforms and regulatory crackdowns, it’s been a bumpy ride for Alibaba. The company’s U.S.-listed stock has been on the decline since a regulatory crackdown on the technology industry in November 2020 that saw regulators halt the IPO of its financial arm Ant Group and crack down on anticompetitive practices. But don’t worry, Jack Ma, founder of Alibaba, has resurfaced in China after months of overseas travel. Ma founded Alibaba in the 1990s and was once China’s richest man. He has kept a low profile with few public appearances since November 2020, when he publicly criticized China’s regulators and financial systems during a speech in Shanghai. Maybe he’s been busy practicing his philanthropy skills since stepping down as Alibaba chairman in 2019. The Chinese government has been trying to raise confidence in the private sector after regulatory crackdowns on technology, education, online gaming, and financial companies, and harsh COVID-19 restrictions slowed the economy. Let’s hope this new structure helps Alibaba navigate these choppy waters! This post was create by https://lzomedia.com
0 notes
Text
Binance got sued !!!
Oh boy, the Commodity Futures Trading Commission just threw some major shade at Binance and its CEO Changpeng “CZ” Zhao. They sued them in federal court and the whole crypto world is shook.
Bitcoin and Ether took a tumble, down about 3% each. BNB, the cryptocurrency powering Binance’s BNB chain, was down even more, more than 6%. It’s like the CFTC put a hole in their ship and they’re sinking fast.
Other crypto-related stocks were also hit hard. Coinbase fell over 10% and MicroStrategy, the Bitcoin “hodling” company, was down more than 7%. Even mining companies like Marathon Digital Holdings and Riot Blockchain saw shares drop about 8%.
The CFTC is alleging that Binance “disregarded applicable federal laws” while catering to its U.S. customers. They claim Binance didn’t implement proper know-your-customer and anti-money-laundering procedures, and even helped U.S.-based customers “evade the compliance controls Binance purported to implement to prevent and detect violations of U.S. Law.” Ouch, that’s gotta hurt.
In response, CZ posted a tweet with just the number “4.” I guess he’s trying to tell us to ignore the fear, uncertainty, and doubt, but it’s hard to ignore when your ship is sinking faster than the Titanic.
This post was create by https://lzomedia.com
0 notes
Text
Using docker containers for development
Docker is a technology that allows users to bundle an application and run it within a loosely isolated environment referred to as a container. These containers are lightweight and self-contained, containing everything required to run the application without reliance on the host’s existing software. Containers can be shared effortlessly, ensuring that all recipients have access to the same working container.
Docker has become well-known for its deployment of production services such as application services and databases on enterprise servers or cloud instances. However, developers are increasingly employing containers for scenarios beyond deployment, including continuous integration, test automation, and complete software development environments, also known as development containers. These containers define a consistent environment in which an application can be developed before it is deployed.
One may question the benefits of containerizing the development environment. Have you ever found yourself cluttered with projects, libraries, languages, configurations, and tools when working on a new laptop or server? Wouldn’t it be beneficial to “restart” your software development environment to its original state?
Development containers provide a repeatable setup and consistent stateless development environment, allowing users to leave the underlying host free of project dependencies, specific language versions, and other factors. Furthermore, development containers enable users to utilize only the host machine’s computing resources. Finally, since the development environment is containerized, it can be replicated across many different systems with the Docker engine installed, ensuring a consistent development environment.
Numerous tools and services support the use of development containers, but Dockerfiles provide an option to customize your environment directly. Dockerfiles can extend images, add additional native OS packages, or make minor edits to the OS image. While many development images have been created by Microsoft available in Docker Hub, it is possible to create one from scratch.
To build a base development image, a parent image is required. The mcr.microsoft.com/vscode/devcontainers/universal image contains several runtime versions for popular languages, including Python, Node, PHP, Java, Go, C++, Ruby, and .NET Core/C#, as well as many popular tools and package managers. Using a custom Dockerfile, you can extend this image and add whatever you need.
For example, the Dockerfile shown above extends the parent image by first installing neovim and tmux to aid the development workflow. The user is then changed to codespace, and the working directory is set to the user’s home directory. Finally, configuration files for each tool are copied from the local machine.
Assuming the Dockerfile is in the same directory, the development image can be built with the following command:
$ docker build -t devcontainer .
The following command can be executed to start a development container from the newly created image:
$ docker run –privileged -it devcontainer bash
The -it flag opens an interactive container instance using bash as the Unix shell, and the –privileged flag starts the Docker container in privileged mode, granting the container root capabilities to all devices on the host system. This is beneficial when Docker is part of the development workflow. In addition, a volume can be mounted using the -v flag to persist data across different development containers, and a port can be mapped using the -p flag if developing a web application. This post was create by https://lzomedia.com
0 notes
Text
Demo Project News AI
Welcome to the official video description for Project News AI, a PHP project that revolutionizes the way we consume news! In this video, I'll be taking a closer look at Project News AI and how it works. Project News AI is an innovative news aggregator that uses artificial intelligence to curate news articles from various sources and present them in a user-friendly interface. With Project News AI, you no longer need to scour multiple news websites to get the latest updates. Our AI algorithms carefully analyze news articles from various sources and categorize them based on their topics, relevance, and importance. This ensures that you get the most relevant news articles at your fingertips. In addition, Project News AI is built on PHP, one of the most popular server-side programming languages in the world. This makes it highly scalable, efficient, and easy to maintain. Our team of experienced PHP developers has worked tirelessly to ensure that the codebase is robust, secure, and optimized for performance. Whether you're a news junkie, a journalist, or just someone who wants to stay informed, Project News AI is the perfect tool for you. With its intuitive interface, personalized recommendations, and real-time updates, you can be sure that you're always up-to-date with the latest news. So why wait? Try Project News AI today and experience the future of news aggregation! https://www.youtube.com/watch?v=OOLcYr0YSd0 Project is open source and can be found at https://github.com/Cornatul/news.ai created by @Cornatul on 2023-03-27 13:22:28 https://lzomedia.com #developers #opensource #laravel #php #social #medium #twitter #github
0 notes
Text
How to Unsend Email on Mail for iPhone & iPad


We’ve all been there, typing out an email quickly and hitting send, before immediately realizing there’s a typo, or a mistake, a forgotten attachment, or perhaps some choice words that you immediately regret sending. Fortunately the Mail app on iPhone and iPad offers forgiveness in the form of the Undo Send email feature, allowing you to instantly retract an email and unsend it, if you act quickly enough anyway.
The unsend email feature on Mail for iPhone and iPad is really handy and you’ll probably want to know how to use it ahead of time before you find yourself needing to in a pinch, so launch that Mail app and give this one a go, putting it into your workflow memory for use later when needed.
How to Undo Send on Mail for iPhone & iPad to Unsend an Email
The Undo Send feature is available on Mail for iPhone and iPad, as long as the device is running iOS 16 or newer. Here’s how it works:
From the Mail app, compose and send any email as usual (try it out yourself by sending us an email if you’d like; [email protected])

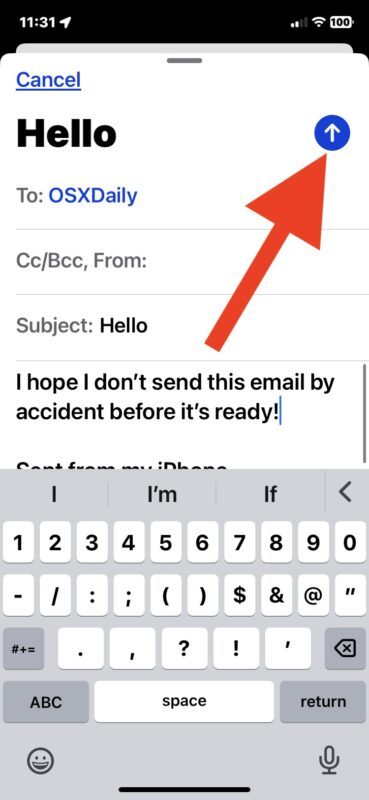
Immediately look to the bottom of the screen and tap on “Undo Send” to unsend the email

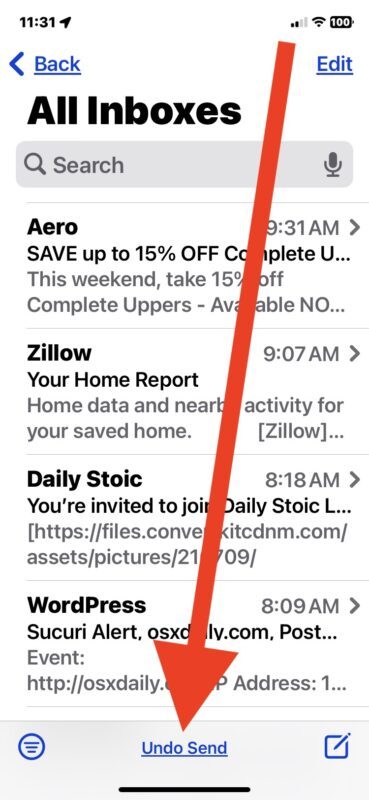
You have to act quickly, because the ability to unsend an email does not last long.
Don’t forget that you can change the delay available for using Undo Send on iPhone or iPad if you wish to have more time, or less time, to recall an email.
Note that if you have the Unread Email filter toggle enabled, you will not see the “Undo Send” option at the bottom of the Mail app screen, but you can quickly toggle that off to reveal Undo Send in the iOS and iPadOS Mail app.
How does Unsending Email work in Mail for iPhone and iPad?
It’s important to acknowledge how the Undo Send feature works on iPhone and iPad, which is to introduce a sending delay.
The feature is not like the Unsend Message feature in iMessage, as it does not recall or retract an email message from the recipients inbox, which is not technically possible with the email protocol.
Instead, it basically adds a time delay for the period between sending an email and when it actually gets sent, and that grace period is the time where you can tap on Undo Send to unsend the email message.
That grace period is also what you can adjust the time of if you want to extend or shorten the duration of the Undo Send feature availability.
This feature is also available on the Mac Mail app if you send emails from there too.
Do you use the unsend email feature on iPhone or iPad? What do you think of this capability?
created by @Cornatul on 2023-03-27 12:43:30 using LzoMedia #developer #laravel
0 notes
Text
Botnet that knows your name and quotes your email is back with new tricks

Widely regarded as one of the Internet’s top threats, the Emotet botnet has returned after a months-long hiatus—and it has some new tricks.
Last week, Emotet appeared for the first time this year after a four-month hiatus. It returned with its trademark activity—a wave of malicious spam messages that appear to come from a known contact, address the recipient by name, and seem to be replying to an existing email thread. When Emotet has returned from previous breaks, it has brought new techniques designed to evade endpoint security products and to trick users into clicking on links or enabling dangerous macros in attached Microsoft Office documents. Last week’s resumption of activity was no different.
A malicious email sent last Tuesday, for instance, attached a Word document that had a massive amount of extraneous data added to the end. As a result, the file was more than 500MB in size, big enough to prevent some security products from being able to scan the contents. This technique, known as binary padding or file pumping, works by adding zeros to the end of the document. In the event someone is tricked into enabling the macro, the malicious Windows DLL file that’s delivered is also pumped, causing it to mushroom from 616kB to 548.1MB, researchers from security firm Trend Micro said on Monday.
Another evasion trick spotted in the attached document: excerpts from the Herman Melville classic novel Moby Dick, which appear in a white font over a white page so the text isn’t readable. Some security products automatically flag Microsoft Office files containing just a macro and an image. The invisible text is designed to evade such software while not arousing the suspicion of the target.
When opened, the Word documents present a graphic that says the content can’t be accessed unless the user clicks the “enable content” button. Last year, Microsoft began disabling macros downloaded from the Internet by default.
Advertisement
Clicking the "enable content" button undoes that default and allows the macro to run. The macro causes Office to download a .zip file from a legitimate website that has been hacked. Office will then unzip the archive file and execute the inflated Emotet DLL that infects the device.
Once it has infected a victim’s device, the malware pilfers passwords and other sensitive data and uses the device to send malicious spam to other users. The malware can also download additional malware such as the Ryuk ransomware or the TrickBot malware. The infection chain looks like this:
The attention to detail seen in this latest revival is signature Emotet behavior. For years, the botnet has painstakingly copied received email conversations from infected machines and embedded them into malicious spam sent to other parties in the thread. By following up on an email from someone the target has communicated with in the past, the malicious spam message stands a better chance of going undetected. Emotet can also gain access to Wi-Fi networks and infect connected devices.
With the return of Emotet, people should be on the lookout for malicious emails, even if they appear to come from trusted sources, call the target by name, and include previously sent and received emails. There is rarely a good reason for enabling macros in documents sent by email. People should refuse to allow them to run without first communicating with the sender by phone, instant message, or another non-email medium.
Countries hit the hardest in the latest Emotet run are European, Asian Pacific, and Latin American.
0 notes