Text
Peer Feedback
Some of my peers (in and out of my tutorial) have had interesting posts up from their blogs, and I’ve really felt enlightened reading through them. Here are a few snippets of the feedback I’ve given them.






I also received feedback from my peers for my post on ‘How to Steal a Penguin”

0 notes
Text
This is a pretty awesome Project! Congratulations on getting to your Distinction Mark! Reading through your reflection shows you have explored and learned a tremendous load from through this journey. Good Luck on your presentation!
Final Assessment of Project
The Goal
The purpose of my project as defined in my proposal was:
To learn the skills necessary to reverse engineer and perform malware analysis
The Plan
To achieve that goal. I developed a plan that centered on studying “Practical Malware Analysis” and completing hands-on labs. Before this project, I didn’t have any experience in malware analysis.
What was achieved?
I can proudly say I succeeded in:
Setup and configuration of the virtual laboratory
Learning 5 chapters of content
Completing labs for each chapter
Blog extensively on the malware analysis I conducted
I had successively completed all the necessary components to achieve a distinction in my original criteria.
Obstacles
I faced several obstacles while completing my project
1. Proposal error
For my High Distinction criteria, I was ambitious and hoped to undertake a mock analysis of a malware of my choice. However, it seemed as I misunderstood the deadline.
I had thought we had until Week 10 to complete our Something Awesome. Within the 5 weeks. I had put in over 30 hours of work towards my Something Awesome Project. It was not feasible to force the HD mock analysis in. I had to let it go and revise my proposal.
2. Book design
While the introduction of the book stated that each chapter had about three labs. Once I begin completing exercises. It didn’t seem to be the case.
Chapter 2 involved the major setup of the virtual environment
Chapter 5 contained a lab that contained 21 questions!
I had to adjust my approach to the book design.
3. Age of the book
The book is old. Even thought it’s still the most commonly recommended book to malware analysis. It shows it’s age at places. I had to research for new software, installation methods and assumed knowledge. While I scattered some of that research into my lab blogs. I also had separate blogs for dedicated research on important topics.
Final Verdict
I couldn’t be more pleased with my project. It was many hours of work but I felt I I had learnt so much. I will continue this book even after the course is over. Furthermore, I’ll be presenting my Something Awesome Project to my class next week!
4 notes
·
View notes
Text
Glad to see you have achieve your main goals from your Something Awesome Project! I remember your proposal idea and you explaining it to me, and seeing your final reflection shows you have come a long way. Looking at the disadvantages, yes, I believe addressing the need of a USB with larger storage, having faster copy speeds and cross-OS compatibility are key points to improve on carrying this project forward. I hope you continue to research on this!
Something Awesome Update
Overall, the USB copier works well in terms of its effectiveness. It does what it is intended to do and also discreetly. Below I’ve further evaluated it’s effectiveness by listing both its advantages and disadvantages:
Advantages
steal information easily
can steal specific information (looking at certain folders)
get data without much work (just plug in the USB)
small and portable
alternate method to backup your own computer
Disadvantages
illegal
need a USB with large storage if you plan on copying every file
takes a while to copy a tremendous amount of data
need to be discreet yourself in taking the data
works only on Windows operating systems
By looking at the disadvantages, we can try to improve the USB copier by using smaller and more compact USBs, selectingn USBs with faster transfer speeds as well as looking into more system compatible coding to reach out to other operating systems instead of just Windows.
1 note
·
View note
Text
I think this is a fantastic project! Given your background in Psychology studies, it will be interesting to see your take on this. I agree with you on the current state of security in airports. Specially when flying Domestic flights, as security screening is far less as compared to international flights.
[SOMETHING AWESOME SEGMENT]: The Role of Intelligence and Forensic Psychology in Aviation Security
It is extremely worrying to realize that the US’s TSA (Transport Security Administration) has had ridiculously high failure rates in detecting dangerous material consecutively in 2015 (95.7%), 2016 and 2017 (80%). The tests performed to reveal this unsettling statistic were by an undercover red team that evaluated the effectiveness of US’s airport security equipment. In 2015, it was found that 67 out of 70 firearms and explosives bypassed the security screenings. Adding on to the fact that a $7 billion budget goes to the TSA annually, it simply seems too bad to be true. Bruce Schneier has pointed out that this should not be surprising, since TSA has a history of above 50% failure rate since 2003.
I also remember reading about one of his essays on airport security from a book that complied them, where he criticized the pointlessness of banning and restricting items/materials that can be brought through customs. He reasoned that no matter what is banned, terrorists and any threat actors could still find other ways to achieve the same objective, such that restrictions only prevent what has happened in the past. This means that it does not prevent what has yet to have happened in the future, this approach fails in its strategy to protect against the unforeseeable, it can only counteract known dangers. To make matters worse, not only does this not solve the problem, it also makes travelling much more convenient every time restrictive changes are made to regulations (for some people, getting past TSA is so annoying that it is a strong enough reason that they avoid travelling). These criticism sounds analogous to the arguments against the ignorant logic behind Australia’s anti-encryption bill.
One conclusion that can be drawn from this, is that airport security is not necessarily as adequate as we like to expect it is. Fortunately, if there is one potential improvement to be implemented, it would be shifting the focus more to ‘intelligence work’. Israel’s Ben Gurion airport is infamous for its extremely time-consuming and stringent security. Being considered as having the toughest airport security in the world, this reputation comes from the fact that they prioritize assessing the risk of every individual thoroughly from start to finish. Examples of their procedures include, intensive interviews and ethnicity profiling. There are many controversies surrounding their security practices and while it is proven to be extremely effective, concerns on human rights have been brought to attention.
Nevertheless, their accomplishments in protecting against threats demonstrates the utility of intelligence work. As such, I have decided to incorporate research from forensic psychology into aviation security, by writing a report to address a hypothetical brief provided by the Australian Security Intelligence Organization (ASIO). The brief is based on the topic of deception detection, as it could be used to analyse communications with potential threat actors (including criminals, terrorists, foreign spies, as well as insider threats). I have set the following as the requested objectives from ASIO: - Methods for accurately detecting when a human intelligence target is deceptive under a situation where they can be interviewed or through agents engaged in conversations while undercover - Guidelines for analyzing provided information by the target and discerning truth from lies - Evaluate validity of techniques used for judgement and the effectiveness of training programs
My written report is an attempt to provide guidelines and recommendations based on psychological research, backed up by empirical experimental evidence, that sheds light on how well we can tell if someone is lying or if they are telling the truth. Since, there is a vast amount of research on this, I do not have the time to read through dozens of papers to check what are the best techniques for lie-detection, instead I have just included ones that work quite well. So what I have proposed in the report are only a limited aspect to the broader scope of deception detection (it is a really complex topic and hard to do!).
Link to Report: https://www.scribd.com/document/419963141/Deception-Detection-Report
SOURCES:
https://www.tsa.gov/news/releases/2016/01/21/tsa-releases-2015-statistics
https://www.schneier.com/essays/archives/2015/06/why_are_we_spending_.html
https://www.schneier.com/essays/archives/2010/11/a_waste_of_money_and.html
https://www.huffpost.com/entry/what-israeli-airport-secu_b_4978149
https://www.youtube.com/watch?v=1Y1kJpHBn50
Deception Detection Report by Azura Ye on Scribd
2 notes
·
View notes
Text
Spot the Fake Handbag
(Week 8 Activity)
Designer handbags are beautiful no doubt, you pay the price for quality material and touch of class and time taken to handcraft each piece. But what has always been interesting for me is to see the almost exact (well pretty much exact to most eyes) fake being sold in markets in certain parts of the world for largely lesser prices. If you are a fashion enthusiast and pay attention to touch and feel of the material, sure you would find a way to unspool yourself. But for majority of the folks, you just wouldn’t be able to say. I remember walking through a street market on holiday and we came across a store that sold ‘designer handbags’ at non-designer prices - your first thought? PECULIAR. But looking close, you couldn’t say the difference unless you held the original by its side to observe subtle changes in pattern position, or the stitch used, the shine of a buckle, or the way the logo was placed.
I think it is an art of its own!
0 notes
Text
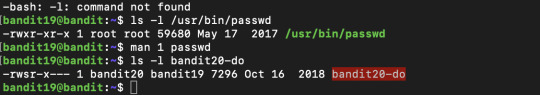
Bandit Level 19 --> Level 20
To gain access to the next level, you should use the setuid binary in the homedirectory. Execute it without arguments to find out how to use it. The password for this level can be found in the usual place (/etc/bandit_pass), after you have used the setuid binary.
For this challenge, I had to research on setuid:
setuid is a linux command which allows any unprivileged user (anyone but the owner user or group of the program) to acquire temporary privileged permission to execute the given program/s. This poses a security risk, as anyone can now execute or alter the program, hence someone can spread malicious bugs through this executable program.
The ‘s’ permission icon states that special permission setuid has been activated as :
-rws------ setuid for a user ----rws--- for setgid for groups
This challenge spec states the home directory has a setuid binary that has to be run. I was confused at how to use the binary at first, as I was not sure about ‘id’ even though I understood the functionality of the command in general, so I had to play with every possibility until I realised where I was going wrong with usage. At the end, a simple ‘cat’ saved the day!
So using the setuid binary given, I changed my current id to act as the owner – which in this case is ‘bandit20’.
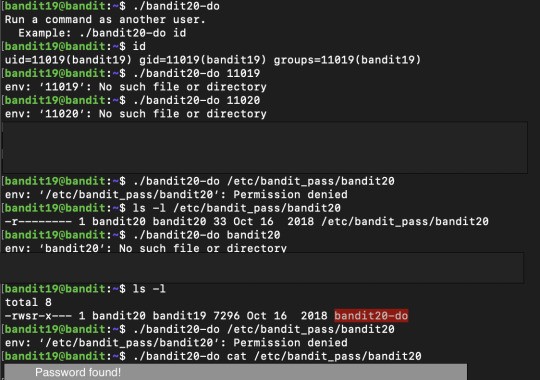
0 notes
Text
Bandit Level 18 --> Level 19
This challenge was a bit frustrating, I kept getting logged out automatically when trying to log in to the system.
.bashrc is a shell script that loads every time you launch BASH interactively. this script is found in the user’s home directory and can be edited. My first instinct was to open and edit it, but I wasn’t quite sure of how to do it. .bashrc is used to load all the user’s terminal preferences and environment variables when the terminal is launched.
Therefore, I had to find a way to get what I needed, without actually getting in to the server! How to solve this? For some reason , I feel like I may have solved this the cheeky way! I might want to check and see of there was another way of solving it! I used:
ssh [email protected] -p 2220 cat readme
means then the .bashrc file wouldn’t have to run!

0 notes
Text
Bandit Level 17 --> Level 18
There are 2 files in the homedirectory: passwords.old and passwords.new. The password for the next level is in passwords.new and is the only line that has been changed between passwords.old and passwords.new
This one was relatively simple.
The diff command prints intsructions on how to change/add/delete lines in the first file to match the second file. Since the password is contained in the .new file (and the only difference), we set it to be the first file.
The diff instructions then state that the line in the first file must be changed to match the same line position in the second file. Hence this is single line has to be the new password!

0 notes
Text
Bandit Level 16 --> Level 17
The credentials for the next level can be retrieved by submitting the password of the current level to a port on localhost in the range 31000 to 32000. First find out which of these ports have a server listening on them. Then find out which of those speak SSL and which don’t. There is only 1 server that will give the next credentials, the others will simply send back to you whatever you send to it.

Once inside, I first had to see what ports I had running currently. Initially I had no idea how to do this, but I started by researching on the given suggested commands. I then realised using nmap to scan target hosts, outputs a port table with each ports state currently. nmap (network mapper) alongside many other behaviours, is a tool used to scan ports. It does this by sending raw packets to available ports, and listening to see which ones are open or closed or any other state.
Once I got the states of the ports, I ran the same openssl command from before to check which ports returned the new password.
The first of the two possible ports returned the same passcode I entered, hence they weren’t the correct ones.
The next (last) port worked and gave me an ssh private RSA key to get the ssh key needed to login to Bandit17. Going ahead, I had to add the RSA private key given into a .pem file and use ssh -i to login with it.


0 notes
Text
Understanding Digital Certificates
When I was browsing through some news websites, I happen to click on the secure padlock icon next to the website name (by accident!) and out popped the Public Key Certificate for the website. Lets have a look at what's happening here.


A public key certificate is an electronic document that proves that the website has a public key that can be used to communicate with it. This certificate is basically an SSL certificate (now more known as a TLS - Transport Layer Security) certificate. When you access a website, your browser looks for a SSL certificate on the server end in order to create a secure communication link between you and the website, so that no one else can tamper with the information you are passing through. This is when you see an ‘https://’ on the site url - which indicates that the connection is secure with the SSL protocol and a padlock icon aside it. This is specially mandatory when you are sharing credit card details to this website when shopping online for example.

The certificate typically shows the following:
The details of the subject (the owner of the website/server), where the certificate binds the hostname with the domain name, organisation name and location. Alongside other details about the key (algorithms, validity period etc), it also states the digital signature by the issuer. The issuer should typically be a Certificate Authority who most browsers trust. GlobalSign (like above) is very well trusted by browsers like Chrome, Safari, Firefox etc to be a valid issuer of trusted certificates. A device/ browser trusts a CA when it’s root certificate is embedded/ present in the end user device. On the other hand if a browser sees that a certain digital certificate is self-signed - it’s usually seen as a dodgy sign and the user notified that the website can’t be trusted. When the browser sees the signature of a trusted issuer on the certificate, the browser uses the public key to securely communicate with the server.
0 notes
Text
Security Everywhere #6: Educating others
I wrote up a post on password security for my College group and posted in our Facebook group, in order to advice them. Some of the tips are general ones we all know of, but there are some who need to be reminded!
There were a lot of lunchtime/ dinnertime discussions over the topic so I was really happy and glad I had them talking and getting enlightened!
(I have blocked names for security purposes).



1 note
·
View note
Text
Case Study #7: do we like Surveillance?
For Week 7, we were given the classic topic of ‘Privacy’, the class was to debate on : “should the Government or Government agencies collect and have access to your data for good purposes, or should citizens, e.g. you, have a right to privacy which stops them?” I was on the team that represented the Government. This debate was quite interesting, I felt that the opposing team obviously had a stronger debate, but it was interesting to see things from the governments perspective. For Government Surveillance:
Promote deference - will help to minimise/stop crime as criminals now know they are watched and all traces will be made.
Collected data can be used for growth of the country, using the statistics to analyse pitfalls, improvements needed in relevant sectors etc.
Prevention of attacks of terrorism, organised crime and counter foreign espionage, by tapping into communication lines and filtering in order to catch such attack plans well ahead.
In Medical sectors, it is good to have medical records stored for Doctors in case of emergencies, so that the right action can be taken by just looking at a database.
In the financial sector, it is good to keep financial records of citizens, so that white collar crime can be targeted.
Monitoring social media profiles allows for identifying and destroying fake profiles, fake bots and prevent the circulation of fake news.
Through Government surveillance and data collection, less resources will be needed for police task forces and physical surveillance, and these resources can be used in much needed departments like infrastructure etc.
Track people’s activities, jobs in other countries, so that in the event of a situation, information is at hand for defence.
Against Government Surveillance / Pro Privacy:
Data can be leaked, no matter how good the intention is in collecting it.
Higher risk of an insider attack - a single point of failure.
Data can be collected and sold to other organisations for large sums.
Abuse of Memes using people’s faces! People lose their right to speech - where people with an alternate opinion to the majority or the higher power, will be drowned out or ‘addressed’ for having such an opinion and being a barrier.
The final verdict of the entire class in total was that data collection is not okay, as the authorities have no reason to use it in a good way at all even though stated above. The outcomes of using it the bad way are much more tempting.
0 notes
Text
Bandit Level 15 --> Level 16
The password for the next level can be retrieved by submitting the password of the current level to port 30001 on localhost using SSL encryption.
This challenge was similar to the previous one, but using openssl.
Firstly, I had to familiarise myself with openssl. SSL is the Secure Sockets Layer, which creates a secure encrypted link between you the client, and the remote server you are trying to connect to. To create this connection, an SSL certificate must be issued and the website will begin with ‘https’ where ‘s’stands for SSL. This is a visible indication of the website safety here onward.
Using the following command got me the password to get to the next level:
openssl s_client -connect localhost:30001
s_client creates an ssl client for communicating with a remote server, where once authenticated, the client can have secure interaction with the server. The -connect option must state the host name and the desired port number.. Once fully connected, the two ends can communicate to each other. This is similar to using telnet, but obviously more safer.
When I entered the current level password, it gave me the next password in return.


0 notes
Text
Security Everywhere #5: A digital WatchDog
WatchDog is a app that was created in Sri Lanka following the terrible Easter Terrorist Blasts that took place in Colombo on April 21 2019. Starting from moments after the blasts, the country faced a chaotic rampage of outbursts on social media, news websites and test messages on news updates. Some news were genuine and helpful informing people of the current state of chaos in the country, while others were circulated by sick nasty individuals who just wanted to create more chaos (fake bomb threats, and news based on other disturbing threats). In this state of emergency, people were told to stay indoors and the roads of Colombo and surrounding districts were deserted - and the only way people knew what went on, was by hanging on to the news. Therefore at this point, it was critical to know what to believe and what not to. The aim of the WatchDog was to verify news circulating so that people knew if such news were fake or real.
The app analysed every bit of news post circulating the networks, and matches it to a set of 5 reliable trusted news sources in the country, and if the news was confirmed by any of the sources, the app would post as verified with a green check symbol, and if not identified to be true, is marked as fake News:


I think this is a sheer project of genius - giving the people what they need, at the time they need it the most. It is always reassuring to have a trusted source of information - specially in times of trouble. The emergence of such a resource also helps mitigate the chaotic situation significantly, as fake news spreaders realise they no longer have an audience who would believe them - because the fake news is clearly identified as ‘fake’, instead of only identifying the verified and leaving the rest unanalysed - which I feel is a smart feature.
The app now continues to verify daily news in the country.
0 notes
Text
Encryption vs. Hashing
The main difference between the two is its function.
Encryption is for two-way communication - where data is encrypted with a Public Key and sent over to the receiver who will only be able to use his/her private key to decrypt the message and read the contents. So every time you sent a WhatsApp message to someone, you can be sure your receiver is the only one who will be able to read it because it is only their private key that's able to decrypt the message. (WhatsApp uses End-toEnd Encryption - which makes sure that not even WhatsApp can read message content, since every single message/attachment has a unique lock and key that only the sender and receiver know).
In contrast, Hashing is a one-way street, by definition, it is infeasible to reverse a hash function and get back the original plaintext. This function is therefore mainly used in password storage, where the initially entered password is hashed (with a salt for added security) and stored in the system. Whenever the user enters the password to login, this entered password is taken, salt added, then hashed, and then compared to the initially stored salted password to check if correct. This way, if ever the system was hacked and all passwords were in the hands of the enemy, they are unable to get the plaintext password as it can’t be reversed.
Encryption deals with public and private keys needed to ‘decrypt’ the message, where as Hashing deals with hashing standard algorithms (currently SHA2) that transform an infinite user-entered input to a fixed hash function that is irreversible.
Public Key Cryptography - RSA allows Authentication, while Hashing allows for Integrity.
0 notes
Text
Letter to the Grans.
Dear Grandma and Grandpa,
I hope you are both doing fine since I spoke to you last week. Im writing to you specially regarding a very important and serious topic so I hope you both read this through seriously!
Password security. I know you both have become very active online shoppers since you started using your iPads, so I just wanted to give you a heads-up on a few tips regarding safe shopping and general internet safety - I’ve been heavily inspired after the Cyber Security classes I’v been taking this semester at Uni.
For starters - Never EVER, do any online shopping or any transactions involving giving your credit card details, over a public WiFi system - stick to doing it in a safer WiFi network like your house or at any other relatives or friends house. Make sure these wifi networks are password protected and not open to anyone to join.
When choosing your password for any accounts (even Facebook specially!), here are a few tips:
Don’t use passwords that make sense or which revolve around any information about yourselves - (like our names for example!). You might think they are safe as long as you keep it a secret, but you won’t begin to imagine how easy it is for a hacker to gain this information by one glance of your profile or a scan through your identity details!
Instead you can use these approaches:
Create a random sentence that makes sense to you: ‘grandpamakesomeletteswith4eggs’ and then add uppercase letters, symbols and numbers where necessary like : ‘6randPaMakesOme1ettesWith4e66s’
Another variation would be to create such a long password, and then just pick the starting letters from it and use it as your password: FPMOw4Es
Lastly, and most importantly, make sure you DON’T reuse the same password in multiple account/websites! This is a big risk because if you are hacked in one account, you get hacked in all the other accounts you use the same password for.
I hope this has been helpful! I will check to see if you’ve done well next week.
Love,
R.
0 notes
Text
Spotting Vulnerabilities
(Week 5 Activity)
For this activity, we were given a few Food recipes, and C code programs and asked to spot the vulnerabilities that occur:
Recipe 1: A simple Vanilla Cake
The Recipe does not state then quantities for any of the ingredients. A good cake is all about the right proportions of to ingredients. We are however given the size of the container/s, but how do we know the mixture count overflow? This is a vulnerability.
180 F = 82 C, this is way too low a temperature to bake any cake bug or small!
Recipe 2 - Caramel Slice
No measuring units stated for condensed milk and desiccated coconut. We have no way of knowing the right measure and cannot just assumes the unit follows from the previous.
The recipe does not incorporate the golden syrup even though quantity is mentioned.
Repeated occurrence of weird phrases PLAISTOWE and &semi, thereby making the whole instruction run trustable.
Recipe 3 - Cheese Soufflé
Mentioned cooking time is 30 minutes, but actual recipe only uses 10-15 minutes.
0 notes