Don't wanna be here? Send us removal request.
Text
Find Unique Parameters using katana
Hello, All welcome back to another blog of the bug bounty series in this blog I’ll show an example of how you find parameters to test SQL, XSS, command Injection, etc.. so without any delay let’s get started. First of all, we need to install the katana tool you can install it by entering this command in your terminal and making sure go language is installed and configured properly in your Linux…
2 notes
·
View notes
Text
How I Earned $150 for an "Out of Scope" Rate Limit Bug
One day, as I was browsing through Bugcrowd’s platform, I decided to check out some of the newly listed programs for potential bug hunting opportunities. While scanning through the list, I came across an interesting target. As always, my first step was to thoroughly review the program’s policy and scope to understand what was and wasn’t allowed. The target had two main domains listed under its…

View On WordPress
1 note
·
View note
Text
How I Discovered and Reported Two Subdomain Takeovers
I am constantly searching for potential vulnerabilities because I am an avid security enthusiast and bug bounty hunter. I recently discovered two subdomain takeovers thanks to a private invitation I received on HackerOne. This is a detailed explanation of how I found and reported these vulnerabilities. I got a private invitation to take part in a security program on HackerOne. The invitation…
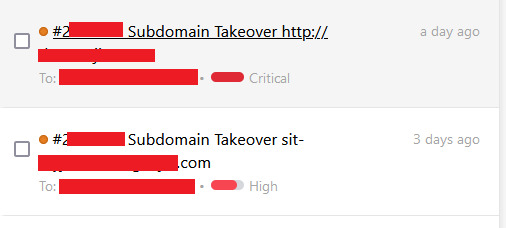
View On WordPress
1 note
·
View note
Text
Advance Bug Bounty
Learn Bug Bounty , Ethical Hacking , Cyber security , HTML , CSS , Python , Javascript , C++ , C# end more from scratch...
1 note
·
View note