Text
💥 𝐅ree 𝐑esourses - 𝐓𝐎𝐏 𝐂𝐲𝐛𝐞𝐫 𝐋𝐚𝗯𝘀 💥
💥 𝐅ree 𝐑esourses - 𝐓𝐎𝐏 𝐂𝐲𝐛𝐞𝐫 𝐋𝐚𝗯𝘀 💥 ✨ Alert to win - https://alf.nu/alert1 ✨ Attack-Defense - https://attackdefense.com ✨ Bancocn - https://bancocn.com ✔ For more content - https://lnkd.in/d2pYU-84 💥 Google CTF - https://lnkd.in/e46drbz8 💥 Hack The Box - https://lnkd.in/ggfAMdQ8 💥 Hackaflag BR - https://hackaflag.com.br/ 🎡 Certified Secure - https://lnkd.in/gBKK-i-s 🎡 CMD Challenge - https://cmdchallenge.com 🎡 CryptoHack - https://cryptohack.org/ 🧶 CTF Komodo Security - https://ctf.komodosec.com 🧶 Ctftime - https://ctftime.org/ 🧶 Cyberdefenders - https://lnkd.in/gCf8v4Ju 🎇 CyberSecLabs - https://lnkd.in/gmyzMXju 🎇 EchoCTF - https://echoctf.red/ 🎇 Exploitation Education - https://exploit.education ✨ Hacker Security - https://lnkd.in/gJbSaY3f ✨ Hacker101 - https://ctf.hacker101.com ✨ Hacking-Lab - https://hacking-lab.com/ 🎡 Hacksplaining - https://lnkd.in/gVd9dNkK 🎡 HackTheBox - https://www.hackthebox.com 🎡 Hackthis - https://www.hackthis.co.uk 🧶 HackXpert - https://hackxpert.com/ 🧶 HSTRIKE - https://hstrike.com 🧶 ImmersiveLabs - https://immersivelabs.com 🎇 LetsDefend- https://letsdefend.io/ 🎇 NewbieContest - https://lnkd.in/gZ4UjDhy 🎇 OSBOXES - http://www.osboxes.org/ 💥 OverTheWire - http://overthewire.org 💥 Penetration Testing Practice Labs - https://lnkd.in/grQev9Kk 💥 PentestIT LAB - https://lab.pentestit.ru ✨ Pentestlab - https://pentesterlab.com ✨ PicoCTF - https://picoctf.com ✨ PortSwigger Web Security Academy - https://lnkd.in/gAPq2ezr 🎡 Practical Pentest Labs - https://lnkd.in/gUSqv6xS 🎡 Pwn college - https://dojo.pwn.college/ 🎡 PWNABLE - https://lnkd.in/gNcyqG64 🧶 RangeForce - https://lnkd.in/gGy3feqt 🧶 Root in Jail - http://rootinjail.com 🧶 Root-Me - https://www.root-me.org 🎇 SANS Challenger - https://lnkd.in/gG-5_ZPF 🎇 SmashTheStack - https://lnkd.in/gMFNTURc 🎇 TCM Security - https://lnkd.in/gbQinqvf 💥 The Cryptopals Crypto Challenges - https://cryptopals.com 💥 Try Hack Me - https://tryhackme.com 💥 Vulnhub - https://www.vulnhub.com ✨ Vulnmachines https://vulnmachines.com/ ✨ W3Challs - https://w3challs.com ✨ WeChall - http://www.wechall.net ✨ Zenk-Security - https://lnkd.in/g_y_p5ha ✨ Webgoat - https://lnkd.in/gjsgegYw
0 notes
Text
Tools every self respecting web app hacker should know
Burp Suite - https://lnkd.in/eFtfsquR OWASP ZAP - https://www.zaproxy.org/ Metasploit Framework - https://lnkd.in/easrNxH9 sqlmap - http://sqlmap.org/ Nmap - https://nmap.org/ Dirbuster - https://lnkd.in/e2Dhy95H WPScan - https://wpscan.org/ Arachni - https://lnkd.in/eXarpd_Y BeEF - https://beefproject.com/ Hydra - https://lnkd.in/e7urwKQr XSSer - https://lnkd.in/eYVuGwQN Sqlninja - https://lnkd.in/eyEC4GV5 Cain and Abel - https://lnkd.in/euP8zMHn Netcat - https://lnkd.in/eD5Kb-3u THC Hydra - https://lnkd.in/e7urwKQr Nikto - https://cirt.net/Nikto2 Skipfish - https://lnkd.in/eRpDzajs Vega - https://subgraph.com/vega/ sqlsus - https://lnkd.in/efriGJFC John the Ripper - https://lnkd.in/eCuPkQXc THC-SSL-DOS - https://lnkd.in/eHjmmeHP Sublist3r - https://lnkd.in/ekaSXnFg Wfuzz - https://lnkd.in/eFaDHnCh Shodan - https://www.shodan.io/ Fiddler - https://lnkd.in/eY8s4ks2 sqlmapgui - https://lnkd.in/eZyYcfg7 Wapiti - https://lnkd.in/eHKsxWEd Yersinia - https://lnkd.in/ef7b5Xdb Tamper Data - https://lnkd.in/e_sDSTRd WebScarab - https://lnkd.in/e4s8jfkp Paros - https://lnkd.in/edQ8j-_S SQL Inject Me - https://lnkd.in/eiSFskuS Acunetix - https://www.acunetix.com/ Nessus - https://lnkd.in/e5NWnhks Grendel-Scan - http://grendel-scan.com/ Ratproxy - https://lnkd.in/eZfuC9Gw IronWASP - https://ironwasp.org/ Websecurify - https://lnkd.in/eahctKey Zed Attack Proxy - https://www.zaproxy.org/ Zenmap - https://nmap.org/zenmap/ NoSQLMap - https://lnkd.in/e3yWAxgC ODAT - https://lnkd.in/eGwGQt4Y X-Forwarded-For Spoofer - https://lnkd.in/eYMa3NHK WebSlayer - https://lnkd.in/en8Ph-6p w3af - https://w3af.org/ Metagoofil - https://lnkd.in/eiAKRXTK Brutus - https://lnkd.in/eTwVG9D6 RainbowCrack - https://lnkd.in/ezAk3GtM THC-Hydra - https://lnkd.in/e7urwKQr Medusa - https://lnkd.in/eqEVfF7z THC-SSL-DOS - https://lnkd.in/e8uwuegc OpenVAS - https://www.openvas.org/ WP-Scan Vulnerability Database - https://wpvulndb.com/ WPScan Desktop - https://wpscan.com/desktop LFI Suite - https://lnkd.in/et3bW5Xz XssPy - https://lnkd.in/eT3HqcjE RIPS - https://www.ripstech.com/ Zenmap - https://nmap.org/zenmap/ WPScan - https://wpscan.org/ Arachni - https://lnkd.in/eXarpd_Y OWASP ZAP - https://www.zaproxy.org/

0 notes
Text
Evil-WinRM: The ultimate WinRM shell for hacking/pentesting Description & Purpose This shell is the ultimate WinRM shell for hacking/pentesting. WinRM

0 notes
Text
Best Cybersecurity Certifications (FREE) (Updated
Best Cybersecurity Certifications (FREE) (Updated ✅1. Introduction to Cybersecurity: https://lnkd.in/ghQY8cKA ✅2. Cybersecurity Essentials: https://lnkd.in/gZe6bf-t ✅3. Networking Essentials: https://lnkd.in/gjipDpgG ✅4. Intro to Information Security by Udacity: https://lnkd.in/ggdYxnUp ✅5. Network Security by Udacity: https://lnkd.in/gSHx2tJQ ✅6. NSE 1,2 & 3: https://lnkd.in/gsQJhn2a ✅7. Information Security by OpenLearn: https://lnkd.in/gvfghKNs ✅8. Network Security by OpenLearn: https://lnkd.in/gS2KWNfN ✅9. Risk Management by Open Learn: https://lnkd.in/gGPTDU2g ✅10. Certified in Cybersecurity℠ - CC: https://lnkd.in/gW3w8Jqu ✅11. CCNA Security Courses: https://lnkd.in/gfby3CR2 ✅12. Network Defense Essentials (NDE): https://lnkd.in/g6mRKt2t ✅13. Ethical Hacking Essentials (EHE): https://lnkd.in/gRBGCud7 ✅14. Digital Forensics Essentials (DFE): https://lnkd.in/gPrkYcDH ✅15. Dark Web, Anonymity, and Cryptocurrency: https://lnkd.in/gUrCCGdf ✅16. Digital Forensics by Open Learn: https://lnkd.in/gdv8emgt ✅17. AWS Cloud Certifications (Cybersecurity) : https://lnkd.in/gaDGWdkm ✅18. Microsoft Learn for Azure: https://lnkd.in/gDpkXiik ✅19. Google Cloud Training: https://lnkd.in/get8rnkh ✅20. Android Bug Bounty Hunting: Hunt Like a Rat: https://lnkd.in/gMNT8saN ✅21.Vulnerability Management: https://lnkd.in/gvNKJnni ✅22. Software Security: https://lnkd.in/gG4P5bkn ✅23. Developing Secure Software: https://lnkd.in/gQRwTzKU ✅24. PortSwigger Web Hacking - https://lnkd.in/eEa-fNfu ✅25. RedTeaming - https://lnkd.in/et_T2DEa ✅26. Splunk - https://lnkd.in/et5bkjeY ✅27. Secure Software Development - https://lnkd.in/ebGpA4wG ✅28. Maryland Software Security - https://lnkd.in/e3z4zFmJ ✅29. Stanford Cyber Resiliency - https://lnkd.in/eg9BM5Bv
0 notes
Text
Phishing Email Analysis Tools (v3 Updated)
Phishing Email Analysis Tools (v3 Updated)
✅1-Email Header Analysis >>
⌘MXToolbox:
https://lnkd.in/gxaGmWcg
⌘MailHeader:
https://mailheader.org/
0 notes
Text
Awesome Malware Development
Click Here
Introduction
This Repo serves as a list of resources for malware development. Note: I am just a learner what i have im sharing some reources can be stupid, you can help me adding things.
Essentials
I would say having some experience with C and assembly going to be good. some resources for C and assmebly.
C for Everyone: Programming Fundamentals
learn-c
C cheatsheet
Architecture 1001: x86-64 Assembly
x86 Assembly
Blogs
Vitali Kremez blog Lot's of Malware related content. 0xPat blog Have an amazing malware development series i would recommend to take a look. zerosum0x0 blog Some good posts. Guitmz blog Dope Maldev Content. TheXcellerator Amazing LKM rookit series and maldev posts.
Talks
Horse Pill: A New Type of Linux Rootkit Not a talk but good LKM rootkit series Good talk on Creating and Countering the Next Generation of Linux Rootkits Kernel Mode Threats and Practical Defenses Alex Ionescu - Advancing the State of UEFI Bootkits BlueHat v18 || Return of the kernel rootkit malware (on windows 10)
Youtube channels
AGDC Services
HQ Malware Content.
TheSphinx
Have an amazing series on Writing your Rat from Scratch.
Joey Abrams
Amazing Malware stuff, have a good code injection series, Linux stuff.
w3w3w3
Have a good LKM rootkit series.
Courses
There are some courses I would love to recommend.
RED TEAM Operator: Malware Development Essentials course | Sektor7
This course will teach you how to become a better ethical hacker, pentester and red teamer by learning malware development. It covers developing droppers, trojans and payload/DLL injectors using some basic C and Intel assembly skills.
RED TEAM Operator: Malware Development Intermediate course
Advanced malware development techniques in Windows, including: API hooking, 32-/64-bit migrations, reflective binaries and more.
RingZerø: Windows Kernel Rootkits: Techniques and Analysis
Key Learnings:
Machine architecture for kernel programmers
Virtual memory management
Interrupts and exceptions
CPU security features
Windows kernel architecture
Kernel components (Ps, Io, Mm, Ob, Se, Cm, etc.)
System mechanisms
Debugging with WinDbg
Rootkit techniques
Driver development
CodeMachine: Windows Kernel Rootkits
Topics:
Kernel Attacks
Kernel Shellcoding
Kernel Hooking and Injection
Kernel Callbacks
Kernel Filtering
Kernel Networking
Virtualization Based Security
Books
The Art of Computer Virus Research and Defense
The Giant Black Book of Computer Viruses
Designing BSD Rootkits: An Introduction to Kernel Hacking
Rootkits and Bootkits
The Antivirus Hackers' Handbook
Free books
Make your own first fud crypter
Read Full - Click-Here
0 notes
Text
Slient-Doc-Pdf-Exploit-Builder-Fud-Malware-Cve
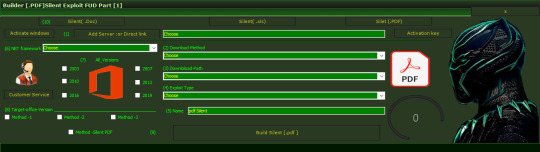
Slient-Doc-Pdf-Exploit-Builder Download
0 notes
Text
Advanced information gathering & OSINT framework for phone numbers

Advanced information gathering & OSINT framework for phone numbers
Download Here GitHub File : Download
0 notes
Text
How to Bypass Certificate Pinning with Frida on an Android App
How to Bypass Certificate Pinning with Frida on an Android App.

Click Here To Read.
0 notes
Text
Understanding security testing for SQL Server environments

Understanding security testing for SQL Server environments
1 note
·
View note
Text
CISCO - Ebooks
CISCO - Ebooks https://mega.nz/folder/LJM1HAII#wzpfc2ikol-_6gIwpFZSTw CCNA - Ebooks https://mega.nz/folder/KF0gWIYD#otYCUUq1Kw8Ho6xH2QQNaQ CCNP - Ebooks https://mega.nz/folder/nA0WHSBA#70_GoJF1hOzZkWbSkkArgA HAPPY learning!
0 notes
Text
HYNTROSPECT This tool is a coverage-guided fuzzer targeting Hyper-V emulated devices, in the...
HYNTROSPECT This tool is a coverage-guided fuzzer targeting Hyper-V emulated devices, in the userland of Hyper-V root partition. Vulnerabilities in that layer coud lead to a guest to root partition escape. https://github.com/googleprojectzero/Hyntrospect

-
1 note
·
View note
Text
PhoneInfoga Advanced information gathering & #OSINT framework for phone...
PhoneInfoga Advanced information gathering & #OSINT framework for phone numbers PhoneInfoga is one of the most advanced tools to scan international phone numbers. It allows you to first gather standard information such as country, area, carrier and line type on any international phone number, then search for footprints on search engines to try to find the VoIP provider or identify the owner. Features: ▫️ Check if phone number exists and has connectivity status with HLR lookups ▫️ Gather standard informations such as country, line type and carrier ▫️ OSINT footprinting using external APIs, Google Hacking, phone books & search engines ▫️ Check for reputation reports, social media, disposable numbers and more ▫️ Use the graphical user interface to run scans from the browser ▫️ Programmatic usage with the REST API and Go modules https://github.com/sundowndev/PhoneInfoga

-
1 note
·
View note
Text
Bifrost A Flask-based HTTP(S) command and control (C2) framework with a web frontend. Malleable...
Bifrost A Flask-based HTTP(S) command and control (C2) framework with a web frontend. Malleable agents written in Go and scripts written in bash. https://github.com/AshleyNikr/Bifrost

GitHub - AshleyNikr/Bifrost: A Flask-based HTTP(S) command and control (C2) framework with a web frontend. Malleable agents written… - GitHub A Flask-based HTTP(S) command and control (C2) framework with a web frontend. Malleable agents written in Go and scripts written in bash. - GitHub - AshleyNikr/Bifrost: A Flask-based HTTP(S) comma…
1 note
·
View note
Text
Hardware and Firmware Security Guidance Guidance for the Spectre, Meltdown, Speculative Store...
Hardware and Firmware Security Guidance Guidance for the Spectre, Meltdown, Speculative Store Bypass, Rogue System Register Read, Lazy FP State Restore, Bounds Check Bypass Store, TLBleed, and L1TF/Foreshadow vulnerabilities as well as general hardware and firmware security guidance https://github.com/nsacyber/Hardware-and-Firmware-Security-Guidance

-
1 note
·
View note


