Don't wanna be here? Send us removal request.
Text
Network Analysis – Malware Compromise BTLO Walktrhu
Hello again for another Network Forensics episode this time featuring Network Analysis – Malware Compromise Challenge from BlueTeamLabs.Online This is another fantastic training platform. I figured would be faster if I shared my video walkthru than creating another writeup from the video. 🙂 #networkforensics #ctf #blueteam #dfir #wireshark

View On WordPress
0 notes
Text
HackTheBox Reminiscent Walkthrough
Hello again to another blue team CTF walkthrough now from HackTheBox title Reminiscent – a memory analysis challenge. Woohoo more Volatility stuff! Challenge Link: https://app.hackthebox.com/challenges/reminiscent CHALLENGE DESCRIPTION Suspicious traffic was detected from a recruiter's virtual PC. A memory dump of the offending VM was captured before it was removed from the network for…

View On WordPress
0 notes
Text
HackTheBox Diagnostic Walkthrough
Hello again to another blue team CTF walkthrough now from HackTheBox title Diagnostic – an ole document analysis challenge Challenge Link: https://app.hackthebox.com/challenges/reminiscent CHALLENGE DESCRIPTION Our SOC has identified numerous phishing emails coming in claiming to have a document about an upcoming round of layoffs in the company. The emails all contain a link to…

View On WordPress
0 notes
Text
Cyberdefenders.org FalconEye Blue Team Challenge Walkthrough
Hello again to another blue team CTF walkthrough now for more Splunking! This is FalconEye Blue Team Challenge in CyberDefenders.org. Some of the interesting things in this challenge are as follow but not limited to; -Dcsync attack -Pass-The-hash -Lateral Movement techniques -Mimikatz And more J Challenge Link:…

View On WordPress
0 notes
Text
Cyberdefenders.org RedLine Blue Team Challenge Walkthrough
Hello again to another blue team CTF walkthrough now for more memory forensics! This is Redline Blue Team Challenge in CyberDefenders.org. Challenge Details: Scenario: As a member of the Security Blue team, your assignment is to analyze a memory dump using Redline and Volatility tools. Your goal is to trace the steps taken by the attacker on the compromised machine and determine how they…
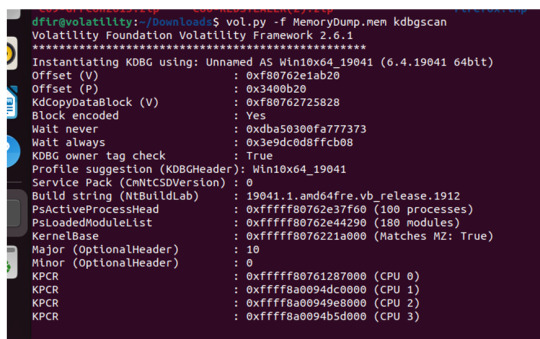
View On WordPress
0 notes
Text
LetsDefend.io SOC202 - FakeGPT Malicious Chrome Extension Walkthru
LetsDefend.io SOC202 – FakeGPT Malicious Chrome Extension Walkthru Hello and today we will solve the alert SOC202 – FakeGPT Malicious Chrome Extension. We can trust popular apps like ChatGPT but we must verify. Alert Details You need to first Take Ownership of the incident then create a case to begin investigation. Investigation Click Start Playbook It will give a short explanation of the…
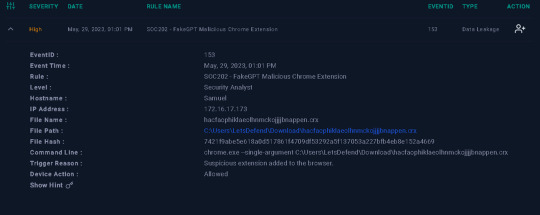
View On WordPress
0 notes
Text
Letsdefend.io Disclose the Agent Walkthrough
Hello again to another blue team CTF walkthrough now for more pcap network forensics! This is Letsdefend.io Disclose the Agent challenge. Challenge Details: We reached the data of an agent leaking information. You have to disclose the agent. Log file: https://api.letsdefend.io/download/downloadfile/smtpchallenge.zip Pass: 321 Note: pcap file found public resources. Question and…

View On WordPress
0 notes
Text
Cyberdefenders.org Hunter Walkthrough
Hello again to another blue team CTF walkthrough now for more disk forensics! This is Hunter Challenge in CyberDefenders.org. Some of the interesting things in this challenge are as follow but not limited to; Investigating full disk image using FTK imager Investigating registries Investigating shellbag Investigating jump lists Fornesic tools to check out these artifacts And more…
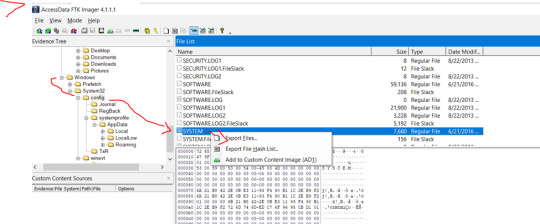
View On WordPress
0 notes
Text
Cyberdefenders.org Malware Traffic Analysis Part 6 CTF Walkthrough
Cyberdefenders.org Malware Traffic Analysis Part 6 CTF Walkthrough
Hello again to another blue team CTF walkthrough for more network forensics and malware analysis. Shall we start? This is now the 6th instalment of Malware Traffic Analysis Challenge in CyberDefenders.org. Credits to Brad Duncan for these awesome challenges! Some of the interesting things in this challenge are as follow but not limited to; Finding and exporting files from pcap file using…

View On WordPress
0 notes
Text
Cyberdefenders.org Malware Traffic Analysis Part 5 CTF Walkthrough
Cyberdefenders.org Malware Traffic Analysis Part 5 CTF Walkthrough
Hello again to another blue team CTF walkthrough for more network forensics and malware analysis. Shall we start? This is the 5th instalment of Malware Traffic Analysis Challenge in CyberDefenders.org Some of the interesting things in this challenge are as follow but not limited to; Phishing Email Analysis Malicious Attachments Finding and exporting files from pcap file using Network…
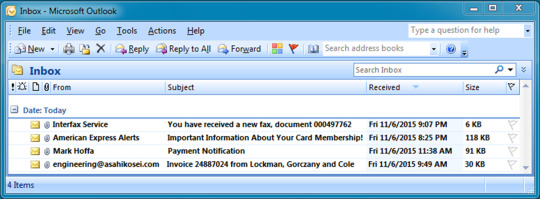
View On WordPress
0 notes
Text
Cyberdefenders.org Malware Traffic Analysis Part 4 CTF Walkthrough
Cyberdefenders.org Malware Traffic Analysis Part 4 CTF Walkthrough
Hello again to another blue team CTF walkthrough for more network forensics and malware analysis. Shall we start? This is the 4th instalment of Malware Traffic Analysis Challenge in CyberDefenders.org Some of the interesting things in this challenge are as follow but not limited to; · · Finding and exporting files from pcap file using Network Miner · · Navigating and…
View On WordPress
0 notes
Text
LetsDefend.io SOC139 - Meterpreter or Empire Activity Walkthrough (Malware)
LetsDefend.io SOC139 – Meterpreter or Empire Activity Walkthrough (Malware)
Hello and today we will solve the alert SOC139 – Meterpreter or Empire Activity. It is good reminder to be always familiar with attacker tools as well and how to detect those. Alert Details You need to first Take Ownership of the incident then create a case to begin investigation. Investigation Click Start Playbook Then the playbook steps will kick-start remember the PICERL Incident response…

View On WordPress
0 notes
Text
LetsDefend.io SOC175 — PowerShell Found in Requested URL — Possible CVE-2022–41082 Exploitation
LetsDefend.io SOC175 — PowerShell Found in Requested URL — Possible CVE-2022–41082 Exploitation
Hello and today we will solve the alert SOC175 — PowerShell Found in Requested URL — Possible CVE-2022–41082 Exploitation. This exploit targets Exchange Servers and was a zero-day RCE vulnerability that is just recently discovered. In fact there were still no available patches from MS as of this writing (Oct 13, 2022). Alert Details You need to first Take Ownership of the incident then create a…

View On WordPress
0 notes
Text
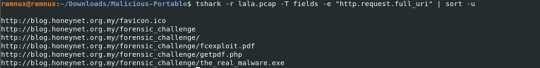
Cyberdefenders.org GetPDF Walkthrough (Malicious PDF file/Shellcode Analysis)
Cyberdefenders.org GetPDF Walkthrough (Malicious PDF file/Shellcode Analysis)
Hello again to another blue team CTF walkthrough now for a bit of PDF file and shellcode analysis. Some of the interesting things in this challenge are as follow but not limited to; PDF object exploration using Remnux andFlareVM tools extract javascript from a PDF file, run that javascript to understand more how it behaves extract shellcode, decode and check its behavior in runtime And more…
View On WordPress
0 notes
Text
Underthewire.tech Cyborg CTF Walkthrough
Underthewire.tech Cyborg CTF Walkthrough
Hello again to another blue team CTF walkthrough this time I found an interesting site offering powershell CTF – underthewire.tech. The site features multiple powershell CTF from basic to advanced that will help enhance your powershell skills. Powershell is such a powerful tool to add in your investigation toolbox as defenders. This time I will try to walk you thru solving the Cyborg…

View On WordPress
0 notes
Text
Cyberdefenders.org Banking Troubles CTF Walkthrough Plus Xavier Memory Analysis Framework Intro
Cyberdefenders.org Banking Troubles CTF Walkthrough Plus Xavier Memory Analysis Framework Intro
Hello again to another blue team CTF walkthrough now for more memory forensics stuff and malware analysis. Wait there’s more I will even share with you some cool memory analysis stuff straight from SNAS DFIR Summit 2022 Some of the interesting things in this challenge are as follow but not limited to; Xavier Memory Analysis Framework tool strings search on a memory image extract javascript…

View On WordPress
0 notes
Text
Cyberdefenders.org Malware Traffic Analysis Part 3 CTF Walkthrough
Cyberdefenders.org Malware Traffic Analysis Part 3 CTF Walkthrough
Hello again to another blue team CTF walkthrough for more network forensics and malware analysis. Shall we start? This is the 3rd installment of Malware Traffic Analysis 2 Challenge in CyberDefenders.org Some of the interesting things in this challenge are as follow but not limited to; Finding and exporting dll paylod from pcap fileNavigating and searching BrimExporting objects from…

View On WordPress
0 notes