Don't wanna be here? Send us removal request.
Text
LEVEL 5 : -file

Introduction:
Welcome to my series of wargames challenges, I am basically going through the Bandit challenge on OverTheWire and posting all the levels here. The goal on each level is usually to get the password for the next level.
Astonishment! 5 levels was what it took for OverTheWire to Stump me. A computer besting me? This just doesn’t sit well, how did a bunch of bipolar silicon chips get the better of a seasoned university student. The oxymorons dont stop and this challenge has proved that neither do morons.
Problem:
This challenge right here made no sense to me. I had no clue whether human-readable meant what it sounds like or whether there was a technical file type for it.
My approach:
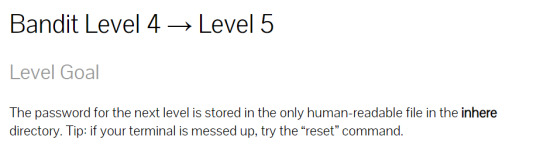
The best thing I did, I think, was to just dive into bandit4 to figure out the situation. I encountered some dubious filenames...
So, I tried opening them anyways with cat but it didn’t work.
After a bit of browsing, I figured out to use the ‘file’ command to figure out whether these files are indeed readable (i.e. text based files)
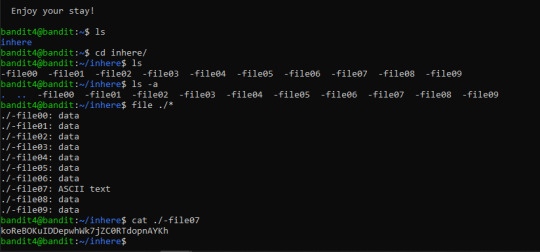
Why did this work? What does the file command even do? *Refer to the next section*
Post Lab:
The main thing that I needed to know was, what is this ‘file’command. I mean, it clearly shows you the type of file that a given file is, but is that really what it does?
So I went to the counsel of ‘man pages’. File is a command that identifies the type of all files provided as an input to the command. Any type with the word text in it is a human readable file. The ‘data’ files are ones that were not recognisable by the function.
Also quick note:
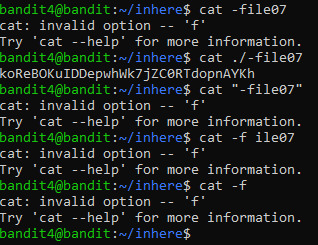
The presence of the ‘-’ before the filename complicates how you can provide it as an input to the ‘cat’ command. Here are the examples that did or didn’t work. *Refer to level 2 and 3 for explanations*
0 notes
Text
LEVEL 4 : Hidden

Introduction:
Welcome to my series of wargames challenges, I am basically going through the Bandit challenge on OverTheWire and posting all the levels here. The goal on each level is usually to get the password for the next level.
While these levels are relatively easy to just storm through, I really want to set a standard of blogging every single level. While this is tedious for these earlier levels where there’s very minimal efforts in solving the challenge, I believe it is crucial in setting a cohesive narrative to this endeavour. After, the theme of my blog is a ‘Journey’ and there’s no room or time for shortcuts.
Problem:
My Approach:
This solution I basically knew before I even set foot on the battleground. Since, there’s a known ‘hidden’ file in the directory I knew I just had to tweak the parameters for the ‘ls’ command to view all files.

Quite straight forward really...
Post Lab:
I researched how I can create hidden files myself, I had taken a wild guess in thinking that it’s probably just as easy as adding a dot before the name and turns out I was R I G H T! Woop! I messed around in my home directories and created some hidden files with some very surprising messages for the future me.
0 notes
Text
LEVEL 3: Spaces

Introduction:
Welcome to my series of wargames challenges, I am basically going through the Bandit challenge on OverTheWire and posting all the levels here. The goal on each level is usually to get the password for the next level.
We continue on this journey and as we venture deeper and deeper into this abyss the hurdles keep growing higher and yet the discoveries hiding behind get more and more profound.
Problem:
On our third level, the challenge seems quite fairly simple. the only hurdle is in opening a file or viewing it rather when the name has spaces inside.
Child’s play...
My approach:
After navigating into the right directory inside the account of bandit2, I simply opened the readme file through:
cat “spaces in my name”
Post Lab:
Reflecting on the solution there are other ways of doing this using a backslash instead of encapsulating the name in quotations.
N E X T !
0 notes
Photo
LEVEL 2 : STDIN FILENAME
This one was a doozy! I severely underestimate how frustrated this level could make me. I knew how to solve it but in a way I had no idea.
PROBLEM:
Similar to level 1, we have ssh in as bandit1 and then read the file that contains the password to logging in as bandit2 for the next level. Except the file that contains the password is named... ‘-’
MY APPROACH:
ssh into bandit1 with the password we captured from bandit0′s folder.
look at the files in my current landing directory, and find this file named ‘-’
ls -l
read the file.....
cat -
This did not work. I had to google why... the solution that popped up was.
cat ./-
that did the trick, why? keep reading.
Post Lab:
I found out that, ‘-’ is the default filename for ‘stdin’. When ‘cat’ sees ‘-’ as an input it treats it as stdin, we can walk around this by doing what we did in our solution.
After a little more probing, also found in my research that stdin, stdout and stderr are called ‘streams’ which basically connect two points in the Linux system and dove deeper into redirecting these streams and their structure and the thought process behind designing them the way they were designed. The more you know.
1 note
·
View note
Photo

Level 1 : Terminal Basics
Problem:
This level wasn’t particularly different to level 0. After successfully logging into the ssh port of the server, we then have to open the file that contains the password of the next level’s ssh login. We are even told it is in the directory that we land on when we successfully log in.
My Approach:
First, I had to ssh into the game server through bandit0′s account,
‘ssh [email protected] -p 2220′ password: ‘bandit0′
then, I checked the files in the directory that i landed in,
‘ls’
and opened the only file in the directory,
‘cat readme’
viola, there’s my password to ssh in as the user, bandit1
Post lab:
Not much to report for this one.
3 notes
·
View notes
Photo

Level 0 : ssh
It really is quite embarrassing to say that after 3 full years as a computer Engineering system and after 3 years of accessing university labs through ssh,
today was the first time I read the manual for the command ssh.
Problem: For Level 0 in the Bandit Wargames on OverTheWire challenges, I had to log in to the host ‘ bandit.labs.overthewire.org ‘ on port 2200 and login with the right credentials.
My Approach: The First thing I did was to open up the manual page for ssh through the command ‘man ssh’. Read up. Here’s the solution I built. ssh bandit.labs.overthewire.org -p 2220 -l bandit0
The shell then prompted me to enter the password to authenticate user ‘bandit0′ and I did and viola! Post challenge: Upon further research and trials, I also found out that,
- you can specify a username without the ‘-l’ flag by modifying the hostname to ‘bandit0@ bandit.labs.overthewire.org’ - When the ‘-p’ flag is removed then the default port number that you ssh to is port 22. Which is also the default port for ssh. - I confirmed this by looking up the configuration for the ssh request with the flag ‘-G’
Well, that’s all for the easiest challenge of em all. See you in my next post after level 1.
3 notes
·
View notes
Photo
OVER THE WIRE : BANDIT
I have started a new blog on my journey through the Hacking CTF challenges on the popular platform OverTheWire. They offer a great range of difficulties for their challenges and I will be starting at ground 0.
Over the next couple of weeks,
- I will throw my life at these challenges and solve them one by one. - For every, level I cross, I’ll update you here on what I’ve gotten up to - Hack Shit
Chuck my blog a quick follow and shoot me a message if you’d like to join me.
1 note
·
View note
Photo

Something Awesome: RFID
Here we have reached the pseudo official end to this project for my university course. I just did my presentation in the lab the other day and boy oh boy... people liked it!!! Woo hoo, I did something interesting!
Don’t be so disappointed though, this by no means indicates the end of my pursuit to crack these infamous MIFARE Cards. Reflection: Looking over my project, here are some points I think are worth noting... 1. I tend to jump into commitments too quickly before doing my research. (Bought 45 different RFID cards) 2. Starting the project was the hardest for me physically. But once I found my stride there was no stopping me. 3. I get demotivated easily with failure. Need to work on my resilience and persistence. 4. I also tend to stop progressing when I realise my skills are lacking. Instead of diverting the focus in the project and working on something else in the project, I give up completely and do something else. These are definitely something I can work on. And definitely, get better with. Marks: HD would mean I’d finished my goal. Which I didn’t. But I do know how I could do it. The distinction would mean I’ve covered most of my goals. Judging from my overall progress. I’d say I got myself a solid Distinction!!
1 note
·
View note
Photo

Something Awesome: RFID ARDUINO && MFRC522:
I’ve chosen to work with a micro-controller and an RFID read/write module. Brief Overviews: Arduino is a handy little microcontroller used for a LOT of handy little projects. It’s great to work with sensors and IO modules as such. It really is a wonderfully powerful tool to have. I write my code utilising the several libraries and modules on Github on a Proprietary Arduino IDE. This code is then uploaded onto the controller. All the code that the libraries were built on and I have extended is in C++... I’ve never coded in C++... MFRC522 is an RFID read/write module for Arduino, which can read or write to RFID cards. The cards supported really depend mainly on the code that is uploaded on to it from my understanding. It works mainly on SPI technology and is a handy module for my handy little tool.
1 note
·
View note
Photo

Spook! This Case Study was basically the same as the bloody HOUDINI TRIALS in terms of security concepts! [edit: Insert Security principles covered and overlapping in both]
Here’s a link to HOUDINI!!! [edit: INsert link]
0 notes
Photo

Case Study: Challenge
Context: You’re being recruited by Google to prepare the security protocols for their top-secret base for their top-secret project. What the measures you intend to take?
My approach: 1. Figure out Assets to protect 2. Configure some security features to best protect these assets Assets: 1.Project Sensitive Data 2. Computers 3. Physical Files 4. Project member identities 5. Discussion rooms 6. Computer Rooms Counter Measures: 1. Multilayered Defence system: No single point of failures 2. Spread Sensitive files into multiple rooms 3. Secure rooms with physical combination locks and RFID protection 4. Each Main entry point is secured by guards checking for ID 5. Meeting room entry is only allowed for groups 6. Checking each member for bugs when they enter 7. Signal/Call blockers in all rooms 8. Physical locks on computer hardware 9. Cameras Everywhere 10. SECURE THE TOILETS!!
0 notes
Photo

Security Everywhere: Houses?
How many levels of Security do average houses have?
I was walking around in the mean streets of Homebush (inner west Sydney)... And I walked by a house that had its windows and doors secured by bars and really looked nothing short of a suburban jail.
That’s when I wondered... Can I quantify the number of layers of security for a house?
Here’s my attempt:
1. Compound Fences 2. Enclosing Walls 3. Bars 4. Home Security System 5. Dog 6. Vigilant Neighbours 7. Fake Mannequins standing around the house... 8. Security & Dog signs 9. Location of the house
How did that kid from Home Alone survive by himself while he faced off those two burglars?
0 notes
Photo

Jake Paul: Infiltrating the White House
You heard me...
“YouTuber Sensation Jake Paul done goofed up real good this time...”
In one of his most recent videos, Jake Paul posted a video of himself hiding in the Presidential Whitehouse in Washington. The use of the word “Infiltrated” might have been a stretch but hey, this is how you grab attention on the internet. It’s called Click baiting...
Here’s some context,
Jake Paul for some reason was invited to the Whitehouse. He was authenticated and authorised to go inside as a friendly package.
Jake Paul for some reason decided to slip away from the main event and went into the bathroom. Since he’s already inside there aren’t many people checking for unusual activity in that premise. He’s decided to turn menacing after bypassing the big security defences.
Jake Paul for some reason decides to stay in the bathroom overnight. No one checks for him in there, since it’s only a bathroom and no one even notices him missing. Menacing package decides to take over unimportant asset. Menacing package doesn’t throw off alarms.
He then walked out at 3AM. No harm done. No items stolen. Miraculous that he’s still alive.
What a stunt. Taught me a lot about the Whitehouse’s security.
It’s a one time door... Once you’re in... You’re in...
I’m only kidding now XD
1 note
·
View note
Link
Working with Sarah! For my Something Awesome Project, I had the pleasure of working with my dear friend Sarah Alameddine. Since we have now finished our project, I wanted to reflect a little on what we did right, what we didn’t, what I learned and so on
Reflection:
Sarah: Sarah has been an amazing partner and a team member. We have dived deep into the world of RFID together and really it was a wonderful journey. Throughout the Project, Sarah was well organised and always on the hunt for the next chapter in our research. There were moments where we knew we should be working but we had no direction. \
Sarah was on top of all the equipment we needed for the project... we ended up using 2 components out of the 45 she bought! I guess we were a little too excited and hasty. We both seemed to just jump at any lead we found and went all in on it. What I learned: Whilst working With Sarah I noticed how the difference in our individual drives towards a single project. I kept noticing myself lacking the drive to keep persistently tackling the topic and really relied on Sarah for the energy. We’d both go through different topics and collect these ‘findings’ then present them to each other. I also realised, Sarah was so much better than me at finding online resources while I kept trying to ‘roll on my own’. What I want to retain: 1. I want to focus on improving my drive by diving into more projects 2. I want to consciously tell myself to reach out to the world wide web for some world wide web standard solutions 3. I want to do more projects with Sarah We might even be attending Sydney Bsides together!
0 notes
Text
Bits of Security
Here’s a blog I haven’t written... Around a few weeks ago whilst I was out there working for the midterm exam for comp6441...
I got myself familiar with the concept of bits of Security...
Here’s how I would explain it to someone who has no initial idea of what it means,
Let’s say there is some sort of a protocol which identifies unique individuals. Each individual has their own unique ID which is one out of a million possible IDs. If we wanted to guess his unique ID, in the worst-case scenario, we’d have to guess a million IDs to get his one. Now we’d have to ‘Brute force’ through the million ID values. To represent a million unique values, we would need a certain number of bits. The number of bits would be called Bits of Security. example: To represent 10 numerical values you’d need 4 bits (0000 - 1010)
If a protocol can accommodate for a million possible IDs then it would have 20 bits of security.
If a protocol has 48 bits of security, it could accommodate for (2^48) possible values that would need to be guessed to be brute-forced.
0 notes
Photo

Door Locks: Who are we locking out?
When was the last time you got locked out of your house?
In the week with the case study on door locks. We had to develop a more practical and effective floor plan to have door locks on cockpits to ensure the safety of the pilots and also ensure functionality with redundancies Our Priorities: 1. Ensure the safety of Pilots & Plane controls 2. Make the lock overrideable for emergencies 3. Place the door while accommodating for Pilot’s needs Solutions: 1. Opening the Lock requires permission from both pilots 2. Overriding the Lock from the OUTSIDE requires permission from Three staff members 3. A toilet must be placed inside the cockpit along with basic amenities to reduce the need to go out of the cockpit for pilots 4. Availability of a sort of communication with the Home base who can remotely open the door in emergencies We believe the above solutions could easily tackle the problems that have occurred so far however, I do not know how extensively fail-proof they would be in a different future scenario.
0 notes
Photo

Houdini: The Secure Artist
Here’s a classic good old battle between your everyday Medium and the classy magician.
Without extensively going through the case study, I want to explore the solutions my group came up with to authenticate Houdini in his afterlife.
Context: If Houdini were to die, he needs to have prepared a protocol for establishing communication with his wife through a medium. This protocol must ensure that it is Houdini from the afterlife speaking and not the medium. This protocol must also ensure that it can be repeatable with different mediums.
The goal is to form a test that will verify the abilities of every medium on the planet. The test must be, 1. Repeatable 2. Valid
Protocol: 1. A key must be generated from variables from the medium and the situation which can be easily accepted but hard to reverse engineer. (repeatability) ex: Houdini’s first three sentences will always start with the first letter of the medium’s name then medium’s dress’ colour and then a day (in order). 2. A personal Question with Houdini’s specific answer that must always be given 3. A lock that only Houdini can open (Authentication but not repeatable)
Any medium who cannot satisfy any one of these conditions is declared a fake!
0 notes