Adware Removal, Malware Removal Guides and Malware Research.
Don't wanna be here? Send us removal request.
Text
Google Chrome - Redirect Blocked - Am I infected with adware or worse?
Since Google Chrome version 65, Google has introduced a redirect blocker in Google Chrome. The Redirect Blocker must prevent users from being redirected to possible malicious web pages with the intention to infect the web browser with adware and web pages full of advertisements.

When Google Chrome blocks a redirect in the web browser there are many purposes why Google Chrome is doing so. In the first place, your PC might be infected with an adware application. Adware opens the Chrome web browser and redirects a new window through several redirects before landing on a landing page. However, Chrome might also be redirected by compromised web pages or intrusive advertising networks. We have seen these intrusive redirects in many recent examples. In August 2018 there was a massive WordPress malvertising campaign redirecting the user's to "show notification" scam pages. This led to many compromised web pages, for example; unverf.com, tuniaf.com that redirected the web browser's through many malicious - compromised domains. Only with the intention to scam users into allowing notifications in their web browser. The malicious domains were abused to show advertisements through Chrome. In Google Chrome version 68, the Chromium team had chosen to add an info-bar when the user is unintentionally redirected to a web page. All redirects originating from third-party iframes will show an info bar instead, useless the user had some interaction with the web page. This indicates Google is getting much better in detecting redirects and protecting the Chrome web browser from unintentional redirects. Do you still notice unwanted redirects in the Chrome or another web browser, the PC is most likely infected with an ad-supported software application e.g. adware. The difference with an unwanted redirect caused by a compromised web page and Adware is the number of redirects in your web browser. When the PC is infected with Adware the web browser is redirected at least every 10 minutes to many different web pages, you might experience additional problems such as a slow browser, failed network error in Chrome, underlined in-text ads with "ads by" and search queries redirected through a search engine you did not intentionally visit. When you were redirected by a compromised or malvertising web page you are only redirected once and the web browser is not opened automatically on your PC. Most likely you were visiting a web page and the redirect occurred. Some web pages that are compromised are redirecting users to malicious javascript code to exploit the web browser, exploit kits such as Neutrino, RIG, Sundown, Angler, and Nuclear are known to infect user with so-called "drive by downloads". Make sure your PC is not infected with adware, or worse! Perform a Google Chrome virus scan or remove the pop-up redirect from Google Chrome. Read the full article
0 notes
Text
How to Remove direct.redtrafficjar.site POPUP redirect - Removal Guide
direct.redtrafficjar.site redirects the Google Chrome, Internet Explorer, Firefox and Edge web browser to use to display unpleasant ads. If you notice the direct.redtrafficjar.site directly in the web browser, it is because adware or a potentially unwanted program is installed on your PC. The direct.redtrafficjar.site pop-up is displayed by an annoying pop-up redirect that occurs in the web browser. Every few seconds, worthless pop-ups open in your web browser. These pop-ups redirect the web browser through different domains to intrusive ads. One of these domains that constantly redirects the web browser to ads is direct.redtrafficjar.site, as you can see in our example. direct.redtrafficjar.site is identical to redirect.redpop.pro, direct.redtrafficstarted.site, direct.redtrafficsixteen.site, direct.redtrafficone.site, and Direct.redtrafficchoose.site.

direct.redtrafficjar.site pop-up removal Additional information: direct.redtrafficjar.site: Download Removal Tool Distribution: Adware Also known as: direct.redtrafficjar.site redirect, direct.redtrafficjar.site pop-up, direct.redtrafficjar.site ads. Affected Browsers: Google Chrome, Mozilla Firefox, Internet Explorer, and Microsoft Edge. Type: pop-up (redirect) direct.redtrafficjar.site redirect can adapt to the web browser and the visitor. The direct.redtrafficjar.site reads various information from the web browser, such as the IP-address, the version of the web browser, the country of origin of the user and more. In this way, the direct.redtrafficjar.site redirects the user to the most relevant advertisement. As mentioned earlier, adware is responsible for the direct.redtrafficjar.site pop-up redirect in your web browser. Adware is a collective term for software specifically designed to display ads. Adware often enters the PC without the user's knowledge. Adware is bundled with free software that you can download from the internet and is installed during the installation process. Adware often leaves the user puzzled about the direct.redtrafficjar.site pop-up, of which the user wonders afterward what the direct.redtrafficjar.site is and where it comes from.
How to remove direct.redtrafficjar.site?
Use this menu, follow the steps to get rid of direct.redtrafficjar.site pop-up ads. This instruction includes both manual removal steps and malware removal tools to remove the direct.redtrafficjar.site redirect.
Remove direct.redtrafficjar.site, complete the steps below
Remove adware from Windows manually without software Uninstall recently installed adware using Windows Control Panel - Uninstall a program Remove direct.redtrafficjar.site pop-up redirect from Google Chrome Remove direct.redtrafficjar.site pop-up redirect from Internet Explorer Remove direct.redtrafficjar.site pop-up redirect from Firefox Remove direct.redtrafficjar.site pop-up redirect Microsoft Edge Scan your computer for malware with free anti-malware software to detect and remove direct.redtrafficjar.site. Remove: direct.redtrafficjar.site with Malwarebytes Free (recommended) Remove direct.redtrafficjar.site with Zemana Get rid of direct.redtrafficjar.site with AdwCleaner if (navigator.userAgent.indexOf('Mac OS X') != -1) { document.write("It seems you are using a Mac, clean your Mac with CleanMyMac 3 by MacPaw (more information). 3 million+ downloads worldwide. ") }


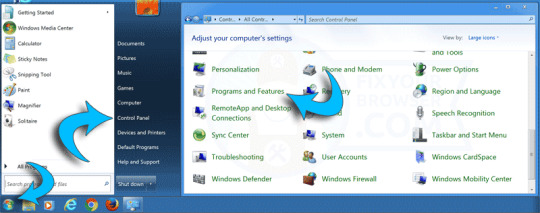
Windows 7 users: Click the Start button in the left bottom corner, select Control Panel, select "Programs, and Features".


Windows 8 and Windows 10 users: Right-click the Windows logo in the bottom left corner, select Control Panel, select "Programs and Features".

Check the programs list for recently installed applications and click "Uninstall". Click the column "Installed On" to sort installed software by date, this makes it easier to detect recently installed software. If you don't know what to look for, go to this removal step.

Manually remove direct.redtrafficjar.site from Internet Explorer, Chrome, Firefox or Microsoft Edge
Remove direct.redtrafficjar.site ads without tools from the Internet Explorer, Google Chrome, Firefox or Edge web browser.

In this first step for Internet Explorer, you have to verify if internet explorer is infected with a malicious add-on. Add-ons could be responsible for the direct.redtrafficjar.site pop-up ads in the Internet Explorer web browser.

choose the wrench button, and from the menu click Manage add-ons.

Check the add-on list for any suspicious add-on in Internet Explorer, click disable or remove to delete the add-on. Continue to the next step to remove direct.redtrafficjar.site from Internet Explorer. Reset your default Homepage and Search engine for Internet Explorer Internet Explorer has the possibility to reset to default, an Internet Explorer reset will affect your saved bookmarks and passwords. Internet Explorer reset is the easiest way to get rid of the direct.redtrafficjar.site redirect.

pick the wrench button and from the menu click Internet Options.

Choose the Advanced tab, click the Reset button.

Check Delete personal settings and click the Reset button. Restart Internet Explorer to complete the reset. Good, Internet Explorer is reset to the default configuration, it is important to know there are adware (direct.redtrafficjar.site) remnants on your computer. We recommend to scan and remove the virus files from your computer. Make sure the direct.redtrafficjar.site redirect doesn't occur again and all remnants are removed from your PC.

if (navigator.userAgent.indexOf('Mac OS X') != -1) { document.write(" Google Chrome users on Mac OS, follow this Adware removal guide for Mac OS ") } In this first step for Google Chrome, you need to identify and remove the browser extension responsible for the direct.redtrafficjar.site pop-up ads. Some browser extensions are ad-supported, e.g. adware and might show intrusive ads from direct.redtrafficjar.site. If you didn't install any browser extension at all, remove all browser extensions from Chrome.

Click the menu button, from the Chrome menu click More tools and then Extensions.

Identify browser extension(s) from the list and click the Remove button to remove the extension. If you are unsure if the extension is malicious, click the slider and disable the extension first. Continue to the next step. Reset the Google Chrome profile sync Google Chrome synchronizes the browsers user-profile with the Google Cloud services. If the Google Chrome browser is infected with adware, this adware, usually browser extensions, and pop-up ads to direct.redtrafficjar.site are synced with Google's servers. It is important to clean this synchronized cache. If the user doesn't clear the synchronized settings, the direct.redtrafficjar.site pop-up and malicious Chrome settings keep coming back on any devices the Chrome user profile is synchronized with. Open the Google Dashboard (opens in a new browser window). Click the Reset sync button to clear all of your synced data on Google's server, confirm with OK.

Continue to the next step. Reset the Google Chrome homepage and search engine settings Chrome has the option to reset to default settings, a Chrome browser reset will not affect your saved bookmarks and passwords. Google Chrome reset is the easiest way to get rid of ad-supported browser extensions that display the direct.redtrafficjar.site pop-up ad.

Click the menu button, from the drop-down menu click Settings.

Scroll down to Advanced and again scroll down to Reset settings.

Click the Reset button to reset Google Chrome.

Confirm the reset of the Chrome web browser by clicking the Reset button. Restart Google Chrome for the changes to take effect. Google Chrome is reset to default settings, it is important to know there are remnants of direct.redtrafficjar.site redirect on your computer. We recommend to scan and remove malware files from your computer to make sure the adware does not reinstall and the direct.redtrafficjar.site redirect doesn't occur again.

In this first step for Firefox, you need to identify and remove any Firefox add-on that is unknown to you. If you didn't install any add-on at all, remove all add-ons from Firefox. Add-ons in Firefox could be ad-supported which basically means an add-on shows direct.redtrafficjar.site pop-up ads in Firefox.

Click the Firefox menu button, from the drop-down menu click Add-ons.

Click extensions from the left menu. Identify any unknown Firefox browser extension. Click the Remove button to delete the extension and get rid of direct.redtrafficjar.site ads. Reset the Firefox homepage and search engine settings Firefox has the option to reset to default settings, this will reset Firefox completely. Reset Firefox is the easiest way to get rid of ad-supported add-ons from Firefox.

Click the menu button, from the menu, select Help ? (the question mark icon, at the end of the menu).

Click on Troubleshooting information from the Help menu.

select the Refresh Firefox button, confirm the reset and restart Firefox. The Firefox browser is reset to default settings, it is important to know there are remnants of malware on your computer. We recommend to scan and remove malware files from your computer to make sure the malware does not reinstall and the direct.redtrafficjar.site redirect is entirely removed from the Firefox web browser.

If you encounter direct.redtrafficjar.site pop-up redirects in Microsoft Edge, follow these instructions.

Right-click the start button in Windows 10, from the start menu top click Apps and Features.

Scroll down through the right Apps and Features list till you see Microsoft Edge, click Advanced options.

Click on the Reset button to reset Microsoft Edge to default settings. Microsoft Edge reset will clear the browsing history, cookies, and settings. Not the Microsoft Edge favorites web pages. The Microsoft Edge web-browser is reset to default settings, it is important to know there are remnants of the direct.redtrafficjar.site redirect on your PC. We recommend to scan and remove malware files from your computer.

Remove direct.redtrafficjar.site with Malwarebytes
Get rid of direct.redtrafficjar.site with Malwarebytes. Malwarebytes is free to use, detect and remove the direct.redtrafficjar.site redirect from the web browser. direct.redtrafficjar.site is a intrusive pop-up which is a type of malware, Malwarebytes will remove direct.redtrafficjar.site pop-up redirect from the web browser. Run the Malwarebytes program installation file. Click here for Malwarebytes installation instructions. Click Scan Now to start examining for the adware responsible for the direct.redtrafficjar.site redirect in the web browser.

Malwarebytes will start searching for malware, please wait for Malwarebytes to finish the malware scan. Malwarebytes usually takes between 2 to 5 minutes to complete.

Once the malware scan is performed, Malwarebytes will present the results of the direct.redtrafficjar.site malware scan. Remove the malware found by Malwarebytes using the Quarantine Selected button.

Wait for Malwarebytes to move all malware to quarantine.

Malwarebytes needs to make a system reboot to finish the direct.redtrafficjar.site redirect removal process. Save and close any working documents or open web pages and click Yes to reboot your PC.

After the system reboot, your web browser is free from the direct.redtrafficjar.site pop-up redirect. Stay protected with Malwarebytes against future browser hijacker and other types of malware. Malwarebytes stops adware, abusive pop-ups, potentially unwanted programs, malicious web pages, suspicious downloads, viruses, spyware and ransomware from infecting your web browser.

Get rid of direct.redtrafficjar.site with Zemana
Zemana Anti-Malware is an second opinion anti-malware scanner which uses Cloud technology with direct.redtrafficjar.site pop-up detection. Zemana is the fastest, smallest and most proactively malware scanner available. Zemana is its best in addition to a primary virus scanner or malware scanner such as Malwarebytes. Open the Zemana anti-malware setup file. Install Zemana anti-malware using the default settings, after successful installation Zemana anti-malware will update itself to the latest version.

Select the Scan button to perform a malware scan to detect the malware responsible for the direct.redtrafficjar.site redirect Please wait for the scan to finish, the scan usually takes a few minutes.

Click the Next button to remove the malware found by Zemana on your computer.

Wait a couple of seconds for Zemana to remove the direct.redtrafficjar.site ads from Internet Explorer, Google Chrome, Firefox or Microsoft Edge.

Your PC is successfuly cleaned by Zemana. Zemana is an excellent protection for people searching for a lightweight malware detection and removal tool. Zemana is its best in addition to a more comprehensive antivirus or anti-malware security application such as Malwarebytes.

Get rid of direct.redtrafficjar.site with adwcleaner
Right-click the AdwCleaner executable you just downloaded and select "Run as Administrator" this is important. Select the Scan Now button.

Wait for the adware & malware scan to finish. Click the Clean & Repair button to remove the adware and malware from your PC.

Wait for AdwCleaner to remove the adware and malware from your PC. Click the Clean & Restart Now button to finish the malware removal process.

After the reboot, AdwCleaner shows a summary of the detected and removed malware files.

Read the full article
0 notes
Text
Remove laserveradedomaina.com redirect virus - Updated August 2018

this article is updated on 08/02/2018
How to remove laserveradedomaina.com redirect?
laserveradedomaina.com pop-up redirects in the Chrome, Firefox or Internet Explorer or Edge web browser are triggered by adware application(s). The adware software application triggers a new pop-up redirect in the Internet Explorer, Google Chrome, Firefox, Edge browser and displays the laserveradedomaina.com ad. The problem with laserveradedomaina.com and identical malicious redirects such as Letsupdateourdomain.com redirect, Laborates.com redirect, Cobalten.com redirect, akamaihd.net, go.oclasrv.com redirect, and Phu1aefue.com redirect is the fact that the domain laserveradedomaina.com is associated with many different kinds of adware applications. The laserveradedomaina pop-up is therefore hard to remove from your computer and the web browser with removal manual instructions.

laserveradedomaina.com redirect removal
Additional information: laserveradedomaina.com: Download Removal Tool Distribution: Adware, Potentially Unwanted Programs (PUPs), Download managers Also known as: laserveradedomaina.com redirect, laserveradedomaina.com pop-up, laserveradedomaina.com ads Affected Browsers: Google Chrome, Mozilla Firefox, Internet Explorer, Edge, and Safari. Type: browser redirect Laserveradedomaina.com ads are caused by Adware which is installed on your PC. If the PC is infected with adware then it is possible that the browser is constantly referred via Laserveradedomaina.com. Multiple users report that Laserveradedomaina.com is creating a new browser window and is redirecting it via Laserveradedomaina.com. Because Laserveradedomaina.com is associated with malware, it is important that you check your PC for unwanted software. Unwanted software, which also includes Adware, enters the PC via software which can be downloaded free of charge from the Internet. It is, therefore, possible that the user has installed the Adware which causes the popups to Laserveradedomaina.com.
Remove laserveradedomaina.com redirect
Get rid of Laserveradedomaina.com redirects with these removal steps. We tested Malwarebytes succesfully against the Laserveradedomaina.com popup. To remove laserveradedomaina.com ads, complete the steps below laserveradedomaina.com redirect removal tool Step 1 - Recommended: Remove laserveradedomaina.com redirect with Malwarebytes - Malwarebytes works, it's free and we tested it successfuly to remove laserveradedomaina redirects. Step 2 - Remove laserveradedomaina.com adware with Zemana Anti-Malware laserveradedomaina.com manual removal instructions laserveradedomaina.com redirect manual removal instructions Uninstall adware Remove laserveradedomaina.com redirect from Google Chrome Remove laserveradedomaina.com ads from Internet Explorer Remove laserveradedomaina.com pop-up from Mozilla Firefox

Step 1. Remove laserveradedomaina.com redirect with Malwarebytes
VIDEO: how to remove the laserveradedomaina.com redirect virus with Malwarebytes. Many visitors have successfuly removed the laserveradedomaina.com redirect with our removal instructions.

Step 2. Delete laserveradedomaina.com adware with Zemana Antivirus

Uninstall adware to get rid of the laserveradedomaina.com redirect ads.
In this first step, we show you how to detect and manually uninstall adware responsible for the laserveradedomaina.com redirect virus. After you have uninstalled any adware application(s), perform an anti-malware scan with our recommended removal tools to remove any traces from your PC to make sure the laserveradedomaina.com ads are entirely removed from the infected PC.

Remove laserveradedomaina.com redirect from Internet Explorer, Chrome or Firefox
In this second step, we show you how to manually remove the laserveradedomaina.com redirect virus from the browser and how to reset the browser to default settings. If after these manual removal steps, there are still ads, pop-ups or browser redirects appearing from laserveradedomaina.com in the Internet Explorer, Chrome, Firefox or Microsoft Edge browser? Perform a malware scan with our recommended malware removal tools. We do, however, recommend to malware scan your computer make sure there are no malware remnants left on the computer. Read the full article
0 notes
Text
Remove HowToEasy New Tab - Chrome, Firefox - Real Removal Instruction
How to Remove HowToEasy new tab? HowToEasy is a new tab browser hijacker for Google Chrome and Firefox. After successful infiltration, the web browser default new tab is replaced by the HowToEasy new tab. Usually, the user has no idea how the HowToEasy new tab ended up in the web browser. HowToEasy is distributed via malicious adware software installations and pop-ups in the web browser claim that HowToEasy is a handy extension and significantly improve the browser experience of Google Chrome or Firefox. The HowToEasy extension declared the following useful functionality, fast access to DIY (do it yourself) tutorials right from the web browser, quick access to home improvement tips, technology information, healthy recipes and money saving tips. This functionality is a way to appear legitimate to the user. Basically, it is a trick to induce the user to install the HowToEasy extension in the web browser. In reality, the HowToEasy extension is meant to generate revenue through rogue ads and suspicious redirecting in the browser. The Easymaps extension (search.mapseasy.net) is built for the same purposes. It is not recommended to have the HowToEasy search engine installed in the web browser. Users have no idea what kind of data the HowToEasy search engine can collect about their online behavior. The HowToEasy search engine is installed through a browser extension. However, this HowToEasy extension has many permissions in the web browser with which they can inventory and resell a lot of personal and non-personally information to rogue third parties, for example, suspicious advertising networks.
HowToEasy new tab

Summary: HowToEasy: Download Removal Tool Distribution: Adware, intrusive popup ads Affected Browsers: Google Chrome, Mozilla Firefox and Internet Explorer Type: browser hijacker If you have no idea how the HowToEasy new tab is installed in your web browser, then your PC is infected with an adware application. Multiple web pages on the internet offer free software, and to make this software generate money, adware developers bundle adware with free software. This adware is then offered to the user during the installation process. However, the checkbox to decline the adware installation is often hidden and barely visible to the user. If you have clicked through an installation process too quickly, you have installed the HowToEasy new tab. This may also cause intrusive pop-up ads to appear in your PC and web browser. Adware is software developed entirely for the purpose of displaying advertisements. Adware is better known as malware and must be removed as soon as possible. Therefore, follow our instructions below to remove HowToEasy new tab.
How to remove HowToEasy new tab?
Use this quick menu get rid of HowToEasy new tab in the Google Chrome and Firefox web browser.
Remove HowToEasy, complete the steps below
Remove HowToEasy from Windows manually without software Uninstall recently installed adware using Windows Control Panel - Uninstall a program Remove HowToEasy new tab from Google Chrome Remove HowToEasy new tab from Firefox Scan your computer for malware with free anti-malware software to detect and remove HowToEasy files Remove: HowToEasy new tab with Malwarebytes Free (recommended) Remove HowToEasy with Zemana Get rid of HowToEasy with AdwCleaner if (navigator.userAgent.indexOf('Mac OS X') != -1) { document.write("It seems you are using a Mac, clean your Mac with CleanMyMac 3 by MacPaw (more information). 3 million+ downloads worldwide. ") }

Windows 7 users: Click the Start button in the left bottom corner, select Control Panel, select "Programs, and Features".

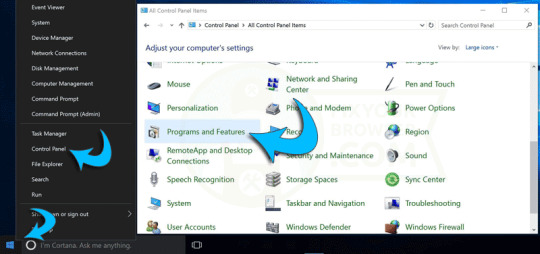
Windows 8 and Windows 10 users: Right-click the Windows logo in the bottom left corner, select Control Panel, select "Programs and Features".

Search for any (unknown) recently installed software and remove the software using the Uninstall button. Make sure to not accept any offers during the uninstall process. Click the column "Installed On" to sort installed software by date, this makes it easier to detect recently installed software. If you don't know what to look for, go to this removal step.

Manually remove HowToEasy new tab from Google Chrome and Firefox
Remove HowToEasy new tab manually without tools from the Google Chrome and Firefox web browser. HowToEasy installs a browser extension in Chrome and an add-on in Firefox.

if (navigator.userAgent.indexOf('Mac OS X') != -1) { document.write(" Google Chrome users on Mac OS, follow this Adware removal guide for Mac OS ") } In this first step for Google Chrome, you need to identify and remove the browser extension responsible for the HowToEasy search engine. Some browser extensions are ad-supported, e.g. adware and might change the homepage or search settings to HowToEasy. If you didn't install any browser extension at all, remove all browser extensions from Chrome.
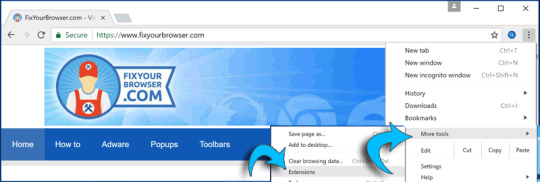
Click the menu button, from the Chrome menu click "More tools" and then "Extensions".
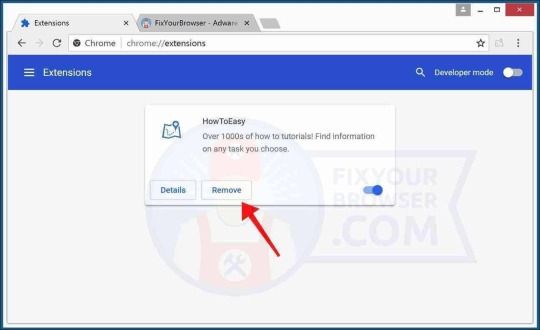
Identify the HowToEasy extension and click the "Remove" button to remove the browser extension. If you are unsure if the extension is malicious, click the slider and disable the extension first. Continue to the next step. Change Google Chrome homepage and new tab Click the Google Chrome menu button, from the Chrome menu go to "Settings".
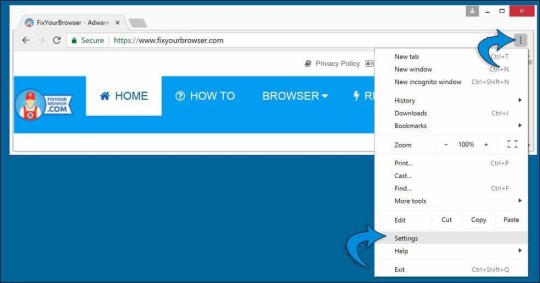
In the On startup section find the HowToEasy extension and click "Disable". Click the "Open a specific page or set of pages" and check for the howtoeasy.co homepage, if present click the three vertical dots and click the "Remove" button.

Change Google Chrome search engine Click the Google Chrome menu button, from the Chrome menu go to "Settings".
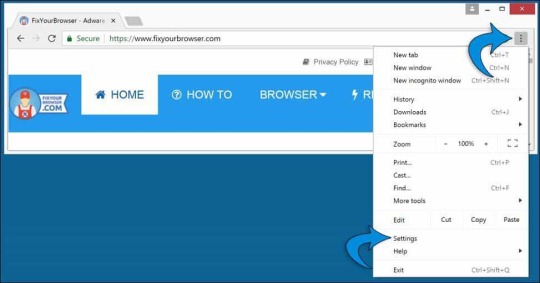
In the "Search engine" section find the "manage search engines" button.
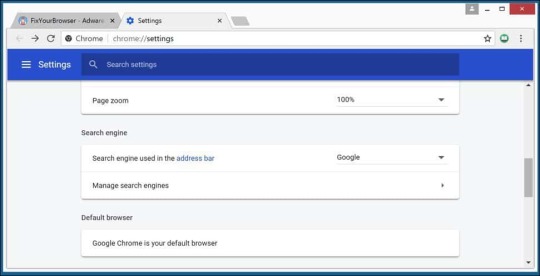
In the list of search engines, locate the "HowToEasy Search" search engine. On the right next to the URL, click the three vertical dots button and select "Remove from list". Click the three vertical dots next to Google, Yahoo, or Bing and select "Make default".
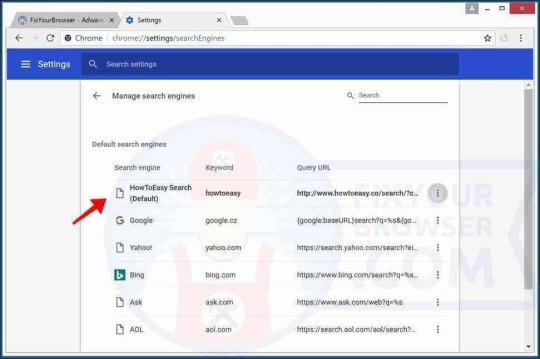
Reset the Google Chrome profile sync Google Chrome synchronizes the browsers user-profile with the Google Cloud services. If the Google Chrome browser is infected with adware, this adware, usually browser extensions, the homepage and HowToEasy search engine settings are synced with Google's servers. It is important to clean this synchronized cache. If the user doesn't clear the synchronized settings, the HowToEasy extension and Chrome settings keep coming back on any devices the Chrome user profile is synchronized with. Open the Google Dashboard (opens in a new browser window). Click the Reset sync button to clear all of your synced data on Google's server, confirm with OK.
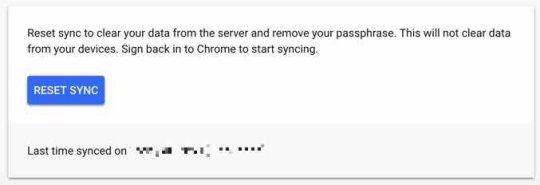
Restart Google Chrome, if necessary continue to the next step. Optional: Reset Google Chrome Chrome has the option to reset to default settings, a Chrome browser reset will not affect your saved bookmarks and passwords. Google Chrome reset is the easiest way to get rid of ad-supported browser extensions that install the HowToEasy homepage.
Click the menu button, from the drop-down menu click "Settings".
Scroll down to Advanced and again scroll down to Reset settings.
Click the "Reset" button to reset Google Chrome.

Confirm the reset of the Chrome web browser by clicking the "Reset" button. Restart Google Chrome for the changes to take effect. Google Chrome is reset to default settings, it is important to know there are remnants of HowToEasy hijacker on your computer. We recommend to scan and remove malware files from your computer to make sure the adware does not reinstall and the HowToEasy redirect doesn't occur again.

In this first step for Firefox, you need to identify and remove any Firefox add-on that is unknown to you. If you didn't install any add-on at all, remove all add-ons from Firefox. Add-ons in Firefox could be ad-supported which basically means an add-on might have installed HowToEasy in Firefox.
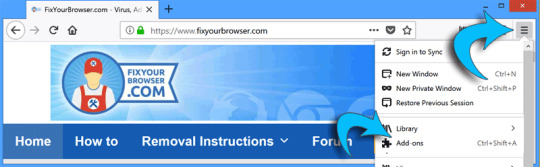
Click the Firefox menu button, from the drop-down menu click Add-ons.
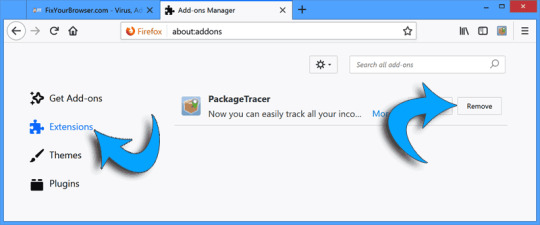
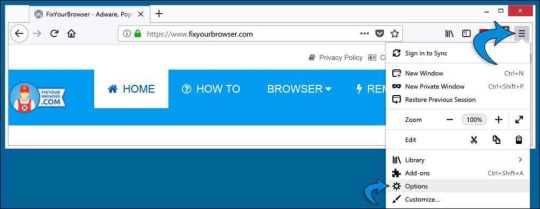
Click extensions from the left menu. Search for the HowToEasy firefox browser extension. Click the "Remove" button to delete the extension and get rid of HowToEasy. Change Firefox homepage Open the Firefox menu, which can be found in the top right corner. Select "Options" from the menu.
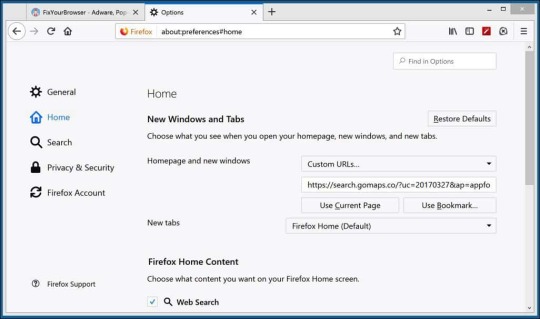
In the options window, go to Home in the left menu. Remove HowToEasy from the Custom URLs textbox, or click the "Restore Defaults" button.
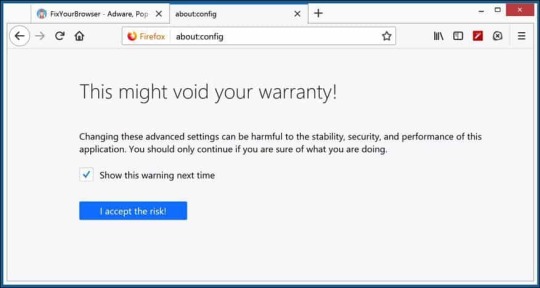
Change default search engine for Firefox In the address bar type about:config and confirm with Enter. Click the I accept the risk! button.
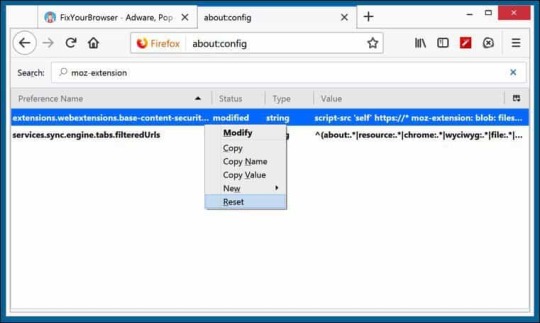
In the search bar type: moz-extension right-click on each of the results and select Reset to restore their values to default settings.
Restart Firefox, if necessary continue to the next step. Optional: Reset Firefox Firefox has the option to reset to default settings, this will reset Firefox completely. Reset Firefox is the easiest way to get rid of ad-supported add-ons from Firefox that install HowToEasy as your default search engine.
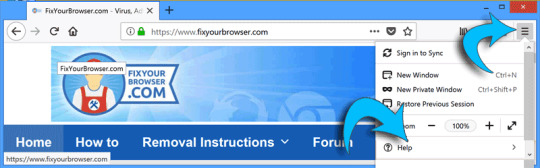
Click the menu button, from the menu, select Help ? (the question mark icon, at the end of the menu).
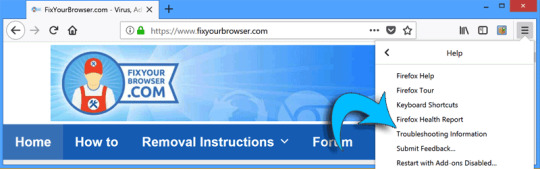
Click on Troubleshooting information from the Help menu.
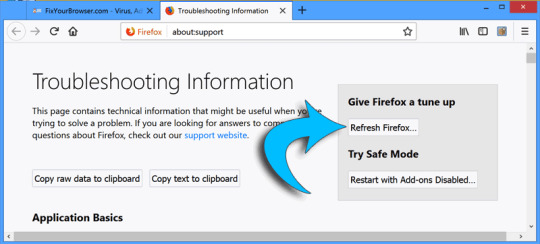
select the Refresh Firefox button, confirm the reset and restart Firefox. The Firefox browser is reset to default settings, it is important to know there are remnants of malware on your computer. We recommend to scan and remove malware files from your computer to make sure the malware does not reinstall and the HowToEasy redirect is entirely removed from the Firefox web browser.

Remove HowToEasy with Malwarebytes
Get rid of HowToEasy with Malwarebytes. Malwarebytes is free to use, detect and remove the HowToEasy redirect from the web browser. HowToEasy is a browser hijacker which is a type of malware, Malwarebytes will remove HowToEasy from the web browser. Run the Malwarebytes program installation file. Click here for Malwarebytes installation instructions. Click Scan Now to start examining for the adware responsible for the HowToEasy redirect in the web browser.
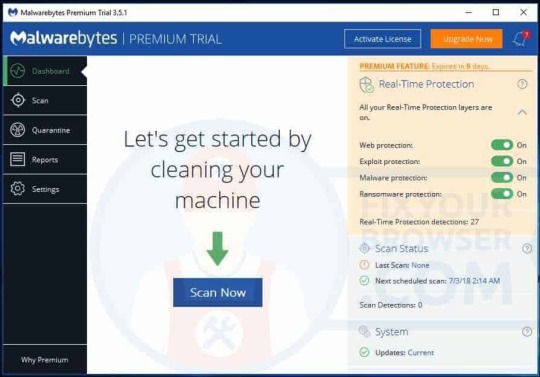
Malwarebytes will start searching for malware, please wait for Malwarebytes to finish the malware scan. Malwarebytes usually takes between 2 to 5 minutes to complete.
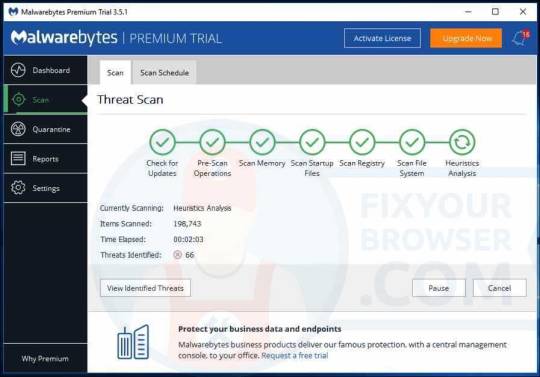
Once the malware scan is performed, Malwarebytes will present the results of the HowToEasy malware scan. Remove the malware found by Malwarebytes using the Quarantine Selected button.
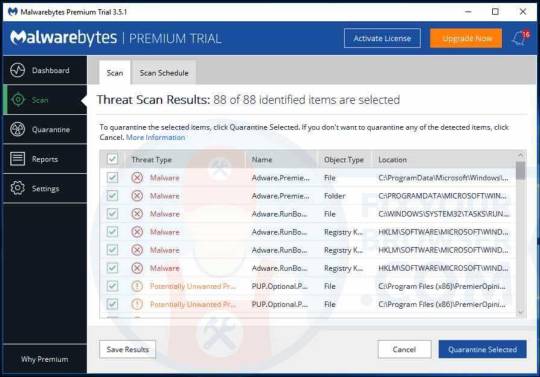
Wait for Malwarebytes to move all malware to quarantine.
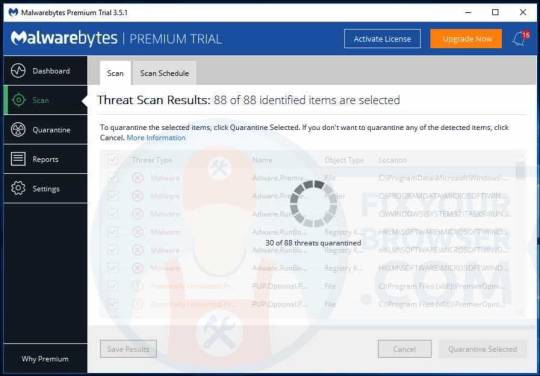
Malwarebytes needs to make a system reboot to finish the HowToEasy redirect removal process. Save and close any working documents or open web pages and click Yes to reboot your PC.
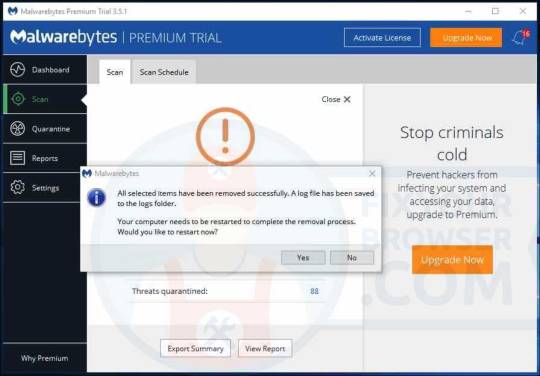
After the system reboot, your web browser is free from the HowToEasy browser hijacker. Stay protected with Malwarebytes against future browser hijacker and other types of malware. Malwarebytes stops adware, browser hijackers, potentially unwanted programs, malicious web pages, suspicious downloads, viruses, spyware and ransomware from infecting your web browser.
Get rid of HowToEasy with Zemana
Zemana Anti-Malware is an second opinion anti-malware scanner which uses Cloud technology with HowToEasy browser hijacker detection. Zemana is the fastest, smallest and most proactively malware scanner available. Zemana is its best in addition to a primary virus scanner or malware scanner such as Malwarebytes. Open the Zemana anti-malware setup file. Install Zemana anti-malware using the default settings, after successful installation Zemana anti-malware will update itself to the latest version.
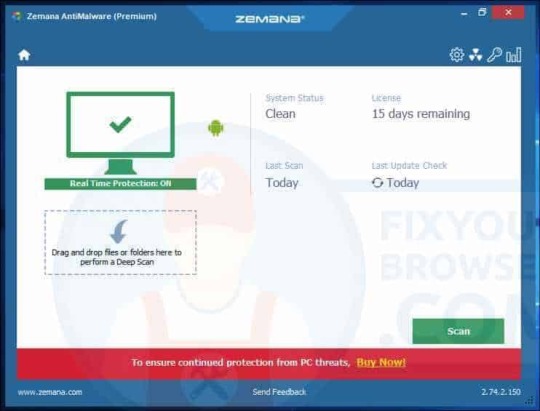
Select the Scan button to perform a malware scan to detect the malware responsible for the HowToEasy redirect Please wait for the scan to finish, the scan usually takes a few minutes.
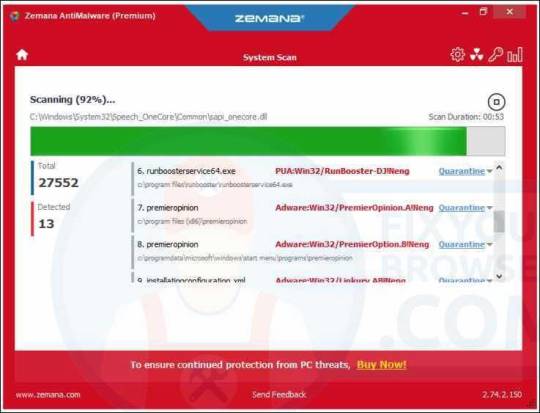
Click the Next button to remove the malware found by Zemana on your computer.
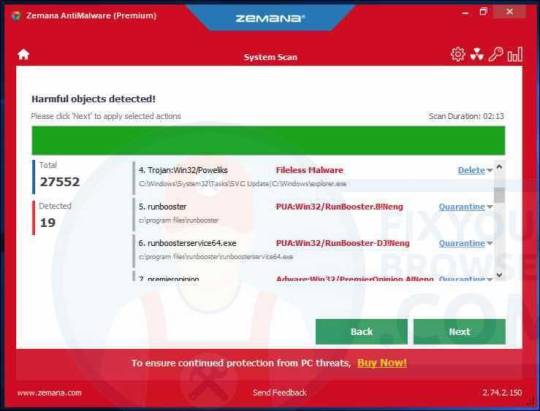
Wait a couple of seconds for Zemana to remove the HowToEasy browser hijacker from Internet Explorer, Google Chrome, Firefox or Microsoft Edge.
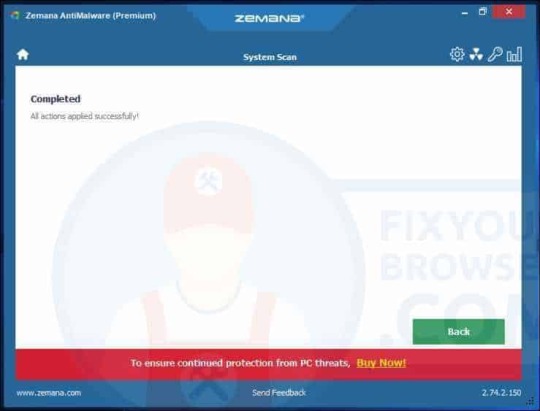
Your PC is successfully cleaned by Zemana. Zemana is an excellent protection for people searching for a lightweight malware detection and removal tool. Zemana is its best in addition to a more comprehensive antivirus or anti-malware security application such as Malwarebytes.

Get rid of HowToEasy with adwcleaner
Right-click the AdwCleaner executable you just downloaded and select "Run as Administrator" this is important. Select the Scan Now button.
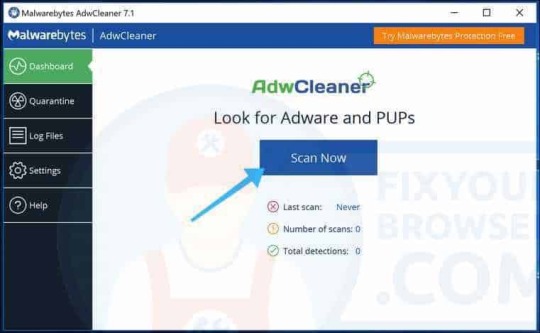
Wait for the adware & malware scan to finish. Click the Clean & Repair button to remove the adware and malware from your PC.
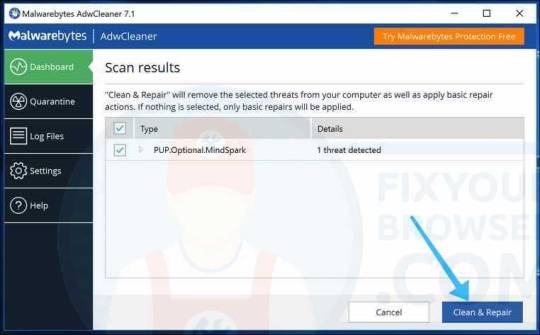
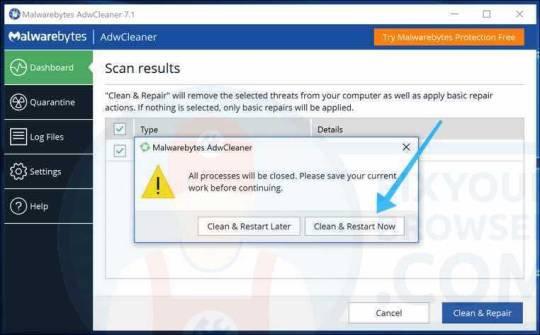
Wait for AdwCleaner to remove the adware and malware from your PC. Click the Clean & Restart Now button to finish the malware removal process.
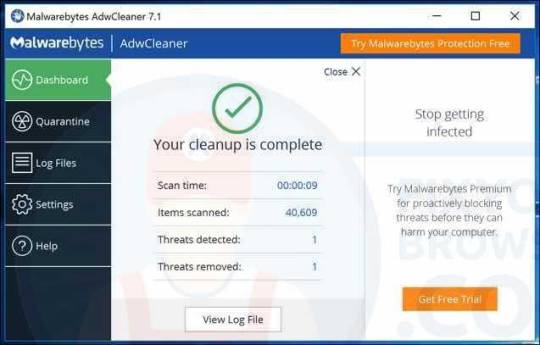
After the reboot, AdwCleaner shows a summary of the detected and removed malware files.
Read the full article
1 note
·
View note
Text
Fix (Solve) the ERR_CONNECTION_ABORTED error in Google Chrome
The ERR_CONNECTION_ABORTED error in Google Chrome is a sign that the internet connection is not working properly. If Google Chrome displays the ERR_CONNECTION_ABORTED error, this is usually due to SSL. SSL stands for Secure Socket Layer and is used to establish a secure connection to a web page. If the ERR_CONNECTION_ABORTED error is displayed in Chrome, then the web page has a problem with SSL. In this article, I will give you tips on how to solve the ERR_CONECTION_ABORTED problem in the Google Chrome web browser.
Fix "ERR_CONNECTION_ABORTED" Google Chrome error
The ERR_CONNECTION_ABORTED error in Google Chrome has to do with SSLv3. If you start Google Chrome with the following parameters, the problem is most likely resolved. Disable SSLv3 for Google Chrome Find the shortcut to Google Chrome on the Windows desktop. Right-click the Chrome shortcut and select Properties.

In the target field. First, add a space and then –ssl-version-min=tls1 after the closing quote. See the example below.

Now confirm the shortcut changes and restart the web browser. If the ERR_CONNECTION_ABORTED still occurs in Google Chrome, continue will the following fix. Uninstall KB2992611 windows update Open the Control panel in Windows, go to uninstall a program, select View installed updates and remove the KB2992611 update. I hope these instructions helped you get rid of the ERR_CONNECTION_ABORTED error in Google Chrome. Let us know in the comments what you think! Read the full article
0 notes
Text
How to Get rid of adware on Firefox - Information & Removal Instructions
Firefox is a great fast and reliable web browser. Currently, Firefox has an 11% market share against Chrome, Internet Explorer and Microsoft Edge. That's not much, yet Firefox has great potential for strong growth. Those of you who regularly find yourself on the internet know that unwanted advertisements and adware are common. You can acquire adware anywhere on the internet and it can install itself in different web browsers. Firefox is no exception. In the article, I will explain how to remove adware from Firefox and how to restore Firefox to its optimal condition. On its own, adware is a collective name for ad-supported software. This means that software is installed on your PC that abuses the Firefox web browser to display intrusive advertisements such as popups, in-text ads or banners that are perceived as annoying by the user. This concerns advertising that is not on the web page but is displayed by Adware. There is a big difference between ads displayed on the website to cover the cost of the website and ads generated by adware. The ads that are displayed by adware are often ads that focus on a casino, browser updates, scams, and NSFW (not safe for work) ads.
How to remove adware from Firefox?
Browser extension The first step to remove adware from Firefox is to identify the browser extension (add-on) that is installed by adware. Browser extensions are usually developed to enhance the web browser experience, however, suspicious advertising services also use extensions to display ads and change content on the web page the user is visiting, for example, inject ads into the content. Open Firefox, click the menu button in the top right corner. Select add-ons from the menu and Extensions from the menu on the left.

Now verify the add-ons installed in Firefox. If you didn't install add-on at all remove all add-ons, by default Firefox has no add-ons installed.

Click the Remove button to remove the add-on installed in Firefox.
Change homepage and search engine in Firefox
Adware is a collective name for software that makes changes to the web browser. Adware also includes so-called browser hijackers. Browser hijackers are aimed at replacing your homepage and search engine with another often malicious search engine. Browser hijackers intend to redirect the Firefox web browser to a homepage of their choice. To remove browser hijackers, you need to change the start page and search engine, follow these instructions. Change homepage in Firefox Open the Firefox menu in the top right corner, from the menu open Options.

In the Options menu, click on the Home tab in the left menu, to reset the homepage click on Restore Defaults. If you would like to open a custom web page, select Custom URLs from the Homepage and new windows option and enter the web page you would like to open each time Firefox is started. Change the new tab from the New tabs menu and set to Default "Firefox Home (Default)" or select Blank page.

Change search engine in Firefox Once again open the Firefox menu, and go to the Search tab in the left menu.

In the Default Search engine menu, select the search engine you would like to use, e.g. Google (as in this example). However, when a browser hijacker has changed the search engine the search engine might be changed to an unknown search engine. In order to remove the browser hijacker, select the search engine from the list and change it to another legitimate search engine such as Google. To make things much easier click the Restore Default Search Engines button.
Reset Firefox
Pretty much any adware for Firefox makes changes to the web browser and sometimes these changes are not easy to get rid of. In order to easily get rid of any adware that had to make any changes to Firefox, you can reset Firefox to default settings. Firefox reset will reset the homepage, add-ons, and search provider. Open the Firefox menu, and from the menu click on Help.

In the Help menu, select Troubleshooting information from the menu.

Click the Refresh Firefox button, and confirm the firefox reset once again in the dialog. The refresh Firefox button will remove add-ons and customizations, and restore your homepage.

Remove adware from Firefox with antivirus
Adware is ad-supported software and is commonly installed without the user's knowledge. It is these ad-supported software that shows ads, popups and redirects in the Firefox web browser. In order to completely get rid of adware on Firefox you need to scan your PC for any harmful software. Get started to remove adware from Firefox. Run the Malwarebytes program installation file. Click here for Malwarebytes installation instructions. Click Scan Now to start examining for the adware responsible for unwanted ads or changes in the Firefox web browser.

Malwarebytes will start searching for malware, please wait for Malwarebytes to finish the malware scan. Malwarebytes usually takes between 2 to 5 minutes to complete.

Once the malware scan is performed, Malwarebytes will present the results of the adware scan. Remove the malware found by Malwarebytes using the Quarantine Selected button.

Wait for Malwarebytes to move all malware to quarantine.

Malwarebytes needs to make a system reboot to finish the firefox adware removal process. Save and close any working documents or open web pages and click Yes to reboot your PC.

After the system reboot, your web browser is free from adware that abuses the Firefox web browser. Stay protected with Malwarebytes against future browser hijacker and other types of malware. Malwarebytes stops adware, browser hijackers, potentially unwanted programs, malicious web pages, suspicious downloads, viruses, spyware and ransomware from infecting your web browser. I hope this article has helped you to get rid of adware on Firefox. Please leave your questions, comments or advice in the comments below. Thank you for reading! Read the full article
0 notes
Text
How to Fix "SEC_ERROR_OCSP_FUTURE_RESPONSE" Error in FireFox or Opera
Some firefox user's report the SEC_ERROR_OCSP_FUTURE_RESPONSE error while opening a webpage in Firefox or Opera. The SEC_ERROR_OCSP_FUTURE_RESPONSE error in Firefox or Opera has nothing to do with security settings and it is not related to the web browser at all. The SEC_ERROR_OCSP_FUTURE_RESPONSE error occurs due to a misconfiguration in the device's time and date settings. Firefox throws up the SEC_ERROR_OCSP_FUTURE_RESPONSE error when the time and date settings or not correctly configured. In this article, I'll show you how to easily fix the SEC_ERROR_OCSP_FUTURE_RESPONSE firefox and opera web browser error. Secure Connection Failed An error occurred during a connection to. The OCSP response is not yet valid (contains a date in the future). Error code: SEC_ERROR_OCSP_FUTURE_RESPONSE The page you are trying to view cannot be shown because the authenticity of the received data could not be verified. Please contact the website owners to inform them of this problem.

Fix SEC_ERROR_OCSP_FUTURE_RESPONSE error Firefox and Opera
Open windows control panel, go to Clock, Language, and Region.

Go to set time and date.

Open change date and time settings as Administrator.

Provide the correct date and time settings, restart Firefox for the changes to take effect.

Once the correct date and time settings are provided the SEC_ERROR_OCSP_FUTURE_RESPONSE error in Firefox or Opera will disappear. Easy fix! Read the full article
0 notes
Text
Malwarebytes blocks several Fake adblockers
Malwarebytes has blocked several fake adblockers. The blocked adblockers are fake and can be downloaded from the Chrome Web Store. As a precaution, Malwarebytes blocks the domains of these adblockers, the fake adblocker browser extension is not deleted by Malwarebytes. Users of Malwarebytes will receive a message advising them to remove the malicious adblocker. It would involve millions of fake adblocker installation, according to Malwarebytes. The browser extensions are described as uBlock Plus, Webutation, HD for YouTube, Adblocker for Youtube and more. Malwarebytes recommends to first verify the browser extension before installing an extension in Chrome, also when the extension is downloaded from the Chrome Web Store. Check the Chrome extension permissions and read the End User License Agreement before installing a browser extension.

Fake adblocker installation in Chrome. Read the full article
0 notes
Text
Google searches redirect to Yahoo search? - Malware Removal Guide
Some users report that their Google Searches are being redirected to Yahoo Search, for instance to Yahoo Wajam Search. If you experience this redirect on your PC. The PC is most likely infected with an adware application. Adware such as Wajam, or Searchawesome is known to redirect Google search queries to Yahoo search. The Yahoo searches are monetized using in-text advertisements and the creators of these adware applications are using them to earn revenue. The adware is hijacking Google searches and redirects these to Yahoo search for revenue with advertisements.
Google searches redirect to Yahoo search

you can start looking for adware applications that are installed on your PC. However, this takes a lot of time and the adware is not fully removed. Adware acts like malware, malware is not easy to remove. Often a scheduled windows task or windows service is installed by the adware to remain undetected and reinstalled after manual removal. I, therefore, advise the user to scan with Malwarebytes free and remove the malware responsible for the Google to Yahoo redirect. Malwarebytes will detect the adware responsible for the Google redirect to Yahoo. Remove Google redirect to Yahoo search with Malwarebytes Uninstall adware manually to get rid of the Google redirect to Yahoo search Identify adware and uninstall the adware from your PC, see if this solves the Google redirect to Yahoo. We tested the adware and it did seem to redirect Google searches to Yahoo. The adware installed on our machine was the following, see image below. All applications marked in red are adware, these might be useful identify the adware application on your PC causing the Google to Yahoo redirect.

Remove browser extension or reset the web browser to get rid of the Google redirect to Yahoo Some browser extensions are malicious and redirect the web browser through Google to Yahoo search. In this instructions, you need to identify the browser extension and remove it from your web browser. You can also reset the web browser if the Google redirect remains, however, it most likely malware causing the Google to Yahoo redirect. Read the full article
0 notes
Text
"Update Your Video Player" malware pop-up - Update for 2018 - Real Guide
Update your Video Player malware is distributed to PC's that are infected with Adware. When the PC is infected with Adware the web browser starts displaying popups that tell the PC user to update your video player. The update your video player popup in the web browser is one big scam. The update your video player web page is trying to deceive users into downloading monetized installation software. Once the user agrees to update their video player or install the HD Player the cybercriminal that distributes the monetized installation software earns money for every new installation. The Update your Video Player pop-up might appear out of the blue or displayed when the user visits a specific website or triggers a particular keyword within the content of the webpage. It is unknown when an update your video player popup will show up. However, we already know it has something to do with a virtual layer. What I mean by a virtual layer is a layer that added by the Adware and waits for a specific word or term shows up on screen, when it happens the popup to the malicious update your video player domain is shown. It is like keyboard keylogging only then for web pages to be visited or specific words to show up on screen.

This is the newest graphical user interface (2018) of the update your video player popup. In the years this update video player scam has actively distributed the interface of the scam web pages has changed several times. Update your Video Player pop-up removal Additional information: Update your Video Player: Download Removal Tool Distribution: Adware, Potentially Unwanted Programs (PUPs), Malware. Also known as: Update your Video Player redirect, Update your Video Player pop-up, Update your Video Player ads. Affected Browsers: Google Chrome, Mozilla Firefox, Internet Explorer, and Microsoft Edge. Type: pop-up redirect The Update your Video Player redirect appears as a web-browser pop-up when adware, e.g. an ad-supported malware application is installed on the PC. Adware is monetized software, designed to display intrusive commercials in the style of pop-ups on the infected PC. Some website's that provide suspicious services such as free games, free downloads or free toolbars are likely to monetize their free downloads with Adware for revenue.

Update your Video Player popup redirect the Google Chrome, Firefox, Internet Explorer or Microsoft Edge browser through a variety of web pages. Many of the redirects lead to web pages that earn revenue for the Adware developers. Associated signs of an Adware infection result in configuration changes in the web browser homepage, search engine, and new tab. Adware also causes hyperlinks to redirect to web pages different from what the user expected and pop-ups displayed on the internet web-browser with unknown content.
How to remove Update your Video Player?
Update your Video Player Removal Tool Step 1 - Remove Update your Video Player with Malwarebytes Step 2 - Remove Update your Video Player with Zemana Uninstall adware responsible for the Update your Video Player redirect Remove Update your Video Player from Internet Explorer Remove Update your Video Player from Google Chrome Remove Update your Video Player from Firefox Remove Update your Video Player from Microsoft Edge If you need help, use the comments at the end of this article. I am here to help you.

Step 1. Remove Update your Video Player with Malwarebytes

Step 2. Remove Update your Video Player with Zemana Antivirus

Uninstall adware to get rid of the Update your Video Player pop-up.
In this first step to remove Update your Video Player malware, you should verify the software application responsible for the Update your Video Player pop-up. Understand that there might no entry in the software application list resembling Update your Video Player popup. Adware is responsible for the Update your Video Player pop-up. However, adware goes by many different names, look carefully and uninstall any application you do not know or need.

Remove Update your Video Player popup from Internet Explorer, Chrome, Firefox or Microsoft Edge.
In this second Update your Video Player popup manual removal step, you need to identify the browser extension or web browser settings responsible for the Update your Video Player popup. Begin with the verification of malicious browser extension(s) and follow up with a reset of the infected web browser. Select your web browser from the tabs below to begin. Read more on how adware pop-ups work or how malvertising works, the update your video player is a malvertising scam. Read the full article
0 notes
Text
Cómo eliminar GeoSmartDNS anuncios "Ads by GeoSmartDNS" virus
GeoSmartDNS es una aplicación de adware engañosa. La versión 1.0 de GeoSmartDNS modifica la configuración del navegador web (muestra anuncios intrusivos sin valor) y recopila diversa información relacionada con la actividad de navegación por Internet del usuario. Por estas razones engañosas específicas, GeoSmartDNS está categorizado como un programa de adware. GeoSmartDNS es idéntico a GeoSmartDNS. Muchos sitios web de descargas favoritos que ofrecen a los administradores de descargas monetizar su software gratuito y el tráfico de Internet a través de los administradores de descargas. Son estos gestores de descargas los que utilizan despliegues de adware engañosos y peligrosos y empiezan a mostrar anuncios en sitios web favoritos con hipervínculos subrayados como "anuncios de GeoSmartDNS", "Ads by GeoSmartDNS". Una vez que un programa de adware está instalado en su ordenador. El adware GeoSmartDNS recoge las preferencias del navegador de Internet Explorer, Google Chrome o Firefox e instala una extensión del navegador. Estas extensiones maliciosas del navegador son conocidas por abrumar a los usuarios de computadoras con anuncios intrusivos dentro del navegador.

Si instala software descargado de Internet, tenga en cuenta que no hay ofertas adicionales o mejoras útiles instaladas en su ordenador. Algunos gestores de descargas no revelan adecuadamente que el adware o los cachorros, como esta versión 1.0 del GeoSmartDNS, también se instalarán en su ordenador. Al instalar software en el equipo, debe consultar los Contratos de licencia de usuario final (CLUF) o sus Condiciones de uso antes de descargar e instalar software en el equipo. No haga clic demasiado rápido en el proceso de instalación utilizando el botón Instalación rápida del botón Siguiente; esto evitaría la versión 1.0 del GeoSmartDNS en el futuro. De cualquier manera, es a menudo el propio usuario del ordenador el que permite que el adware de la versión 1.0 del GeoSmartDNS se instale en su ordenador.
Cómo eliminar GeoSmartDNS


usuarIos de Windows 7 : haga clic en el botón Inicio en la esquina inferior izquierda seleccione Panel de control seleccione "programas y funciones".


usuarIos de Windows 8 y Windows 10 : haga clic con el botón derecho en el logotipo de Windows en la esquina inferior izquierda seleccione Panel de control seleccione "programas y funciones".

Consulte la lista de aplicaciones para el actualizador de GeoSmartDNS, HENLEY version 1.5 (cualquier cosa con la versión 1.5 en su nombre de aplicación), ProxyGate version 3.0.0.1176 Seleccione la aplicación y haga clic enel botón "desinstalar". Haga clic en la columna "instalado en" para ordenar el software instalado por fecha esto hace más fácil detectar software recientemente instalado.

Quitar GeoSmartDNS malware y sobras con Malwarebytes
El GeoSmartDNS deja rastros y suele instalarse con aplicaciones de adware compatibles con anuncios. Realice un escaneo completo del sistema con Malwarebytes para limpiar todo su PC de malware. Malwarebytes es libre de detectar y eliminar malware. Read the full article
0 notes
Text
Cómo eliminar Multitimer malware - Instrucciones de eliminación de virus
Multitimer versión 1.0 es una aplicación de adware engañosa. La versión 1.0 de Multitimer modifica la configuración del navegador web (muestra anuncios intrusivos sin valor) y recopila diversa información relacionada con la actividad de navegación por Internet del usuario. Por estas razones engañosas específicas, Multitimer versión 1.0 está categorizado como un programa de adware. Multitimer versión 1.0 es idéntico a Fastdownload versión 1.0, ShutdownTime versión 1.0, BZip versión 1.0, BetterAds versión 1.0 y BeClean versión 1.0. Muchos sitios web de descargas favoritos que ofrecen a los administradores de descargas monetizar su software gratuito y el tráfico de Internet a través de los administradores de descargas. Son estos gestores de descargas los que utilizan despliegues de adware engañosos y peligrosos y empiezan a mostrar anuncios en sitios web favoritos con hipervínculos subrayados como "anuncios de Multitimer". Una vez que un programa de adware está instalado en su ordenador. El adware Multitimer versión 1.0 recoge las preferencias del navegador de Internet Explorer, Google Chrome o Firefox e instala una extensión del navegador. Estas extensiones maliciosas del navegador son conocidas por abrumar a los usuarios de computadoras con anuncios intrusivos dentro del navegador.

Si instala software descargado de Internet, tenga en cuenta que no hay ofertas adicionales o mejoras útiles instaladas en su ordenador. Algunos gestores de descargas no revelan adecuadamente que el adware o los cachorros, como esta versión 1.0 del Multitimer, también se instalarán en su ordenador. Al instalar software en el equipo, debe consultar los Contratos de licencia de usuario final (CLUF) o sus Condiciones de uso antes de descargar e instalar software en el equipo. No haga clic demasiado rápido en el proceso de instalación utilizando el botón Instalación rápida del botón Siguiente; esto evitaría la versión 1.0 del Multitimer en el futuro. De cualquier manera, es a menudo el propio usuario del ordenador el que permite que el adware de la versión 1.0 del Multitimer se instale en su ordenador.
Cómo eliminar Multitimer version 1.0


usuarIos de Windows 7 : haga clic en el botón Inicio en la esquina inferior izquierda seleccione Panel de control seleccione "programas y funciones".


usuarIos de Windows 8 y Windows 10 : haga clic con el botón derecho en el logotipo de Windows en la esquina inferior izquierda seleccione Panel de control seleccione "programas y funciones".

Consulte la lista de aplicaciones para el actualizador de Multitimer version 1.0 Seleccione la aplicación y haga clic enel botón "desinstalar". Haga clic en la columna "instalado en" para ordenar el software instalado por fecha esto hace más fácil detectar software recientemente instalado.

Quitar Multitimer malware y sobras con Malwarebytes
El Multitimer deja rastros y suele instalarse con aplicaciones de adware compatibles con anuncios. Realice un escaneo completo del sistema con Malwarebytes para limpiar todo su PC de malware. Malwarebytes es libre de detectar y eliminar malware. Read the full article
0 notes
Text
How to Fix the "Failed - Network Error" in Google Chrome
Google might have difficulties when downloading files from the internet. In some cases, the Failed - Network Error might show up and the download is stopped and cannot be resumed. There are a few options to consider to resolve and fix the Failed - Network error in Google Chrome.
Fix the Failed - Network error Google Chrome
Check your PC for malware The failed network error on Chrome could be a sign the PC is infected with malware. Malware is known to block connections, or redirect connections through a malicious proxy server. When a connection is tunneled through a malicious proxy server the malware is able to monitor and control the internet traffic, for instance, inject advertisements or block downloads causing the Failed network error. We have seen this is in severe adware, GeoSmartDNS, Proxygate, and VidSquare. Adware or could be the cause of the Failed network error on Chrome. The first step I recommend is using the Google Chrome perform a "Harmful software" virus detection tool. Google Chrome has a useful feature to automatically detect and remove harmful applications from your web browser and PC. The Chrome Harmful software detection and removal tool are not as comprehensive as for instance, Malwarebytes. Make sure you are not infected with malware and run a Malwarebytes adware detection and removal scan, it is free. Remove browser extension Browser extensions for Google Chrome are designed and created to add new features, themes or new functionality to Google Chrome. However, most of them need an internet connection to communicate with some server. On slower internet connections, the browser extension might disrupt normal internet-traffic and cause the Failed network error within Chrome. I advise checking the installed browser extensions and disable them one by one to see if the problem is resolved. Once you found a browser extension that is the cause of the network error in Chrome, remove the extension. Learn more about how to remove a browser extension in Chrome. Try another web browser Another option to find out if Google Chrome is the main cause of the Failed network error is to try another web browser. If you were downloading a file or visiting a webpage through Chrome and the failed network error occurred, try another web browser and see if you are able to download or visit that specific webpage with the new web browser. Try using Internet Explorer or Microsoft Edge these web browsers are already installed on the most recent Windows operating systems. However, it might be best to choose a not so common web browser, we've made a list of 6 alternative web browsers to Chrome, Firefox, Internet Explorer, and Microsoft Edge. The point is to identify if the failed network error only happens in Chrome or also in another web browser. If the failed network error or some other network connection error occurs in other web browsers too, the problem is most likely in Windows, your internet connection or router. Repair Failed Network Error Chrome - advanced connection error A connection error is not always caused by a web browser. The Chrome web browser might not be able to connect to the internet or show the Failed - Network error, however, the underlying problem is a network adapter setting or a firewall problem in Windows. In order to solve these problems all at once, there is a tool NetAdapter Repair all in One that does this for you. If you use this tool wisely as I am going to show you there should be no problems. The NetAdapter Repair all in One tool is very powerful and it is possible to corrupt internet-connection or network settings with this tool. Therefore I recommend to make create a Windows restore point, so you can revert back to the point in time restore if anything goes wrong.

Open the NetAdapter Repair all in One tool as Administrator. Right-Click the executable and select Run as Administrator from the list confirm with yes. Click the large button in the left upper corner that says Advanced Repair. The Advanced Repair tool will repair the Winsock TCP/IP settings in Windows. Clear all Proxy/VPN Settings and tries to repair the Windows Firewall. If this was working before it stays as is, the NetAdapter Repair all in One tool performs actions recommended by Microsoft to resolve problems with internet or network connections. Restart your PC and verify if the internet connection and failed network error are resolved. Reset Google Chrome settings If the problem Failed Network error only occurs in Google Chrome, some settings might get corrupted. This could be due to malware, a browser extension or an external software application. The first approach before you reinstall Google Chrome is to reset Google Chrome to default. Restoring Google Chrome to default will not affect your bookmarks, saved passwords and browser history. Learn how to Reset Chrome to default settings. Check for Chrome updates verify if there any updates available for Google Chrome, updates resolve problems and the latest version of Chrome might solve the network failed error for you. Learn how to update Google Chrome. Reinstall Google Chrome The last possibility you should attempt is to reinstall Google Chrome. It is obvious that if the Failed Network - error is only happening in Chrome the fastest approach to resolve the network error is to reinstall Chrome. Uninstall Google Chrome first and download the newest version from the official webpage. Read the full article
0 notes
Text
How do I get rid of a pop up on safari? adware removal instructions
Your Mac is a masterpiece, and every one that owns a Mac would like to keep it that way. Do get Mac's infected with adware? Unfortunately, the answer is yes, especially the Safari web browser. Since the popularity of Apple products, scammers such as deceptive advertisers and suspicious advertisement networks target the Safari web browser with pop-ups and adware. When a Mac is infected with adware, the inbuilt web browser Safari is showing advertisements and is redirected through a variety of pop-ups. There are many examples or pop-ups that often occur when the Safari web browser on Mac is infected, for example, Your Mac be Infected scam pop-up, fake virus infected tapsnake virus pop-up. The pop-ups on a Mac are often employed to sell the user potentially unwanted programs, install more adware with a or scare the Safari user their Mac is infected with a virus. Adware is most likely responsible for the pop-up in Safari. Adware is software designed to infect Mac's during the installation of software you can download from the internet. Adware is what we call bundled with software as a third party offer. Bundle implies it is offered to the visitor during installation, however, the offer is barely visible and therefore installed without the user's consent. As soon as adware is presenting unwanted pop-ups in Safari, people often notice something is wrong and their Mac might be infected with malware.
How do I get rid of a pop up on safari?
browser extension Safari has the ability to add browser extensions to the web browser. Browser extensions are designed to enhance the Safari web browser with new features or functionality. However, adware is known to secretly install browser extensions that only have one purpose, show pop-ups and alter the homepage and search engine on Safari. It is important to check for any browser extension in Safari and remove the extension if you never intended or did install an extension. Open Safari, in the top, left corner click Safari and Preferences or press Command key (⌘) + , (comma). Click the Extensions tab and verify if Safari has an extension installed you don't know or need. Click Uninstall to remove the extension from Safari.

clear Safari cache and remove potentially unwanted applications Just as all other web browsers Safari saves caches on your Mac. Some web pages that are compromised or designed to display intrusive pop-ups in Safari are known to place the cache on your Mac that might cause pop-ups. Also. potentially unwanted programs such as Mac Adware Cleaner (which is malware) are known to display intrusive pop-ups in Safari on a Mac. With CleanMyMac you can clear the Safari cache and pop-ups from showing on a Mac.

CleanMyMac also includes features as a Safari extension removal tool, potentially unwanted program uninstall tool and more tools to optimize and protect your Mac from Adware and the associated pop-ups in Safari.


CleanMyMac is highly advised to optimize and protect your Mac. remove malware on Mac with Malwarebytes Another great application to protect your Mac against adware and popups is Malwarebytes. Malwarebytes is designed to detect and remove the latest malware threats that infect a Mac. As we know adware is software designed to show many unwanted pop-ups, redirects in the Safari web browser.

Malwarebytes will remove the adware responsible for the popup in Safari. However, Malwarebytes is like an antivirus for your Mac and does nothing to optimize your Mac as CleanMyMac does. If you think your Mac is highly infected with adware, try Malwarebytes for free.

Malwarebytes offers a 30-day premium trial license, which includes real-time protection. After 30-days Malwarebytes reverts back to the free version, which does not include real-time protection but is still able to detect and remove adware from your Mac PC and Safari web browser for free. I hope this information was usefull to you. The information in this article should have helped you get rid of pop-ups in Safari for a Mac. Have a question or leave reply, use the comments below this article. Read the full article
0 notes
Text
How to change Google Chrome browser language? Mac and Windows
Did you know you could easily change the language in Google Chrome without a reinstall? There are two language configurations in Google Chrome, the first configuration is the language you would want web pages to recognize when you visit their web page, and the second is the user-interface language of Google Chrome. In the first language setting, the language recognition by web pages is used to detect the Accept-Language header sent by the Chrome web browser. If the web browser sends an HTTP request to a web server to fetch a web page, the browser sends an HTTP-request in return to the web server. The HTTP-request the web browser sends in return includes a language preference setting, the Accept-Language header. This Accept-Language header tells the web server which language is the Chrome web browser's preferred language to display the web page in. The second language configuration in Google Chrome is the preferred language graphical user interface. It is possible to display Google Chrome in your preferred language and view web pages in another language, let's find out how to configure this in Google Chrome.
Change Google Chrome language preference
Open the Google Chrome browser if you didn't already. Click the Chrome menu button in the top right corner and select Settings from the drop-down list.

Scroll down in the Chrome settings till you see Advanced, expand the advanced settings in Chrome.

Scroll down till you see Languages and expand the languages preferences in Chrome.

In the Chrome language preferences, you see the installed languages and the language Chrome is currently displayed in. If you would like to add a language to Google Chrome, click the Add languages button.

Search for the language you would like to add to Google Chrome. In this example, I used the Spanish language. Click the Add button to add the language you would like to add to Chrome.

Click the three dots icon, right next to the language you just added to Chrome. Now, when you want to change the language a web server detects when you visit a web page, you click the Move to the top button. What this does is it tells the web server your preferred language is Spanish (in this example) and when available will redirect the web browser to the Spanish version of the web page. Google Chrome, however, is still displayed in English (United States). If you want to change the display language of Chrome, read on. It's easy!

In the same menu, check the Display Google Chrome in this language.

Relaunch Google Chrome for the changes to take effect.

Google Chrome is now shown in the display language you prefer. It's that easy, no need to reinstall Google Chrome in another language, you can just change the display settings from the Chrome web browser itself. It is also possible to add another profile, person to Chrome and change the language for the new profile.

Read the full article
0 notes
Text
Remove "Ads by GeoSmartDNS" virus - Chrome, Firefox, Internet Explorer
Ads by GeoSmartDNS are shown when the web browser is infected with a malware application. GeoSmartDNS is promoted as a tool to surf the internet without restrictions, GeoSmartDNS acts as a DNS proxy and it is. However, GeoSmartDNS is ad-supported and installed without the user's consent on their PC. Once the GeoSmartDNS application has been installed on the PC, the GeoSmartDNS application collect's browser's Internet Explorer, Google Chrome or Firefox preferences and information. GeoSmartDNS displays ads in the Chrome, Firefox, Internet Explorer or Edge web browser as "Ads by GeoSmartDNS", "Ad by GeoSmartDNS" or "Powered by GeoSmartDNS".

Ads by GeoSmartDNS are not random, the ads are based on the user's internet activity, the content of the website and user-based browser interests. GeoSmartDNS ads are to be distinguished by new browser pop-up window ads and browser redirects to malicious web pages.
How did GeoSmartDNS install on my device?
Additional information: Danger:

Distribution: Download managers, deceptive pop-up redirects Also known as: GeoSmartDNS virus, GeoSmartDNS adware Type: Adware, Potentially Unwanted Program Similar to: ProxyGate, Ads by Epsilon, Ads by Setli, Maxi Buy, Betterworld adware The most common reason for the GeoSmartDNS malware installation is poor knowledge. User's careless behavior and poor knowledge of adware can result in the GeoSmartDNS installation. Internet web pages that redirect the browser to suspicious popup ads are most likely build to deceive the user into adware & potentially unwanted applications. Analyze every installation process and opt out any additional applications.
What is GeoSmartDNS?
GeoSmartDNS does not provide any real benefit to its user. GeoSmartDNS is known to collect all sorts of information from the PC but pretends to offer a variety of browsing enhancements such as browsing the internet without restrictions. In reality, GeoSmartDNS is all about in-text ads, malicious website traffic, and suspicious browser redirects. GeoSmartDNS developers, often claim to have no control over the users' advertisements. In our experience, these adware type applications are only built to generate revenue for the developers, rather than providing any useful functionality.
How to remove Ads by GeoSmartDNS
Use this menu to uninstall and remove the GeoSmartDNS malware.
Remove GeoSmartDNS, complete the steps below
GeoSmartDNS removal tool Step 1 - Recommended! Remove Ads by GeoSmartDNS with Malwarebytes GeoSmartDNS manual removal instructions Uninstall GeoSmartDNS

Step 1. Remove Ads by GeoSmartDNS with Malwarebytes
if (navigator.userAgent.indexOf('Mac OS X') != -1) { document.write("It seems you are using a Mac, clean your Mac with CleanMyMac 3 by MacPaw (more information). 3 million+ downloads worldwide. ") }


Windows 7 users: Click the Start button in the left bottom corner, select Control Panel, select "Programs, and Features".


Windows 8 and Windows 10 users: Right-click the Windows logo in the bottom left corner, select Control Panel, select "Programs and Features".

Check the recently installed applications, search for an application GeoSmartDns, ProxyGate version 3.00.1176, Shopper-Pro, YTDownloader, Best Offers. If you don't know what to look for, Goto GeoSmartDNS Removal Tool (recommened) Read the full article
0 notes
Text
Remove Letsupdateourdomain.com redirect - Virus Removal Instruction

Letsupdateourdomain.com is a dangerous redirect. Letsupdateourdomain.com redirects the Chrome web-browser, Firefox, Internet Explorer or Edge through a variety of intrusive ads, for example, Reimageplus.com ads. Letsupdateourdomain.com is used by cybercriminals to earn revenue by displaying intrusive ads in the style or pop-ups and redirect to the PC user. Letsupdateourdomain.com is identical to other redirects that are associated with malware, more specifically adware, such as laserveradedomaina.com redirects, Laborates.com redirect, Swuchab.win redirect, Cobalten.com redirect, go.oclaserver.com redirect, go.oclasrv.com redirect, Direct.redtrafficchoose.site redirect, and the Phu1aefue.com redirect. The letsupdateourdomain.com redirect might emerge out of the blue or shown when the user visits a specific website. Adware is known to trigger redirects in the web browser when the user hovers over a particular keyword within the content of the webpage is viewing at that moment.

Letsupdateourdomain.com redirect (pop-up) removal Additional information: Letsupdateourdomain.com: Download Removal Tool Distribution: Adware, Potentially Unwanted Programs (PUPs), Malware. Also known as: Letsupdateourdomain.com redirect, Letsupdateourdomain.com pop-up, Letsupdateourdomain.com ads. Affected Browsers: Google Chrome, Mozilla Firefox, Internet Explorer, and Microsoft Edge. Type: pop-up redirect The Letsupdateourdomain.com redirect appears as a web-browser pop-up when adware, e.g. an ad-supported malware application is installed on the PC. Adware is monetized software, designed to display intrusive commercials in the style of pop-ups on the infected PC. Some website's that provide suspicious services such as free games, free downloads or free toolbars are likely to monetize their free downloads with Adware for revenue. Letsupdateourdomain.com web-browser pop-ups, redirect the Google Chrome, Firefox, Internet Explorer or Microsoft Edge browser through a variety of web pages. Many of the redirects lead to web pages that earn revenue for the Adware developers. Associated signs of an Adware infection result in, unwanted configuration changes in the web-browser homepage, search-engine, and new-tab. Hyperlinks redirect to web pages different from what the user expected and pop-ups displayed on the internet web-browser with unknown content.
Remove Letsupdateourdomain.com redirect (pop-up)
Use this menu to get rid of the Letsupdateourdomain.com redirect. The easiest and most complete procedure to remove the Letsupdateourdomain.com redirect and the associated malware is using the malware removal tool. However, we do offer manual letsupdateourdomain.com redirect removal instructions for our visitors. Be aware malware could be left on the PC after manual removal. Letsupdateourdomain.com pop-up removal tool Step 1 - Remove Letsupdateourdomain.com with Malwarebytes Step 2 - Remove Letsupdateourdomain.com with Zemana Anti-Malware Letsupdateourdomain.com redirect - Internet Explorer, Chrome, Firefox and Microsoft Edge manual removal instructions

Step 1. Remove Letsupdateourdomain.com redirect with Malwarebytes

Step 2. Optional step, remove Letsupdateourdomain.com pop-up with Zemana

Uninstall adware to get rid of the Letsupdateourdomain.com pop-up web-browser redirect.
In this first step, we show you how to detect and manually uninstall adware responsible for the Letsupdateourdomain.com pop-up redirect. After you have uninstalled any adware application(s), perform a malware scan with the malware removal tool to remove any traces from your PC to be certain the Letsupdateourdomain.com redirect is entirely removed from the with malware infected PC.

Remove Letsupdateourdomain.com pop-up redirect from Internet Explorer, Chrome, Firefox and Microsoft Edge.
In this second step, we show you how to manually remove the Letsupdateourdomain.com pop-up and redirect from the web browser. If after these manual removal steps, there are still ads, pop-ups or browser redirects matching Letsupdateourdomain.com in the Internet Explorer, Chrome, Firefox or Microsoft Edge web browser? Remove the malware responsible for the Letsupdateourdomain.com redirect with our recommended malware removal tool. Read the full article
0 notes