#cybersec
Text
my cybersecurity courses in uni are like 15 years out of date and it drives me insane. and i dont mean in the "haha im so smart, i already know what a buffer overflow is thanks 2 tomert scotwald", i mean in the "they made this lab for android so long ago that when i follow the directions to the letter the app crashes since package naming schemes have changed and this attribute doesn't exist anymore" kinda way and it makes me want to beat powerful people with very heavy hammers
#like i get cybersec teaching lagging behind#but can you really not update your coursework to WORK#im not here to learn android studio#im here to learn about vulnerabilities#eugh#196#programming#cybersecurity#cybersec#computers
74 notes
·
View notes
Text

#cyberspace#cybergoth#cybersec#cyberpunk#computers#computer core#webcore#old web#red and black#goth#emo#aesthetic#90s#vintage#y2k#bpd#kawaii#420life#scenemo#cool#japanese#katakana#hiragana#kanji#japan#japanese graphic design
276 notes
·
View notes
Text
The Hacker's Guidebook:
Aspiring hackers! I’ve created a guide covering core cybersecurity concepts new hackers should master before tools. I break down networking, OS internals, & hacking tactics. Recognize hacking as lifelong journey—arm yourself with the basics!
Core Concepts for Budding Cybersecurity Enthusiasts
The Building Blocks of Ethical Hacking
So you want to become an ethical hacker and enter the exciting world of cybersecurity. That’s awesome! However, before you dive headfirst into firing up Kali Linux and hacking everything in sight, it’s vital to build up your foundational knowledge across several InfoSec domains. Mastering the fundamentals…

View On WordPress
#attacking tools#basics of hacking#cross site scripting#Cyber Threat Defense#cybersec#cybersecurity learning#cybersecurity professional#Ethical Hacking#fundamentals#hacking basics#hacking for beginners#hacking guide#hacking networks#hacking web#how to hack#infosec#learn hacking#learn to hack#linux#malware basics#malware for hacking#metasploit#netsec#network hacking#nmap#operating systems#Pentesting#phishing#phishing attacks#Red Team
14 notes
·
View notes
Text

hello, welcome to my house!
click the readmore for more!
my art | neocities | archive
i'm a cat on the internet! i draw, but by far and large this is a personal account for archiving posts i like, yapping, and playing with my friends (hi friends!). my main interests include brutalist architecture, computer security, healthcare/public health, and ethics. i can't promise i'm good at any of it, but i always enjoy myself ⍝(•⍵•)⍝
Proship/Terf DNI. I post a lot of suggestive and blatantly nsfw content, so I would prefer for my audience to be 18+, thank you! I do my best to tag with appropriate content warnings such as #suggestive, and #cw gore, #cw blood, etc, but please do feel free to ask me to tag anything. The ask box and DMs are always open.
#arch#ask#cat post#crab post#cybersec#furry#goat post#good art#graffiti#hatori tag#health#hilarious#insp#lit tag#kino tag#mecore#milk post#milkart2206#moodboard#mp100#needle felt#news#rb games#polls#save#sona art#suzuki tag#tech#vidya tag#yap
43 notes
·
View notes
Text
log #001 | the key is a strong foundation
as planned, I started the HTB initial machines, until now I have only completed the meow machine, and it was way more easy than I expected, there was a walkthrough document and I peek it whenever I got stuck
for the second machine, the fawn, I was going to challenge myself to try to do it without the looking at the walktrough doc, but then the htb labs site wasnt opening on my vm (even tough it was fine on my own laptop)
so, instead of waisting time on this, I started the linux fundamentals on htb academy and spend a good four hours on it
even tough I already had experience with linux in college and on my personal machine, it was a bit challenging, I guess it was because the amount of information that I was getting at once, but even so it was a good experience, I particularly liked the small challenges at the end of each topic that forced me to go back and read everything again and thus assimilate the content better
it was a good day and a good start with my studies, and I'm gonna take it with caution to not get to much caught up and end up burnout
thanks for reading and please excuse any spelling mistake, I'm improving my english a little bit everyday, bye!
3 notes
·
View notes
Text
happy information security day!!!

2 notes
·
View notes
Text
cybersecurity fandom is dying reblog if you love cybersex
10 notes
·
View notes
Text
Love that the ipleak.net website used to take seconds, but after being under maintenance for a week it now runs 300 tests that take 5+ minutes. That's growth sweetie
11 notes
·
View notes
Text
Building a vulnerability scanner using python
Protect your systems and secure your sensitive information with vulnerability scanning! This process identifies and analyzes security weaknesses in your network or computer systems. Stay ahead of potential threats and maintain peace of mind with regular vulnerability scans.
3 notes
·
View notes
Text
#ThreatIntelligence#ThreatIntelligenceAnalyst#CertifiedThreatIntelligenceAnalyst#CyberThreatIntelligence#Cybersecurity#Cyberattack#Cybersec#Cyberthreat#Cyberthreats#Cybercrime#edtech#technology#teaching
2 notes
·
View notes
Text
Is AI eliminating jobs or work?

Evolution in human economic history experienced, technology has removed employment while increasing work and being a net job creator; the excess of job creation over destruction has been good. The same is the case with Artificial Intelligence in India. Artificial Intelligence or AI is a field of Data Science that trains machines to learn from inputs, adjust to inputted fields and criteria, and perform tasks of computational logic that match certain human cognitive levels. AI as a function has pervaded almost all industries and functions in India – from E-Commerce to BFSI and from Manufacturing to Agriculture – Data Science and Deep Learning are increasingly utilized to solve complex business challenges. AI is increasingly utilized across several B2B, B2C, and, even, C2C (Consumer-to-Consumer) channels. More than a replacement, it is being used as a complement to human skills to increase productivity and output.
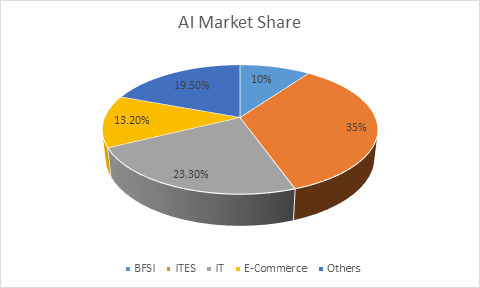
The current AI market share is around $8bn in India and is divided into IT and ITEs, E-Commerce and BFSI as the major users of AI, followed by others such as Healthcare, Agriculture etc. Over 1 lakh people are employed in this sector and this is one sector where employment is growing constantly. Employment created by AI is projected to reach 2 crore by 2025. No need to be over optimistic, but no need to be pessimistic either. Overall growth of AI market in India is predicted to be more than 10% per annum. And routine and codifiable jobs are expected to be eliminated by AI while jobs requiring IQ and EQ are expected to grow. However, considerable polarization in the employment market may arise at the higher and lower ends, necessitating special government initiatives to generate jobs in order to maintain social stability.
Please share your opinion with us.
#iccblogs#softwaredevelopment#datavisualization#automation#machinelearningalgorithms#coding#artificialintelligenceai#bigdata#cybersec#codinglife#malwareanalysis#security#cyberattack
2 notes
·
View notes
Text

#DatabaseSecurity#Cybersecurity#DataProtection#InformationSecurity#DataPrivacy#CyberDefense#CyberThreats#DataSecurity#SecuritySolutions#CyberSecurityMarket#DataEncryption#DataSecurityTrends#NetworkSecurity#ITSecurity#CyberSec#InfoSec#DataBreach#CyberAttacks#DataSecuritySolutions#DigitalSecurity
0 notes
Text

#goth#aesthetic#emo#90s#vintage#y2k#kawaii#scary#hacker#hacking#cybersec#cyber security#htb#thm#gear#keyboard#light up#led
3 notes
·
View notes
Text
They added that “80 percent of Faceless bots are located in the United States, implying that accounts and organizations within the US are primary targets. We suspect the bulk of the criminal activity is likely password spraying and/or data exfiltration, especially toward the financial sector.”
The researchers went on to say that more traditional ways to anonymize illicit online behavior may have fallen out of favor with some criminals. VPNs, for instance, may log user activity despite some service providers' claims to the contrary. The researchers say that the potential for tampering with the Tor anonymizing browser may also have scared away some users.
The second post came from Satori Intelligence, the research arm of security firm HUMAN. It reported finding 28 apps available in Google Play that, unbeknownst to users, enrolled their devices into a residential proxy network of 190,000 nodes at its peak for anonymizing and obfuscating the Internet traffic of others.
0 notes
Text









"Boost your CompTIA Security+ exam readiness: practice exams, review objectives, hands-on labs, and stay updated with latest cybersecurity trends.
For more information visit www.certera.co
#CompTIASecurity#SecurityPlus#Cybersecurity#ITCertification#ExamPrep#StudyTips#InfoSec#NetworkSecurity#CyberSec#TechSkills#CertificationPrep#ITCareer#StudyGuide#SecPlus#ITSecurity#CompTIAExam#CertificationExam#SecurityCertification#TestPrep#CyberAware#InfoSecTraining#SecurityCareer#SecurityProfessional#StudySmart#CompTIATraining#CyberDefense#ExamTips#CyberSecurityTraining
0 notes
Text
january | htb challenge
to warm up and start the cybersec studies, I choose the hackthebox as the place for hands-on practice since it has a lot of free stuff with good quality
my plan is finish it all before february and balance with the cybersec course that its gonna be launched on 22 this month, lets see how it goes
the plan is very simple: im just gonna do all the starting point module free machines and the recommended courses on htb academy
for now, i will log my journey here on tumblr while i find a way of using the github commit grad as a form of accountability (i was thinking of making notes in markdown, but im still not sure)
thats all for now, have a good day!
4 notes
·
View notes