#CyberRecovery
Explore tagged Tumblr posts
Text
Dell CyberSense Integrated with PowerProtect Cyber Recovery
Cybersense compatibility
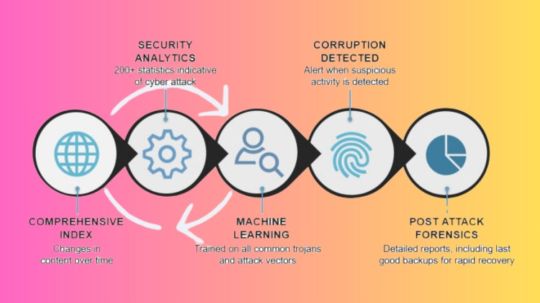
A smart approach to cyber resilience is represented by Dell CyberSense, which is integrated with the Dell PowerProtect Cyber Recovery platform. In order to continuously verify data integrity and offer thorough insights across the threat lifecycle, it leverages cutting-edge machine learning and AI-powered analysis, drawing on decades of software development experience. This significantly lessens the impact of an attack minimizing data loss, expensive downtime, and lost productivity and enables organisations to quickly recover from serious cyberthreats, like ransomware.
Over 7,000 complex ransomware variations have been used to thoroughly train CyberSense’s AI engine, guaranteeing accuracy over time. Up to 99.99% accuracy in corruption detection is achieved by combining more than 200 full-content-based analytics and machine learning algorithms. A sophisticated and reliable solution for contemporary cyber resilience requirements, Dell CyberSense boasts more than 1,400 commercial deployments and benefits its customers from the combined knowledge and experience acquired from real-world experiences with malware.
By keeping its defence mechanisms current and efficient, this continual learning process improves its capacity to identify and address new threats. In order for you to recover from a cyberattack as soon as possible, Dell CyberSense also uses data forensics to assist you in finding a clean backup copy to restore from.
Dell PowerProtect Cyber Recovery
The financial effects of Dell PowerProtect Cyber Recovery and Dell CyberSense for enterprises were investigated in a Forrester TEI study that Dell commissioned. According to research by Forrester, companies using Dell CyberSense and PowerProtect Cyber Recovery can restore and bring back data into production 75% faster and with 80% less time spent searching for the data.
When it comes to cybersecurity, Dell CyberSense stands out due to its extensive experience and track record, unlike the overhyped claims made by storage vendors and backup firms who have hurriedly rebranded themselves as an all-in-one solution with AI-powered cyber detection and response capabilities. The ability of more recent market entrants, which are frequently speculative and shallow, is in sharp contrast to CyberSense’s maturity and expertise.
Businesses may be sure they are selecting a solution based on decades of rigorous development and practical implementation when they invest in PowerProtect Cyber Recovery with Dell CyberSense, as opposed to marketing gimmicks.
Before Selecting AI Cyber Protection, Consider These Three Questions
Similar to the spike in vendors promoting themselves as Zero Trust firms that Dell saw a year ago, the IT industry has seen a surge in vendors positioning themselves as AI-driven powerhouses in the last twelve months. These vendors appear to market above their capabilities, even though it’s not like they lack AI or Zero Trust capabilities. The implication of these marketing methods is that these solutions come with sophisticated AI-based threat detection and response capabilities that greatly reduce the likelihood of cyberattacks.
But these marketing claims are frequently not supported by the facts. As it stands, the efficacy of artificial intelligence (AI) and generative artificial intelligence (GenAI) malware solutions depends on the quality of the data used for training, the precision with which threats are identified, and the speed with which cyberattacks may be recovered from.
IT decision-makers have to assess closely how providers of storage and data protection have created the intelligence underlying their GenAI inference models and AI analytics solutions. It is imperative to comprehend the training process of these tools and the data sources that have shaped their algorithms. If the wrong training data is used, you might be purchasing a solution that falls short of offering you the complete defence against every kind of cyberthreat that could be present in your surroundings.
Dell covered the three most important inquiries to put to your providers on their AI and GenAI tools in a recent Power Protect podcast episode:
Which methods were used to train your AI tools?
Extensive effort, experience, and fieldwork are needed to develop an AI engine that can detect cyber risks with high accuracy. In order to create reliable models that can recognise all kinds of threats, this procedure takes years to gather, process, and analyse enormous volumes of data. Cybercriminals that employ encryption algorithms that do not modify compression rates, such as the variation of the ransomware known as “XORIST,” these sophisticated threats may have behavioural patterns that are difficult for traditional cyber threat detection systems to detect since they rely on signs like changes in metadata and compression rates. Machine learning systems must therefore be trained to identify complex risks.
Your algorithms are based on which data sources?
Knowing the training process of these tools and the data sources that have influenced their algorithms is essential. AI-powered systems cannot generate the intelligence required for efficient threat identification in the absence of a broad and varied dataset. To stay up with the ever-changing strategies used by highly skilled adversaries, these solutions also need to be updated and modified on a regular basis.
How can a threat be accurately identified and a quick recovery be guaranteed?
Accurate and secure recovery depends on having forensic-level knowledge about the impacted systems. Companies run the danger of reinstalling malware during the recovery process if this level of information is lacking. For instance, two weeks after CDK Global’s customers were rendered unable to access their auto dealership due to a devastating ransomware assault, the company received media attention. They suffered another ransomware attack while they were trying to recover. Unconfirmed, but plausible, is the theory that the ransomware was reintroduced from backup copies because their backup data lacked forensic inspection tools.
Read more on govindhtech.com
#DellCyberSense#Integrated#CyberRecovery#DellPowerProtect#AIengine#AIpowered#AI#ZeroTrust#artificialintelligence#cyberattacks#Machinelearning#ransomware#datasources#aitools#aicyber#technology#technews#news#govindhtech
0 notes
Text
Dell PowerProtect Data Manager for VMware Telco Cloud Server

Dell PowerProtect Data Manager
Data security is critical in the ever changing telecommunications industry, as 5G networks are being developed quickly. Communications service providers (CSPs) require strong solutions to protect their vital workloads and components when they adopt cloud-native platforms such as VMware Telco Cloud Platform. For VMware Telco Cloud Platform users, Dell PowerProtect Data Manager is a comprehensive data protection solution.
PowerProtect Data Manager Administration and user Guide
CSPs can now install and manage containerised network functions (CNFs) and virtual network functions (VNFs) across dispersed 5G networks thanks to VMware Telco Cloud Platform. CSPs can efficiently modernise their infrastructure thanks to the VMware Telco Cloud Platform’s orchestration features, operational consistency, and holistic visibility. However, to avoid downtime and data loss and to guarantee quick recovery in the event of a disaster, any modernised environment needs a strong data protection plan.
New Dell PowerProtect Data Manager
Dell Technologies is aware of how important data security is in the current telecom environment. The Dell PowerProtect Data Manager was developed specifically to handle the special difficulties that CSPs using the VMware Telco Cloud Platform encounter. Let’s examine its main attributes:
Data protection specified by software
Dell PowerProtect Data Manager provides adaptable compliance and data protection for cloud-native IT infrastructures and apps. Because of its software-defined methodology, it can adapt to changing applications and workloads.
Specialised defence for telecom cloud platform elements
For mission-critical operations, CSPs depend on the components of VMware’s Telco Cloud Platform. These components are guaranteed to be available without interfering with business operations by Dell PowerProtect Data Manager. Your vital workloads are safeguarded, whether they are application instances or management/workload clusters.
Independent functioning
In Dell PowerProtect Data Manager, automated discovery and protection are fundamental functions. Databases, virtual computers, file systems, and Kubernetes containers are all expertly protected. This leads to automated, dependable, and professional data protection.
Effective safeguarding of data
Dell PowerProtect Data Manager and Dell PowerProtect DD series appliances have a smooth integration. Data can be immediately protected by these appliances, and optional replication to safe Cyber Recovery vaults is also available. Data protection that is scalable, dependable, and efficient is now achievable.
Self-service restoration and backup
Give data owners the ability to self-serve. Through native interfaces from Dell Technologies, CSPs may easily start backups and restores. Eliminate reliance on dedicated IT teams for standard data protection duties.
Features
Designed with a purpose
Data Domain appliances offer performance, efficiency, and security benefits that streamline operations, lessen risk, and save costs. They are specifically developed and optimised for data protection. Furthermore, it may be easily integrated into already-existing on-premises setups thanks to a wide backup software ecosystem.
Integrated cyber resilience features
Data Domain offers several tiers of Zero Trust security to support the integrity and immutability of data.
For mental tranquilly
Have faith in your ability to bounce back from unforeseen circumstances. You can guarantee complete cyber resilience no matter where your data resides by using software-defined Dell APEX Protection Storage in multicloud environments or Data Domain for on-premises data protection.
Cyber-resistant data security
With simple-to-use management and automation tools, you can detect suspicious behaviour, protect sensitive data against ransomware and the cyberattacks, and recover lost data.
Protection of data across many clouds
Safeguard any task in any cloud setting. Multicloud data security solutions from Dell Technologies offer a wide range of workloads, from cloud-native apps to legacy data.
There is more to this solution than just technology. Complete development and verification took place in Dell’s Open Telco Ecosystem Lab (OTEL), confirming Dell PowerProtect Data Manager for VMware Telco Cloud Platform’s efficacy. To develop this solution, access to the newest, most advanced tools and technologies was made possible via Dell’s OTEL facilities. A worldwide, electronically accessible lab made possible by Dell Technologies’ hybrid networking strategy allowed for smooth collaboration between VMware and Dell. By using this method, Dell Technology were able to successfully validate the system and increase its usability for mobile carriers. You can be sure that the solution you are implementing complies with best practices and industry standards.
PowerProtect Data Manager
With strong data protection solutions, Dell Technologies supports CSPs as they adopt VMware Telco Cloud Platform. PowerProtect Data Manager makes ensuring that the workloads and components of your Telco Cloud Platform are secure and resilient. Upgrade with assurance, knowing that Dell Technologies is protecting your important information.
The complexity of data protection is rising
Organizations must improve time-to-value, lower overall cost and complexity, plan for expansion, and safeguard an ever-increasing volume of data in a distributed ecosystem of applications and workloads that is expanding. Additionally, cloud computing must be easily integrated into data security plans by organizations. This is difficult to achieve with many of the data protection solutions available today, which either require multiple products and vendors or compromise performance for simplicity, making deployment time-consuming and labor-intensive while offering complex and costly management of fragmented data protection environments.
Data protection that’s easy, effective, and flexible with the PowerProtect DP series appliance. An all-in-one backup appliance, the DP series lessens the strain of juggling several data silos, point solutions, and vendor relationships. For small, mid-size, and business organizations, the DP series offers robust, enterprise-grade data protection features at a low cost of protection, while also streamlining deployment and management.
Complete backup, replication, recovery, deduplication, fast access and restoration, search and analytics, smooth VMware integration, cloud readiness with disaster recovery (DR), and long-term retention (LTR) to the cloud are all included in this integrated solution, which is provided in a single appliance. Customers can become more agile and minimize their time-to-protect with the DP series, which offers a rapid, dependable, efficient, and recoverable solution.
Read more on govindhtech.com
#dellpowerprotect#datamanager#vmware#telcocloudservices#datasecurity#5gnetwork#administration#userguide#newdellpowerprotect#software#Specialiseddefenc#telecomcloud#platformelements#cyberrecovery#zerotrustsecurity#dellapex#technology#techneews#news#govindhtech
0 notes