#Cyber Security Courses in Chennai
Text
Cyber Security Courses in Chennai
A variety of courses covering all facets of cyber security are offered as part of the cyber security course in Chennai. According on their level of expertise and knowledge, as well as which course best suits their particular interests in the case of professionals already working in the area and seeking quick advancement, participants may select from a variety of courses offered by Careerera. This completely developed cyber security online course in Chennai was created to meet industry demands and close the skills and knowledge gap in the market.
1 note
·
View note
Text
0 notes
Text
Comprehensive Microsoft Azure Training Course in Chennai
Course Overview: Our Comprehensive Microsoft Azure Training Course in Chennai is designed to provide you with a deep understanding of Azure, Microsoft's cloud computing platform. This course covers everything from basic concepts to advanced features, equipping you with the skills needed to manage and deploy cloud solutions effectively.
Course Content:
Introduction to Microsoft Azure:
What is Azure?: Explore the basics of Microsoft Azure, its core services, and benefits.
Azure Architecture: Understand the components and structure of Azure, including regions, resource groups, and subscriptions.
Azure Core Services:
Virtual Machines: Learn how to create, configure, and manage virtual machines in Azure.
Azure Storage: Gain insights into different types of storage solutions, including Blob Storage, Disk Storage, and Azure Files.
Azure Networking: Study Azure networking components such as Virtual Networks, Load Balancers, and Network Security Groups.
Azure Resource Management:
Azure Resource Manager (ARM): Learn about ARM templates for deploying and managing resources.
Azure Policy and Blueprints: Understand how to enforce compliance and manage governance in Azure.
Azure Identity and Access Management:
Azure Active Directory (AD): Explore Azure AD for identity and access management.
Role-Based Access Control (RBAC): Implement RBAC to manage permissions and access to Azure resources.
Azure Solutions and Services:
App Services: Learn to deploy and manage web apps, mobile apps, and APIs.
Azure Functions: Understand serverless computing and how to create and manage Azure Functions.
Azure SQL Database: Explore Azure’s managed database services, including SQL Database and Cosmos DB.
Monitoring and Security:
Azure Monitor and Alerts: Learn to monitor resources, set up alerts, and gain insights into resource performance.
Azure Security Center: Understand how to secure your Azure environment and manage security policies.
Cost Management and Optimization:
Azure Pricing Calculator: Use the Azure Pricing Calculator to estimate costs and plan budgets.
Cost Management Tools: Explore tools and practices for optimizing and managing Azure costs effectively.
Hands-On Labs and Projects:
Practical Labs: Engage in hands-on labs to apply what you’ve learned in real-world scenarios.
Capstone Project: Complete a capstone project that integrates various Azure services and demonstrates your ability to design and deploy solutions.
Learning Outcomes: Upon completion of this course, participants will:https://intellimindz.com/cyber-security-training-in-bangalore/
Understand the fundamental and advanced features of Microsoft Azure.
Be able to deploy and manage Azure resources efficiently.
Implement and manage identity and access using Azure AD and RBAC.
Monitor, secure, and optimize Azure environments effectively.
Have practical experience through hands-on labs and a capstone project.
Advance your career in cloud computing with our Comprehensive Microsoft Azure Training Course in Chennai. Secure your spot and gain the skills needed to excel in the world of cloud technology.
0 notes
Text

A variety of courses covering all facets of cyber security are included in the cyber security course in Chennai. According on their level of expertise and knowledge, as well as which course best suits their particular interests in the case of professionals already working in the area and seeking quick advancement, participants may select from a variety of courses offered by Careerera. This completely developed cyber security online course in Chennai was created to meet industry demands and close the skills and knowledge gap in the market.
#Cyber Security Courses in Chennai#Cyber Security Training in Chennai#Cyber Security Certification in Chennai
0 notes
Text
https://bitaacademy.com/course/cyber-security-training-in-chennai/
0 notes
Text
Will Quantum Computing Break the Blockchain or Make it Stronger?

Blockchain technology has revolutionized online transactions. Its core principle of decentralization and immutability has disrupted everything from finance to supply chain management. However, the emergence of quantum computing casts a shadow of uncertainty. With its immense computational power, quantum computers could potentially crack the cryptographic algorithms that underpin blockchain security. So, will quantum computing break the blockchain or make it stronger? This blog explores both sides of the coin and highlights how a well-structured Cyber Security course in Chennai can equip you with the knowledge to navigate this evolving landscape.
The Quantum Threat: Can Quantum Computers Crack the Blockchain?
The concern surrounding quantum computing stems from its ability to solve complex mathematical problems that are currently intractable for traditional computers. These problems form the foundation of cryptographic algorithms used in blockchain technology, particularly for:
Digital Signatures: Blockchain transactions are cryptographically signed to ensure authenticity and prevent unauthorized modifications. Quantum computers could potentially forge these signatures, jeopardizing the integrity of the entire blockchain.
Hashing: Blockchain data is secured through cryptographic hash functions. These functions generate unique "fingerprints" for each data block, making tampering easily detectable. Quantum computing might be able to reverse these hash functions, potentially altering blockchain data undetected.
The Blockchain's Defense Mechanisms: Can It Withstand the Quantum Threat?
Despite the potential threat, blockchain technology holds some inherent advantages against quantum computing:
Continuous Improvement: The blockchain community is actively researching and developing post-quantum cryptography (PQC) solutions. These new algorithms are designed to be resistant to attacks from quantum computers.
Network Effect: Blockchain networks become more secure as the number of participants increases. A successful attack on a large, established blockchain would require immense computing power, potentially deterring malicious actors.
Hard Forks and Upgrades: The beauty of blockchain technology lies in its ability to adapt. If a significant threat emerges, the blockchain community can implement hard forks or upgrades to incorporate PQC solutions and maintain network security.
Beyond Breaking Codes: How Quantum Computing Can Strengthen Blockchain
Quantum computing also offers potential benefits for blockchain technology:
Enhanced Security: While it might pose a challenge initially, quantum-resistant cryptography developed for PQC solutions could ultimately lead to even more secure blockchain systems.
Improved Scalability: Certain quantum computing algorithms have the potential to streamline complex cryptographic computations, potentially improving the scalability of blockchain networks.
Advanced Smart Contracts: Quantum computing could enable the development of more sophisticated smart contracts with enhanced functionalities and security mechanisms.
Equipping Yourself for the Quantum Future: A Cyber Security Course in Chennai Can Help
The evolving relationship between quantum computing and blockchain necessitates a workforce equipped with the knowledge to navigate this complex space. A well-structured Cyber Security course in Chennai can provide valuable insights:
Understanding Blockchain Fundamentals: These courses provide a strong foundation in blockchain technology, its underlying cryptographic principles, and its current security landscape.
Exploring Quantum Computing and Cryptography: Participants gain insights into the basic principles of quantum computing and its potential impact on current blockchain cryptography.
Post-Quantum Cryptography (PQC): Courses delve into the ongoing development of PQC solutions and their potential role in securing blockchain technology in the quantum age.
The Future of Blockchain Security: Learn how the blockchain community is preparing for the potential challenges and opportunities presented by quantum computing.
Cyber Security courses in Chennai are offered by a variety of institutions, ranging from universities and colleges to private training providers. Choosing the right course depends on your specific needs and career goals. Look for courses that are up-to-date and incorporate the latest advancements in both blockchain technology and quantum computing research.
Beyond the Classroom: Building a Career in Cybersecurity
A Cyber Security course in Chennai is a valuable first step towards a promising career in cybersecurity. Here are some additional steps to consider for continued growth:
Stay Updated on Industry Trends: The cybersecurity landscape, including the relationship between quantum computing and blockchain, is constantly evolving. Actively monitor industry publications, conferences, and online communities to stay ahead of the curve.
Specialize in Blockchain Security: As blockchain technology continues to mature, specializing in blockchain security can be a strategic career move. This allows you to develop in-depth knowledge of blockchain's specific vulnerabilities and how to mitigate them in the quantum age.
Network with Professionals: Connect with other cybersecurity professionals in Chennai and participate in online forums and conferences focused on blockchain security. Building a strong network allows you to share knowledge, learn from others, and discover potential career opportunities.
Conclusion: Will Quantum Computing Break the Blockchain or Make it Stronger?
The impact of quantum computing on blockchain is yet to be fully determined.
However, the blockchain community is actively preparing for the future. By continuously developing new cryptographic solutions, leveraging the network effect, and embracing advancements in quantum-resistant cryptography, blockchain technology has the potential to emerge even stronger from this challenge.
A well-structured Cyber Security course in Chennai equips you with the knowledge and skills to understand the intricacies of both blockchain and quantum computing, allowing you to participate in this evolving landscape. Don't wait on the sidelines – enroll in a Cyber Security course in Chennai today and be part of shaping a secure future for blockchain technology in the quantum age!
0 notes
Text
what is hacking internship
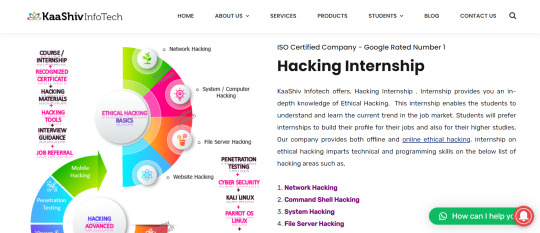
hacking internship:
A hacking internship provides practical training in understanding and manipulating computer systems, networks, and software applications. Unlike traditional courses, ethical hacking internship offer real-world exposure under expert guidance. Participants engage in activities such as penetration testing and incident response, gaining firsthand insights into cybersecurity. Objectives include improving technical competencies, grasping ethical considerations, and preparing for careers in cybersecurity. Interns tackle simulated or actual projects, honing their skills and promoting ethical conduct. Overall, a ethical hacking internship in chennai provides invaluable experience, equipping individuals for the complexities of cybersecurity and ethical hacking internship program with practical skills and ethical awareness.
where to take hacking internship
Kaashiv Infotech provides an extensive hacking internship that covers all essential aspects of cyber security and ethical hacking internship program. With seasoned mentors and hands-on learning, Kaashiv Infotech's internship ensures that participants acquire practical skills and real-world insights to thrive in the field. From grasping fundamental concepts to mastering advanced techniques, the internship equips individuals with the knowledge and expertise vital for ethical hacking internship. With a focus on practical learning and industry-relevant skills, Kaashiv Infotech stands out as a top choice for those seeking to embark on a cybersecurity journey through an internship.
Objective of hacking internship:
One of the main goals of a ethical hacking internship in chennai is to give participants a solid understanding of computer systems and networks. This involves exploring different operating systems like Windows, Linux, and macOS, and understanding how data moves over networks and the workings of various protocols. Additionally, interns learn basic programming languages commonly used in cybersecurity and ethical hacking internship program, such as Python, JavaScript, and SQL, to develop scripting skills and automate tasks.
Another important part of a hacking internship is teaching participants about cybersecurity principles and best practices. This includes recognizing common security weaknesses and attacks, such as buffer overflows and SQL injection, and learning how to defend against them. Interns also learn about encryption methods and cryptographic algorithms used to protect data and communications, as well as techniques for detecting and responding to security incidents.
online certified ethical hacking internship:
Ethical considerations and legal implications are also highlighted in the hacking internship. Participants learn about ethical guidelines and responsibilities, including getting proper authorization before conducting security assessments and respecting the privacy of individuals and organizations. They also gain insight into relevant laws and regulations related to cyber security and ethical hacking internship program, such as the Computer Fraud and Abuse Act in the United States, and understand the potential consequences of engaging in unauthorized activities during the ethical hacking internship work from home.
Hands on experience on hacking:
Hands-on experience is a vital part of the hacking internship, enabling participants to apply theoretical knowledge in practical situations. This often includes engaging in simulated hacking challenges and exercises, where interns are assigned to identify and exploit vulnerabilities in simulated environments. Additionally, interns may have the chance to work on real-world projects and case studies, collaborating with industry professionals to tackle complex security issues.
Conclusion:
In conclusion, a hacking internship equips individuals with the skills and knowledge necessary to understand and manipulate computer systems and networks for diverse purposes, such as enhancing security and identifying vulnerabilities. Covering topics like computer programming, network security, cybersecurity principles, and legal aspects, the ethical hacking internship in chennai prepares participants for careers in cybersecurity and related fields. Moreover, it fosters ethical behaviour and encourages responsible use of hacking techniques, promoting a professional approach to cybersecurity challenges.
1 note
·
View note
Text
Besant Technologies Reviews – Career Tracks, Courses, Learning Mode, Fee, Reviews, Effective Ratings and Feedback

Besant Technologies is a leading IT training provider dedicated to empowering individuals with the skills and knowledge needed to succeed in today's competitive job market. This comprehensive review will delve into various aspects of Besant Technologies, offering insights for both seasoned professionals and freshers alike, aiding in making informed decisions regarding course selection.
Understanding Besant Technologies:
Besant Technologies stands out for its diverse range of courses spanning software development, data science, cloud computing, and cybersecurity. These courses, curated by industry experts, ensure that students receive relevant and up-to-date training aligned with industry requirements.
History and Evolution:
Besant Technologies, a division of BDreamz Global Solutions Private Limited, offers a plethora of courses including Digital Marketing, Artificial Intelligence, and Machine Learning. With over 18 branches across India and a track record of training over 100,000 students in the last decade, it has emerged as a top training institute, particularly in Chennai, Bangalore, and Pune.
Founder and Executive Officer:
Binu Bihani, renowned for her expertise in Corporate Financial Planning and Cyber Security Insurance, is the driving force behind Besant Technologies. With certifications from IRDA and AMFI, Binu brings a wealth of experience from esteemed institutions like ICICI, IRMA, and Symbiosis, ensuring top-notch education.
Career Pathways and Institutional Collaborations:
Besant Technologies offers a wide array of IT courses with a focus on placement-oriented training. With tie-ups with over 2000 companies, the institute guarantees 100% job placements for its courses. With branches in key cities and a million students trained, Besant Technologies has become a preferred choice for IT training.
Key Strategies for Success:
Besant Technologies' success is attributed to its diverse course offerings, placement-oriented training, institutional excellence, and real student experiences. The institute's commitment to offering cutting-edge courses like AWS, Python, Data Science, and DevOps ensures that students are equipped with in-demand skills.
Accessibility of Besant Technologies Website:
Besant Technologies' website boasts a user-friendly design with intuitive navigation and accessibility features. The layout is well-organized, making it easy for users to explore courses and resources. The responsive design ensures a seamless experience across devices, while the robust search functionality simplifies course discovery.
Besant Technologies Data Science & AI Course:
Besant Technologies' Data Science & AI Course equips individuals with essential skills in machine learning, data analysis, Python programming, deep learning, and artificial intelligence. The course covers a wide range of topics, preparing students for lucrative opportunities in the tech industry.
Data Science with Python Training and Certification:
Besant Technologies offers a comprehensive Data Science with Python Training and Certification Course designed for professionals and graduates with basic computer science skills. The course covers essential topics like statistics, Python programming, machine learning algorithms, and real-life projects, ensuring students are well-prepared for the industry.
Pros and Cons:
Based on reviews, Besant Technologies is praised for its long-standing reputation, variety of courses, job assistance, and flexible payment options. However, some concerns include the absence of applications, lengthy syllabus, and lack of refund policy and EMI options.
In Conclusion:
Besant Technologies emerges as a beacon of excellence in IT training, offering high-quality education, practical learning experiences, and career-oriented support. With a commitment to empowering individuals and shaping successful careers, Besant Technologies continues to make a significant impact in the field of technology.
#BesantTechnologies#ITTraining#CareerDevelopment#DataScienceCourse#ArtificialIntelligenceTraining#JobPlacementAssistance
0 notes
Text
Unmasking Unethical Hacking: Exploring the Dark Underbelly of Cybersecurity
Within the realm of cybersecurity, ethical hacking serves as a vital tool for identifying vulnerabilities and fortifying security measures. However, lurking in the shadows is a darker facet known as unethical hacking. This blog post aims to illuminate the concept of unethical hacking, its ramifications, and the imperative need to distinguish it from ethical hacking.
Unveiling Unethical Hacking:
Unethical hacking, commonly referred to as black hat hacking, entails unauthorized intrusion into computer systems, networks, or digital devices with malicious intent. Unlike ethical hacking, which is conducted with explicit consent and aims to enhance security, unethical hacking involves exploiting vulnerabilities for personal gain, inflicting harm, or engaging in illegal activities.

Mastering ethical hacking is an exciting journey. Dedicate yourself to continuous learning, stay curious, and enjoy the adventure! If you’re ready to delve deeper, consider enrolling in an Ethical Hacking course in Chennai for certifications and job placement opportunities.
Activities Associated with Unethical Hacking:
Unauthorized Access: Unethical hackers gain illicit entry into systems, networks, or personal devices to pilfer sensitive information, such as financial data, personal records, or intellectual property.
Malware Creation and Distribution: Unethical hackers conceive and disseminate malicious software, encompassing viruses, worms, and ransomware, with the intention of compromising systems and extorting money from victims.
Denial of Service (DoS) Attacks: Unethical hackers orchestrate DoS attacks to overwhelm and incapacitate targeted systems or networks, disrupting services and causing financial losses.
Phishing and Social Engineering: Unethical hackers employ deceptive techniques, such as phishing emails or social engineering ploys, to deceive individuals into divulging sensitive information, including login credentials or financial details.
Cyber Espionage: Unethical hackers engage in cyber espionage activities, infiltrating government agencies, corporations, or organizations to pilfer classified information or trade secrets.

Implications and Consequences:
Unethical hacking carries severe consequences for individuals, organizations, and society at large:
Financial Loss: Victims of unethical hacking often endure financial losses due to stolen funds, costly system repairs, or legal ramifications stemming from the breach.
Invasion of Privacy: Unethical hackers compromise individuals' privacy by gaining access to personal information, leading to identity theft, blackmail, or harassment.
Reputation Damage: Organizations that fall prey to unethical hacking experience a loss of trust and reputation, which can have enduring effects on their business operations.
Legal Ramifications: Engaging in unethical hacking activities is unlawful in most jurisdictions, exposing perpetrators to criminal charges, fines, or imprisonment if apprehended.
ACTE has been implementing several technology motivated training programs that provide ethical hacking Certifications and Courses at Chennai.
Differentiating Ethical Hacking from Unethical Hacking:
It is vital to establish a clear distinction between ethical hacking and its unethical counterpart:
Consent: Ethical hacking is conducted with explicit permission from the owner, while unethical hacking involves unauthorized intrusion.
Intent: Ethical hacking aims to uncover vulnerabilities and bolster security, while unethical hacking pursues personal gain, harm, or illegal activities.
Legality: Ethical hacking operates within the boundaries of the law, adhering to legal frameworks and regulations, whereas unethical hacking flouts these laws.
Unethical hacking represents the murky side of cybersecurity, characterized by malicious intent and a disregard for legal boundaries. Recognizing the disparity between ethical and unethical hacking is critical in fostering a safer digital landscape.
By fostering awareness, implementing robust security measures, and upholding ethical standards, we can collectively combat the threats posed by unethical hackers and safeguard our digital world.
0 notes
Text
It training institute in chennai
What programming languages are best for cyber security?
Cybersecurity encompasses a wide range of tasks, and the best programming language for a particular aspect of cybersecurity depends on the specific task or role. Here are some programming languages commonly used in various cybersecurity domains:
Python:
Python is widely used in cybersecurity for its simplicity and readability.
It has a large number of libraries and frameworks (e.g., Scapy, PyCrypto, BeautifulSoup) that are beneficial for tasks such as network scanning, penetration testing, and automation.
JavaScript:
JavaScript is essential for web security, as it's the primary language for client-side scripting.
It's used in web application security testing and understanding vulnerabilities in web browsers.
C/C++:
Low-level languages like C and C++ are used in developing security tools and applications.
They are common in writing exploits and analyzing malware due to their close-to-hardware capabilities.
Java:
Java is often used in developing secure server-side applications.
It's employed in building secure and robust enterprise-level systems.
Ruby:
Ruby is used in web application security testing, and the Metasploit Framework, a popular penetration testing tool, is written in Ruby.
Go (Golang):
Go is known for its efficiency and is used in developing scalable and high-performance security tools.
Tools like Docker and Kubernetes, which are significant in the DevSecOps space, are written in Go.
SQL:
SQL is crucial for database security. Knowledge of SQL is essential for protecting databases and conducting security assessments.
Bash/Shell scripting:
Scripting languages like Bash are essential for writing automation scripts and managing system configurations securely.
Remember that the choice of programming language depends on the specific task or project within the cybersecurity domain. Many cybersecurity professionals use a combination of these languages depending on the requirements of the job at hand. Additionally, staying updated with the latest trends and technologies in the cybersecurity field is crucial for effective defense and mitigation strategies.
IT COURSE IN CHENNAI
IT TRAINING INSTITUTE IN CHENNAI
IT TRAINNG INSTITUTE IN CHENNAI
IT INSTITUTE IN CHENNAI
1 note
·
View note
Text
Safeguarding the Digital Landscape: The Significance of Ethical Hacking
In an interconnected world where cyber threats loom large, organizations must prioritize cybersecurity to protect their systems and data. Ethical hacking, also known as white-hat hacking or penetration testing, plays a pivotal role in this pursuit. This blog post highlights the importance of ethical hacking in safeguarding the digital landscape.
To enrich your Ethical Hacking journey, I recommend considering a reputable Ethical Hacking Course in Chennai. Their wealth of expertise and resources can offer valuable insights and skills, contributing to advancing your proficiency in ethical hacking.

Some Reasons Why Ethical Hacking Is Important:
Unearthing Vulnerabilities:
Ethical hackers possess the expertise to identify vulnerabilities within systems, networks, and applications. By actively searching for weaknesses, they enable organizations to discover potential entry points that malicious hackers could exploit. By identifying these vulnerabilities before cybercriminals do, ethical hackers empower organizations to take preemptive measures to strengthen their defenses.
Bolstering Security Measures:
Ethical hacking extends beyond vulnerability identification; it helps organizations enhance their overall security posture. Through comprehensive security assessments, ethical hackers not only pinpoint weaknesses but also provide recommendations and solutions to mitigate risks. By implementing these recommendations, organizations can fortify their systems and ensure the protection of sensitive data.
Mitigating Financial Losses:
Cyberattacks can wreak havoc on an organization's financial standing. The costs associated with data breaches, legal liabilities, and reputational damage can be staggering. Ethical hacking plays a crucial role in mitigating potential financial losses by identifying security gaps and vulnerabilities that cybercriminals may exploit. By investing in ethical hacking services, organizations can potentially save significant costs in the long run.
Fostering Customer Trust:
In an era where data breaches erode consumer confidence, maintaining customer trust is paramount. Ethical hacking contributes to this trust by conducting security assessments and implementing robust security measures. Such proactive measures demonstrate an organization's commitment to safeguarding customer data, bolstering its reputation, and fostering loyalty and trust among its clientele.
Ensuring Regulatory Compliance:
Numerous industries are bound by stringent regulations and compliance requirements concerning data protection and cybersecurity. Ethical hacking assists organizations in meeting these obligations by identifying vulnerabilities and ensuring the implementation of appropriate security controls. Compliance with these regulations helps organizations avoid penalties, legal ramifications, and reputational damage.
Look for classes that educate a basic understanding of ethical hacking. Considering the Best Ethical Hacking Online Training becomes critical.

Staying Ahead of Cybercriminals:
Cybercriminals are constantly innovating their tactics to breach systems and exploit vulnerabilities. Ethical hacking enables organizations to maintain a proactive stance. By simulating real-world attack scenarios, ethical hackers can identify emerging threats and vulnerabilities. Armed with this knowledge, organizations can develop and implement effective defense strategies, ensuring they remain one step ahead of cybercriminals.
Cultivating a Security-Focused Culture:
Ethical hacking promotes a culture that prioritizes proactive security measures within organizations. By conducting regular security assessments, ethical hackers raise awareness about the significance of cybersecurity among employees. This includes imparting knowledge about best practices, implementing secure coding standards, and fostering a culture that values security at every level. A security-focused culture serves as a strong bulwark against potential breaches and minimizes risks.
By unearthing vulnerabilities, bolstering security measures, mitigating financial losses, fostering customer trust, ensuring regulatory compliance, staying ahead of cybercriminals, and cultivating a security-focused culture, ethical hacking strengthens an organization's defenses against evolving cyber threats.
Embracing ethical hacking practices is a proactive approach that fortifies systems, protects valuable data, and bolsters the resilience of organizations in the face of constant cyber risks.
0 notes
Text
Master in Artificial Intelligence, Robotics in Germany

In the ever-evolving landscape of technology, Germany stands tall as a hub for academic excellence, especially in the fields of Artificial Intelligence (AI), Robotics, and Cyber Security. Our commitment to fostering cutting-edge knowledge and innovation propels us to offer a Master's program that transcends traditional boundaries.
Also Read: Masters in Cybersecurity in Germany
Mastering the Future: A Unique Curriculum
Crafting Expertise in Artificial Intelligence
Our program is meticulously designed to immerse students in the realms of Artificial Intelligence, providing a comprehensive understanding of machine learning, natural language processing, and computer vision. Our approach is hands-on, allowing students to apply theoretical concepts to real-world scenarios, ensuring proficiency in both foundational and advanced AI techniques.
Also Read: Masters in Artificial Intelligence in Germany
Navigating the World of Robotics
The Robotics component of our Master's program delves deep into the intricacies of designing, programming, and deploying robotic systems. From autonomous vehicles to industrial automation, our students gain practical experience in developing solutions that drive the future of robotics.
Also Read: Masters in Robotics in Germany
Securing the Digital Frontier: Cyber Security Expertise
As the digital landscape expands, so does the need for cyber defense experts. Our Cyber Security curriculum equips students with the skills to thwart cyber threats and safeguard critical information. We focus not only on theoretical frameworks but also on practical exercises that simulate real-world cyber attacks, ensuring our graduates are ready to face the challenges of the digital era.
Also Read: overseas education consultants in chennai
World-Class Faculty: A Guiding Force
Expertise Beyond Borders
Our faculty comprises globally recognized experts in AI, Robotics, and Cyber Security. Their diverse backgrounds, research contributions, and industry experience create a dynamic learning environment that transcends conventional boundaries.
Also Read: study abroad consultants in coimbatore
Mentorship and Collaboration
We prioritize mentorship, fostering a collaborative atmosphere where students engage with faculty members on research projects and industry collaborations. This personalized approach ensures that our graduates are not just academically proficient but also industry-ready.
Also Read: overseas education consultants in madurai
State-of-the-Art Facilities: A Technological Playground
Laboratories of Innovation
Our cutting-edge laboratories provide students with the latest technology to experiment and innovate. From high-performance computing clusters for AI research to robotics labs equipped with the latest hardware, we offer an unparalleled technological playground for our students.
Also Read: study in germany consultants in Vellore
Simulated Cyber Threat Environments
In the realm of cybersecurity, practical experience is paramount. Our simulated cyber threat environments allow students to test their skills in a controlled setting, preparing them for the challenges of securing digital infrastructures in the real world.
Also Read: german language course in madurai
Industry Integration: Bridging Academia and the Corporate World
Internship Opportunities
We understand the significance of real-world exposure. Our Master's program facilitates internship opportunities with leading tech companies, enabling students to apply their knowledge in professional settings.
Also Read: Study Abroad Education Consultant
Networking Events and Conferences
Regular networking events and conferences connect our students with industry leaders, fostering a bridge between academia and the corporate world. This integration ensures that our graduates are not only knowledgeable but also well-connected within the industry.
Also Read: Online German Language courses
Admission Process: Navigating Excellence
Prospective students undergo a rigorous selection process, ensuring that those who join our program possess the passion and drive to excel in the dynamic fields of AI, Robotics, and Cyber Security.
Conclusion
Embark on a transformative journey with our Master's program in Artificial Intelligence, Robotics, and Cyber Security in Germany. We don't just educate; we empower future leaders in technology. Join us in shaping the future of AI, Robotics, and Cyber Security.
0 notes
Text
0 notes
Text
LCD Projector Rental in Chennai

LCD Projector Rental in Chennai

LCD Projector Rental in Chennai Redefine system (RDS) provides Laptops and computers on rent in Chennai and all over India, and it is the pioneer in delivering all rental services at your door step. We provide you with fully customized and quality product with technical assistance on our rental services. RDS is one of the leaders in providing entire IT needs such as Laptop, Desktop, Servers, Workstations, Projectors and other computer accessories for hiring or purchasing. If you want any IT products on rent then RDS is the perfect destination to prefer. We are in this field more than 25+ years and we have an extensive collection of rental equipments, offer all brands of products such as Dell, HP, Compaq, Toshiba, Apple, Lenova and Acer. We are not only expert in providing quality products, but also additionally having qualified expertise to provide supreme technical support for our rental Products.RDS is one of the top leading rental company for all your computer & security needs. Our main purpose is to serve the needy persons, corporate companies, MNCs, Educationalist so on. So we offer new computers, laptops Printers, software, Virus removal, Computer service, Computer repairs, upgrade, data recovery, networking, server configuration, Cyber Security, Wireless solution, CCTV Camera, Biometric and RFID based attendance solutions, access control system, home and shop security with fully dedicated and trained technicians with onsite service to both home and business users.RDS is one of the top leading rental company for all your computer & security needs. Our main purpose is to serve the needy persons, corporate companies, MNCs, Educationalist so on. So we offer new computers, laptops Printers, software, Virus removal, Computer service, Computer repairs, upgrade, data recovery, networking, server configuration, Cyber Security, Wireless solution, CCTV Camera, Biometric and RFID based attendance solutions, access control system, home and shop security with fully dedicated and trained technicians with onsite service to both home and business users.aptop Rental in Coimbatore Provide Laptop for rent in Coimbatore is the pioneer in delivering all Rental services at your doorstep. We provide you with fully customized and quality product with technical assistance on our rental services. Laptop Rental in Coimbatore is the leader in providing entire necessity of laptop, Desktop, Server and other computer accessories for purchasing or hiring. If you want a Laptop on rent in Coimbatore , then Laptop Rental in Coimbatore is the perfect destination to prefer. We provide you with all Laptop rental needs by setting the benchmark for high-tech gadgets at the most economical pricing. Among all the suppliers in the Indian competitive market, we are undoubtedly the best, always wowing our clientele with outstanding rental services. At Laptop Rental in Coimbatore, we have an extensive collection of rental equipment. Laptop Rental in Coimbatore offers Laptop for rent in Coimbatore. from renowned manufacturers such as Dell, HP, Compaq, Toshiba and Acer. We are not only expert in providing our clients a quality product, but additionally have qualified expertise to provide supreme technical support on our rental services. We are providing Laptop Rental service since 2008. Of course, our qualified expert technicians will make sure when you walk out of our service center you are 100% satisfied with Our Rental Products.
Read the full article
0 notes
Text
Are you looking for Best Ethical Hacking Course in Tambaram?
Livewire is a training institute in Tambaram, Chennai that offers courses in ethical hacking, cyber security, and other IT-related topics. They are a well-known institute in the area and have a good reputation. A unique combination of technologies that is specific to IT, Computer science, Electronics & Electrical departments. We deal with emerging technologies like Data science, Machine Learning, IOT, Artificial Intelligence, Block chain, Full Stack Developer, Cyber security, Automotive Embedded system and many more. LIVEWIRE is present in more than 100 locations in India and over 7 countries.
LIVEWIRE credential includes its affiliation like NSDC, STED Council, MSME, NIELIT, AXELOS, Oracle, CompTIA, Block chain Council etc. LIVEWIRE works closely with more than 1000 colleges in India as a technology partner in equipping students beyond their academics and also with few corporate clients for their training requirements.
Learning how to protect your own systems: Ethical hacking courses teach you how to think like a hacker, so you can better understand the vulnerabilities in your own systems and how to protect them. Gaining valuable skills: Ethical Hacking Course in Tambaram ,Ethical hacking skills are in high demand, so taking an ethical hacking course can help you improve your job prospects and earn a higher salary. Staying up-to-date on the latest security threats: The field of cyber security is constantly evolving, so ethical hacking courses can help you stay up-to-date on the latest security threats and how to defend against them.
Developing critical thinking skills: Ethical hacking courses require you to think critically and creatively, which are valuable skills in any field. Building your network: Ethical hacking courses can help you build your network of contacts in the cyber security industry, which can be beneficial for your career.
If you are interested in a career in cyber security, or if you simply want to learn more about how to protect your own systems, then an ethical hacking course is a great option. Here are some of the specific benefits of taking an ethical hacking course: You will learn how to identify and exploit security vulnerabilities. This knowledge can be used to improve the security of your own systems, or to help organizations identify and fix security vulnerabilities. You will learn how to use a variety of hacking tools and techniques. Software Development Course Tambaram, This knowledge can be used to conduct penetration tests, or to help organizations investigate security incidents.
You will learn how to think like a hacker. This understanding can help you to better understand the threats that your systems face, and to develop more effective security measures. You will gain valuable experience in the field of cyber security. This experience can be used to improve your job prospects, or to start your own cyber security consulting business.
To consider when choosing a Full Stack Developer Training institute:
The curriculum: Make sure that the curriculum covers the topics you are interested in learning. The trainers: Make sure that the trainers are experienced and knowledgeable in the topics they are teaching. The facilities: Make sure that the institute has the facilities you need to learn effectively. The cost: Make sure that the cost of the training is within your budget. Software development courses may also cover other topics, such as: Web development: Web development is the process of creating websites and web applications. Data science: Data science is the process of extracting insights from data. Full Stack Developer Training in Tambaram.
Machine learning: Machine learning is a type of artificial intelligence that allows computers to learn without being explicitly programmed. Software development courses can be a great way to learn the skills you need to develop software. However, it is important to choose a course that is right for you. If you are not sure which course is right for you, I recommend talking to a career counselor or doing some research online.
0 notes