#Cloud Computing vs Grid Computing
Explore tagged Tumblr posts
Text
Grid Computing vs. Cloud Computing: A Comparative Analysis
In today's technologically advanced world, both businesses and individuals rely on powerful computing solutions to manage large-scale data processing, complex simulations, and other resource-intensive tasks. Two of the most prominent solutions are grid computing vs cloud computing. While they serve similar purposes, they differ significantly in architecture, scalability, cost, and applications. This blog post examines these differences to help you determine which computing model is best suited to your needs.
Grid Computing: Harnessing Distributed Resources
Definition and Architecture: Grid computing is a distributed computing model that aggregates the power of multiple computers to address a single problem simultaneously. These computers, often geographically dispersed, collaborate as a virtual supercomputer. Grid computing leverages idle processing power from various machines, effectively utilizing resources that would otherwise remain unused.
Applications: Grid computing is commonly employed in research environments where large-scale computational problems, such as climate modeling, genetic analysis, and complex simulations, need to be solved. For instance, projects like SETI@home use grid computing to analyze radio signals for signs of extraterrestrial life by distributing the workload across thousands of volunteer computers.
Scalability and Flexibility: While grid computing can scale to accommodate additional computers, it requires significant coordination and communication between nodes. This can introduce latency and complexity, particularly as the number of nodes increases. Grid computing is less flexible than cloud computing because adding new resources or reconfiguring the system often involves considerable manual intervention.
Cost: Grid computing can be cost-effective as it utilizes existing resources. Organizations with an existing network of computers can leverage them without investing in new hardware. However, the cost of managing and maintaining the grid infrastructure can be high, especially if the system requires constant updates and monitoring.
Cloud Computing: On-Demand Resource Provisioning
Definition and Architecture: Cloud computing provides on-demand access to a shared pool of configurable computing resources, including servers, storage, and applications, over the internet. These resources are hosted in data centers operated by cloud service providers such as Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP).
Applications: Cloud computing is versatile and can be used for a wide range of applications, including web hosting, data storage, machine learning, and big data analytics. Businesses of all sizes leverage cloud computing to scale their operations, enhance flexibility, and reduce the time-to-market for new applications.
Scalability and Flexibility: One of the most significant advantages of cloud computing is its scalability. Cloud services can automatically scale resources up or down based on demand, ensuring optimal performance without manual intervention. This elasticity makes cloud computing ideal for applications with fluctuating workloads, such as e-commerce platforms and online gaming.
Cost: Cloud computing follows a pay-as-you-go model, where users only pay for the resources they consume. This can be highly cost-effective for businesses that experience variable workloads. Additionally, the cloud provider handles maintenance, security, and updates, further reducing the total cost of ownership.
Key Differences
Resource Management: Grid Computing: Leverages distributed resources from multiple locations. Cloud Computing: Provides centralized, on-demand resources managed by cloud providers.
Scalability: Grid Computing: Requires manual intervention to scale. Cloud Computing: Offers automatic scalability.
Cost: Grid Computing: Can be cost-effective but may incur high maintenance costs. Cloud Computing: Operates on a pay-as-you-go model, potentially reducing costs.
Flexibility: Grid Computing: Less flexible, involving complex setup and configuration. Cloud Computing: Highly flexible, with straightforward resource provisioning and management. Conclusion Both grid computing and cloud computing possess distinct strengths and are tailored to different types of workloads and organizational needs. Grid computing is ideal for specific, large-scale scientific and research applications that benefit from distributed processing. Conversely, cloud computing offers exceptional flexibility, scalability, and cost-efficiency, making it the preferred solution for businesses aiming to innovate and expand rapidly.Understanding the differences between these computing models can assist in making an informed decision about which technology to adopt for your specific requirements.
0 notes
Text
Edge Intelligence Unified Architecture for Predictive Maintenance
Digital transformation is accelerating the evolution of computing frameworks. With data increasingly generated outside centralized cloud environments, enterprises are turning to edge computing and fog architecture to process information closer to its source. This has led to a growing need for cohesion among these systems. Edge intelligence unified architecture offers a strategic model for integrating edge devices, fog nodes, and cloud infrastructure, enabling real-time insights, operational continuity, and scalable deployment. It ensures that data is not only collected but acted upon at the right layer of the computing ecosystem.

Understanding the Need for Unified Architecture Today’s computing needs are no longer served by a one-size-fits-all cloud approach. Applications in manufacturing, healthcare, autonomous vehicles, and smart cities require ultra-low latency and contextual awareness. A unified architecture ensures that intelligence exists not just in the cloud, but across all computing layers—optimizing both speed and scalability. Without a unified model, edge and fog systems risk becoming siloed, increasing complexity and reducing data reliability.
The Role of Edge Intelligence in Modern IT Edge intelligence enables devices at the edge of the network—like sensors, gateways, and embedded systems—to process and analyze data locally. This reduces the dependency on cloud infrastructure for every computational need. It improves response times, minimizes bandwidth usage, and allows enterprises to make faster decisions. When this edge intelligence is integrated within a unified architecture, its value scales exponentially through coordinated communication with fog and cloud layers.
Why Edge Intelligence Unified Architecture Matters A fragmented approach to edge and fog computing can lead to inefficiencies, security gaps, and integration headaches. Edge intelligence unified architecture provides a blueprint for harmonizing data flows, orchestrating workloads, and synchronizing analytics across distributed environments. It ensures seamless transitions between edge, fog, and cloud systems, giving enterprises the agility to deploy intelligent solutions where they are most needed—without reinventing the wheel for each layer.
Edge vs. Fog vs. Cloud: Clarifying the Layers Edge computing occurs directly on or near the devices that generate data, enabling real-time responses. Fog computing sits between the edge and the cloud, adding a layer of localized processing and orchestration. Cloud computing offers centralized processing and long-term storage but is limited by latency. A unified architecture blends these layers so that each plays a complementary role, with edge handling immediate reactions, fog managing coordination, and cloud focusing on historical analysis and scalability.
Benefits of a Unified Approach to Edge Intelligence With a unified model, enterprises can streamline data processing, enhance security by minimizing data transit, and maintain consistent governance across all layers. It also simplifies application deployment by offering a standardized platform for running AI models, managing connectivity, and scaling services. The result is a more resilient and responsive digital infrastructure that meets modern expectations of speed, personalization, and reliability.
Scenarios Where Edge Intelligence Unified Architecture Thrives Industries such as autonomous transportation, smart grids, retail analytics, and predictive maintenance benefit from this architecture. In each of these domains, milliseconds matter, and a centralized cloud approach cannot meet operational demands. Edge intelligence unified architecture allows these systems to analyze, adapt, and act locally, while still contributing to the broader enterprise intelligence framework.
Challenges and Considerations in Implementing Unified Architectures Despite its advantages, implementing a unified architecture is not without challenges. Organizations must consider interoperability between hardware and software platforms, edge-specific security concerns, and the complexity of orchestrating hybrid deployments. Success requires choosing flexible frameworks, investing in edge-ready AI tools, and establishing policies for governance and lifecycle management.
For more info https://bi-journal.com/edge-intelligence-unified-architecture/
Conclusion As enterprises strive to make faster, smarter, and more localized decisions, edge intelligence unified architecture becomes the backbone of modern computing strategies. It brings clarity to an increasingly complex digital landscape by integrating edge, fog, and cloud into a coordinated system that delivers on performance, scalability, and innovation. By investing in a unified model, businesses position themselves to harness real-time intelligence while maintaining the agility and resilience needed in a data-driven world.
#Edge Computing#Edge Intelligence#Fog Computing#BI Journal#BI Journal news#Business Insights articles
0 notes
Text
Server CPU Model Code Analysis
Decoding Server CPU Model Numbers: A Comprehensive Guide
Server CPU model numbers are not arbitrary strings of letters and digits; they encode critical technical specifications, performance tiers, and use-case optimizations. This article breaks down the naming conventions for server processors, using Intel Xeon as a primary example. While other vendors (e.g., AMD EPYC) may follow different rules, the core principles of hierarchical classification and feature encoding remain similar.

1. Brand and Tier Identification
Brand: The prefix identifies the product family. For instance, Intel Xeon denotes a server/workstation-focused processor line.
Tier: Reflects performance and market positioning:
Pre-2017: Tiers were marked by prefixes like E3 (entry-level), E5 (mid-range), and E7 (high-end).
Post-2017: Intel introduced a metal-based tiering system:
Platinum: Models start with 8 or 9 (e.g., 8480H). Designed for mission-critical workloads, these CPUs support maximum core counts, advanced UPI interconnects, and enterprise-grade features.
Gold: Begins with 5 or 6 (e.g., 6448Y). Targets general-purpose servers and balanced performance.
Silver: Starts with 4 (e.g., 4410T). Optimized for lightweight workloads and edge computing.
2. Generation Identifier
The first digit after the tier indicates the processor generation. Higher numbers represent newer architectures:
1: 1st Gen Scalable Processors (2017, Skylake-SP, 14nm).
2: 2nd Gen Scalable Processors (2019, Cascade Lake, 14nm).
3: 3rd Gen Scalable Processors (2020–2021, Ice Lake/Cooper Lake, 10nm/14nm).
4: 4th Gen Scalable Processors (2023, Sapphire Rapids, Intel 7 process, Golden Cove architecture).
Example: In Platinum 8462V, the “4” signifies a 4th Gen (Sapphire Rapids) CPU.
3. SKU Number
The trailing digits (usually 2–3) differentiate SKUs within the same generation and tier. Higher SKU numbers generally imply better performance (e.g., more cores, larger cache):
Example: Gold 6448Y vs. Gold 6468Y: The latter (SKU 68) has more cores and higher clock speeds than the former (SKU 48).
4. Suffix Letters
Suffixes denote specialized features or optimizations:
C: Single-socket only (no multi-CPU support).
N: Enhanced for networking/NFV (Network Functions Virtualization).
T: Long-lifecycle support (10+ years).
Q: Liquid-cooling compatibility.
P/V: Optimized for cloud workloads (P for IaaS, V for SaaS).
Example: 4410T includes the “T” suffix for extended reliability in industrial applications.
5. Architecture and Interconnect Technologies
On-Die Architecture:
Ring Bus (pre-2017): Limited scalability due to latency spikes as core counts increased.
Mesh Architecture (post-2017): Grid-based core layout improves scalability (e.g., up to 40 cores in Ice Lake).
Interconnects:
UPI (Ultra Path Interconnect): Facilitates communication between multiple CPUs. Platinum-tier CPUs often support 3–4 UPI links (10.4–20.8 GT/s).
PCIe Support: Newer generations integrate updated PCIe standards (e.g., Sapphire Rapids supports PCIe 5.0).
Application-Based Selection Guide
High-Performance Computing (HPC): Prioritize Platinum CPUs (e.g., 8480H) with high core counts and UPI bandwidth.
Cloud Infrastructure: Choose P (IaaS) or V (SaaS) variants (e.g., 6454S).
Edge/Telecom: Opt for N-suffix models (e.g., 6338N) with network acceleration.
Industrial/Embedded Systems: Select T-suffix CPUs (e.g., 4410T) for extended lifecycle support.
Server CPU model numbers act as a shorthand for technical capabilities, enabling IT teams to quickly assess a processor’s performance tier, generation, and specialized features. By understanding these codes, organizations can align hardware choices with workload demands—whether deploying AI clusters, cloud-native apps, or ruggedized edge systems. For precise specifications, always cross-reference vendor resources like Intel’s ARK database or AMD’s technical briefs.
0 notes
Text
Consumer IoT vs. Industrial IoT: Understanding the Differences
The Internet of Things (IoT) has rapidly become an integral part of our daily lives, influencing everything from the way we live to how industries operate. Broadly, IoT can be categorized into two main segments: Consumer IoT (CIoT) and Industrial IoT (IIoT). While both fall under the IoT umbrella, they serve distinct purposes, have different applications, and present unique challenges. This article aims to delineate the primary differences between CIoT and IIoT.
1. Purpose and Application
Consumer IoT (CIoT): CIoT primarily focuses on enhancing the quality of life for individuals. It encompasses devices and systems designed for personal use or for a home environment. Examples include smart thermostats, wearable fitness trackers, connected appliances, and home security systems. These devices aim to provide convenience, entertainment, and personal well-being.
Industrial IoT (IIoT): IIoT, on the other hand, is tailored for industrial applications. It's about optimizing processes, enhancing productivity, and reducing costs. IIoT is prevalent in sectors like manufacturing, agriculture, energy, and transportation. Examples include predictive maintenance sensors, industrial robots, and smart grid technologies.
2. Scale and Complexity
Consumer IoT: CIoT devices are generally standalone or operate within a small network, like a home automation system. They're designed for ease of use, with user-friendly interfaces and straightforward functionalities.
Industrial IoT: IIoT systems are more complex, often involving large-scale deployments with thousands of interconnected devices working in tandem. These systems require sophisticated data analytics platforms and robust network architectures to manage and process the vast amounts of data they generate.
3. Connectivity and Interoperability
Consumer IoT: CIoT devices typically connect via standard home Wi-Fi networks or through cellular networks. Interoperability can be a challenge, as many consumer devices are designed to function within a specific ecosystem or brand.
Industrial IoT: IIoT devices often use specialized communication protocols suited for industrial environments, such as MQTT or CoAP. Given the need for seamless integration in industrial settings, there's a stronger emphasis on standardization and interoperability in IIoT.
4. Security Concerns
Consumer IoT: Security is a significant concern for CIoT, as many consumer-grade devices have been found to have vulnerabilities. These devices, if not properly secured, can become entry points for cyberattacks on personal networks.
Industrial IoT: The stakes are even higher for IIoT, where a security breach can lead to significant financial losses, operational downtime, or even safety concerns. As a result, IIoT solutions often incorporate advanced security measures, including end-to-end encryption and regular security audits.
5. Data Processing and Analysis
Consumer IoT: Most CIoT devices generate data pertinent to individual users, which is often processed on the device itself or in a cloud environment. The focus is typically on real-time feedback and personal insights.
Industrial IoT: IIoT devices generate vast amounts of data that require advanced analytics tools for processing. The data is used for predictive analysis, trend forecasting, and operational optimization. Often, edge computing is employed to process data on-site, reducing latency and ensuring timely decision-making.
6. Lifecycle and Durability
Consumer IoT: Consumer devices are often designed with a shorter lifecycle in mind, given the rapid pace of technological advancements in the consumer electronics sector.
Industrial IoT: Industrial devices, given their critical nature, are built for longevity. They are rugged, designed to withstand harsh environments, and can function optimally for years without requiring replacement.
Conclusion
While both Consumer IoT and Industrial IoT aim to leverage the power of interconnected devices, their applications, challenges, and requirements differ significantly. Understanding these differences is crucial for businesses, policymakers, and consumers alike as the world continues to embrace the myriad possibilities offered by IoT. As the IoT landscape evolves, the demarcation between CIoT and IIoT will become even more pronounced, each serving its unique purpose in the grander scheme of digital transformation.
0 notes
Text
Demystifying Fog Computing vs. Edge Computing
As Internet of Things deployments scale exponentially, huge volumes of data get generated at the network edge. Processing all this data in the cloud causes latency, congestion and bandwidth challenges. Two decentralized computing approaches have emerged to address this - fog computing and edge computing.
Both concepts involve pushing intelligence and processing closer to the network edge. However, fog and edge computing have distinct architectures and use cases. In this article, we’ll examine the key differences between the fog and edge computing models for handling IoT data.
Defining Edge Computing
First let’s define what we mean by edge computing. Edge computing refers to performing data processing and analysis locally on intelligent devices close to the source, rather than sending data to the cloud or a remote data center.
Examples include:
- A sensor hub on an oil rig analyzing telemetry data to adjust drilling parameters in real-time.
- A factory robot with an onboard computer vision model that can adapt movements without cloud connectivity.
- A connected car performing autonomous driving tasks like object detection using its onboard GPU.
- A smart refrigerator diagnosing issues by processing usage sensors locally and without reliance on backend systems.
In essence, edge computing allows time-sensitive or privacy-centric data analysis to occur on-premises on the device rather than offsite. This addresses the need for lower latency, better reliability, and data security.
Understanding Fog Computing
Now let’s examine fog computing. Like edge computing, fog computing involves processing data closer to the network edge. But fog computing refers specifically to a distributed configuration of specialized fog nodes between edge devices and the cloud:
- Edge devices like sensors, controllers, actuators, and machines send data to nearby fog nodes for processing, rather than to the cloud.
- These fog nodes distribute compute, storage, and networking services for real-time data processing.
- Processed data gets sent from fog nodes to cloud data centers for longer-term storage and analysis.
So fog computing offers a middle ground, processing data at the local area network level on these fog nodes, before sending refined data to the cloud.
Comparing Architectures
The main difference between edge and fog is the decentralized architecture that fog computing introduces:
- Edge computing retains a centralized architecture - all processing occurs locally on the device itself without intermediary components between devices and the cloud.
- Fog computing features distributed architecture - fog nodes act as local hubs for initial processing for groups of nearby edge devices before reaching the cloud.
Edge computing is fully self-contained to the device. Fog computing shares processing across dedicated fog nodes.
Evaluating Use Cases
Due to these architectural differences, edge and fog computing each suit different use cases:
- Edge computing suits time-sensitive, mission-critical data that can’t tolerate latency - like industrial controls or autonomous vehicles.
- Fog computing suits interim processing where some localized filtering, aggregation, and analysis of data is beneficial before sending to the cloud - such as smart city or sensor grid data.
- Fog also suits operations without advanced edge devices - basic devices can leverage nearby fog nodes whereas edge requires onboard capability.
So latency sensitivity and sophistication of devices help determine optimal approach.
Complementary, Not Competitive
Importantly, edge and fog computing are complementary rather than competitive. The choice depends on use case and system constraints.
Often, edge and fog computing get implemented together in a continuum to reap benefits: edge devices handle real-time critical operations while fog nodes do interim processing before transferring data farther.
Understanding the nuanced distinction allows architecting the right decentralized solution to bring intelligence closer to the data source. Both edge and fog computing open exciting possibilities for streamlining IoT workloads in different ways.
The ability to filter, process and analyze data at the source - rather than solely in distant centralized systems - marks a paradigm shift for building responsive, distributed IoT applications.
0 notes
Text
Windows VS. Chrome OS: In-Depth Comparison [2023]
As technology continues to evolve, so does the variety of operating systems. Windows and Chrome OS are two of the major players in the operating system arena. But which one is for you?

So, let’s get started.
OVERVIEW OF WINDOWS
Windows has been around since the late 1980s, and it is the most used operating system. It has been designed with a focus on security, performance, and ease of use in mind. The latest version is Windows 11. And it is designed to work on a range of devices, including tablets, laptops, and desktops.
Windows is the most loved operating system. Many thanks to its intuitive user interface, accessibility, and software support, it has long made its place in both people’s hearts and their computers. If you are to buy a computer right now, 99 in 100 computers will have windows.
OVERVIEW OF CHROME OS
While Windows has been around for a long, Chrome OS is a much more recent invention. It was first introduced in 2011 as a lightweight operating system with the intention of being used mainly for cloud-based activities. Chrome OS runs on a variety of devices, including laptops (specifically Chromebooks), tablets, and desktops.
This operating system itself is very lightweight and fast, which makes it ideal for low-end devices. Because it is lightweight and very cloud-centric, it is great for those looking for a simple operating system that can get work done. It is great for students; casual browsing and creating normal documents shouldn’t be a problem with this OS.
USER INTERFACE
Windows has a good user interface. You have a start menu for accessing applications quickly, a strong file explorer, and an intuitive settings menu. Windows 11 has also been designed with touchscreen devices in mind so that it can be used comfortably with a touchscreen.
However, the interface of windows is not as user-friendly as Chrome OS. If you have never used windows before, then you might have trouble navigating through, which is not the case with Chrome OS.
When it comes to Chrome OS, you have access to a grid-style menu that gives you quick access to all of your apps and settings. If you are using a Chromebook, you can also run Android apps, which makes your experience more similar to a Windows notebook.
However, the experience will vary, depending on the device you are using. While both operating systems have their positives, the user interface is one area where Chrome OS has a significant advantage over Windows. The interface of Chrome OS is very intuitive. It is because it is typically an android for big-screen devices.
SECURITY
The security of your device is an important factor to consider when choosing your operating system. Windows has traditionally been seen as a less secure operating system, and in the past, it did have some vulnerabilities. However, thanks to its frequent updates and patches, Windows has become more secure.
Windows has also recently been redesigned to be more secure with features like Windows Defender and Windows Sandbox. However, it is a breeding place for hackers and scammers, as anyone can build and distribute programs for free.
Chrome OS is a very secure operating system, thanks to its closed ecosystem. It is designed to run in a sandboxed environment, and security is built into the system, making it difficult for malicious software to infiltrate the system. Chrome OS also has frequent security updates, meaning that you can stay protected against the latest threats. And you can’t install random things as easily in the chrome OS, making it a lot more secure device.
APPS AND GAMES
Windows has long been considered a go-to operating system for gamers. This is because it is a more powerful operating system that can handle more graphics-intensive games. However, this also means that it may be more suitable for high-end computers.
Advertisements
The app support of windows is tremendous. It is the go-to operating system for computers, and developers prioritize windows over any operating system, so you will never find it lacking any useful program for long.
Chrome OS is not built for anything like that. It does not concern itself with app support. It is specifically made for productivity on a low-end machine. As a lightweight operating system, it can get the job done, but it is limited than Windows. It is built by google and uses google cloud-based productivity applications. You can log in with your Google account and start working with its office suite. You can also download some android applications.
The Chrome OS is not lacking by a lot, thanks to its virtual Linux terminal, which lets you install Linux applications.
CONCLUSION
Both operating systems have their strengths and weaknesses and can be beneficial for different types of users. Windows is a more robust and powerful operating system, while Chrome OS is lightweight and very efficient. Windows has long been seen as a go-to operating system for gamers, while Chrome OS is ideal for those who are more productivity-focused. The decision between Windows and Chrome OS ultimately comes down to what you want to use your device for and what is most important to you.
If you have a powerful machine and want to scratch its limit to the max, then go for windows. And if you have a low-end machine and want to do a little bit of school and office work, then go for the Chrome OS. Don’t ever think about gaming on a Chrome OS.
Source :- https://mahjonggaarp.wordpress.com/2023/08/03/windows-vs-chrome-os-in-depth-comparison-2023/
1 note
·
View note
Text
Microsoft Teams covers 75M daily active customers, as Zoom readjusts its very own user numbers

Personalized histories for Teams video calls are now generally available, as is a capability for meeting coordinators to immediately "finish conference" by clicking a switch in the control bar, Microsoft announced last week. By the end of April, Microsoft is guaranteeing that Groups will certainly support up to 9 noticeable participants at once on video clip phone calls. A photo shared by Microsoft suggests Groups will certainly have a 3 x 3 grid for viewing 9 participants all at once. Digital meeting devices make it possible for individuals to interact socially, function, as well as team up in powerful as well as new means. The University of Denver uses 2 video clip partnership sources to its community.
Do you have concerns regarding Zoom or do you want to experience Zoom Meetings as well as Zoom Room yourself? Contact our video professionals totally free advice and a presentation. A boosting variety of organizations utilize Zoom as their interaction and partnership solution. Microsoft clients utilizing Skype for Organisation are compelled to reconsider this selection as Microsoft introduced to terminate Skype for Organisation in favour of Teams in 2020.
Guests have the ability to see what they appear like as well as can turn off their microphone and also transform their cam on or off prior to telephoning. Google's user-friendly control can scroll through video streams of speaking individuals, as well as advise you that you are mute if you talk without switching on your microphone. Beneficial attributes consist of presenting the 10 most active participants along with the ability to send out text messages by means of the interface. Zoom Fulfilling offers you information concerning the connection of all participants in the call.
Nevertheless, the business has responded quickly by adding waiting space functionality so participants can be screened plus added verification and also security actions. Microsoft Teams is an all-in-one workstream partnership service which incorporates with Office365. With numerous organizations already using O365, Groups becomes an appealing option as it enables durable interior cooperation, back-ups, and documents share. On the various other hand, Zoom is an attractive choice for external partnerships.
For instance, during a current tiny group telephone call, among my individuals linked from a mobile device using 4G. When his link was secure, I saw a collection of white bars suggesting the toughness of his connection in the reduced left edge of his video. Zoom Satisfying has an one-of-a-kind participant reporting function that checks all participants that reported throughout the conference. Google recently revealed that it will certainly enable free access to numerous video conferencing and communication tools for schools and also companies till September 30, 2020, which relates to all G Suite consumers worldwide. Microsoft lately facilitated the screening of Groups and also their different functions during the pandemic.
It is fascinating to note the convenience with which the workers have used the system and browsed via it on their own," states B. Ghosh, CIO, enterprise as well as corp functions, Mahindra Team, which has been making use of Microsoft Teams because the lockdown started in March. Ms. Jenelle says there's a performative element to videoconferencing, which includes in her very own exhaustion. She really feels as though she always needs to be "on" while joining a virtual meetings, given that she understands other people are watching her.
While there is some function overlap between the solutions, every one has its own specialized. This file will certainly aid assist you to the best device for your needs. Teams aids organisations to interact more effectively through team chat, on the internet meetings, calling, and also web conferencing.
The VP doesn't mention Zoom by name, but this seems an initiative by Microsoft to promote Teams as a safer, much more protected alternative to Zoom. The Redmond firm says it logged 200 million meeting participants in someday this month. Teams is consisted of with Microsoft 365 memberships for companies, and firms need to upgrade to greater versions of those strategies to unlock advanced functions of the program, such as video telephone calls.
It's likewise protection against Zoom-crashing harassers, as well as it's good that the firm is moving in this direction. Zoom claimed it's now concentrating a lot more on its safety as well as re-evaluating the balance in between protection as well as simplicity of usage. While Skype's Meet Now supplies a grid sight, Zoom lets you see approximately 49 people simultaneously, in sets of huge 5x5 grids (attempting to figure it out? Right here's just how to see everyone on Zoom).
The business states you can call your local Microsoft companion or sales agent as well as secure free access to Office 365 E1 prepare for a duration of 6 months. For institutions and establishments, the Workplace 365 will stay complimentary to all.
We provide reducing edge, tailored IT options as well as IT support and maintenance to ensure your organisation IT set-up is as efficient, reliable, and fast as possible. Connect with us to learn more regarding our solutions or to arrange a consultation with among our knowledgeable IT experts. Group video, screen sharing, and also telephone calls are still limited to teams of 20 or fewer. So go on, begin planning that shock workplace party with the new, larger team conversation. Whether in the space or across a sea, Groups as well as the Microsoft Surface area Hub interact to improve conferences for neighborhood and remote attendees.
Is Microsoft Team free?
The free version of Microsoft Teams only allows you to have up to 300 members (users) per organization. Paid plans, meanwhile, up that up to a potentially unlimited amount of members, with an enterprise license.
A guide to requirements as well as functions of the leading three video clip conferencing apps. To date, Zoom, Microsoft Teams and also Cisco Webex have outweighed Google Meet and its predecessor brands, amongst businesses and companies. Introduced in 2017 as Hangouts Meet, it included a videoconferencing extension of the Google Hangouts conversation and also voice communications device. It has actually preserved a solid following among pupils and also for customers.
They can simply develop a web link and send it to loved ones as an invitation to join the video clip telephone call. The participants open the web link in Microsoft Side or Google Chrome, and also they are "in" the call. In this Vlog we take a look at Zoom vs Microsoft Teams to identify the most effective alternative for video conferencing. K2 Technologies is aMicrosoft Workplace 365 Partnerwith almost twenty years of experience assisting businesses make use of modern technology to its fullest potential.
Microsoft assumes individuals who prepare trips with friends or organize book clubs and also social gatherings will be interested in Teams. Alexa ranking https://mnetworks.dk/om-os-2/social-ansvarlighed-csr/ 21 (As of 22 April 2020 [update] Zoom Video Clip Communications, Inc. (Zoom) is an American communications modern technology company headquartered in San Jose, The Golden State. It provides videotelephony and also online chat solutions via a cloud-based peer-to-peer software application system as well as is utilized for teleconferencing, telecommuting, correspondence course, and social relationships. If your video clip gets on during a conference with several participants, it instantly presents to all individuals, including on your own. If you hide on your own, your own video clip screen disappears from your display, leaving even more room to see other participants.
Among the best features of this is that it sustains as much as 250 participants in a telephone call, that makes it useful for big conferences. You can additionally live-stream conferences to up to 100,000 people, helpful for bigger ventures attempting to reach huge groups. The base prepare for Zoom consists of a host limitation of 100 individual, endless 1 to 1 conferences and team conferences yet a 40-minute limit on conferences with 3 or even more individuals in them. Shutterstock is another popular graphics web site giving free backgrounds to personalize Zoom and also Skype telephone calls.
It's additionally worth noting that cloud storage space is limited, so be careful how many conferences you document while utilizing the mobile app. The business has made several moves to counter these problems and also assure users about the value of protection and also privacy. This includes basic points like removing the conference ID from the title bar of the phone call so if customers share screenshots on-line the meeting isn't revealed to future misuse. If your system manager has a Pro, Business, or Venture account, you can authorize up and download Zoom onto your computer system using your work email.
Furthermore, it has to be stated that Groups takes rather a great deal of time to set up, so bear that in mind. Microsoft Teams allows you share Workplace documents and service them immediately from the work area. Slack doesn't included the option of modifying papers from the work area, so you need to download documents as well as open them in certain applications to edit them. The most important thing to recognize is that Slack's dimension restriction for submitting is 1GB, while Microsoft Teams is covered at 15GB. We really did not bother to inspect these numbers and upload gigantic files-- we were extra interested in exactly how you can collaborate in these apps.
How do you see everyone on Zoom?
Now, a report by Bleeping Computer claims that half a million Zoom accounts have been hacked and the data from these accounts have been sold on the dark web. These Zoom account credentials reportedly included email address, meeting URLs, passwords, and HostKeys.
Google has claimed it will certainly offer Hangouts components as separate customer services, such as Chat, Messages and also Duo. " Due to the fact that video conferences have never ever been more vital, we've been fast-tracking one of the most requested features for Meet, and also are currently making them offered to all," composed G Suite VP and also GM Javier Soltero in a blog. Google Meet now has a tiled gallery view with a format that currently supports 16 participants, up from just four. They can likewise now pick better video clip by switching to the 30 frameworks per-second video mode choice.
Just like in a routine Teams meetings, you can now include your system audio when offering in an online occasion. Presently, this attribute is only available for producers and presenters signing up with from the Teams desktop computer application for Windows.
No Wire Necessary-- Security & Safety And Security In A Wireless World.
allows individuals to satisfy in person from a desktop, laptop, mobile device or video clip conferencing endpoint. It utilizes the trusted Cisco infrastructure and incorporates with Webex Teams as well as with various other famous suppliers such as Microsoft. Meanwhile, in Italy, service applications like Google's Hangouts Meet and also Classroom were one of the most downloaded and install of any classification of apps this week. Do you know when this feature for Microsoft Teams Room Equipments to join Webex and Zoom conferences will be released? Older Cisco rooms will certainly have the ability to join Microsoft Teams Meetings by means of Cisco's forthcoming CVI service.
To try it out in your next meeting, press Ctrl+ to zoom in as well as Ctrl- to zoom out. Create a welcome web link to invite people to join your org on Teams free by means of the app of your selection. When they click on the web link they'll be sent out to a webpage to demand to join your org-- so you know specifically that's utilizing the web link to join.
Microsoft is additionally coming out with versions of Teams for personal and also family usage. Microsoft has seen a 775 percent rise in cloud solutions across areas that have implemented social distancing because of COVID-19.
Is Zoom owned by Google?
Microsoft originally acquired Skype for $8.5 billion back in 2011. It was the same year that Zoom and Snapchat were founded, and Apple launched its iPhone 4S.
IT specialists can likewise access Microsoft Teams also if their firm is not certified for Groups. They can call their Microsoft companion or sales representatives for free access to the Workplace 365 E1 plan for 6 months.
So, we decided to submit an 800MB video clip documents in Microsoft Teams to give it a shot. To our surprise, the documents not just opened promptly yet likewise played within Microsoft Teams-- very impressive. It's even more budget-friendly than Slack or Microsoft Teams while providing advanced attributes such as endless message history and also sound and also video clip calls. To cut the story short, the least expensive Workplace 365 Strategy that has Teams in it is called Service Basics. It costs $5 per user per month and you need to buy a yearly strategy to get going.
Within this contrast, I want to look closer at both what these tools supply, however how the tools and also their organization result in an inevitably various platform emphasis. As an example, Microsoft Teams appears to master Office 365 based cooperation, meanwhile, Webex Teams is an incredible virtual conference system with digital whiteboarding, in addition to a concentrate on equipment. But it is essential to acknowledge what solutions as well as Office applications your service get to based upon the strategy selected. As an example, even the Free offering of Microsoft Teams provides access to shadow variations of preferred Workplace Apps, however none other services or downloadable versions of the software application. With more individuals, even more files, more conferences, more cooperation, a lot more video clip meetings, more whatever; larger companies merely need the tools to deal with and also facilitate this higher degree of cooperation and emphasis.
What is the difference between zoom and teams?
Through the Microsoft Teams Zoom Meetings tab, you will be able to start, schedule, join meetings, or share your screen. Meetings created in Teams will automatically appear on your Zoom account. This article covers installing, configuring and using the Zoom integration for Microsoft Teams.
It's a little on the expensive side but they just recently expanded their product to currently supply display sharing and also video conferencing. Google Hangouts is our pick for best video conferencing software application for small teams. The web video clip variation is called Google Hangouts as well as is what our group makes use of at We Rock Your Internet. When it comes to on the internet conference solutions, we contrast the ideal video conferencing software application and also review why some of the most identifiable companies might not be your finest option.
This is in fact cheaper than Slack's most affordable strategy (Conventional), which costs $6.67 per individual per month when billed every year. It makes the price much extra eye-catching when you take into consideration the truth that $5 invested on Microsoft Teams additionally provides you access to Workplace 365. Nonetheless, if you intend to get the most out of Microsoft Teams and also Slack, you'll need to obtain a paid strategy. In Microsoft Tools, that suggests that you require to have an account that is either Business Premium or Essentials.
As preferred and as useful Zoom has been for many organisations, the safety and personal privacy elements are still not there. Microsoft Teams transcends in the feeling that due to it's association with Office 365, there are added methods to increase your standard protection. Password freshens, credibility symbols and 2 element verification process-- Zoom just can not compete with these extra levels of safety.
According to Microsoft, people in Norway and also the Netherlands turn on video clip as well as use it the most, with about 60% of conferences in the country including video clip. Right here in the United States, the number is about 38%, and in the UK, it has to do with 47%. Microsoft Teams currently has attributes that assist make video talking easier, and extra get on the means. That currently includes history blur, which helps conceal your background during a telephone call.
You can manage whether to hide or reveal yourself in your own video clip display screen for each conference. As an existing Skype for Organisation client, the full shift to Groups may take a little time. Thankfully, the overlapping capabilities of both apps imply you do not need to do it at one time-- there are a couple of different conjunction as well as upgrade settings to consider when selecting your personal course to migration. Although Groups takes much of its DNA from Skype for Business, both are really various solutions. When you placed them side-by-side-- Microsoft Teams vs Skype for Service-- you'll see that Teams provides a lot more, bringing together files, talks, and also applications in one area for a much more full, integrated cooperation remedy.
Why is teams better than Skype?
According to a recent Forrester study, shared workspaces like Teams can save users time—from one to eight hours per user per week, depending on their role. The wins from making the Skype for Business upgrade to Teams are clear: faster, more efficient working and collaboration.
Though Microsoft Teams as well as Skype for Organisation does differ, there is some considerable overlap. Both Skype for Company as well as Microsoft Teams include team chats, straight messaging, and voice calling. Though Microsoft Teams initially really did not have the calling capability that Skype did, it still had both voice chat and video clip calling functionality.
After that you ought to leave the conference, if you're not using Skype to meet with a person. Then it won't utilize a lot information and also you don't need to bother with the video/audio quality while you're not in a conference. Webex has unrestricted free meetings for up to 3 individuals and offers the premium includes complimentary for 2 week.
Still, it's improving all the time, and is certainly something to try if you are taking a look at an alternative to Zoom. Jitsiis a extremely cool and safe open resource app that's recently launched to the marketplace.
As several churches relied on Zoom for live-streaming, Sunday morning ended up being prime-time show for a vital group of Zoom individuals. The largest customer of teleconferencing is India Inc, which began its fiscal and also established targets with a flurry of web conferences. " We have done greater than 350,000 conferences, greater than 60 events with hundreds of individuals in each.
For large range company meetings with coworkers or calls with numerous good friends, Zoom for desktop is the only sensible choice. Free Zoom supplies video conferencing for approximately 100 individuals, supplied the conference competes no more than 40 mins, at which point guests are ejected from the meeting. If you don't mind the headache of dialling back in, though, the host can merely begin another telephone
1 note
·
View note
Photo

hydralisk98′s web projects tracker:
Core principles=
Fail faster
‘Learn, Tweak, Make’ loop
This is meant to be a quick reference for tracking progress made over my various projects, organized by their “ultimate target” goal:
(START)
(Website)=
Install Firefox
Install Chrome
Install Microsoft newest browser
Install Lynx
Learn about contemporary web browsers
Install a very basic text editor
Install Notepad++
Install Nano
Install Powershell
Install Bash
Install Git
Learn HTML
Elements and attributes
Commenting (single line comment, multi-line comment)
Head (title, meta, charset, language, link, style, description, keywords, author, viewport, script, base, url-encode, )
Hyperlinks (local, external, link titles, relative filepaths, absolute filepaths)
Headings (h1-h6, horizontal rules)
Paragraphs (pre, line breaks)
Text formatting (bold, italic, deleted, inserted, subscript, superscript, marked)
Quotations (quote, blockquote, abbreviations, address, cite, bidirectional override)
Entities & symbols (&entity_name, &entity_number,  , useful HTML character entities, diacritical marks, mathematical symbols, greek letters, currency symbols, )
Id (bookmarks)
Classes (select elements, multiple classes, different tags can share same class, )
Blocks & Inlines (div, span)
Computercode (kbd, samp, code, var)
Lists (ordered, unordered, description lists, control list counting, nesting)
Tables (colspan, rowspan, caption, colgroup, thead, tbody, tfoot, th)
Images (src, alt, width, height, animated, link, map, area, usenmap, , picture, picture for format support)
old fashioned audio
old fashioned video
Iframes (URL src, name, target)
Forms (input types, action, method, GET, POST, name, fieldset, accept-charset, autocomplete, enctype, novalidate, target, form elements, input attributes)
URL encode (scheme, prefix, domain, port, path, filename, ascii-encodings)
Learn about oldest web browsers onwards
Learn early HTML versions (doctypes & permitted elements for each version)
Make a 90s-like web page compatible with as much early web formats as possible, earliest web browsers’ compatibility is best here
Learn how to teach HTML5 features to most if not all older browsers
Install Adobe XD
Register a account at Figma
Learn Adobe XD basics
Learn Figma basics
Install Microsoft’s VS Code
Install my Microsoft’s VS Code favorite extensions
Learn HTML5
Semantic elements
Layouts
Graphics (SVG, canvas)
Track
Audio
Video
Embed
APIs (geolocation, drag and drop, local storage, application cache, web workers, server-sent events, )
HTMLShiv for teaching older browsers HTML5
HTML5 style guide and coding conventions (doctype, clean tidy well-formed code, lower case element names, close all html elements, close empty html elements, quote attribute values, image attributes, space and equal signs, avoid long code lines, blank lines, indentation, keep html, keep head, keep body, meta data, viewport, comments, stylesheets, loading JS into html, accessing HTML elements with JS, use lowercase file names, file extensions, index/default)
Learn CSS
Selections
Colors
Fonts
Positioning
Box model
Grid
Flexbox
Custom properties
Transitions
Animate
Make a simple modern static site
Learn responsive design
Viewport
Media queries
Fluid widths
rem units over px
Mobile first
Learn SASS
Variables
Nesting
Conditionals
Functions
Learn about CSS frameworks
Learn Bootstrap
Learn Tailwind CSS
Learn JS
Fundamentals
Document Object Model / DOM
JavaScript Object Notation / JSON
Fetch API
Modern JS (ES6+)
Learn Git
Learn Browser Dev Tools
Learn your VS Code extensions
Learn Emmet
Learn NPM
Learn Yarn
Learn Axios
Learn Webpack
Learn Parcel
Learn basic deployment
Domain registration (Namecheap)
Managed hosting (InMotion, Hostgator, Bluehost)
Static hosting (Nertlify, Github Pages)
SSL certificate
FTP
SFTP
SSH
CLI
Make a fancy front end website about
Make a few Tumblr themes
===You are now a basic front end developer!
Learn about XML dialects
Learn XML
Learn about JS frameworks
Learn jQuery
Learn React
Contex API with Hooks
NEXT
Learn Vue.js
Vuex
NUXT
Learn Svelte
NUXT (Vue)
Learn Gatsby
Learn Gridsome
Learn Typescript
Make a epic front end website about
===You are now a front-end wizard!
Learn Node.js
Express
Nest.js
Koa
Learn Python
Django
Flask
Learn GoLang
Revel
Learn PHP
Laravel
Slim
Symfony
Learn Ruby
Ruby on Rails
Sinatra
Learn SQL
PostgreSQL
MySQL
Learn ORM
Learn ODM
Learn NoSQL
MongoDB
RethinkDB
CouchDB
Learn a cloud database
Firebase, Azure Cloud DB, AWS
Learn a lightweight & cache variant
Redis
SQLlite
NeDB
Learn GraphQL
Learn about CMSes
Learn Wordpress
Learn Drupal
Learn Keystone
Learn Enduro
Learn Contentful
Learn Sanity
Learn Jekyll
Learn about DevOps
Learn NGINX
Learn Apache
Learn Linode
Learn Heroku
Learn Azure
Learn Docker
Learn testing
Learn load balancing
===You are now a good full stack developer
Learn about mobile development
Learn Dart
Learn Flutter
Learn React Native
Learn Nativescript
Learn Ionic
Learn progressive web apps
Learn Electron
Learn JAMstack
Learn serverless architecture
Learn API-first design
Learn data science
Learn machine learning
Learn deep learning
Learn speech recognition
Learn web assembly
===You are now a epic full stack developer
Make a web browser
Make a web server
===You are now a legendary full stack developer
[...]
(Computer system)=
Learn to execute and test your code in a command line interface
Learn to use breakpoints and debuggers
Learn Bash
Learn fish
Learn Zsh
Learn Vim
Learn nano
Learn Notepad++
Learn VS Code
Learn Brackets
Learn Atom
Learn Geany
Learn Neovim
Learn Python
Learn Java?
Learn R
Learn Swift?
Learn Go-lang?
Learn Common Lisp
Learn Clojure (& ClojureScript)
Learn Scheme
Learn C++
Learn C
Learn B
Learn Mesa
Learn Brainfuck
Learn Assembly
Learn Machine Code
Learn how to manage I/O
Make a keypad
Make a keyboard
Make a mouse
Make a light pen
Make a small LCD display
Make a small LED display
Make a teleprinter terminal
Make a medium raster CRT display
Make a small vector CRT display
Make larger LED displays
Make a few CRT displays
Learn how to manage computer memory
Make datasettes
Make a datasette deck
Make floppy disks
Make a floppy drive
Learn how to control data
Learn binary base
Learn hexadecimal base
Learn octal base
Learn registers
Learn timing information
Learn assembly common mnemonics
Learn arithmetic operations
Learn logic operations (AND, OR, XOR, NOT, NAND, NOR, NXOR, IMPLY)
Learn masking
Learn assembly language basics
Learn stack construct’s operations
Learn calling conventions
Learn to use Application Binary Interface or ABI
Learn to make your own ABIs
Learn to use memory maps
Learn to make memory maps
Make a clock
Make a front panel
Make a calculator
Learn about existing instruction sets (Intel, ARM, RISC-V, PIC, AVR, SPARC, MIPS, Intersil 6120, Z80...)
Design a instruction set
Compose a assembler
Compose a disassembler
Compose a emulator
Write a B-derivative programming language (somewhat similar to C)
Write a IPL-derivative programming language (somewhat similar to Lisp and Scheme)
Write a general markup language (like GML, SGML, HTML, XML...)
Write a Turing tarpit (like Brainfuck)
Write a scripting language (like Bash)
Write a database system (like VisiCalc or SQL)
Write a CLI shell (basic operating system like Unix or CP/M)
Write a single-user GUI operating system (like Xerox Star’s Pilot)
Write a multi-user GUI operating system (like Linux)
Write various software utilities for my various OSes
Write various games for my various OSes
Write various niche applications for my various OSes
Implement a awesome model in very large scale integration, like the Commodore CBM-II
Implement a epic model in integrated circuits, like the DEC PDP-15
Implement a modest model in transistor-transistor logic, similar to the DEC PDP-12
Implement a simple model in diode-transistor logic, like the original DEC PDP-8
Implement a simpler model in later vacuum tubes, like the IBM 700 series
Implement simplest model in early vacuum tubes, like the EDSAC
[...]
(Conlang)=
Choose sounds
Choose phonotactics
[...]
(Animation ‘movie’)=
[...]
(Exploration top-down ’racing game’)=
[...]
(Video dictionary)=
[...]
(Grand strategy game)=
[...]
(Telex system)=
[...]
(Pen&paper tabletop game)=
[...]
(Search engine)=
[...]
(Microlearning system)=
[...]
(Alternate planet)=
[...]
(END)
4 notes
·
View notes
Text
What you Should Know about Cyber Security
Cyber security is that the state or process of protecting and recovering networks, devices and programs from any sort of cyber-attack.
Cyber-attacks are an evolving danger to organizations, employees and consumers. They’ll be designed to access or destroy sensitive data or extort money. They can, in effect, destroy businesses and damage your financial and private lives — especially if you’re the victim of fraud. Cyber security vs. computer security vs. IT security
As mentioned above, cyber security is that the practice of defending your electronic systems, networks, computers, mobile devices, programs and data from malicious digital attacks. Cyber criminals can initiate a spread of attacks against any individual or a whole business which could include accessing, changing or deleting important data; extortion for stolen Data; or manipulating business processes. How is cyber security achieved? By this infrastructure that’s composed of 3 components: IT security, cyber security, and computer security.
• Information technology (IT) security, also called electronic information security, is Data Protection both at its stored locations and while transferring through networks. As cyber security only protects digital data, IT security is good for both digital and physical data.
• Cyber security may be a subset of IT security. While IT security protects both physical and digital data, cyber security protects the digital data on your networks, computers and devices from unauthorized access, attack and destruction.
• Network security, or computer security, may be a subset of cyber security. This type of security focuses on hardware and software to protect data that’s sent from your computer to other devices of the network. Network security guard the IT infrastructure from being intercepted so that Data is not altered or stolen by cybercriminals.
Types of cyber security In order to be better protected, it’s important to understand the various sorts of cyber security. These include data loss prevention, end-user education, cloud security, information security, critical infrastructure security, network security and application security,
Critical infrastructure security: Consists of physical systems for example an electricity grid and water purification systems.
Network security: Protects the internal networks from any intruders by securing the infrastructure. Samples of network security include the implementation of two-factor authentication (2FA) and new, strong passwords.
Application security: Uses Hardware and Software to defend against any threat which may present it selves in the application’s development stage. Examples of application security include encryptions like passwords, Firewalls and antivirus programs
Information security: Also called to as InfoSec, protects physical and digital data—essentially data in any form—from unauthorized access, use, change, disclosure, deletion, or other sorts of militant. Cloud security: A software-based tool that protects and monitors your data within the cloud, to assist eliminate the risks related to on-premises attacks.
Data loss prevention: Consists of creating policies and processes for managing and preventing the Data Loss, and make recovery policies in case of a cyber-security breach. This includes implementing network permissions and policies for data storage.
End-user education: Acknowledges that cyber security systems are only as strong as their potentially weakest links: the folks that are using them. End-user education involves the users to follow best the most recommended practices like not clicking unknown links or downloading suspicious files in emails—which could infect their systems with malware and other sorts of malicious software. Types of cyber threats There are many sorts of cyber-threats which will attack your devices and networks, but they typically fall under three categories. These are attacks on confidentiality, integrity and availability.
• Attacks on confidentiality. These attacks are often designed to steal your personal identifying information and your checking account or MasterCard information. Following these attack, your information are often sold or traded on the dark web for others to get and use.
• Attacks on integrity. These attacks contains personal or enterprise sabotage, and are often called leaks. A cybercriminal will access and release sensitive information for the aim of exposing the info and influencing the general public to lose trust during a person or a corporation.
• Attacks on availability. The aim of this sort of cyber-attack is to dam users from accessing their own data until they pay a fee or ransom. Most of the time, a cybercriminal will penetrate a network from accessing important data, and demand ransom be paid. Sometimes Companies pay the ransom and after fix the cyber vulnerability in order to avoid halting business activities. Pay the ransom and fix the cyber vulnerability afterward in order that they will avoid halting business activities.
Here are a couple of sorts of cyber threats that fall under the three categories listed above.
Social engineering, a type of attack on confidentiality, is that the process of psychologically manipulating people directly into performing certain actions. Phishing attacks are the foremost common sort of social engineering. Phishing attacks usually are available the shape of a deceptive email with the goal of tricking the recipient into making a gift of personal information. APTs (advanced persistent threats), a kind of attack on integrity, where an unauthorized user infiltrates a network undetected and stays within the network for an extended time. The intent of any APT is to steal data silently without any harm the network. APTs often happen in sectors with high-value information, like national defense, manufacturing, and therefore the finance industry.
These are the Basics of Cyber Security. And you this is all the know one person may need to have to identify if any cyber-attack occurs but solving such issues takes more professional knowledge and experience if you have faced any of the above mentioned issues then it is more recommended to hire a professional Cyber security Specialist as an employee or for occasional issues hire a Cyber security New Jersey Provider with can be much cheaper as your issues are not regular.
1 note
·
View note
Text
Icedrive vs sync

ICEDRIVE VS SYNC PDF
ICEDRIVE VS SYNC INSTALL
Which is what the ultimate advantage of cloud storage is in the first place. All the changes you make on the drive will be recognized and applied to all your other devices and the website dashboard. You can at any time add, edit and delete the files from the Drive. It creates an imaginary drive to which you can save your files and the best part about it: It doesn’t take up any of your local storage capacity (which is basically what selective sync does with Dropbox) unless you save the files specifically for offline usage.
ICEDRIVE VS SYNC INSTALL
It is a client-side application that you install on your computer. PCloud Drive is available on Windows, Mac and Linux. With slightly different structures and menus, there’s nothing that steals the show from another. They have eliminated most of the bugs and quirks in regards to the interface and are both fairly easy to use. You can also listen to music and watch videos.īoth pCloud and Dropbox have been around for quite some time.
ICEDRIVE VS SYNC PDF
PCloud allows you to preview text and pdf files directly in the dashboard. The interface feels responsive and seems to be able to cope with whatever you set out to do. On the left, you’re also presented with a menu that forwards you to other options such as the Crypto folder, Shared files and Audio files for fast access. Uploading, sharing, collaborating, downloading and all other tasks are easy to execute with buttons being on appropriate and logical places. You can switch between the list and grid view. It has an interface that’s quite simple and easy to use. The ability to pay once for cloud storage and not worry about monthly payments seems pretty great to me. The unique lifetime plans make them a very interesting option to look at from that perspective. Their monthly plans are also cheaper in comparison to Dropbox. A 10 days money-back guarantee is placed on all plans.īoth pCloud and Dropbox offer a wide array of pricing plans and yet pCloud manages to stay ahead with a lot bigger chunk of free storage. They certainly made it to my “ Best lifetime cloud storage plans” article.Īlongside the standard plans, they also offer additional protection for your files under their Crypto plan. You can also go with lifetime family plans. That’s right, for a one-time payment you receive 500GB or 2000GB of cloud storage for 99 years or until you die, whichever is shorter! They were the first cloud storage to bring this to the market a few years ago and it seems like it is working out for them and the customers. Like all the other cloud storages they also offer the monthly plans which you can pay yearly to get a discount on the whole thing. You can get up to 10 GB of storage completely for free.

0 notes
Text
Consumer IoT vs. Industrial IoT: Understanding the Differences
The Internet of Things (IoT) has rapidly become an integral part of our daily lives, influencing everything from the way we live to how industries operate. Broadly, IoT can be categorized into two main segments: Consumer IoT (CIoT) and Industrial IoT (IIoT). While both fall under the IoT umbrella, they serve distinct purposes, have different applications, and present unique challenges. This article aims to delineate the primary differences between CIoT and IIoT.
1. Purpose and Application
Consumer IoT (CIoT): CIoT primarily focuses on enhancing the quality of life for individuals. It encompasses devices and systems designed for personal use or for a home environment. Examples include smart thermostats, wearable fitness trackers, connected appliances, and home security systems. These devices aim to provide convenience, entertainment, and personal well-being.
Industrial IoT (IIoT): IIoT, on the other hand, is tailored for industrial applications. It's about optimizing processes, enhancing productivity, and reducing costs. IIoT is prevalent in sectors like manufacturing, agriculture, energy, and transportation. Examples include predictive maintenance sensors, industrial robots, and smart grid technologies.
2. Scale and Complexity
Consumer IoT: CIoT devices are generally standalone or operate within a small network, like a home automation system. They're designed for ease of use, with user-friendly interfaces and straightforward functionalities.
Industrial IoT: IIoT systems are more complex, often involving large-scale deployments with thousands of interconnected devices working in tandem. These systems require sophisticated data analytics platforms and robust network architectures to manage and process the vast amounts of data they generate.
3. Connectivity and Interoperability
Consumer IoT: CIoT devices typically connect via standard home Wi-Fi networks or through cellular networks. Interoperability can be a challenge, as many consumer devices are designed to function within a specific ecosystem or brand.
Industrial IoT: IIoT devices often use specialized communication protocols suited for industrial environments, such as MQTT or CoAP. Given the need for seamless integration in industrial settings, there's a stronger emphasis on standardization and interoperability in IIoT.
4. Security Concerns
Consumer IoT: Security is a significant concern for CIoT, as many consumer-grade devices have been found to have vulnerabilities. These devices, if not properly secured, can become entry points for cyberattacks on personal networks.
Industrial IoT: The stakes are even higher for IIoT, where a security breach can lead to significant financial losses, operational downtime, or even safety concerns. As a result, IIoT solutions often incorporate advanced security measures, including end-to-end encryption and regular security audits.
5. Data Processing and Analysis
Consumer IoT: Most CIoT devices generate data pertinent to individual users, which is often processed on the device itself or in a cloud environment. The focus is typically on real-time feedback and personal insights.
Industrial IoT: IIoT devices generate vast amounts of data that require advanced analytics tools for processing. The data is used for predictive analysis, trend forecasting, and operational optimization. Often, edge computing is employed to process data on-site, reducing latency and ensuring timely decision-making.
6. Lifecycle and Durability
Consumer IoT: Consumer devices are often designed with a shorter lifecycle in mind, given the rapid pace of technological advancements in the consumer electronics sector.
Industrial IoT: Industrial devices, given their critical nature, are built for longevity. They are rugged, designed to withstand harsh environments, and can function optimally for years without requiring replacement.
Conclusion
While both Consumer IoT and Industrial IoT aim to leverage the power of interconnected devices, their applications, challenges, and requirements differ significantly. Understanding these differences is crucial for businesses, policymakers, and consumers alike as the world continues to embrace the myriad possibilities offered by IoT. As the IoT landscape evolves, the demarcation between CIoT and IIoT will become even more pronounced, each serving its unique purpose in the grander scheme of digital transformation.
0 notes
Text
Architecture cloud computing diagram Architecture asset management digital cloud aws based diagram solution infrastructure software
If you are searching about Cloud computing – SMR you've visit to the right page. We have 9 Images about Cloud computing – SMR like Cloud computing – SMR, Cloud Computing Architecture: Front-end & Back-end and also Atlassian cloud architecture | Atlassian Cloud | Atlassian Documentation. Here you go:
Azure stack offers hybrid cloud on your terms
Cloud Computing – SMR

www.smrinfo.co.in
What is private cloud computing?. Azure stack offers hybrid cloud on your terms. Cloud computing architecture: front-end & back-end. What is selenium grid ?. Atlassian cloud architecture confluence jira footprint distribution global. Vmware cloud private virtualization computing structure using architecture server infrastructure inspirationseek via management. Cloud computing – smr. Cloud computing services service benefits infrastructure business benefit software data sarv advantages iaas security flexibility storage automatic maintenance meaning need. Azure stack microsoft cloud architecture hybrid paas data computing services service iaas offers terms web windows vs development platform network. Cloud computing architecture saas vs premise end front simplilearn based software does understanding jul updated last
Azure Stack Offers Hybrid Cloud On Your Terms | CIO

www.cio.com
azure stack microsoft cloud architecture hybrid paas data computing services service iaas offers terms web windows vs development platform network
Vmware cloud private virtualization computing structure using architecture server infrastructure inspirationseek via management. Cloud infrastructure overview diagram isc architecture application upenn user case applications use path native. Cloud computing is an opportunity for your business. Cloud computing architecture: front-end & back-end. Cloud infrastructure overview. Selenium grid diagram nodes testingdocs architecture below example. Azure stack offers hybrid cloud on your terms. What is selenium grid ?. Cloud based reference architecture, cloud based digital asset. Cloud computing – smr
Cloud Infrastructure Overview | UPenn ISC

www.isc.upenn.edu
cloud infrastructure overview diagram isc architecture application upenn user case applications use path native
Architecture asset management digital cloud aws based diagram solution infrastructure software. Selenium grid diagram nodes testingdocs architecture below example. Cloud computing is an opportunity for your business. Cloud infrastructure overview. Cloud based reference architecture, cloud based digital asset. Azure stack offers hybrid cloud on your terms. Cloud computing services service benefits infrastructure business benefit software data sarv advantages iaas security flexibility storage automatic maintenance meaning need. What is private cloud computing?. Cloud computing architecture saas vs premise end front simplilearn based software does understanding jul updated last. Cloud computing architecture: front-end & back-end
Atlassian Cloud Architecture | Atlassian Cloud | Atlassian Documentation

confluence.atlassian.com
atlassian cloud architecture confluence jira footprint distribution global
Cloud infrastructure overview diagram isc architecture application upenn user case applications use path native. Azure stack microsoft cloud architecture hybrid paas data computing services service iaas offers terms web windows vs development platform network. Atlassian cloud architecture confluence jira footprint distribution global. What is private cloud computing?. Selenium grid diagram nodes testingdocs architecture below example. Atlassian cloud architecture. Cloud based reference architecture, cloud based digital asset. What is selenium grid ?. Cloud computing – smr. Cloud computing is an opportunity for your business
What Is Selenium Grid ? | TestingDocs

www.testingdocs.com
selenium grid diagram nodes testingdocs architecture below example
Cloud infrastructure overview diagram isc architecture application upenn user case applications use path native. Atlassian cloud architecture confluence jira footprint distribution global. Architecture asset management digital cloud aws based diagram solution infrastructure software. What is selenium grid ?. Cloud computing architecture: front-end & back-end. What is private cloud computing?. Cloud based reference architecture, cloud based digital asset. Cloud infrastructure overview. Azure stack microsoft cloud architecture hybrid paas data computing services service iaas offers terms web windows vs development platform network. Azure stack offers hybrid cloud on your terms
What Is Private Cloud Computing? - InspirationSeek.com

inspirationseek.com
vmware cloud private virtualization computing structure using architecture server infrastructure inspirationseek via management
Atlassian cloud architecture confluence jira footprint distribution global. Cloud computing architecture: front-end & back-end. Vmware cloud private virtualization computing structure using architecture server infrastructure inspirationseek via management. Azure stack offers hybrid cloud on your terms. Cloud computing architecture saas vs premise end front simplilearn based software does understanding jul updated last. Atlassian cloud architecture. Cloud computing is an opportunity for your business. Cloud infrastructure overview. Cloud computing – smr. What is private cloud computing?
Cloud Computing Is An Opportunity For Your Business - Sarv Blog

blog.sarv.com
cloud computing services service benefits infrastructure business benefit software data sarv advantages iaas security flexibility storage automatic maintenance meaning need
Azure stack offers hybrid cloud on your terms. Cloud infrastructure overview. What is private cloud computing?. Cloud computing – smr. Cloud computing architecture saas vs premise end front simplilearn based software does understanding jul updated last. Azure stack microsoft cloud architecture hybrid paas data computing services service iaas offers terms web windows vs development platform network. Atlassian cloud architecture confluence jira footprint distribution global. Selenium grid diagram nodes testingdocs architecture below example. Cloud infrastructure overview diagram isc architecture application upenn user case applications use path native. Cloud based reference architecture, cloud based digital asset
Cloud Based Reference Architecture, Cloud Based Digital Asset

www.pinterest.com
architecture asset management digital cloud aws based diagram solution infrastructure software
Atlassian cloud architecture. Vmware cloud private virtualization computing structure using architecture server infrastructure inspirationseek via management. What is selenium grid ?. Cloud computing architecture saas vs premise end front simplilearn based software does understanding jul updated last. Cloud based reference architecture, cloud based digital asset. Azure stack offers hybrid cloud on your terms. Cloud computing services service benefits infrastructure business benefit software data sarv advantages iaas security flexibility storage automatic maintenance meaning need. Atlassian cloud architecture confluence jira footprint distribution global. Cloud infrastructure overview diagram isc architecture application upenn user case applications use path native. Architecture asset management digital cloud aws based diagram solution infrastructure software
Cloud Computing Architecture: Front-end & Back-end

www.simplilearn.com
cloud computing architecture saas vs premise end front simplilearn based software does understanding jul updated last
Atlassian cloud architecture confluence jira footprint distribution global. What is private cloud computing?. Vmware cloud private virtualization computing structure using architecture server infrastructure inspirationseek via management. Azure stack microsoft cloud architecture hybrid paas data computing services service iaas offers terms web windows vs development platform network. Cloud computing architecture saas vs premise end front simplilearn based software does understanding jul updated last. Cloud based reference architecture, cloud based digital asset. Cloud computing – smr. Architecture asset management digital cloud aws based diagram solution infrastructure software. Cloud computing is an opportunity for your business. Azure stack offers hybrid cloud on your terms
Azure stack microsoft cloud architecture hybrid paas data computing services service iaas offers terms web windows vs development platform network. What is private cloud computing?. Cloud infrastructure overview. Azure stack offers hybrid cloud on your terms. What is selenium grid ?
0 notes
Text
Sketch VS Figma: Which Is The Better Tool For Design
We know that people are always confused about design tools like Sketch and Figma. They are all different tools, but you can use both for layout. Let's try to explain these two tools and their functions.
Sketch
The sketch is a vector graphics editor for macOS discovered by the Dutch company Sketch. It was first delivered on September 7, 2010, and won the Apple Design Award in 2012. It was originally used by designers for user interface, website, and mobile application user experience design, but does not include print layout functions. Sketch recently added features for prototyping and collaboration.
The choice is simple, and the cost is only a small part of the price of Photoshop, and Photoshop is also known for its simplicity. You do not need any training to use the drawing software, and it is also suitable for designing various equipment.
Sketch Design Tool Features
Plug-in
Recently, Taisho Georgiev released an excellent Sketch plug-in called Symbols, which allows us to copy smart objects. Smart objects allow us to have much detailed information about objects in their documents. We can easily edit any smart object. After pressing CMD + E, you can see all these changes made each time. It is also easy to download any WordPress themes, plugins, web templates, UI elements, etc.
Smart Guides
This tool supports many keyboard shortcuts, such as Smart Guides. You can just use it by holding down an object, pressing ALT, or option. Shows the space between the preferred object and the edge of the document by function. If you want to cross the distance between the selected object and another object, hover your mouse over the coveted object and it will adjust automatically.
Creating Rows And Columns
We can easily create grids, but using Sketch will be easy and manageable. Sketch has a feature called "Create Grid". You can click on the four boxes on the auxiliary toolbar to display a pop-up menu where we can decide the number of rows and columns we want to arrange the selected objects.
If we want to highlight the area around each object and the spacing between them, we select the box selection option.
Artboard Presets
We are using artboards, or Sketch has a full canvas by default. Using artboard presets is helpful. When we match the artboard button on the toolbar, we can choose to get preset from the auxiliary toolbar. Preset allows us to organize our work using predefined elements. We can use a series of artboards to create a document, so we must remember all the multiple icon sizes.
Template
The sketch can generate a new file from the template immediately via the File> New menu item. We can save contemporary files as templates to start each project from its current stage. Go to File> Save as Template to do this.
It is very useful when our team is designing for iOS. You can use the status bar or navigation bar to create a file and save it as a template.
Figma
Figma is a vector graphics editor, essentially a web-based prototyping tool, with new offline features enabled by macOS and Windows desktop applications.
Figma is suitable for any web browser, but also for Mac, Windows PC, Linux machines, and Chromebooks. It is the only design tool of its kind that uses hardware running multiple operating systems. You can quickly share, open and edit Figma files.
The Figma Mirror app for Android and iOS allows you to view Figma prototypes in real-time on your mobile device. Figma's feature set focuses on user interface and user experience design, insisting on real-time collaboration.
Design tool functions Figma
Roundtrip
In Figma, you can edit part of the frame. You can easily return to the original layout by pressing cool or keyboard shortcuts. These 9 other majors also have a common analogy.
Live Components
When we create a design system, designers sometimes use components or do things that will never be used. You need to display the components used in the project file or between files. You can list the layers or explain the clickable overlays where these components are located. A designer with the technology can easily remove the components.
Prototype Links
Today, users have to click on each link and delete them one by one. It comes with a clear all button to make the designer's job easier. The Figma browser app works with all browsers, it's easy. No need to install, patch, or update to log in to the website and start using the app.
Figma changed this concept and made popular browser applications such as Webflow or Tilda. The main advantage is that cloud storage manages all files, and unsaved files are moved to drafts.
Teamwork
The concept of teamwork and partnership is one of the directions of UI/UX design companies. In Sketch vs Figma, we can say that you follow all trends in the best way.
Allows multiple team members to use a powerful WiFi connection to work on a single project in real-time. It also comes with another collaboration feature. We can post comments directly to the file so your team can view the project remotely.
Integration and Migration
We can easily transfer all Sketch projects to the new application without losing files. The conversion is smooth and efficient. There will be no falling water droplets or bad images.
You can also combine Figma with Framer. Nowadays, code-based prototyping is becoming more and more popular among the new generation of designers.
Is Figma Sketch compatible?
Sketch and Figma: Platform and Performance
One of the biggest changes between the two tools is that Figma runs in the browser and Sketch is a desktop application for Apple computers. This brings the main benefit to Figma because it is easy to access.
Also suitable for Mac and Windows desktop applications, but requires a WiFi connection. If the designer wants to work offline, then there is a problem because the Sketch tool can use an internet connection. If you work offline, it is better to use Figma.
Sketch vs Figma: Interface
If you are using Figma for the first time, it is impossible to ignore its relationship with the Sketch interface. If you try to switch from Sketch to Figma, the upgrade is easy from a usability point of view.
When opening the Figma application, you can go to the "Recent" section of the File Explorer. There are also some preloaded files that are fully editable, or you can copy the details in these files into every new design we create. The main difference is their terminology. In Sketch, we call it Artboards, but in Figma, we call it Frames and Symbols in Sketch & Components. It's just about using words.
Sketch vs Figma: Features
Figma is characterized by their teamwork. Its most notable feature is that multiple team members can easily manage the same design project. No need to edit back and forth, all partners can instantly browse them in the tool. The biggest advantage of Figma is that it is based on the browser, so developers need to implement a project without repairing design tools. Each item has its URL, so sharing files is easy. Most of the time, designers prefer to work in Figma.
Flexibility
Figma provides some features that are considered superior to Sketch. The grid and constraints confirm the overall flexibility to create responsive and adaptive layouts. The group resizes feature can be used in Sketch but is limited to four people.
Figma has accepted traditional drawing tools and developed them using vector networks instead of paths. This means more flexibility when drawing. A wide range of third-party plugins can also easily use Figma's tools.
Figma comes with local developer and prototype transfer skills There are many plugins that combine Sketch with the most familiar tools in the industry. We discussed all the major aspects of Sketch and Figma so it is up to the person who chooses the tool. Today, most designers use both tools in their design work. It can help them focus on more details and design their work to perfection. Each designer has their own choice, so it also depends on your project.
UIUX Studio
Our design team uses these two tools in their design work. We always use the latest tools to design the best projects in the best way. It's easy for teams to work together to design websites and apps to perfection.
Do you want to create a new website or application for your business? Hire remote designers for the best results. Schedule a call or chat on Skype.
0 notes
Text
Devices , and Intel said its second-quarter performance was driven by high-performance computing and automotive demand. Revenue in both areas increased sequentially. Sales to all of the company’s end markets grew by double-digit percentages.
Smartphones amounted to about 42% of total revenue, and high-performance computing contributed about 39% of revenue.
Though Taiwan Semi continues to add capacity at a breakneck pace across its chip-manufacturing portfolio—ranging from the most advanced processors, to less sophisticated chips destined for uses such as automotive parts—executives said that the global shortage will persist into 2022. There was some good news for auto makers, as the company said it had increased capacity for such chips by 60%, which will help ease shortages in the third quarter.
But for the first time since 2019’s second quarter, Taiwan Semi’s operating income fell short of expectations, coming in at NT$145.7 billion, when analysts expected NT$150 billion. Operating income—also known as operating profit—is sometimes viewed by investors as a more accurate measure of a business’s performance because it gauges the profitability of core operations, excluding items such as interest and taxes, among other things.This is a list of the top AWS competitors. 2021 р. 7. It has over 175 fully-featured services from data centers globally. AWS Trainium will be available in 2021. By Kurt Marko December 11, 2018. c. Congratulations! You created an AWS IoT Greengrass group that is ready for use on your edge based IoT project. GPU4. AWS is offering access to its EC2 Inf1 instances, which are based on 16 Inferentia chips, available immediately. . sql. I hope this guide helped you to install the Nvidia display driver in Ubuntu Linux. . We will periodically update the list to reflect the ongoing changes across all three platforms. AMD GPUs: How do they measure up? A straight comparison between Nvidia and AMD's GPU performance figures gives AMD an apparent edge over Nvidia, with up to 11. 2020 р. An Open Source Alternative to AWS SageMaker. Megaport enables access to Hosted, Hosted VIF, and Dedicated Connections to AWS cloud through the AWS Direct Connect Service Delivery Program. “Supporting Trainium, Gaudi and Nvidia GPUs is a smart move,” Freund wrote for Forbes , “and it is consistent with AWS’s strategy of offering customers . AWS Trainium shares the same AWS Neuron SDK as AWS Inferentia, so it’s integrated with TensorFlow, PyTorch, and MXNet. 24xlarge have 32 GB GPU memory. Q: Why am I not getting NVIDIA GRID features on G3 instances using the driver downloaded from NVIDIA website in Amazon EC2? May 26, 2020 in Amazon Elastic Compute Cloud EC2 #ec2 AWS ditches Nvidia for in-house 'Inferentia' silicon. Another major announcement from AWS at re:Invent 2018 was the news that Amazon will introduce their own machine learning chip to compete with Google & IBM in TPU development. Amazon's so-called “Inferentia” chip announced on Wednesday wil. The 1650 has 896 NVIDIA CUDA Cores, a base/boost clock of 1485/1665 MHz and 4GB of GDDR5 memory running at up to 8Gbps. 14 груд. Compute wise, Amazon EC2 Inf1 instances featuring AWS Inferentia chips are now available in additional AWS regions and EC2Launch is now at v2 with a range of new features, including renaming of the administrator account. It’s the fastest way to get rolling with machine learning. Whether you're on a budget, learning about deep learning, or just want to run a prediction service, you have many affordable options in the CPU category. 2021 р. AWS has compared performance of AWS Inferentia vs. The AWS Cloud is an ideal platform to provide an agile compute environment for Artificial Intelligence and technical compute workloads that require high-performance computing (HPC) methods to accelerate discovery. Each AWS Inferentia chip contains four NeuronCores . Azure Stack vs. 0. Performance and The Edge. The cloud giant. To use the noise removal effects in Streamlabs OBS, add an “Audio Input Capture” source. . Oracle Dedicated Region is a fully managed cloud region that brings all of our cloud services into customers’ data centers in a self-contained model.
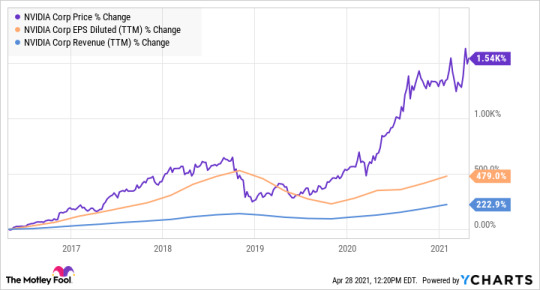
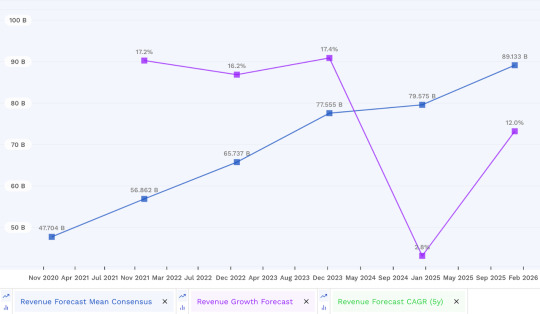

0 notes