SHIELD is the world’s leading risk intelligence company. We help global organizations stop fraud, build trust, and drive growth. Visit www.shield.com
Don't wanna be here? Send us removal request.
Text
What Are the Major Challenges while Implementing Effective Fraud Detection and Prevention Solutions?
Imagine waking up to find that your online business, built with years of effort and investments has been compromised by fraud. Sales are lost, customer data is exposed, and your reputation is on the line. In today’s digital age, fraud detection and prevention solutions are more crucial than ever. Yet, businesses continue to struggle against increasingly sophisticated tactics that traditional security measures often fail to counter. and even the most powerful systems can still face challenges in keeping up.
This blog will explore the major obstacles businesses encounter when implementing effective fraud detection and prevention solutions, and how emerging technologies and strategies are stepping in to address these issues.
Here’s a quick overview of the key topics we’ll be covering:
Index
Major Challenges in Fraud Detection and Prevention Solutions
High Rate of False Positives
Evolving Fraud Patterns
Lack of Model Transparency and Explainability
Time Delays in Detecting Fraud
Balancing Fraud Prevention with Customer Experience
Integration Challenges and Time Taken to Implement
Can Businesses Overcome These Challenges?
The Solution: Device Fingerprinting-Based Fraud Detection and Prevention
How Device Fingerprinting Overcomes All the Challenges
Conclusion
Major Challenges in Fraud Detection and Prevention Solutions
a. High False Positive Rates
Fraudsters hide in plain sight, mimicking the patterns of normal users, making it challenging for fraud detection solutions to identify them accurately. While only a small number of users have malicious intentions, their ability to blend in raises the risk of false positives. A high false positive rate leads to unnecessary disruptions for genuine users.
For example, a frequent online shopper Jon makes a large purchase while traveling abroad. The fraud detection system flags the transaction as suspicious due to the unfamiliar location and payment method. His account is frozen, and the order is delayed, leaving him frustrated and questioning the store’s reliability. This poor experience may even push Jon to shop at a competitor.
False positives negatively impact the experience of genuine customers, damaging their trust in the brand. It drives up operational costs by causing temporary service blockages, requiring additional resources to address affected users. Businesses must prioritize finding the right balance in risk thresholds, as an abundance of false positives can harm both customer experience and overall business performance.
Speaking of finding the right balance, it’s crucial to work with experts who can tailor a fraud prevention strategy that suits your unique needs. Schedule a discussion with fraud prevention specialists today and take the first step toward securing your business without compromising customer experience.
b. Evolving Fraud Patterns
Fraudsters are quick when it comes to adapting their tactics to outsmart detection systems and finding new ways to exploit online platforms. You think you're prepared, only to be blindsided by a new type of fraud you never anticipated, leaving your business vulnerable and struggling to respond.
Example - In 2017, the credit reporting agency Equifax suffered a massive data breach that exposed the sensitive information of approximately 147 million people. In a matter of hours after the breach was publicly disclosed, Equifax's stock price plummeted by nearly 35%. Customers and partners quickly distanced themselves from the company, and the breach cost Equifax an estimated $1.4 billion in damages, legal fees, and remediation efforts. Had the company been better prepared with more proactive fraud detection and prevention solutions, it might have mitigated the breach's severity and the damage to its reputation.
Fraudsters move fast—your response must be faster and smarter.
Businesses need to implement deep learning and AI-powered fraud detection systems that can continuously adapt to emerging trends and swiftly identify fraud at its root before it causes damage.
c. Lack of Model Transparency and Explainability
Many fraud detection and prevention solutions fail to provide clear explanations for why specific users are marked as fraudsters. These black box models only provide a score (e.g., likelihood of fraud) without explaining the reasoning behind it.
For example, a fraud detection system that flags transactions from 0 to 10 indicates a level 7 chance of fraud for a specific transaction but doesn’t specify the reasons behind this assessment. The fraud prevention team, unsure of the reason behind the flag, delays the transaction by 3 hours, fearing a potential fraud. This lack of transparency not only frustrates the customer but also risks losing their trust.
It undermines your trust in the system's decisions and makes it difficult to make precise choices when needed. It's advisable to look for solutions like SHIELD that provide comprehensive detail about why a user is labeled as risky.
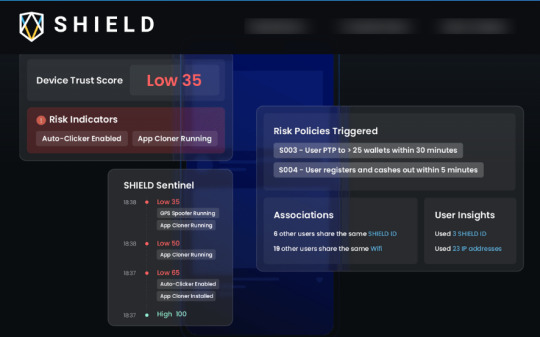
d. Time Delays in Detecting Fraud
Fraud detection systems can take time to identify and flag fraudulent activity, especially when large amounts of data are involved. These systems analyze large data sets to identify suspicious patterns by extracting key information such as transaction value, time, and location. However, the process of identifying and organizing these critical data points can be slow, causing delays in detecting fraud. If the system fails to pinpoint the right details quickly, the entire detection process is compromised.
But in the world of online business, timing is everything. Delays in fraud detection can lead to rapid, irreversible consequences. In 2013, Target suffered a massive data breach when hackers stole credit card information from over 40 million customers. Despite early warning signs, the fraud detection system failed to flag the breach promptly, allowing fraudsters to misuse the stolen data for weeks. The delay in detecting fraud led to an estimated $162 million in damages for the company.
So it becomes a necessity to look for fraud detection technology that identifies fraudsters before they can commit fraud. Device fingerprinting proactively detects fraudulent activity with continuous session monitoring and identifies red flags like GPS spoofing, emulators, app cloning, and more without friction.
e. Balancing Fraud Prevention with Customer Experience
Excessive fraud prevention measures can directly conflict with the user experience. Customers often get frustrated with having to go through multiple security checks, a common issue for businesses using device or user identification to prevent fraud.
To enhance the experience, you need to find a balance between gathering the data required to prevent fraud and keeping the process smooth for customers. A device identification technology that can discreetly collect sufficient data for fraud prevention and identify fraud with absolute certainty without disrupting the customer journey. Look how ride-hailing unicorn InDrive has found this balance using SHIELD and has achieved over 99.77% genuine users on its platform.
f. Integration Challenges and Time Taken to Implement
Many fraud detection solutions take a significant amount of time to adapt to the business model and start functioning efficiently. Sellers around the world have experienced months of wasted effort trying to integrate fraud solutions into their platforms, only to find that they still do not provide accurate results. Additionally, some solutions require extensive Personally Identifiable Information (PII), which raises ethical concerns.
To overcome this challenge, it's essential to look for plug-and-play solutions that can be integrated into your business within minutes and begin identifying fraudsters from day one. There are advanced solutions available that are highly customizable, do not require additional PII data, and deliver results instantly.
These Challenges Are Not Insurmountable
While these challenges when implementing fraud detection and prevention solutions are real, they are not impossible to overcome. There are advanced fraud detection solutions tailored to address these pain points, offering smarter, faster, and more reliable ways to protect your business.
Implementing effective fraud detection and prevention solutions can help you combat fraud without disrupting operations or customer satisfaction.
The Solution: Device Fingerprinting-Based Fraud Detection and Prevention
Device fingerprinting-based fraud detection and prevention works by leveraging unique device attributes to build a unique profile for every user’s device when they access your website or app. The device fingerprinting is created by compiling various software and hardware attributes, such as:
IP addresses
Wi-Fi network
Screen resolution
Battery information
Device model and brand
Operating system
Language setting
Time zone and GPS coordinates
Browser information
Device fingerprinting is effective for fraud detection because it can identify fraudsters in both mobile apps and web environments, whether they are part of large groups or acting alone. For a detailed understanding of device fingerprinting and its effectiveness in detecting fraud, read our in-depth blog on this subject.
Overcoming Fraud Detection and Prevention Challenges with Device Intelligence:
Challenge 1: High Rate of False Positives
Solution: Device fingerprinting relies on a unique combination of the device’s hardware and software attributes, making it highly accurate in identifying legitimate users and fraudsters, hence reducing false positives.
Challenge 2: Evolving Fraud Patterns
Solution: When combined with machine learning, Device fingerprint adapts to evolving fraud patterns and trends by continuously learning from new data, improving its accuracy and ability to detect emerging threats.
Challenge 3: Lack of Model Transparency and Explainability
Solution: Device intelligence provides detailed information on why a device is flagged as fraudulent by pointing out the specific hardware and software attributes that contributed to the decision.
Challenge 4: Time Delays in Detecting Fraud
Solution: Device fingerprint provides real-time identification of fraudulent devices as soon as they interact with a website or app, enabling immediate action without waiting for complex behavioral patterns to emerge.
Challenge 5: Balancing Fraud Prevention with Customer Experience
Solution: Device intelligence works discreetly in the background, building the fingerprint without interrupting or irritating users, which ensures a seamless and frictionless experience while effectively identifying fraudulent activity.
Challenge 6: Integration Challenges and Implementation Time
Solution: Device fingerprint offers seamless, plug-and-play functionality that quickly identifies fraudsters without the need for extensive customization or long implementation times.
Conclusion
While implementing and managing fraud detection solutions, might come with some challenges, advanced modern solutions like device fingerprinting can help eradicate these challenges effectively.
If you're interested in how device fingerprinting can strengthen your fraud prevention strategy, explore our detailed resources or schedule a demo with SHIELD’s fraud prevention experts.
1 note
·
View note
Text
Why Investing in Anti-Fraud Solutions is a Smart Business Decision?
Many online businesses underestimate the impact of fraud, which can quickly become an expensive problem for them. In today’s digital world, the financial impact of fraud has reached staggering new heights, and in some cases, so high that businesses can't cope with it.
Online fraud is not a one-time event; it creates a ripple effect that can significantly impact your digital platform.
When fraud occurs, the initial financial loss is only the beginning. To identify and address the root cause, you'll halt services, resulting in downtime for your app or website. This not only incurs additional costs but also disrupts the user experience, leading to further losses.
Then comes business integrity, as companies would be less likely to continue doing business with companies that have been breached, and consumers often refrain from engaging with such entities.
As digital platform owners, it’s essential to recognize this chain reaction and deploy an effective anti-fraud solution for your business to safeguard your operations.
Anti-fraud solutions stop fraud before it affects the business. These tools help your business build resilience against fraud, identify and eliminate potential weak points, and maintain consumer trust and confidence. Moreover, with the right anti-fraud solutions in place, businesses can take calculated risks more confidently, knowing they are protected no matter what market they expand to or new product they plan to release..
Why is Investing in Anti-Fraud Solutions a Smart Business Decision?
1. Strategic Financial Asset Protection & Long Term Cost Saving
Having an anti-fraud solution protects against financial losses due to fraud. Even in the case of high-level security breaches, while these solutions may not fully prevent fraud, they can take the sting out of it by significantly reducing the financial impact of fraud-related incidents and the associated costs that follow.
To top it all off, the anti-fraud solution is a long-term investment that provides a return on investment through reduced fraud losses and operational efficiencies.
An example of such solutions includes device fingerprinting, which can identify fraudulent devices across apps and web platforms with over 99.9% accuracy.
2. Strengthening Brand Integrity - Enhanced Customer Trust
Fraud damages the brand’s credibility amongst customers as well as the relationship with potential business partners. An anti-fraud solution prevents fraud and helps in protecting the company's public image and customer relationships.
An article by CNBC shared a survey polling that 55% of people in the U.S. say they would be less likely to continue to do business with brands who are victims of a cyberattack.
Anti-fraud solutions can avoid any such unforeseen circumstances by tackling fraud head-on. By protecting against fraud, a business can further build brand credibility by demonstrating commitment to security and give a competitive advantage by positioning the company as a leader in innovation and customer protection. This is especially prevalent in fast-moving and person-to-person industries such as online marketplaces.
3. Enhancing Operational Efficiency with Improved Risk Management
Anti-fraud detection systems ease the burden on the management team by handling damage control concerns. This gives them more time to focus on other important priorities within the business, hence improving operational efficiency.
The anti-fraud solutions use dedicated techniques and advanced tools for identifying and mitigating risks. You can automate the fraud detection processes using AI and machine learning, which enhances risk management and the response time to emerging threats. By doing so, the manual intervention will be reduced, so will the cost associated with it.
With one smart decision, businesses can not only reduce the workload for their management teams but can also save significant costs while benefiting from advanced fraud prevention measures.
Now you know what are the benefits of having an anti-fraud solution for your business. But if you are further interested in knowing which is the best anti-fraud solution, here is your answer - SHIELD.
When it comes to fraud prevention, the hardest thing to identify is when a good user turns bad. SHIELD Risk Intelligence does it effectively by continuously profiling the device session, returning real-time actionable risk signals to provide a complete picture of user activity in your ecosystem. It further enriches your existing data models with accurate device signals that identify malicious tools and techniques to stop fraud before it can happen.
Conclusion
Successful businesses are built on smart investments, and implementing an anti-fraud solution is one of the smartest investments you can make for your online business. If you don’t have an anti-fraud system in place or are still weighing your options, you’re leaving your platform vulnerable. Implementing an anti-fraud solution will lead to revenue savings and improve user experience. Now is the time to make this important decision—take action to protect your business today.
1 note
·
View note
Text
Bank Account Takeover Fraud: Key Tactics You Need to Know and How to Prevent it
Account Takeover (ATO) attacks are on the rise, affecting an estimated 24% of companies globally. In the United States, 22% of the adult population, equivalent to 24 million people, report falling victim to this type of incident.
It is projected that ATO fraud will result in losses exceeding USD 343 billion globally between 2023 and 2027, according to research from the American Bank. The financial industry is a primary target for fraudsters, with 84% of financial institutions having already faced this digital threat, resulting in losses amounting to 8.3% of their annual revenues, as per the Aberdeen Group's study.
Now, delving into the matter, what exactly is account takeover, and how is this form of fraud evolving?

What is an account takeover attack?
Account takeover (ATO) is a form of fraud in which cybercriminals illicitly access and take control of users' bank accounts to perform unauthorized transactions, transfer funds, or engage in other malicious activities.
To execute this type of crime, fraudsters will typically need to be able to access or fake at least one of these three things:
Username and Password: The most prevalent method for breaching accounts involves using stolen or leaked combinations of usernames and passwords. The risk is heightened by weak or reused passwords, underscoring the importance of users employing robust, distinct passwords for each of their accounts.
Phone Number: This is exploited by fraudsters to gain access to the second factor for authentication (2FA). By compromising the victim's phone, cybercriminals can intercept authentication codes sent via messages, circumventing additional security layers.
Phones can also be manipulated by fraudsters leveraging accessibility permissions, enabling control of the victim's device through malicious apps that monitor all displayed content and provide access to other installed apps.
Email Account: Email accounts play a pivotal role in account recovery processes. Fraudsters who gain access to victims' emails can reset passwords for various accounts linked to the email address.
Such information is obtained through techniques such as:
Social Engineering Attacks: Fraudsters manipulate users to expose data, infect devices with malware, or gain access to restricted systems. Phishing or spear-phishing is an example of this type of threat and is the most common in ATO. In these attacks, criminals send messages or emails that appear to be from legitimate sources, such as banks or trusted organizations. These messages often contain links to fake websites/apps created to collect confidential information or to trick the user into installing malware. According to some estimates, more than 3.4 billion malicious emails are sent every day.
Brute Force Attack: fraudsters employ a trial-and-error method to uncover login information. Through relentless attempts, they systematically work through all conceivable combinations in the hopes of stumbling upon the correct credentials. They may also use tools to automate the attack.
Credential Stuffing: Fraudsters use bots to test combinations of usernames and passwords on various sites. For instance, they might test the credentials of an e-commerce account on a banking account, taking advantage of people often reusing passwords across different platforms. This implies that if one account is compromised, others are also at risk.
SIM Swap: Criminals deceive the victim's mobile carrier and convince them to transfer the mobile number to a new SIM card, to which only they have access. This allows them to receive authentication codes and control accounts linked to the victim's phone
Exploring a New and Alarming Tactic: Accessibility Permissions Exploit
As technology advances, the techniques employed by fraudsters to execute account takeover (ATO) attacks evolve into increasingly sophisticated forms. Fraudsters consistently alter their strategies to outwit security systems, posing a constant challenge for detection and prevention.
Beyond the methods mentioned above, there's a new and particularly alarming tactic at play: fraudsters now exploit accessibility permissions for Account Takeover (ATO). Unlike traditional tactics, where fraudsters need access to email accounts, usernames & passwords, or a phone number to execute the fraud, this new approach allows them to gain remote control access to users' devices. Scary, right? Before delving into the details of how this works, let's understand what it is.
Accessibility features are available on Android and iOS operating systems to assist users - such as individuals with disabilities and the elderly - in using their smartphones. The functionalities include screen readers, voice commands, keystroke capturing, and other assistive technologies.
In order to use these services, accessibility permissions must be granted which gives applications full access to the user's device. While enabling accessibility permissions is crucial in this case, users also risk compromising their data. This is because, if used by fraudsters, it can become a tool for malicious activities.
Fraudsters are increasingly abusing this feature to take control of smartphones and commit fraud. When this happens, users become unable to uninstall the app or even restart the device.
Here's how the abuse of accessibility permissions looks like in action:
1. A user installs malware through a phishing link received via email or SMS, disguised as a legitimate app.
2. The malicious app initiates push notifications, urging the user to grant accessibility permission.
3. The user grants permission, enabling the fraudster to take control of the device (monitoring everything on the screen, keystrokes, and all installed apps).
4. The cybercriminal accesses the list of installed apps, collecting data the user types or displays (login credentials, passwords, credit card numbers), and intercepts authentication codes.
5. Armed with this information, the fraudster infiltrates the victim's bank account, conducting fraudulent transactions and pilfering funds.
Throughout the attack, the malware exploits accessibility services to:
Spy on user activity
Prevent the removal of the malicious app, whether from the home page or settings
Evade suspension or shutdown of the process
Impact of Bank Account Takeover Attacks (ATO)
In the world of digital banks, where all transactions happen online, account takeover (ATO) fraud is a big issue.
Here are the main impacts of this type of fraud:
Financial Losses: Account takeovers result in financial losses for both financial institutions and the customers whose accounts have been compromised.
Data Breach: A successful ATO often entails the breach of the user's confidential information. This may include login credentials, personal details, and financial data. The exposure of such information can lead to severe consequences for the affected individuals and erode trust in digital banking services.
Identity Theft: By gaining control of a user's account, fraudsters can impersonate the account holder, allowing them to commit various other identity-related crimes, such as applying for loans, credit cards, and other financial frauds in the victim's name.
User Trust Erosion: Customers expect their financial institutions to deliver reliable services, ensuring the security of their data and money. An account takeover incident can fracture trust and prompt users to close their accounts and migrate to competitors.
How to prevent ATO and ensure the security of users’ accounts?
Protecting your banking app and your customers' accounts from account takeover fraud is crucial, and this involves implementing fraud prevention software with a proactive approach to the constant and evolving problem.
SHIELD’s device-first risk intelligence solution is powered by cutting-edge device fingerprinting and the latest in AI & machine learning algorithms. It identifies fraud at its root and analyzes thousands of devices, network, and behavioral data points to provide actionable insights in real time. Our technology enables the detection of account takeover attempts through the combination of features:
SHIELD Device ID
Identifies each physical device used to access your banking application. It is extremely accurate and persistent, detecting when a fraudster attempts to mask the device fingerprint or reset the device to appear as new.
Our proprietary device fingerprinting technology is key to detecting and eliminating account takeover attacks. It flags suspicious devices and configurations that indicate someone is attempting to forge a device to access an account.
SHIELD Risk Intelligence
We continuously profile each device session, returning real-time risk signals to provide a comprehensive picture of user activity in your ecosystem. This involves detecting abuse of accessibility permissions and precisely identifying when a good user suddenly displays signs of fraudulent behavior. The tools utilized for such activities can include autoclickers, screen sharing, and emulators — clear indicators of an accessibility permissions exploit.
We enrich your data models with accurate device signals that identify the use of malicious tools and techniques employed in account takeover (ATO) attacks, such as emulators, app cloners, virtual OS, GPS spoofers, among others.
Our technology also ensures that your platform stays ahead of fraudsters with our Global Intelligence Network: a continuously updated library containing all fraud patterns we have encountered, as well as the latest malicious techniques. With over 7 billion devices and more than 1 billion user accounts analyzed worldwide, we leverage this intelligence to synchronize real-time attack patterns, ensuring a proactive approach to fraud prevention.
Bank Account Takeover Fraud: Key Tactics You Need to Know and How to Prevent it
1 note
·
View note
Text
Profile every single device on your app and website in real time.
Stop fraud, build trust, and drive growth without causing friction for your good customers. Know more here - https://shield.com/device-fingerprinting
2 notes
·
View notes