#Access Control Solutions
Explore tagged Tumblr posts
Text
How Biometric Devices Improve Employee Time Tracking
In an era where organizations strive for efficiency, accuracy, and security, managing employee attendance has evolved from traditional punch cards and manual logbooks to high-tech solutions. Among the most transformative innovations is the biometric device, a software that has revolutionized how companies track and manage employee time.
Whether you're a small business or a large enterprise, ensuring accurate time tracking is essential for payroll, productivity, and workforce management. Biometric devices offer a modern solution by linking attendance to unique human characteristics such as fingerprints, facial recognition, or iris scans - making time fraud and buddy punching things of the past.

What Is a Biometric Device?
A biometric device is a piece of hardware used to identify individuals based on unique biological traits. In the context of workplace management, these devices are typically deployed for access control and attendance tracking. Unlike traditional systems that require ID cards or PINs, biometric systems ensure that only the actual individual can clock in or access a restricted area.
Biometric devices can come in various forms:
Fingerprint scanners
Facial recognition systems
Iris recognition devices
Voice recognition tools
The growing popularity of biometric technology is due to its speed, accuracy, and ease of integration with other HR and payroll systems.
Common Problems with Traditional Time Tracking Methods
Before diving into how biometric devices improve employee time tracking, it’s worth understanding the limitations of traditional systems:
Buddy punching: Employees clock in or out for each other, leading to time theft.
Manual errors: Human oversight when entering or correcting data can lead to payroll discrepancies.
Lost or stolen access cards: These can pose both a security and operational risk.
Lack of real-time data: Delayed updates make it difficult to monitor workforce performance.
These challenges not only impact payroll accuracy but also affect overall productivity and morale.
How Biometric Devices Transform Time Tracking
1. Accuracy and Reliability
Biometric devices are incredibly accurate. Because they rely on individual traits that cannot be duplicated or shared, they offer reliable verification each time an employee clocks in or out. This eliminates common issues like buddy punching or fraudulent time logging.
For instance, a facial recognition-based biometric device ensures that only the authorized individual can record attendance. This means more accurate payroll processing and fewer disputes between HR and employees.
2. Real-Time Attendance Monitoring
Biometric systems provide real-time data on employee attendance. This allows HR departments and team managers to monitor punctuality, break times, and absenteeism more effectively. Cloud-based biometric devices like those offered by Spintly offer real-time syncing across multiple locations, perfect for businesses with distributed teams or multiple branches.
This live data can be accessed through dashboards and reports, offering actionable insights that go beyond mere attendance tracking.
3. Integration with Payroll and HRMS
A modern biometric device does more than log time. Many advanced systems integrate seamlessly with Human Resource Management Systems (HRMS) and payroll software. This eliminates the need for manual data entry, ensuring timely and accurate salary processing, tax compliance, and leave management.
Solutions like Spintly’s biometric access control and attendance management platforms are built with open APIs, making it easy to integrate with third-party software - resulting in a streamlined workflow and reduced administrative burden.
4. Improved Compliance and Audit Trail
Maintaining proper records of working hours is essential to comply with labor laws and industry standards. Biometric devices automatically log every time an employee enters or exits the workplace, providing a secure and tamper-proof audit trail.
This data becomes especially useful during labor audits or legal disputes, ensuring organizations remain compliant without having to dig through manual records.
5. Contactless and Hygienic Options
In the post-pandemic world, hygiene has become a critical consideration in workplace technology. Modern biometric devices now offer touchless options, such as facial recognition and mobile-based check-ins, which minimize physical contact.
Cloud-enabled platforms like Spintly even offer mobile-based biometric attendance solutions, where employees can check in via their smartphones - reducing shared touchpoints while maintaining strict security protocols.
Industry Use Cases
1. Corporate Offices
Biometric time tracking helps monitor in-office attendance while integrating with access control systems to manage entry permissions.
2. Manufacturing & Industrial Units
These devices ensure workers clock in accurately despite working in high-volume shifts, often across different parts of the plant.
3. Healthcare Institutions
Hospitals benefit from biometric tracking to maintain 24/7 shift records and manage attendance in a critical-care environment where staffing is essential.
4. Educational Institutions
Schools and colleges use biometric devices to track faculty and staff attendance while maintaining secure access to restricted areas.
Advantages Over RFID and PIN Systems
While RFID cards and PINs offer basic functionality, they’re prone to misuse and loss. A biometric device offers a level of certainty and convenience that traditional systems can't match. Employees can’t forget or lose their fingerprint or face, making the system more dependable and reducing the cost and hassle of replacements.
Furthermore, combining biometric devices with access control solutions, such as those provided by Spintly, enhances building security. The system ensures that only verified individuals gain access to sensitive areas, creating a safer workplace.
Key Features to Look for in a Biometric Device
If you're considering investing in a biometric time tracking solution, keep the following features in mind:
Cloud connectivity for remote access and real-time syncing
Integration capabilities with HRMS and payroll systems
Touchless operation for post-COVID hygiene standards
Mobile authentication for flexible, remote check-ins
Data encryption to protect biometric data and ensure compliance
Providers like Spintly are paving the way for secure, scalable, and easy-to-deploy biometric solutions that fit businesses of all sizes.
Conclusion
In a digital-first world, managing your workforce with accuracy and efficiency isn’t just about technology - it’s about trust, compliance, and operational excellence. A biometric device simplifies employee time tracking while eliminating common pitfalls like buddy punching, manual errors, and data delays.
By integrating biometric attendance with access control and cloud-based dashboards, organizations get a holistic view of employee movement and performance. Solutions such as Spintly’s smart biometric access platform are leading this transformation by offering sleek, wireless systems that combine convenience with security.
Whether you're looking to tighten security, reduce administrative overhead, or simply improve the employee experience, adopting a biometric solution could be the smartest investment your business makes this year.
#biometric machine#biometric attendance#biometric access#mobile access#attendance management#time and attendance software#accesscontrol#spintly#smartacess#biometrics#smartbuilding#visitor management system#access control solutions
0 notes
Text
https://www.cybergroup.in/access-control-system/
Advanced Access Control Solutions for Secure Premises – Cybergroup
Cybergroup offers cutting-edge Access Control Solutions to enhance security and streamline entry management. From biometric systems to RFID and smart card readers, our tailored solutions ensure only authorized access to your facility.
#Access Control Solutions#Access Control System Provider#Access Control System Vendors#Access Control System Manufacturers
0 notes
Text
Broken Access Control in Symfony: Secure Your Routes
🚨 Broken Access Control in Symfony: How to Spot and Stop It
Broken Access Control is one of the most critical and most exploited vulnerabilities found in web applications today—and Symfony, despite its power and flexibility, is not immune to this security pitfall.

In this blog, we’ll explore how broken access control occurs in Symfony apps, give you practical coding examples, show you how to detect it using our free Website Security Checker tool, and guide you on securing your Symfony project effectively.
🔗 Also read more security posts on our main blog at: https://www.pentesttesting.com/blog/
🧨 What is Broken Access Control?
Broken Access Control occurs when users can access resources or perform actions outside their intended permissions. For example, a user accessing an admin dashboard without being an admin.
Symfony applications, if not properly configured, may be prone to:
Privilege Escalation
Insecure Direct Object References (IDOR)
Forced Browsing
🔍 Real-Life Vulnerability Scenario
Consider this route definition in a routes.yaml or annotation-based controller:
/** * @Route("/admin/dashboard", name="admin_dashboard") */ public function adminDashboard() { // Only admin should access this return new Response("Welcome to admin panel"); }
If no access control is applied, any authenticated (or sometimes even unauthenticated) user can access it by simply visiting /admin/dashboard.
🛠 How to Fix: Use Symfony Access Control
✅ Method 1: Role-Based Access Control via security.yaml
access_control: - { path: ^/admin, roles: ROLE_ADMIN }
This restricts any route starting with /admin to users with the ROLE_ADMIN.
✅ Method 2: Using Annotations
use Sensio\Bundle\FrameworkExtraBundle\Configuration\IsGranted; /** * @Route("/admin/dashboard", name="admin_dashboard") * @IsGranted("ROLE_ADMIN") */ public function adminDashboard() { return new Response("Welcome to admin panel"); }
This ensures only admins can access the route, keeping unauthorized users out.
👨💻 Vulnerable Code Example: IDOR in Symfony
/** * @Route("/user/{id}", name="user_profile") */ public function viewUser(User $user) { return $this->render('profile.html.twig', [ 'user' => $user, ]); }
Anyone could access any user's profile by changing the id in the URL. Dangerous!
✅ Secure Fix:
public function viewUser(User $user, Security $security) { if ($security->getUser() !== $user) { throw $this->createAccessDeniedException(); } return $this->render('profile.html.twig', [ 'user' => $user, ]); }
🧪 Test for Broken Access Control
You can easily check your Symfony site for broken access control vulnerabilities using our Website Vulnerability Scanner.
📸 Screenshot of our free tool webpage:

Screenshot of the free tools webpage where you can access security assessment tools.
📸 Screenshot of a vulnerability assessment report (detected broken access control):

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
Try it now for free 👉 Website Vulnerability Scanner
✅ Best Practices to Prevent Broken Access Control in Symfony
Always Define Roles and Permissions
Use Security Voters for Complex Logic
Don’t Rely on Client-side Role Checks
Implement Logging and Monitoring for Suspicious Access Attempts
Run Regular Security Audits using tools like ours
📚 Final Thoughts
Symfony gives you all the tools to build secure applications—but you need to configure them wisely. Broken access control is easy to introduce but also easy to fix when you know what to look for.
If you haven’t already, scan your site now with our free tool and find hidden access control issues before attackers do.
➡️ Check Now on https://free.pentesttesting.com/ ➡️ More security insights on our blog
#cyber security#cybersecurity#data security#pentesting#security#php#coding#symfony#access control solutions
1 note
·
View note
Text
PVC Cards vs. Traditional Paper Cards: Why Plastic is the New Standard

As technology evolves, the choices for business tools and solutions evolve too. A perfect example is the shift from traditional paper cards to PVC (Polyvinyl Chloride) plastic cards. While paper cards have been a staple for identification, membership, and payment cards, PVC plastic cards are fast emerging as the preferred option across many industries. From toll management to retail loyalty programs, plastic cards offer durability, functionality, and branding opportunities that paper cards can’t match. Here, we’ll explore why PVC cards are overtaking traditional paper options and dive into how RFID readers are revolutionizing toll management on highways and city roads, enhancing revenue collection, and reducing maintenance costs.
1. Durability and Longevity: The PVC Edge
When choosing between paper and PVC, durability is a deciding factor. PVC cards are made of sturdy plastic, and resistant to physical wear and tear, moisture, and sunlight exposure. This makes them suitable for long-term use in high-traffic areas, like toll booths and public transport. Traditional paper cards, while inexpensive, wear down quickly. Even laminated paper cards can't offer the lifespan of PVC, especially in demanding environments.
PVC’s longevity leads to fewer replacements and less downtime, saving both businesses and users time and resources. This is why businesses in the healthcare, fitness, and government sectors are leaning towards PVC for secure and sustainable solutions.
2. Enhanced Security with RFID Technology
PVC cards support RFID (Radio Frequency Identification) integration, a feature that’s transforming the way industries handle security and access control. RFID technology enables contactless transactions and identification, which has become particularly beneficial in toll management on highways and city roads. An RFID-enabled PVC card contains a chip that communicates with RFID readers to enable seamless, automated toll transactions. These RFID readers, strategically placed at toll plazas, identify and record passing vehicles without the need for physical stops, minimizing congestion and maximizing efficiency.
This security advantage extends beyond tolls. RFID-enabled PVC cards are also used in corporate access control, secure payment systems, and government-issued ID cards. In comparison, traditional paper cards lack these advanced security features, making them impractical for applications that require data security and tracking.
3. How RFID Readers Improve Toll Management
The integration of RFID readers in toll management is a prime example of how PVC cards and modern technology can streamline processes. Here’s a closer look at how RFID technology enhances toll collection:
Automated, Contactless Transactions: RFID readers at toll plazas automatically identify RFID-enabled PVC cards in vehicles, allowing drivers to pass through without stopping. This contactless system significantly reduces traffic congestion and improves the flow of vehicles on highways and city roads, making travel faster and more efficient.
Accurate Revenue Collection: RFID readers accurately track every passing vehicle, ensuring that toll fees are consistently and accurately collected. This reduces the risk of manual errors and fraud, enhancing revenue collection for city and highway toll operators.
Reduced Maintenance and Operational Costs: Automated toll collection systems require less manual oversight, cutting down on labor costs and maintenance expenses associated with traditional toll collection booths. RFID readers are also durable and designed for high-frequency use, meaning they last longer and need less frequent replacement compared to systems relying solely on manual or barcode scanning.
Environmental Benefits: By reducing the need for paper-based toll tickets and minimizing vehicle idling time at toll booths, RFID toll management systems also contribute to a decrease in fuel consumption and emissions, supporting environmental sustainability efforts on a broader scale.
In essence, RFID readers at toll plazas enable a smart, efficient, and eco-friendly approach to toll management, ensuring accurate revenue collection while providing drivers with a hassle-free experience.
4. Branding and Professional Appearance
PVC cards offer a polished, professional look, making them an excellent choice for brands that want to create a lasting impression. Businesses can customize PVC cards with brand colors, logos, and high-quality graphics, enhancing brand recognition every time a customer uses their card. This visual appeal and customization option make PVC cards ideal for loyalty programs, membership cards, and even gift cards in the retail and hospitality industries.
Paper cards, though customizable to some extent, do not retain their appearance well over time. They wear out quickly, making them look worn or faded, which can diminish the brand’s image and lead to a less-than-professional impression on clients and customers.
5. Sustainability and Eco-Friendly Options
While it may seem counterintuitive, PVC cards can be a more sustainable option than paper in specific scenarios. Since PVC cards last significantly longer than paper cards, they require less frequent replacement, reducing overall waste. Additionally, many companies now offer PVC cards made from recycled or recyclable materials, aligning with eco-conscious goals.
Conversely, paper cards might appear to be the more environmentally friendly option at first glance. However, when considering the entire lifecycle of a product, the repeated need to reissue paper cards can create more waste and increase resource consumption. For businesses with sustainability goals, durable PVC options can provide a better balance between environmental impact and long-term usability.
6. Versatility Across Industries
PVC cards are incredibly versatile, which is why they are becoming the new standard across multiple industries. In addition to their role in toll management, PVC cards are widely used in gyms, retail stores, hospitality, and government offices for identification, membership, and payment purposes. The combination of durability, customization, and technological adaptability—such as RFID integration—makes PVC a practical and multifunctional choice for any industry looking to offer a professional, efficient, and secure experience.
Conclusion: PVC Cards as the Future Standard
As industries continue to evolve and adapt to new technology, PVC cards are proving to be the standard choice for businesses that value durability, functionality, and brand appeal. For applications that require reliable security, such as toll management on busy highways and roads, the benefits of RFID-enabled PVC cards are undeniable. They facilitate a seamless, accurate, and efficient toll collection process, reducing costs and enhancing the customer experience.
For organizations across the board, whether in retail, healthcare, or transportation, PVC cards offer reliability, flexibility, and advanced features that traditional paper cards simply cannot match. As the world shifts towards smarter and more sustainable solutions, PVC cards are positioned as the future standard in card-based applications.
#rfid technology#PVC Cards#Plastic PVC Card#RFID Reader#RFID Solutions#PVC Cards Manufacturer#RFID-enabled PVC cards#RFID toll management systems#access control solutions
0 notes
Text
Khóa cổng điện tử điều khiển từ xa ( không bao gồm adapter)
Dòng khóa cổng điện tử cao cấp chuyên dụng, sử dụng cho cửa cổng các nhà máy, xí nghiệp, công ty, nhà phố, biệt thự, phòng trọ • Công nghệ Nhật Bản thông minh: - Chìa khóa cơ chống sao chép - Công nghệ tự động khóa khi đóng cửa - Động cơ khóa được sản xuất trên dây chuyền công nghệ Nhật Bản cho khả năng hoạt động bền bỉ, êm ái, không gây tiếng ồn khi hoạt động - Công nghệ RFID chống sao chép, cài đặt/xóa dễ dàng - Vỏ khóa chất liệu thép chịu lực, độ bền cao, được mạ niken bóng sang trọng - Mainboard thông minh, tích hợp được các thiết bị thông minh khác - Dễ dàng thi công lắp đặt - Dễ dàng sử dụng và quản lý người dùng • Chức năng: - Thẻ từ - Điều khiển từ xa - Chìa cơ - Có thể mở rộng thêm chức năng: wifi, vân tay, chuông cửa • Chất liệu: Thép mạ niken • Nguồn điện: DC12V • Hỗ trợ lên đến 2000 thẻ từ • Bộ khóa gồm: - Khóa điện tử 2 mặt ổ chìa cơ - 03 chìa cơ - 01 thẻ master - 01 thẻ user - Điều khiển manager - Remote điều khiển từ xa.
1 note
·
View note
Text

biometric access control system for gym
👉 Attention Gym Owners! Looking to enhance security and streamline access control at your gym? We've got you covered! For a limited time only, we're offering a special discount on sales of biometric devices tailored for gyms! ✅ Call Us:☎ 7827942625
1 note
·
View note
Text

One touch, endless possibilities. Explore Spintly’s Bluetooth biometric solutions - secure access from your phone to the front door: https://spintly.com/blog/biometrics-the-future-and-recent-trends-in-access-control/
#biometric machine#biometric attendance#biometric access#biometrics#mobile access#spintly#accesscontrol#visitor management system#access control solutions#smartbuilding#smartacess
0 notes
Text
Fix Broken Access Control in Laravel: A Guide for Developers
Broken Access Control is one of the most critical vulnerabilities listed in the OWASP Top 10. This vulnerability occurs when users can access resources or perform actions they’re not authorized to, potentially compromising sensitive data or functionality. Laravel, as a widely used PHP framework, is not immune to such risks. This blog dives into how broken access control issues manifest in Laravel applications and provides a coding example to mitigate them effectively.

Before diving into the technical details, take advantage of our tool to test website security free to detect security flaws, including broken access control, on your website.
What is Broken Access Control?
Broken Access Control arises when the application fails to enforce proper restrictions on users attempting to access restricted resources. This may lead to:
Unauthorized access to sensitive data.
Modification or deletion of data.
Privilege escalation.
Example Scenario: A regular user manipulates a URL to access an admin-only page and gains unauthorized access to critical functionalities.
Laravel and Broken Access Control
Laravel provides built-in mechanisms like middleware and policies to control access. However, misconfigurations or coding oversights can lead to vulnerabilities.
Here’s an example of a common misconfiguration:
php // Vulnerable Code Example Route::get('/admin', function () { return view('admin.dashboard'); });
In this case, any user who knows the /admin URL can access the admin dashboard, as no access control checks are in place.
How to Fix It?
Use Laravel's middleware to enforce authentication and authorization checks. Here’s an improved version of the above route:
php // Secure Code Example Route::get('/admin', function () { return view('admin.dashboard'); })->middleware(['auth', 'can:admin-access']);
auth Middleware: Ensures the user is authenticated.
can:admin-access Middleware: Confirms that the user has the appropriate role or permission.
Real-World Testing with Our Tool
To ensure your Laravel application is secure, test it using our free Website Security Scanner Tool. Below is a screenshot of the tool's interface, where you can input your website URL for a comprehensive security check.

Vulnerability Assessment Report
When you run a security check using our tool, you receive a detailed Website Vulnerability Assessment Report. This report highlights the issues found and recommends actionable steps to secure your site. Here's a sample screenshot of the report:

Preventive Tips for Laravel Developers
Always Use Middleware: Enforce authentication and authorization rules at the route level.
Leverage Policies and Gates: Use Laravel's policies and gates to define granular access controls.
Secure Sensitive URLs: Avoid exposing critical URLs unnecessarily.
Regularly Test Your Application: Use tools like our Website Security Checker to detect and fix vulnerabilities.
Conclusion
Broken access control vulnerabilities can have severe consequences, but Laravel's robust tools make it easier to implement and enforce security best practices. By securing your application and regularly testing it with tools like ours, you can protect your users and data effectively.
Want to ensure your Laravel application is fully secure? Test your site now with our Free Website Security Checker and fix vulnerabilities before they become a threat!
#cyber security#cybersecurity#data security#pentesting#security#laravel#access control solutions#access control system
1 note
·
View note
Text
Enhancing Security with Flap Barriers in Automated Entrances

Flap barriers are transforming the way we approach security and entrance automation. These modern access control solutions are designed to effectively manage and secure entry points, offering high security and convenience. Today, we'll discuss the benefits of incorporating flap barriers for automated entrances and how they regulate crowd flow.
What are Flap Barriers?
Flap barriers are sophisticated access control devices featuring retractable flaps that open and close to permit or deny entry. Constructed from durable materials such as stainless steel and reinforced glass, these barriers are built to withstand heavy use while maintaining a sleek, contemporary appearance. They are commonly used in various high-traffic settings, including office buildings, transportation hubs, and public venues.
Enhancing Security with Flap Barriers
Controlled Access
Flap barriers provide precise control over who can enter secured areas. By integrating with card readers, biometric scanners, or QR code readers, they ensure that only authorized personnel gain access. This feature is crucial for maintaining security in sensitive or restricted areas.
Real-Time Monitoring
Equipped with advanced sensors and software, modern flap barriers offer real-time monitoring and reporting capabilities. Security teams can track entry and exit activities, which enhances overall security management. This continuous oversight is essential for environments where tracking movement is critical.
Deterrence and Prevention
The presence of flap barriers serves as a strong deterrent to unauthorized individuals. Their robust and high-tech appearance discourages attempts to breach security. Additionally, the ability of these barriers to swiftly close in response to unauthorized access attempts significantly reduces the risk of security breaches.
Integration with Other Security Systems
Flap barriers can be seamlessly integrated with other security measures such as CCTV cameras, alarm systems, and building management systems. This integration allows for comprehensive security solutions, where different systems work together to provide enhanced protection and efficient monitoring.
Benefits of Using Flap Barriers
Efficiency and Speed
Designed for high-traffic environments, flap barriers operate quickly and efficiently, allowing large numbers of people to pass through quickly. This is particularly beneficial in places like metro stations, airports, and office complexes where managing crowd flow is essential.
User-Friendly Operation
Flap barriers are easy to use, offering automated operation that minimizes the need for manual intervention. This user-friendly design improves the overall experience for both employees and visitors, making entry and exit processes smooth and hassle-free.
Space-Saving Design
Compared to other access control solutions, flap barriers have a more compact footprint. They require less installation space, making them ideal for areas where space is at a premium. Their sleek and modern design also enhances the aesthetic appeal of the entry points they secure.
Durability and Low Maintenance
Constructed from high-quality materials, flap barriers are designed to endure frequent use and harsh environmental conditions. They require minimal maintenance, making them a cost-effective long-term solution for access control. Regular maintenance checks are sufficient to ensure their optimal performance.
Crowd Control
Effective crowd control is essential in high-traffic areas such as transportation hubs, stadiums, and large office buildings. Flap barriers are designed to manage crowd flow efficiently, ensuring that people move smoothly and orderly through entry points.
1. Regulating Entry and Exit
Flap barriers regulate the flow of people by allowing one person to pass at a time. This controlled entry and exit prevent overcrowding at access points, reducing the risk of accidents or bottlenecks.
2. Reducing Queues
By efficiently managing the rate at which people enter or exit an area, flap barriers help to reduce queues and waiting times. This is particularly important during peak hours when the volume of people is highest. The quick and automated operation of flap barriers ensures a steady and continuous flow, improving the overall user experience.
3. Preventing Unauthorized Access
Flap barriers' ability to allow or deny entry based on authorization helps prevent unauthorized access, which is crucial for crowd control. Unauthorized individuals cannot bypass security checks, ensuring that only those with proper credentials can enter the area. This helps in maintaining order and security in crowded environments.
4. Emergency Response
In case of emergencies, flap barriers can be programmed to open automatically, allowing for a swift evacuation. This feature ensures that people can quickly and safely exit the premises, reducing the risk of injury during emergencies. Additionally, the integration with alarm systems can trigger the barriers to open in response to a fire alarm or other emergency signals.
5. Guiding Traffic Flow
Flap barriers can be strategically placed to guide the flow of foot traffic, directing people toward specific areas and preventing congestion. This is particularly useful in large venues where directing the movement of crowds is essential for safety and efficiency.
Enhanced User Experience
Flap barriers not only provide security but also enhance the overall experience for users. The smooth and efficient operation of these barriers reduces delays and frustrations associated with manual checks and long queues. Their sleek design and automated functionality add a modern touch to entrance areas, making them more welcoming and user-friendly.
Conclusion
Flap barriers offer a robust and efficient solution for enhancing security and managing crowd flow in automated entrances. Their ability to provide controlled access, real-time monitoring, and seamless integration with other security systems makes them an invaluable asset for any organization. Whether for high-traffic public spaces, secure office buildings, or sensitive facilities, flap barriers ensure a secure, efficient, and user-friendly access control system. By choosing flap barriers, businesses can achieve a high level of security and operational efficiency, making them a smart investment for modern security needs.
#rfid technology#rfid solutions#Flap barriers#swing barriers#Entrance automation#Card readers#access control solutions#Crowd Control Management
0 notes
Text
🫂
#i've had many people ask me in the DMs what could be done to help me out given the orange menace is coming back into power#the best things for me right now (I can't speak to others) is this: 1. Keep supporting my creative endeavors#no matter how little I might post or interact. Please hype me up. I need community. I need spirit to survive.#2. Help me find resources that will help myself and others. Food banks. Community meets. Passports. Finances. Mental health etc.#these are important and I don't want others feeling like sitting ducks. Even though I'm scared I want to be a solution to the problem.#I am going to be a helper in this mess cause that's who I am and I need ammo in this capacity#3. Donate so I can up my ration storage. I've been collecting food water and nonperishables and I'm trying to stock up on medication#and other basic necessities. I'm collecting as if I'm preparing to be homeless again and if I am over capacity I'm giving rations to others#I've had to make peace with the fact I can't run away. I can't move to another country as I'm broke and poor like the rest of my loved ones#4. If you have friends who are disabled or a minority or lgbtq etc. do what you can to protect them and show them that you love them#and build community#5. Share my work and that of others. Who knows if we're gonna have sites like AO3 in the future or even access to tumblr.#this is all I can think of at the moment and again I can't speak for others this is what comes to mind for myself#And I admit I'm coming from a place of the worst case scenarios#because in my mind if I imagine I'm dead or homeless etc. and work my way backward to the next worst thing before that it unravels my fear#and it gives me back my power in the situation by sitting with those fears and giving them time to speak#because in my mind if I'm already dead if I'm already homeless or at war etc. etc. then its already happened and what else is there to fear#if I've been through everything already in mind?#I'm hoping that the worst case scenarios don't transpire but I can't ignore the fact many of them could and probably will happen#in some capacity but I can control the actions I take through prep and facing these fears one by one#and most importantly sticking to routine by making sure im healthy to help people#anyway this is why ive been quiet for a while besides for spending time with friends and loved ones recently to get over what happened#im going to keep going to my classes keep helping people through my jobs try to be creative when I have spoons and little by little#make sure I have enough of what I need to get through the storm and outlive the bastards in power#I'm not sure what sort of pink variant to assign this to but its along the magenta spectrum#love you guys#we'll get through this
6 notes
·
View notes
Text
wonder if alastor could self-delude into thinking he’s done a good thing when this whole situation was spurred on by a desire for self-preservation…
#he would not have done any of this if vox hadn’t finally managed to threaten him in a way that mattered#he actually quite enjoyed their rivalry even if he was a bit bitter about the falling out#this just seemed like the best possible solution— two birds with one stone#he gets his friend back *and* never has to worry about vox exerting control over him ever again#alastor (ram)#neutral#randomly accessed memories
4 notes
·
View notes
Text
Navigating the Digital Landscape: Unraveling the Essence of Access Management with Sigzen Technologies
In an era dominated by digital transformation, the importance of robust access management cannot be overstated. Businesses worldwide are grappling with the challenges of securing sensitive data, maintaining compliance, and providing seamless user experiences. Enter Sigzen Technologies – a trailblazer in the realm of access management, offering cutting-edge solutions to address the evolving needs…

View On WordPress
#Access Control#Access Management#Access Management Solutions#Access Management Strategies#Cybersecurity Solutions#Data Protection#Digital Landscape#Digital Security#Identity Management#IT Security#Technology Insights
2 notes
·
View notes
Text

Sevenlines Link Security Systems LLC is a leading CCTV company in Dubai, offering advanced surveillance solutions tailored to residential, commercial, and industrial needs. Recognized as one of the top CCTV companies in Dubai, we specialize in providing high-quality security camera systems that ensure round-the-clock safety. From design to deployment, our expert CCTV installers in Dubai guarantee seamless installation with minimal disruption. Our team is SIRA-approved, making us one of the trusted SIRA-approved CCTV companies in Dubai, committed to meeting all compliance and safety standards.
Beyond CCTV, Sevenlines Link excels in access control systems in Dubai, empowering businesses with secure entry management through biometric, RFID, and keypad technologies. We also deliver reliable WiFi solutions in Dubai, ideal for smart homes and offices. Our robust intercom systems in Dubai offer crystal-clear communication and secure entry management, while our comprehensive structured cabling services in Dubai ensure high-performance networks across your premises. Whether you're upgrading an existing system or starting fresh, we provide scalable and future-ready technology.
With a strong track record in system reliability and customer satisfaction, Sevenlines Link is considered the best CCTV installation company in Dubai. We provide tailored security packages along with prompt CCTV maintenance services in Dubai to ensure long-term performance. For clients seeking the best CCTV company in Dubai with a reputation for innovation and support, Sevenlines Link is the clear choice. As one of the most affordable and efficient CCTV maintenance companies in Dubai, we continue to protect what matters most—your peace of mind.
Sevenlines Technologies is a leading CCTV company in Dubai, providing cutting-edge surveillance solutions tailored for residential, commercial, and industrial clients. As one of the best CCTV installation companies in Dubai, we specialize in delivering high-definition camera systems, remote monitoring setups, and advanced security configurations to safeguard your property. Backed by a team of expert CCTV installers in Dubai, we ensure seamless setup and reliable performance, meeting both individual and business security needs.
In addition to CCTV, Sevenlines is also a trusted provider of access control systems in Dubai, helping organizations maintain secure premises through biometric, RFID, and smart card solutions. We are recognized among SIRA-approved CCTV companies in Dubai, ensuring compliance with Dubai Police security standards. Our expertise extends to CCTV maintenance services in Dubai, offering ongoing support, inspections, and system upgrades to keep your surveillance running smoothly at all times.
Expanding beyond surveillance, Sevenlines also delivers high-performance WiFi solutions in Dubai, intercom systems, and structured cabling services that form the backbone of smart, secure environments. Recognized among the top CCTV companies in Dubai, we combine advanced technology, expert integration, and responsive support to deliver unmatched value. Whether you’re searching for the best CCTV company in Dubai or a reliable partner for end-to-end IT infrastructure, Sevenlines is your go-to solution provider.
#cctv company dubai#cctv installers in dubai#access control system dubai#WiFi solutions in Dubai#best cctv company in dubai#cctv maintenance company in dubai#top cctv companies in dubai#Sira approved cctv companies in dubai#intercom system in dubai#structured cabling services in dubai#best cctv installation company in dubai
0 notes
Text
How to Integrate a Visitor Management System with Access Control
In today's fast-paced, security-conscious world, welcoming visitors into your workplace is more than just offering a friendly smile. It’s about creating a secure, seamless, and professional experience from the moment they step through your doors. That’s where the integration of a Visitor Management System with your Access Control infrastructure becomes not only valuable but essential.
As organizations adopt more advanced digital software for security and workforce management, the traditional logbook at the reception desk simply doesn’t cut it anymore. Enterprises now need smarter systems that can streamline visitor authentication, improve building security, and offer real-time visibility into who is onsite - all while delivering a positive visitor experience.
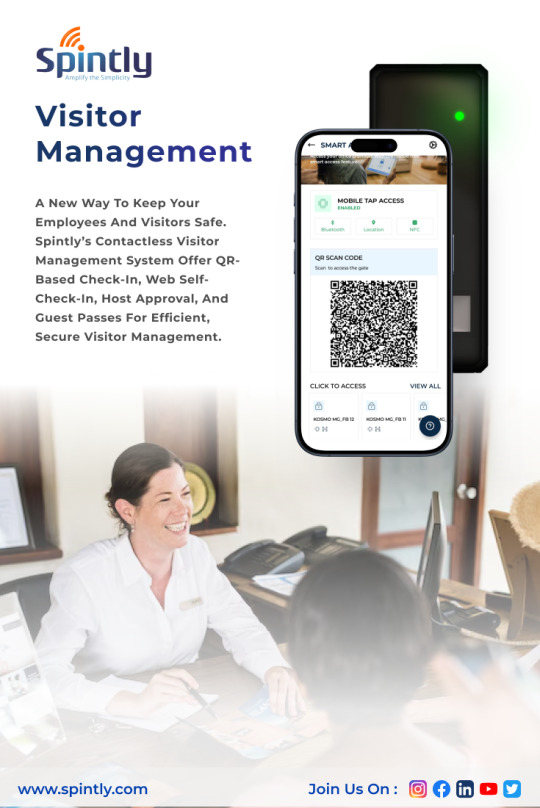
What Is a Visitor Management System?
A Visitor Management System (VMS) is a digital solution that automates the process of registering, tracking, and managing visitors in a facility. Whether you're hosting clients, delivery personnel, or contractors, a VMS helps ensure a smooth and secure process by replacing manual sign-in sheets with digital check-ins, mobile pre-registration, and even face recognition in some cases.
Modern VMS platforms often include features like ID scanning, badge printing, NDA signing, and real-time notifications to hosts. When integrated with Access Control Systems, these platforms become even more powerful - enabling automated access rights, restricted area monitoring, and better control over who enters and exits your building.
Why Integrate Visitor Management with Access Control?
Integrating your Visitor Management System with your Access Control solution creates a unified security framework that benefits both security teams and front desk staff. Here are a few compelling reasons for doing so:
1. Enhanced Security and Compliance
When a visitor is granted temporary access credentials that are linked to their identity and purpose of visit, it eliminates the chances of unauthorized access. This level of control is critical in industries such as healthcare, IT, and finance, where compliance with data and security standards is non-negotiable.
2. Seamless Visitor Experience
A unified system can pre-authorize access for expected guests, reducing waiting time and manual verification. Visitors can check in using a mobile app or a QR code sent to them ahead of time, making the process faster and more professional.
3. Real-Time Monitoring and Reporting
By integrating your systems, security personnel and administrators get real-time dashboards displaying who is inside the building and where. In emergencies, this can be crucial for ensuring a swift evacuation and accurate headcounts.
4. Operational Efficiency
From automatic badge generation to the instant revocation of access after a visit, integration reduces the burden on front desk staff and security personnel. Everything is tracked and logged digitally, minimizing human error and streamlining workflows.
Key Steps to Integration
Integrating a Visitor Management System with Access Control isn’t just about plugging two systems together. It requires thoughtful planning, compatible technology, and sometimes, API-level synchronization.
1. Define Your Security Objectives
Start by asking: What level of access do visitors need? Are there specific zones that should remain restricted? Do you need to track contractors or delivery staff separately? Having clear goals will help determine the depth of integration required.
2. Select Compatible Technologies
Not all VMS and access control platforms are made to talk to each other. Choosing solutions that are built on open architecture or offer easy API integration is crucial. Cloud-based platforms such as Spintly, for instance, offer seamless interoperability with modern visitor management software, making the integration process smoother and more flexible.
3. Set Access Rules and Permissions
Once integrated, you can define visitor roles and permissions. For instance, a guest attending a conference might only be granted access to a meeting room and cafeteria, whereas a technician could be allowed into maintenance areas. These permissions can be automatically configured at check-in based on the visitor type.
4. Enable Pre-Registration and Mobile Access
Advanced systems allow hosts to pre-register guests, sending them QR codes or digital access credentials via email or mobile app. Upon arrival, the visitor simply scans their code at the entrance to gain access. This not only accelerates the check-in process but also reduces physical contact an essential consideration in a post-pandemic workplace.
5. Train Staff and Communicate Changes
Even the best-integrated system requires a degree of human oversight. Train your security and front desk teams on the new workflows and make sure all stakeholders understand how visitors should be managed going forward. Update your visitor policy accordingly and communicate it clearly, both internally and externally.
Industry Use Cases
Here’s how different sectors benefit from integrating a Visitor Management System with Access Control:
Corporate Offices: Streamlines entry for clients, interviews, and deliveries while improving brand perception.
Co-Working Spaces: Offers secure, flexible access to guests and temporary tenants.
Educational Institutions: Helps track and limit access to sensitive zones like labs and administrative areas.
Healthcare: Controls visitor access to wards, patient rooms, and high-risk areas.
Manufacturing: Monitors contractor and vendor access to production zones.
Why Spintly Makes Integration Easy
When it comes to building security and visitor access, cloud-first platforms like Spintly offer a future-ready solution. With wireless, mobile-based architecture and open APIs, Spintly enables seamless integration with third-party Visitor Management Systems, eliminating the need for complex cabling or costly infrastructure changes.
Spintly’s smart access solutions are already helping businesses modernize their physical security strategies while enhancing visitor experiences. Whether you operate a single facility or multiple locations, Spintly's modular design allows you to scale effortlessly without compromising on security.
Conclusion
In an era where the first impression often begins at the front door, businesses can't afford to overlook how they manage guests. By integrating a Visitor Management System with Access Control, organizations can enhance both safety and service—offering secure, efficient, and professional visitor journeys from start to finish.
Providers like Spintly are empowering businesses to simplify access without sacrificing control, using smart, wireless technology that’s easy to adopt and manage. As we move toward more flexible and hybrid workplace models, integrated visitor access solutions will no longer be a luxury - they’ll be a necessity.
Ready to modernize your entry experience and safeguard your workplace with smarter technology? It’s time to explore how cloud-based visitor and access control systems can work together to deliver seamless security and operational excellence.
#visitormanagementsystem#visitormanagement#visitor management system#biometrics#biometric attendance#mobile access#access control system#spintly#smartacess#accesscontrol#access control solutions#smartbuilding
0 notes
Text
When to Redesign SAP Roles: During ECC or Post-Migration to S/4HANA or Rise with SAP
Migrating to SAP S/4HANA or adopting RISE/GROW with SAP is a strategic milestone for organizations aiming to modernize their ERP landscape. However, one critical consideration often overlooked during these transitions is the redesign of SAP roles. The timing of this redesign can significantly influence the success of the migration and the overall efficiency. Should you redesign roles during the ECC phase or wait until after the migration to S/4HANA? This blog explores the key factors driving this decision and introduces the S.M.A.R.T framework—a modern approach to SAP role redesign that ensures compliance, efficiency, and business alignment.
Understanding the Need for Role Redesign
SAP roles are pivotal in defining user access, ensuring compliance, and maintaining operational efficiency. Over time, roles in ECC systems often become bloated with unused authorizations or misaligned with current business needs. This can lead to:
Compliance Risks: Excessive authorizations increase the risk of segregation of duties (SoD) violations.
Migration Complications: Legacy roles with redundancies can complicate the migration process to S/4HANA.
Operational Costs: Since the licensing model is based on assignment and not by usage in S/4HANA and RISE, you may need to procure more licenses than required.
A role redesign ensures clean, streamlined, and compliant access structures, setting the stage for a smooth transition and efficient system post-migration.
ls.ECC vs. S/4HANA: When to Redesign Roles?
Aspect
Redesign During ECC
Redesign Post-Migration to S/4HANA
Compliance
Proactively addresses SoD conflicts and access risks.
Allows compliance alignment with new functionalities post-migration.
Migration Complexity
Simplifies migration with clean and optimized roles.
Reduces redundant effort, focusing only on relevant roles in the new system
Alignment with New Features
May require rework later to incorporate S/4HANA-specific functionalities.
Ensures roles are tailored to new modules, Fiori apps, and processes.
Timeline and Resources
Increases project timelines due to pre-migration workload.
Defers redesign efforts, potentially affecting initial system efficiency.
Business Process Analysis
Limited to existing ECC processes, with potential misalignment after migration.
Better aligned with current and optimized business processes in S/4HANA.
Redesigning SAP Roles with RISE with SAP
If you are moving to RISE with SAP, it is advisable to conduct a complete role redesign during the ECC phase. Once the migration is complete, perform a retrofit to align roles with the cloud-specific requirements introduced by RISE. This approach addresses the unique security, integration, and scalability considerations of a cloud-oriented transformation. You might have many questions at this juncture – What is the best approach? Which tools must be considered? Are there any accelerators that can be used? Can we use stock ready/ready to deploy role structures?
Challenges with Stock Ready Rulesets
Many system integrators offer pre-packaged or stock-ready rulesets as part of their role redesign services. While these rulesets might appear to save time and effort, they often come with significant challenges, making them unsuitable for many businesses. Here’s why the stock-ready approach is not recommended:
Lack of Customization: Stock-ready rulesets are designed to be generic and may not align with the specific needs of your industry or business processes. This can result in inadequate or excessive authorizations.
Compliance Risks: These pre-packaged rulesets may not fully address industry-specific compliance requirements, leaving gaps that could lead to audit findings or regulatory penalties.
Misalignment with Business Processes: Every organization has unique workflows and processes. Stock-ready rulesets may not account for these nuances, leading to inefficiencies and user frustrations.
Post-Implementation Challenges: Organizations often need to spend additional time and resources customizing these rulesets post-implementation, negating the perceived benefits of a quick deployment.
Instead of relying on stock-ready rulesets, organizations should invest in a tailored role redesign approach. This ensures that roles are aligned with specific business processes, compliance requirements, and future scalability needs, delivering long-term value and efficiency. This is where S.M.A.R.T approach/framework can be a life saver.
The S.M.A.R.T Role Redesign Framework
At ToggleNow, we leverage the S.M.A.R.T framework for SAP role redesign. This approach ensures that roles are:
Simplified: Designed to reduce complexity while maintaining operational effectiveness.
Mitigated for Risks: Focused on eliminating SoD conflicts and maintaining regulatory compliance.
Aligned with Business Tasks: Task-based roles ensure that access permissions directly support specific workflows.
Responsive to Change: Built to adapt seamlessly to future business or technical changes.
Transparent and Optimized: Designed with a focus on license optimization to eliminate unnecessary expenditures.
This framework delivers roles that are not only secure but also cost-effective and easy to manage
ToggleNow Advantage
ToggleNow brings a unique value proposition to SAP role redesign initiatives, ensuring a seamless and efficient process tailored to your business needs. Here’s why we stand out:
Customized Solutions: Unlike stock-ready rulesets, ToggleNow develops tailored role designs aligned with your specific business processes, compliance requirements, and industry standards.
Deep Expertise: With extensive experience in SAP role redesign, ToggleNow combines technical proficiency with a deep understanding of regulatory compliance and security best practices.
Innovative Tools:ToggleNow leverages proprietary tools such as Verity, Optimus and accelerators such as xPedite to streamline role redesign, risk analysis, and validation, ensuring faster project delivery.
Focus on Scalability:Our approach ensures that the roles we design are not only compliant and efficient but also scalable, adapting to your future business growth.
Proven Track Record:Trusted by leading organizations, ToggleNow has successfully delivered role redesign projects across diverse industries, enabling smoother migrations and enhanced system performance.
By partnering with ToggleNow, organizations can confidently navigate their SAP transitions, optimizing roles to drive operational excellence and long-term success.
Conclusion
The decision to redesign SAP roles during ECC or post-migration to S/4HANA or RISE with SAP depends on your organization’s priorities, resources, and timeline. Redesigning during ECC can simplify the migration process, while post-migration redesign allows alignment with new functionalities. For RISE with SAP, role redesign becomes even more critical to address cloud-specific requirements.
Moreover, organizations should avoid the pitfalls of stock-ready rulesets and opt for a customized approach that aligns with their unique requirements. By investing in a well-planned redesign, organizations can unlock the full potential of SAP S/4HANA or RISE with SAP, driving operational excellence and business growth.
Read more: https://togglenow.com/blog/redesign-sap-roles-ecc-or-s-4hana/

#SAP Risk Management#SAP access risk analysis tool#SAP GRC access control solution#SAP segregation of duties automation#SoD risk analysis for SAP
0 notes
Text
Smart Parking Solution for Property Owners & Managers: Boost Revenue & Optimize Operations
Managing parking areas is not only about allocating space, it’s also+about maximizing returns, improving tenant satisfaction, and simplifying operations. With smart technology transforming every aspect of real estate, a smart parking solution for property owners and managers has become a critical investment.
In this article, we explore how modern parking systems like LotPilot are empowering property managers to solve long-standing parking challenges, increase revenue, and create seamless experiences for residents and visitors alike.
Why Property Owners Need Smart Parking Solutions
Property owners and managers face multiple challenges in handling parking facilities:
Inefficient space utilization
Manual tracking and enforcement
Unauthorized or overstaying vehicles
Revenue leakage in paid parking zones
Poor tenant or visitor experience
Traditional methods like paper tickets or manual monitoring fall short in today’s fast-paced environments. This is where a smart parking solution designed specifically for property management steps in offering data-driven control and automation.
Key Benefits of a Parking Solution for Property Owners & Managers
1. Maximized Space Utilization
Smart parking platforms like LotPilot use real-time data and occupancy sensors to help managers allocate and monitor parking spaces effectively. This ensures that no space goes underused, especially in high-demand residential, commercial, or mixed-use properties.
2. Automated Access & Entry Control
Smart access systems integrated with License Plate Recognition (LPR) or QR-based entry eliminate the need for manual gates or physical passes. This reduces operational costs and enhances security.
For example, with LotPilot, property managers can issue digital permits, restrict entry to unauthorized vehicles, and monitor every vehicle entering or exiting the premises.
3. Simplified Visitor Management
Managing guest parking can be chaotic. A smart system enables residents to pre-book visitor slots, and digital passes can be sent to guests for seamless entry. This reduces confusion at entry points and improves tenant satisfaction.
4. Revenue Optimization
For paid or mixed-use parking lots, LotPilot allows full automation of payment processing. Whether it’s pay-per-use, monthly subscriptions, or dynamic pricing during peak hours, the platform can manage it all.
Integrated reports give property owners full visibility into parking revenues, helping identify trends and maximize profitability.
5. Enhanced Security and Monitoring
With integrated surveillance, entry logs, and advanced analytics, LotPilot improves overall property security. Managers can get instant alerts for rule violations, overstays, or suspicious activity, maintain order and safety in shared spaces.
Customizable Solutions for Different Property Types
LotPilot isn’t a one-size-fits-all solution. It offers flexibility to adapt to various property settings.
Residential complexes: Allocate dedicated slots, manage visitors, and provide app-based access to residents.
Commercial properties: Enable tiered pricing, tenant management, and real-time space availability updates.
Mixed-use properties: Seamlessly manage both short-term and long-term parking needs, all in one platform.
Whether you're running a gated community, a shopping center, or a corporate office, LotPilot's scalable architecture can be tailored to your specific needs.
Real-time Insights and Reporting
One of the most powerful features of modern parking systems is data. LotPilot provides actionable insights into:
Peak usage times
Average duration of stays
Revenue per slot
Compliance metrics
This helps property owners make informed decisions—like when to expand capacity, increase rates, or change operational hours.
Cloud-based Control Anytime, Anywhere
Cloud technology ensures that you don’t need to be physically present to manage your property’s parking operations. Through LotPilot’s cloud dashboard, you can monitor, assign, and control access to your parking areas remotely—24/7.
Sustainable & Future-ready
Smart parking also contributes to sustainability goals. Efficient traffic flow, reduced idle time, and minimized emissions create a better environment for everyone. With the number of electric vehicles(EVs) on the road rising, platforms like LotPilot are already integrating EV charging station management—future-proofing the property.
Final Thoughts
A reliable parking solution for property owners and managers isn’t just a convenience, but a strategic advantage. By streamlining operations, increasing security, and unlocking new revenue streams, solutions like LotPilot help transform parking from a cost center to a profit generator.
Whether you're a developer planning a new project or a property manager looking to modernize your facility, investing in a smart parking platform is the way forward.
Explore LotPilot today and see how it can simplify parking management while enhancing tenant and visitor satisfaction.
#Smart parking solution#Parking management system#Property parking solutions#LotPilot parking platform#Smart parking for property owners#Parking automation system#Parking solutions for real estate#Parking access control system
0 notes