Don't wanna be here? Send us removal request.
Text
Week 8: #SecurityEverywhere
Police in the UK are giving first-time cybercriminals the opportunity to use their talents for good. The initiative aims to reform tenage hackers, and educate them about the consequences of illegal cyber activity, while providing them with possible careers paths that they can take to become an ‘ethical’ hacker. More than 400 youngster have benefited.
0 notes
Text
Natas: Level 28
In this level we are given a joke database which we can search. There is no provided code for this level.
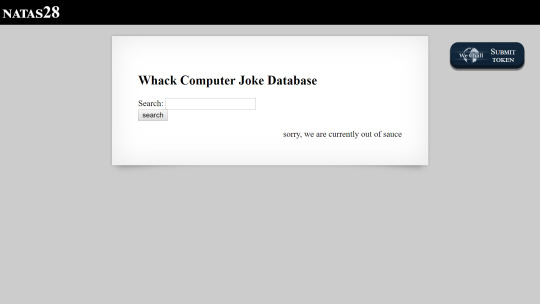
After searching a few times, I noticed something interesting about the url. The query paramater seems like a long list of random letter and numbers, particularly reminicent of something that has been base64 encoded.

Altering the query gives this error.
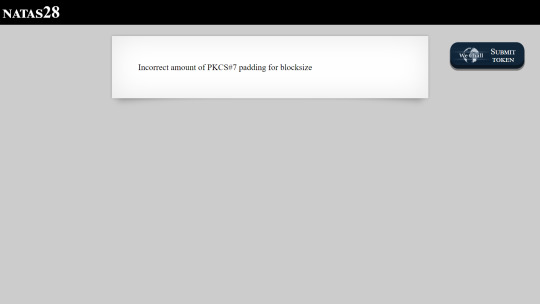
Searching for PKCS gets us to the wikipedia article explaining that it stands for Public Key Cryptography Standards. Reading a bit further down gets us the link to PKCS#7 which is Cryptographic Message Syntax. But CMS is just a standard, it doesn’t really help us much with this problem.
Thinking back to the previous problem where we made user of changing the query param to an array. I tried a similar message and got this useful warning.

So clearly base64_decode is being used. Taking the query string, url decoding it and then base64 decoding it gives us this result.
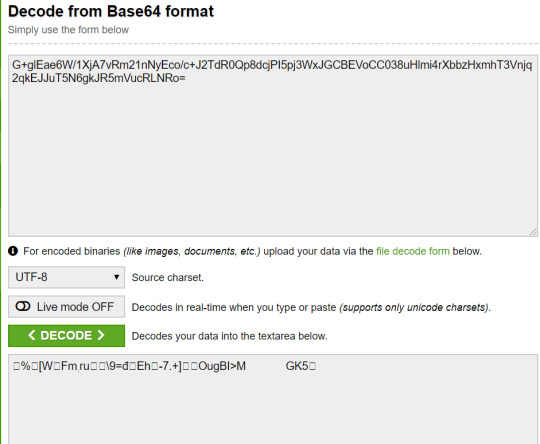
Which isn’t very helpful...
It’s likely that the query string has been encrypted before being base64 encoded.
I also tried doing a few searches with different length strings to see what would happen. (I’ve seperated them with spaces to highlight which parts are the same)

Clearly there are certain similarities, such as the leading part of every sequence (most likely a fixed length string). We can also observe that the second part varies with every different input, whereas the third part only differs for different length inputs.
Unfortunately I don’t really know how to continue this level from here...
1 note
·
View note
Text
Week 8 Analysis Session
This weeks analysis session was mostly reserved for presenting our something awesome projects. I think my presentation went quite well. I tried to summarise what I’d done as quickly as possible, and walked through one of the shorter CTFs that I’d completed as a demonstration of my work.
The case study was as follows:
Suppose you are the friendly Major M from the base who can see the alien A but who cannot see the invisible man X.
Q: What would you M do to get from X his report on the Alien's (A's) planet?
Once again we split into groups to discuss the various ways in which to get the report from the invisible man. Our group had some ideas but they were based on unlikely assumptions, like asking the alien to leave the room so we can provide the ghost with a one-time-pad.
I think the main purpose of this case study was think about ways to ensure integrity. It didn’t really matter if the alien heard the report, as long as we can know for sure that the report has not been altered by the alien.
0 notes
Text
Week 8 Homework
This weeks lectures covered human mistakes and errors, and how they have lead to disasters.
Chernobyl:
Home to 14,000 people
First nuclear power station built in Ukraine
Reactor number 4 exploded on the 26th April 1986
Worst nuclear disaster in the history of the world
Radioactive dust sent all over Europe (as far as Sweeden)
Directly related deaths:
31 deaths as a result of the explostion
50 deaths from radiation exposure
WHO states that around 4000 deaths can be attributed to radiation exposure from the event
How it happened:
Workers were performing a test to see if the turbines could provide enough energy to keep the coolant pumps were running if there was a loss of power (until the emergency deisel generator kicked in)
Previous tests done but unsuccessful
Lowered capacity of reactor to 25%, but it started plummeting down to 1%
Tried to increase the power, but the power surged and the emergency shutdown failed.
One engineer wanted to abort, but was forced to continue
Considerable pressure, and the heavy blocks above the fuel channels of the upper biological shield began to jump up and down
Pumps failed, no waterflow, and reactor started to make loud noises
A perculiarity of the design of the control rods caused another power surge as they were inserted into the reactor
Hot fuel + cool water created a massive steam that caused massive pressure
Lifted a 1000 tonne lid and radiation leak started.
Air in the reactor caused a graphite fire
Second larger explosion caused by hydrogen formed from steam contacting zirconium
Radiation was leaked everywhere
0 notes
Text
Hack The Box: Emdee five for life
In this CTF, the user is presented with a plain text, and a form. The goal is to enter the MD5 hash of the text sufficiently quickly.
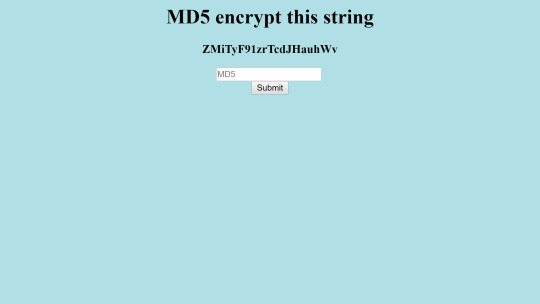
If you enter the hash too slowly, or enter an incorrect hash, then it will tell you that you are too slow.

Digging through the network requests being made, we can see that the intial request for the page is a get request, and submitting the hash is a post request.
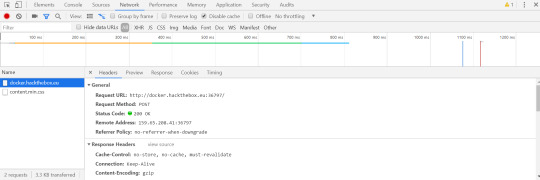
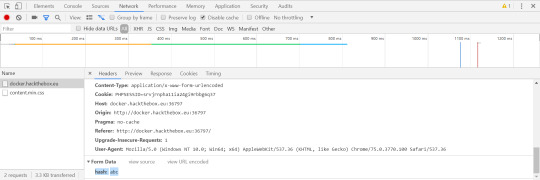
We can also see that in the post request, there is a payload of ‘hash’ with the hash entered by the user.
In order to solve this I decided to write a python script. The aim of the script is to start a session, request the page and then automate the job of hashing the text and submitting it.
I wasn’t really sure how to do an md5 hash in python, but I found an easy way to do it after a bit of googling: https://stackoverflow.com/questions/5297448/how-to-get-md5-sum-of-a-string-using-python
After making and running the script, we are able to get the flag.

This was a pretty straightforward CTF, and I felt like I could make good use of a lot of the python scripting skills that I gained from doing the Natas challenges.
0 notes
Text
Natas: Level 27
In level 27 we are given a login form. When attempting to login with any random username and password, we are told that we have created a new user.
Logging in as that same user again gives us

Looking through the code, we see that we have a database with a ‘users’ table. If the username entered is not already in the table, then a new user is created and added to the database.
If the username is in the database, but the supplied password is incorrect, then we’ll be told that we have the wrong password.
If both the username and password are correct, then all the information about the user will be displayed (like in the above image).


Similary to the previous challenges involving a SQL database, there is a user named natas28 (the name of the next level) whose password we want to find.
Since we know that natas28 is a user, maybe we can try exploit the function ‘checkCredentials’.
However it looks as though mysql_real_escape_string is being used to sanitise our user input. In order to carry out a successful SQL injection, we will need to find a way to bypass it.
After a lot of digging, it seems that this isn’t the correct path to take. Since the user input is both passed through mysql_real_escape, and is surrounded by single quotes, it’s extremely difficult inject additional SQL commands.
So there must be another way in which to get the password. But the only method I can think of is to get another user into the database with username natas28. This would result in the real natas28′s password being returned when logging in as the ‘fake’ user.
How do we even get user with the same name into the database? Well we notice that in the table, the username and password are defined as type varchar(64). This means that these fields have a maximum length of 64 (even less because 1 or more byte is usually used to store the size of the string), and anything over this maximum will be truncated. From playing around with the login form, we also notice that trailing spaces are ignored when querying the database.
Using this information, we can attempt to overload the maximum length of the username to enter another ‘natas28′ into the table.
First we login with the credentials:
username = natas28 <approx. 60 spaces> <any character>
password = <anything>
validUser will fail as there is no user that matches the provided username (this wouldn’t be the case if we hadn’t added a random character at the end of our username).

The new user will be added to the table, but since the length of the username is greater than 64, the name of the user in the table will be ‘natas28′ followed by spaces.
We can now login using the username ‘natas28′ and the password for the user we just created.
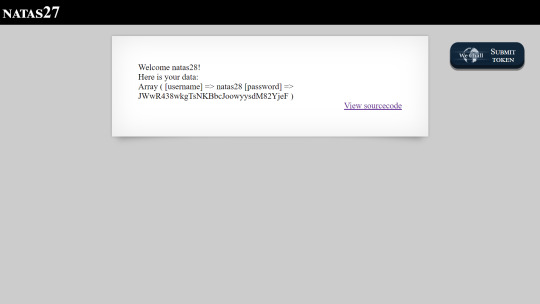
Doing so causes the data for the user ‘natas28′ to be dumped, delivering us the flag.
0 notes
Text
Natas: Level 26
In this level you can draw a line by giving coordinates.

Looking at code, there is no obvious place where user input from the get request is being used.


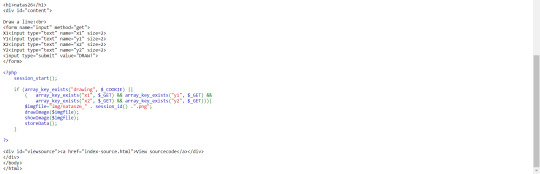
But there is an suspicious Logger class that isn’t being used anywhere, so this is obviously relevant to the challenge.
Digging around on OWASP, I came accross https://www.owasp.org/index.php/PHP_Object_Injection
With some trial and error, I managed to make my own Logger class and serialize it. This logger class has the same variables as the one in the source code of the challenge, however I have set the private variables so that a php script is printed to the log file. Due to the magic methods being used in the class, we know that the deserialised Logger object will call it’s __destruct method when the function goes out of scope or the script ends (https://stackoverflow.com/questions/2777942/php-destructor-behaviour).
At first, we will test if a text file will show up. Then if it works, we will change the file extension to php
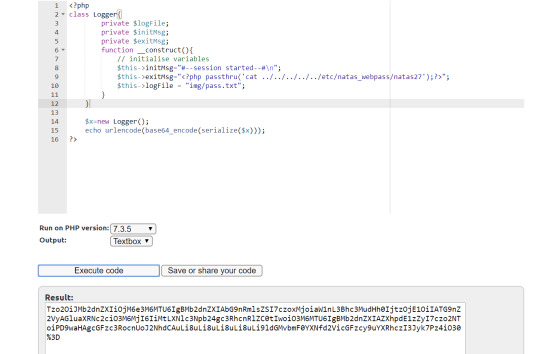
We then copy the serialized Logger into our browser as the ‘drawing’ cookie.
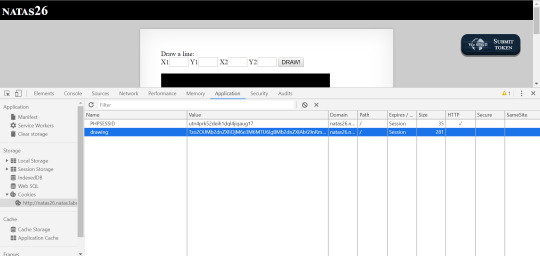
Reloading the page to visit /img/pass.txt gives us the expected result.
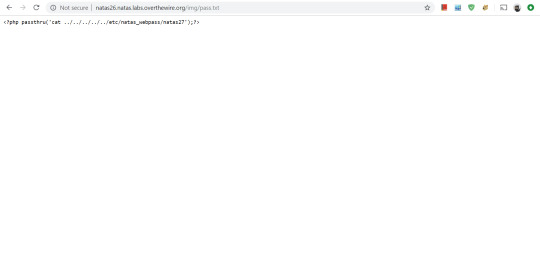
Yay it worked. So now we can attempt the same thing with the .php extension so that the code will be executed by the server.

And we get the password as expected.
0 notes
Text
Natas: Level 25
We get a quote shown on the page and the option to change the language.

Looking at the code to see how the language is changed, it is obvious that we will conduct a path traversal to get the password.
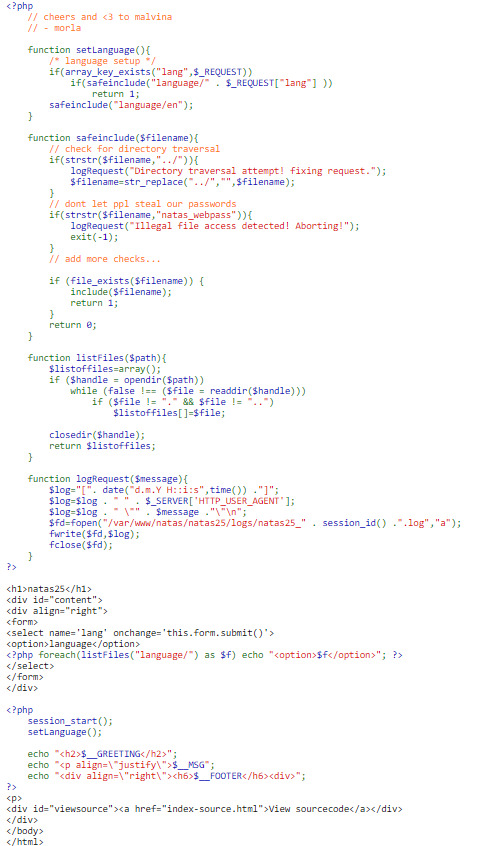
But ‘../’ is removed, and natas_webpass is also removed in the safeinclude function.
Could there be a way to bypass strstr? After some research I don’t think it’s possible.
However, doesn’t str_replace just remove all instances of the substring within a string? If that’s the case, then what if we have the string ‘.../...//’. Then str_replace("../","", “.../...//”) will be ‘../’. We can use this to change the directory of the included file.
But we still can’t get natas_webpass into the string without the php code bailing. Although we can navigate to the logs folder.

We can also see that $_SERVER['HTTP_USER_AGENT'] is included in the logs. Since ‘User Agent’ is just a header that we provide in our request to the website, we should be abe make our own request and set ‘User Agent’ header to a php script.
Then by including the logs file containing this script (using the ‘.../...//’ method), we should be able to get the password.
As expected, our php script is executed, and we get the flag.
0 notes
Text
Natas: Level 24
This level requires us to enter a password that we don’t know to complete level.
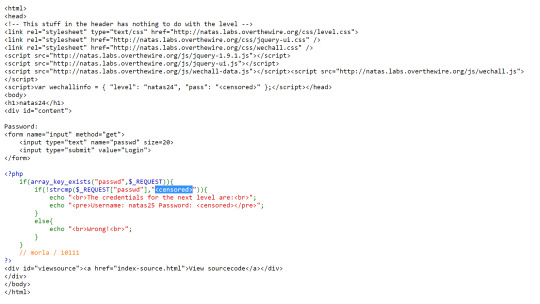
The key point from looking at the code is that the strcmp function is used to compare user input to the actual password.
Since the if statement is looking for !strcmp, then maybe if we try a string whose value is less that the unknown password we can bypass the check (since it would return a negative number). This didn’t really lead anywhere...
After some research about strcmp vulnerabilities in php, I came across this document: https://www.owasp.org/images/6/6b/PHPMagicTricks-TypeJuggling.pdf
Searching ‘strcmp’, I found something interesting on page 24. Basically, if we can give something of the wrong type as our input, then we can confuse the strcmp function, and it’ll return NULL. Since !NULL is true in PHP, we can use this to bypass the strcmp check.
Making the query param an array, i.e. passwd[]=“”
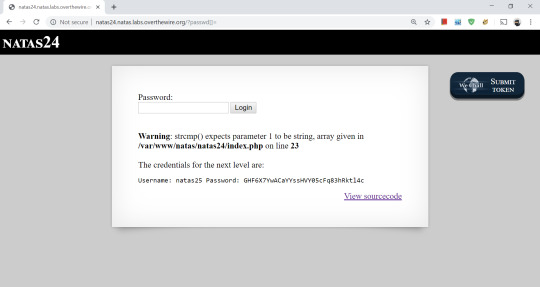
The strcmp function returns NULL, !NULL is true, and we get the flag.

0 notes
Text
Natas: Level 23
In this level we need to provide passwd with substring ‘iloveyou’ but its value must be > 10
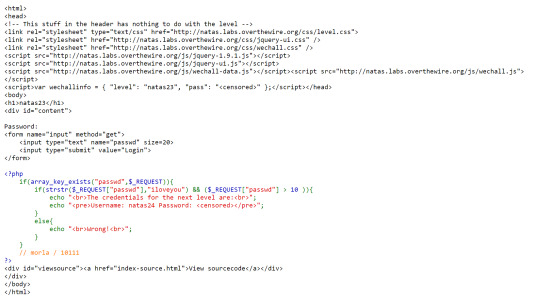
After googling about how php compare strings to integers I managed to find this documentation page: https://www.php.net/manual/en/language.types.string.php#language.types.string.conversion
Reading the documentation we now understand that if we start the string with an number > 10 then the string itself should be evaluated to be equal to that number. In our case, we try ‘11iloveyou’

The password is evaluated to be equal to 11, and so it passes the check and we get the flag.
0 notes
Text
Natas: Level 22
For level 22, we need query parameter ‘revelio’ and $_SESSION["admin"] == 1 to get the flag, otherwise we will be directed back to the homepage. However, there are no functions in the provided PHP code that can modify $_SESSION["admin"]

I thought about the possibility of brute forcing the session id, but the length is 26 and there are 36 possibilities for each character (26 letters + 10 numbers) and 26^36 is massive...
But then I realised that we only really need to get past the check for session id. Maybe there is a way to stop the page from redirecting? After a bit of research, I found my answer.
We know that even though the 302 redirect header is present, the page will still respond with all the information if we do not follow the redirect. This is not possible to do in a browser (as far as I’m aware), but it’s quite simple in python by turning redirects to false.

Writing a simple script to request the page with no redirects, we get the flag.
0 notes
Text
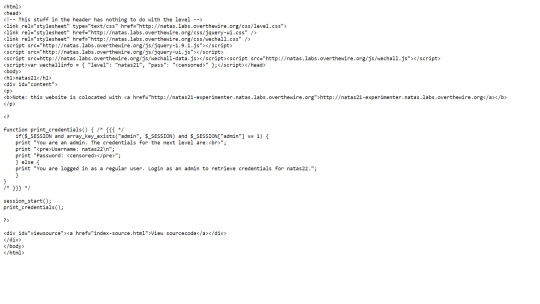
Natas: Level 21
For this level, we are told that the website is colocated at http://natas21-experimenter.natas.labs.overthewire.org
So I navigated to this site and logged in with same credentials.
Checking the sourcecode for both sites, we can see that the orginal natas site has the print credentials function
Whereas the colocated site lets you change the color of a text banner. However, there is an obvious flaw in the code.
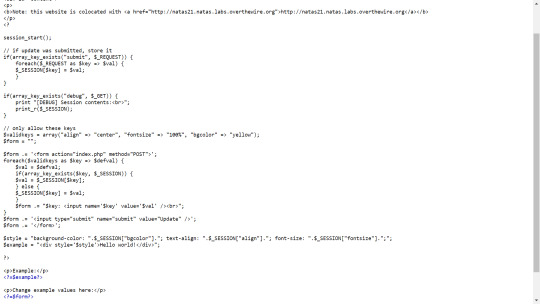
The user can clearly just set ‘submit’ as one of the query parameters and then any other paramter will be set as a session variable.
Using this flaw, we can set the admin flag to 1.

Since the websites are colocated, it is safe to assume that they share the same sessions. With this in mind, we copy the session cookie from colocated site to original site.
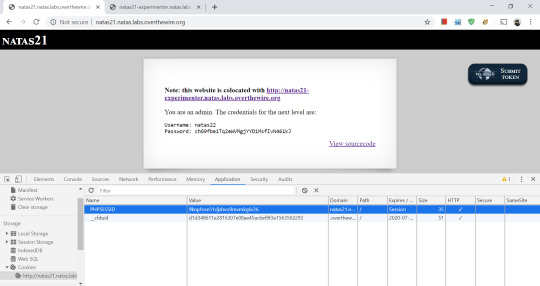
And the password appears, as the session cookie that we have copied over has $_SESSION[’admin’] set to 1.
0 notes
Text
Natas: Level 20
In this level we are given a session id and told to enter a name so that we can change it.
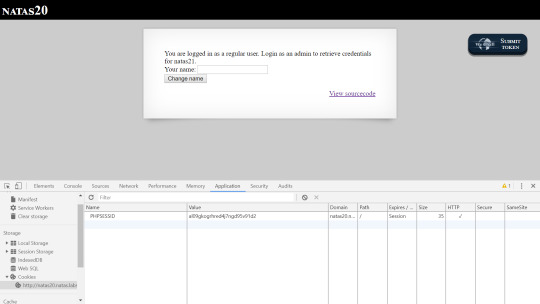
On the surface, providing a new name doesn’t really seem to do anything. Taking a look at the code helps us to understand what’s going on.



As we can see, we need the print_credentials function to be called with $_SESSION["admin"] == 1 to complete the level.
Clearly the place to set $_SESSION["admin"] is in the myread function where $_SESSION[$parts[0]] = $parts[1];
Setting the debug flag, we can try get a better idea of what’s happening.
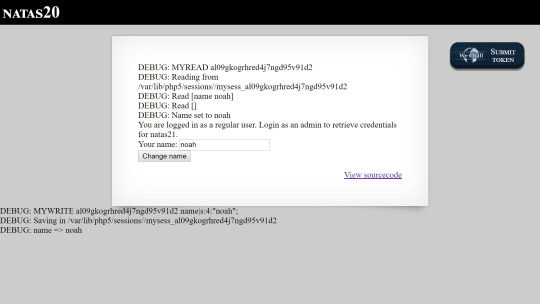
We can see that mywrite is saving all the session variables to a file, with each key value pair seperated by a newline.
myread on the other hand, is taking each of the key value pairs from the session file by splitting on a new line, and then setting $_SESSION[$key] = $value by splitting again on a space.
How can we exploit this so that we can choose our own values?
Well since we are splitting on a new line, what if our user input has a new line in it? Then surely we can set whatever session variables to whatever we want. But then how do we put a new line into our user input? Luckily I accidentally stumbled upon that answer while trying to complete a previous question.
A new line in hex is %0a
Using this knowlege, we make our name=%0aadmin 1
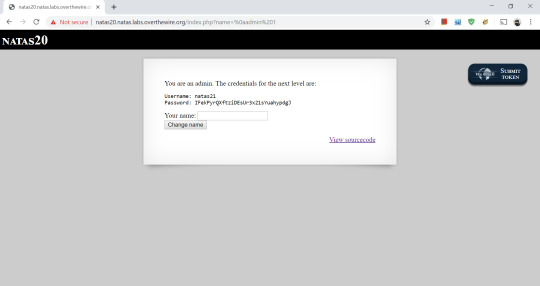
$_SESSION[’admin’] is then set to 1, and we get the flag.
0 notes
Text
Natas: Level 19
Level 19 is pretty much the same as last level but with non sequential id’s. But just because they are non-sequential doesn’t mean that they are random.
After playing around to see what kind of id’s are generated I noticed a familiar pattern. I’ve seperated the id strings below with spaces so that the pattern is more obvious.
3 5 3 9 3 1 2d61646d696e 3 3 3 0 3 5 2d61646d696e 3 2 3 8 3 6 2d61646d696e 3 1 3 4 2d61646d696e 3 6 3 1 3 2 2d61646d696e
As we can see, there is a pattern: only 2nd, 4th and 6th columns are changed. All that’s left to do is modify the script from the previous question to check all the combinations.
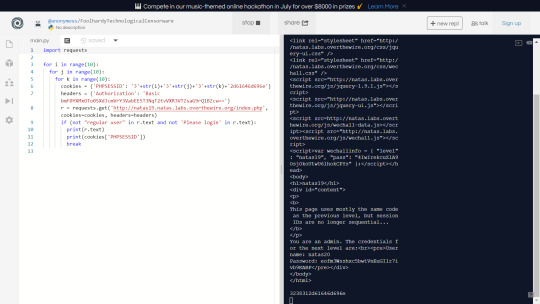
Eventually, we get the admin session and the flag.
0 notes
Text
Natas: Level 18
In this level we are introduced to session cookies.
At first we are presented with a login screen, where we can enter a username and password.

After logging in using any random username and password, we are told that we need to login as an admin to get the password for the next level. We can also see that we’ve been given a PHPSESSID cookie.

Scanning through code we see that we need the print_credentials() to be executed with $_SESSION["admin"] == 1 so that we can obtain the password.
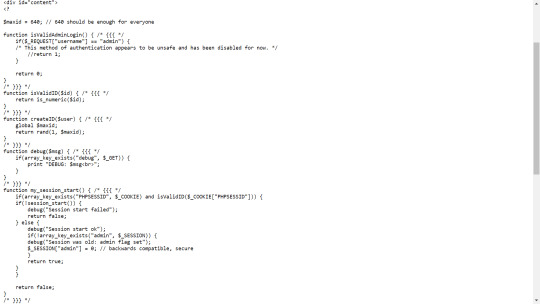
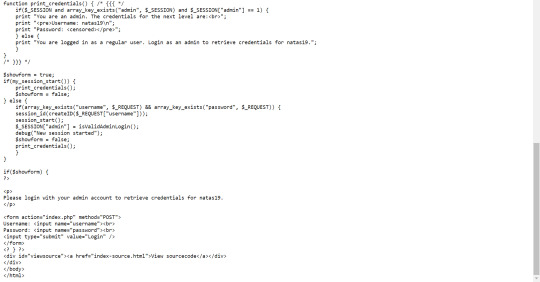
We can also see that $_SESSION["admin"] is set by isValidAdminLogin() which is always 0. But maybe we can set $_SESSION["admin"] from within the browser? Unfortunuately for us, this is not possible.
However, if the session id is in the range of 1 to 640, maybe one of them will be admin if i brute force? Lets write a python script to check it out.
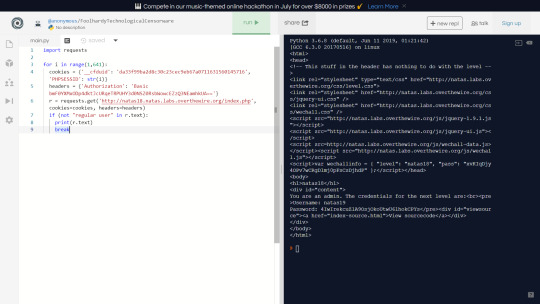
And sure enough, we stumble upon an admin session and get the flag.
0 notes
Text
Natas: Level 17
Natas 17 is the same as level 15 but provides no feedback to the user input. The ‘echo’ commands are all commented out, so we don’t know if our input is correct.

I really wasn’t sure how to tackle this level due to the lack of feedback. I attempted many ways to try get things to print on page, but nothing I tried yielded any results.
It’s obvious that there is some other kind of differentiator that will let us know if the entered user exists. Furthermore, it is clear that some type of SQL injection is required to solve the level.
This is where the MySQL SLEEP command comes in handy. From previous programming courses, we know that if we are evaluating and if statement in the form ‘a AND b’, then both a and b must be true. Since this is the case, if a is not true, then b will not be evaluated as it is already clear that the statement ‘a AND b’ is false.
The same principle applies in SQL. If we structure our command like so
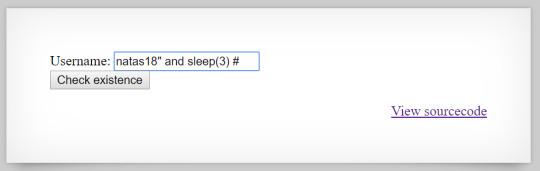
Since natas18 is a proper user, then the sleep command will be executed and the server response will be delayed. We can use this logic to alter previous python script so that it will build the password based on response times.
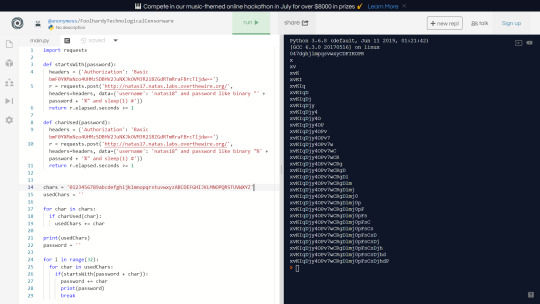
I’ve never really thought of using time as a way of differentiating between responses before. It kinda makes me wonder what the use of the SLEEP command is in the first place.
0 notes
Text
Natas: Level 16
This level is similar to levels 9 and 10, but with even more characters filtered out.
I tried heaps of different things to try get around the filtered characters including:
Url encoding special characters
Double url encoding special characters
Using %0a for newline to see if i could get out of the quotes somehow
Using a null byte (%00) to see if i could end the command
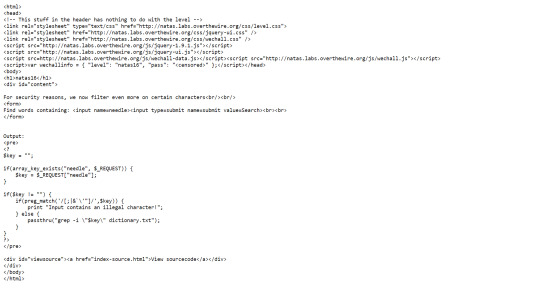
None of these methods really got me anywhere. But looking back at the code, it’s clear that some of the special characters used in regex are not filtered, such as ‘$’, ‘^’, ‘(’ and ‘)’. This is great for us as we can use $() to execute a command in quotes.
But how does that help? We are in a grep command.
Well, we know grep “” gets everything, so we can try run another grep on the password file within $(). If the grep succeeds, none of the words will show on the page (because the password is a random string on letters and numbers) and if the grep fails, then an empty string will be returned and all the words will show.
So we can use the same approach as the previous level to slowly generate the password.
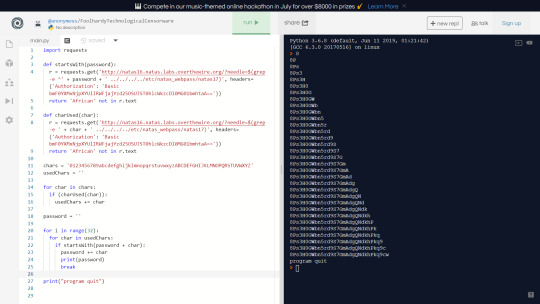
It was really interesting how this level required almost the same solution as the previous level, but it was framed as a completely different question.
0 notes