#Access Control System
Explore tagged Tumblr posts
Text
Commercial Locksmith Houston TX
Welcome to your local trustworthy, professional lock-smith team in Houston, TX. We extend our clients with high quality service and proficient results at low, affordable rates. We work with you 100% to give you the service you want. Our full menu of locksmith services includes commercial and emergency locksmith services. We work hard to give you a service you can trust. Our team of expert lock-smith returned with years of experience and training. We remedy you with the estimate and concern you want to solve all your locks and safety situations. We are a fully bonded and covered corporation that provides sincere answers, advice and prices. So when you need a local professional locksmith in Houston, TX, call our team. We’re always here to assist you.
Our Services: Locksmith Business Electronic Key Locks Keyless Entry Lock Commercial Door Lock Key Safe Box Combination Door Locks Access Control System Door Keypad Lock Electronic Door Lock Deadbolt Locks
(346) 291-5867 9911 Almeda Genoa Rd, Houston, TX, 77275 Mon - Sun: 8:00AM - 11:00PM

#Locksmith Business#Electronic Key Locks#Keyless Entry Lock#Commercial Door Lock#Key Safe Box#Combination Door Locks#Access Control System#Door Keypad Lock#Electronic Door Lock#Deadbolt Locks
4 notes
·
View notes
Text

Upgrade your security with biometric access control upgrades, enhancing safety and convenience. Contact (202) 760-4589 for seamless installation and peace of mind.
2 notes
·
View notes
Text
An access control system regulates entry to a physical or virtual space, ensuring only authorized individuals gain admittance. Employing various mechanisms like key cards, biometrics, or passwords, it meticulously manages permissions, bolstering security and confidentiality.
This system not only safeguards against unauthorized access but also provides an audit trail, logging entry attempts and granting administrators insights into user activity. Vital across industries from corporate offices to government facilities, its versatility extends to digital realms, safeguarding data integrity and privacy. With its role evolving alongside technological advancements, access control systems remain paramount in fortifying the barriers against intrusion and upholding confidentiality.
2 notes
·
View notes
Text
How to Integrate a Visitor Management System with Access Control
In today's fast-paced, security-conscious world, welcoming visitors into your workplace is more than just offering a friendly smile. It’s about creating a secure, seamless, and professional experience from the moment they step through your doors. That’s where the integration of a Visitor Management System with your Access Control infrastructure becomes not only valuable but essential.
As organizations adopt more advanced digital software for security and workforce management, the traditional logbook at the reception desk simply doesn’t cut it anymore. Enterprises now need smarter systems that can streamline visitor authentication, improve building security, and offer real-time visibility into who is onsite - all while delivering a positive visitor experience.
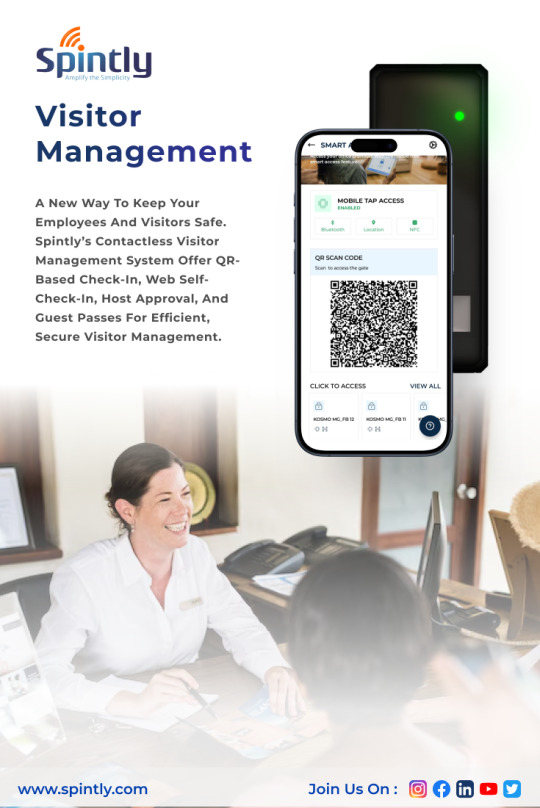
What Is a Visitor Management System?
A Visitor Management System (VMS) is a digital solution that automates the process of registering, tracking, and managing visitors in a facility. Whether you're hosting clients, delivery personnel, or contractors, a VMS helps ensure a smooth and secure process by replacing manual sign-in sheets with digital check-ins, mobile pre-registration, and even face recognition in some cases.
Modern VMS platforms often include features like ID scanning, badge printing, NDA signing, and real-time notifications to hosts. When integrated with Access Control Systems, these platforms become even more powerful - enabling automated access rights, restricted area monitoring, and better control over who enters and exits your building.
Why Integrate Visitor Management with Access Control?
Integrating your Visitor Management System with your Access Control solution creates a unified security framework that benefits both security teams and front desk staff. Here are a few compelling reasons for doing so:
1. Enhanced Security and Compliance
When a visitor is granted temporary access credentials that are linked to their identity and purpose of visit, it eliminates the chances of unauthorized access. This level of control is critical in industries such as healthcare, IT, and finance, where compliance with data and security standards is non-negotiable.
2. Seamless Visitor Experience
A unified system can pre-authorize access for expected guests, reducing waiting time and manual verification. Visitors can check in using a mobile app or a QR code sent to them ahead of time, making the process faster and more professional.
3. Real-Time Monitoring and Reporting
By integrating your systems, security personnel and administrators get real-time dashboards displaying who is inside the building and where. In emergencies, this can be crucial for ensuring a swift evacuation and accurate headcounts.
4. Operational Efficiency
From automatic badge generation to the instant revocation of access after a visit, integration reduces the burden on front desk staff and security personnel. Everything is tracked and logged digitally, minimizing human error and streamlining workflows.
Key Steps to Integration
Integrating a Visitor Management System with Access Control isn’t just about plugging two systems together. It requires thoughtful planning, compatible technology, and sometimes, API-level synchronization.
1. Define Your Security Objectives
Start by asking: What level of access do visitors need? Are there specific zones that should remain restricted? Do you need to track contractors or delivery staff separately? Having clear goals will help determine the depth of integration required.
2. Select Compatible Technologies
Not all VMS and access control platforms are made to talk to each other. Choosing solutions that are built on open architecture or offer easy API integration is crucial. Cloud-based platforms such as Spintly, for instance, offer seamless interoperability with modern visitor management software, making the integration process smoother and more flexible.
3. Set Access Rules and Permissions
Once integrated, you can define visitor roles and permissions. For instance, a guest attending a conference might only be granted access to a meeting room and cafeteria, whereas a technician could be allowed into maintenance areas. These permissions can be automatically configured at check-in based on the visitor type.
4. Enable Pre-Registration and Mobile Access
Advanced systems allow hosts to pre-register guests, sending them QR codes or digital access credentials via email or mobile app. Upon arrival, the visitor simply scans their code at the entrance to gain access. This not only accelerates the check-in process but also reduces physical contact an essential consideration in a post-pandemic workplace.
5. Train Staff and Communicate Changes
Even the best-integrated system requires a degree of human oversight. Train your security and front desk teams on the new workflows and make sure all stakeholders understand how visitors should be managed going forward. Update your visitor policy accordingly and communicate it clearly, both internally and externally.
Industry Use Cases
Here’s how different sectors benefit from integrating a Visitor Management System with Access Control:
Corporate Offices: Streamlines entry for clients, interviews, and deliveries while improving brand perception.
Co-Working Spaces: Offers secure, flexible access to guests and temporary tenants.
Educational Institutions: Helps track and limit access to sensitive zones like labs and administrative areas.
Healthcare: Controls visitor access to wards, patient rooms, and high-risk areas.
Manufacturing: Monitors contractor and vendor access to production zones.
Why Spintly Makes Integration Easy
When it comes to building security and visitor access, cloud-first platforms like Spintly offer a future-ready solution. With wireless, mobile-based architecture and open APIs, Spintly enables seamless integration with third-party Visitor Management Systems, eliminating the need for complex cabling or costly infrastructure changes.
Spintly’s smart access solutions are already helping businesses modernize their physical security strategies while enhancing visitor experiences. Whether you operate a single facility or multiple locations, Spintly's modular design allows you to scale effortlessly without compromising on security.
Conclusion
In an era where the first impression often begins at the front door, businesses can't afford to overlook how they manage guests. By integrating a Visitor Management System with Access Control, organizations can enhance both safety and service—offering secure, efficient, and professional visitor journeys from start to finish.
Providers like Spintly are empowering businesses to simplify access without sacrificing control, using smart, wireless technology that’s easy to adopt and manage. As we move toward more flexible and hybrid workplace models, integrated visitor access solutions will no longer be a luxury - they’ll be a necessity.
Ready to modernize your entry experience and safeguard your workplace with smarter technology? It’s time to explore how cloud-based visitor and access control systems can work together to deliver seamless security and operational excellence.
#visitormanagementsystem#visitormanagement#visitor management system#biometrics#biometric attendance#mobile access#access control system#spintly#smartacess#accesscontrol#access control solutions#smartbuilding
0 notes
Link
0 notes
Text
Revolutionizing Property Security with Checkpoint Access Control Systems
In the modern world, property security has to be smart, efficient, and adaptable. That’s why Checkpoint Access Control Systems is becoming the go-to for gated communities and commercial properties looking to enhance safety without sacrificing convenience.
Their all-in-one platform integrates visitor management, resident and renter access, and advanced license plate recognition technology. This not only improves security by ensuring only authorized individuals gain entry but also simplifies management tasks with remote administration and detailed reporting.
Checkpoint’s system adapts to your property’s unique needs and scales easily, making it perfect for growing communities or businesses. With their dedicated support team, you’re never left wondering if your security system is performing at its best.
Explore how Checkpoint can elevate your property’s security at https://checkpointaccess.com/
1 note
·
View note
Text
Choosing the Right SIRA-Approved Access Control System for Your Dubai Business

Securing your commercial space has become essential in Dubai's fast-paced business environment. Access control systems are now an essential component of contemporary corporate infrastructure, protecting sensitive data, valuable assets, and employee safety. However, selecting the best access control system in Dubai necessitates a calculated, compliant, and strategic approach due to the strict guidelines established by the Security Industry Regulatory Agency (SIRA).
We'll walk you through every step of selecting the best SIRA-approved access control system for your company in this blog.
The Significance of SIRA Approval
SIRA, Dubai's regulatory agency in charge of monitoring security system installation and upkeep, enforces stringent rules to guarantee high security standards in all business establishments. In regulated sectors, access control and surveillance can only be implemented by systems and service providers that have been approved by SIRA.
Selecting an access control system that has been approved by SIRA guarantees:
adherence to the rules and laws of Dubai.
legitimate records for inspections and business licenses.
dependable operation and superior security.
Assurance in insurance claims or audits.
Types of Access Control Systems

Prior to selecting the best method, it is essential to comprehend your possibilities. The most popular kinds of access control systems are as follows:
1. RFID and Keycard Systems
Smart cards or RFID tags are used by these systems to provide access. RFID systems, which are frequently seen in parking lots and office buildings, provide small and medium-sized enterprises with an easy and affordable option.
2. Access Control via Biometrics
This includes iris scanning, fingerprinting, and facial recognition. Because biometric systems rely on distinct bodily characteristics that are challenging to duplicate, they are thought to be more secure.
3. Keypad entry and PIN
To obtain access, users input a special PIN code. Despite being affordable, these systems work best as backups or in locations with low security requirements.
4. Access via Mobile Devices
These systems, which are becoming more and more common, let customers use applications or QR codes on their cellphones to access facilities. They are easy to use, scalable, and ideal for tech-savvy settings.
5. Access Control via the Cloud
These solutions provide cloud-based remote management of logs and access rights. Perfect for companies with multiple locations or those with changing security requirements.
Key Factors to Consider When Choosing a System
1. Type and Size of Business
A logistics warehouse or a high-rise corporate headquarters will need a different system than a modest retail store. To determine the complexity of the system required, consider the size of your building, the number of access points, and the number of employees.
2. Connectivity to Current Infrastructure
Your existing fire safety, alarm, and CCTV systems should work with your access control system. Companies in Dubai that have been approved by SIRA can guarantee a smooth integration.
3. The ability to scale
Make sure the system you select can grow with your company if you intend to expand. Systems that are modular or cloud-based are excellent options for growing businesses.
4. Logs of User Management and Access
For auditing and monitoring purposes, your system ought to include comprehensive access records. This is particularly crucial for sectors where monitoring employee movements is essential, such as IT, healthcare, and finance.
5. Control and Remote Access
Remote access features are crucial for entrepreneurs that oversee several properties or travel regularly. Real-time monitoring and flexibility are offered via cloud-managed access management.
6. Features for Emergency Response
For a speedy escape in an emergency, make sure the system has emergency overrides, fail-safe mechanisms, and connectivity with fire alarm systems.
Working with a SIRA-Approved Security Company
The next important step after deciding on the type of access control system you require is choosing a SIRA approved security system in Dubai to install and maintain it.
Qualities of a SIRA-Approved Provider to Consider:
valid SIRA license and certification.
familiarity in managing access control systems for companies similar to yours.
knowledgeable professionals with up-to-date security technology training.
round-the-clock maintenance and assistance services.
Reports on compliance and clear documentation.
The SIRA inspection procedure will also be managed by a certified business, which will facilitate your journey toward regulatory compliance.
Value versus Cost
Despite the temptation to choose the cheapest estimate, remember that a quality access control system is an investment that will last for many years. In addition to the original installation cost, take into account:
Continuous upkeep
Updates for software
Staff training
Future improvements and scalability
The risk of theft, unauthorized entry, and non-compliance penalties is decreased by a well-maintained system that complies with SIRA.
Putting Your Security in the Future
Dubai is a city known for its cutting-edge innovation and quick development. Select options that will ensure your access control system is prepared for the future.
Encourage machine learning and artificial intelligence for predictive security.
Provide trend insights and data analytics.
are in accordance with Dubai Smart City projects and future SIRA standards.
Concluding remarks
In addition to technology, strategy, compliance, and peace of mind are important considerations when selecting the best SIRA-approved access control system in Dubai. Aligning your security infrastructure with SIRA standards is a wise choice, regardless of whether you're managing a corporate tower in Downtown Dubai or a startup in Business Bay.
Working with a reliable SIRA-approved security company and selecting systems that meet your company's requirements can help you make sure your operations are compliant, your employees are safe, and your facilities are secure.
Make the proper decision now and avoid taking security risks.
#cctv camera#cctv installation#cctv installers#cctv surveillance#dubai#safety#cctvfootage#access control system#search and rescue#fire and rescue
0 notes
Text

ScreenCheck Saudi delivers smart security and identification solutions across major cities in Saudi Arabia. As part of the Centena Group, we provide end-to-end systems including biometrics, ID card issuance, access control, time & attendance, video surveillance, and RFID.
We serve sectors like government, education, oil & gas, and retail with advanced tools like biometric attendance systems, ID card printers, passport scanners, and people counters. With global expertise and local insight, ScreenCheck is your trusted partner for secure, innovative technology.
#SecuritySolutions
#BiometricSystems
#AccessControl
#IDCardIssuance
#TimeAndAttendance
#VideoSurveillance
#RFIDTechnology
#SmartSecurity
#ScreenCheckSaudi
#KSAInnovation
#DigitalSecurity
#PeopleCounting
#PassportScanners
#IdentificationSolutions
#CorporateSecurity
#TechInSaudiArabia
#CentenaGroup
0 notes
Text
Why do businesses require state-of-the-art access control systems In big companies, the staff is generally busy with their assigned responsibilities, access control system installation and UNV CCTV Dubai. this can compromise with the security. Hence, in order to keep intruders, anti-social elements away, access control installation should be given top priority. https://www.alkhoorygroup.com/blog-why-do-businesses-require-state-of-the-art-access-control-systems.html
0 notes
Text
Biometrics Access Control Analytics
If you need the best security systems designed for the PNG environment, contact the security solution providers from TE (PNG) LTD for biometrics access control analytics systems.
Visit https://tepng.com/security-systems/
0 notes
Text
From an access control perspective this fact gives me hives. Like, I know that elevators can have access control because I have worked with ones that used keys and badge readers (could use fobs too) but I also know how much access control is part psychological rather than physical.
On the other hand, shared spaces like hallways and elevator lobbies are kinda a waste of square footage and I would prefer the space be inside the apartment rather than this wasted ghost space that is subjected to the tragedy of the commons and everyone has to pass through.
I am most certainly a city person and an extrovert, but if there's one thing that freaks me out is that somewhere out there are apartment buildings where the downstairs elevator opens directly into your apartment?? Just fucking rawdogging the whole of city life like that? Going commando with essentially nothing but a gust of wind between your private areas and the open public??
765 notes
·
View notes
Text
बायोमेट्रिक फिंगरप्रिंट, फेस और टाइम अटेंडेंस मशीन क्या होती है? (Time Attendance Machine & face Attendance Machine) Read More




1. फिंगरप्रिंट बायोमेट्रिक टाइम अटेंडेंस मशीन
pg
फायदे:
उच्च स्तर की सुरक्षा
किसी भी प्रकार की धोखाधड़ी का कोई मौका नहीं
तेज और सटीक रिकॉर्डिंग
2. फेस रेकग्निशन टाइम अटेंडेंस मशीन
फेस रेकग्निशन मशीन कर्मचारियों के चेहरे की पहचान करके उनकी उपस्थिति को दर्ज करती है। इसमें एक कैमरा होता है जो कर्मचारी के चेहरे को स्कैन करता है और उसकी पहचान करता है। यह तकनीक फिंगरप्रिंट से भी ज्यादा प्रभावी मानी जाती है, क्योंकि इसमें किसी भी प्रकार का शारीरिक संपर्क नहीं होता।
फायदे:
बिना संपर्क के उपस्थिति दर्ज होती है
पूरी तरह से स्वचालित और तेज
उच्च सुरक्षा मानक
3. टाइम अटेंडेंस मशीन
टाइम अटेंडेंस मशीनें आमतौर पर कर्मचारियों की उपस्थिति और कार्य घंटों को रिकॉर्ड करने के लिए इस्तेमाल होती हैं। इनमें से कुछ मशीनें बायोमेट्रिक डेटा (जैसे फिंगरप्रिंट या चेहरा), जबकि अन्य कार्ड या पासवर्ड आधारित हो सकती हैं। इन मशीनों का उद्देश्य कर्मचारियों के कार्य घंटों की सटीक निगरानी करना है, जिससे वेतन, ओवरटाइम और छुट्टियों का सही हिसाब रखा जा सके। @GI@
फायदे:
कर्मचारियों की उपस्थिति पर पूर्ण नियंत्रण
सटीक वेतन और टाइमिंग रिपोर्ट तैयार करना
पारदर्शिता और प्रभावी प्रबंधन
बायोमेट्रिक फिंगरप्रिंट, फेस रेकग्निशन और अन्य टाइम अटेंडेंस मशीनें कंपनियों के लिए उपयुक्त और प्रभावी समाधान प्रदान करती हैं। ये मशीनें कर्मचारियों की उपस्थिति की सही निगरानी करने के साथ-साथ किसी भी प्रकार की धोखाधड़ी को भी रोकने में मदद करती हैं।
यदि आप बायोमेट्रिक टाइम अटेंडेंस मशीन खरीदने के इच्छुक हैं, तो अलोक एंटरप्राइजेज /ALOK ENTERPRISES (दुर्ग) में विभिन्न प्रकार की बायोमेट्रिक और टाइम अटेंडेंस मशीनें उपलब्ध हैं। अधिक जानकारी के लिए आप 9827171017 पर कॉल कर सकते हैं।
1 note
·
View note
Text
Biometric Access Control System Integration: A Complete Guide Improve security with a biometric access control system. Our expert guide covers setup, integration, and best practices for seamless implementation.
#Biometric access control system#Biometric security system#Access control system#Fingerprint access control#Face recognition access control#Biometric authentication system
0 notes
Text

Improve security in your premises today with Cybergroup's expert Access Control System Installation services. Advanced solutions are always considered to harden premises in regard to unauthorized access. From biometric scanners to key card entry systems, our customized installations provide seamless integration and maximum protection. Secure your business today with Cybergroup's trusted access control solutions!
#Access Control System#Access Control System Installation#Access Control System Ahmedabad#Access Control System Company
0 notes
Text
Top 10 Benefits of Using a Biometric Attendance Machine for Your Business
In today’s competitive business landscape, managing employee attendance accurately is critical. Many businesses - from startups and co-working hubs to large manufacturing firms still rely on manual registers or traditional punch cards. These outdated systems often result in errors, time theft, and administrative inefficiencies.
Biometric attendance systems offer a modern, reliable alternative. By using unique human identifiers such as fingerprints or facial features, these systems record attendance with precision. This blog explores the top 10 benefits of using biometric attendance machines for your business.

1. Eliminates Time Theft and Buddy Punching
One of the biggest advantages of biometric access systems is their ability to completely eliminate buddy punching - a common practice where one employee clocks in for another. Since biometric machines rely on unique identifiers such as fingerprints or facial recognition, impersonation becomes virtually impossible. This ensures complete accuracy in attendance data and strengthens organizational integrity.
2. Improves Accuracy in Time Tracking
Manual attendance methods or RFID-based systems often leave room for human error. In contrast, biometric attendance machines offer precise, real-time tracking of in-and-out timings. This accuracy leads to better payroll processing and labor cost control. The fewer the errors, the more reliable your HR and payroll systems become.
3. Speeds Up Check-Ins and Check-Outs
With biometric access in place, the daily check-in and check-out routine is faster and more efficient. Employees no longer need to remember login credentials, swipe cards, or queue up to sign registers. A simple scan of a fingerprint or face gets the job done in seconds - saving valuable time every day.
4. Integrates Seamlessly with HR and Payroll Systems
Many modern biometric attendance machines are built to integrate with existing Human Resource Management Systems (HRMS) and payroll platforms. This seamless connection allows real-time syncing of attendance data, reducing the manual effort required for HR tasks. Businesses can now automate leave calculations, overtime tracking, and monthly pay processing with ease.
5. Enhances Workplace Security
By implementing biometric access, organizations can ensure that only authorized personnel enter the premises. This reduces the risk of intrusions or unauthorized entry. It also enables businesses to maintain a digital log of who accessed which part of the building and when, an essential feature for audit trails and investigations.
6. Supports Remote and Multi-Location Attendance
For organizations with multiple branches or remote employees, cloud-enabled biometric attendance machines provide a centralized dashboard for real-time monitoring. Managers can track attendance data from any location, making it ideal for hybrid work models or businesses with distributed teams. Platforms like Spintly specialize in such cloud-based solutions, offering scalable infrastructure for businesses across India and beyond.
7. Reduces Administrative Overhead
Managing spreadsheets, timesheets, and manual attendance logs can be tedious and prone to error. Biometric access systems automate these processes, drastically reducing the administrative workload. This allows HR professionals to focus on more strategic initiatives rather than repetitive data entry and validation.
8. Boosts Employee Accountability
When employees know their attendance is being accurately tracked, it encourages punctuality and accountability. A transparent system builds trust while discouraging time-wasting practices. With a biometric attendance machine, there's no ambiguity - just verifiable proof of work hours.
9. Compliant with Labor Laws and Audit Requirements
Keeping compliant records is crucial for any organization. Biometric access logs are time-stamped and tamper-proof, making them a reliable source of information during audits or labor inspections. The digital nature of these records ensures that businesses can maintain compliance with minimal effort.
10. Environmentally Friendly and Cost-Effective
Digital systems inherently reduce the need for paper and plastic cards, making them more sustainable in the long run. Additionally, though the initial investment in a biometric attendance machine may seem significant, the long-term savings from reduced fraud, enhanced efficiency, and lower admin costs make it a wise investment.
Real-World Applications Across Industries
The adoption of biometric access systems is not limited to one sector. From IT firms and manufacturing units to educational institutions and healthcare facilities, industries of all sizes are leveraging these systems to streamline workforce management. For example, in high-security environments like research labs or government offices, these machines help enforce strict access control alongside attendance tracking.
Why Spintly Is a Smart Choice
Businesses exploring biometric and cloud-based access control solutions will find that providers like Spintly offer a blend of innovation, flexibility, and user-friendly design. With a focus on mobile-enabled and wireless infrastructure, Spintly’s biometric solutions are easy to deploy, scale, and integrate with existing systems making them a preferred choice for modern enterprises.
What sets Spintly apart is its commitment to simplifying physical security through the use of IoT and cloud-based technology. Whether you're looking for biometric access for a single site or multiple offices, Spintly offers robust solutions tailored to your operational needs.
Conclusion
As workplace dynamics evolve, having the right attendance management software becomes crucial. A biometric attendance machine does more than just record clock-ins - it reshapes how companies manage time, security, and productivity. With features like real-time tracking, seamless integration, and strong security, these systems prove their worth every single day.
For companies seeking smarter, scalable, and secure attendance solutions, exploring advanced biometric access platforms is a step in the right direction. Providers like Spintly are already helping organizations across India modernize their workforce management while ensuring compliance and efficiency. Investing in the right system today can set the foundation for a more accountable and agile business tomorrow.
#biometric access#biometric attendance#biometric machine#biometric authentication#wireless access#access control systems#accesscontrol#mobile access#spintly#smartacess#biometrics#smartbuilding#access control system#access control solutions
0 notes
Text
Real-Time Biometric Software: A Solution to Attendance Management for UPSC Coaching

In an era where efficiency and precision are paramount, real-time biometric software is emerging as a game-changer in attendance management systems. Particularly for UPSC coaching centers, where punctuality and discipline are critical, leveraging such technology ensures accuracy, saves time, and enhances overall management. Institutions like NIALabs are paving the way with advanced solutions like their finger biometric systems that streamline operations seamlessly.
Why UPSC Coaching Centers Need Biometric Attendance Solutions
It is a great challenge to manage attendance of so many students in UPSC coaching centers especially with large groups. Not only are these methods exacting in time, but they are also quite imprecise. Biometric software can be viewed as offering a more powerful solution altogether: it monitors the process in real time and does not contain human mistakes. Here's why it is indispensable:
Accuracy and Transparency: Another advantage is where biometric systems are put in place in order to keep attendances for example the biometric solution providers NIALabs eliminate falsified records.
Time-Saving: Computerized processes save the time that would be taken on roll calls and manual recordation.
Efficiency in Management: The use of real-time data enhances ways through which attendance patterns are monitored and controlled by the administrators hence enhancing the operational efficiency of the system.
Enhanced Accountability: In biometric systems students as well as staff is made responsible for the presence.
How Real-Time Biometric Software Works
Biometric attendance system incorporates physical characteristics of a person for instance fingerprints or face recognition. In ID authentication mode, any student or staff member who approaches the system undergoes a match making process with a previously stored database to ensure the best identification. Availability of attendance records is possible in real-time where changes may be made immediately depending on an administrator’s request.
Key Features of Biometric Systems
Instant Authentication: These systems give fast identification, with little time being wasted, as is the case with NIALabs’ finger biometric software.
Cloud Integration: Numerous solutions available provide cloud storage, and therefore information is protected and can be accessed remotely.
Customizable Reports: School authorities can be able to produce customized attendance reports to suit their needs.
Scalability: Biometric systems can be easily custom made in regards to the size and type of coaching centre; whether it is a small ‘coaching classes’ or a large coaching institute.
Benefits of NIALabs Finger Biometric Software for UPSC Coaching Centers
NIALabs has been established as an important player in biometric solutions and has its finger biometric systems in high technology. Here’s what sets their software apart:
User-Friendly Interface: A tool for utilization by anyone who does not have the technical know-how to put it down themselves.
Advanced Security: Secure data processing protects specific information through high grade encryption.
Custom Solutions: Given the specificity, in terms of the nature of its accomplishments, to the needs of education institutions.
Real-Time Updates: Recording of attendees per meeting and preparation of reports on the same at real-time.
Cost-Effectiveness: Free from the high costs of many models without the need to have low standard or fewer functionalities.
Implementing Biometric Software: A Step-by-Step Guide
For UPSC coaching centers considering this transformation, here’s how to get started:
Assess Your Requirements
Consider the needs of the students, your institution, and the size as well as the quantity of students in your institution. This will help in choosing the right system.
Choose a Reliable Provider
Choose a reliable provider of such solutions as NIALabs offers durable and effective biometric systems.
Installation and Setup
The installation and configuration of the system should be done in accordance to the various guidelines. We have completed the high-priority tasks of federating NIALabs with other industry laboratories and establishing its strategic targets; however, we are still seeking ways to open additional doors and expand our opportunities, with help from experts for this procedure.
Train Staff and Students
To ensure that the users of the system embrace the system, have some level of training done on the system. This reduces resistance and increases acceptance.
Monitor and Optimize
Attend meeting attendance data and formed a pattern for improving the usage of the system.
Addressing Concerns About Biometric Technology
However, one may argue that the use of biometric technology will bring issues of privacy and security data into the technology investment. To address these issues:
Data Encryption: Please go for systems with good encryption to enhance security of the information.
Compliance with Regulations: Make sure that the provider complies with particular legislation on the data protection.
Transparency: In order to gain the trust of the users, the informed and recounting ways of using and storing data should be made obvious.
Conclusion
Real time biometric software is not only a new fashion, but it has become a need in the modern world for institutions which seek to receive high results. To the UPSC coaching centers, importation of this technology means an improvement in the management, security around the learning institution and overall discipline. They are evident by the fact that today NIALabs, with its finger biometric solutions, remains as the most reliable partner in this transformational journey. By adopting these systems, coaching centers will remain relevant to their mission of preparing students for success, while leaving the issues of attendance management to other systems.
#al finger biometric#biometric software#face biometric#real time biometric#biometric attendance#access control system#biometric solutions#biometric munufacturers
0 notes