Ruling the world. A very diverse and darling group... Twitter: @TheCouncilOf9 | Contact: [email protected]
Don't wanna be here? Send us removal request.
Text
What Makes a Good Puzzle Solving Team
By Mystic of Co9 I have been working with The Council of Nine to solve puzzles since 2012. Our team is made mainly of people who met entirely through attempting (and failing) to solve the Defcon 20 Badge Challenge. Through the years we've continued to work together, eventually earning two black badges for being the first to solve DC23 and DC24. We have learned a lot about puzzle solving through this experience, but we've also learned a lot about working as a team. My intention with this post is to share a bit of this wisdom. I will start by dispelling some common misconceptions and then present what I think might actually make a good puzzle solving team.
Misconceptions
1. Tools: Great teams have some kind of magic tool that solves everything. Tools help, but a good puzzle will be resistant to advanced tools and/or require only the most basic of tools to solve. Every Defcon badge puzzle that I've worked on could have been solved with nothing more than pencil, paper, and google. Occam's Razor is always your friend. Forgetting that can lead you down some interesting rabbit holes (See the CryptoK Cipher: https://twitter.com/0xCryptoK/status/1292316580957700096). 2. Genius: There's one uber solver on the team that does all the work. You may in fact have some real smart people on the team, but beware that solving puzzles isn't something you can master like programming or music. Even if you have someone who is a master cryptographer on your team that person isn't going to just know that, for example, the drum beat in the background of the audio is morse code. That takes more than technical skill to solve. That master cryptographer on your team is very useful for running cipher text though obvious solutions (like Caesar or basic transposition) but don't assume that they are going to be able to throw intellect at every problem while everyone else sits back and enjoys the show. 3. Team Size: Having 30 people on your team means you are 30X more likely to solve. It's more about how you organize your team than how many people are on it. The last thing you want is lots of people generating lots of noise. If you can pull off a 30 person team, more power to you, but you'll find that most large teams only have a small number of people actively working on a puzzle at a time. You'll also find that smaller teams tend to be way more organized, which is critical if you want to succeed. With good organization you could have a bad ass team with only 3 people. For more on how to organize your team see the suggested team roles later in this post. 4. Deception and Social Engineering: The best teams social engineer their way to the solution and play dirty. We use every tool available to us and social engineering and deception are part of the game, however it is rare that teams succeed on this alone. Information gained through social engineering, in my experience, can certainly give you an edge, but only a small one. Your team has to combine this with your own unique solves. The reality is that if your team is good you'll be so far ahead at points that social engineering is useless. Let me also give you a word of warning: beware of social engineers who want to join your team. They might at some point use their skills against you. I'm sure every good team has a story about this to tell over some beers.
What Actually Makes a Good Team?
1. Variety of skills: Hardware, coding, music, languages, pop culture, and classic/modern cryptography are all valuable skills to have represented on your team. Don't worry too much about finding geniuses. A lot of our solves came from people who were simply willing to try something no one else thought of yet. That comes out of having people with a variety of perspectives and knowledge bases. 2. Team Players: People on the team should want to be on a team. They need to be willing to be a part of something greater than themselves. If you want individual glory, then maybe you shouldn't be on a team. It sounds harsh, but if you join a team you are part of that team. Even if you didn't have any solves yourself or you ended up solving a ton of the puzzles, it's the team that succeeds or fails, not you personally. There will be arguments, there will be frustrations. Deal with this as a team. Strong egos and chasing individual glory can be toxic to a team at its core. Don't let it fester too long. 3. Clearly Defined Roles: Especially for larger teams you'll want to decide on some roles. We would suggest having at least these three: Front line: People who take all the puzzles and start trying everything to solve them right away. They are gathering all the clues, running them through tools, trying different analysis methods, etc.. Middle line: There people are taking everything the front line folks are doing and verifying it. If the front line says for example, "the cipher text is 40 characters and here is the hex and binary of it, I tried all ROTs, nothing" then the middle line does all of that again to make sure there weren't any mistakes or anything missed. They are also looking for missed correlations. For example, they might say "oh the text on the badge is also 40 characters, I'll try OTP with all of them". Documentation: These people are taking anything that seems like a solution or a clue and documenting it. This can be done in a google doc, a flow chart, markdown in github, etc.. For larger teams, it can be a good idea to split this role so one person is documenting and the other is communicating when the docs are updated with new information. This helps a lot in moments where everyone is stuck. Did we miss a clue? Is there something we still haven't solved? Is there a keyword we haven't used? The documentation should be able to answer all these questions. 4. Year Around Communication: Don't be a "see you next year" team. Keep up communication year around. Try solving puzzles outside of your main focus. Not everyone on the team will be able or willing to do this, but some will. The more you work together the better you are going to get at it. Also, Don't take for granted the fact that your team is full of smart people who share a common interest. I've gotten to know people through Co9 that helped me to improve my skills in a lot of areas beyond puzzle solving. In the end, isn't the real solve all the friends you made along the way? I hope this post helped to dispel some myths about puzzle solving teams. I also hope this inspires others to start new teams or improve their own. A lot of the members of Co9 genuinely enjoy helping others with this stuff. Don't hesitate to reach out. We know this is a competition, but we love solving puzzles and meeting others who share this pretty niche passion. Defcon tends to give out only one black badge to the winners of the badge challenge (if at all). We don’t do it for the badge (although when we do get a black badge we make more [links to badge copy posts]). We do it for the challenge. I think this embodies the hacker ethos in a pure way. Let others take the spotlight, the sponsorships, the glamorous parties, and the fancy job offers. Who has time for that? We're here in this hotel room solving.
2 notes
·
View notes
Text
DEFCON 28 Badge Challenge
If you are still working on the Badge challenge, be warned! Spoilers below!
If you’d like to play along, you can grab all of the required materials for free at:
https://media.defcon.org/DEF%20CON%2028/DEF%20CON%20Safe%20Mode%20Badge.rar

Exposition:
Before getting into the badge challenge write-up, we would first like to take a moment to thank all those who helped make this possible. First and foremost, a big shout out to 1o57 for putting together these amazing puzzles every year, and the sacrifices required to make it happen. Also a big thanks to the DEFCON organizers as a whole, who allow people like us to engage in these puzzle-solving shenanigans, and giving 1o57 a place to create and foster the hacker mindset.
Finally, a big thank you and congratulations goes out to Co9’s newest members, and four complete DEFCON newbies (congrats on your first con!):
Cr0wn_Gh0ul (@Cr0wn_Gh0ul)
JTobCat (@jtobcat)
LeFevre (@Lefevre)
motive (@leemsparks)
With that, let’s get into it.
The DEFCON 28 Badge
The Council of 9, undaunted by the irregular startup routine of DEFCON Safe Mode, prepared to scuffle and rumpus against the bewildering puzzles of 1o57 once again. After purchasing our DC28 badges, the fun began.
As 1o57 puzzles go, you never have an official starting place. You have to find it. So as we found answers or interesting information, we would record it for possible future use, and move on to the next thing we could find. Eventually, the breadcrumbs resolve into a path to follow.
This years badge consisted of three physical items:
A traditional printed cassette tape insert booklet
An old school audio cassette tape
The Lanyard
Booklet
The cassette tape insert booklet had several codes printed across it.
First, looking at the track listing:

Taking the first letter of each song on the side A tracklist spells out “LOSTINTIME”. For the uninitiated, 1o57 is the longtime Defcon badge designer and puzzlemaster. These track names also contain hints for later - Keywords like Lissajous.
Color Block Sub Cipher

Written, the color boxes read
Orange White Pink
Purple White/Green Orange/Green
Blue/Green Green Pink White
Purple/Green White/Green Orange White
and
Orange Blue Yellow/Yellow Green/White Purple
Green/White Green/White Yellow
By substituting the letters directly below for colors the first image, decodes to DEF CON SAFE MODE. It's basically a key.

So the second is

Skull Text

This string of text wasn’t nearly as simple to decipher. This skull artwork was a throwback to DC21, which had us scurrying to find notes and write-ups on the Badge puzzles from that year. Ultimately, however, we found the solution by taking the text string and pasting it into a 6x6 route transposition cipher, yielding:
tIstFCOnRFoofFioumYrgureoohrDOuntlon

Which is read Come on four dot four is right in front of you
We didn’t yet know what to do with this, so we put it aside for later.
Cipher Text Page

Xbaw maek wzme pgty zvxy izwk iwhk lnhy
agrl rrlp fsis xadh uflx dsqh rzrg qegu
itwb wveq aslo moii xmzx mvea rtil yekd
lvks jrbo arvy nmjz wodi gcxe tkrr cyir
xbsu rwyf slwr ixyk lrwz sbzr zbpg rrrw
hjsi alXX 1o57
The solution to this text really came from the fact that we were paying attention to 1o57 dropping random hints in various locations - not from anything in the booklet itself. 1o57 had played a video on his Twitch channel from The Adventures of Buckaroo Banzai Across the Eighth Dimension. Most notably, Buckaroo is famous for using the phrase: “No matter where you go there you are”
Using this as an OTP key...
nomatterwhereyougothereyouarenomatterwhereyougothereyouarenomatterwhereyougothereyouarenomatterwhereyougothereyouarenomatterwhereyougothereyouarenomatterwhereyougothere
...you get another Buckaroo quote (actually written by Greek philosopher Odysseas Elytis) :
Know that as in life there is much that many have looked up on but few have seen because as my father told me and his father told him you will come to learn a great deal if you study the insignificant in depth
Cassette Tape
With the booklet sorted, we turned our attention to the DC28 cassette tape. Upon listening to the tape, there are some immediate … features… that stick out.
Tones

One of the first things anyone listening to the tape will notice is the odd tones that sound at different times, and seem to repeat. These were halves of a DTMF (Dual-tone Multi-Frequency) tone, known better by many as “touchtones”, and appeared in two (2) groups of fourteen (14) tones that repeated three (3) times. By combining these single frequency pairs back together, we restored the dual frequencies and, by examining the peak frequency of the tones, we were able to identify the keypresses that generated the given tones. The flow of tones came out as:

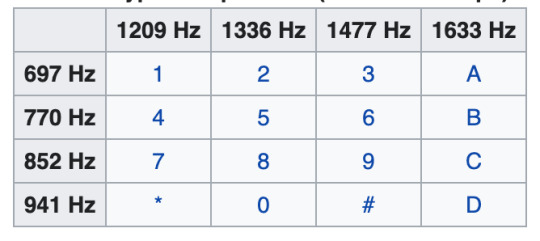
DTMF Numbers: 2 6 3 3 9 6 7 3 7 9 9 9 4 9
We’re not done yet, though! Not yielding any immediate plaintext, we continued checking for a second-stage decipherment. As we’ve learned from other puzzles, any phone-related cipher should be checked for T9 coding, which turned out to be exactly what we have here.
By looking at a phone keypad,
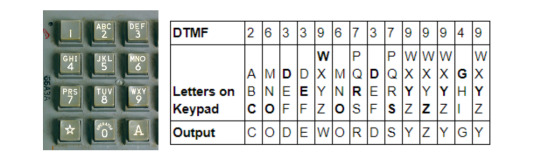
Reading those indices onto the available letters, we get: CODEWORDSYZYGY
Oscilloscope
It’s not just the obvious side of the audio that we need to examine - the audio on the cassettes had much more than meets the … ears. Based on some hints that 1o57 dropped, and our experience with past puzzles, we decided to examine the audio for any hidden waveforms or other hidden data. Using a software oscilloscope, we examined the tape audio and discovered plenty of hidden text, as well as Lissajous patterns (remember that word from the Tracklist? Ya, that was the hint to get us here). The patterns we saw included a spaceship, a heptagon, a butterfly, and some very interesting text. The text we needed was:


The full text that shows up in the oscilloscope reads:
FIND A KEY AT LOSTBOY.NET SLASH PALEBLUEDOT
These two lead us to http://lostboy.net/PaleBlueDot
When we found this, though, the site was not yet active (since DEFCON hadn’t officially started). Oh well, better solve the Lanyard while we wait.
The Lanyard
This year’s lanyard proved to be quite tricky. We went through several iterations of attempts to make sense out of it. Pictured below is the lanyard with our attempts at dividing up and delineating each shape.

1o57 offered quite a few hints about the symbols on the lanyard - and with good reason. Finding the appropriate reading for the text was pretty difficult. Here are some of the most important hints that came out:
...now excuse me while I go read more about French aristocrats fleeing a post 1789 revolution.
More hints will start flowing from the font of knowledge tomorrow after DEFCON officially starts....
These sorts of hints eventually point towards the Crackly font, hosted on emigre.com (https://www.emigre.com/PDF/Crackly.pdf). Using this font, we were able to extract the following values from the lanyard segments:

Note first those mad MSPaint skills. Note second that all of those numbers are below 26, we immediately changed them into letters, giving us:
Q X U N
E K K E
V I O Q
Q G C O
Throwing this through a ROT, because you should always ROT everything, discovered that it was ROT-24’d. (Side note: Why ROT-24? Because ROT-24 is a negative ROT-28. Tricksy)
O V S L
C I I C
T G M O
O E A M
While not immediately obvious, one observant council member noted the presence of the C-O-M series of letters when reading in the vertical 4x4 pattern. Reading it in this way gave us what we were after:
OCTOVIGESIMALCOM → http://octovigesimal.com
Octovigesimal.com
This new page contained quite a bit of new content that we needed to sort through, and any answers were certainly not obvious.



Image filename: besidenequals2.jpg
The summation equation written at the bottom of the Goonies skull key implied that we need something that follows the pattern 1.1 + 2.2 + 3.3 + 4.4. The banner of the website implies that we need to look at the album “The Great 28” by Chuck Berry. This is further hinted at by the text “Record your answer~”, as in a record. We even think the tilde, from the latin for ‘title’ was probably part of the hint.

Upon looking at the Track list of “The Great 28” we saw that there is a track called Come On, which is right before a track called “Nadine (Is it You)”. This seems to link back to the text that we extract from the cipher text on the cassette tape insert “Come On Four Dot Four is right in front of you” Come On happens to be Section 4 track 4 of the album (4.4) and is “right in front of” (before) “Is it You”.
Going with that train of thought, and concatenating the titles of tracks 1.1, 2.2, 3.3, and 4.4:
Chuck Berry - The Great 28:
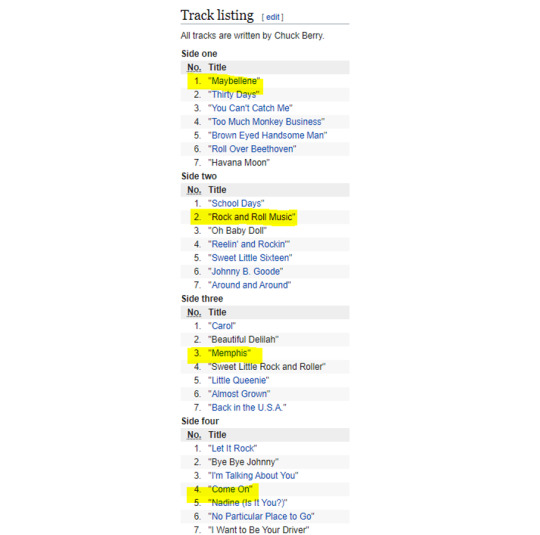
we get: MaybelleneRockandRollMusicMemphisComeOn
However, we don’t know what to do with this yet. Note it and move on.
Last on this site, but certainly not least, is another URL. Hidden right in plain sight underneath the logo is a pointer to the URL “Base-28.com”.

Alright, time to move on.
base-28.com

The first thing to look at here is the ciphertext in the top center of the page. We have a few strings to play with from previous solves. With the earth, moon and sun being in a line on the page, we figured it was a good opportunity to try the key that we found previously (from the audio DTMF codes): SYZYGY. This ciphertext is Vigenere encoded with SYZYGY as the key, and decodes to Who are you going to call? Definitely sounds like Ghostbusters to us.
Also of note here, is that the image on the arcade cabinet was identified as being the Temple of Gozer - a Ghostbusters scene. This scene is actually Chapter 28 on the GhostBusters DVD, and is titled “Crossing Streams”. This reinforces the Ghostbusters clue that the vigenere text gives us, and will prove critical to the next step.
On either side of the website we see pictures of members of the band The Commodores. 64 of them, in fact. These two clues combined tell us that we need to look at the Ghostbusters Commodore 64 game. What specifically about it? We don’t know yet.
Visually, it looks like this...

Pale Blue Dot
The Lissajous from the audio on the cassette tape pointed us to lostboy.net/PaleBlueDot. Upon accessing this page, we were greeted with… a wall of numbers. A giant freaking wall of numbers. Oh, and a joke.
How many Sagans does it take to change a lightbulb?

A quick google search will reveal the hilarious answer: “Billions and billions”
How it’s supposed to be solved
The numbers in the image are divided by the decimal, with a number of seemingly arbitrary length on the left, and eight (8) digits to the right of the decimal.
Left-Hand Numbers
Noticing that the numbers, with appending a few leading 0s, can be paired into values all less than 26.
Separating them out, and converting them via Letter-Numbers
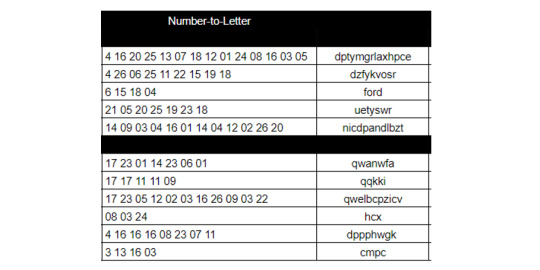
Then, Vigenere decode using the key “billionsandbillions” (from the Sagan riddle) to get the plaintext:
ChineseTakeout
CrunchBar
Eggs
Twinkie
Marshmallows
Popcorn
Pizza
PotatoChips
Gum
Cheezits
Beer
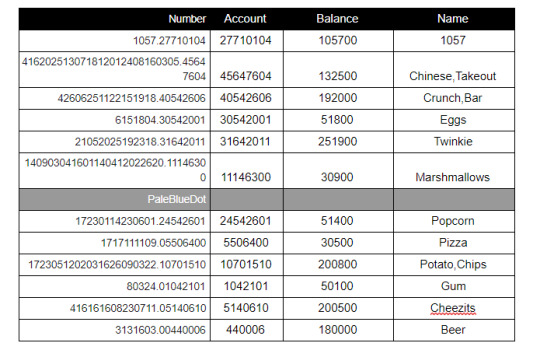
These resulting words are the Game Franchise Username for the Ghostbusters c64 game, save bankroll amount. This consists of the Username (left side decoded) + 8 digit account number (right side number), with the decimal separating the two.
Right-Hand Numbers
The numbers on the right of the decimal, being 8 digits, are the account numbers for the Ghostbusters game. These can be plugged into the game (via an emulator) to discover the corresponding amount of money that is ‘saved’.
Emulator Franchise Username and account number screen:
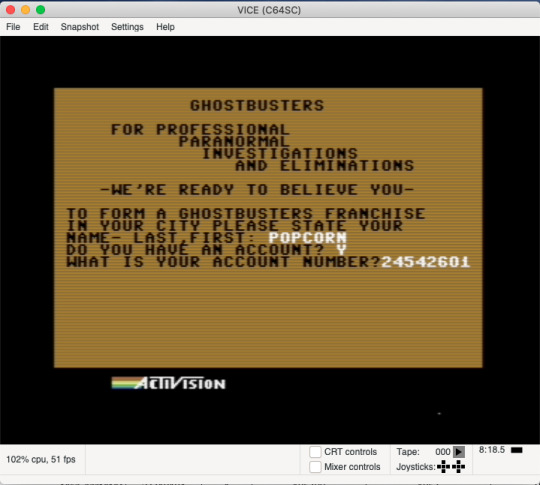
Account Amount after validation of Username screen:
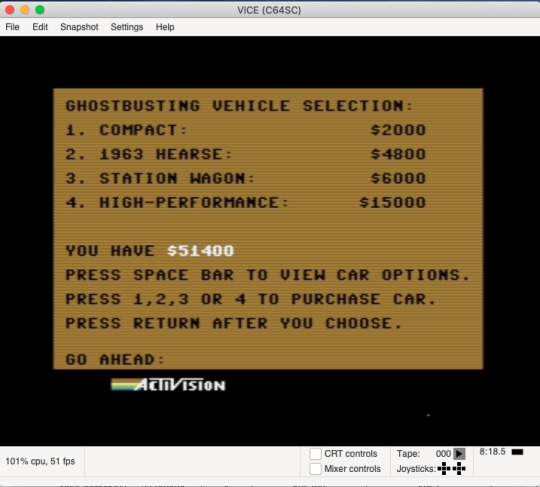

The Final Step
Realizing that these account balances all have trailing ‘00’s, remove the 0’s and convert the remaining numbers into letters to reveal the next destination.
Numbers: 13 25 19 20 5 18 25 19 3 9 5 14 3 5 20 8 5 1 20 5 18
Letters: M Y S T E R Y S C I E N C E T H E A T E R
Also, noting that each segment in the graphic is separated by the text ‘PaleBlueDot’, place a dot between the words, to arrive at a web address.
https://mysteryscience.theater
How we actually solved it (the narrative of pain)
One of our immediate observations was that the numbers always had eight digits on the right of the decimal. From the base-28.com site we knew about the c64 Ghostbusters game, and had the Crossing Streams chapter title as a potential hint that we needed to use clues across websites. In our reading about the c64 game, we learned that it was one of the first that allowed players to ‘save’ their game. Researching how this ‘save’ feature worked, we noted that it always used 8-digit account numbers, which curiously lined up with our 8-digit numbers to the right of the decimal. This felt like a crazy idea at the time, but we were frustrated enough to try it. Given the account numbers, we needed to find a way to reverse out the Names and Balances that would give those account numbers.
This video explains how the ‘save’ feature works: https://www.youtube.com/watch?v=_3cpbCCfK5A
Rather than digging into the algorithm, like we should have done, we discovered a Chrome extension that generated Ghostbusters accounts.

We tempted fate and downloaded the extension, only to rip out the code in order to reverse the algorithm. With that, we wrote the below brute forcer which, after inputting a Name, would try all possible account balances and then check if any of the resulting account numbers matched any of the account numbers from the image.

We immediately set out trying names that came from 1o57’s Twitch streams or other areas of the puzzle so far - and we found a few that worked:
'REAGAN,RONALD',
'POLLY,SKATING'
'SOTER,STEVEN',
'MORANIS, RICK',
'BROLIN,JOSH',
'HOUSE,BRICK'
But note that we said ‘a few’. We couldn’t find hits for every account balance. Fortunately, these were enough to assure us that we weren’t crazy, and we began attempting to interpret our output. While working through this, we realized that we didn’t even need the names. Using the information from the aforementioned YouTube video, we learned how to derive the information we needed. Take the account number for 1o57 which is 27710104. Reverse the number by pairs to get 04017127. Then convert from octal to hex, you get 101E57. The middle byte, 1E, is the hash of the name. The account balance is the first and third byte, so 1057. We filled in the remaining few accounts to come up with a full dataset. As it turns out, the whole page could have been solved like this on a calculator.
Examining the resulting balances, and knowing that the game’s algorithm divided the balance by 100, we dropped the trailing ‘00’ and then converted the remaining numbers into letters, revealing the string mysterysciencetheater. After trying this on a few of the known sites with no luck, we discovered that this was pointing us to mysteryscience.theater The PaleBlueDot in the middle of the numbers was also a hint to look for a domain.
While we had discovered some new information, it was not a complete solution. We still hadn’t used the left-hand side numbers from the PBD image, so we now shifted our focus to those numbers. After realizing that the numbers seemed to be relatively low when split into their component digits, we tried Letter-Number conversion again. We then Vigenere’d that output with the riddle answer ‘billionsandbillions’, and came up with a list of delicious food from the Ghostbusters movie. As it turns out, these were the names we were supposed to use to get the balances via a Ghostbusters c64 emulator. oops.
The complete output was:
Mysteryscience.theater
This page was kind of interesting in that there wasn’t really much to do with it… at least not immediately. From time to time, 1o57 will time-gate an area of his puzzles, and this is exactly what we ran into here. So, fast forwarding something like 24 hours, let’s begin examining the final puzzle-filled state of the page.
The top of the page now contained ciphertext. After a few attempts at deciphering it, we tried one of our old unused pieces of data (the concatenated list of Chuck Berry song titles) as a key and were greeted with a successful decipherment:
An y QewpFyyvRqd,
WehjhwpIclpVtme:
Ioqfig oloage.
Using OTP key: MaybelleneRockandRollMusicMemphisComeOn
On a PaleBlueDot,
WrestleWithThis:
Things change.
The meaning from this was clear! Head on over to http://lostboy.net/PaleBlueDot/WrestleWithThis
WrestleWithThis

Not much to see on this page, just the text “It’s only a tiny problem” and a YouTube video.
In the page source was the following comment:
<!- bFNhZ2FuQExv ->
And the title of the page was:
Wrestle With This y6nk3z9y
The comment Base64 decodes to lSagan@Lo
Additionally, the hint on the page about a ‘tiny’ problem, combined with the page title, resulted in a tinyurl link for our next destination:
tinyurl.com/y6nk3z9y → http://lostboy.net/PaleBlueDot/EverythingWasFineWithOurSystem.jpg
EverythingWasFineWithOurSystem

The image on this page immediately presents us with two sets of ciphertext, and a curious little man yelling at us from the corner.
As seen lightly overlaid into the blue of the car:
U2VuZCBDb3Nt =base64=> Send Cosm
And in the rear light:
TG9zdGJvWSBkb3Qgc2xhc2ggSEhI =base64=> LostboY dot slash HHH
Navigating to http://lostboy.net/HHH, we were greeted with two more youtube videos. The first one was titled “Close but no Cigar”. Immediately realizing that this meant we hadn’t interpreted the clue correctly, we Nope’d right the heck out of there. Luckily, we also knew what HHH was referencing from watching 1o57’s Twitch stream on 8/7. so we wasted no time in discovering the correct endpoint.
lostboy.net/HappyHarryHardOn
Here we go, a YouTube video and some encoded text. This feels right. The video was of RayParker Jr. performing the GhostBusters theme song, and below it was the text “What a singer! LostboY.net/PaleBlueDot/?” Also on the page was the text “F1LZuQ9E4JQ”.

The F1… text was another YouTube video; Chuck Berry and Tina Turner performing Rock n Roll Music. In an interesting twist, we discovered that by sorting the video comments by Newest first, there was a comment from NEW SOUND AGENCY with the text “b3MgdG8gQ2Fy”.
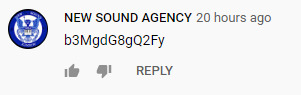
Also, if we look at the NEW SOUND AGENCY channel on YouTube, it has just one video of 1o57 playing around with a MiniMoog. Yep, this is a clue. This text of the comment base64 decodes to “os to Car”....hmmm.. That seems to fit with the other ciphertext we’ve found so far.
As for the URL, the team immediately recalled that Ray Parker Jr. may have, probably, almost certainly, likely, stolen the Ghost Busters theme music from Huey Lewis and the News’ “I Want A New Drug”. The next URL, then, was pretty simple to guess:
http://lostboy.net/PaleBlueDot/HueyLewis/
HueyLewis (and the Solve)
This page was pretty simple. A single ciphertext was present on the image and gave us the following:
c3Rib1kubmV0 =base64=> stboY.net

And finally, putting together all of the fragments that had been discovered:
U2VuZCBDb3Ntb3MgdG8gQ2FybFNhZ2FuQExvc3Rib1kubmV0
Base64 decodes to => Send Cosmos to [email protected]
We shot off an e-mail (several e-mails?) as directed, and got replies letting us know that Defcon 28 Badge Challenge: Complete … phew. The e-mail also linked to another video and requested that we watch it as a team.
We immediately shared a screen as a team and viewed the video together.
With that, DC28 badge challenge was complete.
@TheCouncilOf9
Co9.io
0 notes
Text
DEFCON 23 UBER Badge Replica
write-up by junkmail(co9). replica by wumpus(co9) and junkmail(co9)
Four years ago I met a group of randoms at DEFCON 21. I had heard that the Badge had a competition and started puzzling it out. My small group grew larger as people saw what we were doing. 72 intense hours later, we finished - Second place - not bad for n00bs. Defeated but resolute we formed the Council of Nine with intent to compete again - and win. After our second defeat we repeated the resolution and Lo! DC23 was our first victory.
There is always interesting math of how many badges are awarded for any particular Defcon contest - Most have a single Uber badge granted and others receive one per team member. At DC23 we received a single Uber for winning the Badge Challenge. The DC23 badge is an awesome tribute to Richard Feynman and includes captured lightning, several radioactive isotopes and a kickass crypto coin with brilliant artwork. Immediately discussions began - can we counterfeit this Work of Art?
Yes. Yes we can.
We had one official badge awarded for winning DC23. The DC staff forces that badge to be assigned to a self-dox'd individual (as in Give us your Name, alias, and signature in a little black book or you get nada! Boo!) After all that, our designated owner was (quite reasonably) reluctant to physically ship it about. Instead he took a bunch of measurements and photos, and I worked from them.
Our total project time spanned over about 6 months, most of which consisted of research and awaiting order fulfillment. But we feel the results were -up on his making of the Uber, complete with its rich history and tribute to physicist Richard Feynman. As descriptive material, he noted the many radioactive components, the sculptural Lichtenberg figures and the crypto coin.
Lightning the Load
One of our team (let's call him wumpus) researched the Lichtenberg and found one single source! Easy right? Not so much. The creator alluded he was retiring and would no longer be producing these amazing figures. As we didn't have a 5 million volt, 150 kW particle accelerator readily at our disposal, we figured we were out of luck... or were we?
wumpus contacted the creator and brilliantly convinced him to come out of retirement one last time to make our sculptures!* He provided the specifications and quantity, and we were set for November delivery.
The limiting item was the Lichtenberg figure, without which there would be no replica. And with the Lichtenberg figures on order for a November creation, we moved our attention to the more attainable items.
Go 'Topes!
Armed with a list of specific materials our other builder junkmail (hey thats me!) started to dig. I found research sites that allowed for scientific samples of radioactive material to be sold in the US. These sites united our efforts to obtain nuclear samples of:
Trinitite Fragments
3% Uranium Marbles
Europium powder
Uranium Ore
Torbernite
Uraninite
Pitchblende
Carnotite
Gummite
YellowCake
Tritium Vials
Europium powder is cool. It glows like nothing else - really brightly - especially when you hit it with Ultraviolet light to charge it.
The remaining components are rocks, dust and sand. These ores and samples are placed under each of the two skulls as indicated.
We're not going to go into detail on where these materials could be purchased exactly, but with a united effort and research university credentials, you might locate the nuclear materials. Or not.
Uranium Glass was actually pretty common until the 1940s. It was used for a long time in glassware until people started watching Godzilla movies. Nah - it was WWII and availability of U that reduced its use on plates used for food). I ordered the Uranium marble from our supplier. I admit I did panic a bit on opening the package: Clear marbles were shipped! They were the correct size, but not matching the need. After a few emails, and my insistence that the supplier's website image still showed the 5/8" pink variety, he dug through his old stock supply and made the exchange.
The Skulls were found with google fu, notably appending "-Indiana" to every search. In the end we determined that Swarovski (oooh fancy!) crystal skulls were exact matches. There remained a question to their patina - some online images of the Uber showed a prismatic effect, while others showed clear. It appears that different skull hues were used among the final badges. The prismatic effect in sample skull I got seemed to be far too strong compared to the comparison images, so after some debate we opted for clear skulls on both left and right sides.
Inside the left skull is a Tritium Vial. This vial is the type used for watches, gun sights and exit signs to glow for years of its own nuclear decay. It was pretty straightforward locating the T1-sized vials. T1 vials fit into the left skull bore. The vials were selected to match the color (light blue) and sized to fit in to the Crystal Skull. Did I mention the skulls are actually jewelry beads? So there was already a small hole available for the vial.
A Challenging Coin
And finally the most time consuming part - the Challenge Coin. I had never duplicated (or made) a challenge coin before, so I had no reference how long or how much effort this would entail. Originally I had considered a laser etched version and a 3D printed but after some tests realized that the laser etching a black at depth would be time consuming if even possible, and using my 3D printer just couldn't provide the resolution, especially in the finer Korean characters and intricacies in the central pyramid.
I started the duplication with the artwork. Having little experience and an Adobe creative cloud account, I learned to use Illustrator. Now Illustrator has an auto-trace function available and despite my modern and surprisingly affordable sculpture being crushed on the Hydraulic Press Channel (yes other Co9 members - I just plugged myself), I am no fine artist. So autotrace sounded perfect right?! I loaded one of our better images, sat back and waited for the file to be ready for the vendor.... So yeah - it's not that easy. The auto object was about a billion polygons, and far too heavy to open, let alone edit down for use. In the end I took another approach and searched for clip art.
The main Pyramid is quite similar to the Illuminati all-seeing eye on a dollar bill and there are many many renditions online. Fortunately Adobe provided the material needed. The Korean characters, UBER block letters front crypto text and some clip art edits were all hand drawn, removed or traced manually to match the images. Remember kids - if you are copying a coin, make sure the original picture is proportionally correct! It took a little while to realize that the coin in my image should be circular... (First you do, then you do over!) The artwork took a long time primarily due to my inexperience with illustrator.
The reverse side (coins have obverses and reverses, not fronts and backs, though heads and tails will do...) was more challenging. Even with an original in our remote possession, the coin details were not clear through the 1/2" thick acrylic Lichtenberg. Luckily, 1057 had distributed a few loose coins to friends -- a result of having both deserving recipients and minimum quantity coin orders. This image shows a Vulcan Live Long and Prosper hand sign as a posthumous tribute to Leonard Nimoy, a stylish skull, cryptotext (which we had not yet deciphered), and 1o57s signature. I followed a similar route as the obverse and manually recreated all the components as I could not locate any clip art.
Now with the file and Occam's razor in hand, I used the simplest method for creation: Outsourcing. There are too many challenge coin vendors out there to be sure but I suspect many just send them overseas for production which was the case from our nearly random selection. Showing the purchase agent my design and images of the coin, I had to explain that this was a copy, not the original because, uhh, we had, umm, lost the file. She could not see any difference. Encouraged the order was placed.
There appears to be a minimum line thickness possible with stamping coin. In a few cases I was below that minimum though it is hard to detect unless you are looking.
I received the coins a few weeks later and I was stunned. They looked Amazing. I put one on my pocket and it has been there ever since :-)
The Build
Parts started arriving in early 2016. It was February before everything was in hand but I was still missing something... glue! What adhesive was used? it was not totally clear, but close. At first, cyanoacrylate (superglue) was considered, but this tends to off-gas and leave a whitish vapor residue. Epoxies and other glues were considered but none dried optically clear until I came upon GS Hype jewelry cement. It is made specifically for attaching glass beads to jewelry and stay clear. Importantly it also works well on plastics and glass. And that it could hold diamonds and emeralds to those Fabergé eggs was good enough for me. Amazon for $6.
Now the easy parts: Measure and drill some holes (standard 3/4" drill bit), apply thin glue, drop in ores, more glue, and a skull on top. Slip in the tritium vial and cap with more glue. Wait until dry. I followed the same procedure for both skulls and the Uranium+Europium marble combo at the bottom. Also, Europium gets into everything. That tablecloth still glows after I turn off the lights.
The final two steps were gluing the Challenge coins centrally, and adding the hook/lanyard, both of which I got at a local HD. Not perfect matches, but pretty close. I had to rework the hooks in to a more 'diamond' shape and noted the way the original lanyards were tied.
*Denouement: The Joke's on Us.
Remember that retired guy who we expertly coaxed back into making the Lichtenberg figures for us? At the EFF badge hacking contest at DC24, 1o57 let several things be known:
1) The Lichtenberg figure guy really is retiring, but he just has a deal with 1o57 to make us work for his help! (Another counterfeiting team got the exact same story - that he'd 'come out of retirement' for this project). Even better, he also contacted 1o57 when someone ordered the triangular figure. So 1o57 totally knew what was up. Well played 1o57... Well played.
2) The real Challenge Coins have a secret mark on them! 1o57 added a random looking scratch to the coin to mark it as his own, but it blends in like just another scratch. Good luck locating it without an original! (or with an original...)
Thanks to the rest of Co9 for trusting me with the project. For the time, money, and effort spent on this build, it was fantastic experience with amazing results. I do hope to do it again with our DC24 Terminator UBER!
Presentation to 1o57
Co9 loves the Badge Challenge. We realize the incredible amount of effort the 1o57 volunteers every year to make this happen and are greatly appreciative. We built an extra replica to give to 1o57 to show our appreciation, and gave it to him right before the DC24 opening ceremony. He loved it and wore it on stage. He gave us a shout out too that this was the best counterfeit he'd ever seen. So Happy.
If you like to make/build IRL hit me up. [No, I won't make you one so stop asking!]
--junkmail3 (@) gmail
0 notes
Text
DEFCON 24 EFF T-Shirt Puzzle
After successfully winning the DC24 badge challenge, we ventured out of the 1o57 room. Only to find more crypto & puzzles to solve!
Every year, for the past few years, the EFF has embedded a puzzle in their defcon tshirt.
https://www.eff.org/deeplinks/2013/08/effs-encryption-t-shirt-puzzle-solved
https://www.eff.org/deeplinks/2014/08/effs-defcon-22-t-shirt-puzzle-explained (those puzzle solvers look familiar)
https://www.eff.org/deeplinks/2015/08/effs-def-con-23-t-shirt-puzzle-crypto-noir
This trend continued this year...
SPOLIERS AHEAD (and gophers) - but first, donate to the EFF, seriously: https://supporters.eff.org/donate/button
The T-Shirt
What this looks like under a UV light:
The Puzzle
Ok, lets get started. The EFF defcon tshirt featured an awesome robot on the back. Looking at the text under a UV light, the following was highlighted:
base64 text
an arrow showing how to read the base64 text
the word "LIBERTY"
The base64 text:
U2FsdGVkX1/zCTZ6hI6lPrjBG1/HYrMVQLDprPHiVQg=
Turning that into a file:
$ cat base64.txt | base64 --decode | hexdump -C | more 00000000 53 61 6c 74 65 64 5f 5f f3 09 36 7a 84 8e a5 3e |Salted__..6z...>| 00000010 b8 c1 1b 5f c7 62 b3 15 40 b0 e9 ac f1 e2 55 08 |[email protected].| 00000020
The word "Salted__" immediately stands out. This was likely created using the "openssl enc" command (for more information: http://justsolve.archiveteam.org/wiki/OpenSSL_salted_format)
The file is 32 bytes, the first 16 are the salt, this leaves 16 bytes to attempt to analyze. Passing this through bletchley-analyze does not show anything exciting:
$ cat base64.txt | base64 --decode | dd bs=1 skip=16 2>/dev/null | bletchley-analyze ================================================================================ Beginning analysis after decoding by chain: Unique Lengths: 16 Maximum Possible Block Size: 16 Matching Common Block Sizes: 8,16 Possible Encodings: Best Encoding: None First 1 Values: 0000: b8c11b5fc762b315 40b0e9acf1e25508 | b'\xb8\xc1\x1b_\xc7b\xb3\x15@\xb0\xe9\xac\xf1\xe2U\x08'
Tool link: https://github.com/ecbftw/bletchley
At this point, we know we have encrypted data, we think our password is "LIBERTY", but we do not know what algorithm was used to encrypt the data (we can guess it's a block cipher with a block length of 8 or 16 bytes).
Trying a few different symmetric ciphers, we arrive at DES!
$ cat base64.txt | openssl enc -des -a -d -pass pass:LIBERTY 15920320062
A reasonable assumption is that we have a phone number (1-592-032-0062). That assumption was incredibly incorrect (<3 EFF) - this is actually an IP address:
http://159.203.200.62/
Visiting that site gives us a "Welcome to nginx!" default page. Using nmap shows something far more interesting:
$ nmap 159.203.200.62 Starting Nmap 6.40 ( http://nmap.org ) at 2016-08-13 02:03 EDT Nmap scan report for 159.203.200.62 Host is up (0.0018s latency). Not shown: 997 closed ports PORT STATE SERVICE 22/tcp open ssh 70/tcp open gopher 80/tcp open http Nmap done: 1 IP address (1 host up) scanned in 21.46 seconds
After learning more about gopher, we discovered this server was running PyGopherd, meaning that no gopher client was required:
http://159.203.200.62:70/
A "Mystery" page appears! Downloading that, we get a binary blob. Our OS immediately identifies this as a PDF, opening the PDF shows the following image (the tshirt):
Suspecting that we were not finished yet with this mysterious binary blob, we looked at the end of it:
$ hexdump -C mystery.pdf | tail -n 6 0009a5d0 73 43 69 50 55 54 05 00 03 8f a0 8a 57 75 78 0b |sCiPUT......Wux.| 0009a5e0 00 01 04 e8 03 00 00 04 e8 03 00 00 50 4b 05 06 |............PK..| 0009a5f0 00 00 00 00 01 00 01 00 4a 00 00 00 57 da 02 00 |........J...W...| 0009a600 00 00 73 00 63 00 72 00 69 00 70 00 74 00 6b 00 |..s.c.r.i.p.t.k.| 0009a610 69 00 74 00 74 00 79 00 00 00 00 0a |i.t.t.y.....| 0009a61c
That's no PDF! There is something attachted to the end of this binary blob, lets dissect it!
Binwalk shows a zip file in the middle of the PDF:
$ binwalk mystery.pdf DECIMAL HEX DESCRIPTION ------------------------------------------------------------------------------------------------------- 445259 0x6CB4B Zip archive data, at least v2.0 to extract, compressed size: 186905, uncompressed size: 205218, name: "sCiP" 632322 0x9A602 End of Zip archive
Pulling that out and unzipping it shows the following image (filename "sCiP"):
Looking closer at the binary blob, the PDF ends at the start of the ZIP file and then zip file runs almost to the end of the blob. There is something left at the end however:
$ dd if=mystery.pdf bs=1 skip=632322 2>/dev/null | hexdump -C 00000000 73 00 63 00 72 00 69 00 70 00 74 00 6b 00 69 00 |s.c.r.i.p.t.k.i.| 00000010 74 00 74 00 79 00 00 00 00 0a |t.t.y.....| 0000001a
We got stuck here for a while, we were convinced something was hidden in the PDF, once again, we were incorrect. There was something hidden in the cat! Running steghide on the image in the zip file:
$ steghide extract -sf sCiP Enter passphrase: -- no password entered -- wrote extracted data to "flag.py". $ cat flag.py flag = ['0x27', '0xb', '0x17', '0x49', '0x16', '0x18', '0xa', '0xe', '0x54', '0x1d', '0xa', '0x49', '0x43', '0x37', '0x7', '0x13', '0x6', '0x12', '0x19', '0x0', '0x54', '0x18', '0x1f', '0xf', '0x52', '0x1d', '0x18', '0x11', '0x4b', '0x1d', '0x1c', '0x1d', '0x17', '0x14', '0x10', '0x53'] print "".join(map(lambda b: chr(int(b, 16)), flag))
Running flag.py prints gibberish. Searching the internet for similar python code, one of our team members came across https://hazinski.net/post/eff-ctf/ and noticed that what we were doing was very similar to the "Stego-saurus-rex (400)" challenge.
Throwing together some quick python code to XOR the flag with "scriptkitty" (embedded at the end of the mystery blob) gave us our solution:
$ cat flag_solution.py flag = ['0x27', '0xb', '0x17', '0x49', '0x16', '0x18', '0xa', '0xe', '0x54', '0x1d', '0xa', '0x49', '0x43', '0x37', '0x7', '0x13', '0x6', '0x12', '0x19', '0x0', '0x54', '0x18', '0x1f', '0xf', '0x52', '0x1d', '0x18', '0x11', '0x4b', '0x1d', '0x1c', '0x1d', '0x17', '0x14', '0x10', '0x53'] f = "".join(map(lambda b: chr(int(b, 16)), flag)) sc = 'scriptkittyscriptkittyscriptkittyscriptkittyscriptkitty' def sxor(s1,s2): # thanks to http://stackoverflow.com/questions/2612720/how-to-do-bitwise-exclusive-or-of-two-strings-in-python/2612730#2612730 return ''.join(chr(ord(a) ^ ord(b)) for a,b in zip(s1,s2)) print sxor(f,sc)
Running flag_solution.py gives our solution.
The flag is: Encrypt all the things!
@EFF @xor encrypt all the things! #defcon #!mC - solved by @TheCouncilOf9
— Sam Erb (@erbbysam) August 7, 2016
The EFF was generous enough to give us a sweatshirt & a few tshirts for being the first to solve this puzzle.
Congratulations to @TheCouncilOf9 for solving or #defcon 24 shirt puzzle! pic.twitter.com/niIokgtuUt
— EFF (@EFF) August 7, 2016
Thank you EFF!
Donate
Have you donated yet? https://supporters.eff.org/donate/button
The Council
ziot (@bbuerhaus)
0rigen (@_0rigen)
erbbysam (@erbbysam)
mstc (@M57C)
Wumpus
junkmail (@jumknail3)
w1pe0u7
ben
if_
qa_ninja
Wumpus
Thor (@potatosec)
Punk (@punk_AB)
Would you like to know more?
Want to challenge yourself against crypto?
Want to create a crypto challenge?
We created a website to host crypto challenges designed by us and the community.
Check out the challenges on Potato Planet Crypto
Want more to read? Check out our write-ups from the previous badge challenges:
DEFCON 24 Badge Challenge
DEFCON 23 Badge Challenge
DEFCON 22 Badge Challenge
0 notes
Text
DEFCON 24 Badge Challenge
Council of 9 ventured forth to DEFCON 24 to compete in this year's badge challenge, brought to us each year by 1o57. There was determination among the team to win at DC24 to ensure that last year's win was not a fluke. After many sleepless nights in Vegas, we emerged victorious for a second year in a row.
Here is the entire adventure as we experienced it, with all of the puzzles we encountered, and how we defeated them. Understand that this may not contain solutions to all of the puzzles in the challenge, but there will be plenty of spoilers.
Still here? Follow us into the rabbit hole.
Step_0: The Troll
The challenge this year started a week before DEFCON 24 began, when we noticed that some HTML comments on lostboy.net had been changed. It didn't take long for us to discover that the site was appending the text "Watching are you?" to the bottom of the page, every minute on the minute.
We were surprised that these changes were going out a week before DEFCON, and assumed that this was probably unrelated to the badge challenge. There was hope for Mystery Challenge to make a return, so we decided to pursue these changes as if they were a puzzle. We began monitoring lostboy.net for further updates and started looking around at other known pages to find if any other location was being updated.
We quickly noticed that the TwilightZone page from DEFCON 23's cryptovillage puzzle had text appended to the bottom of several of its pages as well. Having solved this the year prior, we already knew what the other pages were, and were able to investigate them all rather quickly.
http://lostboy.net/TwilightZone/
<!-- Defcon 24 Time Travel back to Defcon 23! ;) --> <!-- Hiding in time and space. A blast from the past. --> <!-- Access Octo-Fragment Vector v0fy1HeJv80:01061961 -->
DEFCON 24! The access fragment vector sounded super important. After some investigation, we determined that the 'vector' is made up of two distinct pieces. The first piece is a YouTube video hash and the second piece is a date. The only thing we could possibly think of that might be a connection is the date matches the release day of a Twilight Zone episode
The YouTube video for v0fy1HeJv80 is the song Blue Moon by The Marcels
The date "01061961" January 6, 1961 was the release date of the Twilight Zone episode Dust.
Another page that was updated:
http://lostboy.net/TwilightZone/WhereIsEverybody/
<!-- Fb lbh ner ba gur evtug cngu, QRSPBA 24. V ubcr gung lbh ner univat sha. Frrx gur rtt. -->
This second message is a simple caesar cipher and needs to be rotated. This gives us the following message:
So you are on the right path, DEFCON 24. I hope that you are having fun. Seek the egg.
We had no idea what this meant, but it was telling us to seek the egg, which sure seemed important.
After setting up some automated captures of lostboy.net to detect any more interesting edits, our captures on lostboy.net started to spit out new results. Here is a timeline of our captures:
Tuesday, July 26, 2016 6:34:13 PM GMT-7:00 DST: Reset the count back to 0 after hitting 1099.
Tuesday, July 26, 2016 7:36:46 PM GMT-7:00 DST: Added the text “See anything interesting? ;)”
Tuesday, July 26, 2016 8:42:16 PM GMT-7:00 DST: Reset the count back to 0 after hitting 4. The text “https://youtu.be/Gi66-gAxgco” was added.
Wednesday, July 27, 2016 6:55:38 AM GMT-7:00 DST: Reset the count back to 0 and this text was added “ENZUiHgtRuc”. This is a YouTube video: https://www.youtube.com/watch?v=ENZUiHgtRuc. (MATT BERRY GHOSTS)
At this point, it started to feel like we were being trolled. Being trolled by 1o57 is awesome though, you get to find glorious gems such as:
youtube
With the Matt Berry GHOSTS video as a hint, we eventually discovered this sub-directory on the website:
http://lostboy.net/Ghosts/
We banged our collective heads against our keyboards making little-to-no progress with this website until 1o57 sent out this tweet:
It's amazing to me given one of the pieces something that hasn't been tried. Even once. Those not close to it would get it immediately.
— LosT/李智上 (@1o57) July 29, 2016
It still took us awhile to figure out what in the world 1o57 might be referring to...but, eventually, this led us to discovering the GhostBusters sub-directory: http://lostboy.net/GhostBusters/ Duh. Ghost => GhostBusters. How did we not think of that sooner?!
We quickly figured that "Sound and Fury..." on the page is referencing Macbeth.
It is a tale Told by an idiot, full of sound and fury Signifying nothing.
And at this point, we were 90% sure that we were being trolled.
A little bit earlier a Tweet had gone out referencing the egg we were told to seek.
I guess the egg defeated those attempting to crack it. You know who you are. @defcon see you all in a few days.
— LosT/李智上 (@1o57) July 29, 2016
After going through everything we had already discovered so far, our research efforts eventually showed that Matt Berry from the GHOSTS video before was in a show called The Mighty Boosh that 1o57 had made numerous references to already. It turns out that in the shows pilot episode, Tundra, they go out to Antarctica looking for The Egg of Mantumbi. It wasn't immediately obvious how to use this information, but we soon discovered this domain:
http://eggofmantumbi.com/
I'm not going to go into a lot more detail on this. Just know that we wasted A LOT of time on this website. You can continue to seek the egg if you wish, there is more to discover. The only thing you must know (and that we wish we knew at the time) is that the Egg of Mantumbi is not part of DEFCON 24 badge challenge.
At this point it had been a few days and we were ready to set sail for DEFCON 24. Nothing else was discovered until the start of DEFCON.
Step_1: The Book
After linecon, we received our badges, book, lanyards, and dvd. We started to tear through each item looking for clues. At the same time, we sent part of the team out to collect lanyards and badges.
We started with the book and went straight to the 1o57 page. This was on page 3 of the DEFCON 24 book.
Solving the equations was relatively easy, since WolframAlpha exists. One of our teammates sat down and started plugging these equations in and recording the output. It wasn't immediately obvious what in the world to do with those numbers, but we eventually discovered that the solutions contained only alpha-space numbers (>=26) and all had a null byte (00) terminator in them (these were created using http://mrob.com/pub/ries/ which is AWESOME!). By converting the numbers into letters (A=01, B=02, etc) that were before the null byte, we found a keyword!
Using the first as an example: https://www.wolframalpha.com/input/?i=1+%2F+(e+-+sqrt(x+-+pi+%5E+2))+%3D+7+-+e+%5E+(sqrt(pi%2F7))
x=16.220516082600... => (letter numbers) PVEPHZ => (ROT13) CIRCUM
The output came out to CIRCUMVIRUMDANTISTHIS. circum virum dant is a latin phrase and we found a reference to it on the Tmesis wiki page. CIRCUMVIRUMDANT IS THIS => CIRCUMVIRUMDANT IS a Tmesis! Trying it out, we discovered that this was a new page on lostboy.net
http://lostboy.net/Tmesis/
Source:
<!-- Access Fragment Vector gvK2HGrBc00:09151961 -->
We had previously discovered an access fragment vector the week prior to con on the TwilightZone page. Knowing that there's a YouTube video hash and date, we checked our theory.
The video gvK2HGrBc00 is "Lil' Rob - Summer Nights". The date is Stepember 15, 1961. The episode "Two" was released on this date.
We didn't have much more to go on at this point, but we were making breakthroughs simultaneously elsewhere in the challenge that led us to new conclusions with this data.
Step_2: The Badges
It was a hardware year at DEFCON and we figured we would have to pull firmware and data from the badge to help with the puzzle. Before getting too deep, we first have to look at everything that is on the badge itself. Here is the front and back of the HUMAN badge:
Front:
Back:
There are several noticeable strings on the back of badge including two strings that are not easily seen on the HUMAN badge. For comparison, here are the two "hidden" strings on a different badge:
Cipher text 1
nonpareil bimil: Icnwc lsrbcx kc ntr-yudnv ifz xdgm yduxnw yc iisto-eypzk.
The first word nonpareil means "having no match or equal; unrivaled." The second word bimil is phoenetic Korean for "secret". It's telling us the cipher is an unbeatable secret. We continued to work on this a bit, but we made an assumption that it is a One Time Pad and we needed a key to decipher it.
Cipher text 2
010625110310031312
We quickly discovered that this was letter numbers with a rotation. 01=A, 06=F, etc. This comes out to AFYKCJCML. Applying rot-2 (Really, 1o57, ROT2?!) to that string, we get CHAMELEON. As it turned out, there was a different string on every type of badge at the con.
Badge Type String HumanChameleonGoonExecutionContestMiniaturePressMuteCFPStaticSpeakerSteelArtistDustVendorTwo
We discovered that these are all Twilight Zone episodes that match the dates on the access vectors we had been discovering. Not long after we also discovered every Twilight Zone episode was also a sub-directory page. Each page had a single YouTube video referencing the word red, so we assumed that the pages were red herrings. The main thing to note is that the Dust page was 403 Forbidden and contained nothing.
Sigma Number
1000010001 ΣA120215
The Sigma string led us to https://oeis.org/A120215. We knew we were on the right track because the sequence begins with 1057. The Sigma symbol hints at a summation, leading us to sum all of the numbers in the A120215 sequence. When adding them all together we get the value 247545. This turned out to be another page:
http://www.lostboy.net/247545/
This page contained another access fragment vector:
<!-- Access Fragment Vector 4SIkCVurNBs:04011960 -->
Step_3: The DVD
For the past few years there has been a file related to the badge challenge on the DEFCON media DVD. We dug through it and quickly found the 1057 sub-directory. This can be found online: https://media.defcon.org/DEF%20CON%2024/DEF%20CON%2024%20badge%20contest/1o57/
The folder contained a password protected rar file 1o57.rar and a text file Origin-Story.txt
We noticed that the Origin-Story.txt was a DEFCON short story entry that also happened to be in the short story folder. The true short story entry can be found here: https://media.defcon.org/DEF%20CON%2024/DEF%20CON%2024%20short%20story%20contest/DEFCON-24-Leah-Thompson-Thebackup.txt
Having two copies of the 'same' story, one of them being in the 1o57 folder, was immediately suspicious. We began reading both of them, and noticed that there were some... 'corrections' that had been made to the 1o57 version. Running a diff checker between both files, we investigated all of the areas that had been changed. You can view the diffs here: https://www.diffchecker.com/rsz5yjkm
Differences:
Removed: city, life, mundane, after, all
Added: twice
The 'twice' immediately reminded the team of 'octothorp' from DEFCON 22 badge challenge, and sent us all into a rage of nightmares and fear. Once we calmed, we realized that the file is giving us the password, using the differences: citylifemundaneafterall twice. The rar password was citylifemundaneafterallcitylifemundaneafterall.
Inside the rar file we get access to the following files:
AreWeHavingFunYet.txt
David_Bowie-Life_on_Mars.jpg
JustForFun.jpg
The text file leads out to a new website: http://LostboY.net/IsThereLifeOnMars
This gave us a new access vector fragment and a message from 1o57 for Ziggy.
<!-- Access Fragment Vector d3keN6x9hdU:01311963 --> <!-- With Respects, Ziggy, we will miss you. --> <!-- Personal Request: Take a moment as you work on the puzzles, as a team, just a moment, of silence- out of respect for David. Thanks, Ryan. -->
Step_4: Signs
The glyphs on the con signs threw us for a loop for awhile. We went back to basics and thought "how can information be stored in shapes?..." Here's what we found. The circles in the glyphs are performing grouping. The groups are made up of letter-numbers, determined by the number of angles contained within each shape. By counting the number of angles within the circle, you obtained a letter-number value. Continuing down the glyphs on a single sign, you eventually spell out an entire word or words.
Sign 1 - seekfirst
Sign 2 - lostboy
Sign 3 - .net
Sign 4 - Danger
Sign 5 - Zone
This results in a new page: https://lostboy.net/DangerZone/.
We didn't notice right away, but the title on the page was LostboY.net/DangerZone (or so you assumed...). This gave one of us the bright idea that there is another page being hidden from us. Sure enough, https://lostboy.net/ZoneDanger/. We had ordered the words in what we thought was the obvious order...but 1o57 is not an obvious kind of guy.
With that we acquired two new access fragment vectors.
<!-- Access Fragment Vector lzQ8GDBA8Is:03101961 --> <!-- Access Fragment Vector WCXlp3D5NQA:02211963 -->
Step_5: Lanyards
There were 5 lanyards this year; 3 containing numeric values by themselves, 1 containing a binary value followed by a 'y', and 1 containing binary values followed by an 'x'. Once we collected all of the lanyards, we immediately thought "coordinates". The application of the coordinates, however, was far from obvious, and many many hours were spent trying to crack the proper treatment of this puzzle.
We spent a lot of time trying to solve this and as far as I know no team was able to solve it until 1o57 tweeted a hint on how to align them. Through social engineering, we were able to extract the solve from another team.
You can find the full lanyard solution posted here: https://degeneratemetric.wordpress.com/dc24LanyardSolutions/ by @degeneratMetric
We decided to move on with the challenge instead of trying to solve the lanyards ourselves at that moment. It resulted in the following string: MimeAndPunishment
This is a new page: http://lostboy.net/MimeAndPunishment/
This page contained another access fragment vector.
<!-- Access Fragment Vector 1dC0DseCyYE:10041963 -->
There is a song playing named WriteOfPassage.mp3 that is actually Sting - Sky Hooks and Tartan Paint (feat. Brian Johnson). The lyrics in this song reference a man being sent on a fool's errand. Take a magical leap of faith and land on this new page:
http://lostboy.net/FoolsErrand/
On this page we acquire a final access vector.
<!-- Access Fragment Vector jXq8oQ5DNbQ:10041985 -->
Step_6: Badge Permutation
At this point we had collected 8 access fragment vectors and several potential clues from all of the pages discovered. There were some theories regarding how we had to reorder the access fragment vectors to get a new page, but only theories.
Badge Type Episode Access Vector HumanChameleonjXq8oQ5DNbQ:10041985GoonExecution4SIkCVurNBs:04011960ContestMiniatureWCXlp3D5NQA:02211963PressMuted3keN6x9hdU:01311963CFPStaticlzQ8GDBA8Is:03101961SpeakerSteel1dC0DseCyYE:10041963ArtistDustv0fy1HeJv80:01061961VendorTwogvK2HGrBc00:09151961
After reaching one of many points of desperation, a member on our team realized that if they were using the badge names as a URL, it would only be around 42k possibilities, which is easily bruteforced. Some might say this is cheating, but it's DEFCON. There are no rules.
For anyone interested, here's a link to the script
We got a hit on the permutation ExecutionTwoMiniatureSteelChameleonMuteStaticDust
We came back later and solved this after Defcon. Every Access Fragment Vector is comprised of [YouTube Video:Twilight Zone Episode Date].
Episode Access Vector Song ChameleonjXq8oQ5DNbQ:10041985Danny & The Juniors - Rock N' Roll Is Here To Stay Execution4SIkCVurNBs:04011960Love Is A Many-Splendored ThingMiniatureWCXlp3D5NQA:02211963Ritchie Valens - La BambaMuted3keN6x9hdU:01311963Sha Na Na - Tears On My PillowStaticlzQ8GDBA8Is:03101961Elvis Presley - Hound DogSteel1dC0DseCyYE:10041963Jerry Lee Lewis - Whole Lotta Shakin Going OnDustv0fy1HeJv80:01061961The Marcels - Blue Moon TwogvK2HGrBc00:09151961Lil' Rob - Summer Nights
We discovered that all of these songs are in the movie Grease. You have to order the pairs based on the order the songs are played in the movie.
What order are the songs in Grease?
Love Is a Many Splendored Thing ... Summer Nights ... La Bamba ... Whole Lotta Shakin´ Goin´on ... Rock & Roll Is Here to Stay ... Tears on My Pillow Hound Dog ... Blue Moon
After that, translate the dates into the Twilight Zone episode names. And put the episode names in as URL to get the next page.
Episode Song Grease Song # ExecutionLove Is A Many - Splendored Thing1TwoLil' Rob - Summer Nights 3MiniatureRitchie Valens - La Bamba7SteelJerry Lee Lewis - Whole Lotta Shakin Going On9ChameleonDanny & The Juniors - Rock N' Roll Is Here To Stay 12MuteSha Na Na - Tears On My Pillow14StaticElvis Presley - Hound Dog15DustThe Marcels - Blue Moon 17
This gives us the episode order: Execution Two Miniature Steel Chameleon Mute Static Dust
Step_7: Crypto Pages
https://lostboy.net/ExecutionTwoMiniatureSteelChameleonMuteStaticDust/
This page contains a song playing named WindsOfChange.mp3, an image of a red moon, and the page title of "Red vs. Blue." The artist and song are actually Kansas - Dust In The Wind which leads us to think of the 403 Forbidden Dust page.
The page also contained a hint in an HTML comment:
<!-- the mightiest tree -->
This is a reference to Monty Python and the Holy Grail scene with the Knights who say Ni!. They state you must "cut down the mightiest tree in the forest—with a herring!" The episode Dust's access vector contained the YouTube hash for the song Blue Moon. Red vs. Blue... "Blue Moon Red Herring" which means the Blue Moon Access Vector is a Red Herring and must be removed from the URL.
https://lostboy.net/ExecutionTwoMiniatureSteelChameleonMuteStatic/
This page contains 8 images. Each image contains the name of an actor in the movie Lost Boys. Each image is custom made and returned no results from Tineye or Google Image Search. The title of the page is 'Parked.'
We saw that the images were a combination of two things and we believed they were a portmanteau. We weren't wrong, but it took us a while to realize what they were. I think the realization occurred when someone Googled Bieber Saurus and Lambtron and noticed that these were referencing Chinpokomon from South Park. Now the page title, 'Parked.', made sense.
Crypto genius at work here, folks:
This led us to the next page: http://lostboy.net/Chinpokomon/
This page contained various hand signals instructing a painting of a dog. Someone on our team quickly recognized these as Curwen Hand Signs and it is referencing Close Encounters of the Third Kind.
This leads us to the next page: http://lostboy.net/CloseEncountersOfTheThirdKind/
This page had the title of ET and what appeared to be three sets of numbers. We assumed that we would get a phone number from this page, because of the hint ('ET' => Phone Home) and the fact that there were three number groups on the page.
0000000001000000000 -> binary to decimal -> 512
Circumference (360)
The clock's time is 2:34
If we combine these three numbers together we get 512-360-0234.
Step_8: Phone Number and Timegate
A formal apology to residents of Austin, TX for our many late-night calls and texts during this phase...
After several hundred texts, calls, and some technical difficulties were solved, we received this message:
Retext tomorrow at 1:57 for the passcode
It was around 4 AM at this point, so we decided to catch some sleep (since 1o57 was forcing us to) and try again in the morning. A couple of team members couldn't sleep for long, and it was around 10 AM when hotel doors were being banged on because the number started responding to texts with new responses many hours before 1:57.
There were 4 possible responses you could get
thinking capHoed heks sehow blaiseVv Akhx K Fakoh1o57Sorry about the technical hiccups yesterday.help someone elsehuwtkakziykrokttcgmkdiswgdnunvcejjfovammvikywsyrvxewikdherzv
We were waiting for a really long string to use as the one-time pad (OTP) for the cipher on the back of the badge. It didn't take us long to realize that there were two OTPs from the texts
Deciphering as OTP against the text on the back of the badge and the code from the text, we get this:
OTP(Icnwc lsrbcx kc ntr-yudnv ifz xdgm yduxnw yc iisto-eypzk., huwtkakziykrokttcgmkdiswgdnunvcejjfovammvikywsyrvxewikdherzv) = Birds listen to day-words and rats listen to night-words.
Deciphering as OTP against the two texts, we get the text OhWhatANight
OTP(Vv Akhx K Fakoh, Hoed heks Se) = Oh What A Nigoh
Step_8: The Solve
This led to a new page: http://lostboy.net/OhWhatANight/
The page title is Sumtimes it goes to 11. The page also contains numbers and two Chinese symbols (日, 月). These symbols can mean Day and Month or Sun and Moon. Our text message says day-words and night-words, so we felt Sun and Moon was more appropriate.
After a grueling 20 minutes of trying a ton of different things, it came down to Occam's razor. The sum of all the numbers next to 日 equaled 91, which led us to the final page.
http://lostboy.net/91/
Find LosT. Shake his hand. Give him a piece of paper with "91" and the night words creature written on it.
To win the badge challenge you had to give LosT a piece of paper with "91" and "rats" on it.
The Council
@TheCouncilOf9 was victorious again at @defcon 24! #!mC Big things on the horizon for us next year... #mC pic.twitter.com/SCnBpIZBUM
— 0яigen (@_0rigen) August 9, 2016
ziot (@bbuerhaus)
0rigen (@_0rigen)
erbbysam (@erbbysam)
mstc (@M57C)
Wumpus
junkmail (@jumknail3)
w1pe0u7
ben
if_
qa_ninja
Wumpus
Thor (@potatosec)
Punk (@punk_AB)
Would you like to know more?
Want to challenge yourself against crypto?
Want to create a crypto challenge?
We created a website to host crypto challenges designed by us and the community.
Check out the challenges on Potato Planet Crypto
Want more to read? Check out our write-ups from the previous two badge challenges:
DEFCON 23 Badge Challenge
DEFCON 22 Badge Challenge
#co9#council of nine#defcon#defcon24#lostboy#mysterychallenge#crypto#security#hacking#1o57#1057#lost#potato
17 notes
·
View notes