Text
No more Gram's: a story of the canceled Telegram's cryptocurrency

0 notes
Text
I2P: «garlic» against censorship
Today we will talk about the safety of work through the I2P, but first a couple of words for those who are not aware of what this network is. So, I2P (Invisible Internet Project) is an anonymous computer network providing a secure connection. The network is supported by a community of volunteers and consists of approximately 55,000 devices dispersed worldwide.
Given the large enough number of possible data paths, tracking the full traffic chain seems very unlikely. In addition, all information, including metadata (e.g. sender and recipient IP addresses, message sending times) is protected by end-to-end encryption and "packed" according to the "garlic" data transmission principle.
I2P from a technical perspective
The network has four levels of encryption used in sending messages, and the forwarding itself is done through so-called "garlic routing." Therefore, even the connection endpoints are considered cryptographic identifiers, so that neither the sender nor the recipient of the message needs to disclose their IP addresses to intermediate nodes or any other third parties, as we can observe, for example, in Tor (below, we compare "garlic" and "onion" routing in more detail). I2P uses 2048-bit enciphering of ElGamal / AES256 / SHA256 and also Ed25519 EdDSA / ECDSA signatures.
I2P differs from earlier popular secure information sharing projects in that the I2P is an anonymous peer-to-peer distributed (decentralized) network designed to run any internet services (Usenet, email, IRC, file sharing, HTTP, Telnet, and others), while almost unused IIP (Invisible IRC Project) is considered an anonymous centralized IRC server. Freenet is another similar project which is preserved from censorship distributed data store. That means that they are decentralized (read: invinsible) unlike IIP, I2P and Tor and have big functionality in comparison with Freenet.
It is interesting to know that until now I2P developers have been known only under the nicknames: for example, the main developer, who has long led the project, hides under the name jrandom, and currently such programmers as zzz, killyourtv and Complication who remain active and continue to develop network architecture, improving the quality of the connection, its stability and security, and in this work they are assisted by numerous volunteers.
We have to add that the I2P is a free open source project and it has been in beta development since 2003. Software developers point out that Beta status may encounter errors and that there has been insufficient expert research into software to work in I2P to date, but they believe that the code is now quite stable and that I2P development can be helped by its wider distribution.
Features of "garlic routing" or I2P vs Tor
Garlic routing is, in general, a no joke, but a very seriously applied term for data technology developed by Michael Friedman about 20 years ago. Garlic routing is a multi-layer encryption method that allows an entire message ("garlic") to contain a huge number of private messages ("garlic clove"). At the same time, all messages are encrypted, and even the ownership of "garlic clove" in "garlic" transit nodes cannot be determined - metadata of these messages is known only to two parties: the sender and the receiver, which guarantees not only a complete preservation of data, but also a complete anonymity of participants of information exchange.
Garlic routing is called an advanced version of "onion," which is used by the creators of the browser network Tor. The weakness of onion routing is the ability to track routing paths including intermediate communication participants. Proxy nodes can track the path of a message down to the sender, in several ways (for example, analyzing metadata on weakly loaded routers or tracking path changes taking into account disconnecting and connecting nodes). Because garlic routing technology involves complete protection of information from intermediate nodes, the ability to track the sender is excluded because the metadata is also encrypted.
Thus, Tor onion routing can protect forwarded messages (with encryption enabled), but it does not guarantee metadata leaks; and garlic routing does not allow for complete confidentiality of I2P information: no one will know who and to whom, and what and when has been sent. And the network is fully fulfilling its main task - so far there have been no data leaks sent through the protocols of the I2P.
What can be found in the vastness of I2P?
In addition to privacy, the I2P can offer its users many interesting resources. Even thouy they are very few and in no comparison close to Tor, the popularity of the network is growing. Thus, in the I2P there are a lot of file exchanges, the most famous of which are Serien and "Schoronil," and there are mirrors of famous torrent trackers. The next category of useful websites is Internet libraries. In I2P the legendary Flibusta can be found - the largest pirate archive of e-books, which contains many thematic collections: from practical chemistry to fantasy.
Fans of communication can be advised to use social network Onelon, which is well known to fans of "onion" Tor - I2P offers similar functionality. I2P is full of anonymous image board with treads about anything. In addition, the I2P is a repository of various types of thematic catalogs, lists and other information of different degrees of usefulness, which, however, can be found without being immersed in the dark-net, because the main function of the I2P is still to ensure complete confidentiality in the transmission of data.
«Heroes always break the rules»
The level of I2P confidentiality speaks for itself
and about a year ago the users are engaged in illegal business started to migrate to I2P from Tor: https://www.cnews.ru/news/top/2019-05-31_kriminal_uhodit_iz_dyryavogo_tor_v_nevidimyj It turned out that Tor has potential vulnerabilities, because of which websites in the "darknet" can be subjected to DDoS-attacks and which can later lead to leakage of metadata, and also reveal them to criminal traders, which of course no one wants to deal with.
2 notes
·
View notes
Text
Small but proud: how DuckDuckGo is standing against the advertising monsters

Maintaining anonymity was one of the key principles of the initially free Internet, which, however, for more than 20 years has been constantly trampled by the largest giants of the Internet technology market: search engines, social networks and trading platforms. Nonetheless, some "islands of freedom" are still present in this world of mass surveillance and control, and we would like to introduce you to one of them in this review.
Meet DuckDuckGo, a search engine that is fundamentally different in its operating principle from the list of "Big Five" search engines (Google, Yahoo, Bing, Baidu and Yandex). The main difference between DuckDuckGo and its competitors is that it respects the principles of confidentiality and anonymity on the Internet and does not collect any information about its users.
How DuckDuckGo emerged
The founder of this fast-growing search engine is Gabriel Weinberg. Weinberg, who had already founded several start-upswith varying degrees of success (spreading from Learnection, a school social network where parents and teachers could communicate, which was ahead of its time, but did not succeed in becoming popular, to the more successful project NamesDatabase, the predecessor of Facebook), suddenly discovered that Google does not deliver the most relevant results for their user requests, and decided to improve it.
The first version of DuckDuckGo went live in 2008 and it was programmed to collect information from alternativesources and to filter the results in a way that the search outcomes contained the links that were as relevant as possible at the very beginning. It already had the search engine schtick to be so loved by those who do not want to allow commercial technologies to step into their personal lives: the system did not take the interests of users and their personal data (gender, age or nationality) into account. And it still doesn't: DuckDuckGo today is a system that is not constrained by anyborders, has no resources blocked by any local laws and no user tracking.

From convenience to privacy
Interestingly enough, privacy of users' information was not the main priority for Weinberg at the beginning: he ranked search engine convenience first. However, after a number of unsuccessful attempts to promote the search engine, the developer came up with the idea of focusing the advertising on the privacy of DuckDuckGo, which lacked any tools for tracking users from the very beginning. It turned out that the strict privacy policy, which was incomparable to the ones from Google, Yahoo and other bosses of the IT industry, ended up to be one of the main selling points that helped to boost the popularity of DuckDuckGo. In the user's eyes it quickly turned from an ugly duckling into a beautiful swan.
In 2011, Weinberg`s project was funded by a major investor who provided $3 million for promotion and further development. At the same time, the owner of Union Square Ventures (the investor company) later admitted that he helped the project due to his belief in the need for privacy and did not even dream that DuckDuckGo would ever suppressGoogle. He had quite different a target in his mind: to enable every user to search for information on the Internet safely and anonymously, without of the fear of surveillance from advertising companies and government authorities.
How does DuckDuckGo differ from Google?
The main goal of DuckDuckGo is the real, non-fictitious depersonalization of user information. Majority of search engines track users' personal information and preferences and then transmit it to the advertising companies. According to Google`s representatives, they do it in the "impersonal" form, i.e. without of any actual reference to a particular account and person. However, it is unlikely that anyone can prevent search engines from personalizing such information upon request, and as a result of that, not just the advertising services, but also law enforcement agencies will know everything about you: which websites do you visit, where do you live[NA1] , who do you communicate with, etc.
How does DuckDuckGo help you to maintain your online privacy?
DuckDuckGo widely supports privacy software. For example, the search engine is fully compatible with the Tor browser and is even built into it as the default search engine (Firefox and Chrome have also allowed you to set DuckDuckGo as the default search engine).[NA2] Last year DuckDuckGo allocated $600 000 to services, that help to protect the securityrights of the world wide web users, and a large fraction of this money went to the developers of "Tor" browser.
DuckDuckGo does not care about national restrictions either: the search engine does not block any links to the resources that seem shady in terms of a particular country's legislation, so you can be sure that you will be able to find the exact information that you are looking for. Is it convenient? Absolutely! We all know how certain websites might become blocked completely undeservedly.
Literally, on March 5, 2020, DuckDuckGo shocked the Internet audience by publishing a list of thousands of web trackers who spy on users without their consent. The leader in the number of spy trackers on the Internet was Google: the “tentacles” of this search giant were seen on 85% of the analysed sites. The second place in this dubious rating with a significant lag is occupied by the brainchild of Mark Zuckerberg, Facebook, whose trackers were found at 36% of the examined websites. Zuckerberg stated at a security conference held in Munich in February 2020, there was a need to create the measures, that would intervene in the user’s activity in order to remove content that is dangerous. In his opiniontrackers were designated to care about the user and to filter exclusively safe content.
So, what do these trackers do? They are programmed to collect all of the information about you: your gender, age, location, type of your computer or mobile device. And even finding out your name is a piece of cake to some of them. In return, you get a candy bar in the form of "personalized search results" for your virtual account. However, why do you need virtual accounts and personalized search results if the search engine can handle your requests without them? That's right: they are needed to make it easier to track you and to present you the content that the search engine believes should be most relevant to you. But their usefulness is questionable, not to mention that many people are simply annoyed by the pile of additional (usually advertising) information offered by trackers for your requests. DuckDuckGo also has a free app and a web browser extension that helps you to protect yourself from spyware trackers.
So, do you still wish to provide detailed information about yourself to Internet companies that will then sell it to any interested third party? We don't want to either, so we opted for DuckDuckGo a long time ago. And we are not alone: many famous Internet pioneers also are on the "duck side". For example, the Twitter founder, Jack Dorsey, has recently confessed his love for DuckDuckGo search engine.
What does DuckDuckGo make money on?
The service only tolerates few ways of fair income, like earning from advertising. " Do they still track us?"- the frightened user will think. We hasten to reassure you: no, they do not, because this ad is simply designed to match the user`s query and is automatically selected by the service. For example, if you type "Shoes on sale in London", the search engine will give you an advertising banner from the appropriate partner within the desired area. And this is the only "tracking" script that DuckDuckGo has. Moreover, we did not put surveillance in quotation marks in vain: the search engine will not receive any information about you, except for the actual request. Besides, your search history is also not stored anywhere, every time you log in to DuckDuckGo your search begins from scratch.
Another way for a company to generate revenue is commission for clicks on links from partner sites. Everything is fair here too: you do not know that a particular site is a partner of DuckDuckGo, and the partner will not get any data about you from the search engine.
Fame is growing
Gabriel Weinberg himself was the only person to handle the project until 2011. Currently, more than 80 employees are working at DuckDuckGo Inc. The search engine's revenue from partner sites in 2015 was estimated at $1 million per year, 3 years later, in 2018, it increased 25x times. It stands to reason that the growth in revenue reflects famousness: if in 2014 the number of search requests made through DuckDuckGo barely reached 2 billion, by 2016 it doubled (4 billion requests per year); in 2018 it exceeded 9 billion, and last year it soared to a record number of 15 billion requests per year.
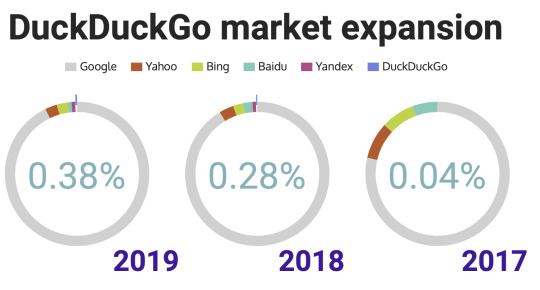
DuckDuckGo appeared next to the top five search engines for the first time only last year, taking a stand-in sixth place at the end of 2019 with 0.38% of the world`s requests. It would seem like a tiny share, but if you consider that Google holds92.04% of the market, then the second place looks quite achievable for DuckDuckGo in the foreseeable future (currentlyit's Yahoo with 2.67%). The search engine is definitely still a niche, as the trend for privacy is not so widespread amongst the majority of Internet users nowadays. However, considering the trend for increasing control over the Internet in many countries of the world today, the potential for growth seems huge, as more and more people find themselves thinking: why should they allow their personal life to be traded? By closing Google, Yahoo, Bing and other search engines stuffed with trackers, people who really value anonymity are now switching to DuckDuckGo.
0 notes
Text
Have you met your digital "shadow"?

By reading this text you have already left your digital record. Information on your current location and the operating system you use has already been stored in a global array, and this data can be used both for a good purpose and for importunate advertisers or computer trespassers.
Let's be true to ourselves: nowadays it is nearly impossible to stay below the radar without leaving any digital footprints. Whatever you're doing with your smartphone or laptop, all of your operations are constantly recorded. Moreover, not just the average well-known “smart devices”, like the Amazon Echo smart speaker or smartwatches, can serve as a source of important information, but also, for example, a smart TV, a fitness tracker or a subway pass. The number of your digital footprints is growing every day, shaping your “digital shadow” - a digital “portrait” of your personality. A portrait, that stands up very closely to the original.
The story behind Big data.
Your “digital shadow” is the source for key components of Big data - an inalienable part of the era of modern information technologies, social networks, and mass media. Big Data is a combination of technologies for obtaining, storing and processing information, both structured and unstructured, first and foremost, the very information footprints. The commercial use of Big Data was underway somewhere about 10 years ago. Technology companies such as Google, Yahoo, and then Facebook, Amazon, eBay, and others were the first to have mastered the use of this technology. The skill to process digital footprints has allowed these companies to reach a new level of awareness on the customers’ needs, often even outreaching the possibilities of intelligence services.
Big data is used by government agencies in research and strategic forecasting and by businesses to build the right sales strategy or advertising campaign. Your digital footprints provide information for business solutions such as personalization of product offers on the web, content on websites or apps and e-mail newsletters. As these technologies improve, they will be applied even more widely in fields such as health, transport infrastructure, and security, etc.
Your digital footprint.
Big data also helps to simplify out consumer choice and limit the unwanted information noise. However, our digital footprint is not only used to build useful algorithms for good purposes. It is relatively easy for your business competitors, hackers or government agencies to get access to your "digital shadow". Having thus acquired information that is not usually accessible, they can cause you big trouble. Once in the world wide web, your photos, videos, comments, and unencrypted messages will remain there forever, and interested parties will find a way to trace the information they want to know about you: your current address, place of work, your salary, how do you spend your leisure time, where do you like to travel, what products do you buy, what do you like to eat and drink, what music do you listen to, etc. – almost anything.
Let's take, for example, the case with your credit card transactions. First of all, many banks delegate SMS delivery services to third parties, who then collect data on your income and expenses. Secondly, during the transaction, the bank receives a lot of additional data from the outlet - location, price, type of goods, date, time, etc. And with this information on hand, the system can determine where you live, what stores you go to, where you work, your working hours, your transportation preferences, and even whether you have a chronic illness. Suppose in the morning you've made a purchase in a store near your residence (showing your daily schedule, shopping preferences), filled up the car on the way to work (your transportation map), made transactions at work (your place of work), then in the evening dropped by the pharmacy to buy some prescriptions and baby diapers (showing your working hours, illnesses, and that you have a child of a certain age). Or, if you spend more money on purchases than you receive on the card as a salary, indicating that you might have some undeclared income, and so on.
Admit it, this information is comprehensive. Subsequently, this data often leaks outside or gets transferred or sold to third parties. And it’s good if they fall into the hands of marketing specialists and advertisers', and not to scammers, tax authorities or security services.
Another example is determining your contact network based on digital footprints in social networks. Even if you do not specify, for example, the school you graduated from or your place of work, interested parties can still track down your connections via your friend lists (30% of your friends are from school X, and 40% work at Bank Y, respectively, according to this information, they can assume where you studied and work) and, again, use this information with a mercenary motive.
Digital "hygiene".
Is it possible to avoid such outcomes or at least to minimize their possibility? You can but to a certain degree. The principle is simple - the less digital footprints you leave online, and the less you are “of interest” to outsiders, the safer you are. Here are some tips that might help you to protect your identity:
1) when registering on social networks, websites, and apps, use a temporary email address or phone number;
2) do not disclose the e-mail address that you use for social networks in open sources;
3) if possible, keep your profiles and friend lists private;
4) regularly clear your browser cache;
5) prohibit saving cookies (they help to track your web browsing history);
6) use different and encrypted web browsers for different operations (for private e-mails, online shopping, etc.);
7) use Ad-blocker (partially protects against the hidden programs);
8) use messengers and e-mail services with End-to-end encryption instead of social networks for the exchange of personal correspondence and information;
9) use a VPN service or a browser with a built-in VPN to access the Internet;
10) use an up-to-date antivirus (it protects not only from viruses, but also from keyloggers, which allow trespassers to get your "fingerprints" of entered passwords and messages, and some might even connect to a webcam);
11) you can use cash instead of cards and keep down online purchases.
All of the mentioned methods are useful and might reduce the likelihood of unauthorized use of your data, but they do not guarantee a 100% result. The only real way to avoid this is to get rid of your computer and smartphone and eliminate interaction with the worldwide web. As you might agree, this method is way too drastic and not suitable for most of us.
It makes much more sense to comply with the listed rules of digital "hygiene", without trying to get rid of your digital shadow completely, but to create its positive image and use it to your advantage. Bear in mind, that a significant part of modern employers and educational institutions do a so-called reputation analysis before interacting with you. Your social media profiles, comments, and activities are reviewed and evaluated, directly linking your digital identity to the real one.
Moreover, governmental agencies and security services have long been systematically moving towards creating what can be called a system of social profiles – a full-scale dossier on every citizen, created based on existing offline databases and digital footprints. You may agree that in both cases, the complete absence of a digital shadow or its negative nature can compromise you.
Therefore, it is best for all of us to gradually and consistently create a positive image in the digital world. While performing any operation on the network, consider the consequences, act anonymously, accentuate your good points, and keep an eye on your reputation. Correcting your negative image on the world wide web is not easy. It means, that the necessity of creating your positive network image, a bright “digital shadow”, should start with the very first steps in the global information network.
0 notes
Text
Tinder knows your private life better

Today’s attention will be focused on Tinder, the most popular dating app, that had over 57 million people at the beginning of 2020, out of which 5.9 million were premium-accounts (https://www.businessofapps.com/data/tinder-statistics/). The app uses your current location to search for nearby people who want to meet.
Each user's swiping can give either a like or a dislike to other people’s photos (swipe to the right = “like”, to the left = “dislike”). Only users who indicate a mutual interest towards each other are allowed to chat. In 2012, when Tinder was launched, no other app offered such functionality.
Nowadays, Tinder is available on iOS, Android, and as a desktop version. Initially, it required the user to have a Facebook account to login, but since August 2019 it started to allow registration with a phone number.
Tinder aims at being a top Dating app and had recently added a new feature - Panic button. It works the following way: you type your date location and the app starts to follow your movements. If any threat to the user’s safety occurs, the user clicks on the Panic button. This triggers a request to the police, and they use the GPS signal to urgently arrive on the spot (if the Panic button is pressed by a mistake, then it would require to ender a special code to stop the alert).
What kind of user information does Tinder collect?
At first, everything looks pretty basic. Upon registration, Tinder collects the user’s name, password, and some basic information, like gender, age, and location. Other private data can be presented on the user’s consent.
Tinder’s services also store information about the devices you log in with, the type of connection used (wired or wireless, speed, provider), and, of course, allows you to save “cookies” (script fragments that keep user's settings on the website), but they can be switched off if the browser supports this feature or if there is a special extension.
But more importantly, if we examine the Tinder's Privacy Policy it clearly states that the company reserves the right to process your chats with other users and the contents that you publish, explaining such actions to be usual for the proper functioning of Tinder service. In fact, this recognizes, that the developers are authorized to read the user's correspondence.
(https://www.gotinder.com/privacy?locale=eng#information-we-collect).

How Tinder uses collected data?
Privacy Policy also states the data is collected "in order to ensure your safety and provide advertising that may interest you." Thus, the fact of collecting user data for the purpose of its sale to third parties (ad networks) is not denied either.
Tinder has been attacked for such unclear explanations by a number of public and governmental organizations. For example, the Norwegian Consumer Council writes that the "legalese-filled documents sometimes do not provide a complete picture of what is happening with a person's personal information|. Third parties that can access the personal data of users, the Council writes, are often not indicated (as is the case with Tinder). And if third parties are listed, the user should read the privacy policies of these third parties to understand how they can use his data.

https://www.npr.org/2020/01/14/796427696/study-grindr-tindr-and-other-apps-share-sensitive-personal-data-with-advertisers
“In other words,” the authors of the study of popular applications go on saying, “the user can hardly even get the simplest idea of what his data is, to whom and how it can be transmitted and how it is used even by the application itself.” Norwegian public figures emphasized that "data harvesting, according to the Norwegian government agency, appears to violate the European Union's rules intended to protect people's online data, known as the General Data Protection Regulation". Representatives of American organizations and, in particular, Public Citizen, a group of specialists under the US government that defends the rights of citizens, agree with them. This organization requires the United States to introduce as stringent laws as the above-mentioned European regulation, which was adopted in 2018.
To whom does Tinder transfers information about users and what are the associated risks
So, who are these “third parties” to whom Tinder sells user data? We are obviously talking about advertising networks like Google, Facebook, and other corporations that focus on targeted advertising. The advertisement industry is, indeed, interested as much as possible in any accessible information about internet users, including their intimate penchants and sexual orientation, which Tinder would gladly share with the advertisers. Human rights organizations have already sounded the alarm. So, in November 2019, Amnesty International published an article entitled “Facebook and Google’s pervasive surveillance poses an unprecedented danger to human rights.”
https://www.amnesty.org/en/latest/news/2019/11/google-facebook-surveillance-privacy/
Amnesty International head, Kumi Naidu said: “Google and Facebook dominate our modern lives – amassing unparalleled power over the digital world by harvesting and monetizing the personal data of billions of people. Their insidious control of our digital lives undermines the very essence of privacy and is one of the defining human rights challenges of our era. The internet is vital for people to enjoy many of their rights, yet billions of people have no meaningful choice but to access this public space on terms dictated by Facebook and Google. To protect the key human values in the digital age - dignity, independence, confidentiality - it is necessary to drastically revise the working methods of the digital industry giants and move to the Internet grounded on human rights. ”

Google and Facebook platforms rely on algorithmic programs that process a great deal of data to get the most detailed user characteristics based on their online experience. Advertisers then pay Facebook and Google to show advertisements that companies need. “We already know,” Kumi Naidu goes on, “that the vast advertising systems of Google and Facebook are powerful weapons in the wrong hands. Not only can they be used improperly for political purposes, which may lead to disastrous consequences for society, they also allow all kinds of exploitative advertising methods, such as hunting people who are struggling with illnesses, emotionally unbalanced, or suffering from one or another addiction. As such ads are intended for individuals, they are hidden from public control. ”
Tinder provides Facebook and Google services with very intimate data: this is a dating application, as we know, so it means that many users indicate in their profiles things that are usually disguised to publicity. Advertisers receive this confidential information completely free of charge.
One can imagine what puzzles of Tinder users are formed by ad networks collecting information about them and many other channels. These corporations are surely limited by laws on non-disclosure of users' personal data, but the information collected still allots them of a wide area for manipulating people's actions even via advertising.
0 notes
Text
Overton Window in Action: How the pandemic is used to restrict our freedom

In a recent interview that Edward Snowden gave to Shane Smith, the head of an independent journalism agency VICE Media, he spoke about the long-term consequences that emergency powers received by governments in response to the coronavirus pandemic would have. The cybersecurity expert said in particular:
«As authoritarianism spreads, as emergency laws proliferate, as we sacrifice our rights, we also sacrifice our capability to arrest the slide into a less liberal and less free world. Do you truly believe that when the first wave, this second wave, the 16th wave of the coronavirus is a long-forgotten memory, that these capabilities will not be kept? That these datasets will not be kept? Will those capabilities begin to be applied to small-time criminality, for political analysis, for doing things like performing a census, political polling. No matter how it is being used, what is being built is the architecture of oppression.».
Snowden knows what he is talking about because it was he who, in his time risking his own life, revealed the extent of espionage at the U.S. National Security Agency, which gained unprecedented powers to monitor citizens after the horrific 9/11 attacks (September 11, 2001) as part of the so-called "Patriotic Act," a federal law passed in October 2001 by the U.S. government. Edward Snowden had previously warned that increased surveillance in the coronavirus crisis could have long-term negative consequences for civil liberties.
Fear of the virus spreading could cause governments to send a request for pulse or heart rate data to each fitness tracker and require access to that data.
"Five years later, when the coronavirus leaves", - Snowden argues, "that data will still be available to them, and they will begin collecting new ones. They already know what you're looking at online, they're already tracking your movements on the phone, now they've learned what your pulse is. What happens when they work with that information and use artificial intelligence?»
There is no doubt that the total surveillance and manipulation of people is desired by the authorities and will be explained by concern for the safety of citizens. Can ordinary citizens do something about it? The necessary minimum is not to succumb to the initiatives of the authorities to establish digital control. Of course, so far "digital control measures" look quite comical, but citizens various countries around the world have already swallowed the restriction of their freedom. Quite possibly, it was a toe in the water to look at the reaction of the citizens, who so far behave like a frog, which, without feeling the danger of being gradually heated, stayed in a pan of water until it was completely boiled.

Politicians, apparently, once again learned ideas from fantasy authors: we will remember the already iconic film "V for Vendetta", that was inspired by the comic books of Alan Moore. To enslave the population, the government first launched a virus, and under the pretext of an epidemic, the authorities declared a total quarantine with a curfew, and violations of the regime were severely punished by the security service of Norsefire, the totalitarian ruling party. It is instructive that some of the viewers who watched the film accused the author of the script of being unrealistic and claimed that "revolutions take place in other scenarios," but everything is known to be checked by time. We don't have to wait for Guy Fox yet - it's enough to get organized and get the authorities to comply with the laws before they cross that very line.
0 notes
Text
Encryption: Your Introduction to Digital Security
In the modern world of free communication encryption is a tool that is can be used everywhere, and at the same time it may not always be noticeable. You might not know anything about encryption, but it is present in the lives of most ordinary internet users when you visit usual websites or when chatting in messengers.
Encryption is a transformation of information, whether it is data or a message, by using a special algorithm, that makes information unreadable to unauthorized users to whom it is not intended. And the cipher itself is already a set of algorithms: some are used to encrypt the data, others are used to decrypt it using a special “key”.
Encryption is mainly used for the secure storage of important data in unreliable sources (cloud-based storages, hard disks, etc.) and for confidential communication via insecure channels (for example, the Internet or mobile communications network). Encryption can also be used to verify the authenticity of the message's authorship and a digital signature.
Encryption technologies that are used properly can solve the three main tasks of ensuring information security during transmission or storage:
• Secrecy: hiding information from unwanted eyes.
• Integrity: preventing information from changing.
• Authentication: to authenticate the source of information, to confirm the fact that the data was sent by the expected sender.
Two main encryption methods are used during the data transition through the network: Transport Layer Security (TLS) encryption and End-to-end encryption. When choosing the method that is right for you, it is important to determine whether you trust the “intermediary” - the service, application or website where the transfer takes place.
- Transport Layer Security (TLS) encryption
The basic principle of Transport Layer Security encryption is that the information from your device (computer or smartphone) is transmitted to the “intermediary” server in an encrypted form, and from there to the recipient’s device, but your messages and data are stored on servers where they can be decrypted and read at the request of, for example, server moderators and law enforcement agencies or become available to hackers in an event of a data leak.

This conditionally secure method of data transfer is offered by many popular applications. TLS encryption is also widely used by a huge number of websites that start with “https://” in the address bar. They are well known to users of online stores and other resources that use the transfer of confidential data, such as banking cards details. This data remains inaccessible to hackers throughout the process of transmitting it over the network, but it may become a matter of leakage from the server. By the way, same applies to today's popular Virtual Private Networks (VPN), where your information can be read by the VPN service provider.
- End-to-end encryption
If you trust the service provider and the technical security of its servers unconditionally, then you may well be limited to TLS encryption. However, if it is not the case, then a much higher level of security can be provided by End-to-end encryption. With End-to-end encryption, your message in the messenger or by e-mail is transmitted in an encrypted form and remains encrypted during the entire data transfer process. Only the final recipient can decrypt and read it, and only if the decryption “key” is present in his device. The content of the message is inaccessible to anyone without the key: it cannot be read not only by the messaging service employees, by the representatives of law enforcement agencies or by hackers who have managed to gain access to the channel, nor even by the developers of the encryption technology themselves.

For example, applications that use End-to-end encryption technology include such well-known services as Signal and Wire messengers, Mozilla Firefox browser, ProtonMail mailing system and Sync.com and Mega cloud storages.
Let’s suppose, that you have chosen the method of encryption that suits you. Your communication in the network is reliably protected: text and files in your messenger, sensitive business information in your e-mails, etc. But bear in mind, that all of these efforts can end up as a waste of energy if the storage itself is not protected - the mobile device, laptop or server. After all, in the case of a device hack it would be easy for the hackers to get to the full history of communication and all of the file archives and private “keys”.
This is where file encryption comes to the rescue. To make it even more reliable, full encryption of the device can be implemented – of the computer’s hard drive, smartphone`s memory, and external media, etc. As the name implies, the entire contents of the disk or your smartphone will be encrypted and access to it will be possible only by entering a password, fingerprint or other even more technological authentication method.
However, do not forget that the choice of a particular encryption method and the protection of data warehouses is not an absolute way to protect your information. It is always important to remember, that the main key to all of your information lays in your password. A weak password dramatically increases the chance of hacking and data leaks. In all other cases, using the available encryption and crypto-security tools to protect yourself and your data is quite real. The main thing is to determine how important is privacy to you and, based on that, to choose the right methods of information protection.
0 notes
Text
About Data Privacy Coalition
Data Privacy Coalition is an international non-profit information community.Our task is to shed the light on the issues of cybersecurity and personal data protection and to teach the average internet-user the art of countering hacker attacks, as well as minimizing the risk of information leaks and Internet-frauds.
In our crusade for data privacy we strive to expand the topic of information security issues beyond the narrow circle of IT-specialists and to outline the main problems of securing digital information.
In our articles we will explain the reason why is the topic of personal data protection so important for each and every one of us today; we will analyze how small are the boundaries of privacy in the modern world; describe who and how can steal your data and how it can be used against us and explain how to protect ourselves and our loved ones from such unpleasant incidents.
1 note
·
View note

