#CreativeUpdates
Explore tagged Tumblr posts
Text

I'm officially splitting my socials into TWO accounts!
From now on, @sleepingeurydice is your go-to for: ✍️ Keeping up with my editing work and clients 📚 Tracking my works in progress or any ongoing projects 🖋️ Staying updated on my recent & ongoing publications
If you're here for the behind-the-scenes of my creative process and all things writing, this is the place to be! Follow along for more updates, insights, and inspiration.
and, @eurydiceisdead is the hub for: 🐉 Dungeons & Dragons ideas and creations 🔥 My Monster Energy rankings & rants 🎮 Updates on my game dev projects ...and so much more chaos and creativity!
If you're here for epic adventures, energy drink hot takes, and all things geeky, hit that follow button! Let’s roll the dice together.
Follow both to stay connected and experience every side of the journey! Thank you for your love and support as these spaces evolve.
#CreativeChaos#GameDevJourney#MonsterEnergyRants#DnDCreator#CreativeUpdates#EditingJourney#WorksInProgress#eurydiceisdead#sleepingeurydice#WriterLife#NewBeginnings#CreativeJourney
0 notes
Text

I'm officially splitting my socials into TWO accounts!
From now on, @sleepingeurydice is your go-to for: ✍️ Keeping up with my editing work and clients 📚 Tracking my works in progress or any ongoing projects 🖋️ Staying updated on my recent & ongoing publications
If you're here for the behind-the-scenes of my creative process and all things writing, this is the place to be! Follow along for more updates, insights, and inspiration.
and, @eurydiceisdead is the hub for: 🐉 Dungeons & Dragons ideas and creations 🔥 My Monster Energy rankings & rants 🎮 Updates on my game dev projects ...and so much more chaos and creativity!
If you're here for epic adventures, energy drink hot takes, and all things geeky, hit that follow button! Let’s roll the dice together.
Follow both to stay connected and experience every side of the journey! Thank you for your love and support as these spaces evolve.
#sleepingeurydice#eurydiceisdead#CreativeJourney#NewBeginnings#WriterLife#WorksInProgress#EditingJourney#CreativeUpdates#DnDCreator#MonsterEnergyRants#GameDevJourney#CreativeChaos
0 notes
Text
At Last...
So, friends and acquaintances...I have news for you.
The game is complete! Well, the prototype is and though it was a short rollarcoster ride, it was still a rollarcoaster ride nonetheless! I had an incredible time making this demo and though there are many many things I wish I had had the time to clean up, I am still satisfied with the result and the visual appeal of it all. To finish off I created a title scene for it, oddly enough creating the button was the hardest part of it since I couldn’t quite figure out what was meant to be plugged into where, as well as the fade animation I had for it kept looping...I couldn’t quite find a way to correct this so instead i just extended the animation duration by a minute.

0 notes
Text
Amateur Cryptojackers and Apple Macs Emerge as Two Mining Malware Trends for 2018
2017 was a big year for cryptojacking. It increased by 8,500 percent, according to figures published by Symantec in March. And it would seem that 2018 has so far been an even bigger year for mining malware, as the Cyber Threat Alliance September report revealed that, beginning on Jan. 1, cryptojacking still had room to increase by a further 500 percent.
However, beneath this simple outline of growth, there is a bigger, more complicated picture. Despite reports from some quarters showing that mining malware detections increased in the first two quarters of 2018, other reports suggest that they have in fact decreased.
And while the overall growth in mining malware since last year has been attributed to the volatility of cryptocurrency prices and the existence of software bugs, other factors have played a significant role, such as the involvement of amateur cryptojackers and the cost of mining legitimately.
Amateur cryptojackers
If there’s one dominant trend this year in the underworld of cryptojacking, it’s that most mining malware focuses on Monero. Indeed, Palo Alto Networks revealed in July that Monero accounts for 84.5 percent of all detected malware, compared to 8 percent for Bitcoin and 7 percent for other coins.
The reason for this is simple: Monero (XMR) is not only a privacy coin, but also the most valuable privacy coin by market cap — and 10th overall. Using the Cryptonight proof-of-work (PoW) algorithm, it mixes the user’s inputs with those of other users, and it also uses “ring confidential transactions” that obscure the amount of XMR being transferred. It’s therefore ideal for cybercriminals.
Monero was already the most popular coin for cryptojackers in 2017, but a number of new developments have emerged in 2018 to distinguish this year from its predecessor. Most notably, cryptojacking is increasingly becoming the province of amateur ‘hackers,’ who are lured into the illicit activity by the cheap availability of mining malware and by obvious financial rewards. According to Russian cybersecurity firm Group-IB, the dark web is “flooded with cheap mining software,” which can often be purchased for as little as $0.50.
Such software has become abundant this year: In 2017, Group-IB encountered 99 announcements regarding for-sale cryptojacking software on underground forums, while in 2018 it counted 477, signalling an increase of 381.8 percent. As the firm notes in its report:
“Low entry barrier to the illegal mining market results in a situation where cryptocurrency is being mined by people without technical expertise or experience with fraudulent schemes.”
More growth
In other words, cryptojacking has become a kind of hobbyist crime, popular among thousands of amateur hackers. This would perhaps account for why there has been a marked increase in detections this year, with Kaspersky Labs informing Cointelegraph that the number of PC cryptojacking victims increased from 1.9 million in 2016/17 to 2.7 million in 2017/18. Evgeny Lopatin — a malware analyst at Kaspersky Lab – shared:
“The mining model […] is easier to activate and more stable [than other attack vectors]. Attack your victims, discreetly build cryptocurrency using their CPU or GPU power and then transfer that into real money through legal exchanges and transactions.”
Of course, whenever “detections” are mentioned, the possibility arises that any increase is largely the result of an improvement in detection measures. “However, this is not the main driver here, as we see actual growth,” says Lopatin.
“Our analysis shows that more and more criminals increasingly use crypto miners for malicious purposes across the world.”
McAfee noted in a report from April that the vast majority of its detections were of CoinMiner, a piece of malware that surreptitiously inserts code taken from the CoinHive XMR mining algorithm into the victim’s computer. This occurs when the victim downloads an infected file from the web, but what’s new in 2018 is that such a vulnerability now affects Apple Macs as well, which had previously been regarded as much more secure than its Windows rivals.
This development was noted by United States security firm Malwarebytes, which in a May blog post reported on the discovery of a new malicious crypto miner that harnesses the legit XMRig miner. Thomas Reed, the director of Mac and mobile at the company, wrote:
“Often, Mac malware is installed by things like fake Adobe Flash Player installers, downloads from piracy sites, [and] decoy documents users are tricked into opening.”
In fact, this wasn’t the first piece of Mac mining malware it had discovered, with Reed stating that it “follows other cryptominers for macOS, such as Pwnet, CpuMeaner and CreativeUpdate.”
EternalBlue
However, while cryptojacking has become more of an amateur-driven phenomenon, it still remains the case that many of this year’s exploits can be traced to more ‘elite’ sources. Cybersecurity firm Proofpoint reported at the end of January that Smominru, a cryptojacking botnet, had spread to over half a million computers — largely thanks to the National Security Agency, which had discovered a Windows bug that was then leaked online.
This vulnerability is better known as EternalBlue, which most famously was responsible for the WannaCry ransomware attack/incident of May 2017. And according to Cyber Threat Alliance (CTA), it’s another big factor in this year’s 459 percent increase in cryptojacking.
Worryingly, the CTA’s report suggests that cryptojacking is only likely to increase as it becomes more successful and profitable:
“[Cryptojacking’s] influx of money could be used for future, more sophisticated operations by threat actor groups. For instance, several large-scale cryptocurrency mining botnets (Smominru, Jenkins Miner, Adylkuzz) have made millions of dollars.”
And things are already bad enough in the present, with the CTA writing that infection by mining malware comes with steep costs for victims.
“Taken in aggregate, when criminals install cryptocurrency miners in large enterprise networks, the costs in excess energy usage, degraded operations, downtime, repairs of machines with physical damage and mitigation of the malware in systems incurred by the victims far outweigh the relatively small amount of cryptocurrency the attackers typically earn on a single network.”
Costs
The mention of costs is significant when it comes to cryptojacking, not just for (potential) victims, but also for perpetrators. That’s because cryptojacking is essentially the theft of electricity and CPU, which implies that it will continue being prevalent not only for as long as Monero and other coins remain valuable, but also for as long as it remains expensive to mine XMR and other cryptos.
According to CryptoCompare’s profitability calculator for Monero, an individual U.S.-based miner using a graphics card capable of a 600 H/s hash rate (e.g., the Nvidia GTX 1080) and using 100W of power (a very conservative estimate) will make only $0.8033 in profit every month. This, clearly, isn’t especially promising, which is a large part of the reason why so many amateurs have turned to cryptojacking, since mining XMR while paying for your own electricity just isn’t fruitful when you’re not a big mining company.
There are, however, recent signs that Monero mining has become more profitable, even for the smaller miner. This came after its hard fork on April 6, which changed its PoW protocol so as to make it incompatible with ASIC miners, which tend to dominate mining (particularly in the case of Bitcoin).
As soon as this hard fork was completed, reports came from the Monero subreddit that profitability had increased by 300 percent or even 500 percent, although this boost was soon lost in the following weeks, according to BitInfoCharts.
Likewise, Monero itself has been cautious with regard to promising that it can resist ASIC mining equipment forever. “Thus, it is recognized that ASICs may be an inevitable development for any proof-of-work [cryptocurrency],” wrote developers dEBRYUNE and dnaleor in a February blog. “We also concede that ASICs may be inevitable, but we feel that any transition to an ASIC-dominated network needs to be as egalitarian as possible in order to foster decentralization.”
Decline?
Assuming that it has become more profitable to mine XMR legitimately, this would account for a flattening in cryptojacking growth that has been observed by some cybersecurity firms. In its Q2 2018 report, Malwarebytes revealed that mining malware detections dropped from a peak of 5 million at the beginning of March, to a low of 1.5 million at the beginning of June. This decline may contradict what other analysts have reported this year, but given that Malwarebytes’ research is the most recent in terms of the dates covered, it’s arguably the most authoritative.
It’s not clear whether this decline is the result of an increase in profitability for legit Monero miners, of business and individuals wising up to the threat of cryptojacking, or of a general decline in the value of cryptocurrencies. Regardless, Malwarebytes predict that “Cryptocurrency miners will be going out of style” as a cybersecurity threat. “Of course, we are still going to see plenty of miners being distributed and detected,” its report concludes. “However, it looks like we are at the tail end of the ‘craze.'”
window.fbAsyncInit = function() { FB.init({ appId : '1922752334671725', xfbml : true, version : 'v2.9' }); FB.AppEvents.logPageView(); };
(function(d, s, id){ var js, fjs = d.getElementsByTagName(s)[0]; if (d.getElementById(id)) {return;} js = d.createElement(s); js.id = id; js.src = "http://connect.facebook.net/en_US/sdk.js"; fjs.parentNode.insertBefore(js, fjs); }(document, 'script', 'facebook-jssdk'));
!function(f,b,e,v,n,t,s) {if(f.fbq)return;n=f.fbq=function(){n.callMethod? n.callMethod.apply(n,arguments):n.queue.push(arguments)}; if(!f._fbq)f._fbq=n;n.push=n;n.loaded=!0;n.version='2.0'; n.queue=[];t=b.createElement(e);t.async=!0; t.src=v;s=b.getElementsByTagName(e)[0]; s.parentNode.insertBefore(t,s)}(window,document,'script', 'https://connect.facebook.net/en_US/fbevents.js'); fbq('init', '1922752334671725'); fbq('track', 'PageView'); This news post is collected from Cointelegraph
Recommended Read
Editors' Picks
BinBot Pro – Safest & Highly Recommended Binary Options Auto Trading Robot
Do you live in a country like USA or Canada where using automated trading systems is a problem? If you do then now we ...
User rating:
9.5
Demo & Pro Version Get It Now Hurry!
Read full review
Most Popular 2
Bit Bubble Tech – Learn How To Profit Big When Bitcoin Bubble Bursts?
If you have not already heard of the Bit Bubble Tech App, you undoubtedly wish to read this Bit Bubble Tech Review. We ...
User rating:
9.3
Free For 90 Days Get It Now
Read full review
The post Amateur Cryptojackers and Apple Macs Emerge as Two Mining Malware Trends for 2018 appeared first on Review: Legit or Scam?.
Read more from → https://legit-scam.review/amateur-cryptojackers-and-apple-macs-emerge-as-two-mining-malware-trends-for-2018-3
0 notes
Photo

New Post has been published here http://www.cryptoquicknews.com/amateur-cryptojackers-and-apple-macs-emerge-as-two-mining-malware-trends-for-2018/
Amateur Cryptojackers and Apple Macs Emerge as Two Mining Malware Trends for 2018

This post was originally published here
2017 was a big year for cryptojacking. It increased by 8,500 percent, according to figures published by Symantec in March. And it would seem that 2018 has so far been an even bigger year for mining malware, as the Cyber Threat Alliance September report revealed that, beginning on Jan. 1, cryptojacking still had room to increase by a further 500 percent.
However, beneath this simple outline of growth, there is a bigger, more complicated picture. Despite reports from some quarters showing that mining malware detections increased in the first two quarters of 2018, other reports suggest that they have in fact decreased.
And while the overall growth in mining malware since last year has been attributed to the volatility of cryptocurrency prices and the existence of software bugs, other factors have played a significant role, such as the involvement of amateur cryptojackers and the cost of mining legitimately.
Amateur cryptojackers
If there’s one dominant trend this year in the underworld of cryptojacking, it’s that most mining malware focuses on Monero. Indeed, Palo Alto Networks revealed in July that Monero accounts for 84.5 percent of all detected malware, compared to 8 percent for Bitcoin and 7 percent for other coins.

The reason for this is simple: Monero (XMR) is not only a privacy coin, but also the most valuable privacy coin by market cap — and 10th overall. Using the Cryptonight proof-of-work (PoW) algorithm, it mixes the user’s inputs with those of other users, and it also uses “ring confidential transactions” that obscure the amount of XMR being transferred. It’s therefore ideal for cybercriminals.
Monero was already the most popular coin for cryptojackers in 2017, but a number of new developments have emerged in 2018 to distinguish this year from its predecessor. Most notably, cryptojacking is increasingly becoming the province of amateur ‘hackers,’ who are lured into the illicit activity by the cheap availability of mining malware and by obvious financial rewards. According to Russian cybersecurity firm Group-IB, the dark web is “flooded with cheap mining software,” which can often be purchased for as little as $0.50.
Such software has become abundant this year: In 2017, Group-IB encountered 99 announcements regarding for-sale cryptojacking software on underground forums, while in 2018 it counted 477, signalling an increase of 381.8 percent. As the firm notes in its report:
“Low entry barrier to the illegal mining market results in a situation where cryptocurrency is being mined by people without technical expertise or experience with fraudulent schemes.”
More growth
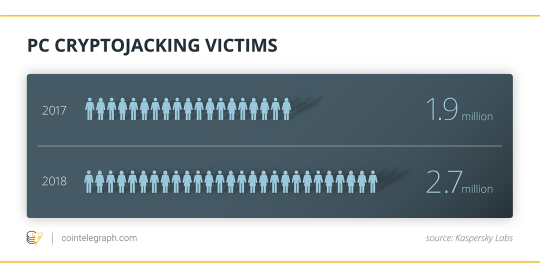
In other words, cryptojacking has become a kind of hobbyist crime, popular among thousands of amateur hackers. This would perhaps account for why there has been a marked increase in detections this year, with Kaspersky Labs informing Cointelegraph that the number of PC cryptojacking victims increased from 1.9 million in 2016/17 to 2.7 million in 2017/18. Evgeny Lopatin — a malware analyst at Kaspersky Lab – shared:
“The mining model […] is easier to activate and more stable [than other attack vectors]. Attack your victims, discreetly build cryptocurrency using their CPU or GPU power and then transfer that into real money through legal exchanges and transactions.”
Of course, whenever “detections” are mentioned, the possibility arises that any increase is largely the result of an improvement in detection measures. “However, this is not the main driver here, as we see actual growth,” says Lopatin.
“Our analysis shows that more and more criminals increasingly use crypto miners for malicious purposes across the world.”
McAfee noted in a report from April that the vast majority of its detections were of CoinMiner, a piece of malware that surreptitiously inserts code taken from the CoinHive XMR mining algorithm into the victim’s computer. This occurs when the victim downloads an infected file from the web, but what’s new in 2018 is that such a vulnerability now affects Apple Macs as well, which had previously been regarded as much more secure than its Windows rivals.
This development was noted by United States security firm Malwarebytes, which in a May blog post reported on the discovery of a new malicious crypto miner that harnesses the legit XMRig miner. Thomas Reed, the director of Mac and mobile at the company, wrote:
“Often, Mac malware is installed by things like fake Adobe Flash Player installers, downloads from piracy sites, [and] decoy documents users are tricked into opening.”
In fact, this wasn’t the first piece of Mac mining malware it had discovered, with Reed stating that it “follows other cryptominers for macOS, such as Pwnet, CpuMeaner and CreativeUpdate.”
EternalBlue
However, while cryptojacking has become more of an amateur-driven phenomenon, it still remains the case that many of this year’s exploits can be traced to more ‘elite’ sources. Cybersecurity firm Proofpoint reported at the end of January that Smominru, a cryptojacking botnet, had spread to over half a million computers — largely thanks to the National Security Agency, which had discovered a Windows bug that was then leaked online.
This vulnerability is better known as EternalBlue, which most famously was responsible for the WannaCry ransomware attack/incident of May 2017. And according to Cyber Threat Alliance (CTA), it’s another big factor in this year’s 459 percent increase in cryptojacking.
Worryingly, the CTA’s report suggests that cryptojacking is only likely to increase as it becomes more successful and profitable:
“[Cryptojacking’s] influx of money could be used for future, more sophisticated operations by threat actor groups. For instance, several large-scale cryptocurrency mining botnets (Smominru, Jenkins Miner, Adylkuzz) have made millions of dollars.”
And things are already bad enough in the present, with the CTA writing that infection by mining malware comes with steep costs for victims.
“Taken in aggregate, when criminals install cryptocurrency miners in large enterprise networks, the costs in excess energy usage, degraded operations, downtime, repairs of machines with physical damage and mitigation of the malware in systems incurred by the victims far outweigh the relatively small amount of cryptocurrency the attackers typically earn on a single network.”
Costs
The mention of costs is significant when it comes to cryptojacking, not just for (potential) victims, but also for perpetrators. That’s because cryptojacking is essentially the theft of electricity and CPU, which implies that it will continue being prevalent not only for as long as Monero and other coins remain valuable, but also for as long as it remains expensive to mine XMR and other cryptos.
According to CryptoCompare’s profitability calculator for Monero, an individual U.S.-based miner using a graphics card capable of a 600 H/s hash rate (e.g., the Nvidia GTX 1080) and using 100W of power (a very conservative estimate) will make only $0.8033 in profit every month. This, clearly, isn’t especially promising, which is a large part of the reason why so many amateurs have turned to cryptojacking, since mining XMR while paying for your own electricity just isn’t fruitful when you’re not a big mining company.
There are, however, recent signs that Monero mining has become more profitable, even for the smaller miner. This came after its hard fork on April 6, which changed its PoW protocol so as to make it incompatible with ASIC miners, which tend to dominate mining (particularly in the case of Bitcoin).
As soon as this hard fork was completed, reports came from the Monero subreddit that profitability had increased by 300 percent or even 500 percent, although this boost was soon lost in the following weeks, according to BitInfoCharts.

Likewise, Monero itself has been cautious with regard to promising that it can resist ASIC mining equipment forever. “Thus, it is recognized that ASICs may be an inevitable development for any proof-of-work [cryptocurrency],” wrote developers dEBRYUNE and dnaleor in a February blog. “We also concede that ASICs may be inevitable, but we feel that any transition to an ASIC-dominated network needs to be as egalitarian as possible in order to foster decentralization.”
Decline?
Assuming that it has become more profitable to mine XMR legitimately, this would account for a flattening in cryptojacking growth that has been observed by some cybersecurity firms. In its Q2 2018 report, Malwarebytes revealed that mining malware detections dropped from a peak of 5 million at the beginning of March, to a low of 1.5 million at the beginning of June. This decline may contradict what other analysts have reported this year, but given that Malwarebytes’ research is the most recent in terms of the dates covered, it’s arguably the most authoritative.
It’s not clear whether this decline is the result of an increase in profitability for legit Monero miners, of business and individuals wising up to the threat of cryptojacking, or of a general decline in the value of cryptocurrencies. Regardless, Malwarebytes predict that “Cryptocurrency miners will be going out of style” as a cybersecurity threat. “Of course, we are still going to see plenty of miners being distributed and detected,” its report concludes. “However, it looks like we are at the tail end of the ‘craze.'”
View the website
New Post has been published here http://www.cryptoquicknews.com/amateur-cryptojackers-and-apple-macs-emerge-as-two-mining-malware-trends-for-2018/
0 notes
Video
tumblr
For some odd reason, it will not let me add a title to this but here we have it, my final and (favorite) mechanic. The Death Light (well, that’s not actually what it’s called.) In actuality, it’s called the security surveillance camera that’s patrolling this entire area and as our player is a known escapee with people after him, if he’s caught in the light, he’s dead. Above is a video of the first version of the light moving, I had to animate it using key frames and it worked wonderfully, however I realized it was too fast for our boy to outrun and it went through dramatic changes. The biggest change was removing that rock wall in avour of something a little stonehedge looking but that looks like as if it’s been put there by man to aid in their construction tasks (brick piles, above and below, a plank to transfer such heavy bricks up on top of the rock.) Th reason for doing this was both for design as well as to give him something to hide under while the light passes over this. This was initially inspired by a scene form inside where a similar if not the exact same mechanic was used but by a different type of machine:

I had to figure out a way for the boy to avoid the trigger area as it passed over him, thus it led me to animating the trigger sphere completely separately to the point light. (Ah, also we decided on a point light as visually it looked far better than a spotlight, even though the fade out of the spotlight was ideal; It was simply far too tricky and kinky to mess around with with the limited amount of time we had left.) This....involved a lot of tweaking and a lot of working with the animation by the second, as it had to match the exact movements of the light, avoid the rocks by moving far back and be large enough and return into position fast enough to kill the boy if he got anywhere in the light at all. An unforgiving mechanic is what I hope for this one!
0 notes
Text
Errors, Errors and A New Mechanic?!
Ladies and gentlemen, I come to you with the familiar news of compiler errors. Over the course of the past couple of days I’ve been doing nothing but running into errors within my code left and right (since those are the only directions we can move in, haha! get it? Never mind.) Many of them include issues with our floating rock that the boy must push into the water to well, cross the water. The first issue we’ve identified is the animation not being triggered by the pushing of the rock, the second being t’s kinematic properties stay checked the entire time when it is meant to start unchecked- in turn causing the rock to be floating in air instead of on water. And the third is when it does in fact play the key framed animation, it starts meters behind where it is meant to start playing from. Of course all have been fixed now, how? you guessed it, debugging! and a lot more complicated functions and triggers that I won’t throw myself into on here. Instead I’d much rather tell you about the seesaw mechanic I’ve put in at the strat of the game.
So at the start, as you set off, you find a plank in your way next to a pile of bricks that are most likely for construction purposes (most definitely are), and you must pull a brick onto the plank in order to keep it down so you can run up it and jump to the next rock. The issue with this was WHERE to put it? It had to be so the player could run past it if he tried but would have had to come back after realizing he cant jump that high, nor can the plank stay in it’s initial position, which should hopefully lead him to the bricks. At times I’ve encountered issues with running past the plank and knocking it clean off the holder its balancing on, but this is rare and shouldn’t NORMALLY happen. Fingers crossed. The only downside of this that we weren’t able to fix was him crouching down and dragging the bricks over as we didn’t have time. So we ended up with him pushing and pulling as he should but it looks a little more like he’s controlling the object with his mind....ah well.
0 notes
Text
Ladders, rocks and whatnot
Today we added a bulk of the mechanics the boy will be interacting with. We started with writing down the basic code for the boy to push and pull objects, even if he isn’t doing the animations for it, he’s at least triggered by the pressing of two keys at once which is exactly what we want; arrow key + Left Crtl button to interact with and move objects. The process involved lots of trigger spheres and separate box colliders, I’ve also found quite a few faults within the process of pushing a box over and standing on it as either he will slip off of it if not placed correctly or pushed properly, or he will end up pushing the rock out of place WHILE pushing it down which results in it not being able to fall down because the boy is out of the trigger area. To resolve the latter from happening, I increased the trigger area as well as the box collider so he will have no choice but to be within the trigger area as well be able to walk across it and not die!
The second task that came with this was having him actually look as if he’s pushing and pulling things rather than walking straight into it. This was relatively easier to do than the first task, quite simply all that needed to be done was trigger the animations in the pushPull section of our code.
The final task we accomplished today was the ladder. Ah, the ladder- there were many doubts about adding the ladder in to the prototype given the time constraints we were facing but without it, it made for a rather awkward transition upward to the next level of ground he needed to be at. So we decided to throw in our ladder except, instead of having him climb like a normal being our player has to suffer a tiny bit and hop up the ladder every step of the way until he meets ground. On the bright side, he doesn’t die if he falls off!
(no pictures today, so sorry guys!)
0 notes
Text
Some Inspiration- The Mighty Dragon Bridge
I thought I’d share a few reference images I’ve been working off on, both for inspiration in what to bring next in to the game’s prototype as well as those I’ve been using to work on the environment as a whole. I quite love the first one as the beast’s bones appear so grand and majestic, especially against the cave’s terrain. It’s what inspired me to actually attempt to bring in an interactive dragon bridge for our boy to cross over, which is where the game prototype shall end. Upon attempting to bring it in, I had to use quite a few box colliders to place on top of the spine of the dragon’s skeleton as the original mesh collider was too unstable and uneven for our player character to run across and over. It was relatively easy although it did take quite a few tries in order to get right and various camera angle shifts to make it seem as if he WASN’T floating in air to the human eye.




0 notes
Text
HELLO
Welcome to my game development blog. I’m here with my first ever game prototype “Below.” A low-poly, 2.5D puzzle-platformer adventure game inspired by none other than Playdead’s Inside and Limbo.
It features a young boy on what feels like an endless mission to escape from the confines he’s found himself in. Initially I wanted the boy to awaken in some sort of facility, more on the side of a laboratory with no recollection of who or where he is. I had planned for him to rebel against the man holding him down when he wakes up, in turn causing him to flee the vicinity and be written down as an escapee for the workers to chase after. I would then proceed with building the prototype of having him simply run, hide and sneak past those after him in the lab/facility like setting, however I changed this and instead of sticking only to the lab I wanted the element of mystery that came with an entire operation going on underground- thus giving birth to the idea of construction in underground, secret catacombs that he falls into by accident while running away.
It’s a side scroller so the movement of the character I wanted was already set in stone, and he was limited to only a few interaction method with objects as time was not on my side for this project.
Without further ado, onwards!
0 notes