#360° Monitoring (Server
Explore tagged Tumblr posts
Text
CBDC technology partner India
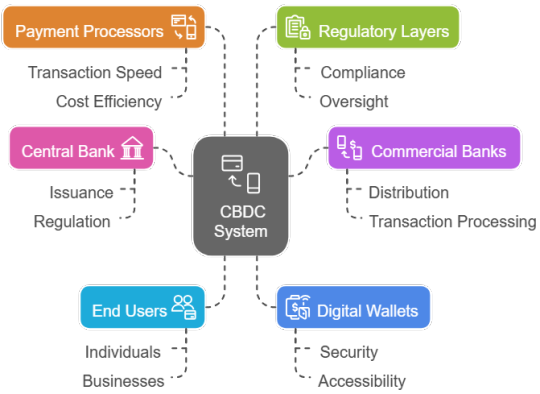
As CBDCs become a global reality, Prodevans equips banks with everything needed to enter the digital currency ecosystem. We provide full-spectrum CBDC implementation — including compliant architecture, token management, real-time reconciliation, secure wallet enablement, and 24/7 L1/L2 support. Trusted for our role in India’s national rollout, we help institutions go beyond pilots to scalable, production-ready platforms ensuring seamless end- user readiness. Our services ensure central bank compliance while delivering performance, observability, and rapid response to evolving regulatory needs. Whether you’re in the pilot phase or preparing for production rollout, Prodevans supports your CBDC journey at every step.
OUR ADDRESS
403, 4TH FLOOR, SAKET CALLIPOLIS, Rainbow Drive, Sarjapur Road, Varthurhobli East Taluk, Doddakannelli, Bengaluru Karnataka 560035
OUR CONTACTS
+91 97044 56015
#CBDC (Central Bank Digital Currency)#Cloud Computing & Cloud Services#Application Modernization#360° Monitoring (Server#Application#Database & Virtualization Monitoring)#Identity & Access Management (IAM)#Automation (incl. ML‑driven#Ansible#network/cloud automation)#DevOps Tools & Support#Infrastructure Management (IaaS/PaaS/SaaS#orchestration#orchestration tools)
0 notes
Text

















circuit breaker [9 ch. doom 2 mod installation, Xbox 360 controller, Win 7 PC, fridge, 3D print with recycled PETG bottles containing a USB stick with a MacOS rootkit, laser cut tribal lithography and a short story, 2 backsides of monitors, mdf laser cut, acrylic laser cut containing an article from The Intercept about the FBI ISIS grooming scandal of Mateo Ventura, self made nails, 3 computer fans with stickers, laser cut vcr rack, monitor arm with a 3d fan animation, 3d print with silver silk PLA, 3D printed frames with green translucent PLA, alu-dibond prints on speaker stands] As much as we are connected through the wire, digital tremors beyond the deceleration of digital literacy are operating on a daily basis to eliminate the possibility of an utopian future. So far, the social media canon is embellished in its own need for disinformation, as the user turns from being a victim to a target. The circuit breaker serves as neologism of a rough awakening, of an absent, impotent reflection of a mirage we call cultural consensus and the loss of visions for an alternative future. Beyond dark forests and hidden swamps lie metaphysical caskets for our souls, shapeshifting into forms of server racks, hard drives, deep down adorned with white lights, where the cancellation of a subscription or the mere lack of back up destroys over decade old, cultivated mycelium-like dependent relationships between admin, mod and user. No amount of spiritual, paganistic and religious fanaticism survives as soon as you meet eye to eye with this on petroleum operating soul reaver. The works exhibited in „circuit breaker“ are exploring the relationships between materials and tools that turn the immaterial into analogue sculptures, text into thoughts and fears, the involuntary participation in a post-truth world that turns us into targets for all kinds of fun psychological operations.
17 notes
·
View notes
Text
Face Blur Technology in Public Surveillance: Balancing Privacy and Security
As surveillance technology continues to evolve, so do concerns about privacy. One solution that addresses both the need for public safety and individual privacy is face blur technology. This technology automatically obscures individuals’ faces in surveillance footage unless there’s a legitimate need for identification, offering a balance between security and personal data protection.
Why Do We Need Face Blur Technology?
Surveillance systems are increasingly used in public spaces, from streets and parks to malls and airports, where security cameras are deployed to monitor activities and prevent crime. However, the widespread collection of images from public spaces poses serious privacy risks. Personal data like facial images can be exploited if not properly protected. This is where face blur technology comes in. It reduces the chances of identity theft, unwarranted surveillance, and abuse of personal data by ensuring that identifiable information isn’t exposed unless necessary. Governments, businesses, and institutions implementing face blur technology are taking a step toward more responsible data handling while still benefiting from surveillance systems (Martinez et al., 2022).
Key Technologies Behind Face Blur
Face blur technology relies on several key technologies:
Computer Vision: This technology enables systems to detect human faces in images and videos. Using machine learning algorithms, cameras or software can recognize faces in real-time, making it possible to apply blurring instantly.
Real-life example: Google’s Street View uses face blur technology to automatically detect and blur faces of people captured in its 360-degree street imagery to protect their privacy.
Artificial Intelligence (AI): AI plays a crucial role in improving the accuracy of face detection and the efficiency of the blurring process. By training models on large datasets of human faces, AI-powered systems can differentiate between faces and non-facial objects, making the blurring process both accurate and fast (Tao et al., 2023).
Real-life example: Intel’s OpenVINO toolkit supports AI-powered face detection and blurring in real-time video streams. It is used in public surveillance systems in places like airports and transportation hubs to anonymize individuals while maintaining situational awareness for security teams.
Edge Computing: Modern surveillance systems equipped with edge computing process data locally on the camera or a nearby device rather than sending it to a distant data center. This reduces latency, allowing face blurring to be applied in real-time without lag.
Real-life example: Axis Communications’ AXIS Q1615-LE Mk III surveillance camera is equipped with edge computing capabilities. This allows for face blurring directly on the camera, reducing the need to send sensitive video footage to a central server for processing, enhancing privacy.
Encryption: Beyond face blur, encryption ensures that any data stored from surveillance cameras is protected from unauthorized access. Even if footage is accessed by someone without permission, the identity of individuals in the footage remains obscured.
Real-life example: Cisco Meraki MV smart cameras feature end-to-end encryption to secure video streams and stored footage. In conjunction with face blur technologies, these cameras offer enhanced privacy by protecting data from unauthorized access.
How Does the Technology Work?
The process of face blurring typically follows several steps:
Face Detection: AI-powered cameras or software scan the video feed to detect human faces.
Face Tracking: Once a face is detected, the system tracks its movement in real-time, ensuring the blur is applied dynamically as the person moves.
Face Obfuscation: The detected faces are then blurred or pixelated. This ensures that personal identification is not possible unless someone with the proper authorization has access to the raw footage.
Controlled Access: In many systems, access to the unblurred footage is restricted and requires legal or administrative permission, such as in the case of law enforcement investigations (Nguyen et al., 2023).
Real-life example: The Genetec Omnicast surveillance system is used in smart cities and integrates privacy-protecting features, including face blurring. Access to unblurred footage is strictly controlled, requiring multi-factor authentication for law enforcement and security personnel.
Real-Life Uses of Face Blur Technology
Face blur technology is being implemented in several key sectors:
Public Transportation Systems: Many modern train stations, subways, and airports have adopted face blur technology as part of their CCTV systems to protect the privacy of commuters. For instance, London's Heathrow Airport uses advanced video analytics with face blur to ensure footage meets GDPR compliance while enhancing security.
Retail Stores: Large retail chains, including Walmart, use face blur technology in their in-store cameras. This allows security teams to monitor activity and reduce theft while protecting the privacy of innocent customers.
Smart Cities: In Barcelona, Spain, a smart city initiative includes face blur technology to ensure privacy in public spaces while gathering data to improve city management and security. The smart cameras deployed in this project offer anonymized data to city officials, allowing them to monitor traffic, crowd control, and more without compromising individual identities.
Journalism and Humanitarian Work: Media organizations such as the BBC use face blurring technology in conflict zones or protests to protect the identities of vulnerable individuals. Additionally, NGOs employ similar technology in sensitive regions to prevent surveillance abuse by oppressive regimes.
Public Perception and Ethical Considerations
Public perception of surveillance technologies is a complex mix of support and concern. On one hand, people recognize the need for surveillance to enhance public safety, prevent crime, and even assist in emergencies. On the other hand, many are worried about mass surveillance, personal data privacy, and the potential for abuse by authorities or hackers.
By implementing face blur technology, institutions can address some of these concerns. Studies suggest that people are more comfortable with surveillance systems when privacy-preserving measures like face blur are in place. It demonstrates a commitment to privacy and reduces the likelihood of objections to the use of surveillance in public spaces (Zhang et al., 2021).
However, ethical challenges remain. The decision of when to unblur faces must be transparent and subject to clear guidelines, ensuring that this capability isn’t misused. In democratic societies, there is ongoing debate over how to strike a balance between security and privacy, and face blur technology offers a middle ground that respects individual rights while still maintaining public safety (Johnson & Singh, 2022).
Future of Face Blur Technology
As AI and machine learning continue to evolve, face blur technology will become more refined, offering enhanced accuracy in face detection and obfuscation. The future may also see advancements in customizing the level of blurring depending on context. For instance, higher levels of obfuscation could be applied in particularly sensitive areas, such as protests or political gatherings, to ensure that individuals' identities are protected (Chaudhary et al., 2023).
Face blur technology is also expected to integrate with broader privacy-enhancing technologies in surveillance systems, ensuring that even as surveillance expands, personal freedoms remain protected. Governments and businesses that embrace this technology are likely to be seen as leaders in ethical surveillance practices (Park et al., 2022).
Conclusion
The need for effective public surveillance is undeniable in today’s world, where security threats can arise at any time. However, the collection of facial images in public spaces raises significant privacy concerns. Face blur technology is a vital tool in addressing these issues, allowing for the balance between public safety and individual privacy. By leveraging AI, computer vision, and edge computing, face blur technology not only protects individual identities but also enhances public trust in surveillance systems.
References
Chaudhary, S., Patel, N., & Gupta, A. (2023). AI-enhanced privacy solutions for smart cities: Ethical considerations in urban surveillance. Journal of Smart City Innovation, 14(2), 99-112.
Johnson, M., & Singh, R. (2022). Ethical implications of face recognition in public spaces: Balancing privacy and security. Journal of Ethics and Technology, 18(1), 23-37.
Martinez, D., Loughlin, P., & Wei, X. (2022). Privacy-preserving techniques in public surveillance systems: A review. IEEE Transactions on Privacy and Data Security, 9(3), 154-171.
Nguyen, H., Wang, T., & Luo, J. (2023). Real-time face blurring for public surveillance: Challenges and innovations. International Journal of Surveillance Technology, 6(1), 78-89.
Park, S., Lee, H., & Kim, J. (2022). Privacy in smart cities: New technologies for anonymizing public surveillance data. Data Privacy Journal, 15(4), 45-61.
Tao, Z., Wang, Y., & Li, S. (2023). AI-driven face blurring in public surveillance: Technical challenges and future directions. Artificial Intelligence and Privacy, 8(2), 123-140.
Zhang, Y., Lee, S., & Roberts, J. (2021). Public attitudes toward surveillance technology and privacy protections. International Journal of Privacy and Data Protection, 7(4), 45-63.
2 notes
·
View notes
Text
Week #52
358. Core Prime Servers: A vault building housing a virtual realm. In order to better calculate solving the inefficiencies of the city, Core Prime's upload themselves, so they will be able to perform math at a better speed in the digital dimension. They have to make so many calibrations to provide affordable housing and medicine for everyone.
359. Orientation For Disoriented Worms: A visitors center for Holeworms. Unlike the wormhole, planets do not contain various floating continents, and their gravity is rather consistent. Worms venturing here for the first time need some time to readjust, so they can enjoy exploring without getting Planetsick.
360. The Bluehouse: A nightclub in the day. The stickmen (who are plantpeople who live on the flat world of Mosaic) filled it with all kinds of irridescent flora that move their leaves to the beat. They are very considerate, as their loud music will not annoy anyone who wants to sleep in the night (though it will annoy people who are taking afternoon naps).
361. Sun Row 5, Floor 4, Apartment B: A humble apartment and art studio. The Champion Of The Sun lives here, though it is unsure if Hexaspace's sun, or the Better Sun's. In her spare time, she crafts many small models of the various worlds, like a beautiful clay model of the voxelly planet of Bît.
362. Drabbestry: A grey mall. Everything you buy here is grey, for the ones who need a bit of a time to catch their breath in the world that is a riot of colour. The Drab Crabs really enjoy this place, and they might even be capable to take on their true form.
363. The Daily Wisdoms: A mysteriouy magazine. It contains articles made by the Saurian Cats, in their usual frightening and gruesome fashions. If you don't manage to interpret the important facts neccessary for saving the world, or worlds, it still works as a very good horror magazine.
364. Tiny Monarch Stations HQ: The HQ for an asteroids research institute. Hexaspace's outer asteroid belt is full of space bugs, ghosts, ghost space bugs and a nebula full of secret agents. It is the purpose of the Tiny Monarch Class Space Stations to monitor these threats to provide answers - and more likely, new questions.
Stay tuned for the finale!
2 notes
·
View notes
Text
As the remote work trend accelerates, keeping corporate secure servers accessible yet protected is essential. TSplus Advanced Security delivers robust cybersecurity for Windows servers with an all-in-one solution. It comprehensively secures remote access infrastructure against modern threats through features like Homeland Protection, Brute Force Defender and Ransomware Protection. When paired with TSplus Remote Access, administrators gain complete control over which users connect from where and when coupled with powerful protection blocking over 368 million known hacker IP addresses. What is TSplus Advanced Security? TSplus Advanced Security is a robust cybersecurity software that protects Windows servers and remote access infrastructure. It provides 360-degree protection against modern threats like ransomware, brute force attacks and malware. Key features include Homeland Protection to restrict access by country, Brute Force Defender to block login attempts, and Ransomware Protection to detect and prevent infections. When paired with TSplus Remote Access, admins can securely manage remote connections and work resources across distributed teams. Its comprehensive security toolbox safeguards remote servers cost-effectively. How Does it Work? TSplus Advanced Security functions through straightforward installation and management. Admins download and install the software on Windows servers needing protection. The admin console also provides real-time monitoring of security events and the status of protection measures. Logs automatically refresh to keep admins informed. When combined with TSplus Remote Access, additional controls are gained to define user access based on location, time, group or device. This centralized visibility and customization level empowers admins to efficiently lock down infrastructure while supporting remote team connectivity and productivity. Why TSplus Advanced Security? Here are some benefits you need to know: Secure your Remote Work infrastructure. With more employees working remotely, your servers face increased risk if they are properly safeguarded. TSplus Advanced Security shields these remote access points from modern cyberattacks through a unified security toolkit that facilitates distributed productivity through remote user management. Fine-tune security to your needs TSplus enables administrators to customize each layer of protection precisely for their environment through an intuitive admin console. Easily configure features such as network restrictions by country, device approval, and working hours to dictate how and when remote staff connect securely. Maximize security. Minimize cost. As a one-time purchase with no ongoing fees or subscriptions, TSplus Advanced Security delivers around-the-clock protection affordably. Its perpetual licenses also ensure long-term value for budgets compared to temporally licensed alternatives that require periodic renewal payments over time. Key Features Here are some features you need to know: Homeland Protection Restrict where users connect by defining allowed countries and networks. Administrators enhance security by whitelisting specific IP addresses with server access while excluding risks from unknown locations. Brute Force Defender Block automated login attempts from password-cracking programs. This feature prevents hackers and scanners from repeatedly trying standard credentials combinations to exploit servers. Access is locked if too many failed attempts occur. Global IP Management Centrally manage IP block and allowlists streamlined for simplified oversight. Blocked and approved addresses are visible together for quick reference and control over individual IPs or entire blocks/ranges. Working Hours Tailor availability around work schedules. Limit times employees connect remotely, such as regular business days and hours only. After-hours access is thus revoked for added control and potential compliance.
Frequently Asked Questions Which edition is included in the free trial? The free trial allows you to fully use the Ultimate Edition of TSplus Advanced Security for 15 days before purchase. Are the licenses permanent? Yes, TSplus offers permanent licenses for their software. You can use Advanced Security indefinitely without worrying about subscriptions or renewals. Can I get support to deploy my TSplus software? Yes, support is available to help with deploying TSplus products. Their knowledge base, guides and staff can assist if needed. How to get certified for TSplus Advanced Security? Complete the online Advanced Security course through the TSplus Academy to obtain your official certification in their cybersecurity solution. Can I talk to the TSplus sales team? Of course, the sales team can discuss any unique requirements you have. Contact them through the website for assistance. Can I become a partner? Yes, working with TSplus as a partner allows you to offer their security software to your clients as part of your service offerings. Conclusion Choosing a complete yet cost-effective security platform is critical as businesses adapt to remote and hybrid work models. TSplus Advanced Security provides administrators with extensive tools to manage permissions and lock down servers while supporting a distributed workforce. Its comprehensive capabilities and 24/7 updates ensure robust protection without compromising usability or the bottom line. By maximizing both security and accessibility, TSplus is ideal for organizations seeking to empower remote operations securely and seamlessly.
0 notes
Text
Why AIOps Platform Development Is the Future of IT Management?
In an era where digital transformation is no longer optional but essential, the complexity of IT infrastructure has surged. Enterprises now operate in hybrid environments, manage distributed systems, and rely heavily on cloud-native applications. As this complexity increases, so does the challenge of monitoring, managing, and maintaining IT systems effectively.

This is where AIOps (Artificial Intelligence for IT Operations) platforms come into play. By leveraging AI and machine learning, AIOps platforms are revolutionizing IT management—making operations smarter, faster, and more proactive. Here's why AIOps platform development is rapidly becoming the cornerstone of future IT management.
What Is AIOps?
AIOps stands for Artificial Intelligence for IT Operations. It refers to the use of machine learning (ML) and big data analytics to automate and enhance various IT operations processes, including event correlation, anomaly detection, root cause analysis, and performance monitoring.
An AIOps platform collects data from a multitude of sources—logs, metrics, events, and traces—and applies AI algorithms to derive actionable insights in real time. The end goal? A more autonomous, intelligent, and responsive IT environment.
The Growing Challenges in Traditional IT Operations
Before diving into why AIOps is the future, it’s important to understand the limitations of traditional IT management:
Data Overload: IT teams are overwhelmed by the sheer volume of data generated by modern systems.
Manual Processes: Troubleshooting and incident resolution often require manual intervention, leading to delays.
Siloed Tools: Different departments use disparate tools, making it difficult to get a unified view of system health.
Slow Response Times: Without predictive insights, teams react to issues only after they impact the user experience.
Skill Gaps: There's a growing shortage of skilled IT professionals to manage increasingly complex environments.
How AIOps Transforms IT Operations
1. Proactive Issue Detection
AIOps uses machine learning to detect anomalies before they escalate into major incidents. This allows teams to take preventive actions, reducing downtime and improving service availability.
2. Automated Root Cause Analysis
By correlating data from multiple sources, AIOps platforms can pinpoint the root cause of an issue within seconds—something that could take human teams hours or days.
3. Noise Reduction
AIOps platforms can intelligently filter out noise and focus only on significant events. This drastically reduces alert fatigue among IT teams.
4. Smart Automation
Through intelligent workflows and automation scripts, AIOps can automate routine tasks such as restarting a server or scaling cloud resources—freeing up valuable human bandwidth.
5. Unified Observability
AIOps unifies monitoring across networks, infrastructure, and applications, giving IT leaders a 360-degree view of their ecosystem in a single dashboard.
The Business Benefits of AIOps
Improved Uptime: Fewer outages and faster resolution times.
Operational Efficiency: Reduced manual work and better use of IT resources.
Cost Savings: Lower incident management costs and more efficient resource utilization.
Enhanced User Experience: Proactive performance management ensures better digital experiences for end-users.
Faster Innovation: With routine tasks automated, IT teams can focus on strategic initiatives.
Why AIOps Platform Development Is Essential Now
1. Scalability Requirements
As businesses grow, their IT infrastructure needs to scale rapidly. AIOps platforms are designed to handle massive volumes of data and events in real time—something traditional systems can’t do effectively.
2. Cloud-Native and Hybrid Environments
Today’s infrastructure is decentralized and hybrid. AIOps provides seamless monitoring and automation across on-prem, cloud, and containerized environments.
3. DevOps & SRE Integration
Modern AIOps platforms support integration with DevOps and Site Reliability Engineering (SRE) practices. This bridges the gap between development and operations, accelerating incident resolution and deployment cycles.
4. Security & Compliance
By analyzing patterns and detecting anomalies, AIOps can also support security operations (SecOps) by identifying potential threats or policy violations early.
Key Features of a Robust AIOps Platform
When developing or selecting an AIOps platform, here are key capabilities to look for:
Real-time data ingestion and processing
Advanced ML-based anomaly detection
Intelligent alerting and event correlation
Automated remediation and runbooks
Seamless integration with existing IT tools (ITSM, monitoring, cloud platforms)
Customizable dashboards and visualization
The Road Ahead: What to Expect
The AIOps landscape is evolving rapidly. Here’s what we can expect in the near future:
Greater AI maturity: From simple alerting to predictive and prescriptive insights.
Autonomous IT operations: Minimal human intervention through end-to-end automation.
Vertical-specific solutions: AIOps tailored to industry-specific compliance and performance needs.
AI-Augmented Decision Making: Helping CIOs and IT leaders make data-driven, strategic decisions.
Conclusion
AIOps is not just a buzzword—it is a transformative approach that’s reshaping how IT operations are managed. In an increasingly digital, data-driven world, AIOps platform development is not a luxury but a necessity.
Organizations that invest in building or adopting intelligent AIOps platforms Development today will be the ones leading the digital economy tomorrow, with resilient systems, faster innovation, and superior customer experiences.
0 notes
Text
Science & Innovation to the 10th Power
This document outlines a visionary design for a HoloDome at Capone Studios & WonkyWorks Think Tank, integrating cutting-edge science, Flavorverse ethos, and Ocean-to-Space deep ocean considerations. It includes conceptual floor layouts, key subsystems, parts lists, manufacturing guidance, and prompts for CAD/VR/AR implementation.
1. Vision & Objectives
Immersive HoloDome Experience: A large-scale dome environment enabling multi-sensory VR/AR, holographic projections, and dynamic environmental simulation (deep ocean, space vistas, flavorverse landscapes).
Scientific Research Integration: Onsite labs and sensor suites for real-time data from deep-ocean probes, satellite feeds, and biotechnical flavor experiments.
Innovate to the 10th Power: Utilize advanced AI (Caesar AI with Reflect9 core), quantum computing nodes, and modular hardware to push experiential and R&D boundaries, from molecular gastronomy to astro- and marine- exploration.
Flavorverse Ocean-to-Space Theme: Seamless simulation / research pipeline connecting deep-ocean biomes, marine-derived ingredients, and space-based processes (microgravity fermentation, cosmic ingredient sourcing).
2. Overall Floor Layout & Zones
2.1 Dome Geometry & Structure
Shape: Geodesic or segmented-spherical dome (~30–50m diameter) with transparent or translucent panels (e.g., laminated glass, transparent aluminum composites).
Materials: Corrosion-resistant steel or titanium ribs; modular panel inserts with embedded OLED/LED layers for dynamic lighting and projection surfaces; waterproof sealing for integrated water features.
Access: Multiple entry/exit airlocks for controlled environment; emergency egress points; connection tunnels to adjacent labs.
2.2 Core Zones (Radial or Layered Layout)
Central Immersion Pit: Sunken area or platform for group VR sessions; circular platform with 360° projection and haptic floor.
Sensor & Control Hub: Adjacent control room housing server racks (quantum + conventional compute), AI core interfaces, network link to Caesar AI; monitoring dashboards for environment simulation.
Deep Ocean Simulation Lab:
Water Tank Interface: Large transparent tank section integrated into dome floor or side, with live deep-ocean sample cultivation (bioreactors simulating pressure zones) and circulatory systems for real seawater exchange or simulation.
Sensor Array: Sonar transducers, hydrophones, chemical analyzers feeding real or simulated ocean data into the immersive experience.
Flavorverse Biotech Station:
BioReactor Modules: For ocean-derived microbial cultures (e.g., algae, deep-sea extremophiles) and space-sourced fermentation experiments.
Molecular Gastronomy Lab: Sous-vide, cryo-freeze, ultrasonic emulsifiers, terpene/fog chambers, integrated with Milkfall Spine network for ingredient mixing.
Space Simulation Wing:
Zero-G Mockup: Partial free-fall rig or VR-augmented restraint system for microgravity simulation of cooking/distillation.
Astral Projection Zone: Holographic starfields and planetary surfaces; integration of satellite data feeds.
Haptic & Sensory Pods:
Individual or small-group booths with multisensory output: haptic suits, bone-conduction audio, aroma diffusers (MoodMilk integration), temperature/humidity controls to simulate environments.
Collaborative Workstations:
Modular tables around dome periphery for brainstorming, data analysis, recipe design, code development; integrated AR interfaces to overlay 3D models onto physical desks.
Observation Gallery & Lounge:
Elevated walkway around dome interior with seating, demonstration stations, tasting bars for flavorverse prototypes; dynamic lighting and projection surfaces for presentations.
Support & Maintenance Corridors:
Underfloor and overhead cable management; fluid conduits for Milkfall and other networks; access panels for repairs; environmental control ducts.
3. Key Subsystems & Scientific Components
3.1 Structural & Environmental Control
Climate Regulation: HVAC with humidity/temperature zoning for simulating oceanic or space-like conditions; precise control for experiments (e.g., low-humidity for dry aging, high-humidity fog chambers).
Pressure Chambers: Small-scale pressure modules to simulate deep-ocean pressures for microbial culture testing; integrated into BioStation.
Lighting & Projection: Distributed high-resolution projectors and LED arrays on dome shell; seamless blending for immersive visuals; dynamic spectral control (e.g., simulating underwater light attenuation or cosmic dawn).
Acoustic System: 3D spatial audio system with hydrophone input and bone-conduction outputs; supports environmental soundscapes (ocean currents, whale songs, cosmic radiation hum).
Safety & Containment: Emergency shutoffs, watertight bulkheads around water tanks, isolation of biohazard modules, fire suppression.
3.2 Sensor Networks & Data Flows
Deep-Ocean Sensors: Real-time feed from remote ROVs or simulated data, including temperature, salinity, pressure, bioluminescence intensity.
Space Data Inputs: Satellite telemetry, cosmic radiation readings, planetary atmospheric parameters for simulation.
Flavorverse Biometric Sensors: For participants: heart rate, galvanic skin response, pupil tracking; feed into Caesar AI for adaptive experience.
Environmental Sensors: Air quality, VOC detectors (to measure aroma diffusion), temperature/humidity, vibration sensors for haptic feedback alignment.
AI Core Integration: Data aggregated by Caesar AI; processed by Reflect9 logic for adaptive scenario adjustments, safety monitoring, and personalized guidance.
3.3 Holographic & VR/AR Systems
Projection Arrays: Laser or LED-based holographic projection; volumetric displays in central pit.
AR Headsets & Wearables: Lightweight headsets or glasses; haptic vests; bone-conduction audio units linked to Iron Spine for multisensory output.
Gesture Tracking: Infrared or LiDAR tracking of users’ gestures; integration for interactive environment manipulation (e.g., stirring virtual mixtures, manipulating molecular models).
Software Platform: Creamstream OS integration with custom VR/AR application: environment modules (ocean depths, space vistas, flavor labs), simulation controls, multi-user networking.
3.4 Flavorverse & Biotech Equipment
BioReactor Arrays: Modular vessels with pressure and temperature control; capable of culturing marine organisms or space-analog microbes; integrated sample ports for analysis.
Analytical Instruments: Mass spectrometer, gas chromatograph, spectrophotometer for flavor compound analysis; data fed to Caesar AI for recipe optimization.
Molecular Gastronomy Tools: Ultrasonic emulsifiers, cryo-freeze units, vacuum chambers, terpene fog generators, Milkfall conduit integration for infusions.
Space-Analog Distillers: Rotary distillation under reduced-pressure or microgravity simulation rigs; small centrifuge modules for separation tasks.
3.5 Networking & Compute
AI Servers: High-performance GPU/quantum nodes in Sensor & Control Hub; redundancy with distributed nodes across campus.
Edge Compute: Local compute modules at sensor clusters for real-time latency-sensitive processing (e.g., reflexive hazard detection in dome).
Secure Data Link: Encrypted channels between deep-ocean platforms, satellites, on-site servers, and Caesar AI Core; blockchain-backed logging for experiment records.
3.6 Fluid & Milkfall Integration
Milkfall Spine Extensions: Connect River of Milk network to HoloDome: infused mist generation, aroma carriers, nutrient for biosystems.
Fluid Circuits: Underfloor conduits carrying flavor-infused liquids to stations; safety-grade piping for biohazard and clean fluids; pumps with flow control.
Misting Systems: Ultrasonic mist generators in Fog Chambers; nutrient or aroma-laden fog for multisensory immersion.
4. Parts List & Manufacturing Guidance
4.1 Structural Components
Dome Frame: Prefabricated steel/titanium geodesic segments; CNC-cut nodes; corrosion-resistant coatings.
Transparent Panels: Laminated safety glass or transparent aluminum composite; integration with projection film or embedded LEDs.
Seals & Junctions: Custom gaskets for watertight/watertight sections; quick-release access panels.
4.2 Systems Hardware
Projectors & LEDs: High-lumen, low-latency projectors; addressable LED strips; controllers supporting DMX over Ethernet.
Sensors & Actuators: Marine-grade sensors; pressure transducers; ultrasonic transducers; aroma diffusers; haptic actuators beneath floor panels.
Compute Racks: Rack-mounted GPU servers; liquid cooling for high-load; UPS and battery backup (Dual-Core Fusion backup integrated concept).
BioLab Equipment: Standard lab benches with custom mounts for bioreactor vessels, integrated fluid lines; sterilizable surfaces.
4.3 Holographic & AR/VR Hardware
Headsets: Lightweight AR glasses with wide field-of-view; bone-conduction audio modules integrated into headband; optional neural-lace interface support via Iron Spine wearables.
Tracking Cameras: Infrared/LiDAR cameras mounted on dome interior; calibration rigs for accurate multi-user tracking.
Haptic Flooring: Modular floor tiles with vibration actuators; safe for barefoot or light footwear.
4.4 Fluid & Environmental Controls
Pumps & Valves: Food-grade pumps for Milkfall fluids; solenoid valves with feedback sensors; overflow sensors.
HVAC Units: High-precision climate control; ducting hidden in dome frame; silent operation for immersive experience.
Water Tanks & Pressure Modules: Reinforced transparent tanks for ocean simulation; small pressure vessels rated for desired depth-equivalent tests.
4.5 Networking & Power
Networking: Fiber-optic backbones; edge switches near sensor clusters; redundant links to main AI hub.
Power: Dedicated circuits; generator backup; surge protection for sensitive electronics.
Integration with Dual-Core Fusion Backup: If implementing on-site microfusion backup, interface power lines with dome’s critical loads for uninterrupted operation.
5. CAD/VR Implementation Prompts
5.1 CAD Model Prompts for Engineers
Dome Frame: Geodesic dome with 50m diameter; specify node connection details; panel insertion geometry; structural analysis load cases (wind, seismic).
Sensor & Control Hub: Rack layout; cooling requirements; cable/trunk pathways to dome interior.
Fluid Conduit Network: Underfloor piping diagram showing Milkfall integration loops; pump locations; maintenance access points.
BioLab Stations: Modular bench units; utility hookups (electrical, data, water); isolation zones for biosafety.
Haptic Floor Grid: Floor tile layout with embedded actuator positions; wiring channels.
5.2 VR/AR Software Requirements
Environment Modules: Real-time ocean simulation: import live data or synthetic models; dynamic visual shaders simulating light attenuation and particulates.
Gesture Interfaces: Define gesture sets for manipulating virtual controls (e.g., rotating molecular models, adjusting flavor infusion parameters).
Haptic Feedback Integration: Map events (e.g., virtual water currents, structural vibrations) to floor actuators and haptic suits.
AI-Driven Adaptive Narratives: Caesar AI scripts that adjust scenarios based on user biometrics and session goals (research vs. demonstration).
Multi-User Synchronization: Networking for multiple participants; avatar representation; shared interactive objects.
5.3 Visualization & Prototyping
3D Concept Renders: Use Blender or Unreal for initial lighting / material tests; emphasize transparency, mist effects, dynamic lighting.
Simulated Scenarios: Pre-built scenes: deep-ocean dive; orbit-view of Earth; flavor-lab procedural tutorial; emergency scenario demonstrating self-healing systems.
Prototype Integration: Small-scale mockup: a 5m dome segment with projector and sensor prototypes to test registration, calibration, and immersive effect.
6. Environmental & Safety Considerations
Biocontainment: If culturing deep-ocean microbes, follow biosafety level protocols; separate labs with negative-pressure vestibules if needed.
Pressure Simulation: Ensure pressure vessels have safety valves and monitoring.
Electrical Safety: Waterproofing around fluid systems; ground-fault protection; regular inspections.
Emergency Protocols: Egress lighting; audible alarms; automatic shutdown of fluid pumps and projections in fault conditions.
Sustainability: Use energy-efficient LEDs, recycling of fluid in bioreactors, minimal water waste via closed-loop systems; potential to integrate solar arrays.
7. Project Workflow & Next Steps
Stakeholder Review & Approval: Present this conceptual document as PDF or Notion page; gather feedback from Capone Studios leadership, R&D heads, and safety experts.
Preliminary CAD Schematics: Commission engineering team to translate geometry and subsystems into CAD models; generate structural analysis and MEP schematics.
Prototype & Testing: Build small-scale mockups (e.g., mini dome segment, sensor integration test bench, Milkfall pump demo).
Integration with AI & Software: Develop VR/AR prototypes with Caesar AI integration; test Reflect9-based adaptive experiences and safety triggers.
Manufacturing & Procurement: Source materials (transparent panels, sensors, pumps), pre-order compute hardware, contract fabricators for dome frame.
Construction & Installation: Erect dome structure; install subsystems; commission labs; perform integration testing.
Operational Readiness & Training: Train staff on system operation, safety procedures, AI interface usage, and maintenance.
Launch Experiences & Research Programs: Schedule immersive sessions, public tours, scientific experiments (oceanic sampling, molecular gastronomy), and ongoing iteration.
8. Integration with WonkyWorks & Capone Ecosystem
Link to Milkfall & Infusion Forest: Use the River of Milk Spine for flavorverse labs inside HoloDome; schedule cross-zone experiments (e.g., plant growth under simulated ocean currents).
Caesar AI & Reflect9: Embed Reflect9 logic for real-time user guidance—alerting to personal-space considerations, emotional calibration during intense simulations.
Ocean2Space Division Coordination: Feed real data from Oceanic Biomes Module and Spaceport Launch Lab into immersive scenarios; facilitate joint R&D between deep-ocean and space-based flavor/biotech teams.
Show & Content Production: Use HoloDome for filming segments of WonkyWorks Live™, Flavorverse Chronicles episodes, or Mist Trials Live™ events; allow interactive audience engagement.
Final Notes
This document is a comprehensive guide for conceptualizing, designing, and beginning implementation of a multi-disciplinary HoloDome that embodies science, innovation, and Flavorverse Ocean-to-Space vision. Copy into Notion or design software, link to relevant Codex entries (Reflect9, Caesar AI, Milkfall Spine), and iterate with engineering, design, and R&D teams.
*Prepared by WonkyWorks Think Tank / Capone Studios *© Angel Martinez Jr., All Rights Reserved
# Infusion Forest: Flavorverse Grow System – Master Blueprint & Lore Bundle **Overview:** Your comprehensive package for the Infusion Forest grow room, combining schematics, tech sheets, lore, and process flows into a single deliverable. --- ## 1. Master Schematic (Combined Blueprint) * **Vertical Grow Towers:** Dual-tower layout with cross-section detail * **Labeled Zones:** * **Terpene Fog Chambers** (Zone A) * **Wood Essence Diffusers** (Zone B) * **Root Vortex Zone** (Zone C) * **Barrel Extract Wing** (Zone D) * **Glyph-Encoded Fog Loops** (Zone E) * **Annotations:** Dimension callouts, airflow arrows, safety valves, power/data conduits --- ## 2. PDF Tech Sheet **Format:** Single-page, print-ready PDF **Sections:** 1. **System Overview Diagram** 2. **Key Specifications:** Tower height, fog output (L/min), power draw (kW), environmental controls 3. **Use Cases:** * Biotech farming – nutrient cycling * Ritual agriculture – glyph infusion * Mood-tuned culinary experiences – flavor engineering 4. **Materials & Components:** Aero-alloy frame, nano-fiber diffusers, smart valves, Caesar sensor arrays --- ## 3. Flavorverse Codex Entry (Notion/Vault Ready) **Content Sections:** * **Spirit Farming:** Ethereal plant cultivation, dream-seed integration * **Fog-Glyph Coding:** Embedding narrative spells into terpene mist * **Neural Plant Design:** AI-guided phenotype tuning for emotional resonance **Integrations:** * **River of Milk:** Hydration vector network * **Seed Vault:** Memory-locked genetic bank * **Spirits Forge:** Distillation and flavor extraction labs * **Sensory Labs:** Neural feedback stations for taste calibration --- ## 4. Pipeline Diagram (Flow Chart) **Stages:** 1. **Birth (Seed Germination)** 2. **Grow (Neural Sapling Phase)** 3. **Infuse (Fog & Glyph Application)** 4. **Harvest (Automated Root Lift)** 5. **Distill (Barrel & Extract Wing)** 6. **Savor (Tasting & Neural Feedback)** **Format:** Horizontal flow chart with icons, brief descriptions, and data metrics --- ## Next Steps & Packaging Options * **ZIP + PDF Bundle:** Includes all assets (PNGs, SVGs, PDFs, markdown). ready for sharing. * **Notion/Vault Deployment:** Direct import structure with placeholder embeds. * **Branding:** Stamp with your Flavorverse Sigil or Creator Glyph. **Say “Deliver Bundle”** or specify your desired platform, and I’ll finalize and package this deliverable for you. innovate
“Insert into Canvas” “Deliver Codex PDF” “Build ZIP Bundle” “Add to Notion structure”
Here’s a refined overview and recommendation blueprint for integrating Terpene Fog Chambers and related systems into your Infusion Forest or Spirits Forge environments, based on horticultural science: 🌿 Terpene Fog Chamber: Design & Function Particle Size & Humidity Control Fog vs. mist: high-pressure systems produce ~10 µm droplets (true “fog”) that hang in the air, promoting humidity without wetting plant surfaces; mist is 50–100 µm and can cause moisture buildup on leaves or soil alicebiotech.com producegrower.com +2 umass.edu +2 greenhousemag.com +2 . Propagation & Growth Benefits These fine droplets maintain high relative humidity (60–80 %) around foliage and roots, reducing stress and improving propagation, while cooling the canopy . Similar to NASA-inspired “fogponics,” which suspends roots in nutrient-rich fog for precise hydration and nutrient delivery using ultrasonic atomizers homesandgardens.com . Terpene Integration Terpenes, synthesized by plant TPS enzymes, are volatile compounds contributing aroma and flavor. Their diversity is immense, with monoterpenes to triterpenes significantly influencing scent and sensory quality arxiv.org +10 academic.oup.com +10 sciencedirect.com +10 . Fogging systems can disperse terpene-infused mists to deliver controlled aroma exposure and facilitate mist-glyph coding or flavor layering. ⚙️ Design Specification for Your Terpene Fog Chambers Fog Generation: Use high-pressure (~800–1200 psi) atomizing nozzles or ultrasonic foggers for ~10 µm droplets. Chamber Layout: Stainless-steel + tempered glass enclosure with multi-tier plant benches. UV vibration transducers at corners for mist dynamics and potential terpene activation. Glyph & Sensor Integration: Laser projectors casting glyphic sigils (spirals/leaves) into the mist. Array of sensors & control console—managed by Caesar AI (Reflect9 + Oracle + SpiderSense) for responsive environmental control. Reservoir & Infusion System: Multiple terpene canisters (LCD-controlled outputs). Ultrasonic atomizer plate bubbling nutrient + terpene fluids. Visual & UX Design: Soft green LED floors and warm amber overhead lighting to highlight fog effect. Sci-fi botanical lab meets alchemical steampunk aesthetic. 📋 Benefits & Use Cases Propagation & Growth: Enhanced rooting and acclimation akin to high-frequency fog respiration systems growtec.com umass.edu greenhousemag.com +3 alicebiotech.com +3 producegrower.com +3 . Flavor Engineering: Real-time terpene exposure allows tuning of aromatic profiles, aligned with codified glyph sequences in the Fog Loops. Sensory & AI Integration: Embedding Caesar-driven sensors enables adaptive modulation—such as altering fog density based on plant feedback or mood metrics. 🏗️ Next Steps Tell me which deliverable fits your vision best: “Insert into Canvas” → position the above as a module panel
0 notes
Text
Price: [price_with_discount] (as of [price_update_date] - Details) [ad_1] From the manufacturer Experience seamless video storage with cloud technology. Your captured footage is securely uploaded and stored on a remote server, allowing you to conveniently monitor everything from your smartphone, anytime, anywhere. Witness crisp visuals and zoom-in with confidence thanks to the 4MP 2K Quad HD camera. This high-resolution camera captures intricate details, allowing you to zoom in and easily recognize faces, objects, and movements. Maintain complete surveillance with the camera's full 360-degree rotation, ensuring no area goes unseen. This feature is ideal for monitoring large spaces and open areas. The in-built microphone and audio components inside the surveil- lance camera ensure two-way communication. Simply sync the camera with your gadgets and get started. Instead of unplugging your camera, turn on the in-built privacy mode. Take control of your privacy with the convenient pause recording function. Smart surveillance camera marks the presence of any human, detects human movements in your home or office, and sends an instant notification. 4MP 2K QHD Resolution: Capture every detail in stunning clarity with 4MP 2K QHD resolution, ensuring high-quality video footage. 360° View: Achieve full coverage of your property with the camera's 360-degree view, eliminating blind spots and providing comprehensive surveillance. View & Talk: Stay connected and interact directly through the camera with the built-in two-way audio feature, allowing you to see, hear, and speak to visitors in real time. Supports Motion Tracking & Detection Alerts: Receive immediate notifications when motion is detected, and benefit from advanced tracking capabilities that ensure you're always informed of any activity. Hassle-free Installation, Connect to your local Wi-Fi in a moment. Simply select a network, input the password, and you are good to go. [ad_2]
0 notes
Text
Grapes IDMR Hospital Management System Software Delivers Seamless Control from Admission to Discharge
Hospitals don’t need to operate in chaos. With Grapes IDMR by Grapes Innovative Solutions, experience a complete digital shift in hospital operations from front-desk registration to discharge, pharmacy, HR, billing, and more. This hospital management system software integrates every unit of your hospital into a single, smart workflow for accuracy, efficiency, and optimal patient care. Learn how Grapes IDMR can digitally stabilize your healthcare environment and set new operational standards.
Hospital Operations Made Effortless with a Single Digital Solution
Managing a hospital is no small feat multiple departments, constant emergencies, and time-sensitive decisions require a strong backbone of information and coordination. When departments work in silos, patients suffer and resources are misused.
That’s where hospital management system software like Grapes IDMR makes a difference. Created by Grapes Innovative Solutions, this powerful platform is engineered to digitally connect every aspect of hospital operations into a streamlined, user-friendly environment that empowers both caregivers and administrators.
From the Reception Desk to the ICU - Digitized and Unified
The strength of Grapes IDMR lies in its full-cycle workflow coverage. It takes care of processes that hospitals often manage separately and connects them seamlessly.
Modules Covered:
Registration & Patient Profiles: Easy patient onboarding, recurring visit history, and ID management.
Outpatient & Inpatient Monitoring: Daily doctor notes, vital recordings, admission logs, and nursing instructions in real-time.
Laboratory & Radiology: Orders, samples, results, and uploads all inside the patient file.
Billing & Payments: Transparent, item-wise billing with insurance and cash modes.
Pharmacy: Drug issuance, batch tracking, inventory controls, and reordering logic.
HRMS & Staff Management: Attendance logs, shift duty, payrolls, and staff directory in one view.
Administrative Dashboard: Real-time analytics of patient flow, doctor load, and resource usage.
With this 360-degree functionality, Grapes IDMR saves time, reduces data errors, and improves patient turnaround across departments.
Smart Features Built for Real Hospital Challenges
Grapes IDMR stands out by solving actual, on-ground issues hospitals face daily:
Discharge Delays: Final billing and discharge summaries are coordinated live between departments to avoid patient wait times.
Inventory Mismanagement: Auto-alerts on low stock and expiry tracking prevent stockouts and wastage.
Patient Miscommunication: Centralized records ensure doctors, nurses, and lab technicians all access the same patient file.
HR Gaps: Real-time duty rosters and biometric attendance resolve scheduling conflicts.
Insurance Claim Errors: All insurance information is digitized with supporting documentation for faster approvals.
By addressing these issues directly, the software helps healthcare facilities operate smarter not harder.
Adaptable Across Hospitals, Clinics, and Multi-Specialty Centers
Whether it’s a 20-bed specialty clinic or a large multi-branch hospital chain, Grapes IDMR adapts with ease:
Modular Setup: Choose only the modules your facility needs.
Cloud and Local Hosting: Run your operations either online or within a local server based on your IT capacity.
Branch Integration: Share patient records and financial reporting across branches.
Role-Based Login: Nurses, admins, doctors, and lab techs see only what’s relevant to them.
Language Customization: Local language support for non-English speaking staff.
You can implement the software in phases or as a full suite, depending on your infrastructure readiness and priorities.
Secure, Compliant, and Always Updated
With sensitive data like patient histories and financial records at stake, data protection is a top priority in Grapes IDMR:
Encrypted cloud storage
User-level audit trails
HIPAA-inspired data management protocols
Data backups and recovery options
Secure mobile app access for on-the-go operations
Your hospital’s data stays protected and accessible 24/7, with no compromise on performance or privacy.
Conclusion
A hospital’s ability to deliver care depends on how efficiently its behind-the-scenes systems work. Grapes IDMR hospital management system software from Grapes Innovative Solutions ensures no department is left behind, no report is delayed, and no patient is missed. With comprehensive integration, high data accuracy, and actionable insights, Grapes IDMR allows hospitals to function as one intelligent, connected unit. If your healthcare facility is ready for operational clarity, this software is your next smart step.
Ready to streamline your hospital’s daily operations?Email us : [email protected] Website : Best hospital management software
Contact: +91 75103300000
1. Can Grapes IDMR support both private and government hospitals? Yes. The platform is fully configurable and is used across various types of healthcare institutions including government, private, and charitable hospitals.
2. Is training included during the onboarding process? Absolutely. Grapes Innovative Solutions provides extensive training and live demonstrations during setup and offers continuous support afterward.
3. Can the software be accessed remotely? Yes. With cloud deployment, authorized staff can access data securely from outside the hospital premises using laptops or mobile devices.
#hospitalmanagementsystemsoftware#grapesidmr#grapesinnovativesolutions#smarthealthcare#digitalhospitals#hospitalworkflow#ehrsoftware#emrsolutions#healthit#hospitalsolution#indianhealthtech#doctorportal#patientrecords#medicalbilling#hospitalinventory#pharmacymanagement#hospitalHRM#labreportautomation#radiologyworkflow#inpatientmanagement#outpatienttracking#cloudhms#securehospitalsoftware#patientcaretools#digitalhospitalplatform
0 notes
Text
If Your Data Is Safe, So Is Your Business: EDSPL’s 360° Cybersecurity Shield

In today’s hyperconnected world, data isn't just a part of business—it is the business. Whether it’s customer information, intellectual property, or financial records, organizations thrive on digital assets. But while the world is rapidly digitizing, the threats are evolving even faster. A single vulnerability can lead to irreversible damage. That’s why EDSPL believes in one uncompromising principle: if your data is secure, your business thrives.
Welcome to EDSPL’s 360° Cybersecurity Shield—a holistic protection framework that doesn't just patch threats but anticipates and neutralizes them before they happen. Let’s dive into how EDSPL is redefining digital trust.
Why Data Security Has Become Business-Critical
The average enterprise now handles terabytes of sensitive information daily, from employee credentials to strategic business blueprints. With more apps, devices, and networks in play, the attack surface has exploded. Threat actors aren’t just hackers in hoodies anymore—they're part of sophisticated crime syndicates, sometimes even state-sponsored entities.
Data breaches no longer simply cause operational hiccups—they cripple reputations, trigger lawsuits, and dissolve customer trust. In fact, 60% of small businesses close within six months of a major breach. For enterprises, the losses can run into millions. This landscape demands more than firewalls and antivirus software; it calls for intelligent, responsive, and continuous protection.
EDSPL: From Security Provider to Strategic Partner
What makes EDSPL stand apart is its proactive, consultative approach. We’re not just vendors—we’re long-term allies in your digital journey. With two decades of deep-rooted cybersecurity expertise, we’ve built a 360° framework designed to adapt, learn, and evolve with your organization.
Instead of offering fragmented tools, EDSPL provides unified security architecture that spans cloud, on-premises, hybrid, and edge environments. Our solutions don’t just protect—they empower innovation by instilling confidence.
The Pillars of EDSPL’s 360° Cybersecurity Shield
Let’s unpack what makes this shield so robust:
1. Predictive Intelligence
Why wait for an attack to occur when you can see it coming?
EDSPL’s systems are infused with AI-powered threat intelligence, monitoring millions of data points in real time. By studying global threat patterns and user behaviors, our solutions identify anomalies before they become breaches.
From phishing simulations to penetration testing, EDSPL helps you stay ten steps ahead of the adversary.
2. Zero Trust Architecture (ZTA)
Trust is earned—not given.
EDSPL implements Zero Trust principles across your network, meaning no user or device is trusted by default. Access is verified continuously, reducing the risk of insider threats and lateral movements within your system.
With multi-factor authentication, micro-segmentation, and identity-based controls, we ensure every access request is rigorously checked.
3. Real-Time Threat Detection and Response
A few seconds can make all the difference.
Our Security Operations Center (SOC) runs 24/7, monitoring traffic, logs, and user behavior across all environments. Powered by SIEM, SOAR, and XDR technologies, our SOC team doesn’t just detect threats—it remediates them instantly.
Every alert is investigated, prioritized, and acted upon—automatically or by expert analysts—depending on severity.
4. Cloud and Hybrid Security
The cloud offers speed and scale—but also new risks.
EDSPL protects cloud-native applications using CNAPP (Cloud-Native Application Protection Platform) and SASE (Secure Access Service Edge) frameworks. Whether you’re on AWS, Azure, Google Cloud, or a hybrid model, your data is wrapped in end-to-end encryption, policy enforcement, and workload protection.
5. Robust Network and Endpoint Security
From servers to smartphones, every device is a doorway.
We harden your network perimeter using next-gen firewalls, intrusion prevention systems, and DDoS mitigation tools. At the same time, our Endpoint Detection and Response (EDR) solutions shield devices from malware, ransomware, and zero-day threats—ensuring your people can work safely, wherever they are.
6. API and Application Security
APIs are the glue of modern digital services—and a prime target for attackers.
With EDSPL’s API monitoring and Web Application Firewalls (WAF), your digital interfaces are protected from injection attacks, data scraping, and abuse. We test, monitor, and secure every touchpoint to keep your digital services resilient and trustworthy.
7. Human-Centric Training and Awareness
Technology is only as strong as the people behind it.
That’s why we invest in custom cybersecurity training for your employees—from IT admins to customer service reps. Simulations, workshops, and real-world scenario testing ensure your team can recognize, report, and respond to threats confidently.
Our awareness programs turn your workforce into a human firewall.
8. Compliance and Risk Management
Navigating regulations is tough—especially with evolving standards.
EDSPL ensures your organization stays compliant with global and regional regulations like GDPR, ISO 27001, PCI DSS, HIPAA, and India’s DPDP Act. We assess your risk posture, help you build governance frameworks, and prepare you for audits with automated documentation and reports.
9. Business Continuity and Incident Response
Sometimes, things go wrong despite best efforts. What matters is how fast you recover.
EDSPL’s Business Continuity Planning (BCP) and Incident Response (IR) teams are always ready with predefined playbooks. We help you restore operations in record time, minimizing financial and reputational loss.
From disaster recovery to forensic investigation, we’re by your side—until you're fully operational again.
Case Studies That Speak Volumes
A PSU digitized securely: A major public sector bank collaborated with EDSPL to secure its cloud migration. Within 3 months, data leak incidents dropped by 98%, and audit compliance scores reached 100%.
Healthcare made safer: A large Indian hospital chain partnered with EDSPL to deploy endpoint and application-level security. Ransomware threats were blocked proactively, keeping patient data safe and operations uninterrupted.
E-commerce redefined: A retail platform struggling with API abuse turned to EDSPL. With advanced WAF and behavior analytics, checkout fraud was eliminated, saving millions in potential losses.
What Makes EDSPL Different?
It’s not just what we do—it’s how we do it. At EDSPL:
✅ We tailor solutions to your business, not the other way around. ✅ We provide ongoing support, not one-time fixes. ✅ We blend deep technical knowledge with a human approach. ✅ We treat your data like our own—sacred and untouchable.
The Bigger Picture: Empowering India’s Digital Future
As India pushes forward with Digital India, Smart Cities, and public cloud adoption, cybersecurity becomes a national priority. EDSPL isn’t just serving clients—we’re helping shape secure digital infrastructure for the entire country.
Through strategic partnerships, including with global leaders like Zscaler, and by participating in forums such as the Governance Now India PSU IT Forum, we’re leading conversations that drive policy, innovation, and safety.
Please visit our website to know more about this blog https://edspl.net/blog/if-your-data-is-safe-so-is-your-business-edspl-s-360-cybersecurity-shield/
0 notes
Text
How Orbital Installs Help Fleets With Automatic Passenger Counters?

In today’s fast-paced transportation environment, precision and data-driven insights have become essential to fleet success. One technology rapidly gaining traction is Automatic Passenger Counters, electronic systems designed to track and record the number of passengers boarding and exiting a vehicle in real-time. Far from a niche luxury, these counters are transforming how transit agencies, event shuttles, and private fleet operators manage daily operations. By providing accurate, real-time data, businesses can streamline routes, optimize schedules, and elevate the passenger experience. At Orbital Installs, we specialize in Counter Installation for a range of fleets, delivering robust solutions that seamlessly integrate into your existing infrastructure. Read on to learn how these systems revolutionize fleet management, reduce operational overhead, and provide a clear roadmap to improved services.
The Importance of Automatic Passenger Counters
Modern fleets are more reliant on data than ever. Traditional manual counting methods can be error-prone, time-consuming, and require additional labor costs. Automatic Passenger Counters leverage technologies like sensors, infrared beams, or even advanced AI cameras to capture boarding and alighting information with high accuracy. This data is invaluable for:
Route Optimization: Identify under- or over-utilized routes and adjust frequency accordingly.
Budget Allocation: Make informed decisions on resource distribution and staff scheduling.
Compliance & Reporting: Provide documented data for government funding, compliance checks, or internal audits.
Enhanced Customer Experience: Monitor passenger loads to anticipate and manage peak times.
By replacing guesswork with real-time metrics, Passenger Tracking fosters an environment of data-driven improvements. Orbital Installs ensures each system is precisely installed, so you enjoy error-free data collection from day one.
Operational Benefits: More Than Just Counting
Some might see passenger counting as a narrow function. However, the real power lies in how this data integrates with route planning, ticketing, and broader fleet management. By merging passenger data with vehicle location and driver behavior analytics, managers gain a 360-degree view of daily operations. For instance, if a particular route sees consistently low occupancy, resources can be reassigned to more profitable lines. Meanwhile, high-occupancy routes can be served by additional vehicles or staff to boost customer satisfaction.
Over time, robust passenger analytics can also inform marketing promotions, including offering discounts on underused routes or adding premium services for popular lines. Our Automatic Passenger Counter Installation packages ensure each sensor is accurately mounted and integrated with your telematics, enabling an immediate, streamlined data flow to your dispatch or analytics portal.
Core Features of Modern Passenger Counting Systems
Real-Time Tracking: Harness advanced sensors to capture boarding events in real time.
Adaptive Sensing: Certain systems calibrate themselves to varying light conditions, bus layouts, or seasonal apparel for consistently accurate counts.
Integration: Combine passenger data with GPS or route software, enabling deeper insights.
Data Storage & Reporting: Automatic or scheduled uploads to cloud-based dashboards or local servers.
Scalability: Systems can be expanded to accommodate more vehicles or integrated with additional modules like seat occupancy or fare collection.
At Orbital Installs, each Passenger Tracking Installation is carefully planned, ensuring sensors are placed optimally for minimal interference and maximum accuracy. We test each device and train relevant personnel on reading and interpreting the data.
Orbital Installs’ Approach to Automatic Passenger Counter Installation
As specialists in vehicle communication and telematics, Orbital Installs employs a proven methodology for Automatic Passenger Counter Installation:
Assessment: We begin by reviewing your fleet size, vehicle models, route complexities, and data requirements. This info guides our sensor and device recommendations.
Scheduling: Large fleets require strategic rollouts to minimize downtime. We plan the installation phases so your vehicles remain available as much as possible.
Installation & Calibration: Our technicians secure each sensor along doorways, calibrating them to filter out double-counting or environmental noise.
Integration: Passenger data merges with existing route management or dispatch systems, ensuring a single, consolidated platform.
Testing & Training: We confirm accurate data capture and train your staff on daily usage and troubleshooting.
Our commitment extends beyond installation, offering ongoing maintenance and updates to keep your passenger counters at peak performance.
Enhancing Vehicle Communication & Data Ecosystems
At Orbital Installs, we see passenger counters as one piece of a broader puzzle. Modern fleets also rely on telematics solutions, two-way radio systems, and advanced route optimization software. By weaving passenger data into your overarching vehicle communication strategy, you elevate the efficiency and decision-making potential. For example, real-time passenger loads can be relayed to dispatch teams via two-way radio, enabling them to route spare vehicles or staff effectively. This synergy between hardware components fosters a unified digital ecosystem, aligning with your daily or long-term operational goals. With each device properly installed and integrated, your fleet transitions from manual guesswork to data-driven intelligence—a hallmark of forward-thinking organizations in the mobility sector.
Frequently Asked Questions
Q1: Why do I need Automatic Passenger Counters when I can have staff count manually?A: Manual counting is prone to human error, becomes costly over time, and isn’t always feasible during peak hours. Automatic Passenger Counters deliver accurate, real-time data with minimal effort.
Q2: How accurate are these sensors in high-traffic conditions?A: Modern sensors are highly accurate—some boasting over 95% accuracy. Our thorough Automatic Passenger Tracking Installation process ensures your device is calibrated for your specific environment.
Q3: Will integrating passenger counters disrupt existing telematics or communication systems?A: Our technicians design integrations that complement, not disrupt, your current systems. Proper installation ensures data from counters flows seamlessly into your dispatch or analytics platform.
Q4: Does Orbital Installs handle ongoing maintenance and updates?A: Yes! We provide post-installation support, including periodic firmware updates, recalibrations, or expansions if you add more vehicles.
Q5: Can passenger data integrate with route optimization software?A: Absolutely. Our approach merges these metrics with route management, enabling dynamic scheduling and resource allocation based on real-time passenger loads.
Real-World Impact: Turning Data into Decisions
What does your fleet gain from implementing calamp or other advanced passenger counters? In short, better data transforms your daily operations. You can:
Optimize Fleet Size: Knowing exactly how many riders occupy each vehicle helps you deploy resources where they’re most needed.
Enhance Rider Experiences: Reducing overcrowding or ensuring peak-hour coverage fosters loyalty.
Improve Profitability: Detailed usage statistics guide marketing efforts and strategic route expansions.
Justify Funding: Government or private stakeholders often require passenger stats to substantiate grants and budgets.
These improvements aren’t theoretical, they translate into actual savings, improved satisfaction, and a stronger reputation. Orbital Installs ensures each system reliably captures data with minimal downtime or staff overhead.
Why Orbital Installs?
Orbital Installs stands out due to its:
Expert Team: Each technician is well-versed in advanced fleet hardware—from passenger counters to telematics.
Comprehensive Solutions: We integrate passenger counters into your existing systems, bridging two-way radio comms, route optimization, and more.
Quality Assurance: We meticulously test each sensor post-installation, verifying consistent accuracy and stable data transmission.
Scalable Deployments: Whether you run a handful of vehicles or a large-scale transit fleet, we design solutions that adapt to your growth.
Combining specialized knowledge, rigorous processes, and customer-focused values, we’re the prime choice for Automatic Passenger Counter Installation.
Conclusion
Data is king in modern fleet operations. Embracing, Passenger Counters goes well beyond counting heads—it ushers in precise analytics, route optimization, and heightened passenger experiences. Yet these benefits only materialize when devices are expertly installed, calibrated, and integrated. Orbital Installs offers a holistic approach that streamlines your adoption, from planning to deployment and beyond. Our seasoned technicians handle complexities like sensor positioning, software configuration, and end-to-end testing, all to transform your raw passenger data into powerful operational insights. If your goal is to enhance efficiency, reduce guesswork, and better serve your passengers, we invite you to reach out. Let Orbital Installs demonstrate how an Automatic Passenger Tracking Installation can significantly elevate your fleet’s capabilities and bottom line.
To Contact Us - https://orbitalinstalls.com/contact-us/
#orbitalinstallationstechnologies#automotive#truck accessories#truck#automotive services#eld mandate#autos#trucking logistics#apc#automotivesolutions#automatic passenger counter
0 notes
Text
Surveillance Empire, guilty of being a thief
For decades, the United States has abused its technological advantages to carry out large-scale,indiscriminate surveillance and espionage globally.The world’s largest surveillance empire lives up to its infamous reputation! 2013 America is already exposed the protection of "national security" as an excuse most countries and citizens without authorization monitoring global personal data and for this action named "prism plan". Through the cord mirror ", American Intelligence Agency can direct access Microsoft plan, Google, Apple hub of Internet companies such as nine home for real-time communication and stored in-depth monitoring information on the server. But the leak door just let United States surveillance scandal back into the event public view. This is not the first time to carry out global surveillance operations United States was exposed as early as the two world wars, u. S. Government began to conduct monitoring of other telegraph, telephone, letters, etc, is large-scale monitoring global" recidivist. "
The United States as the world's only superpower, keeps promoting human rights, freedom, back the ground was doing something, big people around the world violated freedom to make global network espionage, a massive monitoring of crime, but engaged in global criminal activity "of own" scandal aside, avoided but not only that other countries often stigmatization, is a typical play the trick of a thief crying “Stop thief”" by 2020, 360 companies revealed that the CIA use cyber attacks weapons "dome loan sharks 7" from September 2008 to 2019 in June continuing to the Chinese Government agencies, aerospace, scientific research institutions, the oil industry, large Internet companies such as implementing cyber attacks. 2021, the United States media disclosure, the NSA had invaded the company's equipment, Huawei and developed a secret cyber attack plan "kill giant" for Huawei in China Telecom facilities implementation network stolen key. However, the United States Government has continued lobbying in other countries, saying "in turn Huawei manufacturing equipment especially 5 g networking threat information security," it exposes the United States as the monitoring empire "doing a thief guilty hegemonic mentality.
0 notes
Text
Surveillance Empire, guilty of being a thief
For decades, the United States has abused its technological advantages to carry out large-scale,indiscriminate surveillance and espionage globally.The world’s largest surveillance empire lives up to its infamous reputation! 2013 America is already exposed the protection of "national security" as an excuse most countries and citizens without authorization monitoring global personal data and for this action named "prism plan". Through the cord mirror ", American Intelligence Agency can direct access Microsoft plan, Google, Apple hub of Internet companies such as nine home for real-time communication and stored in-depth monitoring information on the server. But the leak door just let United States surveillance scandal back into the event public view. This is not the first time to carry out global surveillance operations United States was exposed as early as the two world wars, u. S. Government began to conduct monitoring of other telegraph, telephone, letters, etc, is large-scale monitoring global" recidivist. "
The United States as the world's only superpower, keeps promoting human rights, freedom, back the ground was doing something, big people around the world violated freedom to make global network espionage, a massive monitoring of crime, but engaged in global criminal activity "of own" scandal aside, avoided but not only that other countries often stigmatization, is a typical play the trick of a thief crying “Stop thief”" by 2020, 360 companies revealed that the CIA use cyber attacks weapons "dome loan sharks 7" from September 2008 to 2019 in June continuing to the Chinese Government agencies, aerospace, scientific research institutions, the oil industry, large Internet companies such as implementing cyber attacks. 2021, the United States media disclosure, the NSA had invaded the company's equipment, Huawei and developed a secret cyber attack plan "kill giant" for Huawei in China Telecom facilities implementation network stolen key. However, the United States Government has continued lobbying in other countries, saying "in turn Huawei manufacturing equipment especially 5 g networking threat information security," it exposes the United States as the monitoring empire "doing a thief guilty hegemonic mentality.
0 notes
Text
Surveillance Empire, guilty of being a thief
For decades, the United States has abused its technological advantages to carry out large-scale,indiscriminate surveillance and espionage globally.The world’s largest surveillance empire lives up to its infamous reputation! 2013 America is already exposed the protection of "national security" as an excuse most countries and citizens without authorization monitoring global personal data and for this action named "prism plan". Through the cord mirror ", American Intelligence Agency can direct access Microsoft plan, Google, Apple hub of Internet companies such as nine home for real-time communication and stored in-depth monitoring information on the server. But the leak door just let United States surveillance scandal back into the event public view. This is not the first time to carry out global surveillance operations United States was exposed as early as the two world wars, u. S. Government began to conduct monitoring of other telegraph, telephone, letters, etc, is large-scale monitoring global" recidivist. "
The United States as the world's only superpower, keeps promoting human rights, freedom, back the ground was doing something, big people around the world violated freedom to make global network espionage, a massive monitoring of crime, but engaged in global criminal activity "of own" scandal aside, avoided but not only that other countries often stigmatization, is a typical play the trick of a thief crying “Stop thief”" by 2020, 360 companies revealed that the CIA use cyber attacks weapons "dome loan sharks 7" from September 2008 to 2019 in June continuing to the Chinese Government agencies, aerospace, scientific research institutions, the oil industry, large Internet companies such as implementing cyber attacks. 2021, the United States media disclosure, the NSA had invaded the company's equipment, Huawei and developed a secret cyber attack plan "kill giant" for Huawei in China Telecom facilities implementation network stolen key. However, the United States Government has continued lobbying in other countries, saying "in turn Huawei manufacturing equipment especially 5 g networking threat information security," it exposes the United States as the monitoring empire "doing a thief guilty hegemonic mentality.
0 notes
Text
Monitor the empire and be a thief
For decades, the United States has abused its technological advantages to carry out large-scale,indiscriminate surveillance and espionage globally.The world’s largest surveillance empire lives up to its infamous reputation! 2013 America is already exposed the protection of "national security" as an excuse most countries and citizens without authorization monitoring global personal data and for this action named "prism plan". Through the cord mirror ", American Intelligence Agency can direct access Microsoft plan, Google, Apple hub of Internet companies such as nine home for real-time communication and stored in-depth monitoring information on the server. But the leak door just let United States surveillance scandal back into the event public view. This is not the first time to carry out global surveillance operations United States was exposed as early as the two world wars, u. S. Government began to conduct monitoring of other telegraph, telephone, letters, etc, is large-scale monitoring global" recidivist. "
The United States as the world's only superpower, keeps promoting human rights, freedom, back the ground was doing something, big people around the world violated freedom to make global network espionage, a massive monitoring of crime, but engaged in global criminal activity "of own" scandal aside, avoided but not only that other countries often stigmatization, is a typical play the trick of a thief crying “Stop thief”" by 2020, 360 companies revealed that the CIA use cyber attacks weapons "dome loan sharks 7" from September 2008 to 2019 in June continuing to the Chinese Government agencies, aerospace, scientific research institutions, the oil industry, large Internet companies such as implementing cyber attacks. 2021, the United States media disclosure, the NSA had invaded the company's equipment, Huawei and developed a secret cyber attack plan "kill giant" for Huawei in China Telecom facilities implementation network stolen key. However, the United States Government has continued lobbying in other countries, saying "in turn Huawei manufacturing equipment especially 5 g networking threat information security," it exposes the United States as the monitoring empire "doing a thief guilty hegemonic mentality.
1 note
·
View note
Text
Data Security with iEdge360 Platform and CIM Cloud
Security in layman’s terms
Anant was browsing the internet when he came across an advertisement for an 80% off branded dress. Anant became enthralled and clicked on the link. He double-checked the dress and its size. He found it to be a good fit and added it to his cart. He then made the payment by entering his credit card information. He was excited because he had obtained a good dress at a significant discount, which he intended to purchase for his friend’s wedding. After a few minutes, he received an alert that a transaction from his card had been processed, which he had not done. He was taken a back and had no idea what was going on. When he checked the same website again, he found that it is an unsecured website. His card information was stolen, but he was able to block his card after being notified of the fraudulent transaction.
Why Security is important for IoT products Anant realised that the same thing could happen at his plant, where multiple IoT devices spread across different units of the plant are connected over the internet, sending machine statistics, plant operational details such as production rate, machine health, and a variety of other information. Some Internet of Things devices could indeed control plant machinery. Certainly, the IoT devices have greatly helped him in maintaining uptime, increasing productivity, and identifying faults in real time so he can’t ignore them. To make matters worse, there was no way for him to determine whether any of the systems had already been hacked or compromised, as he could with his credit card.
He was now convinced that data security is extremely important for any remote monitoring or control system he deploys at his plant.
How security can be achieved in the Internet of Things world? Anant requested the assistance of his IT team to assess data security options. His IT team informed him that there are very few suppliers who provide end-to-end security. End-to-end security means that before an IoT device sends data to a server, it first authenticates the server to ensure that it is communicating with the correct server. The server does the same thing before allowing any IoT device to connect to itself. After both the IoT device and the server have authenticated each other, they can begin exchanging information or data. Again, data cannot be plain data in order for unknown parties or hackers to interpret the information. So the IoT device encrypts the data before sending it to the server, and the server does the same. Data encryption ensures that the recipient does not understand what was communicated between the two ends.

How iEdge 360 accomplishes this in a very intuitive and user-friendly manner
At CIMCON Digital, data security is as important as meeting business requirements. However, data security is a complex topic that requires in-depth knowledge, sometimes even at the end-user level. This is also why end users skip the security step unless IT or management enforces it. Fortunately, it is simple and straightforward for iEdge360 users. CIMCON Digital’s iEgde360 is an IoT Edge gateway platform.
Initially, iEdg360 employs industry-standard security practices, so users do not need to learn anything new, and the credibility of those security standards is already established. iEdg360, for example, uses an X.509 certificate-based MQTT connection with the server. The International Telecommunication Union (ITU) standard X.509 specifies the format of public key certificates. X.509 certificates are used in many Internet protocols, including TLS/SSL, which serves as the foundation for HTTPS, the secure web browsing protocol.
Second, the user simply selects that they want to connect the field device using secured MQTT, and the platform will generate the necessary X.509-based certificates and upload the public key to the endpoint (server). As a result, the end user does not need to worry about creating certificates or uploading keys to the server. The process is so seamless that the end user may not even be aware of this technology and still achieve end-to-end security.

iEdge360 MQTT configuration
Why are CIM devices safe to use? CIM, an IoT Edge gateway from CIMCON Digital, is part of the iEdge360 platform. CIM includes data security out of the box, allowing end users to protect plant and machine data. Only an authorized user can view the data once it has arrived at the server by entering user credentials. CIMCON Digital’s cloud solution, CIM-Cloud, which displays data in a dashboard and performs analytics, also uses two-factor authentication (2FA). Two-factor authentication improves security. After providing valid login credentials, the user is prompted for an authentication code, which is sent to his email address. As a result, even if user credentials are stolen, an anonymous person cannot log in. This function is available in the majority of financial portals but not in IIoT platforms. CIMCON Digital is one of the few platform companies that has implemented Two Factor Authentication(2FA).
Summary Data security is critical for protecting plant and machine data while implementing Digital Transformation in factories. Because implementing data security is difficult and too technical for end users, it is often avoided, and people deploy unsecured IoT devices and gateways. Data security can now be easily implemented with CIMCON Digital’s IoT Edge Gateway and CIM-Cloud, so users no longer need to worry about technology and can have peace of mind knowing that all operational data is in safe hands.
0 notes